1. View the current user's home directory
# Switch to Home Directory
cd ~
# View Home Directory Location pwd
2. Check whether the server is maliciously logged on
# Ubuntu # 1. View recent successful password logins: grep "password" /var/log/auth.log | grep -v Failed | grep -v Invalid # 2. View recent login failures IP And each IP Number of failures: awk '{if($6=="Failed"&&$7=="password"){if($9=="invalid"){ips[$13]++;users[$11]++}else{users[$9]++;ips[$11]++}}}END{for(ip in ips){print ip, ips[ip]}}' /var/log/auth.log | sort -k2 -rn #3. View the usernames and number of recent login failures: awk '{if($6=="Failed"&&$7=="password"){if($9=="invalid"){ips[$13]++;users[$11]++}else{users[$9]++;ips[$11]++}}}END{for(user in users){print user, users[user]}}' /var/log/auth.log | sort -k2 -rn
# CentOS # 1. View successful login grep "Accepted password for" /var/log/secure # 2. View the number of failures per user name grep "Failed password" /var/log/secure | awk '{if (NF==16){c[$11]++}else{c[$9]++}}END{for(u in c)print u,c[u]}' | sort -k 2 -nr | head # 3. View each IP Number of address failures grep "Failed password" /var/log/secure | awk '{if (NF==16){c[$13]++}else{c[$11]++}}END{for(u in c)print u,c[u]}' | sort -k 1 -n | head
3. Server prohibits root Account Logon
Because: Since you have a Linux machine with a public network IP, this information will appear every time you log on: (roughly: someone tried to log on to your server but the account name or password was incorrect which caused the logon to fail [Check it out more] Check if the server is maliciously logged on])
There were 4899 failed login attempts since the last successful login. Last login: Thu Aug 21 15:45:34 2014 from 87.201.230.138 -bash: warning: setlocale: LC_CTYPE: cannot change locale (UTF-8): No such file or directory
So: I chose to turn off the root user (note: some directories may not be accessible when using sftp after the root user is disabled)
(1) Log in to the system using the root account, add a normal account such as test, and set a password for it
# Add a new account useradd test # Set password for test account passwd test # Input password # Re-enter the confirmation password
(2) Edit the configuration file/etc/ssh/sshd_config (vim can be used, vim Use Tutorial (Note: This number of failures is for all users.)
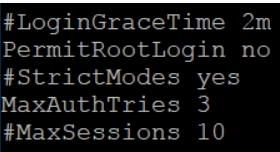
(3) Restart sshd service at last systemctl restart sshd.service, which is then logged in with the root user. Failure to log in indicates successful configuration. You can switch using su/sudo if root privileges are required
4. Linux Delete Ordinary User Steps
(1) Use commands first Cat/etc/passwd Check out all users You can see a slice of the username you need to delete
(2) Using commands who Query the currently logged on user
(3) Using commands Ps-u user name View the user's pid
(4) Using commands kill pid kill his sshd or shell process
(5) Reuse commands Userdel-r username delete user
If you still can't delete the user at this time, it's because there are still processes to kill. Under root,
Enter instruction ps-ef | grep username Delete the first process (there may be other connected processes that don't need to be managed), then execute Step 5
Blog reference:
See where the user's home directory is in linux