In Linux system management, it is sometimes necessary to set account password complexity (length), password expiration policy and so on, which is mainly controlled by some parameters in the / etc/login.defs parameter file. It is mainly used for user account restriction. The parameters are as follows:
/etc/login.defs:
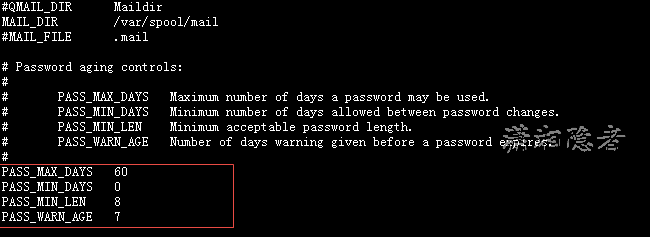
# Password aging controls:
#
# PASS_MAX_DAYS Maximum number of days a password may be used.
# PASS_MIN_DAYS Minimum number of days allowed between password changes.
# PASS_MIN_LEN Minimum acceptable password length.
# PASS_WARN_AGE Number of days warning given before a password expires.
PASS_MAX_DAYS 60 #The maximum validity of the password, where the parameter PASS_MAX_DAYS is 60, indicates that the password will expire after 60 days. 99999 means it will never expire.
PASS_MIN_DAYS 0 #The minimum interval between two password changes is 0, which means you can change your account password at any time.
PASS_MIN_LEN 8 #Minimum password length, invalid for root
PASS_WARN_AGE 7 #How many days before the password expires
#
# Min/max values for automatic uid selection in useradd
#
UID_MIN 500
UID_MAX 60000
UID_MIN #Minimum User ID
UID_MAX #Maximum User ID
#
# Min/max values for automatic gid selection in groupadd
#
GID_MIN 500
GID_MAX 60000
GID_MIN #Minimum Group ID
GID_MAX #Maximum Group ID
#
# If defined, this command is run when removing a user.
# It should remove any at/cron/print jobs etc. owned by
# the user to be removed (passed as the first argument).
#
#USERDEL_CMD /usr/sbin/userdel_local
USERDEL_CMD #Default comment status, if defined, indicates that when a user is deleted, the user owned by the user, such as the work of deleting/printing/cron, should be deleted (passed as the first parameter).
#
# If useradd should create home directories for users by default
# On RH systems, we do. This option is overridden with the -m flag on
# useradd command line.
#
CREATE_HOME yes
CREATE_HOME #Indicates whether to create a user home directory.
# The permission mask is initialized to this value. If not specified,
# the permission mask will be initialized to 022.
UMASK 077
UMASK #Privilege mask initialization value
# This enables userdel to remove user groups if no members exist.
#
USERGROUPS_ENAB yes
USERGROUPS_ENAB #This parameter is enabled to indicate that when userdel deletes a user, if the user group does not exist, the user group is deleted
# Use MD5 or DES to encrypt password? Red Hat use MD5 by default.
MD5_CRYPT_ENAB yes
ENCRYPT_METHOD MD5
ENCRYPT_METHOD #Represents how user passwords are encrypted, where MD5 is used to encrypt passwords
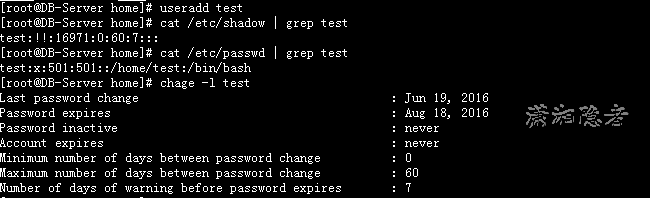
Modifying the parameters under / etc/login.defs takes effect immediately, but only for the user created after the modification. For example, after modifying the PASS_MAX_DAYS parameter, we created a new user test.
[root@DB-Server home]# useradd test
[root@DB-Server home]# cat /etc/shadow | grep test
test:!!:16971:0:60:7:::
[root@DB-Server home]# cat /etc/passwd | grep test
test:x:501:501::/home/test:/bin/bash
[root@DB-Server home]# chage -l test
Last password change : Jun 19, 2016
Password expires : Aug 18, 2016
Password inactive : never
Account expires : never
Minimum number of days between password change : 0
Maximum number of days between password change : 60
Number of days of warning before password expires : 7
[root@DB-Server home]#
Because CREATE_HOME is yes, after user test is created, the test directory is created by default in the / home directory, which can be viewed or modified in the add user's rule file / etc/default/useradd.
[root@DB-Server ~]# cat /etc/default/useradd
# useradd defaults file
GROUP=100
HOME=/home #Build the user's home directory in / home
INACTIVE=-1 #Whether to enable account expiration suspension, -1 means not to enable
EXPIRE= #The account termination date is not set to indicate that it is not enabled.
SHELL=/bin/bash #The type of SHELL used;
SKEL=/etc/skel #The default directory for adding users is the default file location; that is, when we add users with adduser, the files in the user's home directory are copied from this directory.
CREATE_MAIL_SPOOL=yes
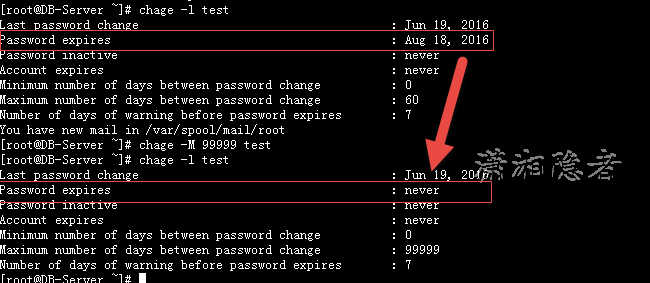
If at this point, if the user test has special requirements, the password of this account will never expire, then you can use the chage command to process (about the chage command, do not expand here)
[root@DB-Server ~]# chage -l test
Last password change : Jun 19, 2016
Password expires : Aug 18, 2016
Password inactive : never
Account expires : never
Minimum number of days between password change : 0
Maximum number of days between password change : 60
Number of days of warning before password expires : 7
You have new mail in /var/spool/mail/root
[root@DB-Server ~]# chage -M 99999 test
[root@DB-Server ~]# chage -l test
Last password change : Jun 19, 2016
Password expires : never
Password inactive : never
Account expires : never
Minimum number of days between password change : 0
Maximum number of days between password change : 99999
Number of days of warning before password expires : 7
[root@DB-Server ~]#
As shown above, / etc/login.defs only controls the minimum length of the account and the validity of the password. How does Linux check the complexity of the user's password? In fact, the system has two parts to control the password:
1 cracklib
2 /etc/login.defs
Pam_cracklib.so is the key file to control the complexity of password/lib/security/pam_cracklib.so. Redhat company has developed cracklib installation package to judge the complexity of password. If you want to see some parameters of pam_cracklib, use the following command
[root@DB-Server security]# man pam_cracklib
Some of the common parameters are
retry=N
Change the number of times the password is entered. The default value is 1. That is to say, if the password input by the user is not strong enough, it will exit. You can use this option to set the number of times you enter so that you don't start all over again.
Prompt user at most N times before returning with error. The
default is 1
minlen=N
Minimum acceptable length of new password
The minimum acceptable size for the new password (plus one if
credits are not disabled which is the default). In addition to the
number of characters in the new password, credit (of +1 in length)
is given for each different kind of character (other, upper, lower
and digit). The default for this parameter is 9 which is good for a
old style UNIX password all of the same type of character but may
be too low to exploit the added security of a md5 system. Note that
there is a pair of length limits in Cracklib itself, a "way too
short" limit of 4 which is hard coded in and a defined limit (6)
that will be checked without reference to minlen. If you want to
allow passwords as short as 5 characters you should not use this
module.
difok=N
The default value is 10. This parameter sets the number of identical characters allowed for new and old passwords. However, if one-second of the characters in the new password are different from the old one, the new password is accepted.
This argument will change the default of 5 for the number of
characters in the new password that must not be present in the old
password. In addition, if 1/2 of the characters in the new password
are different then the new password will be accepted anyway.
dcredit=N
Limit at least how many digits are in the new password
(N >= 0) This is the maximum credit for having digits in the new
password. If you have less than or N digits, each digit will count
+1 towards meeting the current minlen value. The default for
dcredit is 1 which is the recommended value for minlen less than
10.
(N < 0) This is the minimum number of digits that must be met for a
new password.
ucredit=N
Limit the number of uppercase characters in the new password.
lcredit=N
Limit the number of lowercase characters in the new password.
For example, in / etc/pam.d/system-auth, the last additional dcredit=3 ucredit=2 is set in password using pam_cracklib.so
password requisite pam_cracklib.so try_first_pass retry=3 dcredit=3 ucredit=2
password sufficient pam_unix.so md5 shadow nullok try_first_pass use_authtok
password required pam_deny.so
At this point, if your new user's password does not match the password complexity, a BAD PASSWORD: it is based on a dictionary word prompt will appear.
[root@DB-Server ~]# passwd ttt
Changing password for user ttt.
New UNIX password:
BAD PASSWORD: it is based on a dictionary word