1, HTTP protocol
- Plaintext
- No built-in confidentiality security mechanism
Sniffing or proxy truncation can view all plaintext information
https can only improve transport layer security
- Stateless
Each communication between client and server is an independent process
WEB applications need to track client sessions (multi-step communication)
For applications that do not use cookie s, the client needs to re authenticate every request (unrealistic)
Session is used to track user behavior after user authentication
Improved user experience, but increased attack vectors
- cycle
Request response
- Important header
- Set Cookie: SessionID sent by the server to the client (risk of being stolen)
- Content length: the byte length of the response body part
- Location: redirect the user to another page to identify the page that can be accessed after authentication
- Cookie: information sent back by the client to the server to prove the user's status (header: values appear in pairs)
- Referrer: before initiating a new request, the user is on which page, and the server's security restrictions based on this header can be easily modified and bypassed
- Response packet status code
- 100s: server response information, usually indicating that the server has subsequent processing, which rarely occurs
- 200s: the response result returned after the request is successfully accepted and processed by the server
- 300s: redirect, usually to a secure page after successful authentication (301 / 302)
- 400s: indicates a client request error
• 401: authentication required
• 403: access denied
• 404: target not found - 500s: server internal error (503: service unavailable)
2, Experimental environment
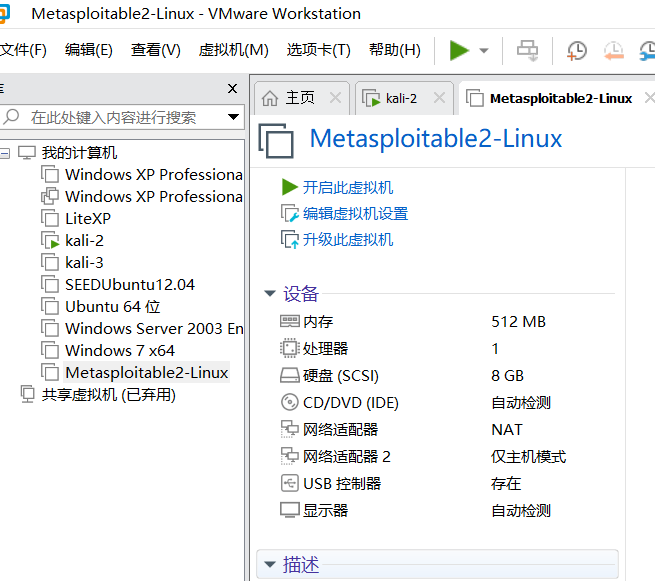
Metasploitable
Direct download target open
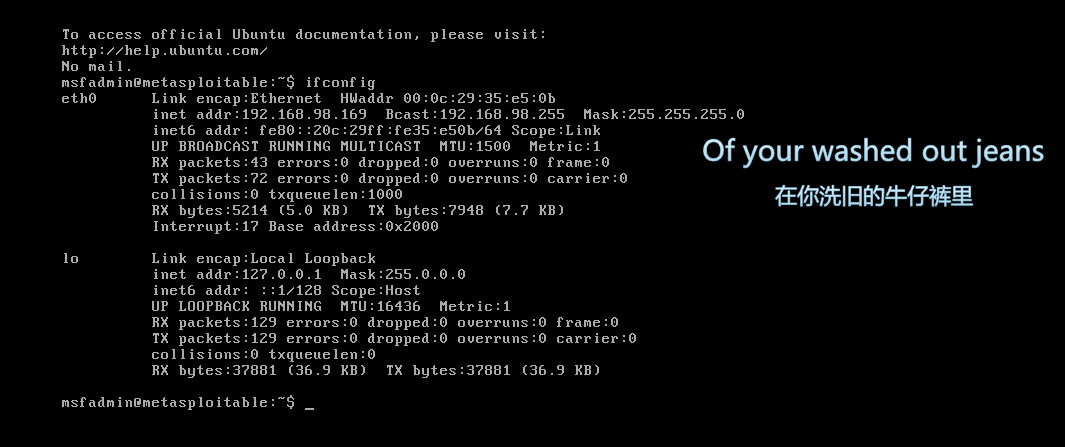
• Dvwa
hey
3, Scanning tool
• Nikto
• Vega
• Skipfish
• W3af
• Arachni
• Owasp-zap
HTTrack crawls the whole station
Crawl the web pages of the whole station for offline browsing to reduce interaction with the target system
Nikto
• open source web security scanner developed in Perl
• software version
• search for files with security risks
• server configuration vulnerabilities
• potential safety hazards at the WEB Application level
• avoid 404 miscalculation
• many servers do not comply with the RFC standard and return a 200 response code for non-existent objects
• according to the response file content, the response content of file 404 with different extensions is different
• take the MD5 value for the content after removing the time information
• -no404
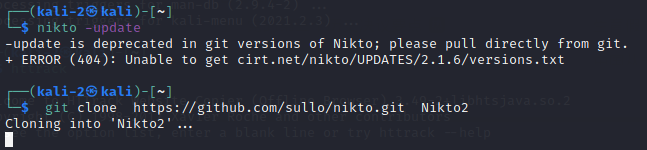
1. Install and update
git clone https://github.com/sullo/nikto.git Nikto2 # After that, nikto.pl will be in the Nikto2/program / directory (also found in the documentation directory). # To keep Nikto updated, simply go to the directory in your warehouse and type: git pull
2. List plug-ins
• nikto -list-plugins
• nikto -update # upgrade databases and plug-ins
• cirt.net
3. Basic scanning
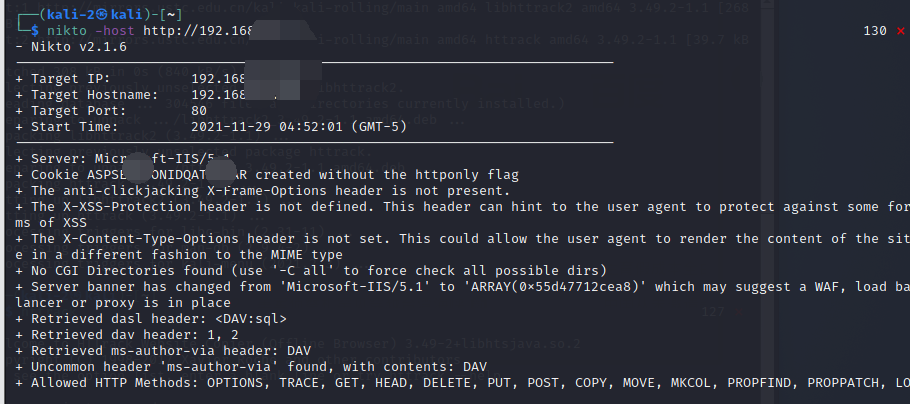
# VPN proxy using local settings • nikto -host 192.168.1.1 -useproxy http://localhost:8087 • nikto -vhost domain name
• http://cirt.net/nikto/UPDATES # url • nikto -host http:// 1.1.1.1
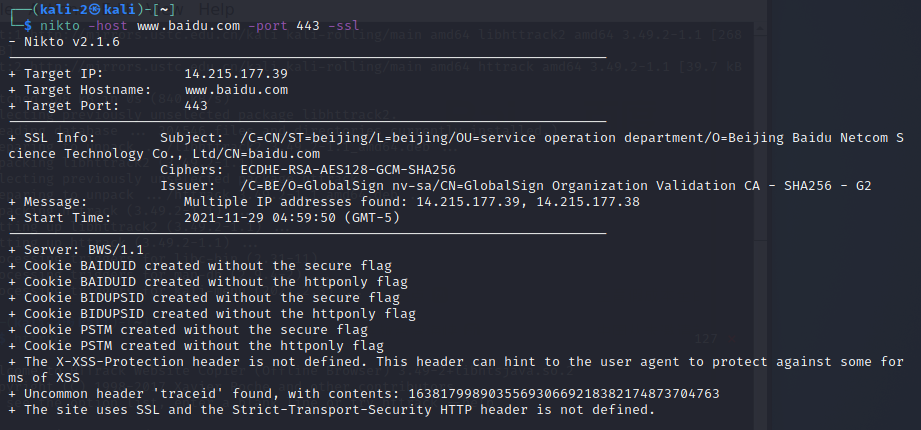
# Specify host and port • nikto -host 192.168.1.1 -ssl -port 443,8443,995 nikto -host www.baidu.com -port 443 -ssl
# Batch scan • nikto -host host.txt
# Scan hosts discovered by nmap nmap -p80 192.168.98.0/24 -oG - | nikto -host - ┌──(kali-2㉿kali)-[~] └─$ nmap -p80 192.168.98.0/24 -oG - | nikto -host - 1 ⨯ - Nikto v2.1.6 --------------------------------------------------------------------------- + nmap Input Queued: 192.168.98.131:80 + Target IP: 192.168.98.131 + Target Hostname: 192.168.98.131 + Target Port: 80 + Start Time: 2021-11-29 05:02:14 (GMT-5) --------------------------------------------------------------------------- + Server: Microsoft-IIS/5.1 + Cookie ASPSESSIONIDQATRSDAR created without the httponly flag + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + No CGI Directories found (use '-C all' to force check all possible dirs) + Server banner has changed from 'Microsoft-IIS/5.1' to 'ARRAY(0x556b6197a130)' which may suggest a WAF, load balancer or proxy is in place + Retrieved dasl header: <DAV:sql> + Retrieved dav header: 1, 2 + Retrieved ms-author-via header: DAV + Uncommon header 'ms-author-via' found, with contents: DAV + Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
4. Nikto interactive
• Space – report current scan status
• v – verbose mode on/off
• d – debug mode on/off # and its details
• e – error reporting on/off
• p – progress reporting on/off
• r – redirect display on/off
• c – cookie display on/off
• a – auth display on/off
• q – quit
• N – next host
• P - Pause
5. Configure file settings to automatically log in and scan using cookie s
• profile
• /etc/nikto.conf
• STATIC-COOKIE="cookie1"="cookie value";"cookie2"="cookie valu"
6. -evasion
Using the IDS avoidance technology in libwhistler, the following types can be used:
• 1 random URL encoding (non UTF-8 mode)
• 1 2self selected path (/. /)
• 3 prematurely terminated URL s
• 4 give priority to long random strings
• 5 parameter spoofing
• 6 use TAB as the separator for commands
• 7 use changing URL s
• 8 use the Windows path separator \ "