Common CNI network plug-ins include the following:
Flannel: Provides network plug-in for overlay network for Kubernetes. Based on TUN/TAP tunneling technology, uses UDP to encapsulate IP messages to create overlay network. Maintains network allocation with etcd. Disadvantage: Unable to support network policy access control.
Calico: A three-tier network plug-in based on BGP also supports network policy for network access control; it runs a virtual route on each host, forwards network packets using the Linux kernel, and implements firewall functions with iptables.In fact, Calico's final implementation is to turn each host into a router, connect each network, and achieve cross-host communication.
Canal: A unified network plug-in jointly published by Flannel and Coalico that provides CNI network plug-ins and supports network policy implementation.
Others include Weave Net, Contiv, OpenContrail, Romana, NSX-T, kube-router, and more.Flannel and Alico are currently the most popular options.
1. Reject All
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-all-egress
namespace: cs1
#Apply to cs1 namespace, do not write namespace to default
spec:
podSelector: {}
ingress:
egress:
#Define the outbound rule. No policy is written here to deny it all.
policyTypes:
- Egress
- Ingress
#If you have Egress, you will define an outbound rule. If you do not write Egress, you will have the default pass. Ingress is inbound in the same way
#It's recommended that you write both and use "podSelector:" to control passage2. Allow All
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-all-egress
namespace: cs1
spec:
podSelector: {}
ingress:
- {}
#This means that all traffic is allowed in the "ingress" direction
egress:
- {}
#This means that all traffic is allowed in the "egress" direction
policyTypes:
- Egress
- IngressThis network policy only works with namespaces and the host is still accessible
3. Scope of action
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-all
namespace: default
#Act only on default namespace
spec:
podSelector:
#Match the pod range if it matches all the POD inputs'{}'for that namespace
matchLabels:
access: "true"
#Label with access=true in matching POD
policyTypes:
- Ingress
- Egress
ingress:
egress:4. Restrict IP Policy
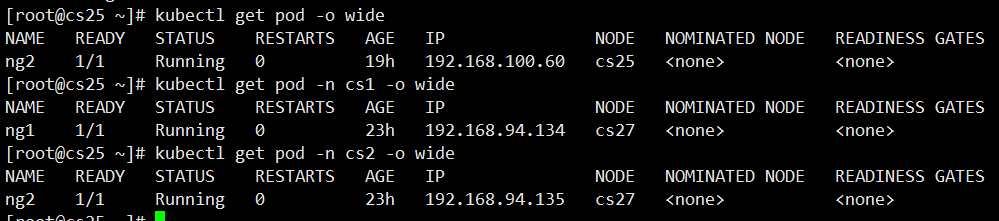
#IP for each cs container shown above
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-all
spec:
podSelector: {}
policyTypes:
- Egress
- Ingress
ingress:
egress:
- to:
#Note: egress uses to, ingress uses from
- ipBlock:
cidr: 192.168.0.0/16
#Release 192.168.0.0/16 Network
except:
- 192.168.94.134/32
#But do not include this ip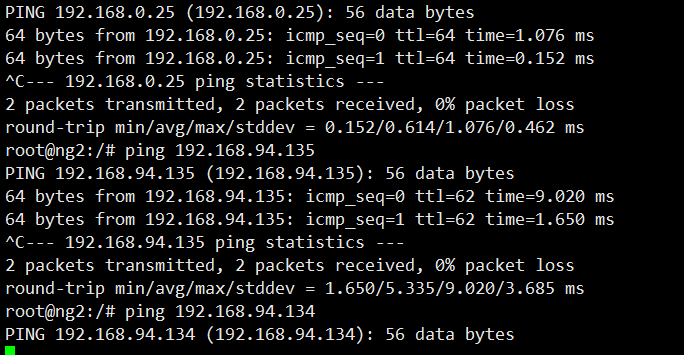
Exc entering pod can see ping192.168.94.134 This IP is not available
5. Namespace label restrictions
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: namespace-allow
namespace: default
spec:
policyTypes: ["Ingress"]
podSelector: {}
ingress:
- from:
- namespaceSelector:
matchLabels:
name: cs1
#Indicates that only namespaces typed "name=cs1" are allowed to enter6. Multiple conditions are satisfied based on namespace label restrictions
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: namespace-allow
namespace: default
spec:
policyTypes: ["Ingress","Egress"]
podSelector: {}
ingress:
- from:
- namespaceSelector:
matchExpressions:
- key: name
operator: In
values: ["cs1","cs2"]
#The default namespace ingress can be communicated within brackets
#Indicates that the namespace has the label name=cs1,name=cs2 to communicate with the default namespace7 based on pod label
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: namespace-allow
namespace: default
spec:
policyTypes: ["Ingress"]
podSelector: {}
ingress:
- from:
- podSelector:
matchLabels:
access: "true"
#Allow pod notes to have access=true traffic#Don't know anything about unsuccessful pod label-based experiments