install
Prepare k8s environment in advance and download Istio installation package , I use version 1.6.14 here, and the k8s version is v1.19.8
tar zxvf istio-1.6.14-linux-amd64.tar.gz cd istio-1.6.14/ cp bin/istioctl /usr/bin
View a list of profiles for different installation modes
istioctl profile list
You can print the contents of the configuration file (optional)
istioctl profile dump [Profile name]
Configuration installation using demo mode
[root@ istio-1.6.14]# istioctl manifest apply --set profile=demo Detected that your cluster does not support third party JWT authentication. Falling back to less secure first party JWT. See https://istio.io/docs/ops/best-practices/security/#configure-third-party-service-account-tokens for details. ✔ Istio core installed ✔ Istiod installed ✔ Ingress gateways installed ✔ Egress gateways installed ✔ Addons installed ✔ Installation complete
Verify that the installation was successful
[root@ istio-1.6.14]# kubectl get pod -n istio-system NAME READY STATUS RESTARTS AGE grafana-7647cf9c74-lvbhp 1/1 Running 0 6m51s istio-egressgateway-6999674db4-tsm28 1/1 Running 0 6m55s istio-ingressgateway-66757b946f-qqvms 1/1 Running 0 6m55s istio-tracing-7fcc6f5848-n99wt 1/1 Running 0 6m50s istiod-7c966f79c4-76zl2 1/1 Running 0 7m38s kiali-7f575d9c4c-ndlc6 1/1 Running 0 6m50s prometheus-fcbb8cbdd-vdm2v 2/2 Running 0 6m50s
Temporarily expose port 20001 in port forwarding mode and enter kiali interface
kubectl port-forward --address 0.0.0.0 kiali-7f575d9c4c-ndlc6 20001 -n istio-system
If you want to expose the port directly, set NodePort to expose the port
kubectl -n istio-system edit svc kiali
Change to the following figure
ports:
- name: http-kiali
nodePort: 32660
port: 20001
protocol: TCP
targetPort: 20001
selector:
app: kiali
sessionAffinity: None
type: NodePort
status:
loadBalancer: {}
Other services installed in istio, such as grafana and Jaeger(tracing), can also be exposed in this way
kubectl -n istio-system get svc
Run the sample microservice Bookinfo
Bookinfo - online book store
Architecture diagram:
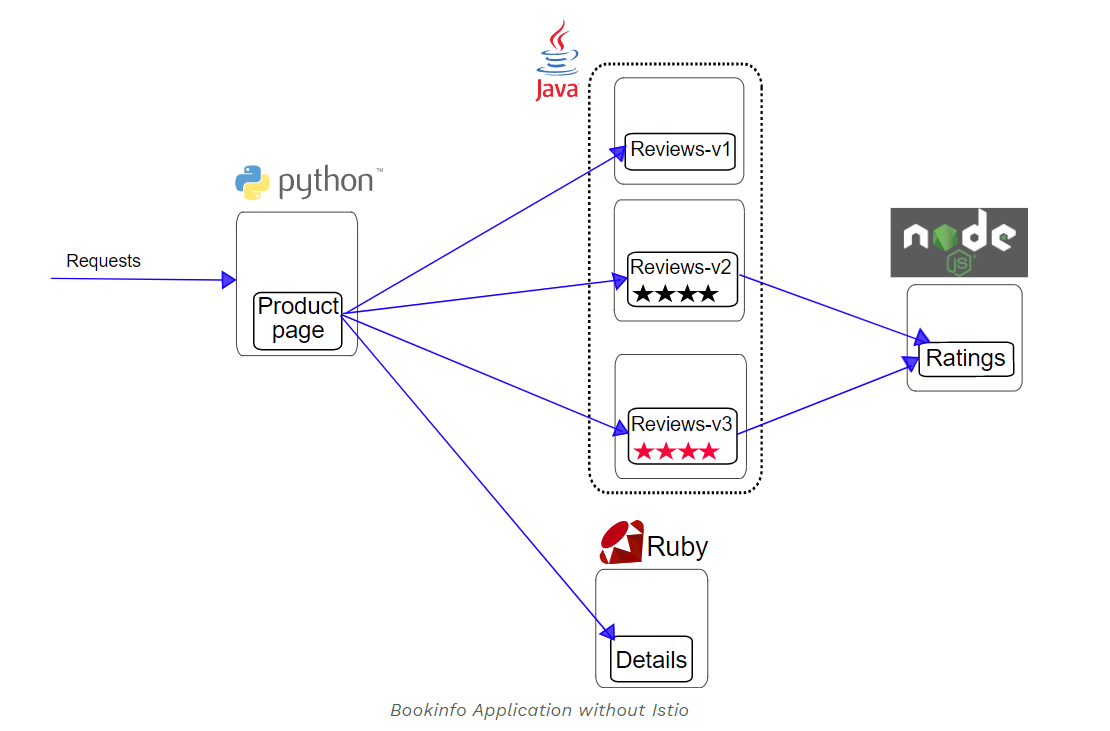
The Bookinfo application is divided into four separate microservices. These services do not depend on Istio, but constitute a representative service grid example: it is composed of services written in multiple languages, and one application will contain multiple versions.
- productpage will call two microservices, details and reviews, to generate pages.
- details contains information about books.
- reviews contain comments about books. It also calls the ratings microservice.
- ratings contains rating information composed of book reviews.
There are three versions of reviews microservice, which can be used to show different call links between services:
- The v1 version does not call the ratings service.
- v2 version will call the ratings service and use 1 to 5 Black Star icons to display the rating information.
- The v3 version calls the ratings service and uses 1 to 5 Red Star icons to display rating information.
Create namespace
kubectl create ns bookinfo
Istio] by default, Sidecar is automatically injected and the bookinfo namespace is labeled istio injection = enabled:
kubectl label ns bookinfo istio-injection=enabled
Deployment Services
kubectl apply -f samples/bookinfo/platform/kube/bookinfo.yaml -n bookinfo
View pod
kubectl get po -n bookinfo
Deployment gateway
kubectl apply -f samples/bookinfo/networking/bookinfo-gateway.yaml -n bookinfo
View exposed ports
kubectl get svc -n istio-system
Visit and you can see the page
http://Host ip: port / productpage
compression
for i in {1..100}; do curl -I http://Host ip: port / productpage/productpage; sleep 1; done
Then check kiali, grafana and Jaeger(tracing) and the data will appear. The default account password of kiali is admin