- iptables release sshd services for local access
- First look at filter rules
[root@server23 ~]# iptables -t filter -L -n
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination - There are no default rules above. Next, add and release rules. Here, 172.25.23.0/24 is released for access. First, add on the INPUT chain.
[root@server23 ~]# iptables -t filter -A INPUT -s 172.25.23.0/24 \
-d 172.25.23.23 -p tcp --dport 22 -j ACCEPT- Above is only the release of the request to enter the local machine, followed by the release of sshd out of the data, where you need to change the source address and target address as well as the source port;
[root@server23 ~]# iptables -t filter -A OUTPUT -s 172.25.23.23 -d 172.25.23.0/24 -p tcp --sport 22 -j ACCEPT- View the rules added to the filter table
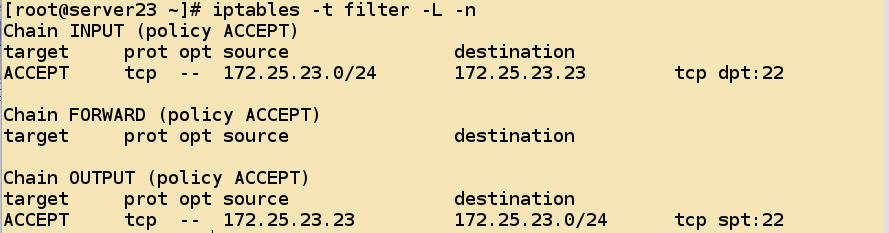
- Add the - v option to view the number of matched messages
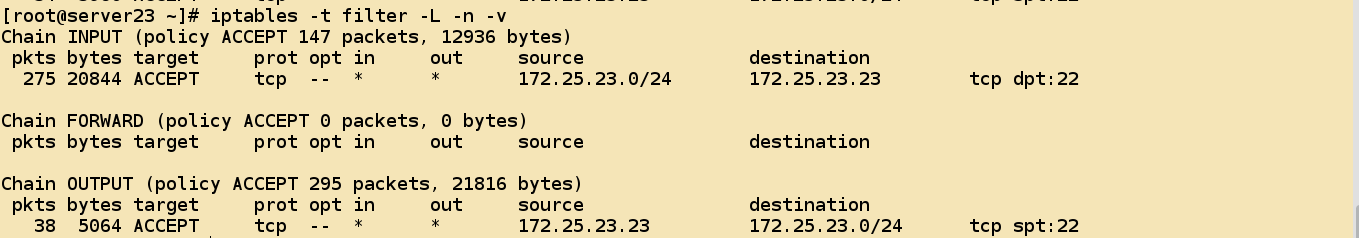
- Detection of access status for DROP service with default policy open
- Because the default rule of this table is ACCEPT, the sshd service is not disconnected. Next, try to change the default policy to DROP, because the default rule of INPUT OUTPUT FORWARD cannot be changed to REJECT.
- Here we open several services httpd:80 mysql-server:3306 vsftpd:21 to check whether the rules are in effect. For filter modification rules, we need to modify the default rules above three chains INPUT OUTPUT FORWARD.
[root@server23 ~]# iptables -P INPUT DROP
[root@server23 ~]# iptables -P OUTPUT DROP
[root@server23 ~]# iptables -P FORWARD DROP- Next, look at the rules
[root@server23 ~]# iptables -L -n
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 172.25.23.0/24 172.25.23.23 tcp dpt:22
Chain FORWARD (policy DROP)
target prot opt source destination
Chain OUTPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 172.25.23.23 172.25.23.0/24 tcp spt:22 - ssh connections are normal because access to 22/tcp ports is allowed.
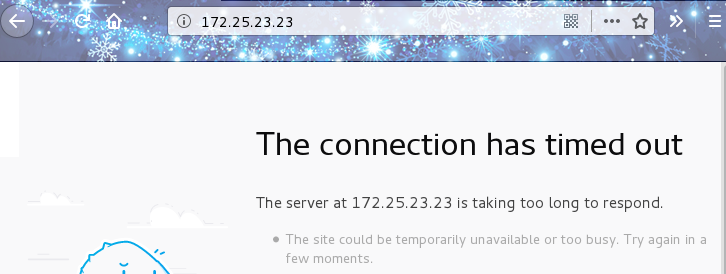
- Services other than sshd are not normally accessible
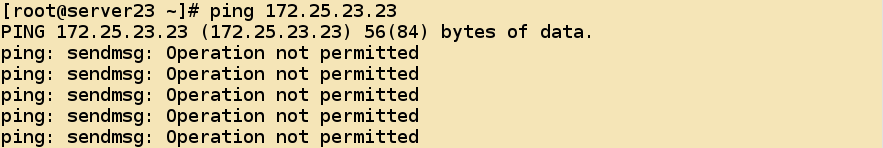
- Service access to ping/icmp protocol is also inaccessible
- Next, release the httpd service
- First, you need to understand the port information used by httpd services and release the service request on the INPUT OUTPUT chain.
[root@server23 ~]# iptables -I INPUT -d 172.25.23.23 -p tcp --dport 80 -j ACCEPT
[root@server23 ~]# iptables -I OUTPUT -s 172.25.23.23 -p tcp --sport 80 -j ACCEPThttpd service access is normal
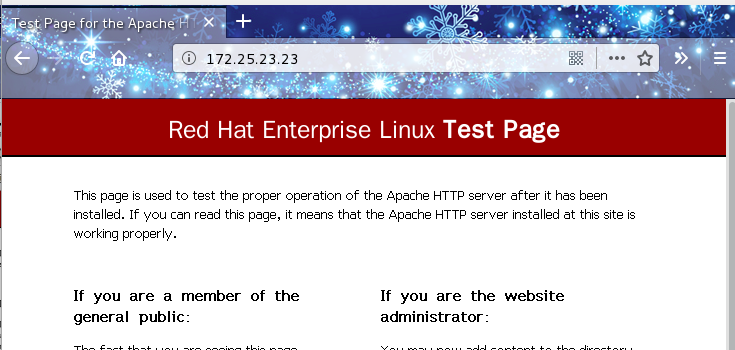
Release local ping requests
- After changing the default policy, the default ping request for the local machine is also rejected. Rules are added here to allow the local machine to ping requests for the local machine.
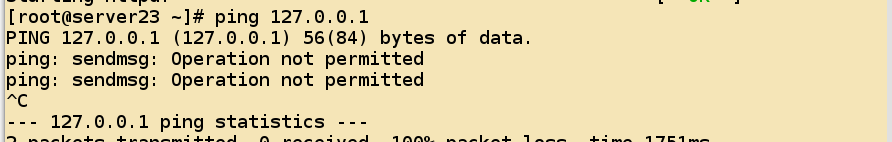
- Adding rules also requires two rules, so that the flow of data is bidirectional
[root@server23 ~]# Iptables-A INPUT-s 127.0.0.1-d 127.0.0.1-i [interface of data inflow and outflow] lo-j ACCEPT
[root@server23 ~]# iptables -A OUTPUT -s 127.0.0.1 -d 127.0.0.1 -o lo -j ACCEPT- View the added rules
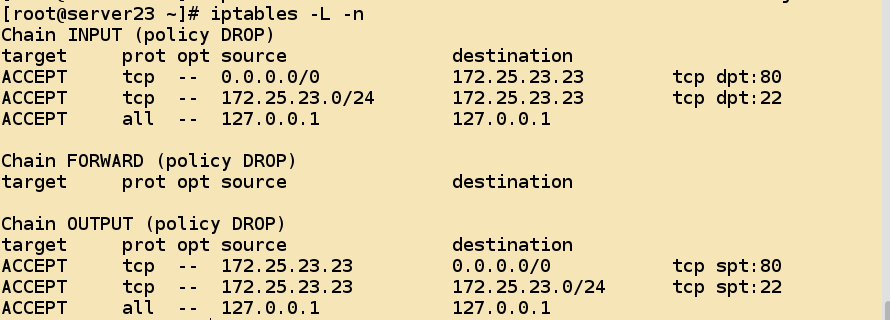
-
ping services are already normal
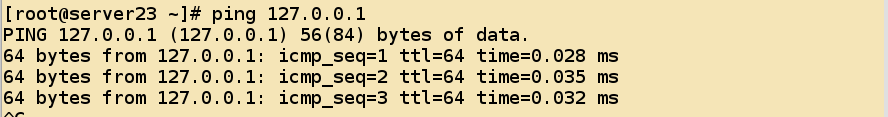
- For external ping requests, there are two states: echo-request, which is represented by number 8, echo-replace by number 0, and release of external ping requests, which include two situations: using one's own to ping the external host or using the external host to ping oneself. The two rules of release are different.
- First, the process of ping ing your own external host
[root@server23 ~]# iptables -A OUTPUT -s 172.25.23.23 -p icmp --icmp-type 8 -j ACCEPT
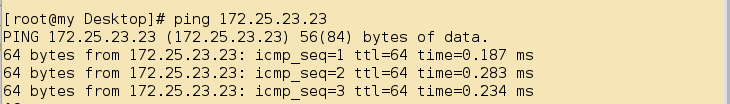
[root@server23 ~]# iptables -A INPUT -d 172.25.23.23 -p icmp --icmp-type 0 -j ACCEPT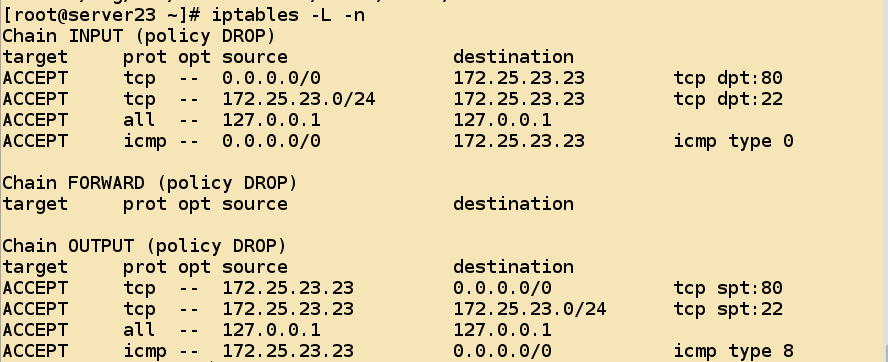
* If you need to implement external main ping internal host
[root@server23 ~]# iptables -A OUTPUT -s 172.25.23.23 -p icmp --icmp-type 0 -j ACCEPT
[root@server23 ~]# iptables -A INPUT -d 172.25.23.23 -p icmp --icmp-type 8
-j ACCEPTThe ping request from the external host will be normal
Firewall Configuration of DNS Server
- For UDP protocol only, four rules are needed. First, DNS server needs to receive user requests as server and return corresponding data. This requires two rules. Secondly, DNS server needs to initiate requests as client to the upper DNS server, and two rules are needed.
[root@server23 ~]# iptables -A INPUT -d 172.25.23.23 -p udp --dport 53 -j ACCEPT
[root@server23 ~]# iptables -A OUTPUT -s 172.25.23.23 -p udp --sport 53 -j ACCEPT
[root@server23 ~]# iptables -A OUTPUT -s 172.25.23.23 -p udp --dport 53 -j ACCEPT
[root@server23 ~]# iptables -A INPUT -d 172.25.23.23 -p udp --sport 53 -j ACCEPT- For udp alone, there are four rules, and for tcp, there are four rules.