Notice: The title, ideas and reference code of the latest autumn signature written test for Huawei and Ali have been sorted out and put in the WeChat Public Number (TechGuide). The most real-time and detailed written test solution can be obtained by replying to the private trust public number (Huawei) or Ali!
Notice: The title, ideas and reference code of the latest autumn signature written test for Huawei and Ali have been sorted out and put in the WeChat Public Number (TechGuide). The most real-time and detailed written test solution can be obtained by replying to the private trust public number (Huawei) or Ali!
Notice: The title, ideas and reference code of the latest autumn signature written test for Huawei and Ali have been sorted out and put in the WeChat Public Number (TechGuide). The most real-time and detailed written test solution can be obtained by replying to the private trust public number (Huawei) or Ali!
Notice: The title, ideas and reference code of the latest autumn signature written test for Huawei and Ali have been sorted out and put in the WeChat Public Number (TechGuide). The most real-time and detailed written test solution can be obtained by replying to the private trust public number (Huawei) or Ali!
First: Cache Forwarding Packet Statistics (100%)
Title Description
There is a forwarding queue of k nodes, each with a forwarding capability of M and a caching capability of n (meaning that this node can forward m packets immediately, the remaining cache, up to n packets cached, and then the remaining discarded packets will continue to be forwarded in the next round).In addition, some nodes in this queue may need to skip forwarding directly due to failures, but there will not be two nodes with continuous failures.
There are now two rounds of operations, the first one sending a packet to this queue for forwarding;The second round directly drives the cached packets to continue forwarding.
Find the total minimum number of packets that may be received in the last two rounds (if there are still packet cache packets to be discarded in the second round of cache)
1 <= k <= 40
1 <= m,n <= 1000
1 <= a <= 1000
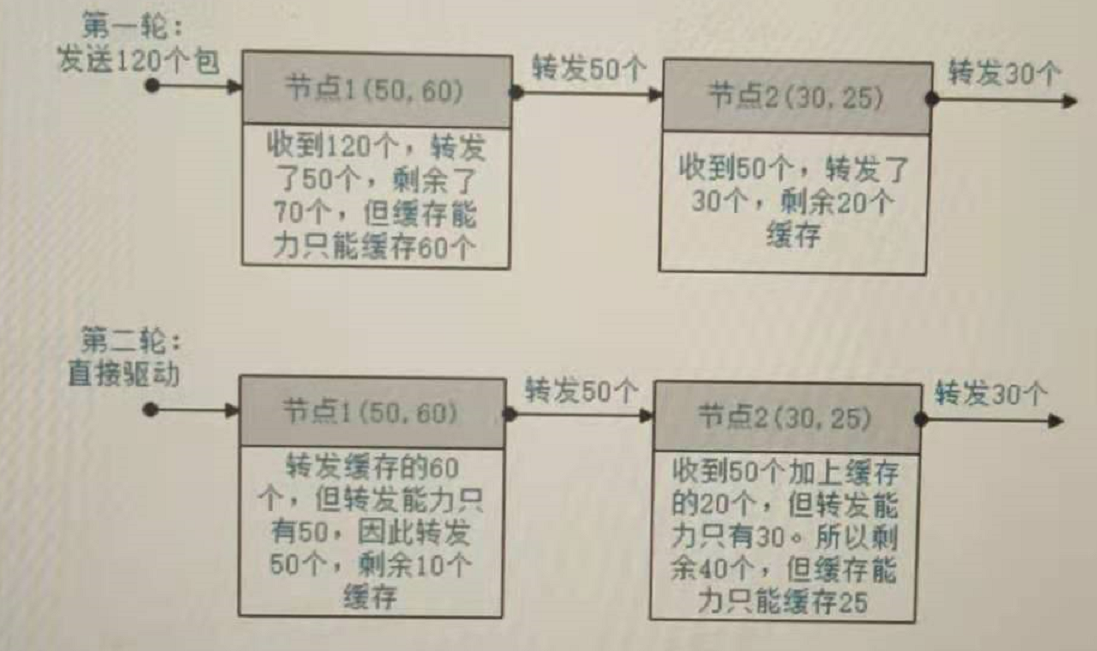
For example, there are two nodes, Node 1 (forwarding capability m:50, caching capability n:60) and Node 2(m:30, n:25), with 120 packets sent.
When there is no node failure:
Enter a description:
First row queue length k
The second behavior is an array of k nodes'forwarding capabilities, separated by spaces.m,n are separated by commas, for example, 10,20 11,21 12,22
Number of third row packets a
2 50,60 30,25 120
Output description:
55
Explanation:
See the legend in the title, when the first node fails, only the second node forwards, and the fewest packets are received.
Reference code:
// Focus on TechGuide!Large factory pen face by lightning!
Second: Find instance knowledge in the knowledge map (100%)
Title Description
A knowledge map is a structured semantic network used to describe the relationships between concepts and their instances in the physical world.A knowledge map can be thought of as a directed graph in which points are concepts or instances and edges are the relationships between concepts and their instances.
Now define a simple map of knowledge
Concepts: Includes parent and child concepts, which can be hierarchically related through subClassOf relationships;
Example: Associate only with concepts through instanceOf relationships:
Relation: Expressed as a tuple, a tuple is a string with spaces as separators between members.For example, "student subClassOf person" means student is a subconcept of person, and "apple instanceOf fruit" means Apple is an instance of concept fruit.
Given a map of knowledge, write a method to find all instances of a concept.If a concept has subconcepts, the results returned need to contain instances of all its subconcepts;If there is no instance of the concept entered, the string "empty" is returned (note: the output string text does not need to contain quotation marks).
The given graph satisfies the following limitations:
1. There are no loops in the directed graph
2. All point and relationship definitions are case sensitive
Enter a description:
Enter the first line representing the number n of relationships in the graph, with a range of values [1,10000]
Rows 2 through n+1 represent the relationships in the graph. Each row is the n+2 row of a relationship triple, representing the meta-node to be found, and is the point in the relationship triple.
Each line of characters does not exceed 100.
3 student subClassOf person Tom inslenceOf student Marry instanceOf person person
Output Description
An array of strings in ascending dictionary order that contains all instances of a concept and its subconcepts.
Marry Tom
Explanation:
Student is a subconcept of person, Tom is an instance of student, and Marry is person's
For example, Marry's dictionary order is less than Tom's, so Marry Tom is returned.
Reference Code
Find if its parent node is a target based on instanceOf.Whether it's subClassOf or instancOf, the child node is on the left, the parent node is on the right, and hash_is usedThe set store is instancOf, and finally based on hash_set traverses whether its parent node reaches the target node or not, and if it does, it is saved in set, sorted by default dictionary
#include <bits/stdc++.h>
using namespace std;
int main(int argc,char* argv[]){
int n;
cin>>n;
unordered_map<string,string> hash;//val is the parent node
unordered_set<string> instance;//Store instacnOf
string s1,s2,s3;
for(int i=0;i<n;++i){
cin>>s1>>s2>>s3;
if(s2=="instanceOf")
instance.insert(s1);
hash[s1]=s3;
}
string ss;
cin>>ss;
set<string> ret;
for(auto s:instance){
string s1=s;
while(hash.count(s1)){
if(hash[s1]==ss){
ret.insert(s);
break;
}
s1=hash[s1];
}
}
if(ret.size()==0){
cout<<"empty"<<endl;
}else{
int i=0;
for(auto s:ret){
if(i==0) cout<<s;
else cout<<" "<<s;
++i;
}
}
return 0;
}
// Focus on TechGuide!Large factory pen face by lightning!
Third way: lakes are connected (100%)
Title Description
There are many lakes on the map, and to enhance the lake's ability to withstand rainstorms, channels need to be digged between the lakes to make them connected (diagonals are considered disconnected).Some land is hard stone, and digging takes twice as much energy as ordinary land, that is, a plain lattice is 1 and a lattice with a hard stone is 2.
Maps are represented by a two-dimensional matrix, with only three possibilities for each location: 0 for lakes, 1 for common land, 2 for hard stones, and max. MN.You need to return to the shortest path through all the lakes, or 0 if it doesn't exist
Limitation: maximum M, N is 20, number of lakes is not more than 11
Enter a description:
First Behavior M
Second Behavior N
The third line starts with a map matrix of M*N
5 4 0 1 1 0 0 1 0 0 0 1 0 0 0 1 0 1 1 1 1 1
Output description:
Return to the shortest path through all the lakes
1
Explanation:
There are two lakes on the map. Just dig through one land and two lakes will connect.
Reference Code
This is a classic example of the Stanner Tree.Steiner trees are a class of problems where there are several (generally about 10) points on an undirected graph with edge weights that require the selection of some edges so that they are within the same junction block, while simultaneously requiring the selected edge weights and the minimum.
How do I solve the Stanner tree problem?In fact, it is a kind of pressure DP.
dp[i][j] denotes that node I is the root and the current state is j (the point in the binary of J that is already connected to I has a corresponding position of 1).
Where did this "rooted in i" come from?Actually, I can be any point in the union block, without additional restrictions, just by introducing this i, DP can be achieved.
When the root I does not change (that is, merge two connected blocks that both contain i), the state transfer equation is:
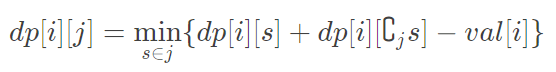
#include <cstdio>
#include <cstring>
#include <cmath>
#include <algorithm>
#include <iostream>
#include <queue>
#define space putchar(' ')
#define enter putchar('\n')
using namespace std;
typedef long long ll;
template <class T>
void read(T &x){
char c;
bool op = 0;
while(c = getchar(), c < '0' || c > '9')
if(c == '-') op = 1;
x = c - '0';
while(c = getchar(), c >= '0' && c <= '9')
x = x * 10 + c - '0';
if(op) x = -x;
}
template <class T>
void write(T x){
if(x < 0) putchar('-'), x = -x;
if(x >= 10) write(x / 10);
putchar('0' + x % 10);
}
const int INF = 0x3f3f3f3f;
int n, m, K, root, f[101][1111], a[101], ans[11][11];
bool inq[101];
typedef pair<int, int> par;
typedef pair<par, int> rec;
#define fi first
#define se second
#define mp make_pair
#define num(u) (u.fi * m + u.se)
rec pre[101][1111];
const int dx[] = {0, 0, -1, 1};
const int dy[] = {1, -1, 0, 0};
queue<par> que;
bool legal(par u){
return u.fi >= 0 && u.se >= 0 && u.fi < n && u.se < m;
}
void spfa(int now){
while(!que.empty()){
par u = que.front();
que.pop();
inq[num(u)] = 0;
for(int d = 0; d < 4; d++){
par v = mp(u.fi + dx[d], u.se + dy[d]);
int nu = num(u), nv = num(v);
if(legal(v) && f[nv][now] > f[nu][now] + a[nv]){
f[nv][now] = f[nu][now] + a[nv];
if(!inq[nv]) inq[nv] = 1, que.push(v);
pre[nv][now] = mp(u, now);
}
}
}
}
void dfs(par u, int now){
if(!pre[num(u)][now].se) return;
ans[u.fi][u.se] = 1;
int nu = num(u);
if(pre[nu][now].fi == u) dfs(u, now ^ pre[nu][now].se);
dfs(pre[nu][now].fi, pre[nu][now].se);
}
int main(){
read(n), read(m);
memset(f, 0x3f, sizeof(f));
for(int i = 0, tot = 0; i < n; i++)
for(int j = 0; j < m; j++){
read(a[tot]);
if(!a[tot]) f[tot][1 << (K++)] = 0, root = tot;
tot++;
}
for(int now = 1; now < (1 << K); now++){
for(int i = 0; i < n * m; i++){
for(int s = now & (now - 1); s; s = now & (s - 1))
if(f[i][now] > f[i][s] + f[i][now ^ s] - a[i]){
f[i][now] = f[i][s] + f[i][now ^ s] - a[i];
pre[i][now] = mp(mp(i / m, i % m), s);
}
if(f[i][now] < INF)
que.push(mp(i / m, i % m)), inq[i] = 1;
}
spfa(now);
}
write(f[root][(1 << K) - 1]), enter;
dfs(mp(root / m, root % m), (1 << K) - 1);
for(int i = 0, tot = 0; i < n; i++){
for(int j = 0; j < m; j++)
if(!a[tot++]) putchar('x');
else putchar(ans[i][j] ? 'o' : '_');
enter;
}
return 0;
}
Congratulations on discovering the treasure!WeChat Search Public Number (TechGuide) pays attention to more fresh articles and the pen scripts of Internet companies.