At present, most RESTful systems use JWT for authorization verification. In Spring Boot, Shiro and JWT can be used for simple permission and authentication verification. In the process of integration with Spring Boot, there are many holes. Combined with their own and common application scenarios, we developed the simplest integration method, fastdep Shiro JWT.
Here also note: the theory of light is not enough. Here, I will send you ten sets of 2020 latest Java architecture practical course + large factory interview question bank, which can be found under the transformation of seven bar umbrella bar and Zero clothing umbrella (Digital homophony). Many new Java architecture project courses can also be exchanged with the old driver for advice!
Source address
I hope you can support it with star. In the future, we will add simple integration of other dependencies.
https://github.com/louislivi/fastdep
Introduce dependency
-
Maven
<dependency> <groupId>com.louislivi.fastdep</groupId> <artifactId>fastdep-shiro-jwt</artifactId> <version>1.0.2</version> </dependency> -
Gradle
compile group: 'com.louislivi.fastdep', name: 'fastdep-redis', version: '1.0.2'
configuration file
-
application.yml
fastdep: shiro-jwt: filter: #shiro filter rules admin: path: /admin/** role: jwt # jwt For token verification front: path: /front/**/** role: anon # anon is no need to check secret: "6Dx8SIuaHXJYnpsG18SSpjPs50lZcT52" # jwt secret key # expireTime: 7200000 # Valid period of token # prefix: "Bearer " # Prefix for token verification # signPrefix: "Bearer " # token generates the prefix of the signature # header: "Authorization" # Header header in token verification # The following corresponds to shiro configuration parameters, which are not required for special requirements # loginUrl: # successUrl: # unauthorizedUrl: # filterChainDefinitions: -
User rights configuration class
@Component public class FastDepShiroJwtConfig extends FastDepShiroJwtAuthorization { @Autowired private UserRequestDataMapper userRequestDataMapper; @Override public SimpleAuthorizationInfo getAuthorizationInfo(String userId) { // Query all permissions under this user (currently, it is the example only to query the user ID real environment and replace it with the user's permission value) Set<String> collect = userRequestDataMapper.selectOptions().stream().map(u -> u.getUserId().toString()).collect(Collectors.toSet()); SimpleAuthorizationInfo simpleAuthorizationInfo = new SimpleAuthorizationInfo(); System.out.println(collect); // The current value is [1] // Add user rights to SimpleAuthorizationInfo simpleAuthorizationInfo.addStringPermissions(collect); return simpleAuthorizationInfo; } }
application
@RestController
public class TestController {
@Autowired
private JwtUtil jwtUtil;
/**
* Currently, it is an example, so the token is returned directly. The real environment is to verify the login information and then return the token
* @author : louislivi
*/
@GetMapping("front/login")
public String login() {
// ... verify that the login information is correct
// Unique identity of incoming user
return jwtUtil.sign("1");
}
/**
* Currently, it is an example, so the permission is written with the user ID real environment replaced by the permission key
* @author : louislivi
*/
@GetMapping("admin")
@RequiresPermissions("1")
public String jwt() {
return "ok!";
}
}test
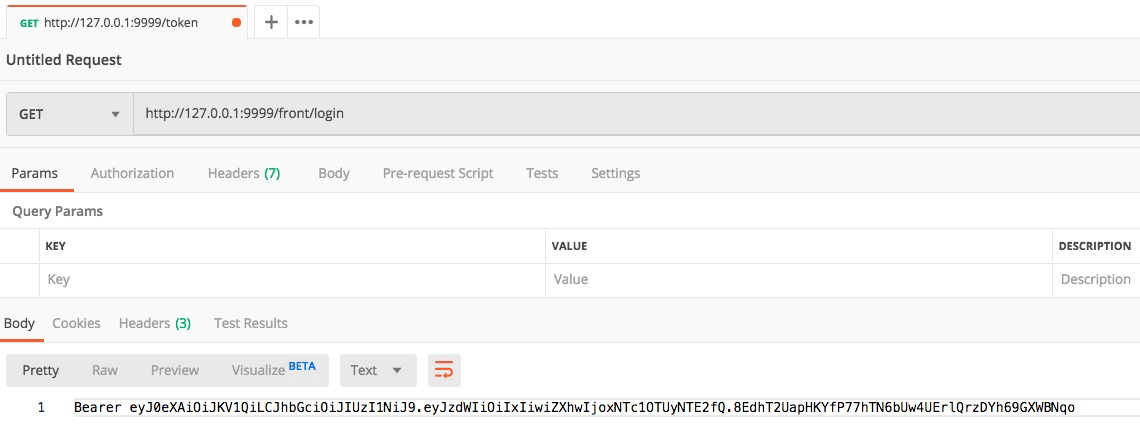
1. Get token
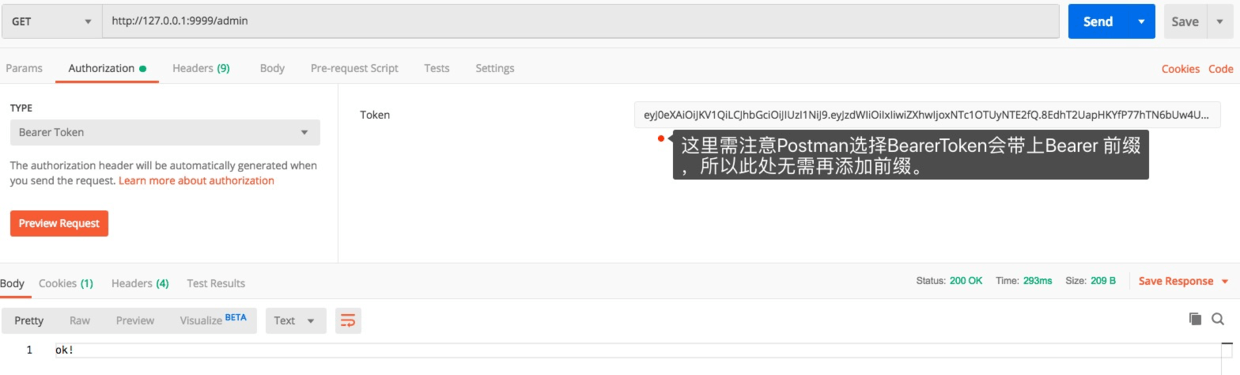
2. Test authority verification
-
With token
-
Without token
{ "msg": "Access denied !", "code": 401 }- With token but no permission specified in SimpleAuthorizationInfo
{ "msg": "Subject does not have permission [1]", "code": 403 }extend
- With token but no permission specified in SimpleAuthorizationInfo
Sometimes, you need to customize the permission verification and error return information structure, etc. in this case, you need to override the method in fastdepshirojwathorization class. For more details, please see here
principle
Using importbeandefinitionregister BeanDefinitionBuilder.genericBeanDefinition to dynamically inject a Bean is actually very simple. If you are interested in looking at the source code, is such dependency integration much easier?
I hope you can support open source, give a little star, and continue to develop other dependent integrations in the future, even compatible with other frameworks. fastdep makes it easier for java to integrate dependencies. Here, we also recruit coder with the same aspiration to jointly improve the project.
Finally note: the theory of light is not enough. Here, I will send you ten sets of 2020 latest Java architecture practical course + interview question bank of Dachang, which can be found under the transformation of seven bar umbrella bar zero and clothes zero umbrella (Digital homophony). Many new Java architecture project courses can also be exchanged with old drivers for advice!
The text and pictures of this article come from the Internet and my own ideas. They are only for learning and communication. They have no commercial use. The copyright belongs to the original author. If you have any questions, please contact us in time for handling