Openssl configuration file: / etc/pki/tls/openssl.cnf
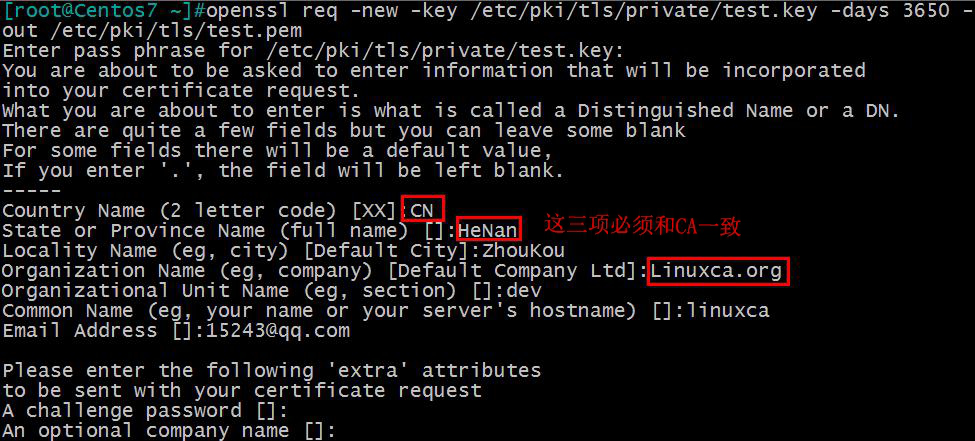
Three strategies: matching, supporting and optional. Matching: refers to the requirement to fill in the application information and CA settings information must be consistent; support: refers to the need to fill in the application information; optional: refers to whether it is necessary or not.
Experimental environment: Two hosts are needed. I use host A (Centos6:ip 172.17.250.83) to create CA and provide CA services to other hosts. Host B (Centos7:ip 172.17.253.204) is an httpd server to apply for certificates.
1. Let's first look at some of the contents of the configuration file. The following must be written when creating CA:
dir = /etc/pki/CA # Where everything is kept certs = $dir/certs # Where the issued certs are kept crl_dir = $dir/crl # Where the issued crl are kept database = $dir/index.txt # database index file. #unique_subject = no # Set to 'no' to allow creation of # several ctificates with same subject. new_certs_dir = $dir/newcerts # default place for new certs. certificate = $dir/cacert.pem # The CA certificate serial = $dir/serial # The current serial number crlnumber = $dir/crlnumber # the current crl number # must be commented out to leave a V1 CRL crl = $dir/crl.pem # The current CRL private_key = $dir/private/cakey.pem # The private key
2. Create the necessary files according to the need of configuration files.
[root@Centos6 ~]#touch /etc/pki/CA/index.txt #Generating files for certificate index database [root@Centos6 ~]#echo 01 > /etc/pki/CA/serial #Specify the serial number of the first certificate issued [root@Centos6 ~]#tree /etc/pki/CA/ /etc/pki/CA/ ├── certs ├── crl ├── index.txt ├── newcerts ├── private └── serial 4 directories, 2 files
Note: The two files created, including the file names created in the next experiment, must be the same as the file names in the configuration file.
3. Create CA services on the host A (Centos6) and self-visa
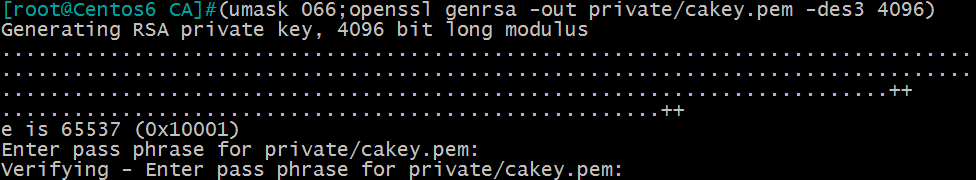
(1) Generating private key
[root@Centos6 ~]#(umask 066;openssl genrsa -out private/cakey.pem -des3 4096) #- des3 encrypts files
Note: The parentheses indicate that the parentheses are executed in the child shell without affecting the setting of the parent shell; the umash is set to 066 to prevent others from having permission to view and modify the generated private key; before 4096, encryption algorithms can be added to the private key, such as des3, rsa, etc. This example uses DES3 encryption.
Take a look at some of the encrypted text:
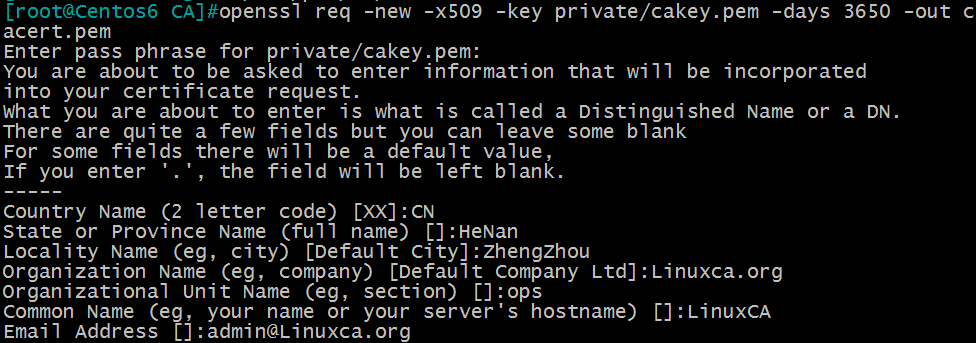
(2) Formation of self-visa
[root@Centos6 ~]#openssl req -new -x509 -key private/cakey.pem -days 3650 -out cacert.pem
Where: -new: Generate a new certificate signing request
- x509: Special for CA to generate self-visa
- key: The private key file used to generate the request
- days n: validity period of certificate
- Out/PATH/TO/SOMECERTFILE: Certificate Preservation Path
Look at some of the encrypted text of the certificate:
(3) Transfer the cacert.pem file to windows. Because the text suffixed by. pem can not be recognized on windows, we need to change the text to suffixed by. cer, and the modified file icon is  .
.
Open the certificate on windows and have a look.
4. Generate certificate requests on host B (Centos7) requiring certificates
(1) Generating private keys for httpd services
[root@Centos7 ~]#(umask 066;openssl genrsa -out /etc/pki/tls/private/test.key -des3 4096) Generating RSA private key, 4096 bit long modulus ..........................................................++ ...........................................................................................................................................................................................................................++ e is 65537 (0x10001) Enter pass phrase for /etc/pki/tls/private/test.key: Verifying - Enter pass phrase for /etc/pki/tls/private/test.key:
(2) Generation of Certificate Application Documents
[root@Centos7 ~]#openssl req -new -key /etc/pki/tls/private/test.key -days 3650 -out /etc/pki/tls/test.pem
(3) Transfer certificate request file to CA
[root@Centos7 ~]#scp /etc/pki/tls/test.pem @172.17.250.83:/etc/pki/tls/ The authenticity of host '172.17.250.83 (172.17.250.83)' can't be established. RSA key fingerprint is 09:52:06:53:a1:13:99:f3:b9:5c:5f:0a:c4:b6:1c:ed. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '172.17.250.83' (RSA) to the list of known hosts. root@172.17.250.83's password: test.pem 100% 1736 1.7KB/s 00:00
5. Sign the certificate on the host A (Centos6) and issue it to the certificate applicant (host B)
(1) Signing Certificate
[root@Centos6 ~]#openssl ca -in /etc/pki/tls/test.pem -out /etc/pki/CA/certs/test.crt -days 3650 Using configuration from /etc/pki/tls/openssl.cnf Enter pass phrase for /etc/pki/CA/private/cakey.pem: Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Sep 12 23:04:23 2017 GMT Not After : Sep 10 23:04:23 2027 GMT Subject: countryName = CN stateOrProvinceName = HeNan organizationName = Linuxca.org organizationalUnitName = dev commonName = linuxca emailAddress = 15243@qq.com X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 97:B6:0A:0A:70:C6:FB:29:BB:B9:4A:26:98:3E:73:8B:20:F4:37:5E X509v3 Authority Key Identifier: keyid:73:E2:DE:70:0B:9E:6B:FA:DD:5F:16:D5:0B:38:D2:A5:A0:2E:B4:D6 Certificate is to be certified until Sep 10 23:04:23 2027 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated
(2) Issue certificates to host B (Centos7)
[root@Centos6 CA]#scp certs/test.crt @172.17.253.204:/etc/pki/CA/ The authenticity of host '172.17.253.204 (172.17.253.204)' can't be established. RSA key fingerprint is 91:d3:76:ba:60:12:0d:13:9b:93:6a:39:71:18:fe:65. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '172.17.253.204' (RSA) to the list of known hosts. root@172.17.253.204's password: test.crt 100% 7311 7.1KB/s 00:00
(3) View the information in the certificate on the host B (Centos7).
openssl x509 -in /PATH/FROM/CERT_FILE
-text|issuer|subject|serial|dates
Opensslca-status SERIAL Views the Certificate Status of the Specified Number
[root@Centos7 CA]#openssl x509 -in test.crt -text
So far, the creation, application and issuance of CA have been completed.