ACL access control list
- Access restriction: match the traffic on the interface of router traffic in and out, and then control it
- Define traffic of interest
Matching rules
Match one by one from top to bottom. The previous match is executed according to the previous one, and the next one will not be viewed
Cisco implicitly rejects all at the end and Huawei implicitly allows all at the end
Classification of ACl
- Standard ACL: only match the source IP address in the traffic
- Extended ACL: match the source IP address or target IP address, target port number and target protocol number in the traffic (relatively thin)
Standard ACL
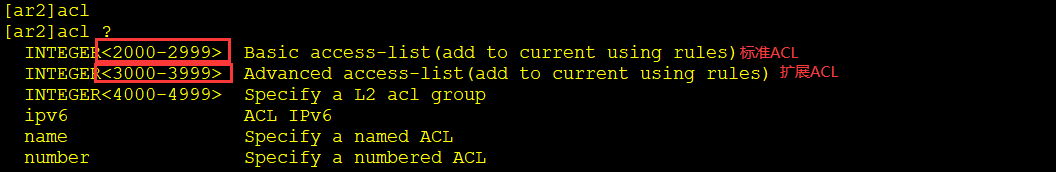
Writing of ACL
- number
- name
Precautions for configuring standard ACL S:
Because only the source IP address in the traffic is matched, the call should be as close to the target as possible to avoid being unable to access other accessible places
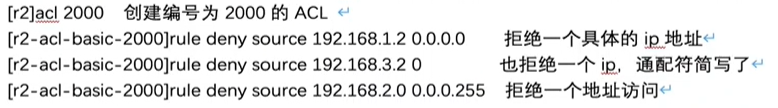
A 0 = = 0.0.0.0
The ACL uses wildcards and OSPF uses anti mask; The difference is that wildcards can be interspersed with 0 and 1
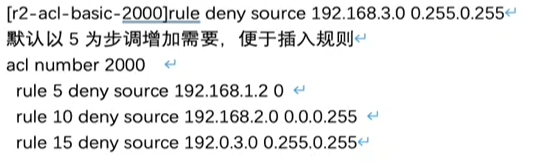
You can use this step to insert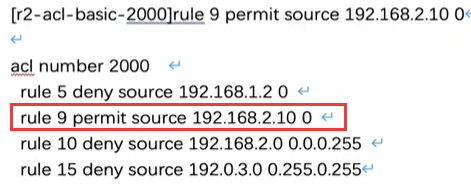
When deleting an entry, you can delete this sequence number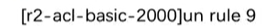
You can also use naming to create a standard ACL list

Remember to call on the interface after ACL configuration is completed

Configure the topology diagram in the following figure
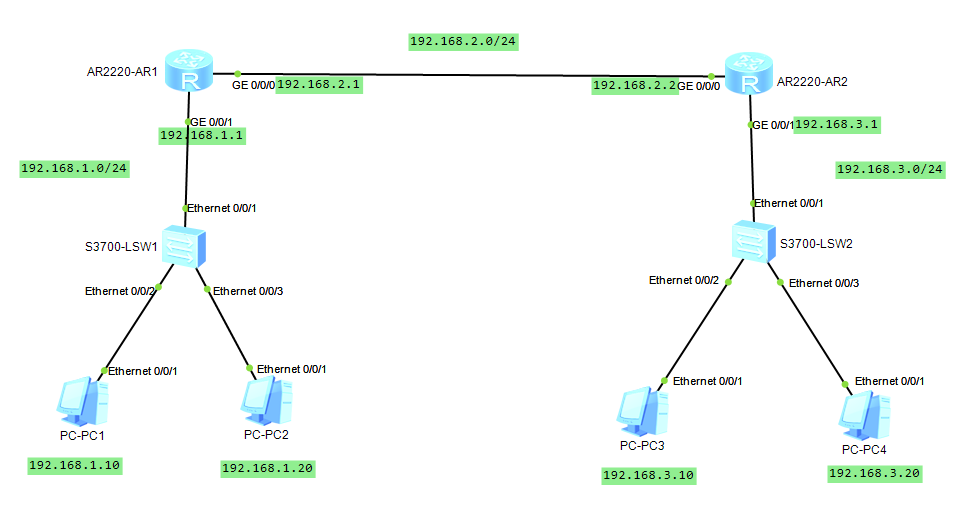
Static routing:
IP route static destination segment mask
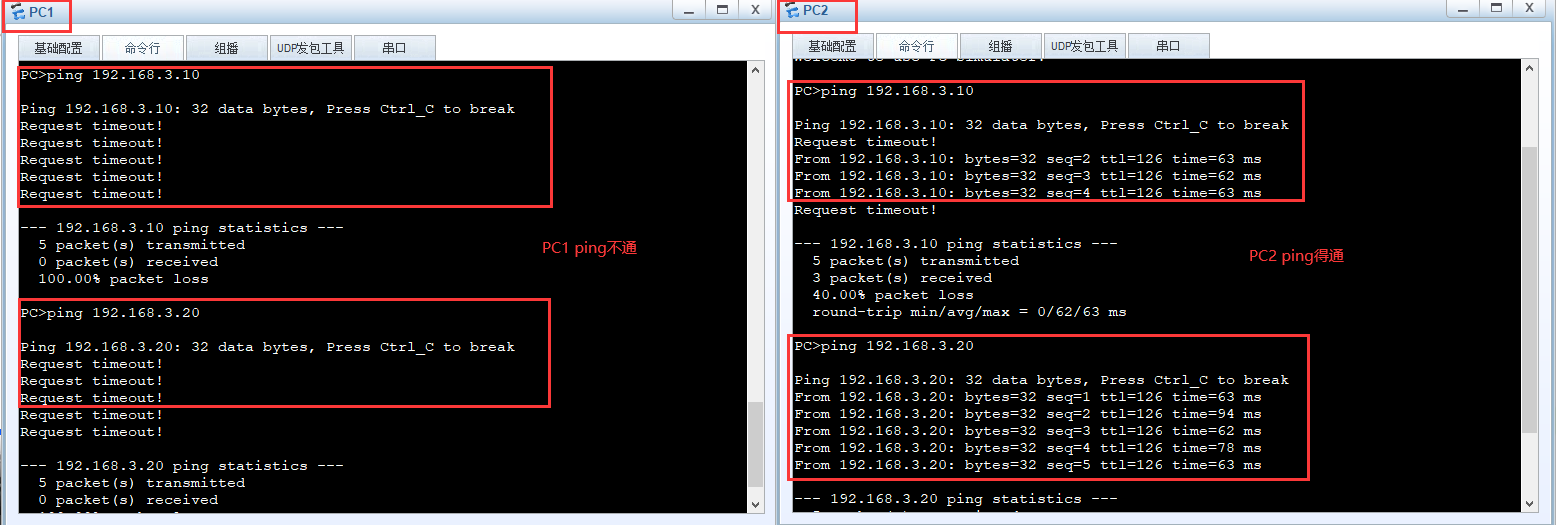
Configure ACL so that PC1 cannot access PC3 and PC4, and PC2 can access PC3 and PC4
[ar2]acl 2000 [ar2-acl-basic-2000]rule deny source 192.168.1.10 0 [ar2-acl-basic-2000]q [ar2]interface g 0/0/1 [ar2-GigabitEthernet0/0/1]traffic-filter outbound acl 2000
test
Extended ACL
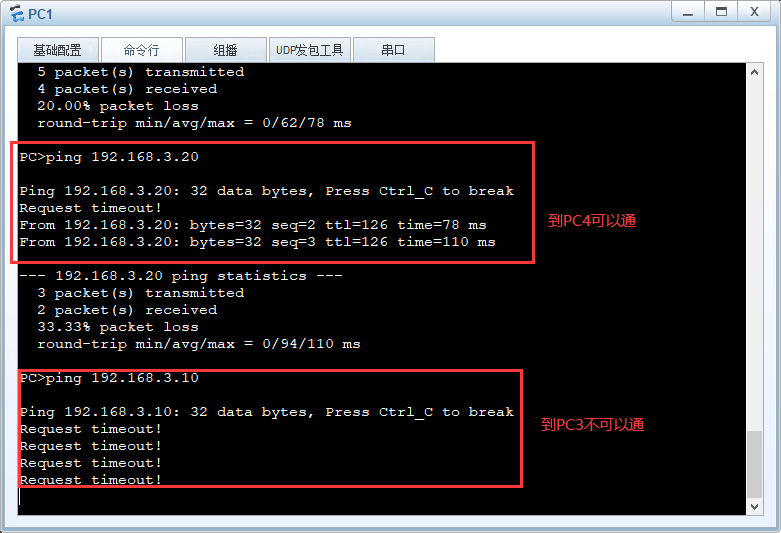
Make PC1 unable to access PC3, but can access PC4
Because the extended ACL can clearly mark the target, the call should be as close to the source as possible
[ar1]acl 3000 [ar1-acl-adv-3000]rule deny ip source 192.168.1.10 0 destination 192.168.3.10 0 [ar1-acl-adv-3000]q [ar1]int g 0/0/1 [ar1-GigabitEthernet0/0/1]traffic-filter inbound acl 3000
telnet remote login
condition
- The login and the logged in device can communicate normally
- The logged in device starts the remote login service
Configure the login account and password
[ar2]aaa [ar2-aaa]local-user xiaobai password cipher 200001 #Add user and password Info: Add a new user. [ar2-aaa]local-user xiaobai service-type telnet #xiaobai only has the function of telnet [ar2-aaa]local-user xiaobai privilege level ? INTEGER<0-15> Level value # Level 1 permission can only display [ar2-aaa]local-user xiaobai privilege level 15 #Level 15 highest authority, you can do anything [ar2]telnet server enable #telnet service is enabled by the login end [ar2]user-interface vty 0 4 [ar2-ui-vty0-4]authentication-mode aaa
Remote login to AR2 with AR1
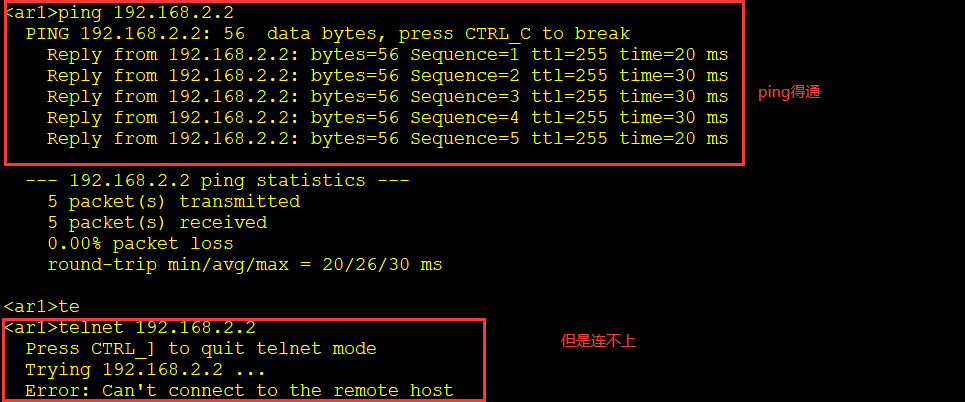
<ar1>telnet 192.168.2.2 Press CTRL_] to quit telnet mode Trying 192.168.2.2 ... Connected to 192.168.2.2 ... Login authentication Username:xiaobai Password: <ar2>
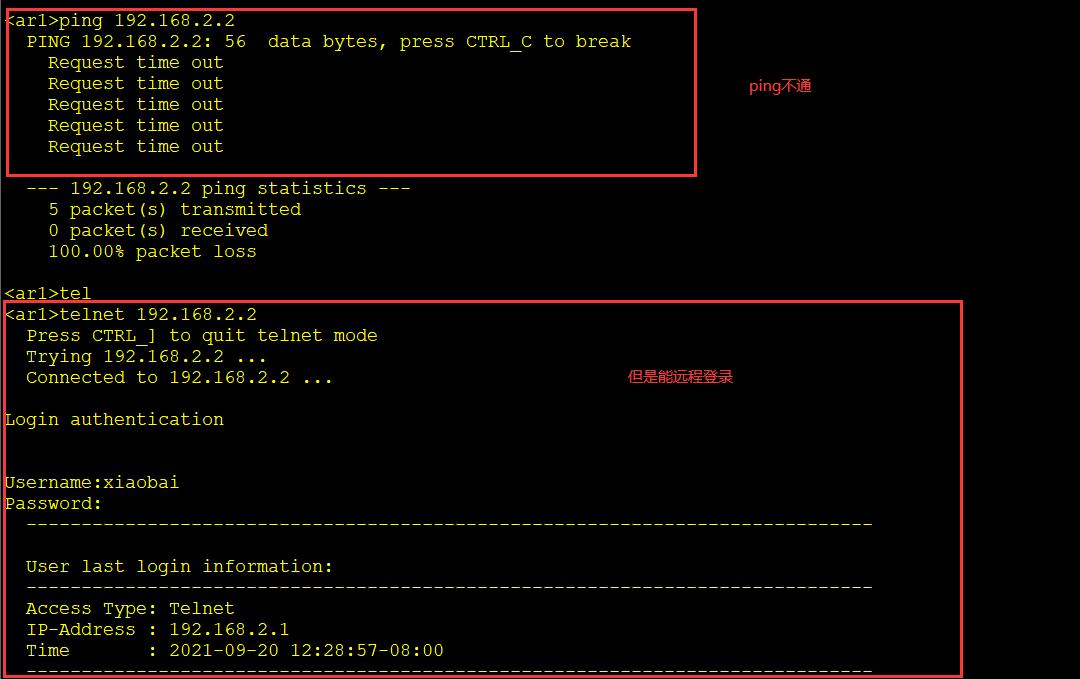
Configure ACL for AR2 so that AR1 can telnet AR2, but cannot ping AR2
[ar2]acl 3001 [ar2-acl-adv-3001]rule deny icmp source 192.168.2.1 0 destination 192.168.2.2 0 #Reject icmp (ping) [ar2-acl-adv-3001]q [ar2]int g 0/0/0 [ar2-GigabitEthernet0/0/0]traffic-filter inbound acl 3001
Go to AR1 for test
Configure ACL for AR2 so that AR1 cannot access AR2 via telnet, but can ping AR2
[ar2]acl 3002 [ar2-acl-adv-3002]rule deny tcp source 192.168.2.1 0 destination 192.168.2.2 0 d estination-port eq 23 [ar2-acl-adv-3002]q [ar2]int g 0/0/0 [ar2-GigabitEthernet0/0/0]traffic-filter inbound acl 3002
Go to AR1 for test