Get Super User Access Rights
Root user:
In RedHat 7.2, the root user privilege is higher than the general privilege on the file system. It is used in the management system. When performing tasks such as installing or deleting software and managing system files and directories, the privilege must be upgraded to the root user.
Most devices are controlled by root users, but some are not. For example, USB mobile devices can be controlled by ordinary users, and by default only root users can manage "fixed" disks.
The root account on Linux is roughly equivalent to the local admin account on windows. In Linux system, most administrators log in to the non-privileged account (root), and then use various tools (su, sudo, polickit) to get root privileges.
Use su to switch accounts:
SU command:
Switch user, switch to root user without specifying user name. When ordinary user calls root user, it needs to enter root user password. SU-: Switch the working directory after switching the user. The environment is set to be exactly the same as the user's login, while SU only uses the current environment settings to start the shell as the user.

Su-c: This command acts as runas in windows, and can execute arbitrary programs as another user.
su flaw: Ordinary users need to enter root user password when using.
The sudo command:
Users can be allowed to run commands as root or other user based on settings in the / etc/sudoers file. sudo requires the user to enter his own password for authentication, rather than the root user password. This allows administrators to delegate system administration tasks to subtle privileged users without requiring root user passwords.
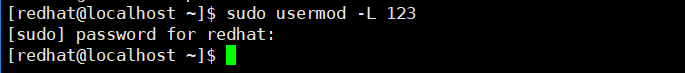
For example, if sudo is configured to allow the redhat user root identity to run the usermod command, then redhat can run the command to lock the user account.
sudo provides a command to edit the file: visudo to modify the file. Configuration errors will prompt you, using a method similar to vim.
 vim editing example
vim editing example
 fangshi, visudo Editor
fangshi, visudo Editor
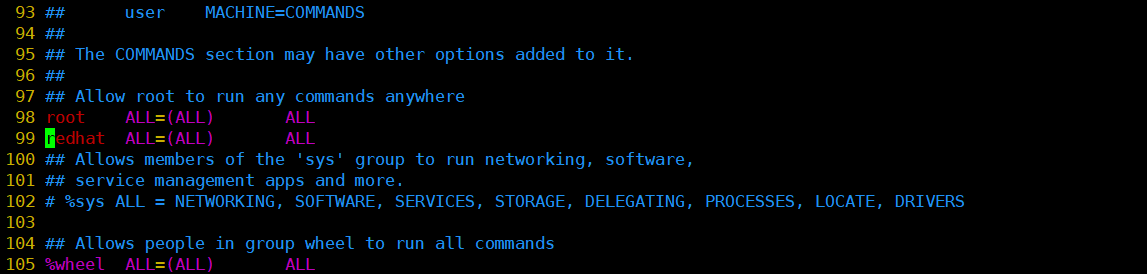
/ Detailed description of etc/sudoers file
1 ## Sudoers allows particular users to run various commands as 2 ## the root user, without needing the root password. 3 ## // No root user password is required to execute various commands that only root users can execute 4 ## Examples are provided at the bottom of the file for collections 5 ## of related commands, which can then be delegated out to particular 6 ## users or groups. // User groups 7 ## 8 ## This file must be edited with the 'visudo' command. 9 10 ## Host Aliases 11 ## Groups of machines. You may prefer to use hostnames (perhaps using 12 ## wildcards for entire domains) or IP addresses instead. 13 # Host_Alias FILESERVERS = fs1, fs2 14 # Host_Alias MAILSERVERS = smtp, smtp2 15 16 ## User Aliases 17 ## These aren't often necessary, as you can use regular groups 18 ## (ie, from files, LDAP, NIS, etc) in this file - just use %groupname 19 ## rather than USERALIAS 20 # User_Alias ADMINS = jsmith, mikem 21 22 23 # Command Aliases 24 ## These are groups of related commands... 25 26 ## Networking//Alias for commands related to network operations 27 # Cmnd_Alias NETWORKING = /sbin/route, /sbin/ifconfig, /bin/ping, /sbin/dhclient, /usr/bin/net, /sbin/iptables, /usr/bin/rfcomm, /usr/bin/wvdial, /sbin/iwconfig, /sbin/mii-tool 28 29 ## Installation and management of software 30 # Cmnd_Alias SOFTWARE = /bin/rpm, /usr/bin/up2date, /usr/bin/yum 31 32 ## Services // Server related command aliases 34 35 ## Updating the locate database // local database upgrade command alias 36 # Cmnd_Alias LOCATE = /usr/bin/updatedb 37 38 ## Storage 39 # Cmnd_Alias STORAGE =/ sbin/fdisk, / sbin/sfdisk, / sbin/parted, / sbin/partprobe, / bin/mount, / bin/umount//disk operation command alias 40 41 ## Delegating permissions // proxy permissions related aliases 42 # Cmnd_Alias DELEGATING = /usr/sbin/visudo, /bin/chown, /bin/chmod, /bin/chgrp 43 44 ## Processes 45 # Cmnd_Alias PROCESSES = /bin/nice, /bin/kill, /usr/bin/kill, /usr/bin/killall 46 47 ## Drivers // process-related command aliases 48 # Cmnd_Alias DRIVERS = /sbin/modprobe 49 50 # Defaults specification 51 52 # 53 # Disable "ssh hostname sudo <cmd>", because it will show the password in clear. 54 # You have to run "ssh -t hostname sudo <cmd>". 55 # 56 Defaults requiretty 57 58 # 59 # Refuse to run if unable to disable echo on the tty. This setting should also be 60 # changed in order to be able to use sudo without a tty. See requiretty above. 61 # 62 Defaults !visiblepw 63 64 # 65 # Preserving HOME has security implications since many programs 66 # use it when searching for configuration files. Note that HOME 67 # is already set when the the env_reset option is enabled, so 68 # this option is only effective for configurations where either 69 # env_reset is disabled or HOME is present in the env_keep list. 70 # 71 Defaults always_set_home 72 73 Defaults env_reset 74 Defaults env_keep = "COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR LS_COLORS" 75 Defaults env_keep += "MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE" 76 Defaults env_keep += "LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES" 77 Defaults env_keep += "LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE" 78 Defaults env_keep += "LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY" 79 80 # 81 # Adding HOME to env_keep may enable a user to run unrestricted 82 # commands via sudo. 83 # 84 # Defaults env_keep += "HOME" 85 86 Defaults secure_path = /sbin:/bin:/usr/sbin:/usr/bin 87 88 ## Next comes the main part: which users can run what software on 89 ## which machines (the sudoers file can be shared between multiple 90 ## systems). 91 ## Syntax: 92 ## 93 ## user MACHINE=COMMANDS 94 ## 95 ## The COMMANDS section may have other options added to it. 80 # 81 # Adding HOME to env_keep may enable a user to run unrestricted 82 # commands via sudo. 83 # 84 # Defaults env_keep += "HOME" 85 86 Defaults secure_path = /sbin:/bin:/usr/sbin:/usr/bin 87 88 ## Next comes the main part: which users can run what software on 89 ## which machines (the sudoers file can be shared between multiple 90 ## systems). 91 ## Syntax: // Grammar 92 ## 93 ## User MACHINE = COMMANDS // Host logged in by user = commands that can be executed 94 ## 95 ## The COMMANDS section may have other options added to it. // The command section can be accompanied by some other options 96 ## 97 ## Allow root to run any commands anywhere 98 root ALL=(ALL) ALL 99 redhat ALL=(ALL) ALL //User passwords can be entered with the highest privileges 100 ## Allows members of the 'sys' group to run networking, software, 101 ## service management apps and more. 102 # %sys ALL = NETWORKING, SOFTWARE, SERVICES, STORAGE, DELEGATING, PROCESSES, LOCATE, DRIVERS 103 104 ## Allows people in group wheel to run all commands // Allows users in the wheel user group to execute all commands 105 %wheel ALL=(ALL) ALL 106 107 ## Same thing without a password 108 # % wheel ALL = (ALL) NOPASSWD: ALL // Allows users in the wheel user group to use all lives without entering a password 109 110 ## Allows members of the users group to mount and unmount the 111 ## cdrom as root 112 # %users ALL=/sbin/mount /mnt/cdrom, /sbin/umount /mnt/cdrom 113 114 ## Allows members of the users group to shutdown this system 115 # % User localhost=/sbin/shutdown-h now//Allow ordinary user shutdown 116 117 ## Read drop-in files from /etc/sudoers.d (the # here does not mean a comment) 118 #includedir /etc/sudoers.d