. find
To find files in directories, you can also call other commands to use
find [-H] [-L] [-P] [-D debugopts] [-Olevel] [path...] [expression]
find [Options], [Paths], [Operational Statements]
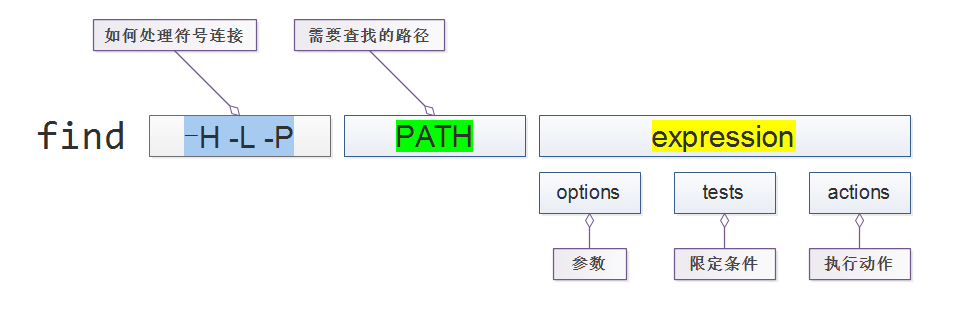
options:
- depth Starts searching for the deepest subdirectory in the specified directory ___________
- maxdept levels Find the maximum directory series, levels is a natural number
- regextype type Regular expression type, default emacs,
tests:
- mtime [-n|n|+n] Search for files according to the modification time of the files, in the unit of "days"
- atime [-n|n|+n] Find files by the access time of files
- ctime [-n|n|+n] Find the file by the time the state of the file changes
- mmin
- amin Find files by the time they are accessed
- cmin Find files by the time the state of the file changes
- Group Find files by the group to which they belong
- name: Find files by filename, support wildcard symbols
- newer Find a new file that changes more than the specified file
- The group to which the file lookup belongs does not exist in / etc/groups.
- Noser Find file arrays do not exist in / etc/passwd ____________
- path pattern Specify the path style, with - prune excluding the specified directory
- perm Find files according to file permissions
- size n[cwbkMG]
- user Find files by file owner
- Type Find files by file type b, c, d, p, l, f, s, D
actions:
- delete. Delete the files found
- exec Give the found file to the shell command after changing the parameters to run
- ok # is the same as - exec, but it will be prompted.
- prune
- The default function of print can be omitted to output matched files to standard output
*! * Reverse
- a) Take intersection, and
- o union, or
find . -atime -2 find /data/ -mtime -5 find /var/log/ -mtime +5 -name '*.log' find . ! -type d find /data/ -perm 755 find . -size +1000c find /data -path "/data/dir3" -prune -o -print # -a and-o Similar to "&&"And "||",Execution when true-prune;Execution for holidays-print find /data \(-path /data/dir2 -o -path /data/dir3\) -prune -o -print find . -nouser find . -group nobody find . -newer file1.txt # Find files that are newer than file1 find . -maxdepth 1 -type d find . -maxdepth 1 -type d ! -name "." find . -maxdepth 1 -type d ! -name "." -o -name "xiaolizi" find . -maxdepth 1 -type d ! -name "." -a -name "xiaolizi" find . -type f -exec ls -l {} \; find . -type f -mtime +14 -exec rm {} \; find . -type f -mtime +14 -ok rm {} \; find . -type f -mtime +14 |xargs ls -l find . -name "*.txt" |xargs -i mv {} dir2/ find . -name "*.txt" |xargs -i mv -t dir2/ find . -type -f -name "test.txt"|xargs tar zcf xiaolizi.tar.gz # Unable to use - exec
. rename
Batch File Name Modification by String Replacement
rename from to file...
from: Characters (filenames or extensions) that need to be replaced or processed
To: Replace the content represented by from with that represented by to
file: Files to be processed, all files can be wildcarded with "*"
rename "_finished" "" * # Replace _finished of all files with empty rename .jpg .xiaolizi *.jpg # Replace.jpg of all files with.xiaolizi
. basename
Display only the file name after removing the absolute path
. dirname
Display only the directory name of the file
. chattr
Changing File Extension Properties
a # can only add data to files, not delete it. It is mostly used for server log security
I Settings file can not be deleted, renamed, written or added to the content, to lock the file + I unlock-i
. lsattr
View File Extension Properties
. file
Display file type
file + filename
. md5sum
MD5 is an irreversible encryption algorithm for computing and verifying files
- b) Read files in # binary mode
- c
- t) Text mode to read files, default mode
Verify that the parameters used in the validation file are not output OK
The -- status # validation file uses parameters, does not output any information, and can be judged by the return value of the command.
md5sum xiaolizi.txt # Encrypted file md5sum xiaolizi.txt>md5.log # Generate checkout files md5sum -c md5.log # Check file integrity md5sum --status -c md5.log # Use"echo $?",Determine whether the implementation is successful
# Server backup script, using md5 to verify data integrity
#!/bin/bash
# Source function library
./etc/init.d/functions# Defined variables
IP=$(ifconfig eth1|awk -F '[ :]+' 'NR==2{print $4}')
Path="/data/backup/$IP"
TIME=`/bin/date +%F`
BackupFile=/server/scripts/backuplist# Judged the exostence of variables
[ ! -d $Path ] && mkdir -p $Path
[ ! -f $BackupFile ] && {
echo "Please give me $BackupFile"
exit 1
}# Defined result function
function Msg(){
if [ $? -eq 0 ];then
action "$*" /bin/true
else
action "$*" /bin/false
fi
}# Backuo config files
tar zcfh $Path/conf_${TIME}.tar.gz `cat $BackupFile` &>/dev/null
Msg 'Backup config files'# Make a flag for backup
find $Path -type f -name "*${TIME}.tar.gz"|xargs md5sum >$Path/flag_${TIME} 2>/dev/null# Successful backup of md5sum file fingerprint database
Msg 'Make a flag for backup'# Send backup to backupsever
rsync -az $Path rsync_backup@rsync::backup --password-file=/etc/rsync.password &>/dev/null
Msg 'Send backup to backup server'
# Check the server backup and notify the administrator by mail
#!/bin/bash
DIR=/data/backup
TIME=`/bin/date + %F`
log=/tmp/$TIME-check.log[ -d $DIR ] && {
find $DIR -type f -name "flag_$TIME"|xargs md5sum -c >$log 2>/dev/null
mail -s "$(date +%F_%T)backup check result" xxxxxx@qq.com <$log
}# Delete backup a week ago
find $Path -type f -name "*.tar.gz" -mtime +7|xargs rm -f &>/dev/null
Msg 'Delete backup a week ago'
. chown
Users and user groups that change files or directories
chown [OPTION]... [OWNER][:[GROUP]] FILE...
Authorized users need to exist first in the operating system
chown oldboy file.txt # Ownership changes chown .odboy file.txt # Genus group changes chown root:root file.txt # Change user and group attributes of files at the same time //perhaps chown root.root file.txt chown -R xiaolizi.xiaolizi file.txt # Recursive authorization
. chmod
Change file or directory permissions, but generally only root users or file groups can use them
chmod [OPTION]... MODE[,MODE]... FILE...
Permission bits:
r: Read 4 w: Write 2 x: Execute 1 -: No privileges
Special privilege bit:
t,T,s,S,X,x
User type:
Subordinate users: u. Subordinate group users: g. Other users:
Operating Characters:
+ Add - subtract = settings
chmod a= file.txt # Empty Ownership chmod u+x file.txt chmod g+w file.txt chmod o+r file.txt chmod uf+r,o-r file.txt chmod u=rwx,g=rx,o=x file.txt chmod -R 644 /dir/ Recursively set file permissions
. umask
Define default permissions for users to create files or directories
1. The maximum permission to create a file is 666, but the set umash code is 022, so the file permission becomes 644.
But when the file permission value, minus, umash value, if the number in the period is odd, then the odd number needs to be + 1 to become even.
2. The default maximum permission to create directories is 777, 777-022 = 755, so the default permission to create directories is 755.
3. The umash value is determined by 61,69 lines in the / etc/profile file. You can see the code in detail.