Both gateway server and website server adopt centos 7 operating system.
Gateway servers are equipped with three Gigabit Network cards, which are connected to Internet, intranet and website servers respectively.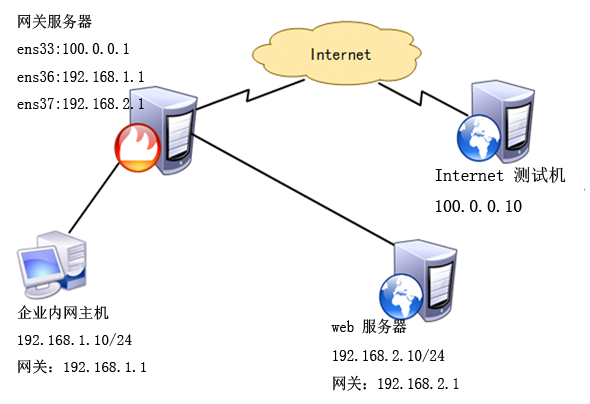
The requirements are as follows:
The gateway server connection card ens33 is configured as a public network IP address and assigned to the external area of firewall; the connection card ens37 address is 192.168.1.1, assigned to the trusted area of firewall; and the connection server network card ens38 address is 192.168.2.1, assigned to the DMZ area of firewall.
Web server and gateway server are managed remotely through SSH. For security, the default port of SSH is changed to 12345.
The website server opens https and filters unencrypted http traffic.
The website server rejects ping and the gateway server rejects ping from the Internet.
Intranet users need to share Internet access through gateway servers.
Internet users need to access web servers.
Basic environmental configuration:
Gateway Server Configuration Network Card:
[root@localhost network-scripts]# ip a = ip addr
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:fc:60:4b brd ff:ff:ff:ff:ff:ff
inet 100.0.0.1/8 brd 100.255.255.255 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::5f65:9c3d:d218:7cea/64 scope link
valid_lft forever preferred_lft forever
3: ens36: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:fc:60:55 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.1/24 brd 192.168.1.255 scope global ens36
valid_lft forever preferred_lft forever
inet6 fe80::7456:2bbc:dc20:31bd/64 scope link
valid_lft forever preferred_lft forever
4: ens37: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:fc:60:5f brd ff:ff:ff:ff:ff:ff
inet 192.168.2.1/24 brd 192.168.2.255 scope global ens37
valid_lft forever preferred_lft forever
inet6 fe80::1e90:6601:56c2:c9ba/64 scope link
valid_lft forever preferred_lft forever
Start the routing and forwarding function on the gateway server:
[root@localhost /]# vim /etc/sysctl.conf net.ipv4.ip_forward = 1 [root@localhost /]# sysctl -p net.ipv4.ip_forward = 1
Network Card Configuring web Server:
[root@localhost /]# ip a
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:2f:24:4b brd ff:ff:ff:ff:ff:ff
inet 192.168.2.10/24 brd 192.168.2.255 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::19de:d9a7:568a:f34f/64 scope link
valid_lft forever preferred_lft forever
[root@localhost /]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.2.1 0.0.0.0 UG 100 0 0 ens33
Internet Tester Network Card Configuration:
[root@localhost /]# ip a
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:45:66:64 brd ff:ff:ff:ff:ff:ff
inet 100.0.0.10/8 brd 100.255.255.255 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::3ebc:8f75:cd28:e516/64 scope link tentative
valid_lft forever preferred_lft forever
web server environment construction:
[root@localhost ~]# systemctl start firewalld #Start Firewall
[root@localhost ~]# yum -y install httpd mod_ssl #Install httpd and mod_ssl
[root@localhost ~]# systemctl start httpd #service httpd start
[root@localhost ~]# systemctl enable httpd #Set to Boot-Up Self-Start
[root@localhost ~]# vim /var/www/html/index.html #New Website Testing Home Page File
<h1>test.com </h1>
[root@localhost ~]# vim /etc/ssh/sshd_config #Change the listening port of SSH (SELinux needs to be turned off):
................
Port 12345
................
[root@localhost ~]# systemctl restart sshd
Configure firewalld firewall on the web server:
1. Set the default area to dmz:
[root@localhost ~]# firewall-cmd --set-default-zone=dmz success
2. Open https service for dmz area and add port 12345 of tcp:
[root@localhost ~]# firewall-cmd --zone=dmz --add-service=https --permanent success [root@localhost ~]# firewall-cmd --zone=dmz --add-port=12345/tcp --permanent success
3. Prohibit ping:
[root@localhost ~]# firewall-cmd --add-icmp-block=echo-request --zone=dmz --permanent success
4. Because the default port of the predefined SSH service has been changed, the predefined SSH service has been removed:
[root@localhost ~]# firewall-cmd --zone=dmz --remove-service=ssh --permanent success
5. Reload the firewalld configuration and view the previous configuration:
[root@localhost ~]# firewall-cmd --reload success [root@localhost ~]# firewall-cmd --list-all dmz (active) target: default icmp-block-inversion: no interfaces: ens33 sources: services: https ports: 12345/tcp protocols: masquerade: no forward-ports: source-ports: icmp-blocks: echo-request rich rules:
firewalld firewall is configured on the gateway server:
1. Add the network card to the specified area:
[root@localhost /]# systemctl start firewalld #Enabling Firewall [root@localhost /]# firewall-cmd --set-default-zone=external #Set the default area to external success [root@localhost /]# firewall-cmd --change-interface=ens37 --zone=trusted #Add ens37 to trusted area The interface is under control of NetworkManager, setting zone to 'trusted'. success [root@localhost /]# firewall-cmd --change-interface=ens38 --zone=dmz #Add ens38 to the dmz region The interface is under control of NetworkManager, setting zone to 'dmz'. success
2. View the configuration and save it as permanent
[root@localhost /]# firewall-cmd --get-active-zones dmz interfaces: ens37 external interfaces: ens33 trusted interfaces: ens36 [root@localhost /]# firewall-cmd --runtime-to-permanent # Save the current configuration to a file success
3. Testing on the internal mainframe of the enterprise: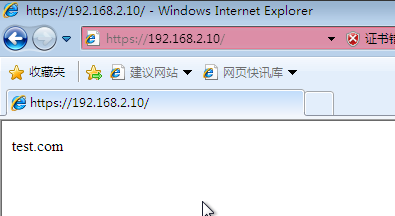
4. Change the listening port of SSH and restart the service (SELinux needs to be closed):
[root@localhost ~]# vim /etc/ssh/sshd_config
................
Port 12345
................
[root@localhost ~]# systemctl restart sshd
5. Configure external area to add tcp port 12345:
[root@localhost /]# firewall-cmd --zone=external --add-port=12345/tcp --permanent success
6. external area removes SSH services:
[root@localhost /]# firewall-cmd --zone=external --remove-service=ssh --permanent success
7. Configure external zone to prohibit ping:
[root@localhost /]# firewall-cmd --zone=external --add-icmp-block=echo-request --permanent success
8. Reload firewall configuration:
[root@localhost /]# firewall-cmd --reload success
Test ssh connection:
The Internet tester connects the gateway server's external interface address through SSH at port 12345:
[root@localhost /]# ssh -p 12345 100.0.0.1 The authenticity of host '[100.0.0.1]:12345 ([100.0.0.1]:12345)' can't be established. ECDSA key fingerprint is 68:df:0f:ac:c7:75:df:02:88:7d:36:6a:1a:ae:27:23. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '[100.0.0.1]:12345' (ECDSA) to the list of known hosts. root@100.0.0.1's password: Last login: Sun Sep 1 16:36:33 2019 [root@localhost ~]#
Use SSH of Intranet Tester to log on to Port 12345 of web Site Server:
[root@localhost /]# ssh -p 12345 192.168.2.10 The authenticity of host '[192.168.2.10]:12345 ([192.168.2.10]:12345)' can't be established. ECDSA key fingerprint is 68:df:0f:ac:c7:75:df:02:88:7d:36:6a:1a:ae:27:23. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '[192.168.2.10]:12345' (ECDSA) to the list of known hosts. root@192.168.2.10's password: Last login: Sun Sep 1 16:36:39 2019 [root@localhost ~]#
Implementing IP camouflage and port forwarding:
1. Build web services on Internet tester to test:
[root@localhost ~]# yum -y install httpd [root@localhost ~]# vim /var/www/html/index.html <h1> www.baidu.com</h1> [root@localhost ~]# systemctl enable httpd [root@localhost ~]# systemctl start httpd
2. Both the internal tester and the dmz website service area can access the website of the external network (if not, it may be the firewall configuration problem of the network tester. The firewall of the public network tester can be shut down or the traffic of related services can be released first):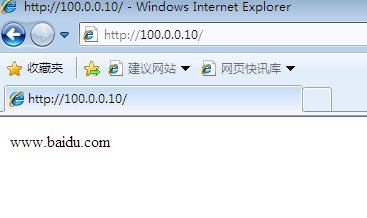
3. Check whether the external area of the gateway server has enabled address camouflage:
[root@localhost /]# firewall-cmd --list-all --zone=external external (active) target: default icmp-block-inversion: no interfaces: ens33 sources: services: ports: 12345/tcp protocols: masquerade: yes # Indicates that address camouflage is enabled forward-ports: sourceports: icmp-blocks: echo-request rich rules:
4. Open the IP camouflage only for the address of the 192.168.1.0/24 segment of the source address.
Turn off external's default address masquerade on gateway server, add rich rules, require that the source address of 192.168.1.0/24 segment in external area open address IP masquerade:
[root@localhost ~]# firewall-cmd --remove-masquerade --zone=external success [root@localhost ~]# firewall-cmd --zone=external --add-rich-rule='rule family=ipv4 source address=192.168.1.0/24 masquerade' success
On the dmz area, the test access found that it was inaccessible, but the intranet host could:
[root@localhost /]# curl http://100.0.0.10 curl: (7) Failed connect to 100.0.0.10:80; No route to host
5. Configure port forwarding to enable Internet users to access internal web servers:
Configure on the gateway server:
[root@localhost /]# firewall-cmd --zone=external --add-forward-port=port=443:proto=tcp:toaddr=192.168.2.10 success
The web server accessing the intranet on the Internet tester succeeded: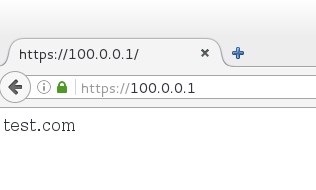
6. Using rich rules to realize port forwarding:
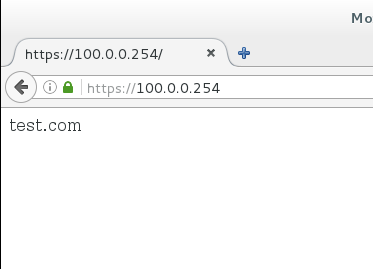
After the above configuration is completed, if the company now applies for a new public network ip address of 100.0.0.254, then it needs to do port forwarding again:
1. Configure the newly applied network address 100.0.0.254 on the external network interface ens33 of the gateway server as the second IP address:
[root@localhost /]# vim /etc/sysconfig/network-scripts/ifcfg-ens33 TYPE=Ethernet BOOTPROTO=static IPADDR0=100.0.0.1 # Change to the next four lines PREFIX0=24 IPADDR1=100.0.0.254 PREFIX1=24 # Add to two IP DEFROUTE=yes PEERDNS=yes PEERROUTES=yes IPV4_FAILURE_FATAL=no IPV6INIT=yes IPV6_AUTOCONF=yes IPV6_DEFROUTE=yes IPV6_PEERDNS=yes IPV6_PEERROUTES=yes IPV6_FAILURE_FATAL=no IPV6_ADDR_GEN_MODE=stable-privacy NAME=ens33 DEVICE=ens33 ONBOOT=yes ZONE=external [root@localhost /]# ifdown ens33;ifup ens33 # Restart Network Card to Make Configuration Effective
[root@localhost /]# ip a # See if the configuration was successful
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:fc:60:4b brd ff:ff:ff:ff:ff:ff
inet 100.0.0.1/24 brd 100.0.0.255 scope global ens33
valid_lft forever preferred_lft forever
inet 100.0.0.254/24 brd 100.0.0.255 scope global secondary ens33
valid_lft forever preferred_lft forever
inet6 fe80::5f65:9c3d:d218:7cea/64 scope link
valid_lft forever preferred_lft forever
2. Configure port forwarding with rich rules:
[root@localhost /]# firewall-cmd --zone=external --add-rich-rule='rule family=ipv4 destination address=100.0.0.254/24 forward-port port=443 protocol=tcp to-addr=192.168.2.10' success
3. Verification: