Preface
Communication on the Internet needs to be accessed with the help of IP address, but people's memory of numbers is far less than that of words, so it's a good way to convert IP address into easily memorized words, but computers can only recognize 0 and 1 codes. At this time, a mechanism is needed to solve the conversion problem between IP address and host name. DNS is called Domain Name System, that is, Domain Name System The function is to resolve the "web address" we often use to IP address. In online distributed database system, most DNS names are resolved locally, and only a few need to communicate on the Internet, so the efficiency is high.
1. Role of DNS server
- Forward resolution: find the corresponding IP address according to the host name (domain name)
- Reverse resolution: find the corresponding host domain name according to the IP address
2. Distributed data structure of DNS system
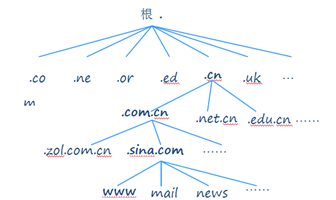
3. DNS query method
- Recursive query: the way that most clients resolve domain names to DNS servers;
- Iterative query: the way that most DNS servers resolve domain names to other DNS servers;
4. Type of DNS server
- Cache domain name server: also known as cache only server, it can obtain domain name - > IP address records by querying other domain name servers, cache the domain name query results to the local, and improve the speed of repeated queries;
- Primary domain name server: the official server of a specific DNS zone, which is unique and responsible for maintaining the mapping records of all domain names - > IP addresses in the zone;
- Secondary domain name server: also known as secondary domain name server, whose domain name - > IP address records are maintained from the primary domain name server;
5. BIND domain name service foundation
- BIND (Berkeley Internet Name Daemon) Berkeley Internet domain name service.
- Main executive program / usr/sbin/named
- Service script / etc/init.d/named
- Default listening port: 53
- Main configuration file: / etc/named.conf
- Zone configuration file / etc/named.rfc1912.zones is used to save the correspondence between domain name and IP address
- Save the data file of DNS resolution record: / var/named/chroot/var/named/
6. DNS server resolution
DNS is mainly used for host name resolution
Analysis:
According to one name provided by the user, query the resolution library to get another name. Domain name - > IP, IP - > domain name;
Resource records:
- TTL value: lifetime, DNS record cache time on DNS server
- IN: indicates that the following data uses INTERNET standard
- SOA record: start authorization record, only one region file
- @: indicates the corresponding domain name (region)
- test.com: authorized host
- root.test.com: management email root@test.com
- rr(resource record): there is a concept of type, which is used for the properties resolved by this record
- A record: used to specify the IP(ipv4) address record corresponding to the host name (or domain name). (AAAA ipv6)
- CNAME record: define an alias (domain name) of the corresponding host
- NS record: domain name server record, used to specify which DNS server will resolve the domain name
- type: type: master, slave, hint
- Master: indicates that the primary domain name server (master-slave) is defined
- Slave: indicates that the secondary domain name server (master-slave) is defined
- MX record: mail exchange record, pointing to mail server
- hint: indicates the root domain name server in the Internet
- Zone: key to define a zone, a zone key to define a zone
- PTR record: reverse DNS record, reverse A record
1, DNS service Bind installation
Host planning
| service | IP |
|---|---|
| DNS service (primary) | 192.168.182.13 |
| DNS service (from) | 192.168.182.12 |
| Test host | 192.168.182.10 |
1. Install bind
[root@localhost ~]# yum install -y bind* [root@localhost ~]# named -v BIND 9.11.4-P2-RedHat-9.11.4-9.P2.el7 (Extended Support Version) <id:7107deb>
2. Turn off firewall policy and selinux
[root@localhost ~]# systemctl stop firewalld [root@localhost ~]# setenforce 0
2, DNS Service Building
1. Master profile
[root@localhost ~]# vim /etc/named.conf ///Only three changes options { #option listen-on port 53 { any; }; #The service listening port is53 ///Change to any anyone can access listen-on-v6 port 53 { any; }; #The service listening port is53(ipv6) ///Change to any anyone can access directory "/var/named"; #Directory where configuration files are stored dump-file "/var/named/data/cache_dump.db"; #Cache of parsed content statistics-file "/var/named/data/named_stats.txt"; #Static cache (generally not used) memstatistics-file "/var/named/data/named_mem_stats.txt"; #Static cache (stored in memory, generally not used) allow-query { any; }; #Clients allowed to connect ///Change to any anyone can access recursion yes; #recursive lookup dnssec-enable yes; #DNSencryption dnssec-validation yes; #DNSAdvanced encryption algorithm dnssec-lookaside auto; #DNSSomething about encryption /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; #Key for encryption (encryption of private key and public key, very strong) }; logging { #Journal channel default_debug { file "data/named.run"; #Operation status file severity dynamic; #Static server address (root domain) }; }; zone "." IN { #Root domain analysis type hint; master slave file "named.ca"; #Root domain profile }; include "/etc/named.rfc1912.zones"; #Extension profile (new domain name) include "/etc/named.root.key";
2. Zone profile
- It is used to save the location of the corresponding relationship between domain name and IP address. In this file, it defines the resolution rules of domain name and IP address, the location of the saved file, and the service type, but does not contain the specific information such as the corresponding relationship between domain name and IP address;
- There are three types of services: hint (root region), master (primary region) and slave (secondary region). The common master and slave refer to the master and slave servers;
[root@localhost ~]# vim /etc/named.rfc1912.zones ///Add positive and negative resolution to the configuration file zone "villiantsang.com" IN { type master; #Service type file "villiantsang.com.zone"; #Domain name andIPAddress resolution rule save file allow-update { none; }; #Which clients are allowed to dynamically update resolution information (master-slave configuration) }; #Forward resolution parameter zone "182.168.192.in-addr.arpa" IN { #Expressed as192.168.182.0/24Reverse resolution area of network segment type master; file "villiantsang.com.local"; #Domain name andIPAddress resolution rule save file allow-update { none; }; #Which clients are allowed to dynamically update resolution information (master-slave configuration) }; #Reverse parsing parameters
Copy plus - p parameter can keep the owner, group, permission attribute and other information of the original file
[root@localhost ~]# cd /var/named/ [root@localhost named]# cp -p named.localhost villiantsang.com.zone $TTL 1D ///Cache record is 1 day @ IN SOA ns.villiantsang.com. root ( ///#@Current domain name ා start of authorization information ා address of DNS zone ා do not use @ symbol for domain name administrator mailbox 0 ; serial ///Update serial number (related to DNS from) 1D ; refresh ///Update time (related to DNS from) 1H ; retry ///Retry latency (related to slave DNS) 1W ; expire ///Expiration time (related to DNS slave) 3H ) ; minimum ///Invalid resolution record time (related to from DNS) @ IN NS ns.villiantsang.com. ///Define ns record ns IN A 192.168.182.13 ///Domain name server, used to specify the IP as DNS server (ns must correspond to DNS server IP) V1 IN A 192.168.182.11 ///Define IP corresponding to v1 host: 192.168.182.11 V2 IN A 192.168.182.12 ///Define IP corresponding to v2 host: 192.168.182.12 www IN A 192.168.182.13 ///Define IP corresponding to www host: 192.168.182.13 bbs IN A 192.168.182.14 ///Define IP corresponding to bbs host: 192.168.182.14 @ IN MX 10 mail.villiantsang.com. ///Define email address mail IN A 192.168.182.10 ///Define email address
The function of reverse resolution is to resolve the IP address submitted by the user to the corresponding domain name information. It is generally used to shield all domain names bound on an IP address as a whole and to shield the spam sent by some domain names
[root@localhost ~]# cd /var/named/ [root@localhost named]# cp -p named.loopback villiantsang.com.local $TTL 1D @ IN SOA villiantsang.com. root ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum @ IN NS ns.villiantsang.com. ///IP of DNS domain name server reverse resolution: 11 11 IN PTR v1.villiantsang.com. ///Define IP for reverse resolution of v1 host header: 11 12 IN PTR v2.villiantsang.com. ///Define IP for reverse resolution of v2 host head: 12 13 IN PTR www.villiantsang.com. ///Define IP for reverse resolution of www host header: 13 14 IN PTR bbs.villiantsang.com. ///Define the IP of bbs host head reverse resolution: 14 10 IN PTR mail.villiantsang.com. ///Define email address, specify IP
- Test whether the configuration file is correct through the command named checkzone
[root@localhost named]# named-checkzone villiantsang.com.zone villiantsang.com.local zone villiantsang.com.zone/IN: loaded serial 0 OK
3. Restart DNS Service
- Restart DNS Service
[root@localhost named]# systemctl restart named
3, DNS domain name resolution test
Forward analysis
1. Modify the domain name resolution file / etc/resolv.conf file of test host 192.168.182.10
[root@test ~]# vim /etc/resolv.conf nameserver 192.168.182.13 ///To test, delete all domain name resolution services and only set this domain name resolution service (Baidu (8.8.8.8 is not allowed to be ping ed))
2. Pass ping test
[root@test ~]# ping v1.villiantsang.com PING V1.villiantsang.com (192.168.182.11) 56(84) bytes of data. ///The IP of v1.villiantsang.com is 192.168.182.11 ^C --- V1.villiantsang.com ping statistics --- 2 packets transmitted, 0 received, 100% packet loss, time 1000ms [root@test ~]# ping v2.villiantsang.com PING V2.villiantsang.com (192.168.182.12) 56(84) bytes of data. ///The IP of v2.viliantsang.com is 192.168.182.12 ^C --- V2.villiantsang.com ping statistics --- 2 packets transmitted, 0 received, 100% packet loss, time 999ms [root@test ~]# ping www.villiantsang.com PING www.villiantsang.com (192.168.182.13) 56(84) bytes of data. ///The IP of www.villiantsang.com is 192.168.182.13 ^C --- www.villiantsang.com ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1000ms [root@test ~]# ping bbs.villiantsang.com PING bbs.villiantsang.com (192.168.182.14) 56(84) bytes of data. ///The IP of bbs.villiantsang.com is 192.168.182.14 ^C --- bbs.villiantsang.com ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1000ms
3. Test with bind tool nslookup
[root@test ~]# nslookup v1.villiantsang.com Server: 192.168.182.13 Address: 192.168.182.13#53 Name: V1.villiantsang.com Address: 192.168.182.11 [root@test ~]# nslookup v2.villiantsang.com Server: 192.168.182.13 Address: 192.168.182.13#53 Name: V2.villiantsang.com Address: 192.168.182.12 [root@test ~]# nslookup www.villiantsang.com Server: 192.168.182.13 Address: 192.168.182.13#53 Name: www.villiantsang.com Address: 192.168.182.13 [root@test ~]# nslookup bbs.villiantsang.com Server: 192.168.182.13 Address: 192.168.182.13#53 Name: bbs.villiantsang.com Address: 192.168.182.14
Backward analysis
Test by reverse parsing command: nslookup -qt=ptr IP
[root@test ~]# nslookup -qt=ptr 192.168.182.10 *** Invalid option: qt=ptr 10.182.168.192.in-addr.arpa name = mail.villiantsang.com. [root@test ~]# nslookup -qt=ptr 192.168.182.11 *** Invalid option: qt=ptr 11.182.168.192.in-addr.arpa name = v1.villiantsang.com. [root@test ~]# nslookup -qt=ptr 192.168.182.12 *** Invalid option: qt=ptr 12.182.168.192.in-addr.arpa name = v2.villiantsang.com. [root@test ~]# nslookup -qt=ptr 192.168.182.13 *** Invalid option: qt=ptr 13.182.168.192.in-addr.arpa name = www.villiantsang.com. [root@test ~]# nslookup -qt=ptr 192.168.182.14 *** Invalid option: qt=ptr 14.182.168.192.in-addr.arpa name = bbs.villiantsang.com.
4, DNS master-slave configuration
1. Modify zone profile in primary DNS Service
[root@master ~]# vim /etc/named.rfc1912.zones ///Add positive and negative resolution to the configuration file zone "villiantsang.com" IN { type master; ///Service type master file "villiantsang.com.zone"; allow-update { 192.168.182.12; }; ///Allow 192.168.182.12 client to dynamically update parsing information }; zone "182.168.192.in-addr.arpa" IN { type master; ///Service type master file "villiantsang.com.local"; allow-update { 192.168.182.12; }; ///Allow 192.168.182.12 client to dynamically update parsing information }; ///Reverse parsing parameters
2. Install bind from DNS Service
[root@slave ~]# yum install -y bind*
3. Modify master profile from DNS Service
[root@slave ~]# vim /etc/named.conf options { listen-on port 53 { any; }; listen-on-v6 port 53 { any; }; allow-query { any; };
4. Modify zone profile from DNS Service
[root@slave ~]# vim /etc/named.rfc1912.zones zone "villiantsang.com" IN { type slave; ///slave service file "slave/villiantsang.com.zone"; ///The configuration file is parsed forward from the service. It does not need to be created. It will be generated automatically at startup masters { 192.168.182.13; }; ///Bind master master service IP address }; zone "182.168.192.in-addr.arpa" IN { type slave; ///slave service file "slave/villiantsang.com.local"; ///The configuration file is parsed from the service reversely. It is not created and will be generated automatically at startup masters { 192.168.182.13; }; ///Bind master master service IP address };
5. Restart the master-slave DNS Service
[root@master ~]# systemctl restart named ///Restart the primary DNS Service [root@slave ~]# systemctl restart named ///Restart from DNS Service
6. Check whether the positive and negative parsing files are automatically generated from the service
[root@slave slaves]# pwd /var/named/slaves ///From service profile directory [root@slave slaves]# ls villiantsang.com.local villiantsang.com.zone ///Auto generated positive and negative parsing configuration file
7. DNS test
Forward analysis
- Pass ping test
[root@slave ~]# ping www.villiantsang.com PING www.villiantsang.com (192.168.182.13) 56(84) bytes of data. 64 bytes from www.villiantsang.com (192.168.182.13): icmp_seq=1 ttl=64 time=0.675 ms [root@slave ~]# ping v1.villiantsang.com PING V1.villiantsang.com (192.168.182.11) 56(84) bytes of data. 64 bytes from www.villiantsang.com (192.168.182.11): icmp_seq=1 ttl=64 time=0.675 ms [root@slave ~]# ping v2.villiantsang.com PING V2.villiantsang.com (192.168.182.12) 56(84) bytes of data. 64 bytes from v2.villiantsang.com (192.168.182.12): icmp_seq=1 ttl=64 time=0.019 ms [root@slave ~]# ping bbs.villiantsang.com PING bbs.villiantsang.com (192.168.182.14) 56(84) bytes of data. 64 bytes from www.villiantsang.com (192.168.182.14): icmp_seq=1 ttl=64 time=0.675 ms
- Test with bind tool nslookup
[root@slave ~]# nslookup www.villiantsang.com Server: 127.0.0.1 Address: 127.0.0.1#53 Name: www.villiantsang.com Address: 192.168.182.13 [root@slave ~]# nslookup v1.villiantsang.com Server: 127.0.0.1 Address: 127.0.0.1#53 Name: V1.villiantsang.com Address: 192.168.182.11 [root@slave ~]# nslookup v2.villiantsang.com Server: 127.0.0.1 Address: 127.0.0.1#53 Name: V2.villiantsang.com Address: 192.168.182.12 [root@slave ~]# nslookup bbs.villiantsang.com Server: 127.0.0.1 Address: 127.0.0.1#53 Name: bbs.villiantsang.com Address: 192.168.182.14
Backward analysis
[root@slave ~]# nslookup -qt=ptr 192.168.182.10 *** Invalid option: qt=ptr 10.182.168.192.in-addr.arpa name = mail.villiantsang.com. [root@slave ~]# nslookup -qt=ptr 192.168.182.11 *** Invalid option: qt=ptr 11.182.168.192.in-addr.arpa name = v1.villiantsang.com. [root@slave ~]# nslookup -qt=ptr 192.168.182.12 *** Invalid option: qt=ptr 12.182.168.192.in-addr.arpa name = v2.villiantsang.com. [root@slave ~]# nslookup -qt=ptr 192.168.182.13 *** Invalid option: qt=ptr 13.182.168.192.in-addr.arpa name = www.villiantsang.com. [root@slave ~]# nslookup -qt=ptr 192.168.182.14 *** Invalid option: qt=ptr 14.182.168.192.in-addr.arpa name = bbs.villiantsang.com.
Video: https://www.bilibilili.com/video/av68500782? P = 3

