Links to the original text: https://blog.51cto.com/executer/2106151
Catalog
- Tool description
- Parameter interpretation
- Blasting subdomain name
- Custom dictionary exploding subdomain name
- Inverse the IP segment of the specified range
- Inversely Check IP Sections Near Designated Domain Names
- Check the C segment IP where the specified domain name is located
- Scan optimization: custom timeout, multithreading
Tool description
Fierce is a DNS tool for IP and domain name mutual search. It can detect vulnerabilities in domain transfer, explode sub-domain names in dictionaries, check IP segments, and check IP segments of designated domain names. It belongs to a semi-lightweight multi-threaded information collection tool. Fierce can try to establish an HTTP connection to determine whether a subdomain exists. This function is non-lightweight, so it is defined as semi-lightweight.
Parameter interpretation
# fierce (C) Copywrite 2006,2007 - By RSnake at http://ha.ckers.org/fierce/
# Use commands: fierce [-dns example.com] [OPTIONS]
Options:
-connect [header.txt] Right or wrong RFC1918 Address processing HTTP Connection (time-consuming, high traffic), default return to the server response header. Can be specified by file HTTP Requesting header Host Information such as: fierce -dns example.com -connect headers.txt
-delay <number> Specify the time interval between two queries
-dns <domain> Specify the domain name for the query
-dnsfile <dnsfile.txt> Specify the reverse query with a file DNS Server List
-dnsserver <dnsserver> Specify to initialize SOA Inquiring DNS The server. (For initialization only, subsequent queries will use the target's DNS Server)
-file <domain.txt> Output the results to a file
-fulloutput And-connect Combined, output all the information returned by the server
-help print the help information
-nopattern Search mode is not applicable to find hosts. (This parameter is not clear for the time being)
-range <1.1.1.1/24> Internally IP Scope to do IP Reverse checking(This parameter is not yet clear). Must and dnsserver Parameter fit, specify interior DNS Servers, such as: fierce -range 111.222.333.0-255 -dnsserver ns1.example.com
-search <Search list> Specify other domains and find them in other domains (this parameter is not clear), such as: fierce -dns examplecompany.com -search corpcompany,blahcompany
-tcptimeout <number> Specifies the timeout time of the query
-threads [number] Specify the number of threads scanned, default single thread
-traverse [number] The top and bottom of the specified scan IP Scope, Default scan up and down 5 each.
-version Printing fierce Edition
-wide Scan entry IP Address C Paragraph. Generate large traffic and gather more information.
-wordlist <sub.txt> Subdomain name explosion using specified dictionary
# The data in [] is optional and <> is mandatory.
Blasting subdomain name
# Specify the domain name to be scanned by dns parameters
root@owefsadfikls:/# fierce -dns ziroom.com
# In turn, fierce acquires DNS servers for specified domains, checks for transmission vulnerabilities in DNS domains, checks for pan-domain resolution, and explodes sub-domains with dictionaries, as shown below.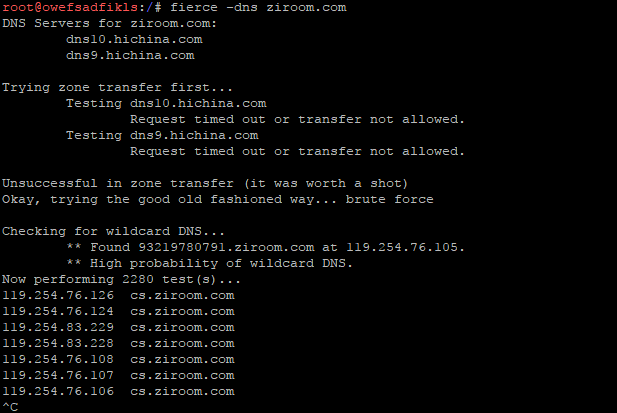
Custom dictionary exploding subdomain name
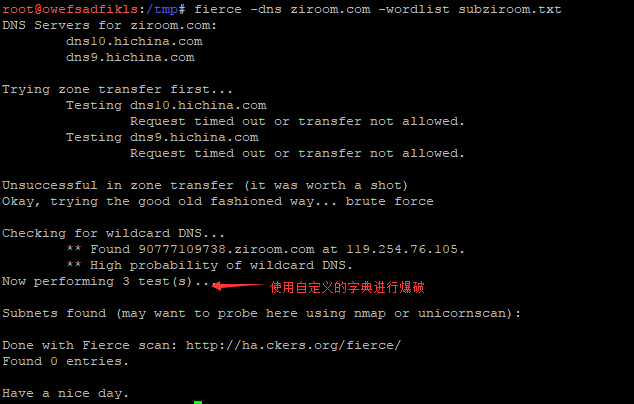
# Specify dictionaries through wordlist
# The prefix of the domain name in the dictionary file, such as admin.ziroom.com, is admin.
root@owefsadfikls:/tmp# fierce -dns ziroom.com -wordlist subziroom.txt
Inversely Check IP Sections Near Designated Domain Names
# Scanning the IP range of the specified domain name through traverse
root@owefsadfikls:/tmp# fierce -dns ziroom.com -traverse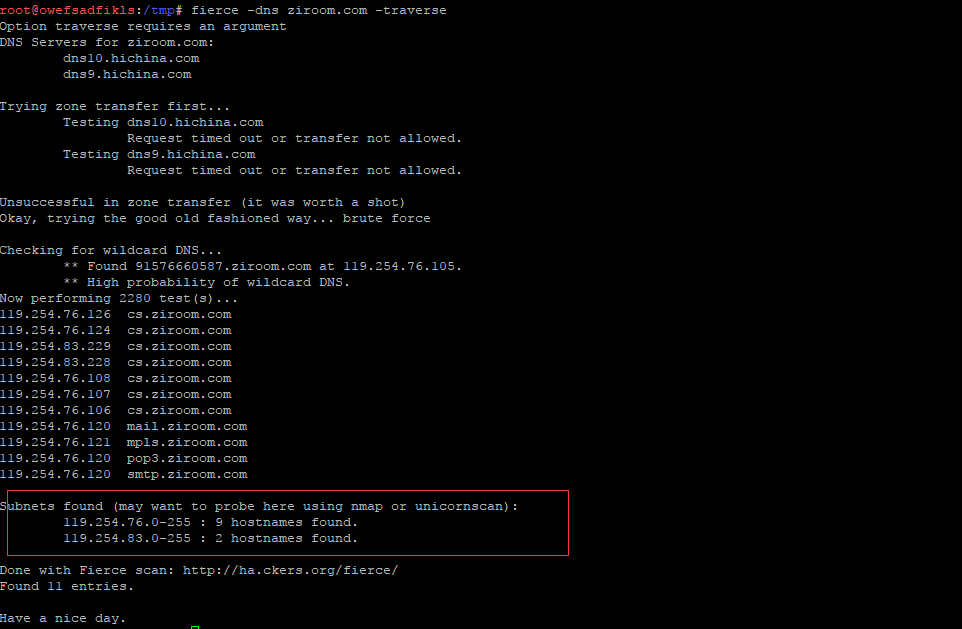
Check Section C of the Designated Domain Name
# Query the host name information of the C segment where the domain name is located by wide
root@owefsadfikls:/tmp# fierce -dns ziroom.com -wide
Scan optimization: multithreading, custom timeout
# Through threads, tcptimeout and delay, scanning can be tuned. Specific parameters vary with different machine and network conditions
