Background
1. Applications such as lancher and kubernetes dashboard need to be accessed through https, so the deployment will enable the support of tracefik for https.
2. Based on the previous lancher ha, it is deployed in the cat system namespace, so this time, it will also deploy tracefik in the cat system namespace, and use the same tls certificate.
II. Traifik deployment
1. Create RBAC policy to authorize service account
Raefik rbac.yaml, a list file of RBAC, is as follows:
--- apiVersion: v1 kind: ServiceAccount metadata: name: traefik-ingress-controller namespace: cattle-system --- kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: name: traefik-ingress-controller rules: - apiGroups: - "" resources: - services - endpoints - secrets verbs: - get - list - watch - apiGroups: - extensions resources: - ingresses verbs: - get - list - watch --- kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: traefik-ingress-controller roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: traefik-ingress-controller subjects: - kind: ServiceAccount name: traefik-ingress-controller namespace: cattle-system
Application manifest file
[root@k8s-master03 traefik]# kubectl apply -f traefik-rbac.yaml serviceaccount/traefik-ingress-controller created clusterrole.rbac.authorization.k8s.io/traefik-ingress-controller created clusterrolebinding.rbac.authorization.k8s.io/traefik-ingress-controller created
2. Use DamonSet controller to deploy tracefik
The list file tracefik ds.yaml of damonset is as follows:
--- kind: ConfigMap apiVersion: v1 metadata: name: traefik-conf namespace: cattle-system data: traefik.toml: | insecureSkipVerify = true defaultEntryPoints = ["http","https"] [entryPoints] [entryPoints.http] address = ":80" [entryPoints.https] address = ":443" [entryPoints.https.tls] [[entryPoints.https.tls.certificates]] CertFile = "/ssl/tls.crt" KeyFile = "/ssl/tls.key" --- kind: DaemonSet apiVersion: extensions/v1beta1 metadata: name: traefik-ingress-controller namespace: cattle-system labels: k8s-app: traefik-ingress-lb spec: template: metadata: labels: k8s-app: traefik-ingress-lb name: traefik-ingress-lb spec: serviceAccountName: traefik-ingress-controller terminationGracePeriodSeconds: 60 hostNetwork: true volumes: - name: ssl secret: secretName: tls-rancher-ingress - name: config configMap: name: traefik-conf containers: - image: traefik name: traefik-ingress-lb ports: - name: http containerPort: 80 hostPort: 80 - name: admin containerPort: 8080 securityContext: privileged: true args: - --configfile=/config/traefik.toml - -d - --web - --kubernetes volumeMounts: - mountPath: "/ssl" name: "ssl" - mountPath: "/config" name: "config" --- kind: Service apiVersion: v1 metadata: name: traefik-ingress-service namespace: cattle-system spec: selector: k8s-app: traefik-ingress-lb ports: - protocol: TCP port: 80 name: web - protocol: TCP port: 8080 name: admin - protocol: TCP port: 443 name: https #type: NodePort
Application manifest file
[root@k8s-master03 traefik]# kubectl apply -f traefik-ds.yaml configmap/traefik-conf created daemonset.extensions/traefik-ingress-controller created service/traefik-ingress-service created
3. Configure forwarding for the traifik UI
traefik-ui.yaml, the manifest file of ﹣ y ingress ﹣ is as follows:
apiVersion: v1 kind: Service metadata: name: traefik-web-ui namespace: cattle-system spec: selector: k8s-app: traefik-ingress-lb ports: - name: web port: 80 targetPort: 8080 --- apiVersion: extensions/v1beta1 kind: Ingress metadata: name: traefik-web-ui namespace: cattle-system spec: rules: - host: traefik-ui.sumapay.com http: paths: - path: / backend: serviceName: traefik-web-ui servicePort: web
Application manifest file
[root@k8s-master03 traefik]# kubectl apply -f traefik-ui.yaml service/traefik-web-ui created ingress.extensions/traefik-web-ui created
4. view
[root@k8s-master01 ~]# kubectl get pods -n cattle-system NAME READY STATUS RESTARTS AGE cattle-cluster-agent-594b8f79bb-pgmdt 1/1 Running 5 11d cattle-node-agent-lg44f 1/1 Running 0 11d cattle-node-agent-zgdms 1/1 Running 5 11d rancher2-9774897c-622sc 1/1 Running 0 9d rancher2-9774897c-czxxx 1/1 Running 0 9d rancher2-9774897c-sm2n5 1/1 Running 1 9d traefik-ingress-controller-hj9nc 1/1 Running 0 142m traefik-ingress-controller-vxcgt 1/1 Running 0 142m [root@k8s-master01 ~]# kubectl get svc -n cattle-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE rancher2 ClusterIP 10.111.16.80 <none> 80/TCP 9d traefik-ingress-service ClusterIP 10.111.121.27 <none> 80/TCP,8080/TCP,443/TCP 143m traefik-web-ui ClusterIP 10.103.112.22 <none> 80/TCP 136m [root@k8s-master01 ~]# kubectl get ingress -n cattle-system NAME HOSTS ADDRESS PORTS AGE rancher2 rancher.sumapay.com 80, 443 9d traefik-web-ui traefik-ui.sumapay.com 80 137m
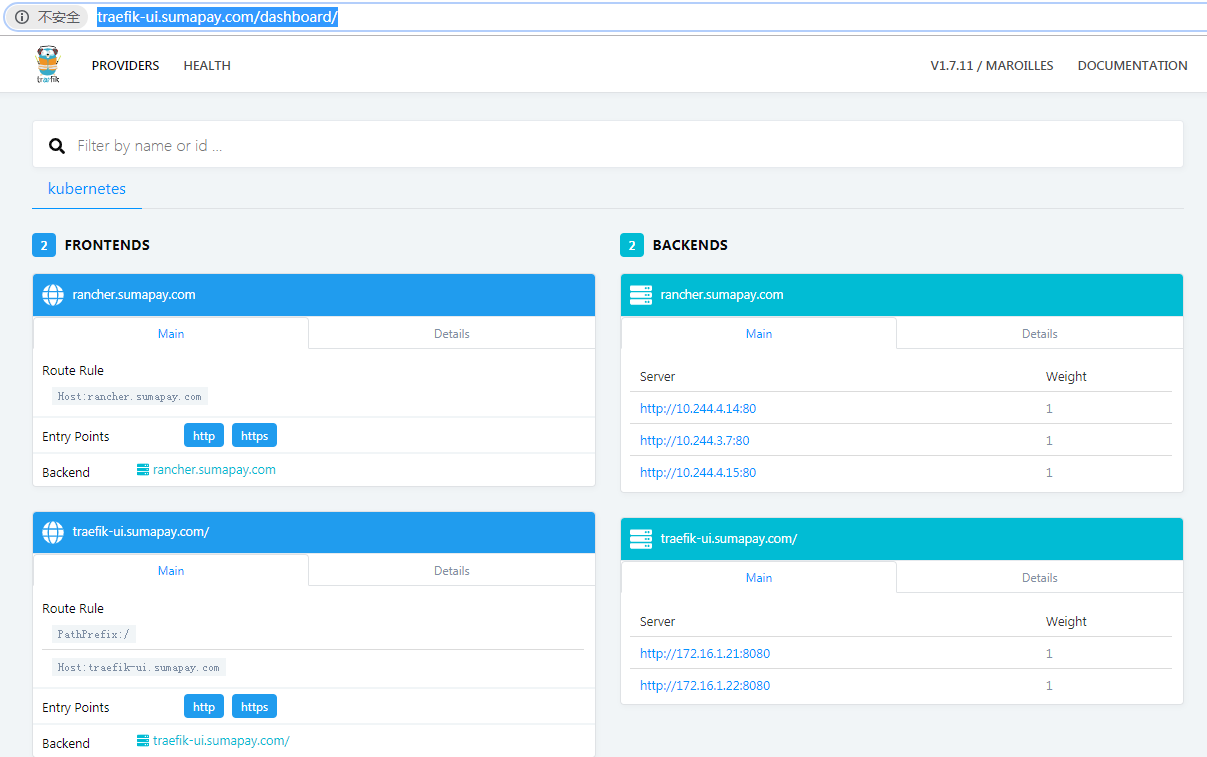
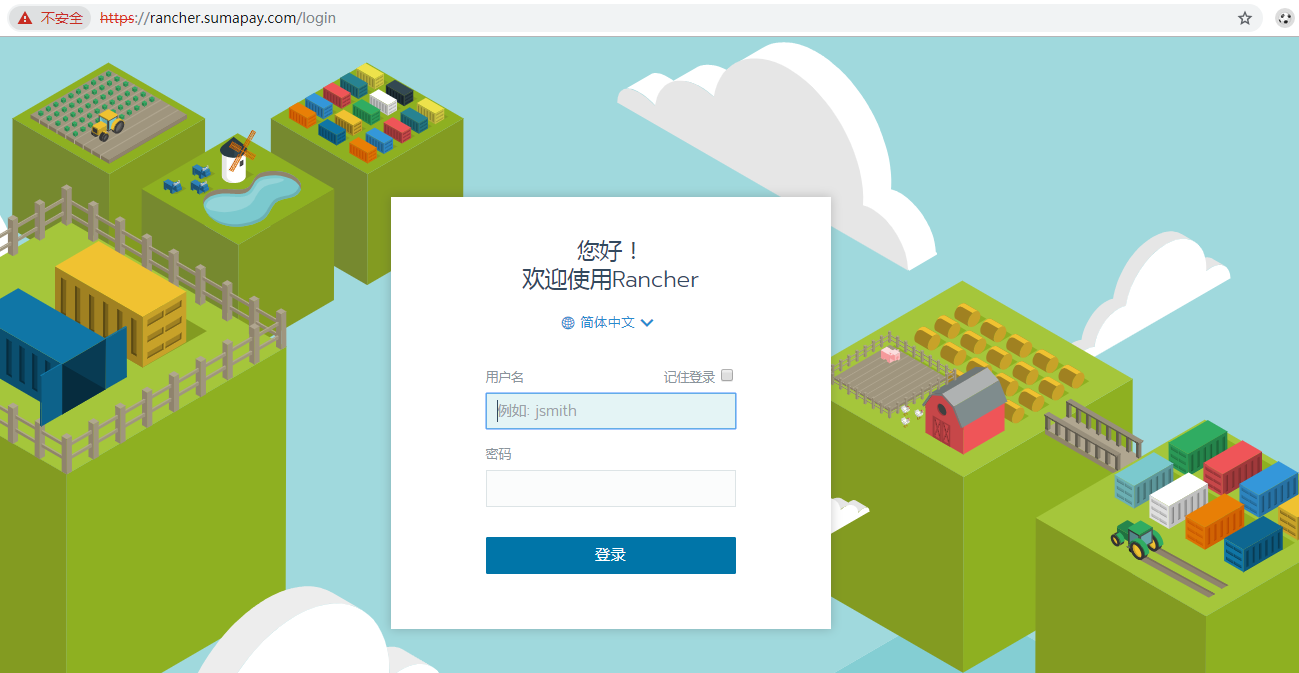
After mapping the domain name to the external load balancing IP, you can access the traifik UI and lancher ha services through the domain name.