Deep understanding of Linux file system and log analysis
1, inode and block overview
-
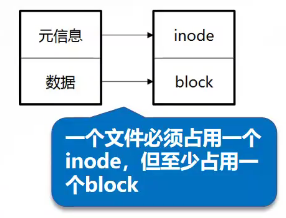
File data includes meta information and actual data
-
Files are stored on the hard disk. The minimum storage unit of the hard disk is "sector", and each sector stores 512 bytes
-
Block
-
Eight consecutive sectors form a block
-
Is the smallest unit of file access
-
-
Inode (index node)
-
The Chinese translation is "index node", also known as i node
-
Used to store file meta information
-
inode table structure
The attribute information of each file, such as file size, time, type, permission, etc., is called file metadata
Metadata is stored in the inode (index node) table. The inode table consists of many records, and the first record stores one
Metadata information of the file.
Each inode table record contains the following information:
- inode number node number
- file type
- jurisdiction
- UID
- GID
- Number of links (number of path names pointing to this file name)
- The file size and different timestamps
- Block pointer to a file on disk
- Other data about the file
Three main time attributes of Linux system files
- ctime(change time)
- The last time a file or directory (property) was changed
- atime(access time)
- The last time a file or directory was accessed
- omtime(modify time)
- The time when the file or directory (content) was last modified
inode content
- Structure of directory file
- A directory is also a file
- Structure of directory file
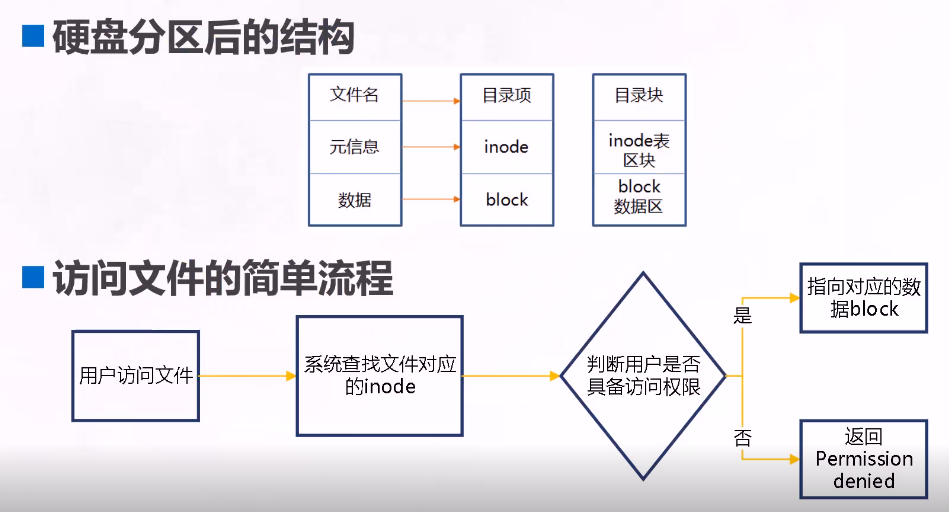
- Each inode has a number, and the operating system uses the inode number to identify different files
- The Linux system does not use the file name internally, but uses the inode number to identify the file
- For users, the file name is just another name for identifying the inode number
About catalog
-
The directory is a special file. The contents of the directory file save the list of files in the directory and the corresponding relationship of inode number
-
The file references an inode number
-
It refers to a file by file name
-
A directory is the mapping between the file name and the file inode number in the directory
cp and inode
cp command:
- Assign a free inode number and generate a new entry in the inode table
- Create a directory entry in the directory and associate the name with the inode number
- Copy data to generate new files
rm command:
- The number of hard links decreases so that the released inode number can be reused
- Put data blocks in the free list
- Delete directory entry
- The data will not actually be deleted immediately, but will be overwritten when another file uses a data block
mv and inode
If the target and source of the mv command are on the same device,
It does not affect the inode table (except timestamp) or the data location on the disk: no data has been moved!
Delete the old directory correspondence and create a new directory correspondence
[root@localhost a]#find -inum 69 -exec rm {} \;
#Use the find command to find the indoe number to delete the specified file
[root@localhost a]#find -inum 69 -delete
File storage summary
inode size
- Inodes also consume hard disk space
- Size of each inode
- Generally 128 bytes or 256 bytes
- Determines the total number of inode s when formatting the file system
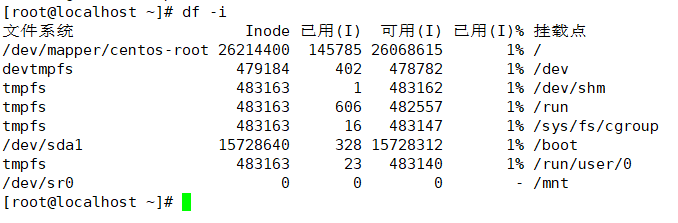
- Use the df -i command to view the total number of inodes per hard disk partition and the number of inodes that have been used
Special role of inode
- Due to the separation of inode number and file name, some Unix/Linux systems have the following phenomena
- When the file name contains special characters, the file may not be deleted normally. You can delete inode directly or delete the file
- When moving or renaming a file, only the file name is changed without affecting the inode number
- After opening a file, the system identifies the file by inode number, regardless of the file name
Link file
- Create linked files for files or directories
- Linked file classification
| Soft link (also known as symbolic link) | Hard link | |
|---|---|---|
| After deleting the original file | invalid | Still available |
| Scope of use | For files or directories | Available only for files |
| Save location | And the original file can be on a different file system | It must be in the same file system (such as a Linux partition) as the original file |
2, Restoring and backing up xfs type files
How to recover a wrongly deleted file using the extundelete tool
Before compiling and installing extendelete, you need to install two dependent packages e2fsprogs LIBS and e2fsprogs devel,
These two packages are available in the / Package directory of the system installation CD. Use rpm or yum to install them.
E2fsprogs devel installation depends on the libcom_err devel package
[root@localhost ~]#yum -y install e2fsprogs-devel e2fsprogs-libs #Install dependent software [root@localhost ~]# tar -jxvf extundelete-0.2.4.tar.bz2 -C /opt #Decompression software [root@localhost ~]# cd /opt/extundelete-0.2.4 #Switch to directory [root@localhost extundelete-0.2.4]# ./configure #Compile and install [root@localhost extundelete-0.2.4]#make [root@localhost extundelete-0.2.4]#make install #Verify the recovery. Create a partition in advance. After mounting, enter the directory to create four files [root@localhost ~]# mkfs.ext3 /dev/sdb1 [root@localhost ~]# mkdir /test/ [root@localhost ~]# mount /dev/sdb1 /test/ [root@localhost ~]# cd /test/ [root@localhost test]# echo a>a [root@localhost test]# echo a>b [root@localhost test]# echo a>c [root@localhost test]# echo a>d
Simulate delete and restore
You need to unmount before recovering
– inode 2 means to view the file with node i as 2. Generally, after the file system is formatted and mounted, node i starts from 2, and 2 represents the initial directory of the file system.
[root@localhost test]# rm -rf a b #Simulated deletion [root@localhost test]# ls c d lost+foun [root@localhost test]# cd [root@localhost ~]# umount /test/ #Unmount [root@localhost ~]#extundelete /dev/sdb1 --inode 2 # The partition viewed by the command starts at node 2 #Check which files exist under this partition [root@localhost ~]# extundelete /dev/sdb1 --restore-all # Command restore all of the partition devices that need to be restored #Use recovery
After executing the restore command, a / RECOVERED_FILES / directory will appear in the current directory, where the recovered files are saved
[root@localhost ~]# ls anaconda-ks.cfg extundelete-0.2.4 extundelete-0.2.4.tar.bz2 RECOVERED_FILES [root@localhost ~]# cd RECOVERED_FILES/ [root@localhost RECOVERED_FILES]# ls a b
Case: restoring files of XFS type
- xfsdump command format
- xfsdump -f backup storage location path or device file to be backed up
- xfsdump backup level (0 by default)
- 0: full backup
- 1-9: incremental backup
- xfsdump common options: - f, - L, - M, - s
- xfsrestore command format
- xfsrestore -f location of recovered files location of recovered files
- Simulate deletion and restore
Common backup parameters include the following:
-
-f: Specify backup file directory
-
-50: Specify the label session label
-
-M: Specify device label media label
-
-s: Backup a single file, - s cannot be directly followed by a path
When using xfsdump, you should pay attention to the following limitations:
- The unmounted file system backup is not supported, so only the mounted file system can be backed up;
- You must use the permission of root to operate;
- Only XFS file system can be backed up;
- The backed up data can only be parsed by xfsrestore;
- Two file systems with the same UUID cannot be backed up (can be viewed using blkid)
process
[root@localhost opt]#mkfs.xfs -f /dev/sdb1 #Force format [root@localhost ~]# fdisk /dev/sdb #Zoning strategy [root@localhost data]#partprobe /dev/sdb #Refresh partition [root@localhost ~]# mkfs.xfs /dev/sdb1 #format [root@localhost ~]# mkdir /date [root@localhost ~]# mount /dev/sdb1 /date/ #mount [root@localhost ~]# cd /date [root@localhost date]# cp /etc/passwd ./ #Copy passwd file into [root@localhost date]# mkdir test [root@localhost date]# touch test/a [root@localhost data]#rpm -qa |grep xfsdump #Check to see if it is installed xfsdump-3.1.4-1.el7.x86_64 [root@localhost data]#yum install xfsdump -y #Not installed. You can use yum to install [root@localhost ~]# xfsdump -f /opt/dump_sdb1 /dev/sdb1 -L dump_sdb1 -M sdb1 #Use the xfsdump command to back up the entire partition and mark it
Recovery after simulated data loss
[root@localhost data]#cd /data/ [root@localhost data]#rm -rf /* [root@localhost data]#ls [root@localhost ~]# xfsrestore -f /opt/dump_sdb1 /date/ ...... xfsrestore: Restore Status: SUCCESS [root@localhost ~]# ls /date/ passwd test [root@localhost ~]#xfsdump -f /opt/dump_sdb1 /dev/sdb1 The file location under the backup path is /opt/dump_sdb1 The location of the backup is/dev/sdb1 please enter label for this dump session (timeout in 300 sec) -> dump_sdb1 #Mark for confirmation session label entered: "dump_sdb1" -> sdb1 media label entered: "sdb1" -> sdb1 #Specify device label media label entered: "sdb1" xfsdump: Dump Status: SUCCESS #recovery [root@localhost opt]#xfsrestore -f dump_sdb1 /data/ use bak File restore data to /data lower [root@localhost opt]#ls /data/ passwd test [root@localhost opt]#xfsdump -l 1 -f /backup/dump_sdb1_level_1 /sdb1 -L dump_sdb1_level_1 -M sdb1 #Set level
3, Log file
- Log function
- It is used to record various events during the operation of the system and program
- By reading the log, it is helpful to diagnose and solve system faults
- Classification of log files
- Kernel and system log
- It is managed uniformly by the system service rsyslog, and the log format is basically similar
- User log
- Record relevant information of system user login and logout
- Program log
- Log files independently managed by various applications have different recording formats
- Kernel and system log
| Log file location | Log file description |
|---|---|
| /var/log/messages kernel and public logs | It is the core system log file, which contains the boot information when the system is started and other status messages when the system is running. I/O errors, network errors, and other system errors are recorded in this file. Other information, such as a person's identity switching to root and the user-defined log of installing software, will also be listed here. |
| /var/log/cron scheduled task log | Record the daily records related to the scheduled tasks of the system |
| /var/log/dmesg system boot log | It records the information of the kernel self-test when the system is powered on. You can also use the dmesg command to directly view the kernel self-test information |
| /var/log/maillog mail log | Log email information |
| User log | |
| /var/log/lastlog | Log the last login time of all users in the system. This file is also a binary file. You can't view it directly with Vi. Instead, use the lastlog command to view |
| /var/log/secure | Record the double interest of authentication and authorization. As long as the procedures involving account and password are recorded, such as system login, ssh login, su switching users, sudo authorization, and even adding users and modifying user passwords will be recorded in this log file |
| /var/log/wtmp | Permanently record the login and logout information of all users, and record the system startup, restart and shutdown events. Similarly, this file is also a binary file. You can't view it directly with Vi, but with the last command |
| /var/tun/ulmp | Record the information of the currently logged in user. This file will change with the user's login and logout, and only record the information of the currently logged in user. Similarly, this file cannot be viewed directly with Vi, but with w, who, users and other commands |
Format of log file:
The format of the log file contains the following 4 columns:
- The time the event occurred.
- The hostname of the server that generated the event.
- The name of the service or program that generated the event.
- Details of the event.
Kernel and system log
It is uniformly managed by the system service rsyslog
- Software package: rsyslog-7.4.7-16.el7.x86_ sixty-four
- Main program: / sbin/rsyslogd
- Configuration file: / etc/rsyslog.conf
Level of log messages
| Class number | news | level | explain |
|---|---|---|---|
| 0 | EMERG | urgent | A condition that causes the host system to become unavailable |
| 1 | ALERT | warning | Measures must be taken immediately to solve the problem |
| 2 | CRIT | serious | More serious situation |
| 3 | ERR | error | An error occurred while running |
| 4 | WARNING | remind | Events that may affect system functions |
| 5 | NOTICE | be careful | It will not affect the system, but it is worth noting |
| 6 | INFO | information | general information |
| 7 | DEBUG | debugging | Program or system debugging information, etc |
User log analysis
- Save the user login, exit the system and other related information
- /var/log/lastlog: recent user login events
- /var/log/wtmp: user login, logoff and system startup and shutdown events
- /var/run/utmp: details of each user currently logged in
- /var/log/secure: security events related to user authentication
- Analysis tools
- users,who,w,last,lastb
Program log analysis
- Managed independently by the corresponding application
- Web Service: / var/log/httpd/
- access_log,errorr_log
- Proxy service: / var/log/squid/
- access.log,cache.log,
- FTP service: / var/log/xferlog
- Web Service: / var/log/httpd/
- Analysis tools
- Text viewing, grep filtering and retrieval, and viewing in Webmin Management Suite
- awk, sed and other text filtering, formatting and editing tools
- Webalizer, Awstats and other special log analysis tools
Log management policy
- Timely backup and archive
- Extend log retention
- Control log access
- The log may contain various sensitive information, such as account, password, etc
- Centralized management log
- Send the log files of the server to the unified log file server
- It is convenient for the unified collection, sorting and analysis of log information
- Prevent accidental loss, malicious tampering or deletion of log information
summary
To deeply understand Linux file system and log analysis, you need to understand the commands of Linux file system and log analysis