Light of dream
Game link: http://monyer.com/game/game1/
F12 view the page source code, click first.php and jump to the first level
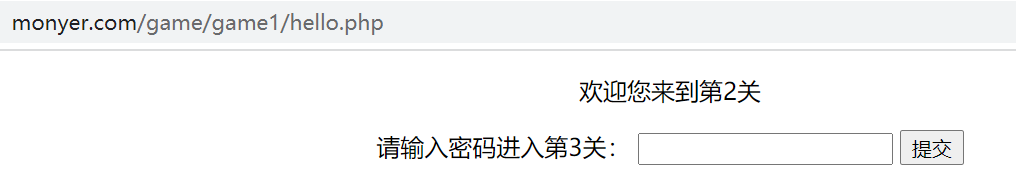
Similarly, check the source code of the first level. The password is two spaces. Submit to the second level
function check(){
if(document.getElementById('txt').value==" "){
window.location.href="hello.php";
}else{
alert("Password error");
}
}
document.oncontextmenu=function(){return false};
var a,b,c,d,e,f,g;
a = 3.14;
b = a * 2;
c = a + b;
d = c / b + a;
e = c - d * b + a;
f = e + d /c -b * a;
g = f * e - d + c * b + a;
a = g * g;
a = Math.floor(a);
function check(){
if(document.getElementById("txt").value==a){
window.location.href=a + ".php";
}else{
alert("Password error");
return false;
}
}
Using js to calculate the value of variable a, you can calculate the result 424178 on the browser console, and submit it to the third level
eval(String.fromCharCode(102,117,110,99,116,105,111,110,32,99,104,101,99,107,40,41,123,13,10,09,118,97,114,32,97,32,61,32,39,100,52,103,39,59,13,10,09,105,102,40,100,111,99,117,109,101,110,116,46,103,101,116,69,108,101,109,101,110,116,66,121,73,100,40,39,116,120,116,39,41,46,118,97,108,117,101,61,61,97,41,123,13,10,09,09,119,105,110,100,111,119,46,108,111,99,97,116,105,111,110,46,104,114,101,102,61,97,43,34,46,112,104,112,34,59,13,10,09,125,101,108,115,101,123,13,10,09,09,97,108,101,114,116,40,34,23494,30721,38169,35823,34,41,59,13,10,09,125,13,10,125));
In the third level, the js script is encoded, decoded by the extension station to get d4g, and submitted to the fourth level
After submitting the password, you will jump back to the third level. You need to press Esc after submitting
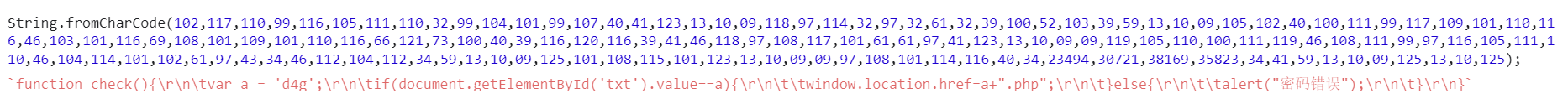
There are two js codes in level 4. The first js obtains sbhe in the extension console, and then runs the second js to obtain the password 3BHE1, which is submitted to level 5;
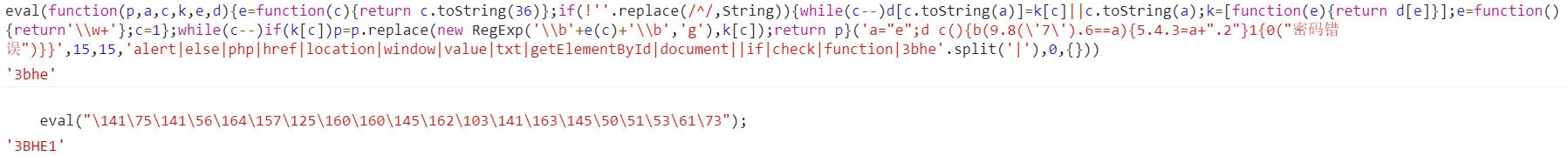
eval(function(p,a,c,k,e,d){e=function(c){return c.toString(36)};if(!''.replace(/^/,String)){while(c--)d[c.toString(a)]=k[c]||c.toString(a);k=[function(e){return d[e]}];e=function(){return'\\w+'};c=1};while(c--)if(k[c])p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c]);return p}('a="e";d c(){b(9.8(\'7\').6==a){5.4.3=a+".2"}1{0("Password error")}}',15,15,'alert|else|php|href|location|window|value|txt|getElementById|document||if|check|function|3bhe'.split('|'),0,{}))
eval("\141\75\141\56\164\157\125\160\160\145\162\103\141\163\145\50\51\53\61\73");
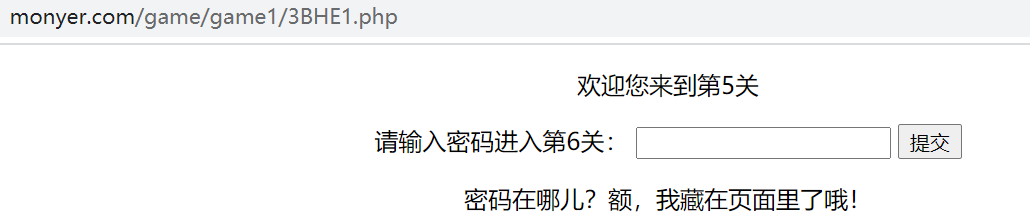
The fifth level prompts the password in the page, but find the password asdf in the request and response, and submit to enter the sixth level
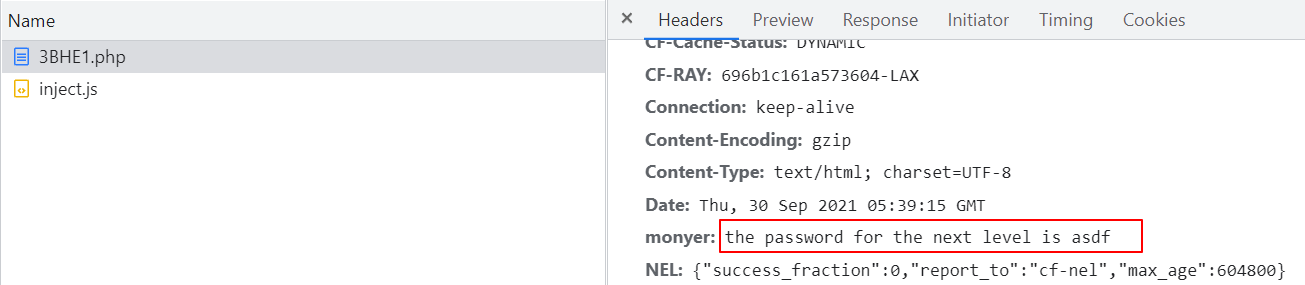
The clue of the sixth level is a search result picture. What is covered is the password. Use Google or bing to search the uncovered content of the page. Find the source of the magazine seventeen and submit it to the seventh level
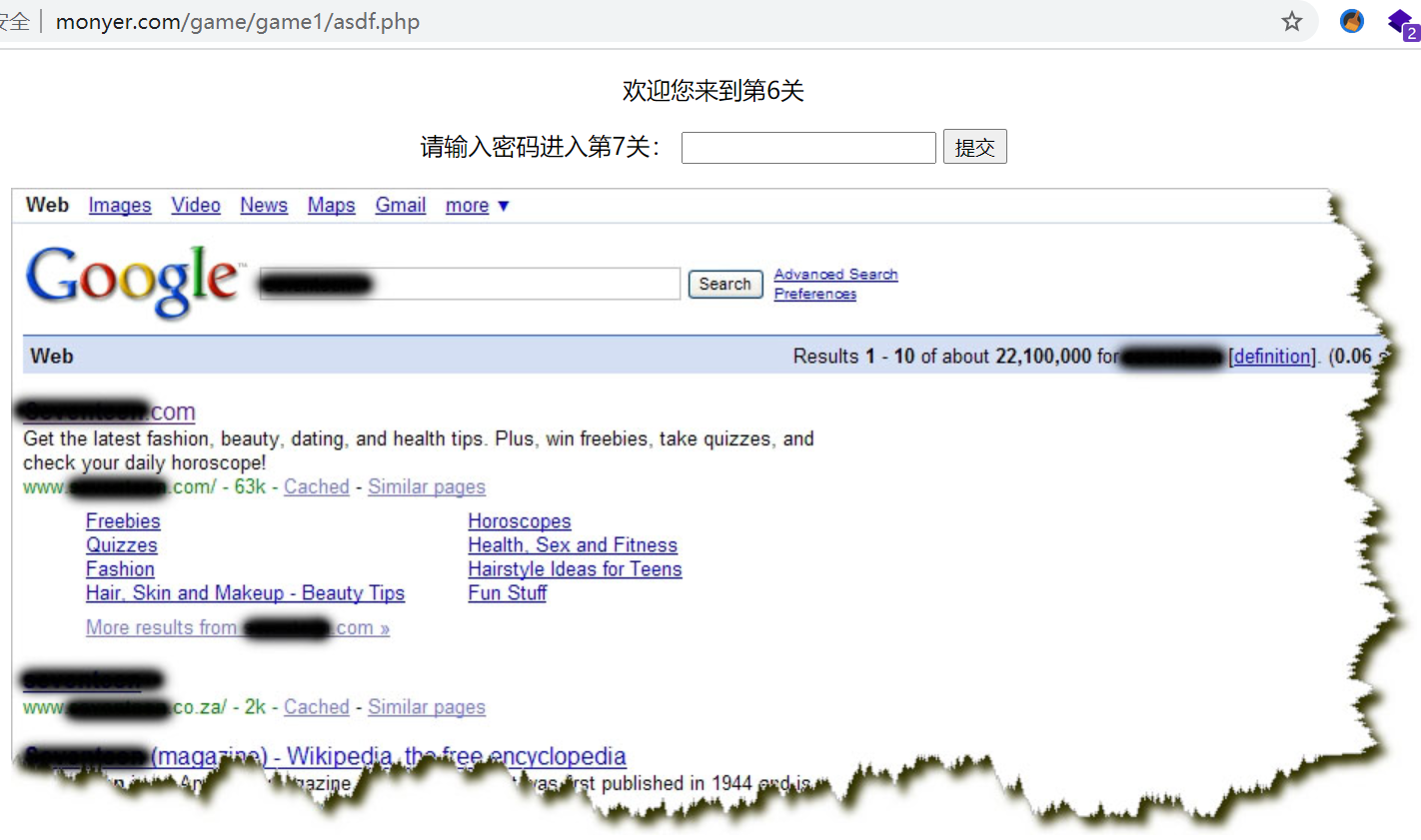
The clue of level 7 is an MD5 value. Decrypt the password eighteen8 and submit it to level 8
Pay attention to other tips. The page that jumps after entering the correct password is a 404 page, but this page is correct. The correct tips are hidden in the page source code
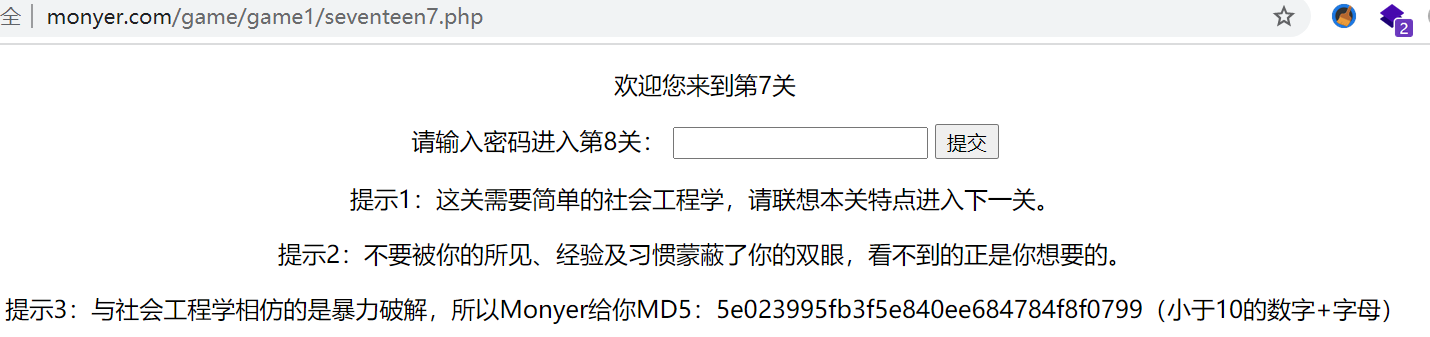
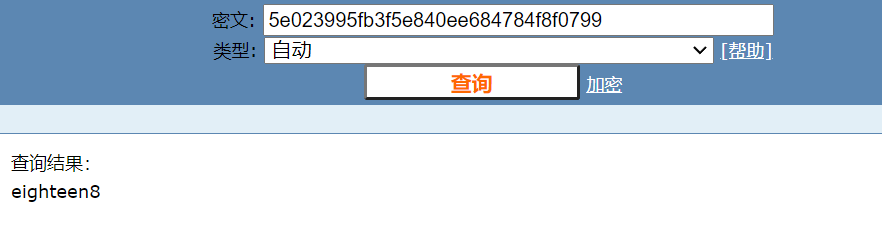
Check the source code of the 8th off page. The password is the sum of all prime numbers within 10000. The calculated result is 5736396. Visit https://monyer.com/game/game1/5736396.php , enter level 9

The 9th level prompts that the password is in the picture. Use notpad + + to open the picture and find the password monyerlikeyou at the bottom of the picture_ The 10 level, submit and enter level 10

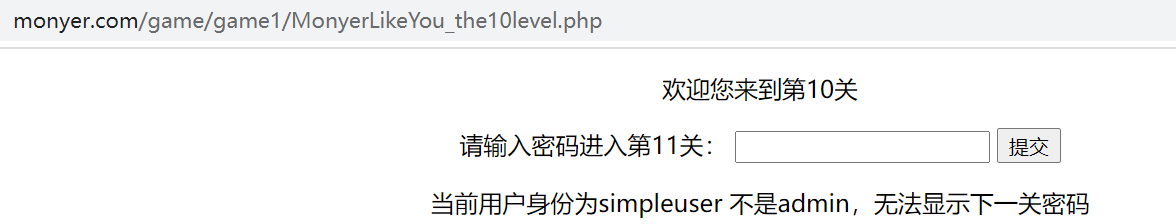
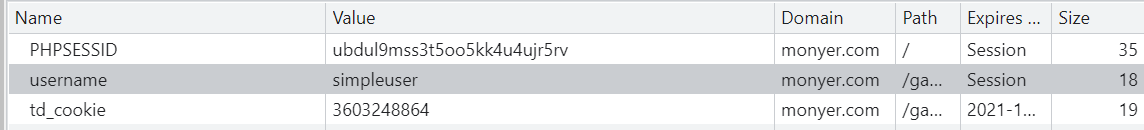
The 10th level prompts that the current user identity is simpleuser and needs to be changed to admin. The server identifies the user identity according to the cookie. On the console, it is found that there is a username field in the cookie, which is modified to admin. The password obtained by refreshing is doyouknow. Submit to the 11th level
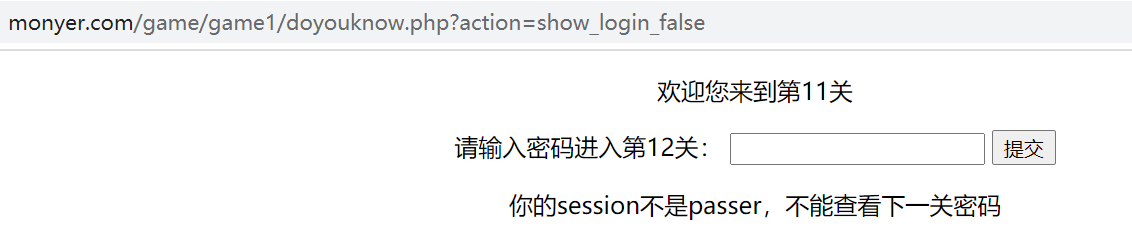
The 11th level prompts that the session needs to be changed to pass. The session is on the server side. We can't tamper with it by modifying the local file, but a new parameter is added to the URL: show_login_false, modified to show_login_true, the requested password is smartboy, submit and enter level 12
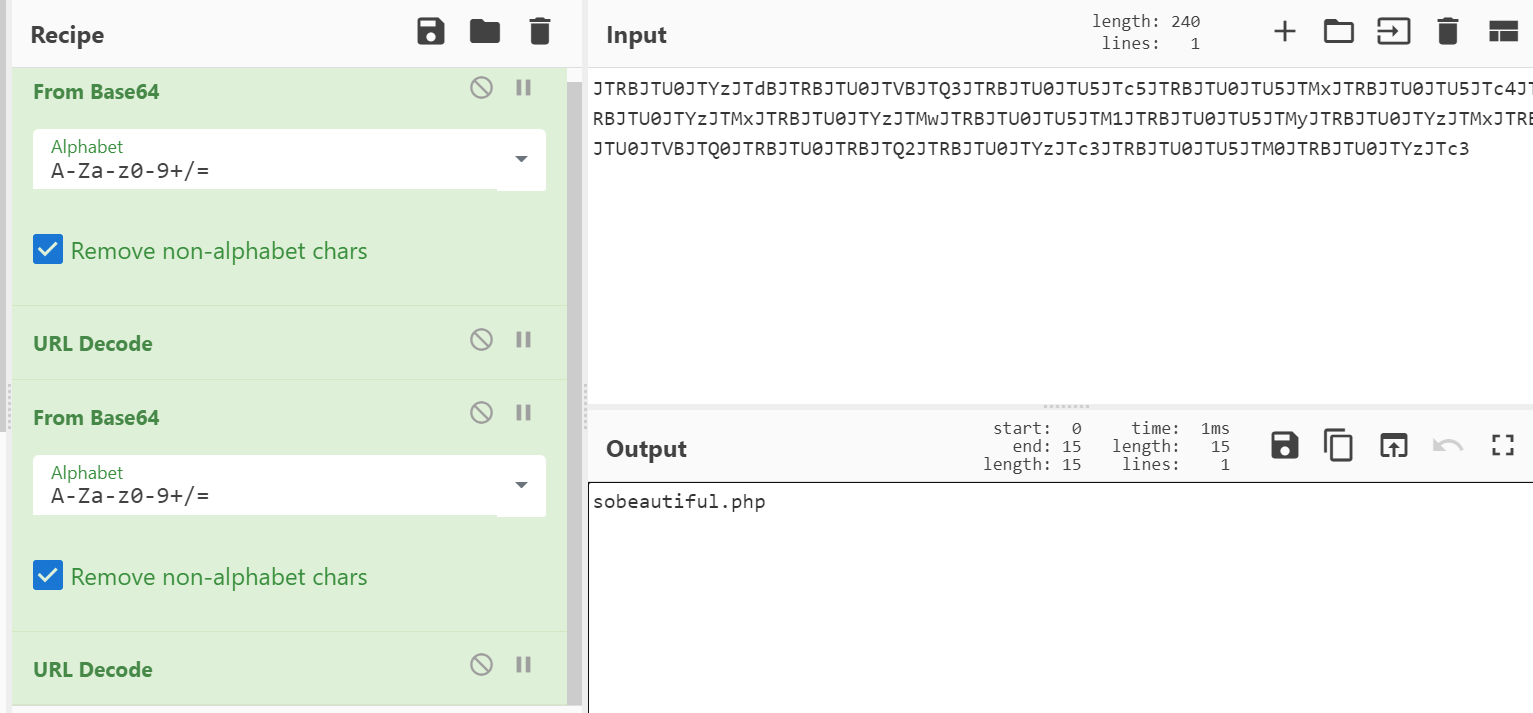
The page of level 12 prompts the encrypted ciphertext. Use CyberChef to decode it. After base64 and URL decoding twice, sobeautiful.php is obtained. This is the URL of level 13. Direct access will report an error. We need to jump from level 12 to level 13
Try to submit the password. The page will display the input on the web page. Consider XSS to generate the 13th hyperlink and click jump
payload is < a href = "sobeautiful. PHP" > 123</a>
JTRBJTU0JTYzJTdBJTRBJTU0JTVBJTQ3JTRBJTU0JTU5JTc5JTRBJTU0JTU5JTMxJTRBJTU0JTU5JTc4JTRBJTU0JTYzJTMxJTRBJTU0JTYzJTMwJTRBJTU0JTU5JTM1JTRBJTU0JTU5JTMyJTRBJTU0JTYzJTMxJTRBJTU0JTVBJTQ0JTRBJTU0JTRBJTQ2JTRBJTU0JTYzJTc3JTRBJTU0JTU5JTM0JTRBJTU0JTYzJTc3
Enter level 13, view the page source code, find the SQL statement in the comments, log in with the universal password 1 'or 1 = 1 -- to get the next level password whatyouneverknow, and submit to level 14
<!--
dim connect
Response.Expires=0 'System database connection
Set connect=Server.CreateObject("ADODB.Connection")
connect.Open "Provider=Microsoft.Jet.OLEDB.4.0;Data Source=" & server.MapPath("/Database.mdb") & ";Mode=ReadWrite|Share Deny None;Persist Security Info=False"
set rss=server.createobject("adodb.recordset")
sqlstr="select password,pwd from [user] where pwd='"&request("pwd")&"'"
rss.open sqlstr,connect,1,1
if rss.bof and rss.eof then
response.write("Password error")
else
response.write(rss("password"))
end if
rss.close
set rss=nothing
connect.close
set connect=nothing
-->
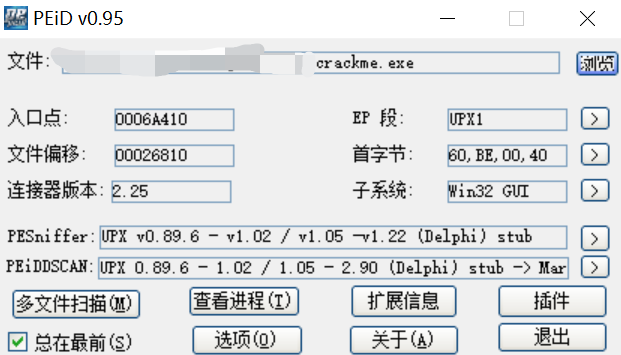
The 14th pass prompts a registration code program. Use the PEiD tool to check the shell and find the UPX shell. Use upx -d crackme.exe on kali to unpack. Use OllyDbg to open the shelled program, find the special string, find the registration code, get the password ipasscrackme, submit it and enter the bottom of the pass successfully