Cisco SD-WAN
Cisco SD-WAN four plane, four component
Management plane -- vManage; Provides a highly visual dashboard that simplifies network operations. It provides centralized configuration, management, operation and monitoring throughout the SD-WAN architecture
Layout plane -- vBond; The coordinator is mainly responsible for coordinating the control connection between management plane, control plane and data plane; Mainly responsible for authorized connection
Control plane -- vSmart; Responsible for routing and control, providing routing strategy, QOS strategy, traffic engineering, etc; There is an OMP protocol (upper management protocol) between vSmart and all vdges, which provides central policies and is responsible for implementing policies
Data plane -- vdge; Responsible for data forwarding, generating routing, and supporting OSPF, BGP and VRRP
VPN
VPNs in SD-WAN
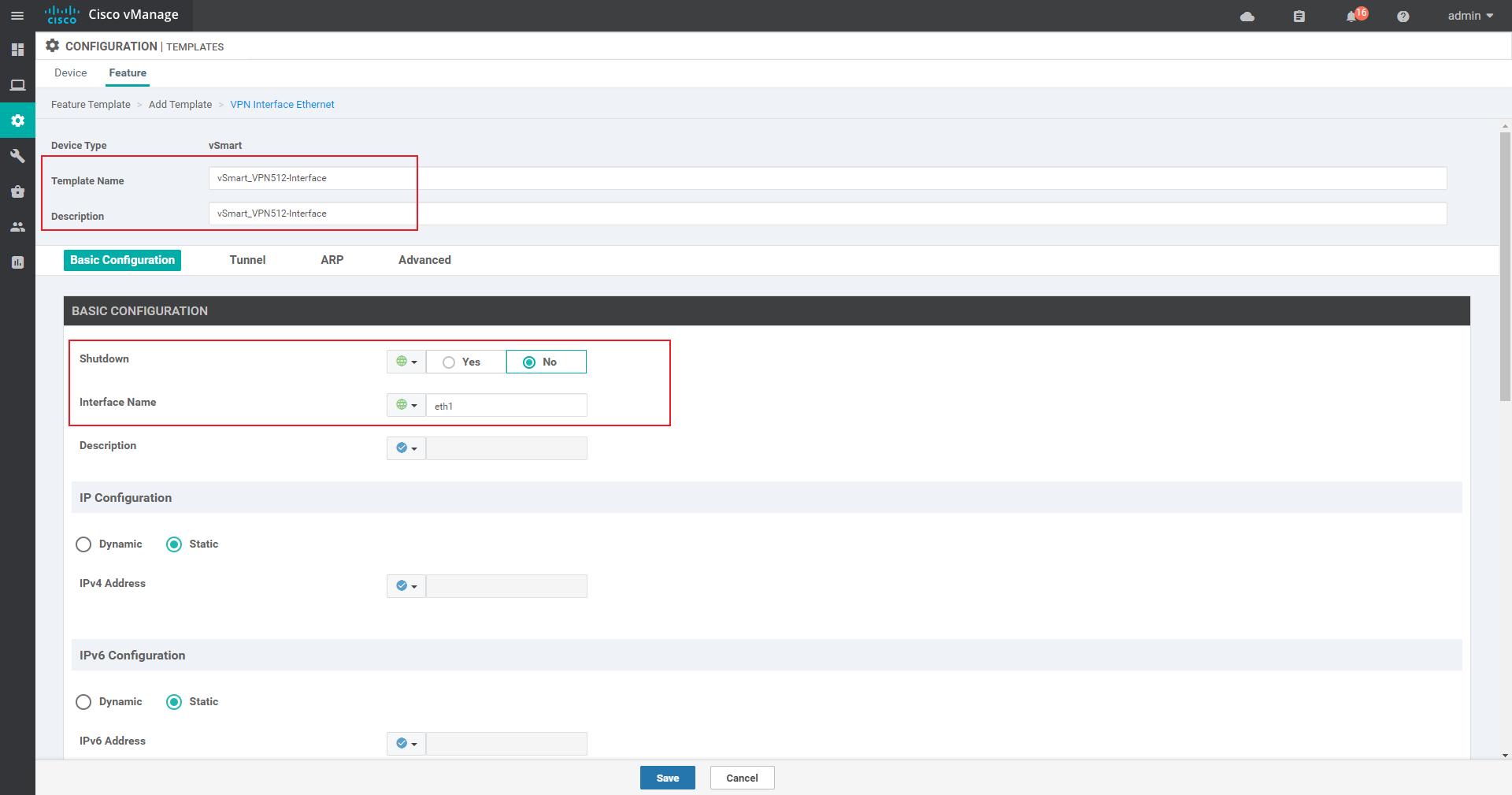
VPN 512 Mainly used for network management (fixed)
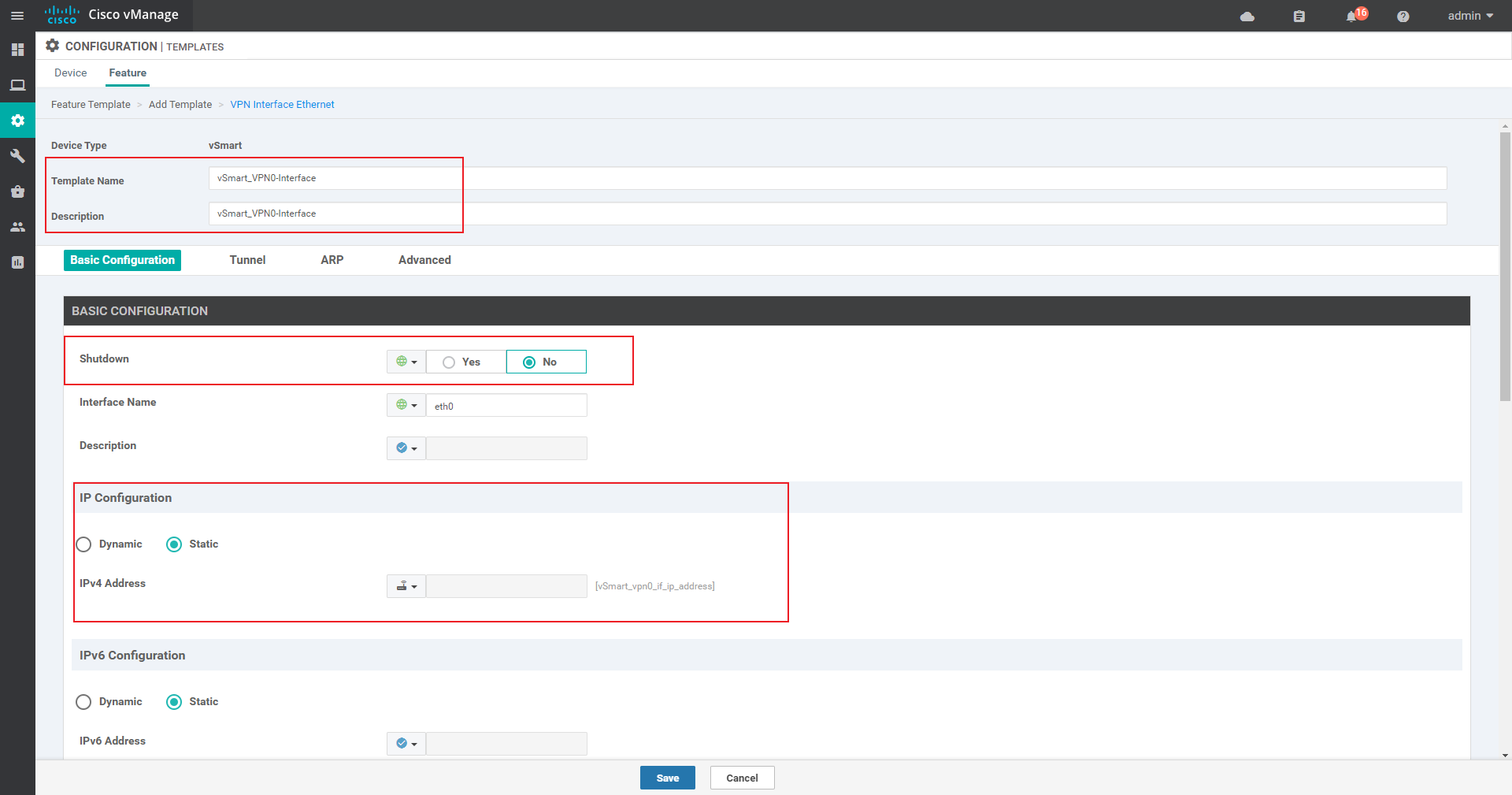
VPN 0 Mainly used for transmission side (fixed)
VPN 1-511 It is mainly used for business VPN
Current demand
The loopback interface of switches in the site can be interconnected,
Environment topology
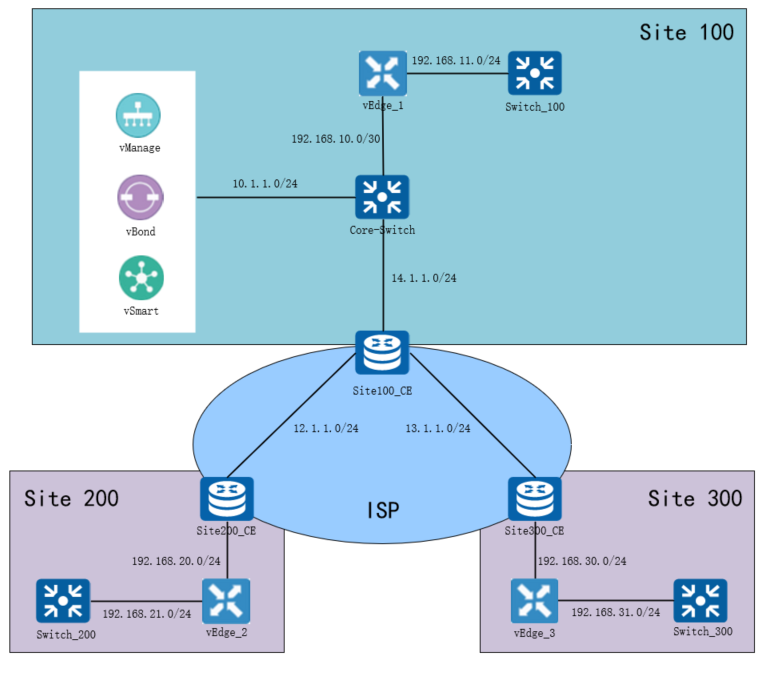
The environment is only used for experiments, not the real environment;
1. Equipment online
1.1 vManage configuration
vmanage(config)# system vmanage(config-system)# host-name vmanage vmanage(config-system)# system-ip 100.1.1.1 vmanage(config-system)# site-id 100 vmanage(config-system)# organization-name alex.com vmanage(config-system)# vbond 10.1.1.2 vmanage(config-system)# commit Commit complete. vmanage(config-system)# exit vmanage(config)# vpn 0 vmanage(config-vpn-0)# interface eth0 vmanage(config-interface-eth0)# ip address 10.1.1.1/24 vmanage(config-interface-eth0)# no shutdown vmanage(config-interface-eth0)# exit vmanage(config-vpn-0)# ip route 0.0.0.0/0 10.1.1.254 vmanage(config-vpn-0)# exit vmanage(config)# vpn 512 vmanage(config-vpn-512)# interface eth1 vmanage(config-interface-eth1)# no shutdown vmanage(config-interface-eth1)# ip address 172.16.30.155/16 vmanage(config-interface-eth1)# exit vmanage(config-vpn-512)# ip route 0.0.0.0/0 172.16.30.254 vmanage(config-vpn-512)# commit Commit complete. vmanage(config-vpn-512)# end
1.2 vBond configuration
vedge(config)# system vedge(config-system)# host-name vbond vedge(config-system)# system-ip 100.1.1.2 vedge(config-system)# site-id 100 vedge(config-system)# organization-name alex.com vedge(config-system)# vbond 10.1.1.2 local vbond-only vedge(config-system)# commit Commit complete. vbond(config-system)# exit vbond(config)# vpn 0 vbond(config-vpn-0)# interface ge0/0 vbond(config-interface-ge0/0)# no shutdown vbond(config-interface-ge0/0)# no tunnel-interface vbond(config-interface-ge0/0)# ip address 10.1.1.2/24 vbond(config-interface-ge0/0)# exit vbond(config-vpn-0)# ip route 0.0.0.0/0 10.1.1.254 vbond(config-vpn-0)# commit Commit complete. vbond(config-vpn-0)#
1.3 vSmart configuration
vsmart(config)# system vsmart(config-system)# host-name vsmart vsmart(config-system)# system-ip 100.1.1.3 vsmart(config-system)# site-id 100 vsmart(config-system)# vbond 10.1.1.2 vsmart(config-system)# organization-name alex.com vsmart(config-system)# commit Commit complete. vsmart(config-system)# exit vsmart(config)# vpn 0 vsmart(config-vpn-0)# interface eth0 vsmart(config-interface-eth0)# no shutdown vsmart(config-interface-eth0)# ip address 10.1.1.3/24 vsmart(config-interface-eth0)# exit vsmart(config-vpn-0)# ip route 0.0.0.0/0 10.1.1.254 vsmart(config-vpn-0)# commit Commit complete. vsmart(config-vpn-0)# vsmart(config-vpn-0)# end
1.4 vdge configuration
vEdge1:
vedge(config)# system vedge(config-system)# host-name vEdge1 vedge(config-system)# system-ip 100.1.1.4 vedge(config-system)# site-id 100 vedge(config-system)# organization-name alex.com vedge(config-system)# vbond 10.1.1.2 vedge(config-system)# commit Commit complete. vEdge1(config-system)# exit vEdge1(config)# vpn 0 vEdge1(config-vpn-0)# interface ge0/0 vEdge1(config-interface-ge0/0)# no shutdown vEdge1(config-interface-ge0/0)# no tunnel-interface vEdge1(config-interface-ge0/0)# ip address 192.168.10.2/30 vEdge1(config-interface-ge0/0)# exit vEdge1(config-vpn-0)# ip route 0.0.0.0/0 192.168.10.1 vEdge1(config-interface-ge0/0)# commit Commit complete. vEdge1(config-interface-ge0/0)#
vEdge2:
vedge(config)# system vedge(config-system)# host-name vEdge2 vedge(config-system)# system-ip 102.1.1.1 vedge(config-system)# site-id 200 vedge(config-system)# organization-name alex.com vedge(config-system)# vbond 10.1.1.2 vedge(config-system)# commit Commit complete. vEdge2(config-system)# exit vEdge2(config)# vpn 0 vEdge2(config-vpn-0)# interface ge0/0 vEdge2(config-interface-ge0/0)# no shutdown vEdge2(config-interface-ge0/0)# no tunnel-interface vEdge2(config-interface-ge0/0)# ip address 192.168.20.1/24 vEdge2(config-interface-ge0/0)# exit vEdge2(config-vpn-0)# ip route 0.0.0.0/0 192.168.20.254 vEdge2(config-vpn-0)# commit Commit complete.
vEdge3:
vedge(config)# system vedge(config-system)# host-name vEdge3 vedge(config-system)# system-ip 103.1.1.1 vedge(config-system)# site-id 300 vedge(config-system)# organization-name alex.com vedge(config-system)# vbond 10.1.1.2 vedge(config-system)# commit Commit complete. vEdge3(config-system)# exit vEdge3(config)# vpn 0 vEdge3(config-vpn-0)# interface ge0/0 vEdge3(config-interface-ge0/0)# no shutdown vEdge3(config-interface-ge0/0)# no tunnel-interface vEdge3(config-interface-ge0/0)# ip address 192.168.30.1/24 vEdge3(config-interface-ge0/0)# exit vEdge3(config-vpn-0)# ip route 0.0.0.0/0 192.168.30.254 vEdge3(config-vpn-0)# vEdge3(config-vpn-0)# vEdge3(config-vpn-0)# commit Commit complete.
1.5 core switch configuration
interface Ethernet0/0 switchport access vlan 30 switchport mode access ! interface Ethernet0/1 switchport access vlan 10 switchport mode access ! interface Ethernet0/2 switchport access vlan 20 switchport mode access interface Vlan10 ip address 10.1.1.254 255.255.255.0 ! interface Vlan20 ip address 14.1.1.4 255.255.255.0 ip ospf network point-to-point ip ospf 1 area 0 ! interface Vlan30 ip address 192.168.10.1 255.255.255.252 Ip ospf 1 area 0 ! router ospf 1 router-id 4.4.4.4 network 10.1.1.0 0.0.0.255 area 0
1.6 ISP configuration
Site100_CE:
vrf definition alex rd 1:1 route-target export 2:2 route-target import 2:2 ! address-family ipv4 exit-address-family ! interface Loopback0 ip address 1.1.1.1 255.255.255.255 ip ospf 6 area 0 ! interface Ethernet0/0 ip address 12.1.1.1 255.255.255.0 ip ospf network point-to-point ip ospf 6 area 0 duplex auto mpls bgp forwarding mpls ip ! interface Ethernet0/1 ip address 13.1.1.1 255.255.255.0 ip ospf network point-to-point ip ospf 6 area 0 duplex auto mpls bgp forwarding mpls ip ! interface Ethernet0/2 vrf forwarding alex ip address 14.1.1.1 255.255.255.0 ip ospf network point-to-point ip ospf 1 area 0 duplex auto ! router ospf 1 vrf alex redistribute bgp 100 subnets ! router ospf 6 router-id 1.1.1.1 ! router bgp 100 bgp log-neighbor-changes no bgp default ipv4-unicast neighbor 2.2.2.2 remote-as 100 neighbor 2.2.2.2 update-source Loopback0 neighbor 3.3.3.3 remote-as 100 ! address-family vpnv4 neighbor 2.2.2.2 activate neighbor 2.2.2.2 send-community extended neighbor 2.2.2.2 route-reflector-client neighbor 3.3.3.3 activate neighbor 3.3.3.3 send-community extended neighbor 3.3.3.3 route-reflector-client exit-address-family ! address-family ipv4 vrf alex redistribute ospf 1 exit-address-family
Site200_CE:
vrf definition alex rd 1:1 route-target export 2:2 route-target import 2:2 ! address-family ipv4 exit-address-family ! interface Loopback0 ip address 2.2.2.2 255.255.255.255 ip ospf 6 area 0 ! interface Ethernet0/0 ip address 12.1.1.2 255.255.255.0 ip ospf network point-to-point ip ospf 6 area 0 duplex auto mpls bgp forwarding mpls ip ! interface Ethernet0/1 vrf forwarding alex ip address 192.168.20.254 255.255.255.0 duplex auto ! router ospf 6 router-id 2.2.2.2 ! router bgp 100 bgp log-neighbor-changes no bgp default ipv4-unicast neighbor 1.1.1.1 remote-as 100 neighbor 1.1.1.1 update-source Loopback0 ! address-family vpnv4 neighbor 1.1.1.1 activate neighbor 1.1.1.1 send-community extended exit-address-family ! address-family ipv4 vrf alex redistribute connected exit-address-family
Site300_CE:
vrf definition alex rd 1:1 route-target export 2:2 route-target import 2:2 ! address-family ipv4 exit-address-family ! interface Loopback0 ip address 3.3.3.3 255.255.255.255 ip ospf 6 area 0 ! interface Ethernet0/0 vrf forwarding alex ip address 192.168.30.254 255.255.255.0 duplex auto ! interface Ethernet0/1 ip address 13.1.1.3 255.255.255.0 ip ospf network point-to-point ip ospf 6 area 0 duplex auto mpls bgp forwarding mpls ip ! router ospf 6 router-id 3.3.3.3 ! router bgp 100 bgp log-neighbor-changes no bgp default ipv4-unicast neighbor 1.1.1.1 remote-as 100 neighbor 1.1.1.1 update-source Loopback0 ! address-family vpnv4 neighbor 1.1.1.1 activate neighbor 1.1.1.1 send-community extended exit-address-family ! address-family ipv4 vrf alex redistribute connected exit-address-family
1.7 certificate processing between devices (here, vManage's Openssl is used to sign and issue certificates)
1.7.1 generate root certificate
vmanage# vshell vmanage:~$ openssl genrsa -out ROOTCA.key 2048 Generating RSA private key, 2048 bit long modulus ................+++ ....+++ e is 65537 (0x10001) vmanage:~$ vmanage:~$ openssl req -x509 -new -nodes -key ROOTCA.key -sha256 -days 1024\ > -subj "/C=CN/ST=HB/L=WH/O=alex.com/CN=ca.vmanage" \ > -out ROOTCA.pem vmanage:~$ ls -l total 12 -rw-r--r-- 1 admin admin 1679 Sep 5 14:49 ROOTCA.key -rw-r--r-- 1 admin admin 1253 Sep 5 14:51 ROOTCA.pem -rw-r--r-- 1 admin admin 394 Sep 5 14:23 archive_id_rsa.pub vmanage:~$
1.7.2 delete the original root certificate and install a new root certificate on vManage, vBond, vSmart and vdge
vManage:
vmanage# request root-cert-chain uninstall Successfully uninstalled the root certificate chain vmanage# vmanage# request root-cert-chain install home/admin/ROOTCA.pem Uploading root-ca-cert-chain via VPN 0 Copying ... /home/admin/ROOTCA.pem via VPN 0 Successfully installed the root certificate chain vmanage#
vBond,vSmart,vEdge:
vbond# request root-cert-chain uninstall Successfully uninstalled the root certificate chain vbond# vbond# request root-cert-chain install scp://admin@10.1.1.1:/home/admin/ROOTCA.pem Uploading root-ca-cert-chain via VPN 0 Copying ... admin@10.1.1.1:/home/admin/ROOTCA.pem via VPN 0 Warning: Permanently added '10.1.1.1' (ECDSA) to the list of known hosts. viptela 16.2.11 admin@10.1.1.1's password: ROOTCA.pem 100% 1253 1.2KB/s 00:00 Successfully installed the root certificate chain vbond#
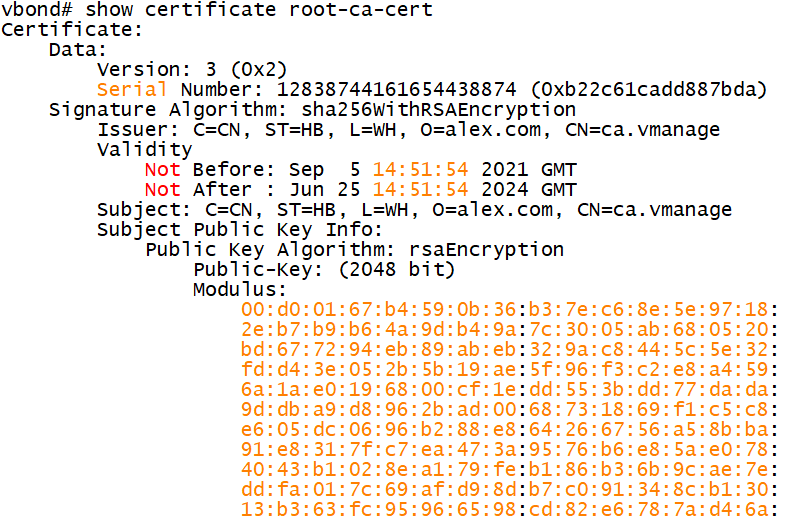
1.7.3 take vBond as an example to view the certificate
1.7.4 application and issuance of personal certificate
Generate certificate request
vManage:
vmanage# request csr upload home/admin/vmanage.csr Uploading CSR via VPN 0 Enter organization name : alex.com Re-enter organization name : alex.com Generating private/public pair and CSR for this vmanage device Generating CSR for this vmanage device ........[DONE] Copying ... /home/admin/vmanage.csr via VPN 0 CSR upload successful
vBond,vSmart,vEdge:
vEdge1# request csr upload scp://admin@10.1.1.1:/home/admin/vedge1.csr Uploading CSR via VPN 0 Enter organization-unit name : alex.com Re-enter organization-unit name : alex.com Generating private/public pair and CSR for this vedge device Generating CSR for this vedge device ........[DONE] Copying ... admin@10.1.1.1:/home/admin/vedge1.csr via VPN 0 Warning: Permanently added '10.1.1.1' (ECDSA) to the list of known hosts. viptela 16.2.11 admin@10.1.1.1's password: server.csr 100% 1212 32.2KB/s 00:00 CSR upload successful vEdge1#
Certificate issued:
vmanage# vshell vmanage:~$ ls -l total 36 -rw-r--r-- 1 admin admin 1679 Sep 5 14:49 ROOTCA.key -rw-r--r-- 1 admin admin 1253 Sep 5 14:51 ROOTCA.pem -rw-r--r-- 1 admin admin 394 Sep 5 15:19 archive_id_rsa.pub -rw-r--r-- 1 admin admin 1212 Sep 5 15:21 vbond.csr -rw-r--r-- 1 admin admin 1212 Sep 5 15:04 vedge1.csr -rw-r--r-- 1 admin admin 1212 Sep 5 15:05 vedge2.csr -rw-r--r-- 1 admin admin 1212 Sep 5 15:05 vedge3.csr -rw-r--r-- 1 root root 1216 Sep 5 15:03 vmanage.csr -rw-r--r-- 1 admin admin 1212 Sep 5 15:22 vsmart.csr vmanage:~$ vmanage:~$ openssl x509 -req -in vmanage.csr -CA ROOTCA.pem -CAkey ROOTCA.key -CAcreateserial -out vmanage.crt -days 500 -sha256 vmanage:~$ openssl x509 -req -in vbond.csr -CA ROOTCA.pem -CAkey ROOTCA.key -CAcreateserial -out vbond.crt -days 500 -sha256 vmanage:~$ openssl x509 -req -in vsmart.csr -CA ROOTCA.pem -CAkey ROOTCA.key -CAcreateserial -out vsmart.crt -days 500 -sha256 vmanage:~$ openssl x509 -req -in vedge1.csr -CA ROOTCA.pem -CAkey ROOTCA.key -CAcreateserial -out vedge1.crt -days 500 -sha256 vmanage:~$ openssl x509 -req -in vedge2.csr -CA ROOTCA.pem -CAkey ROOTCA.key -CAcreateserial -out vedge2.crt -days 500 -sha256 vmanage:~$ openssl x509 -req -in vedge3.csr -CA ROOTCA.pem -CAkey ROOTCA.key -CAcreateserial -out vedge3.crt -days 500 -sha256 vmanage:~$ vmanage:~$ vmanage:~$ ls -l total 64 -rw-r--r-- 1 admin admin 1679 Sep 5 14:49 ROOTCA.key -rw-r--r-- 1 admin admin 1253 Sep 5 14:51 ROOTCA.pem -rw-r--r-- 1 admin admin 17 Sep 5 15:25 ROOTCA.srl -rw-r--r-- 1 admin admin 394 Sep 5 15:19 archive_id_rsa.pub -rw-r--r-- 1 admin admin 1298 Sep 5 15:25 vbond.crt -rw-r--r-- 1 admin admin 1212 Sep 5 15:21 vbond.csr -rw-r--r-- 1 admin admin 1298 Sep 5 15:25 vedge1.crt -rw-r--r-- 1 admin admin 1212 Sep 5 15:04 vedge1.csr -rw-r--r-- 1 admin admin 1298 Sep 5 15:25 vedge2.crt -rw-r--r-- 1 admin admin 1212 Sep 5 15:05 vedge2.csr -rw-r--r-- 1 admin admin 1298 Sep 5 15:25 vedge3.crt -rw-r--r-- 1 admin admin 1212 Sep 5 15:05 vedge3.csr -rw-r--r-- 1 admin admin 1302 Sep 5 15:25 vmanage.crt -rw-r--r-- 1 root root 1216 Sep 5 15:03 vmanage.csr -rw-r--r-- 1 admin admin 1298 Sep 5 15:25 vsmart.crt -rw-r--r-- 1 admin admin 1212 Sep 5 15:22 vsmart.csr vmanage:~$
Installation certificate:
vManage:
vmanage# vmanage# request certificate install home/admin/vmanage.crt Installing certificate via VPN 0 Copying ... /home/admin/vmanage.crt via VPN 0 Successfully installed the certificate vmanage#
vBond,vSmart,vEdge:
vbond# vbond# request certificate install scp://admin@10.1.1.1:/home/admin/vbond.crt Installing certificate via VPN 0 Copying ... admin@10.1.1.1:/home/admin/vbond.crt via VPN 0 Warning: Permanently added '10.1.1.1' (ECDSA) to the list of known hosts. viptela 16.2.11 admin@10.1.1.1's password: vbond.crt 100% 1298 1.3KB/s 00:00 Successfully installed the certificate vbond#
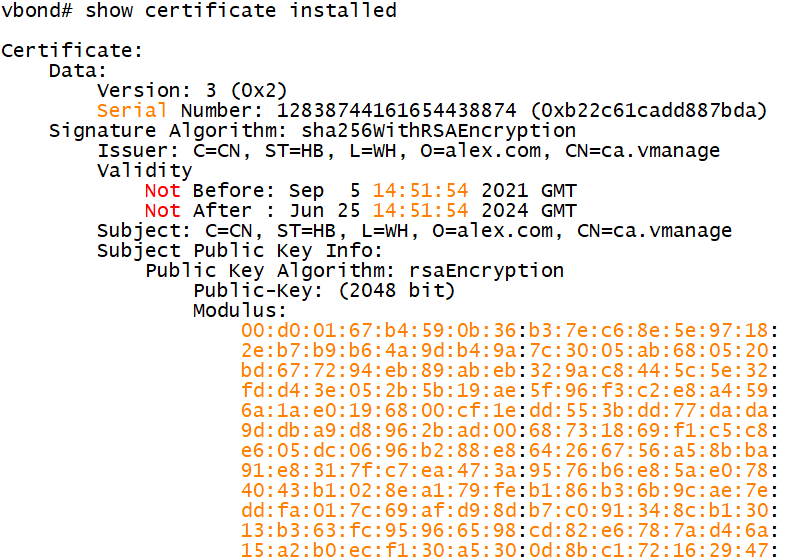
1.7.5 take vBond as an example to view the certificate
1.8 add vBond, vSmart and vdge devices to vmanage
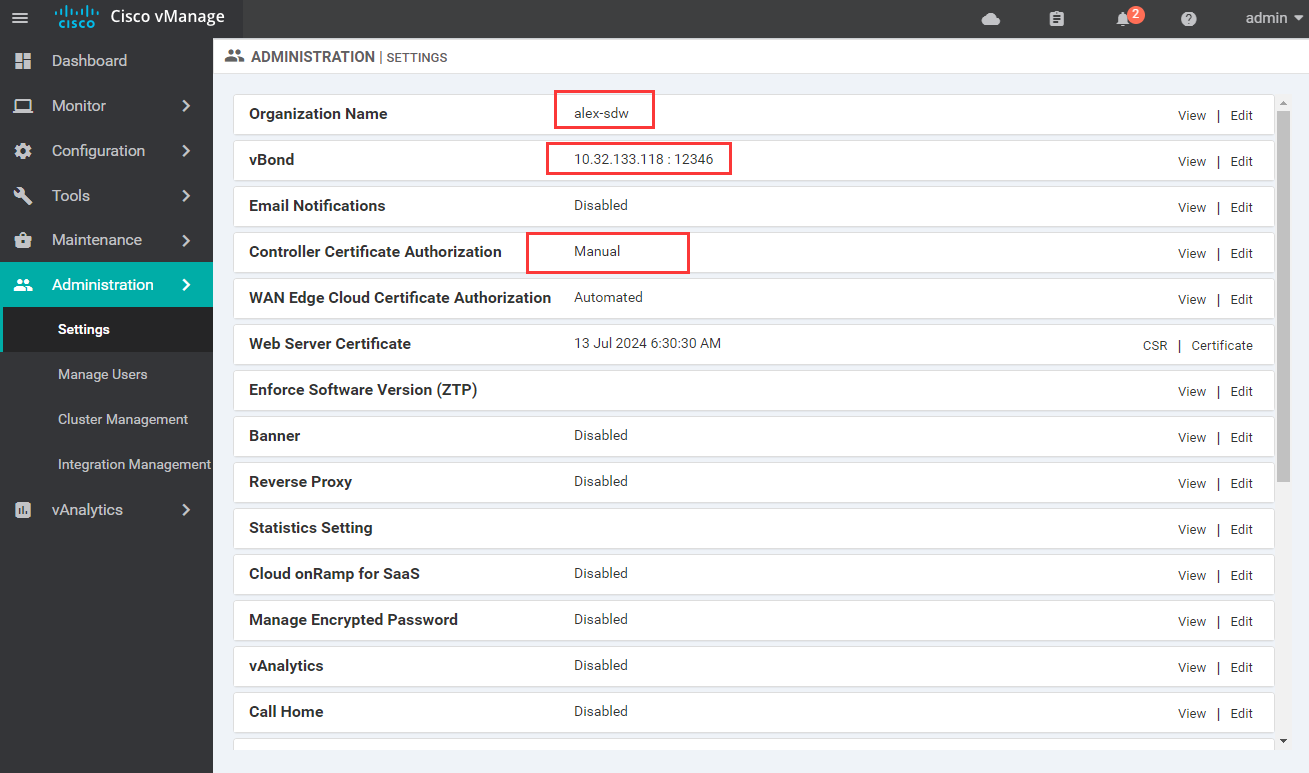
1.8.1 log in to vManage and configure setting (the or name here is inconsistent with the previous setting because of the environment change)
1.8.2 add vBond and vSmart (note that CSR should be checked because we have self signed the certificate)
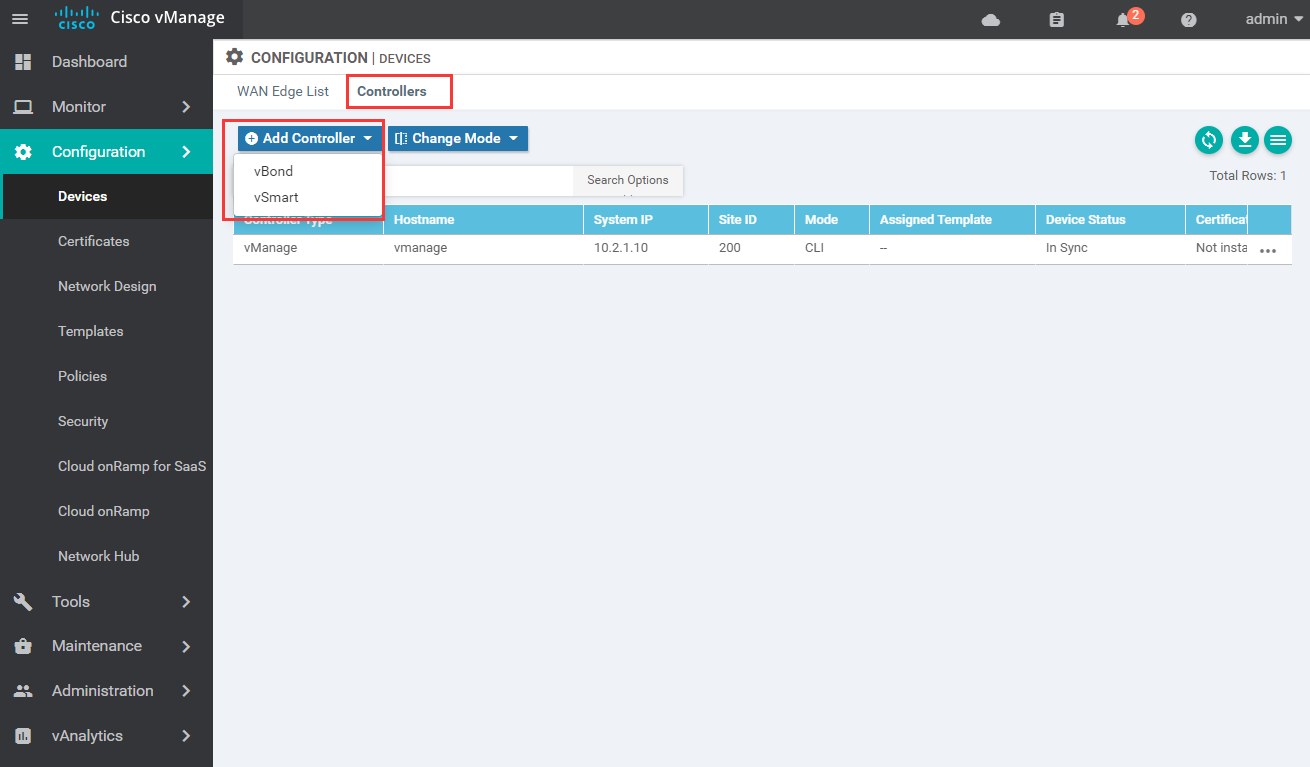
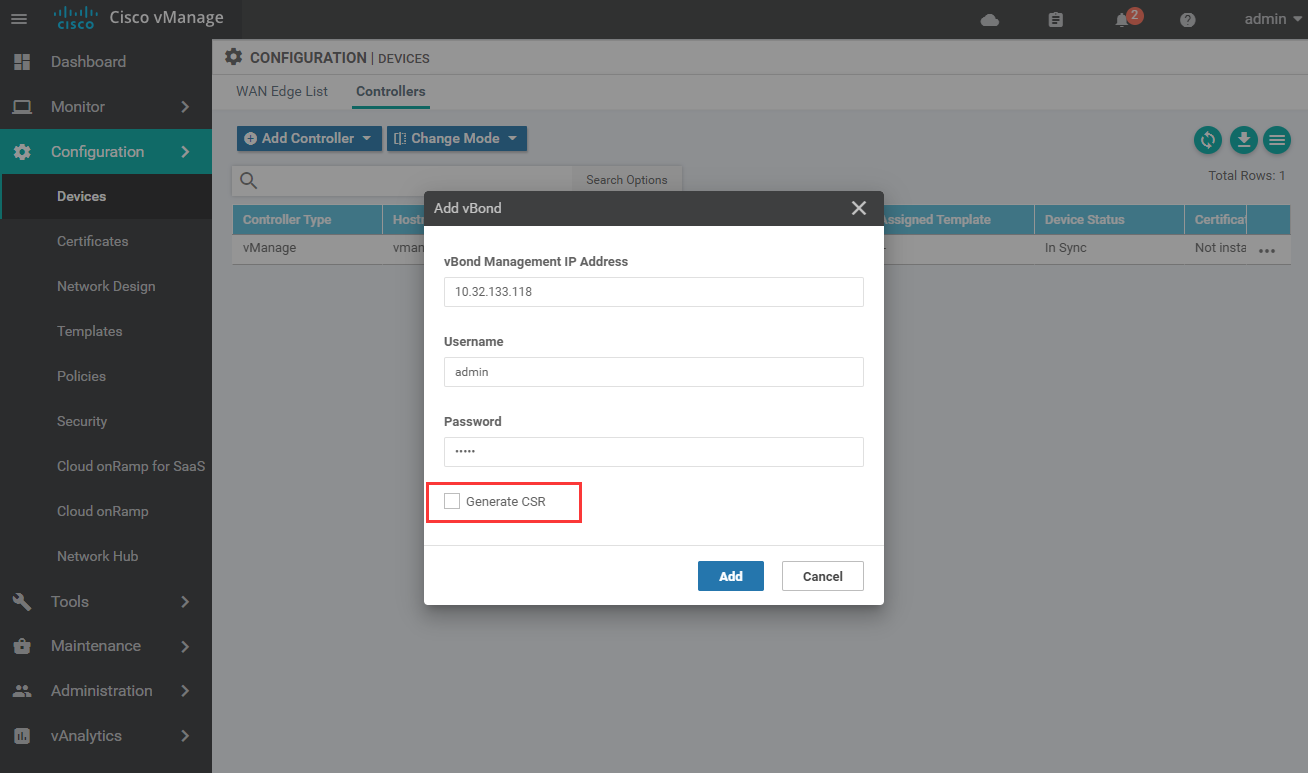
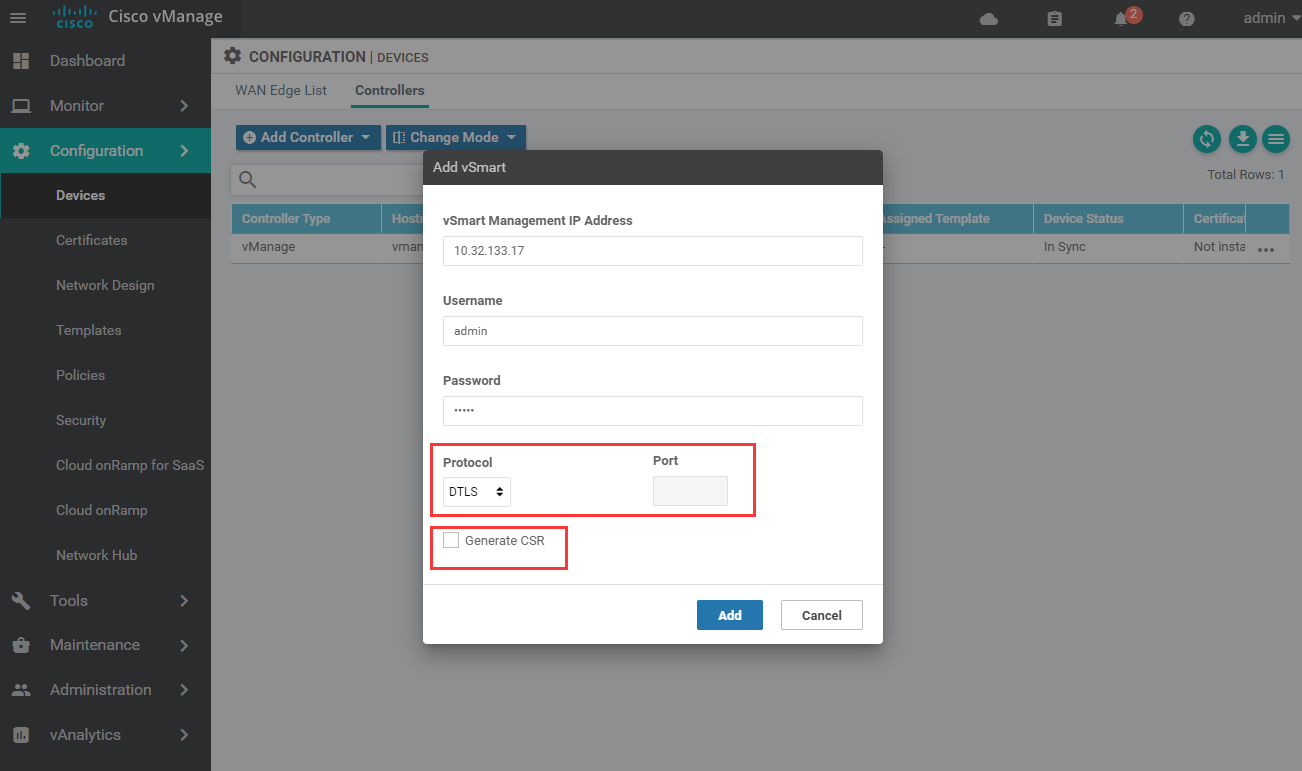
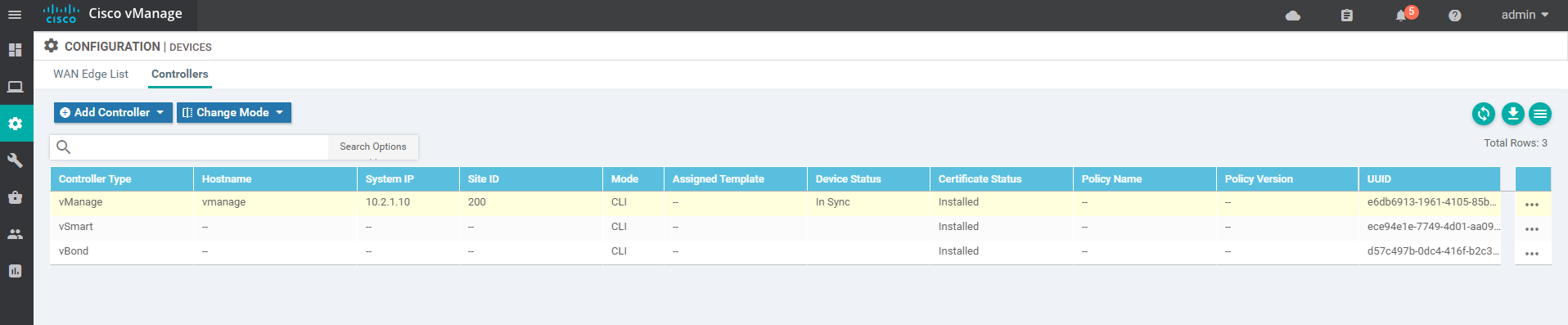
1.8.3 after adding, push the certificate to vBond
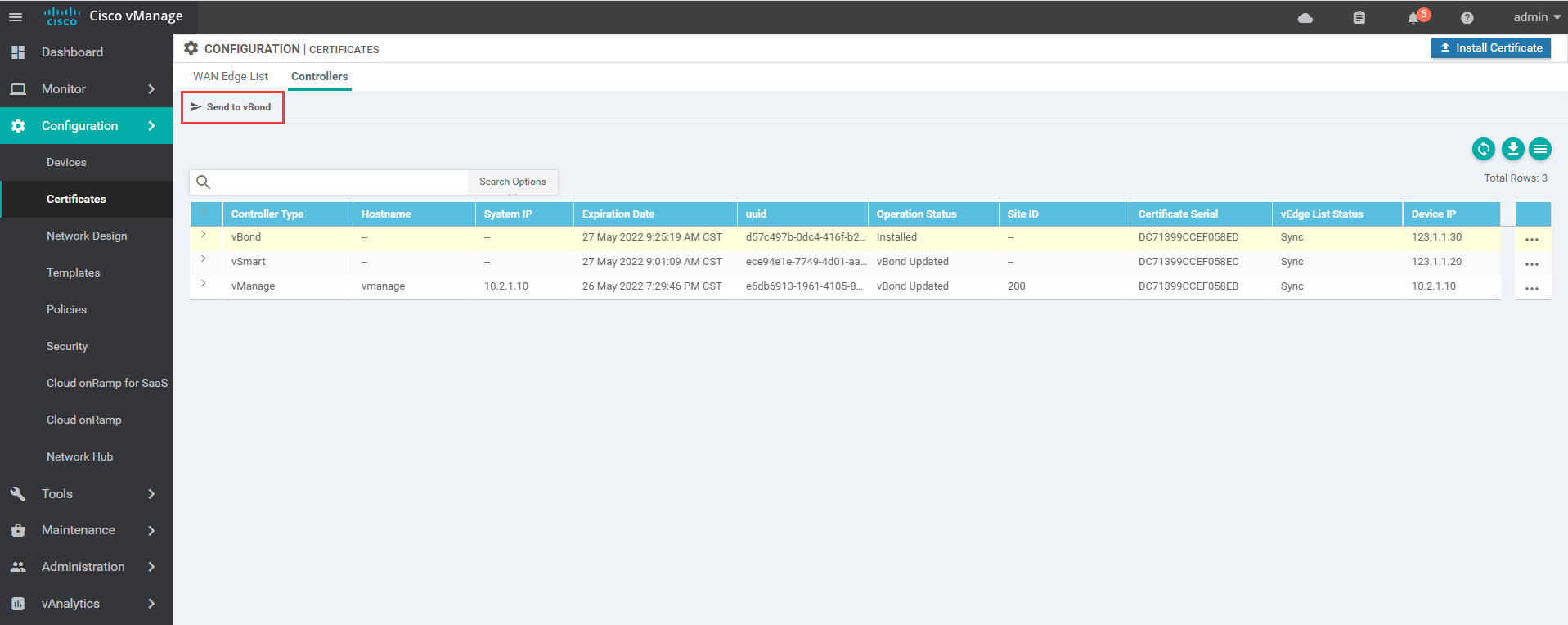
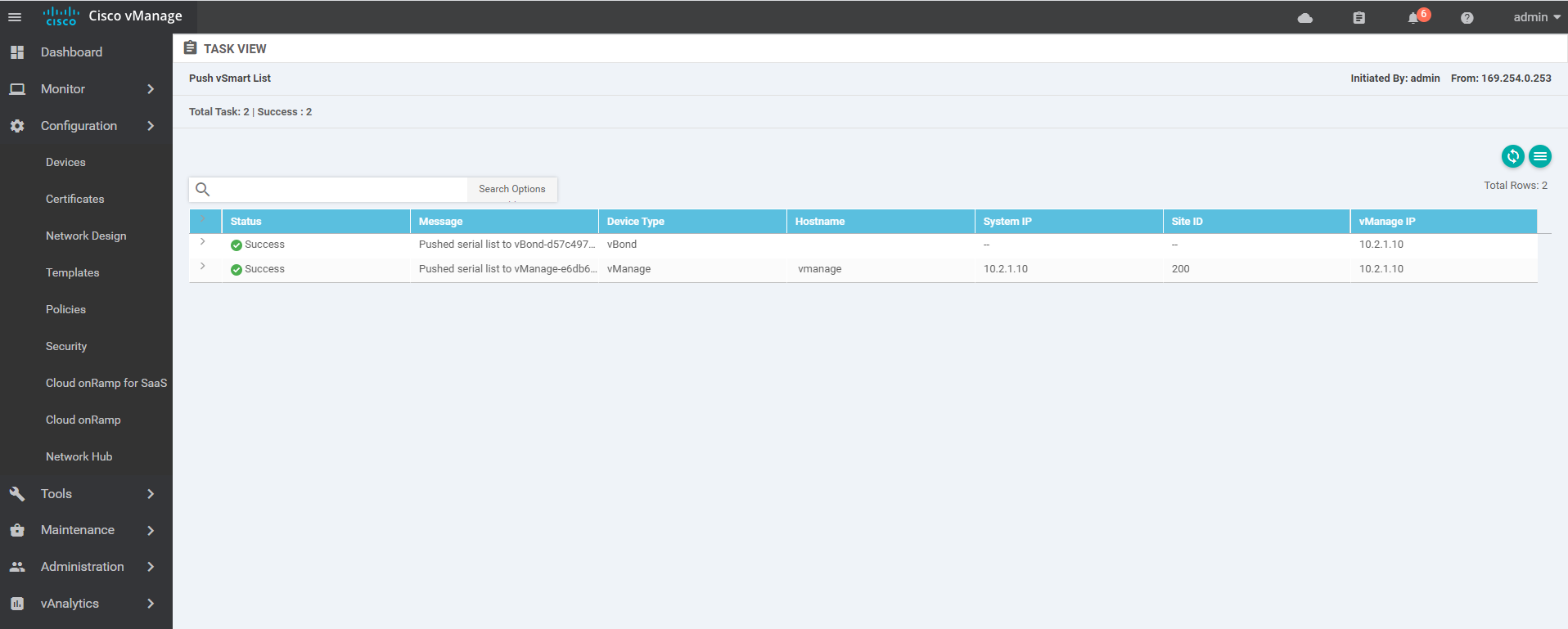
1.8.4 import of vdge authorization file
There is no demonstration here. Cisco Smart account application is required to obtain a whitelist file
The official link is as follows:
https://www.cisco.com/c/en/us/td/docs/solutions/CVD/SDWAN/cisco-sdwan-design-guide.html
https://www.cisco.com/c/dam/en/us/td/docs/solutions/CVD/SDWAN/SD-WAN-End-to-End-Deployment-Guide.pdf
1.9 at this time, vbond, vSmart and vEdge are all online in vManage
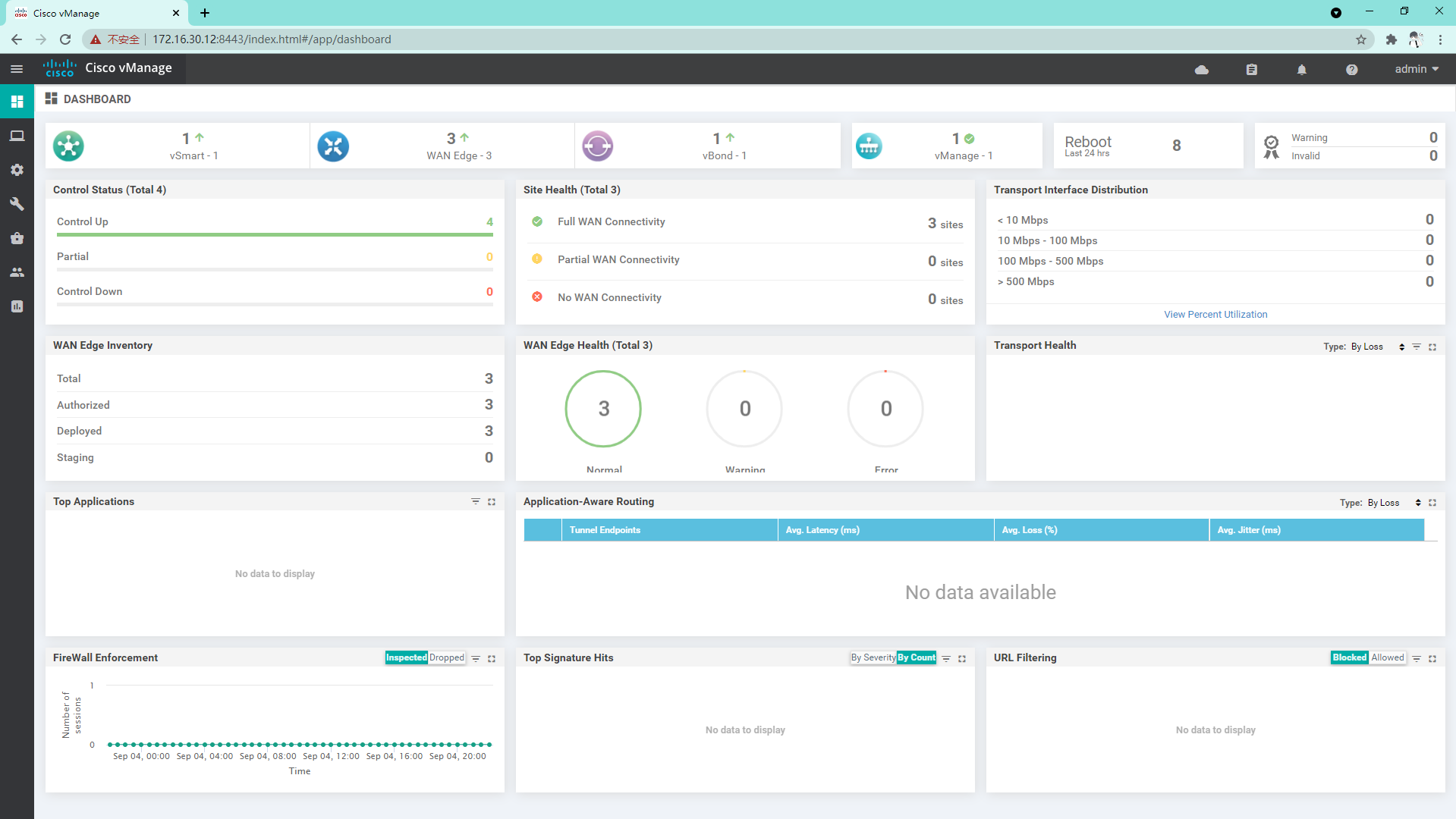
2. Control connection
2.1 viewing control connections between devices
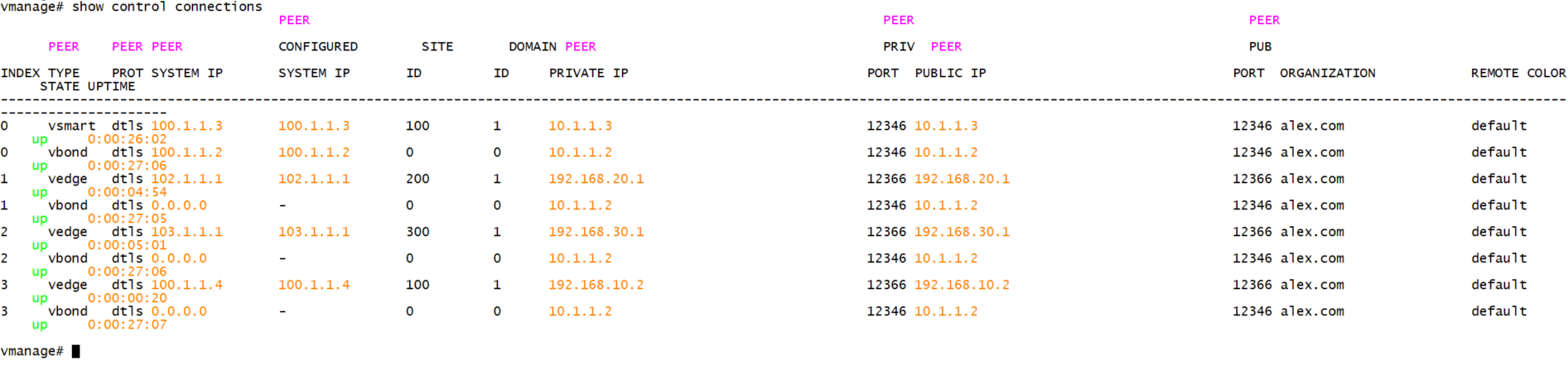
3. Equipment information
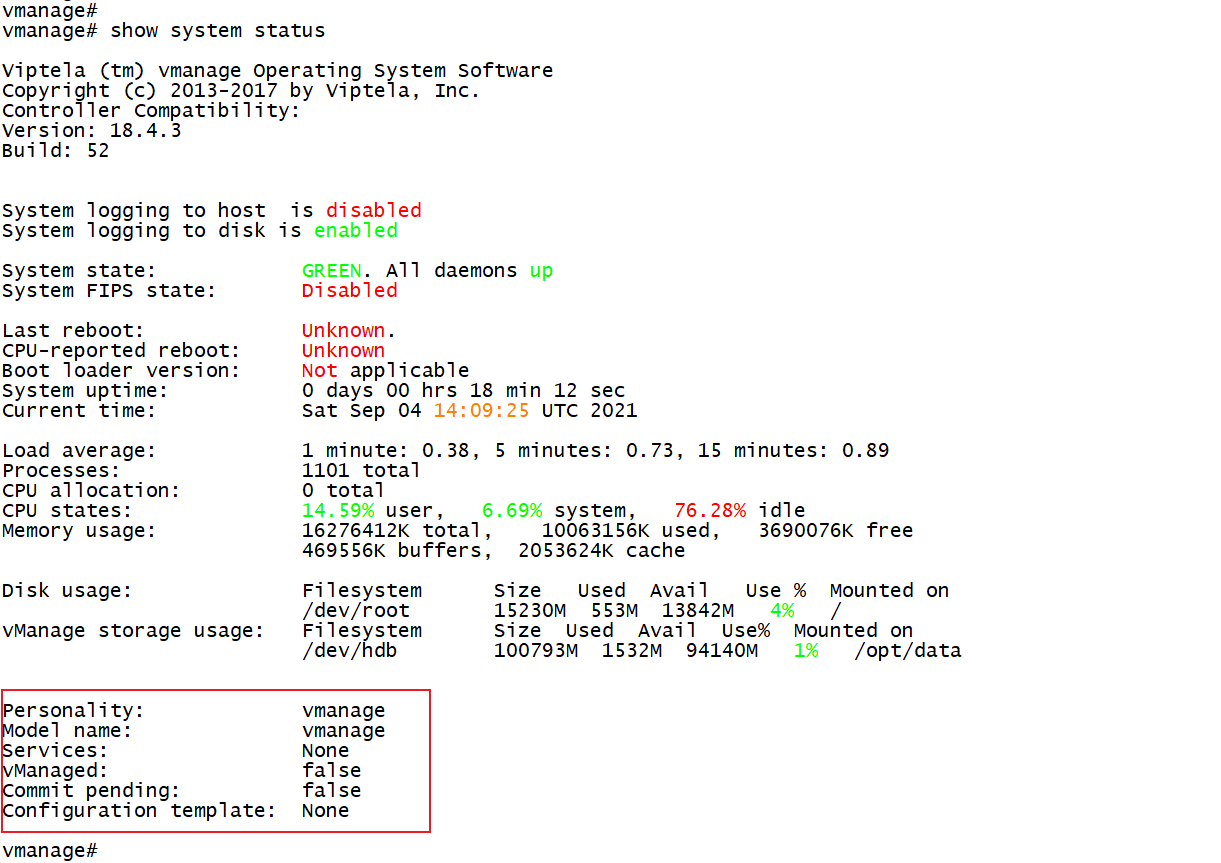
3.1 take vManage as an example to view the system information. At this time, the equipment is not managed by vManage, including vManage itself
4. Pipe receiving equipment
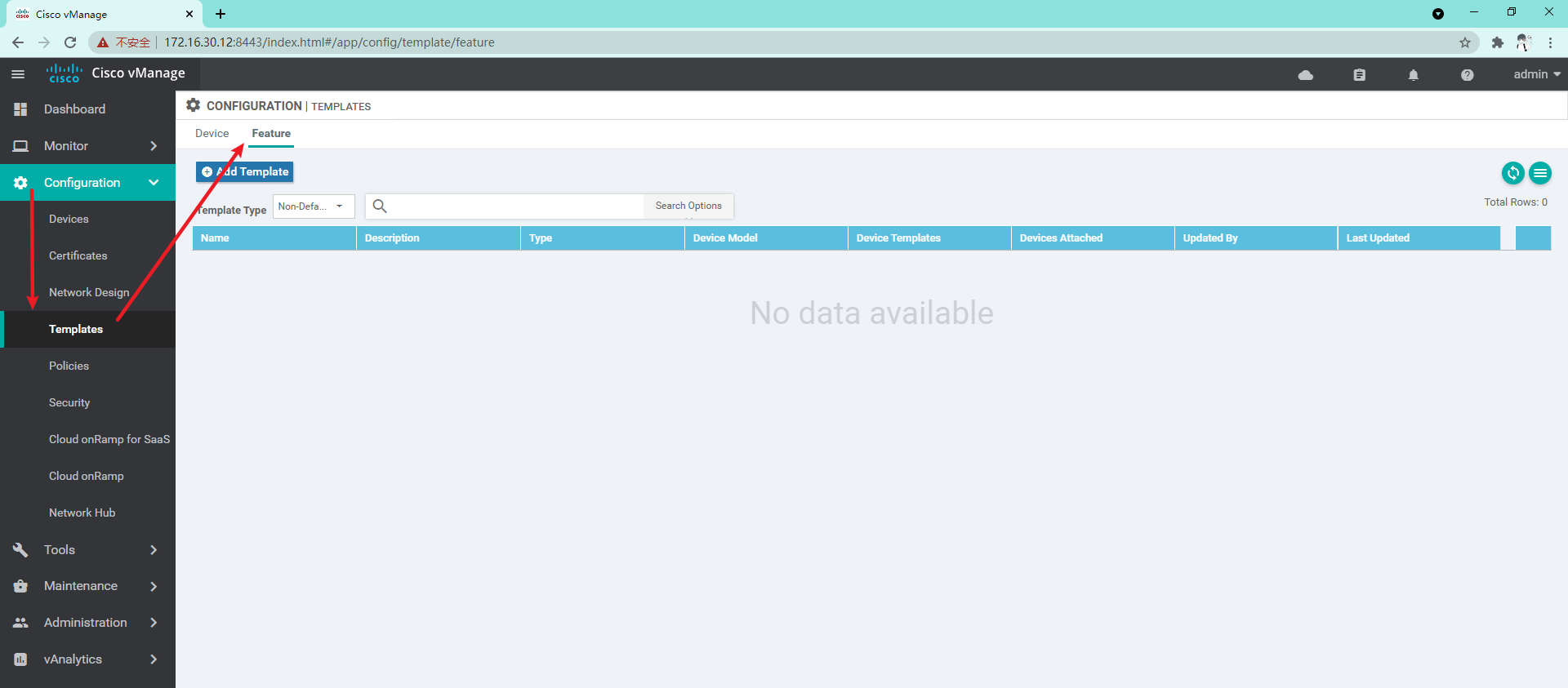
4.1 pipe vManage
4.1.1 create Feature template, including system template, VPN 0 template, VPN 512 template and interface template
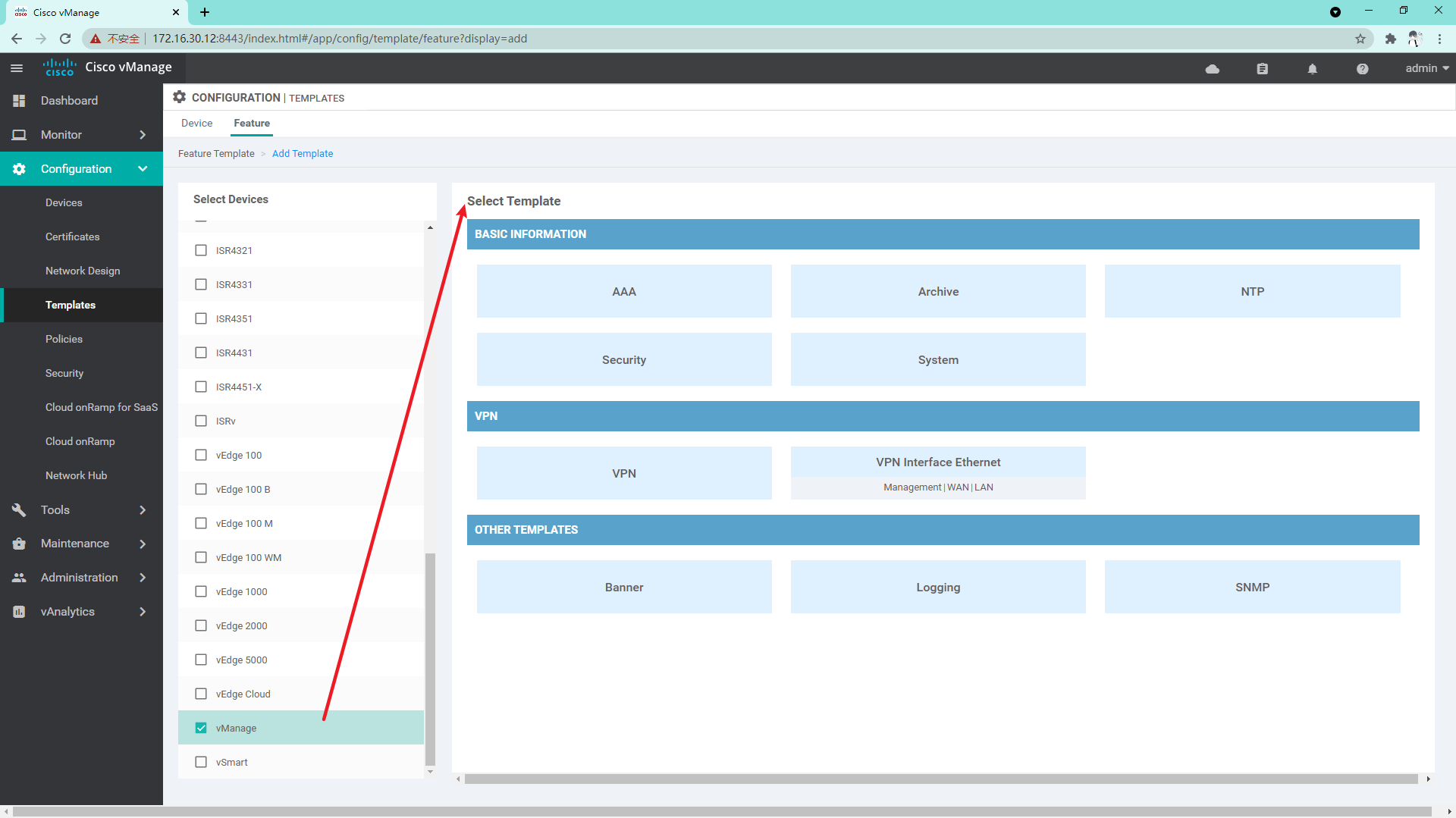
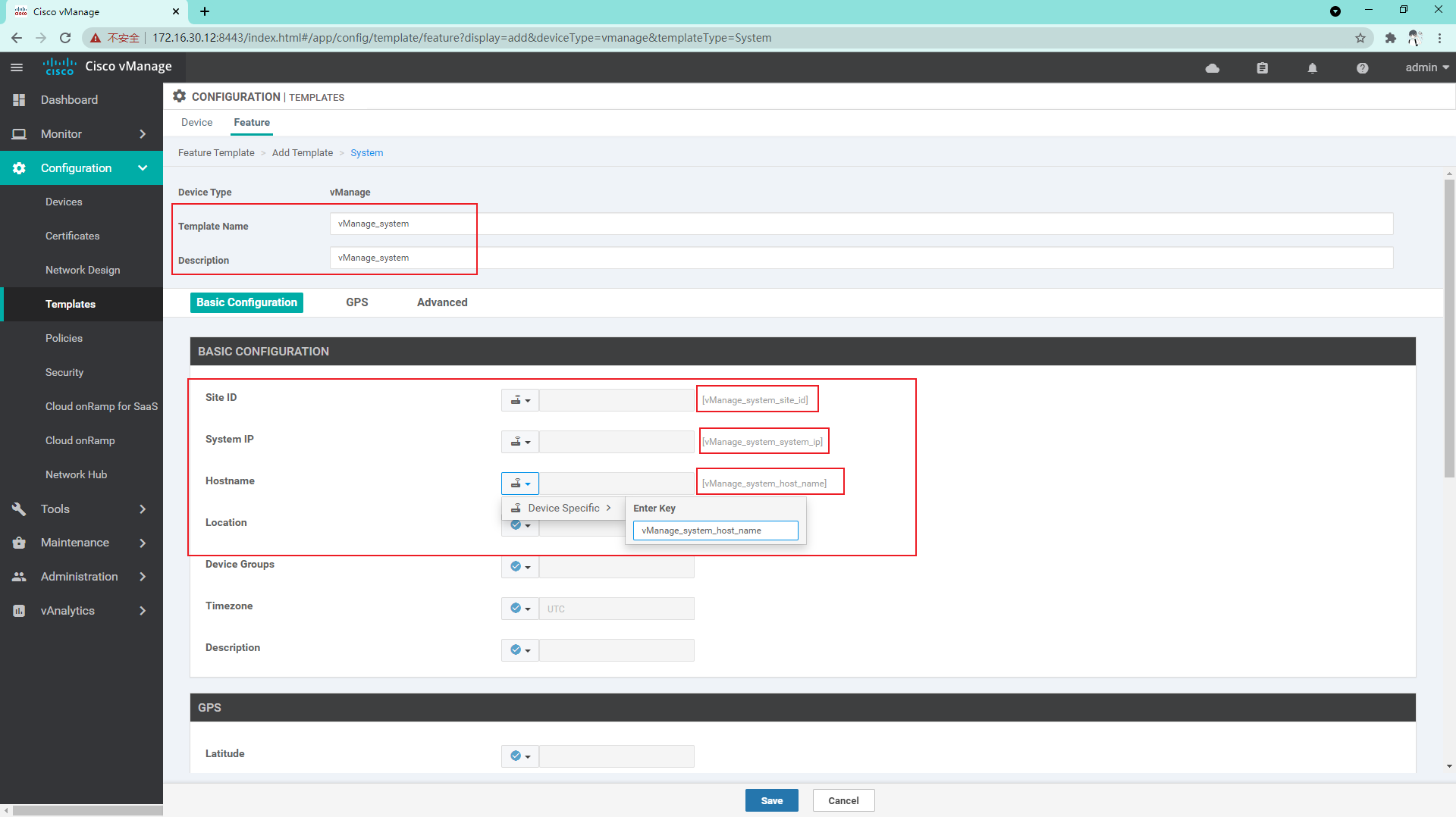
System template. Note that the name should be changed to its own readable name, as shown below. Save it:
VPN 0 template:
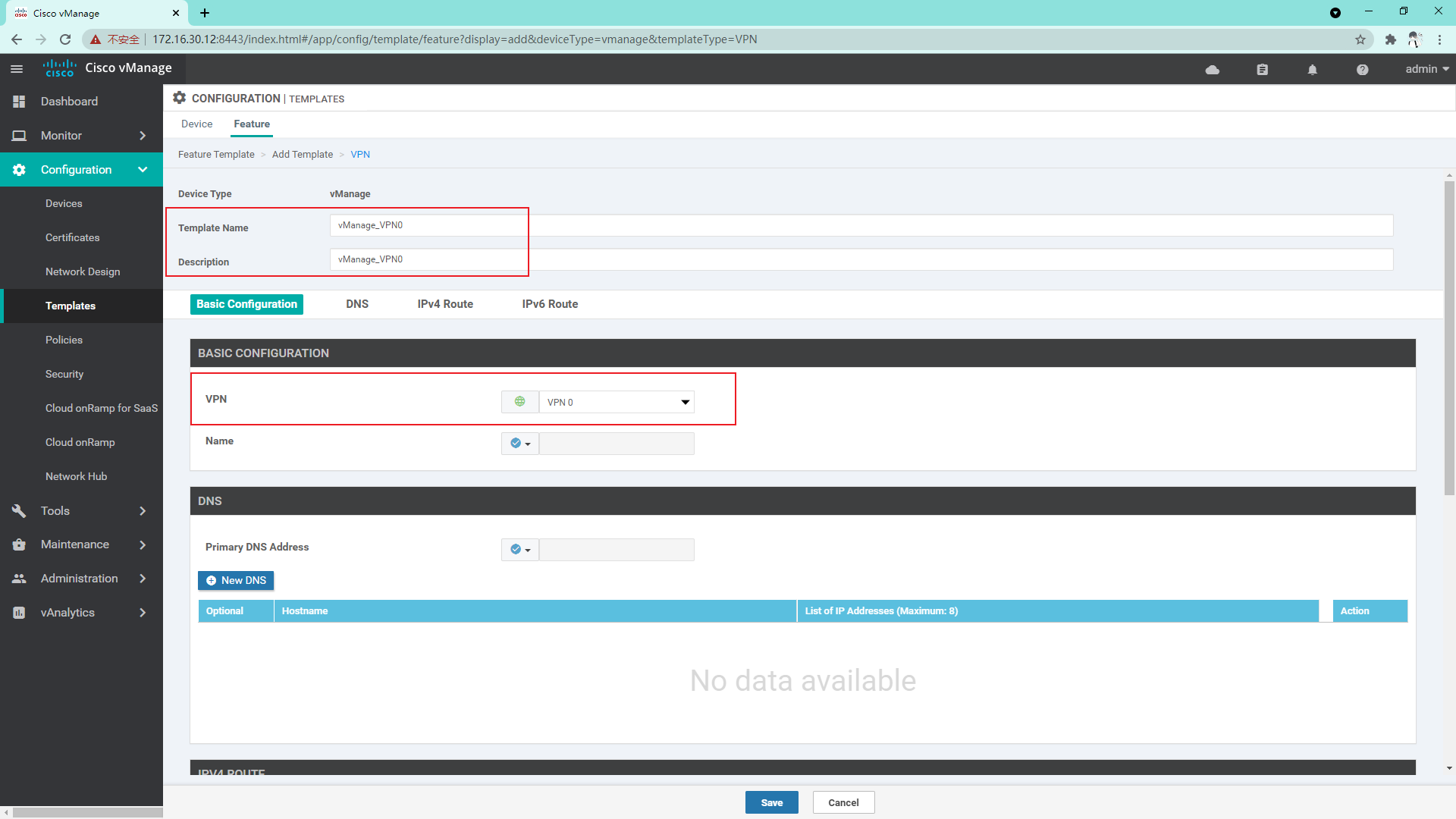
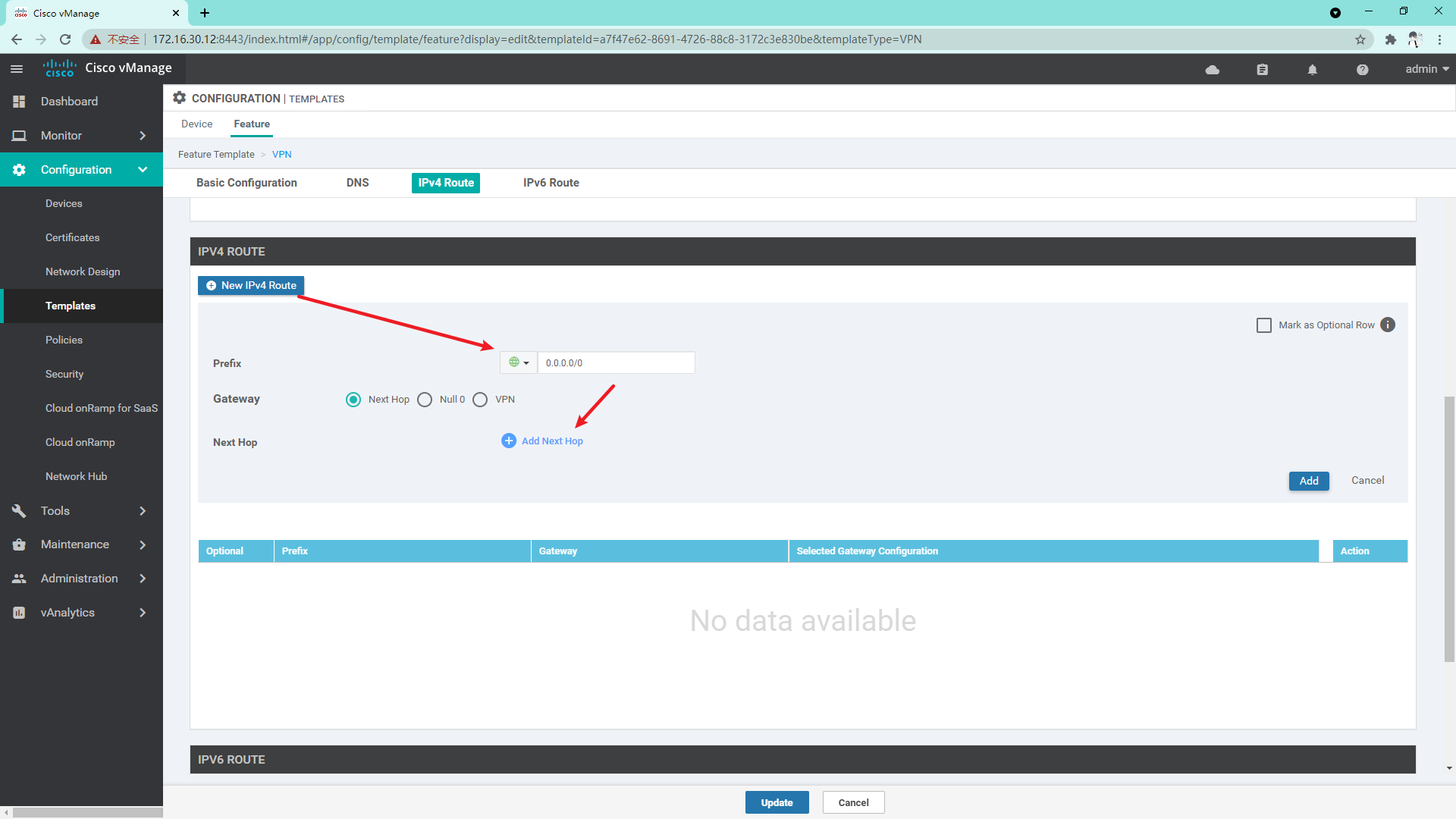
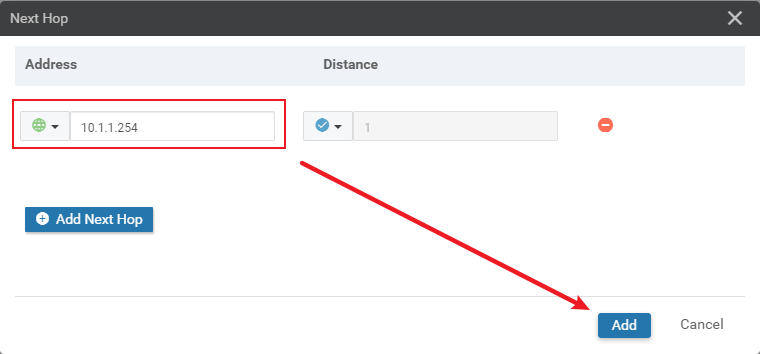
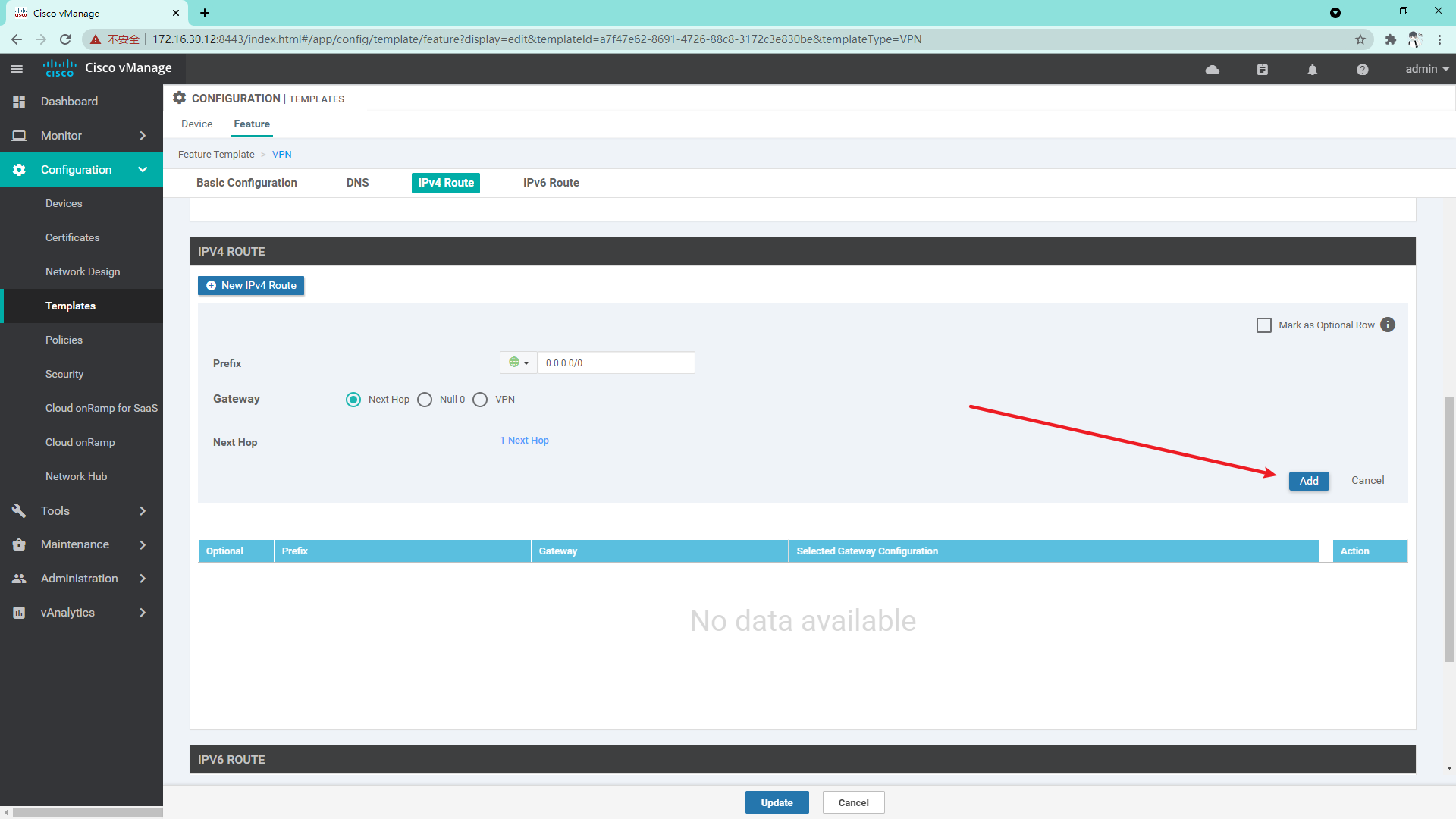
VPN 512 template:
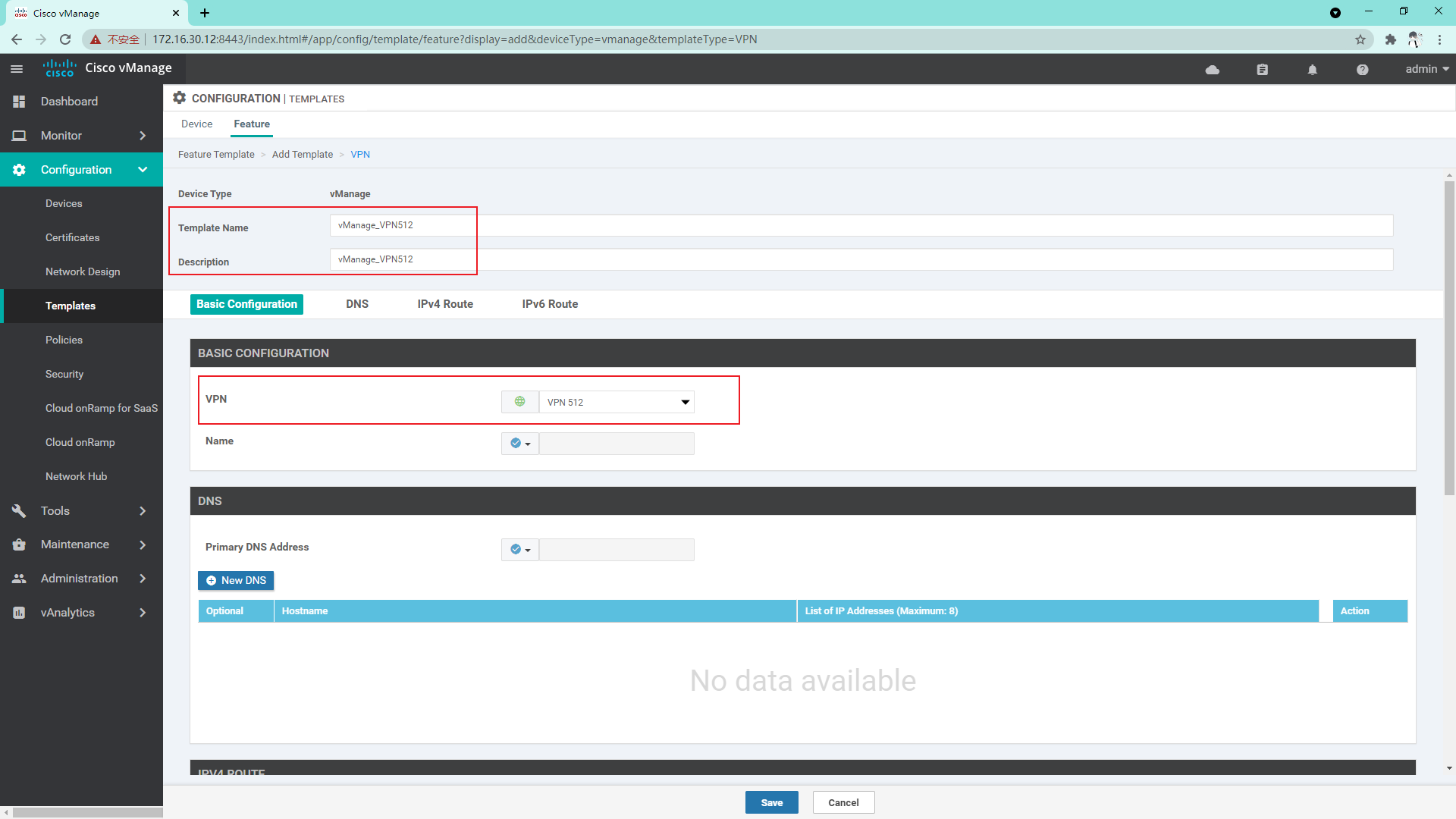
VPN 0 interface template:
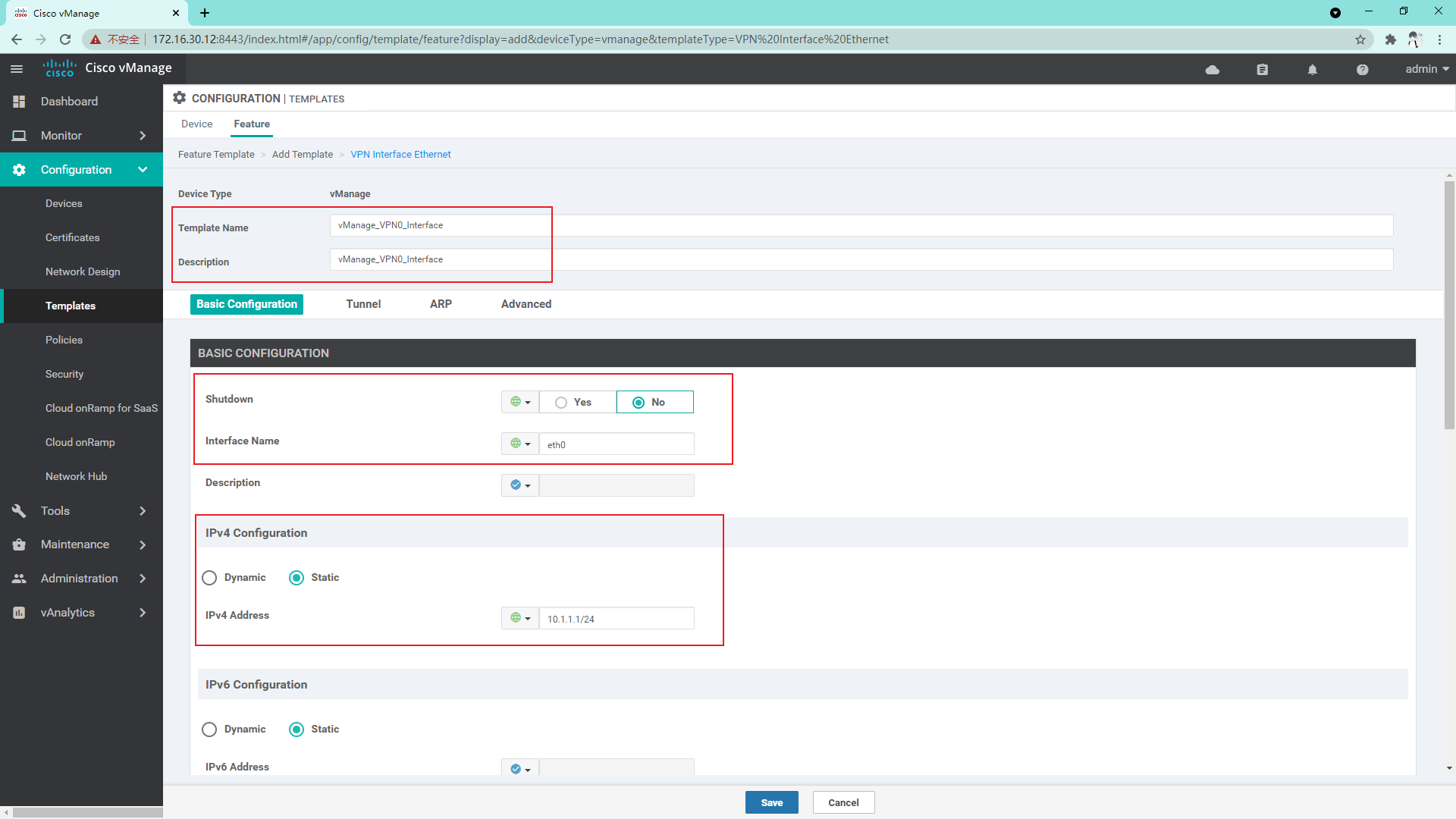
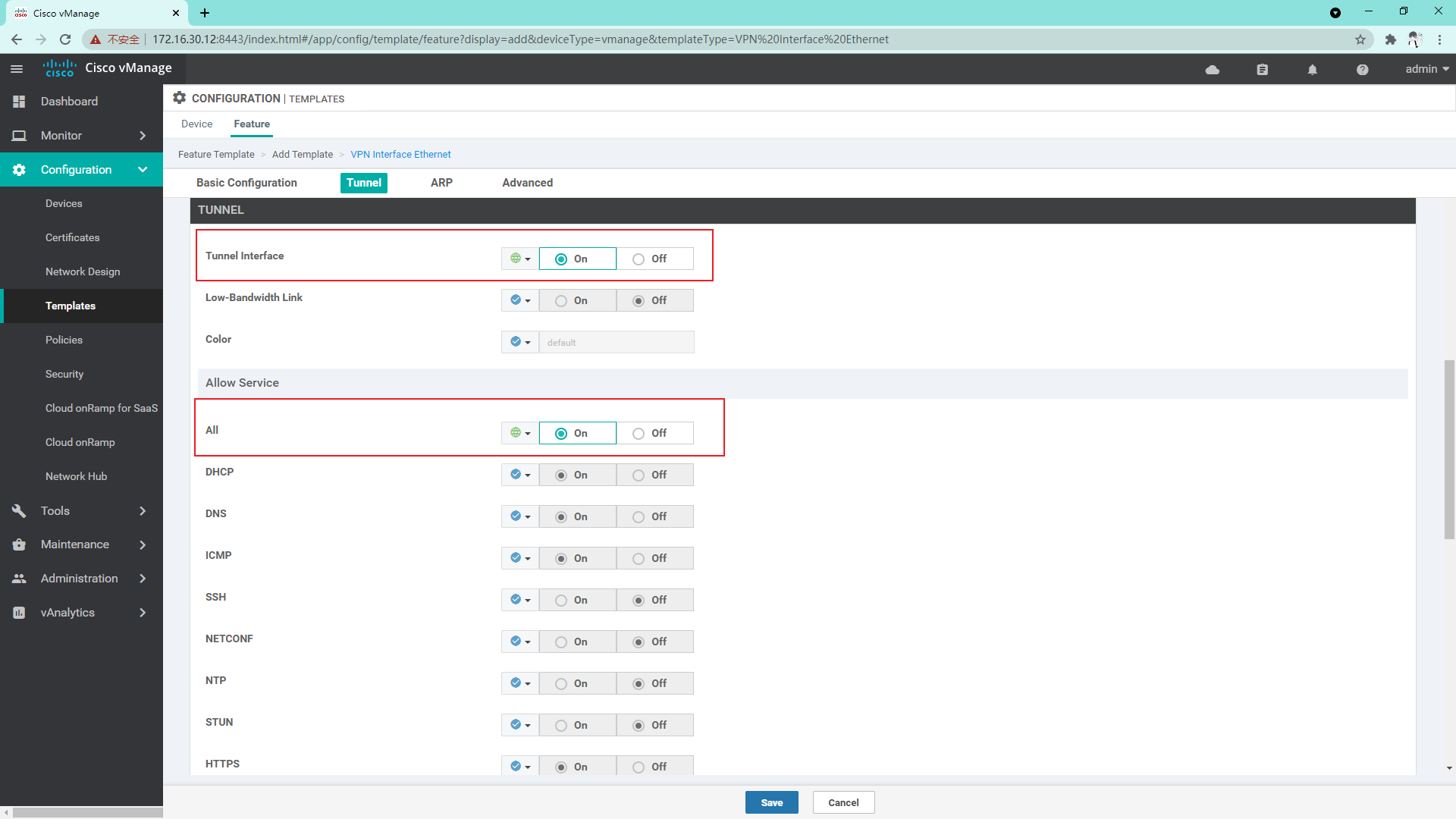
VPN 512 interface template:
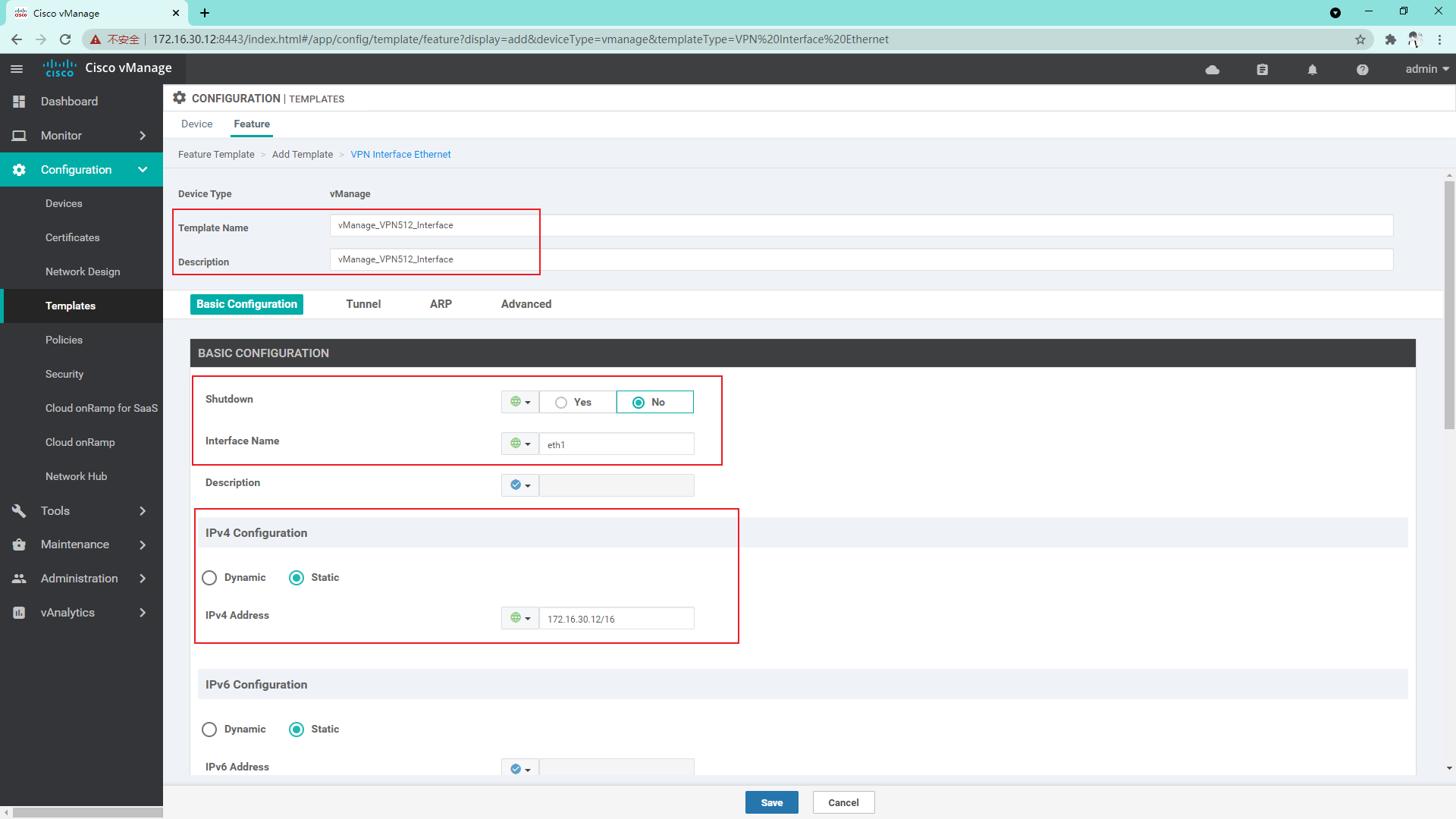
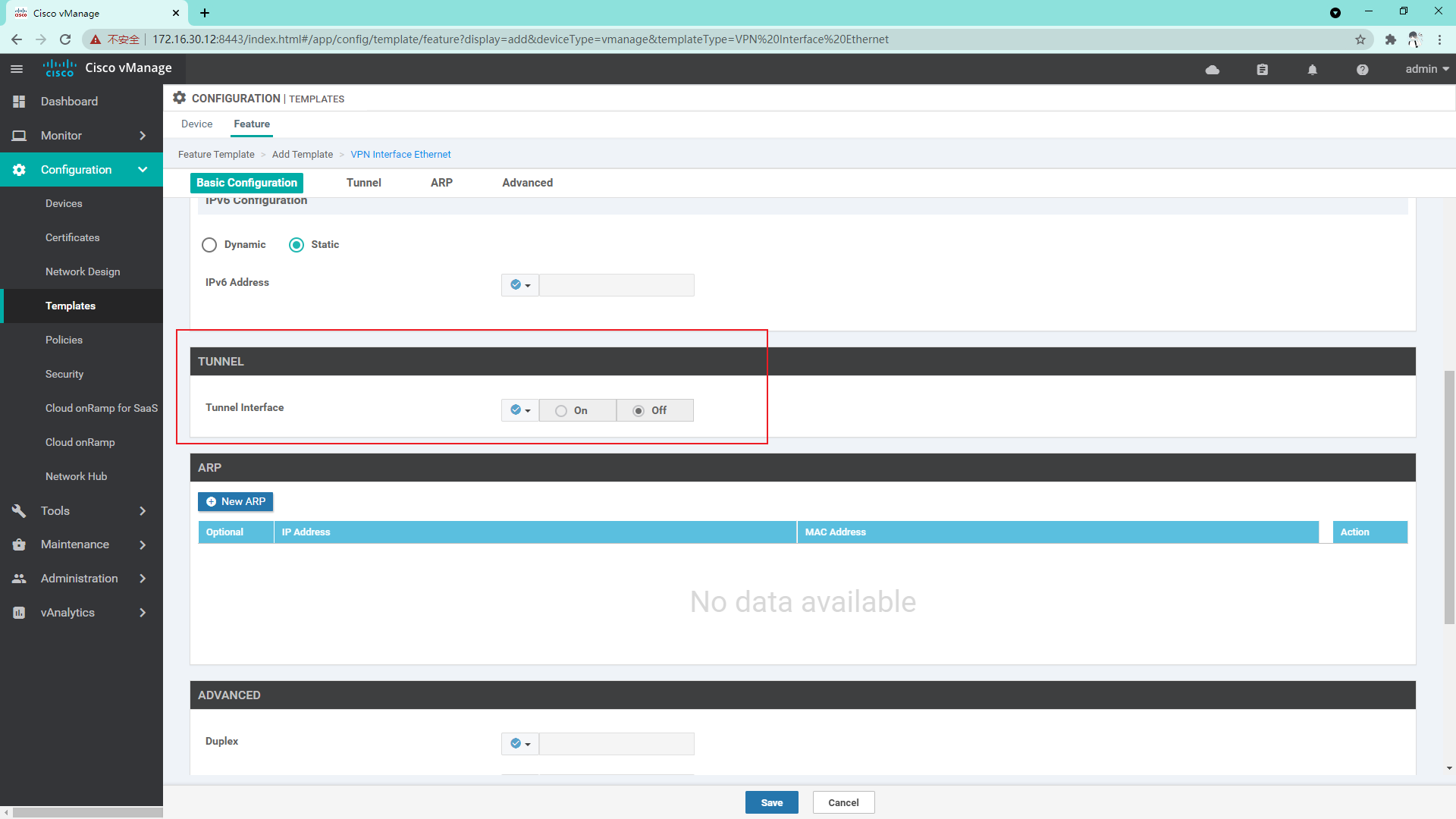
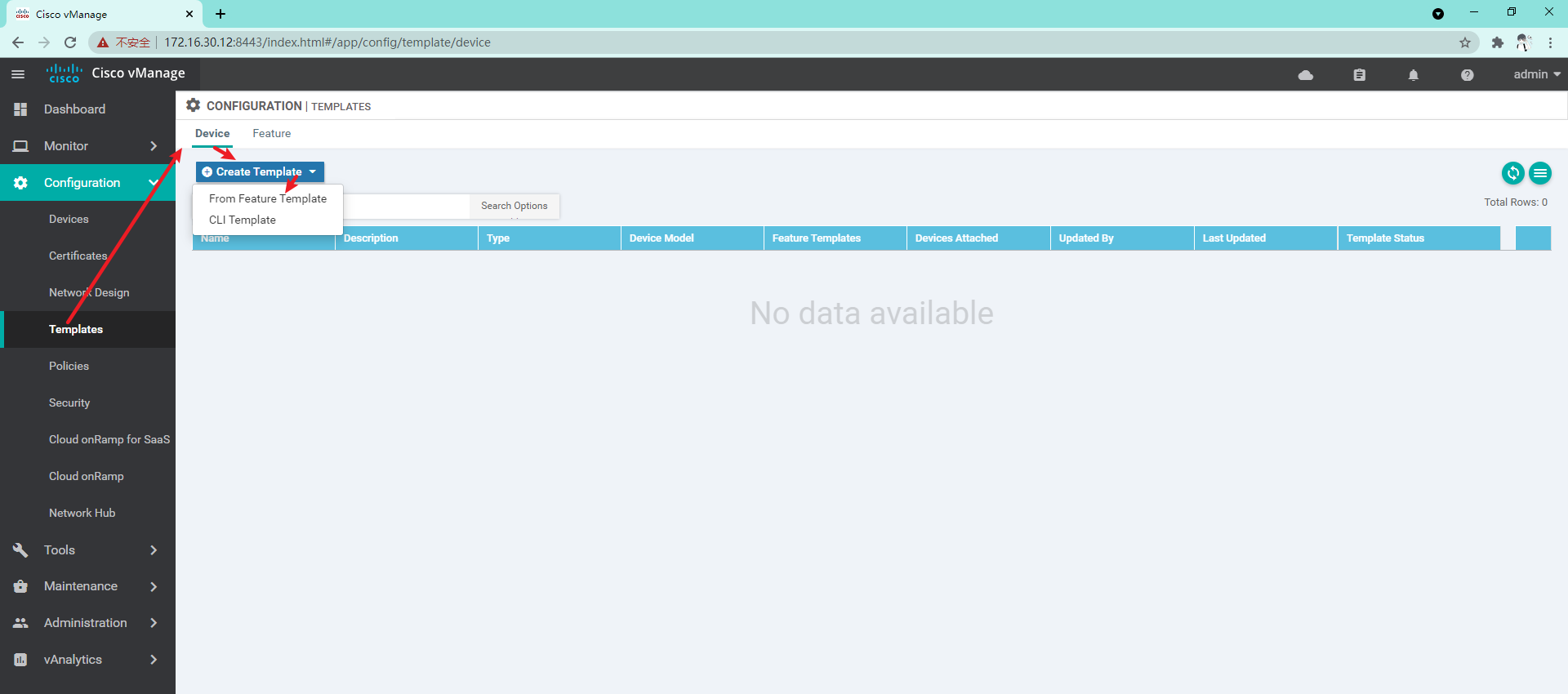
4.1.2 so far, we have created a template sufficient to manage vManage, and then we create a Device template
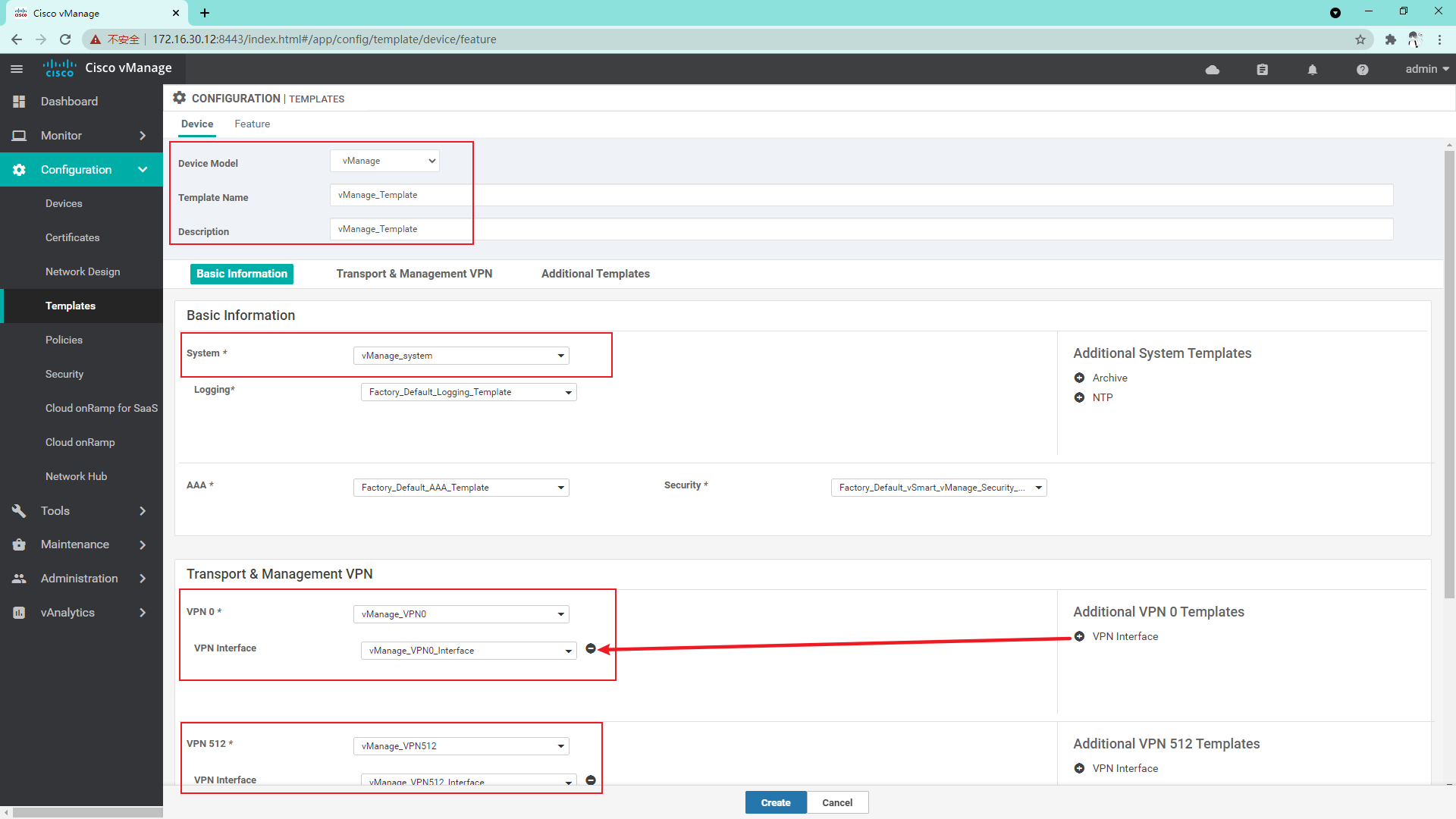
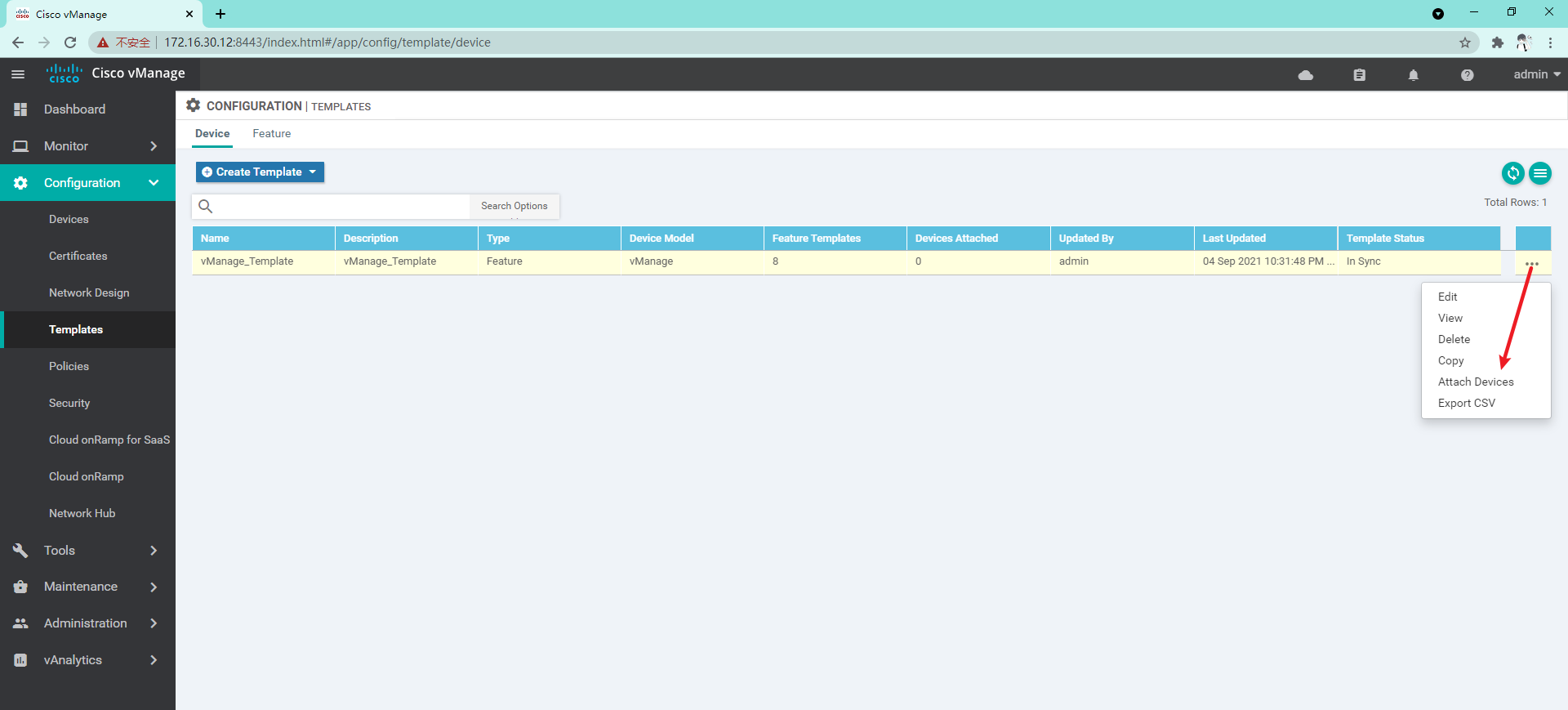
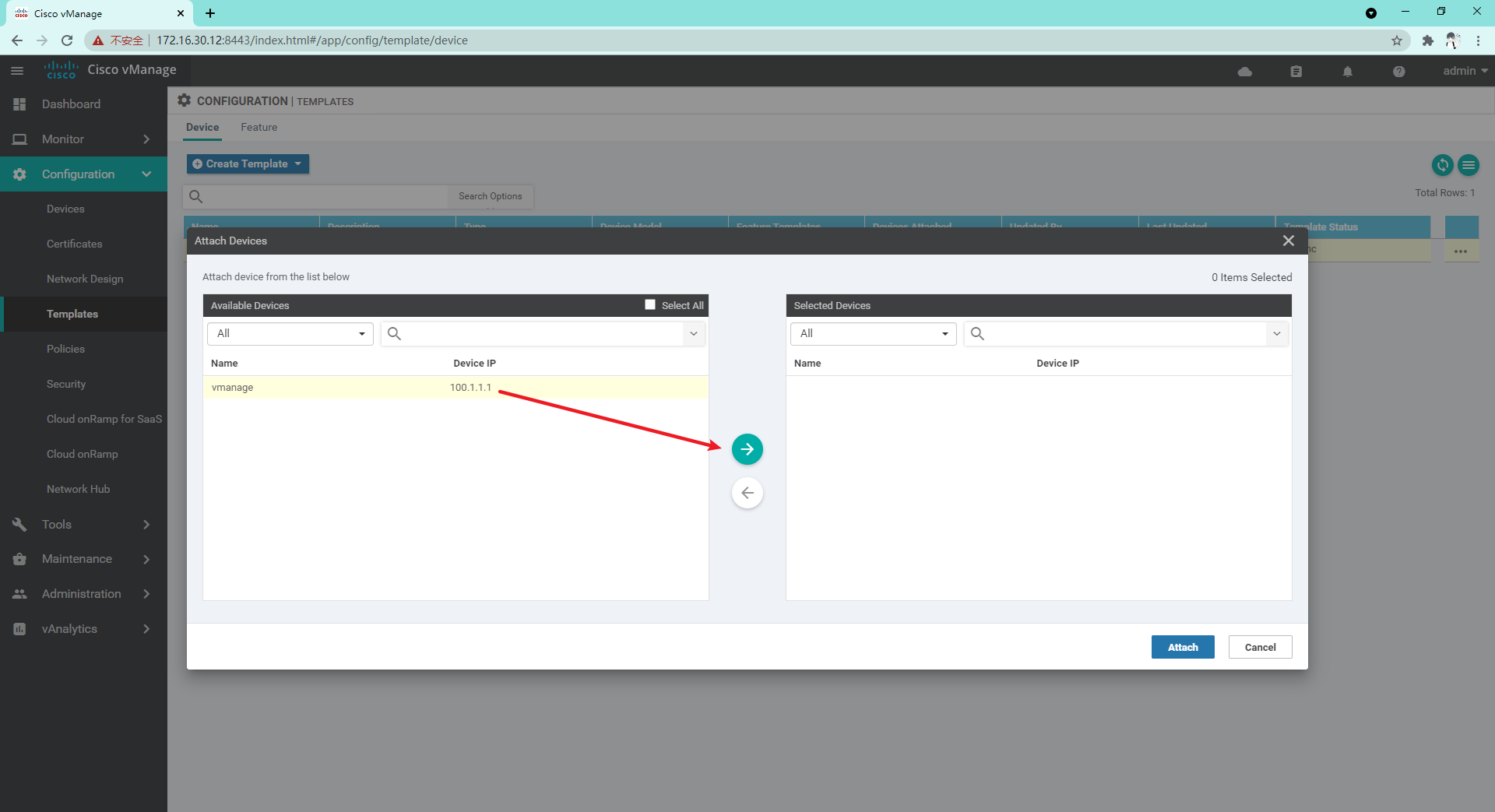
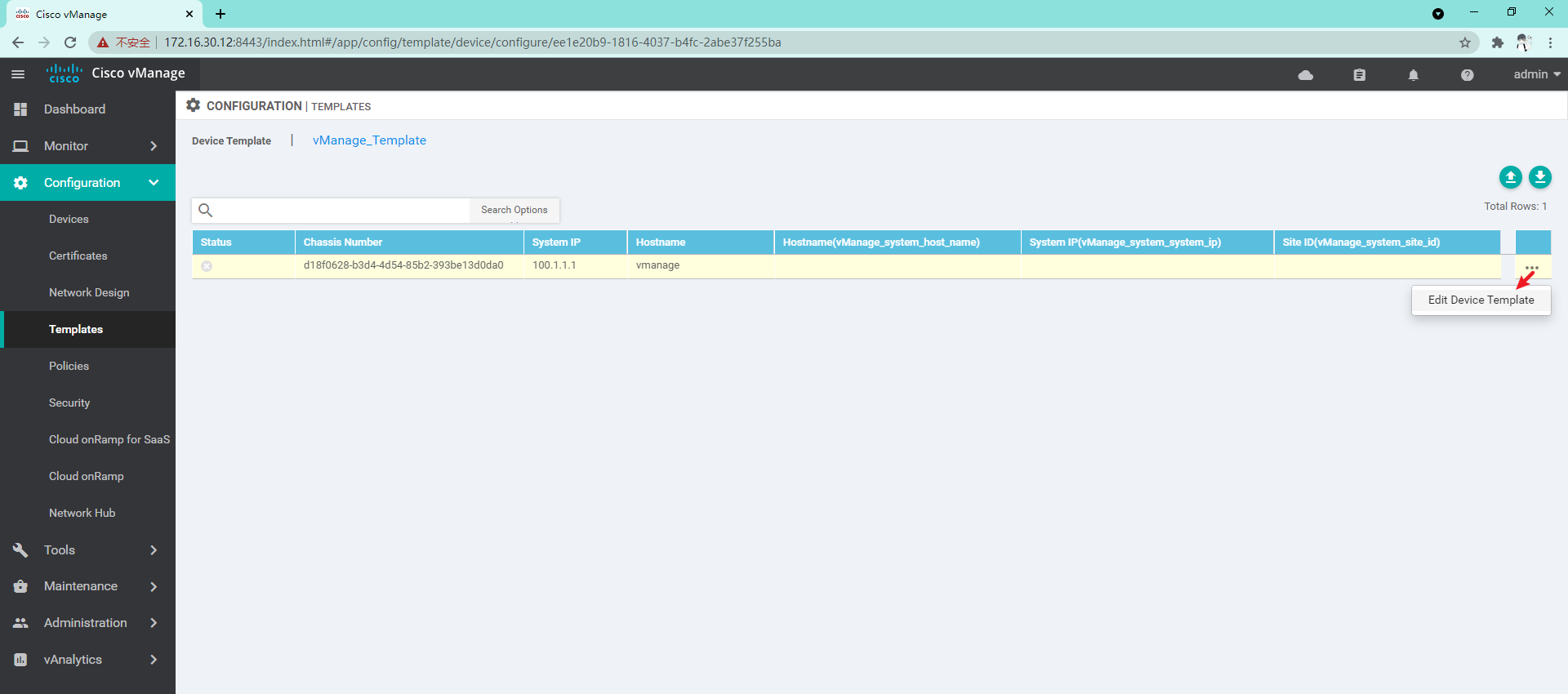
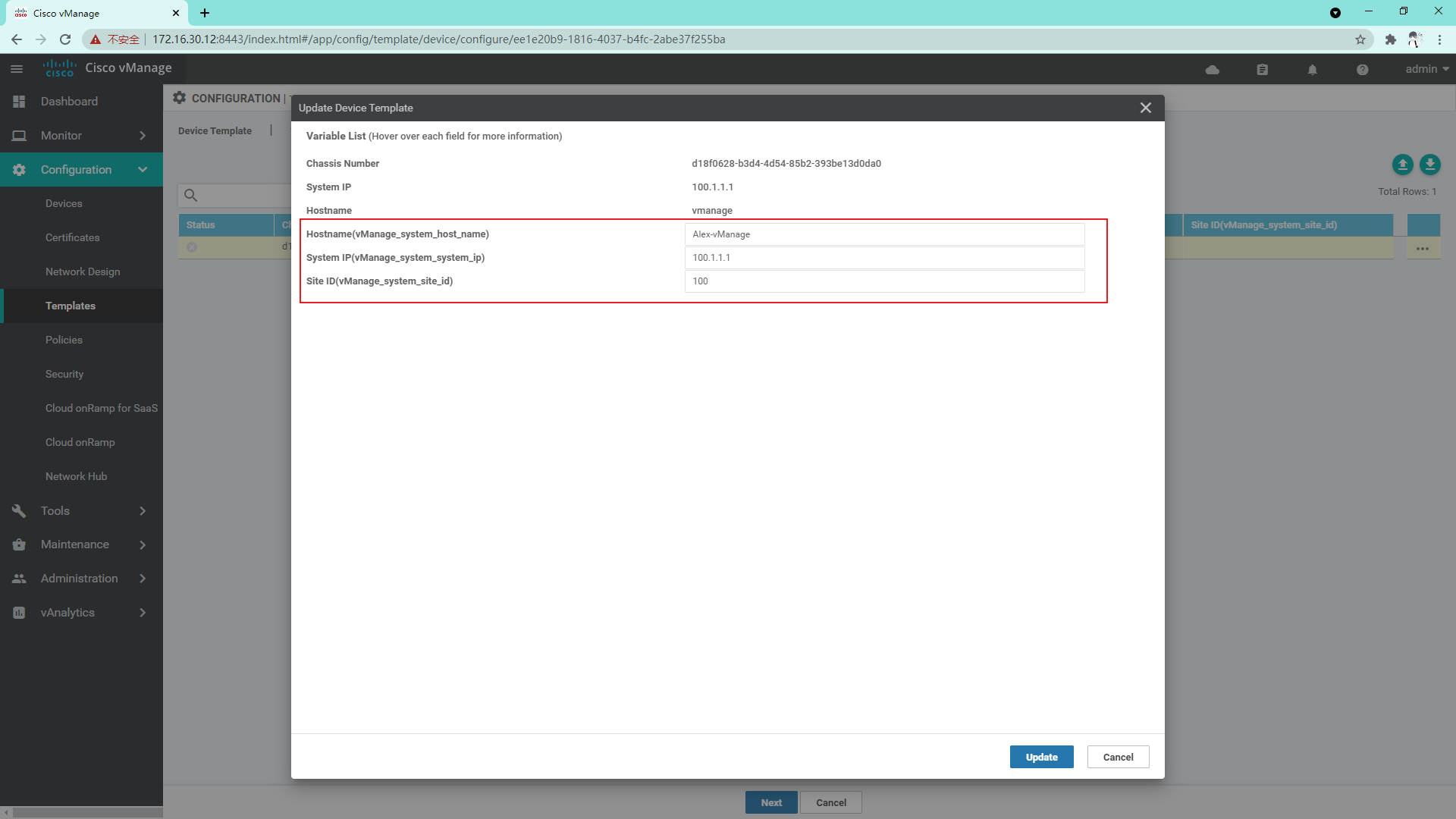
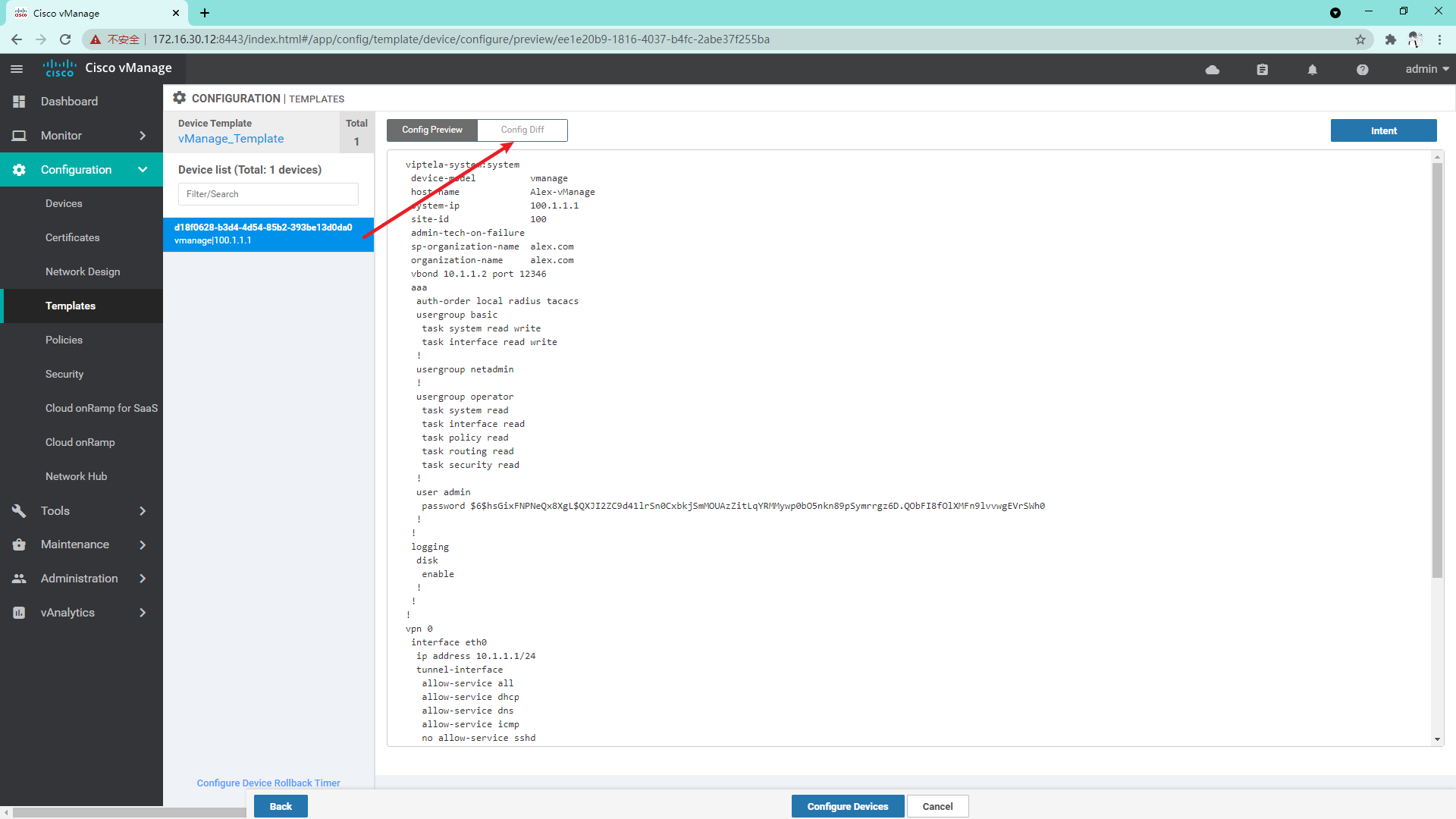
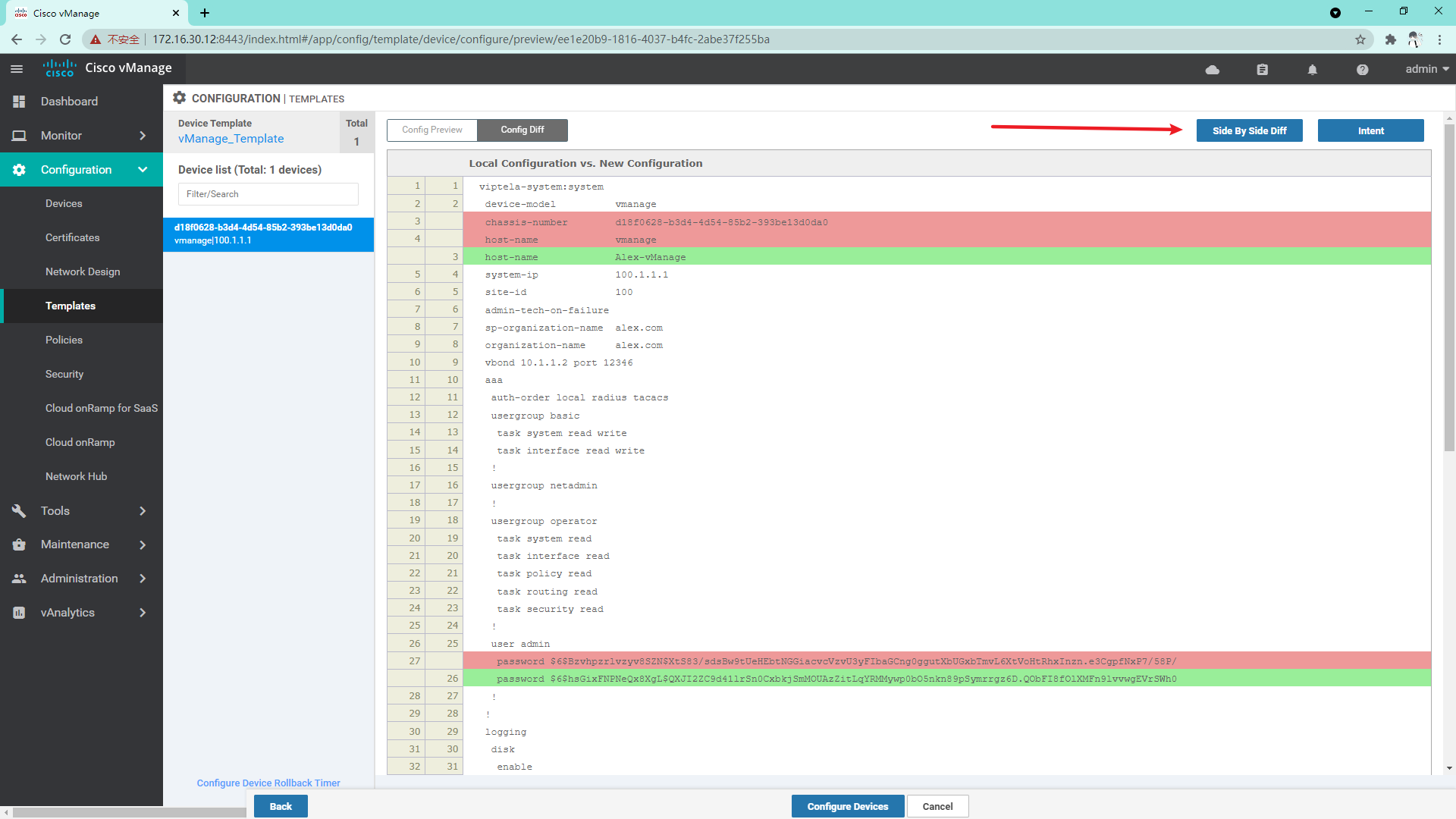
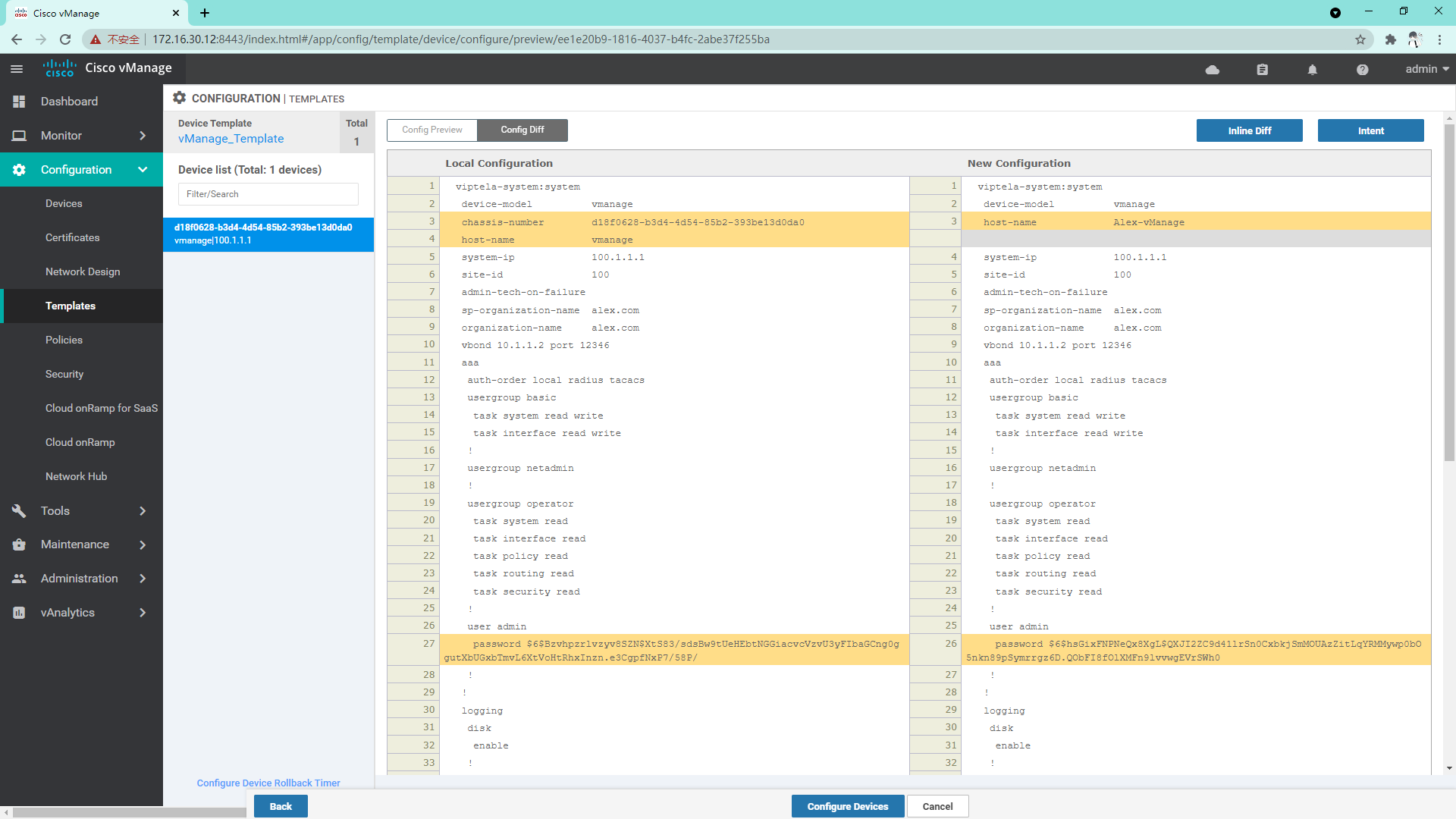
At this time, you can see the difference between the template configuration and the current device configuration. If there is no problem, you can directly click configure devices to issue the configuration;
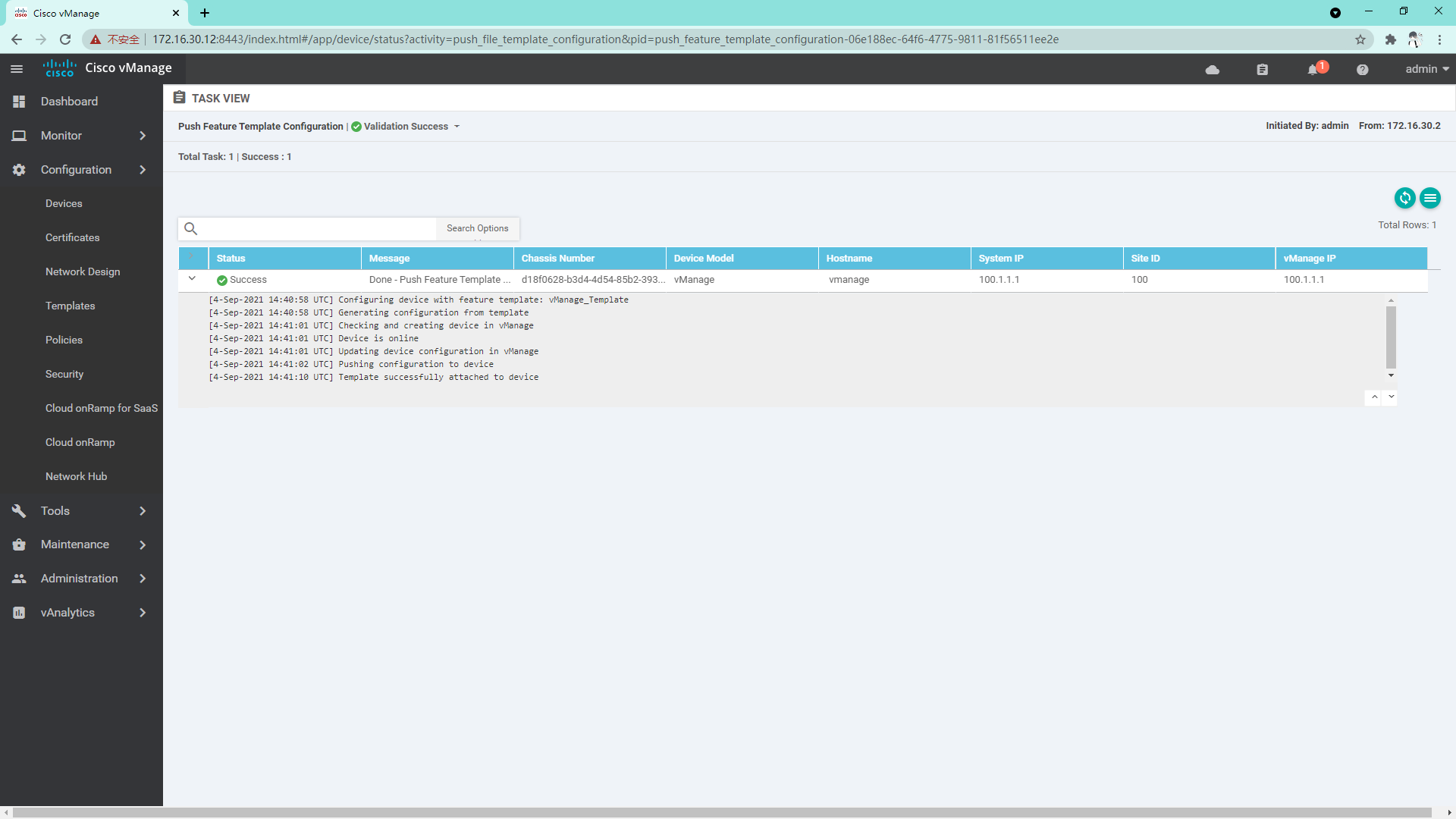
4.1.3 the success representative configuration is issued successfully
4.1.4 at this time, you can view the system information through the SSH login device of vManage
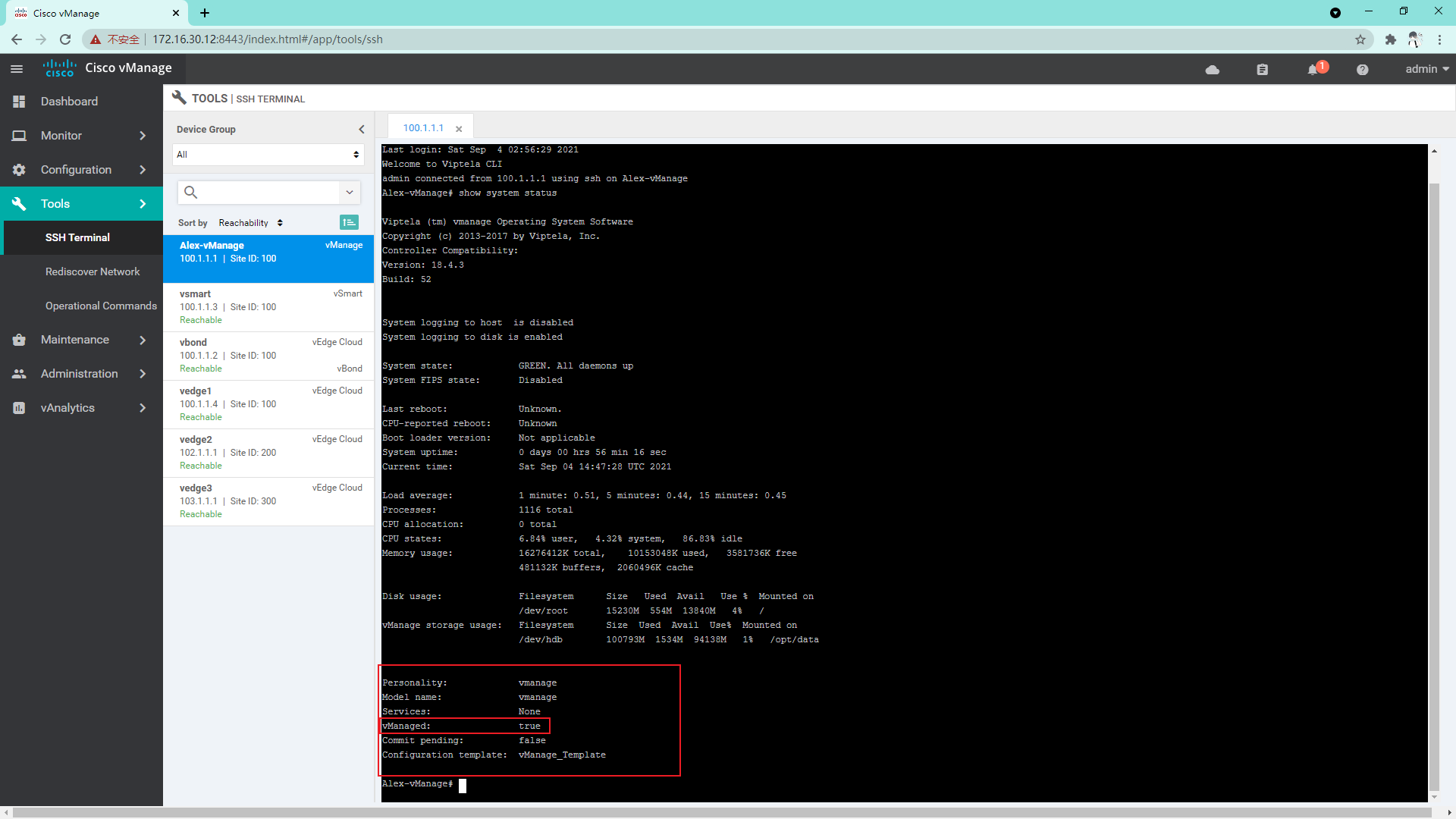
4.1.5 at this time, vMange has been put into the pipe
4.2 pipe laying vSmart
4.2.1 create Feature template, including system template, VPN 0 template, VPN 512 template, interface template and OMP template
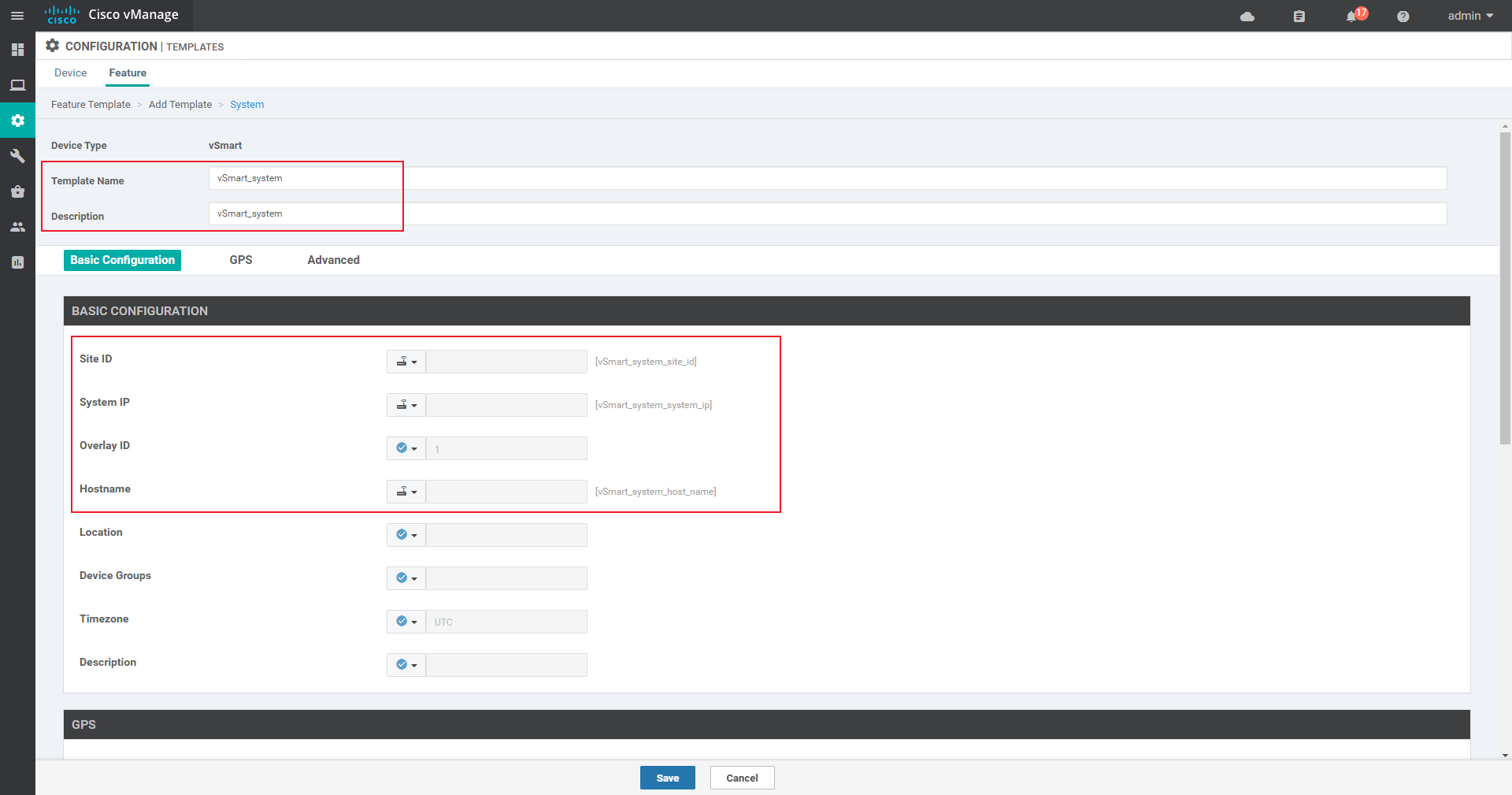
System template:
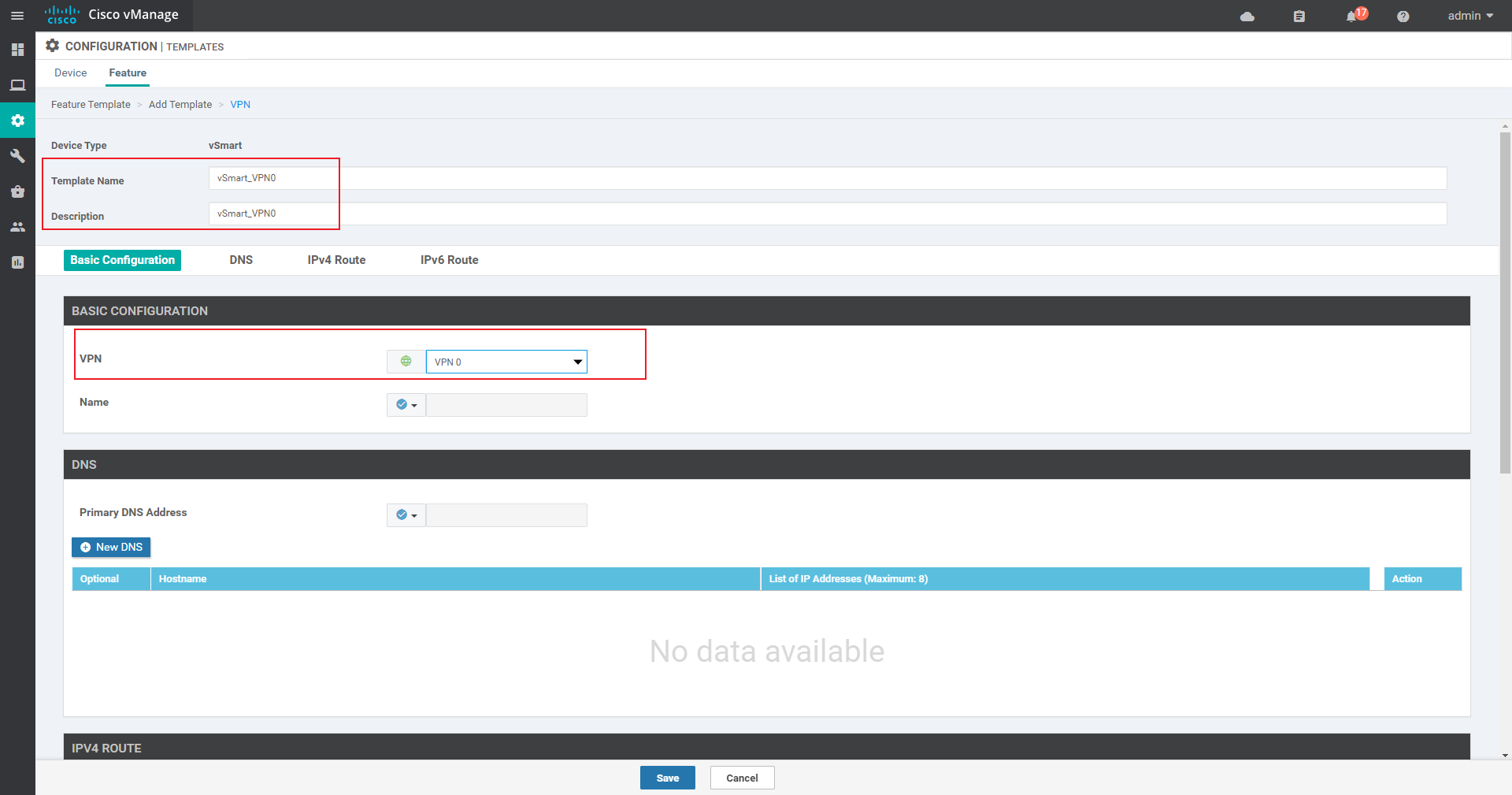
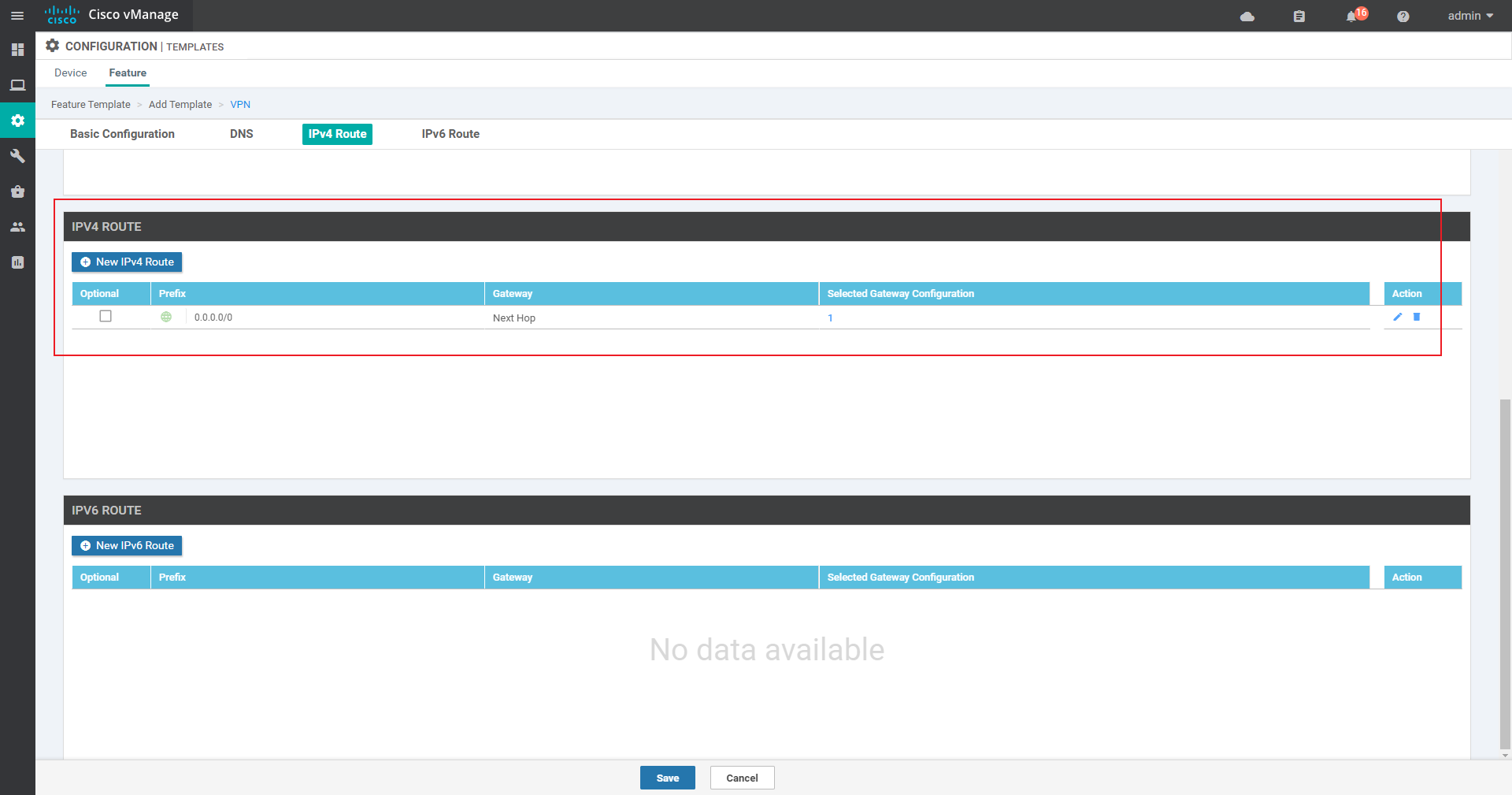
VPN0:
VPN512:
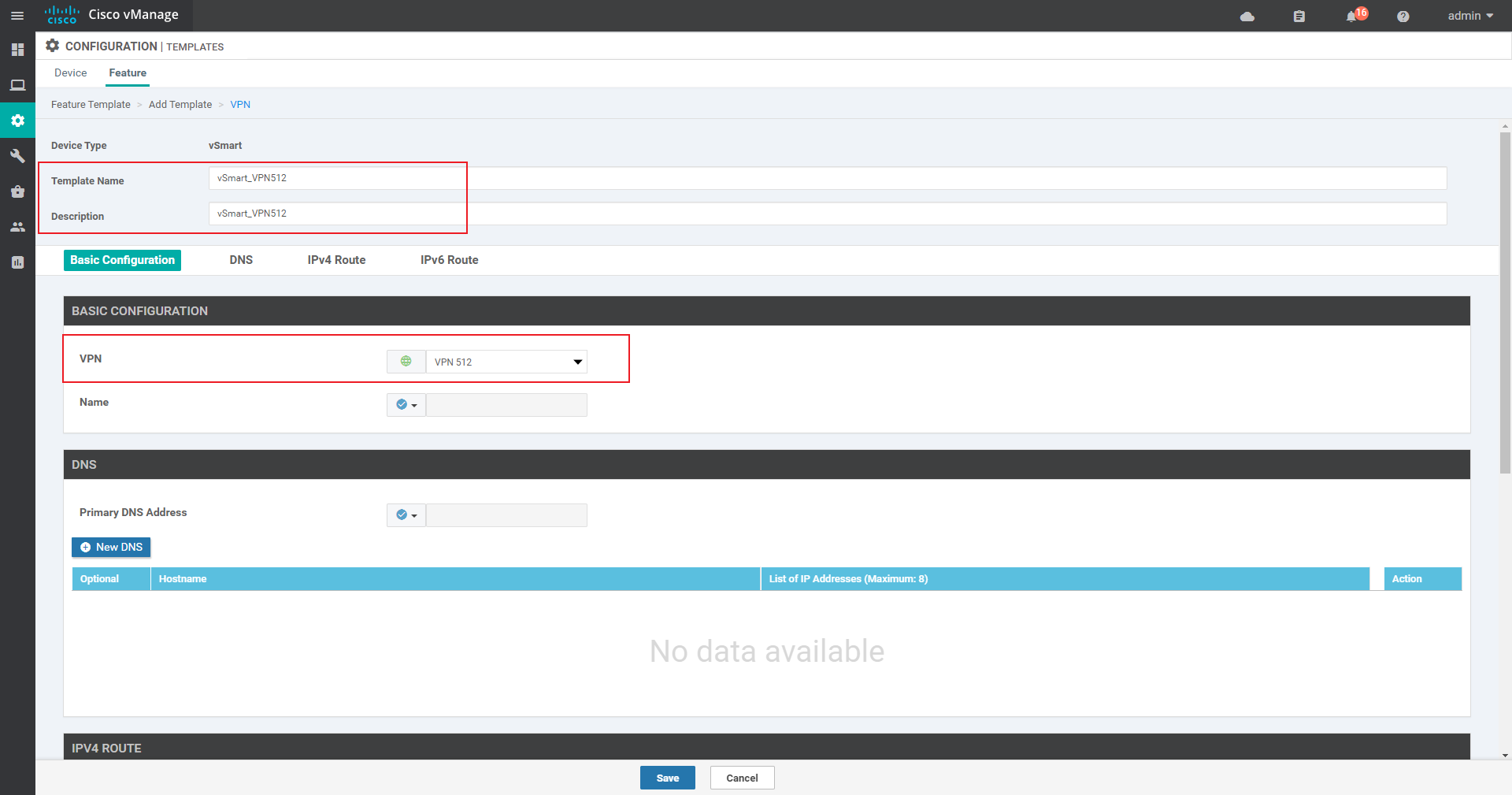
Vpn 0 interface template:
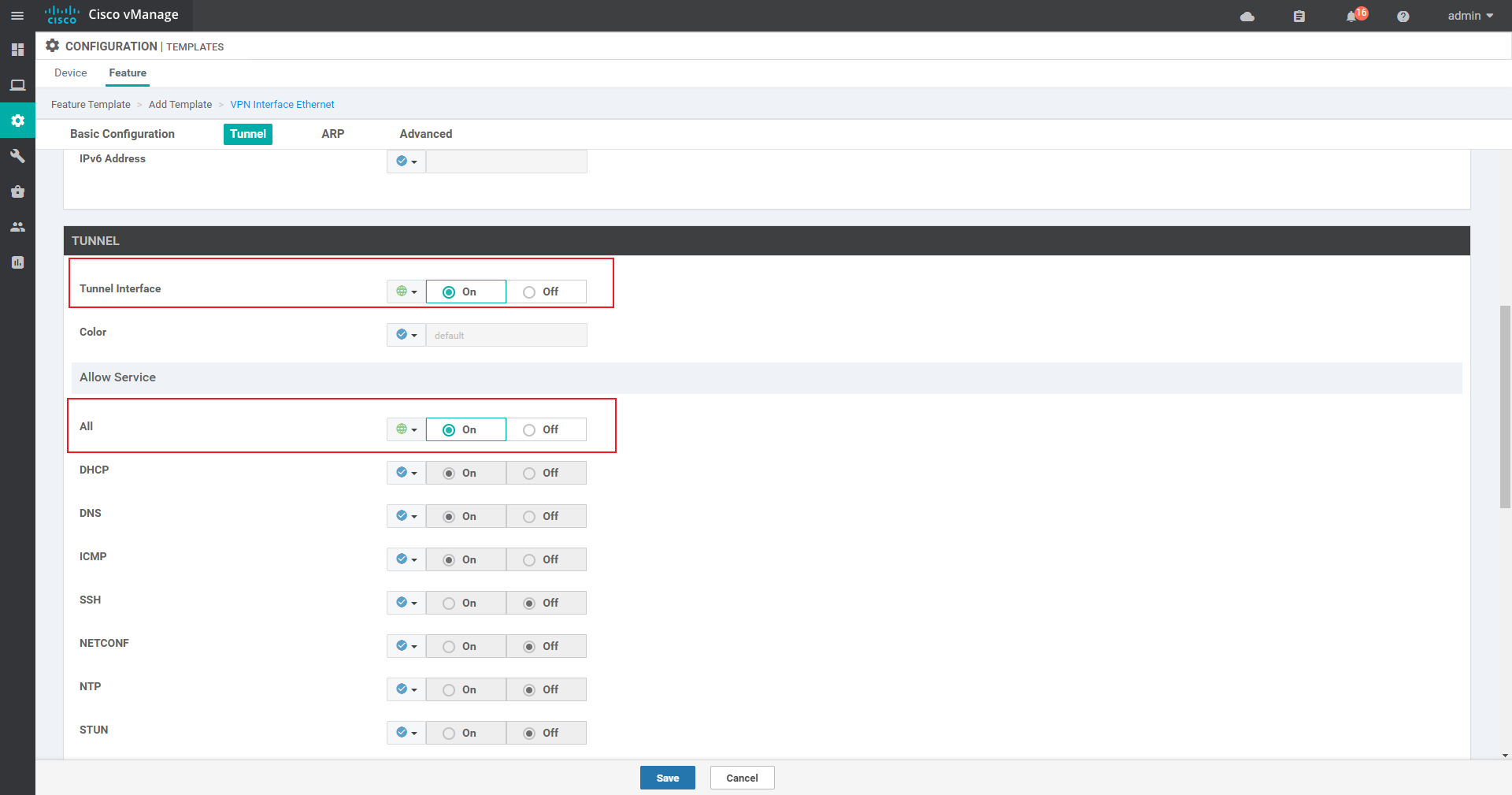
Vpn 512 interface template:
OMP template:
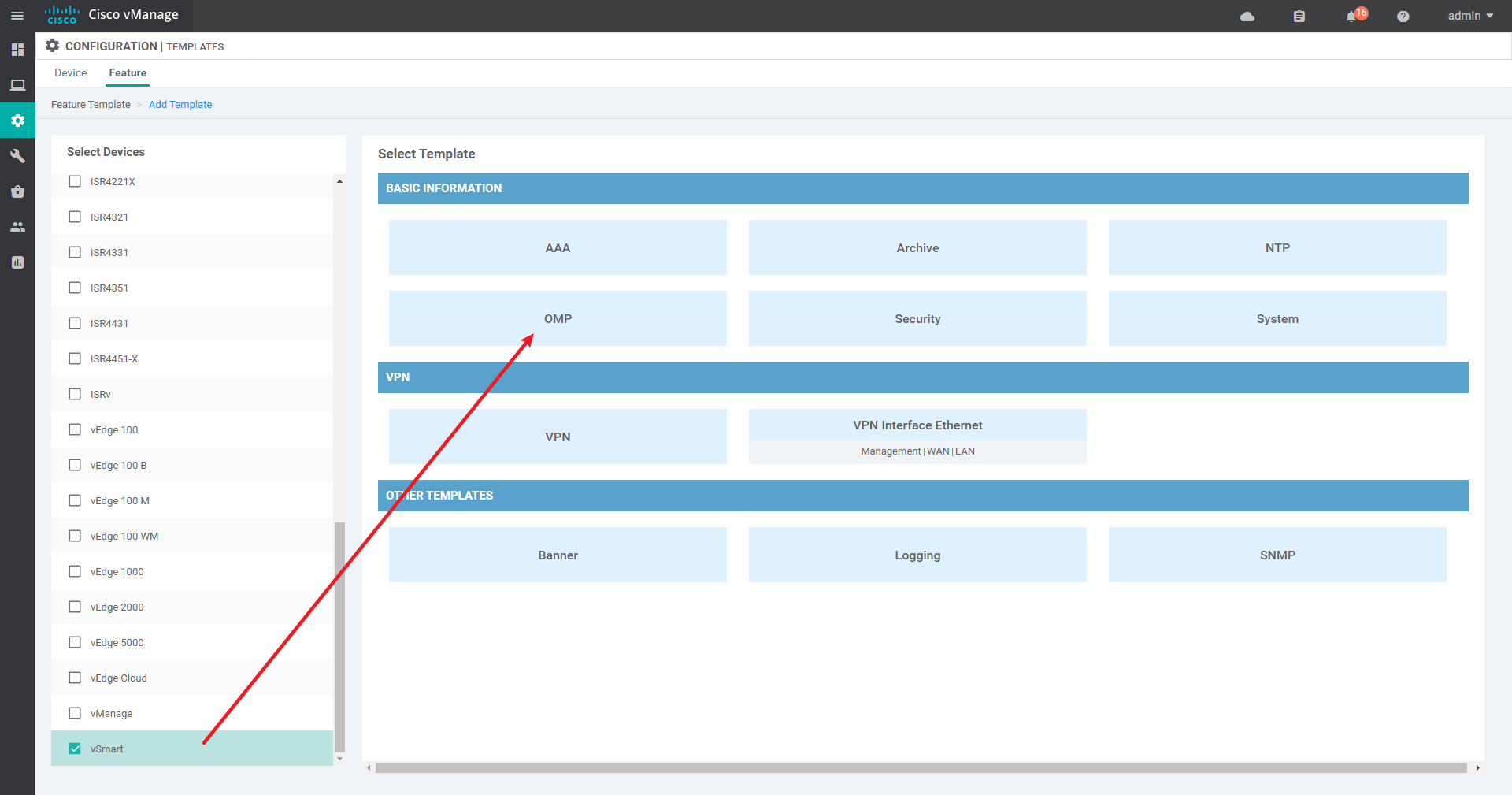
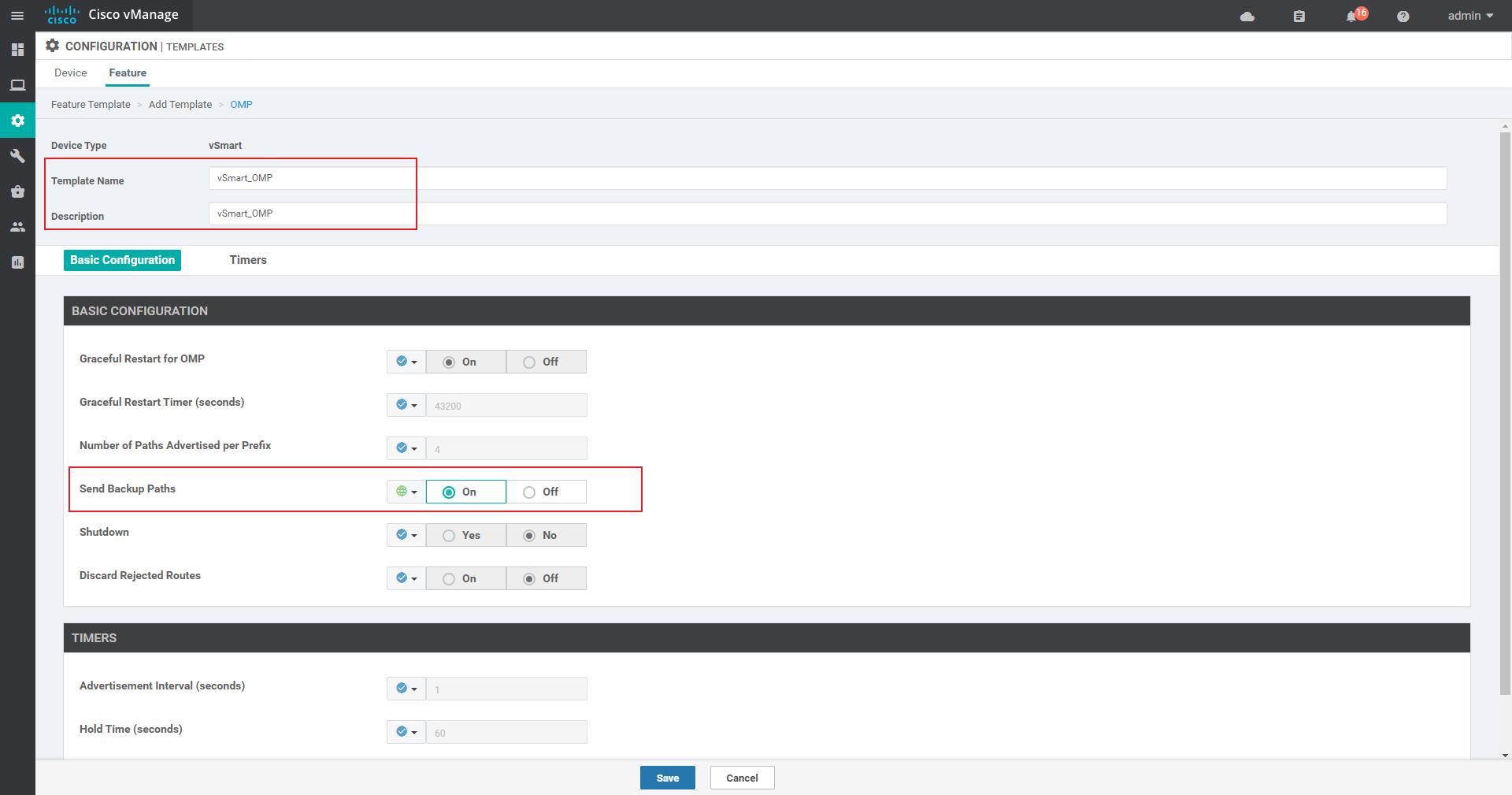
4.2.2 create Device template
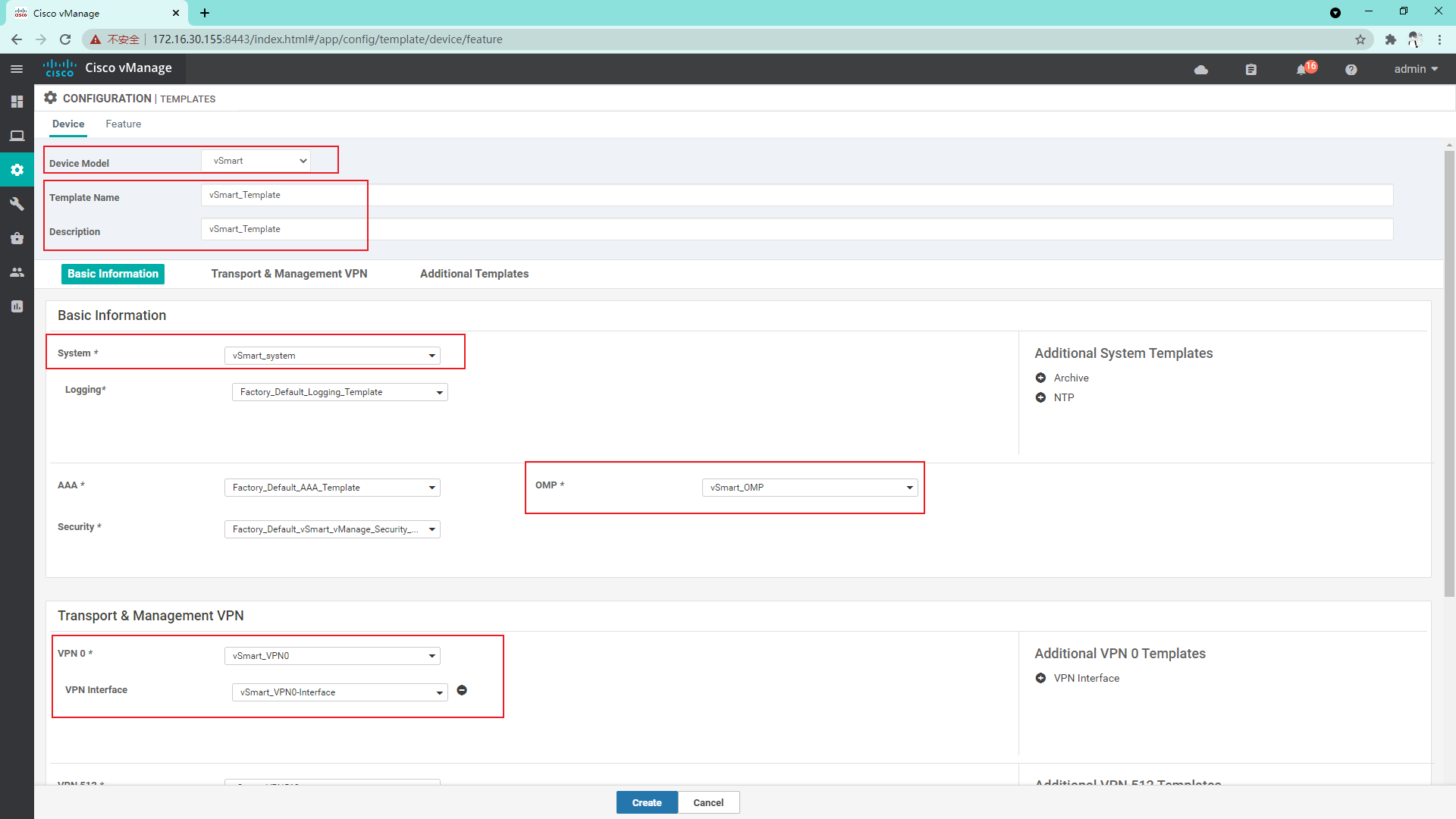
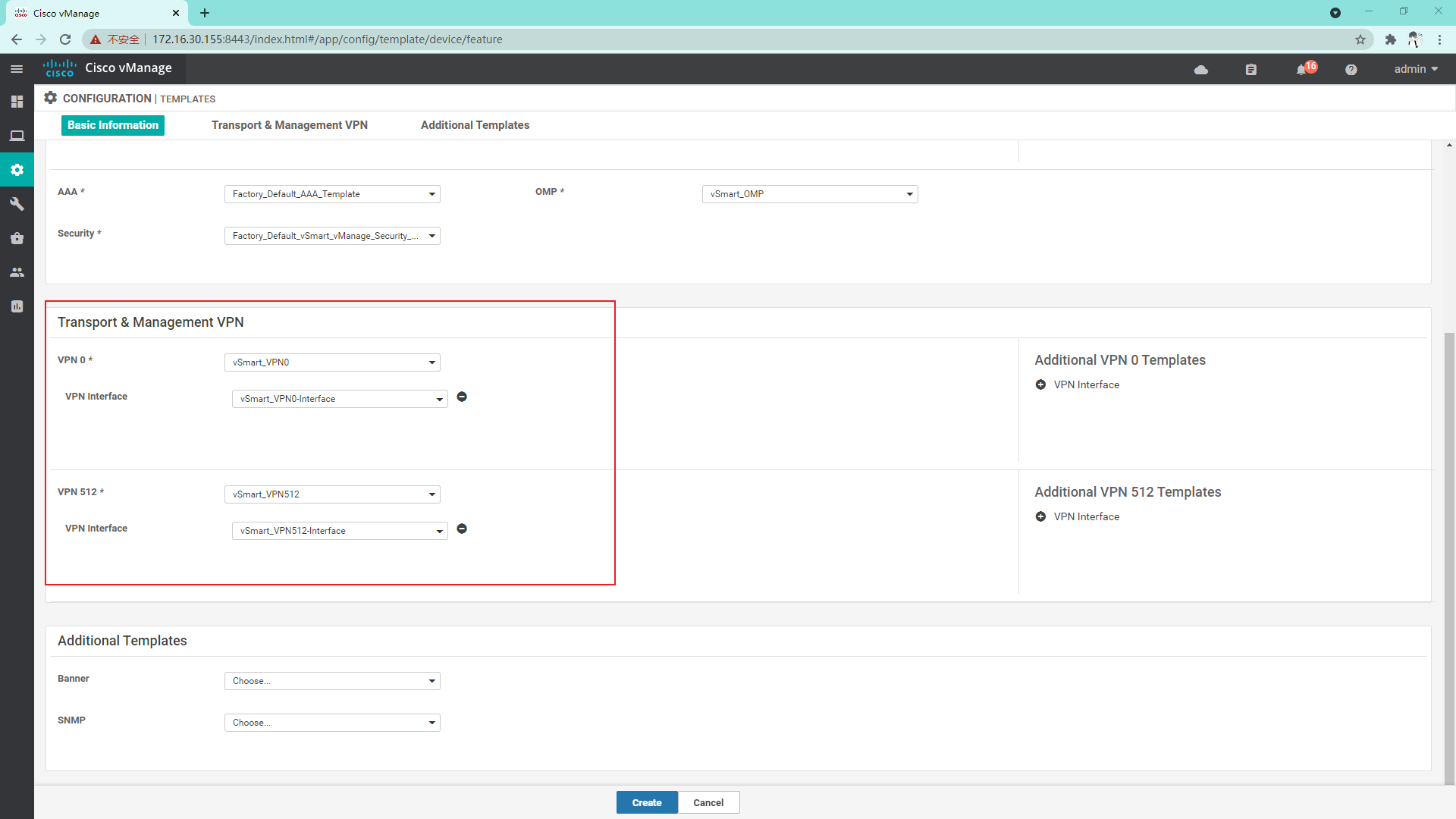
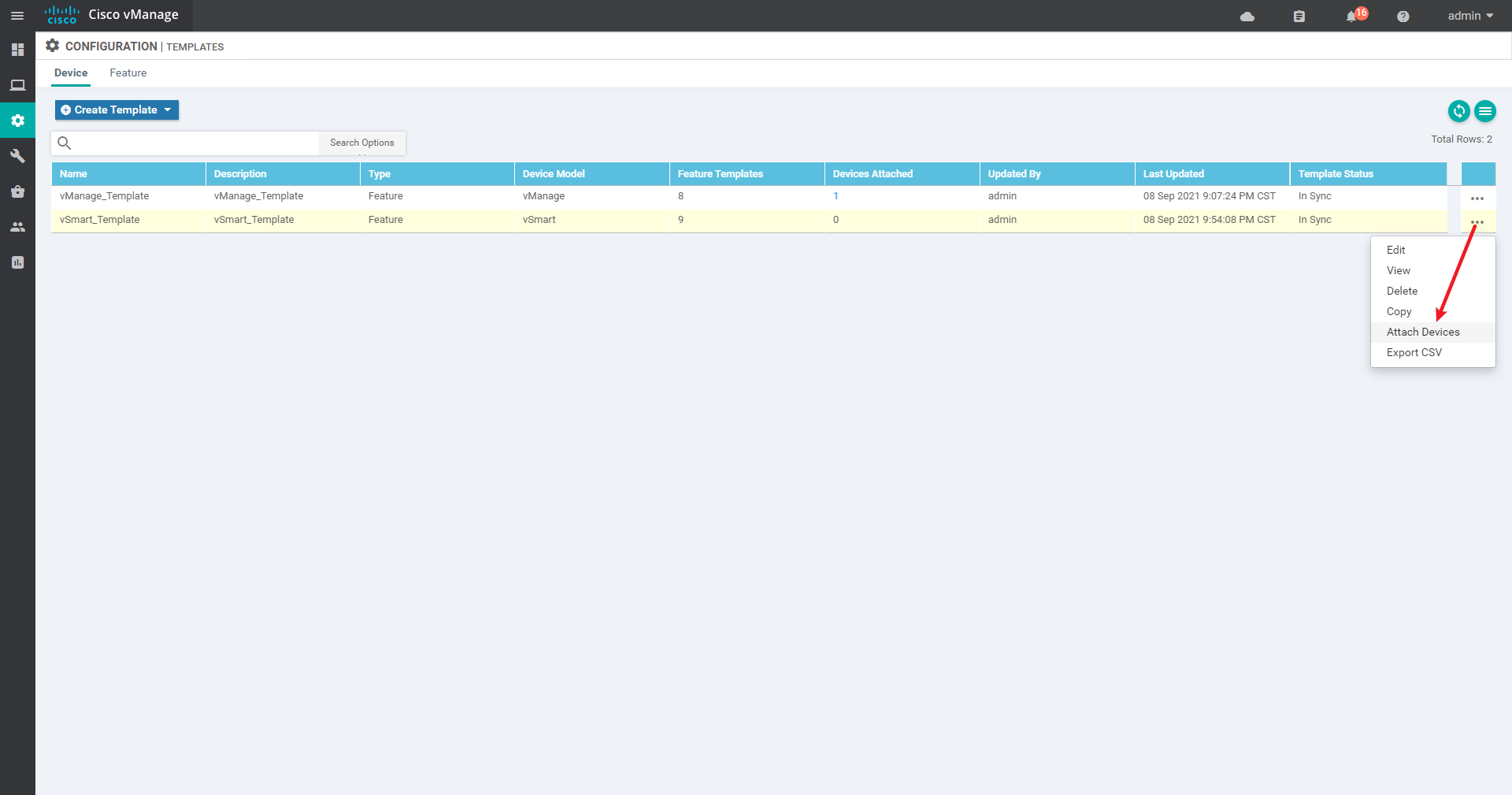
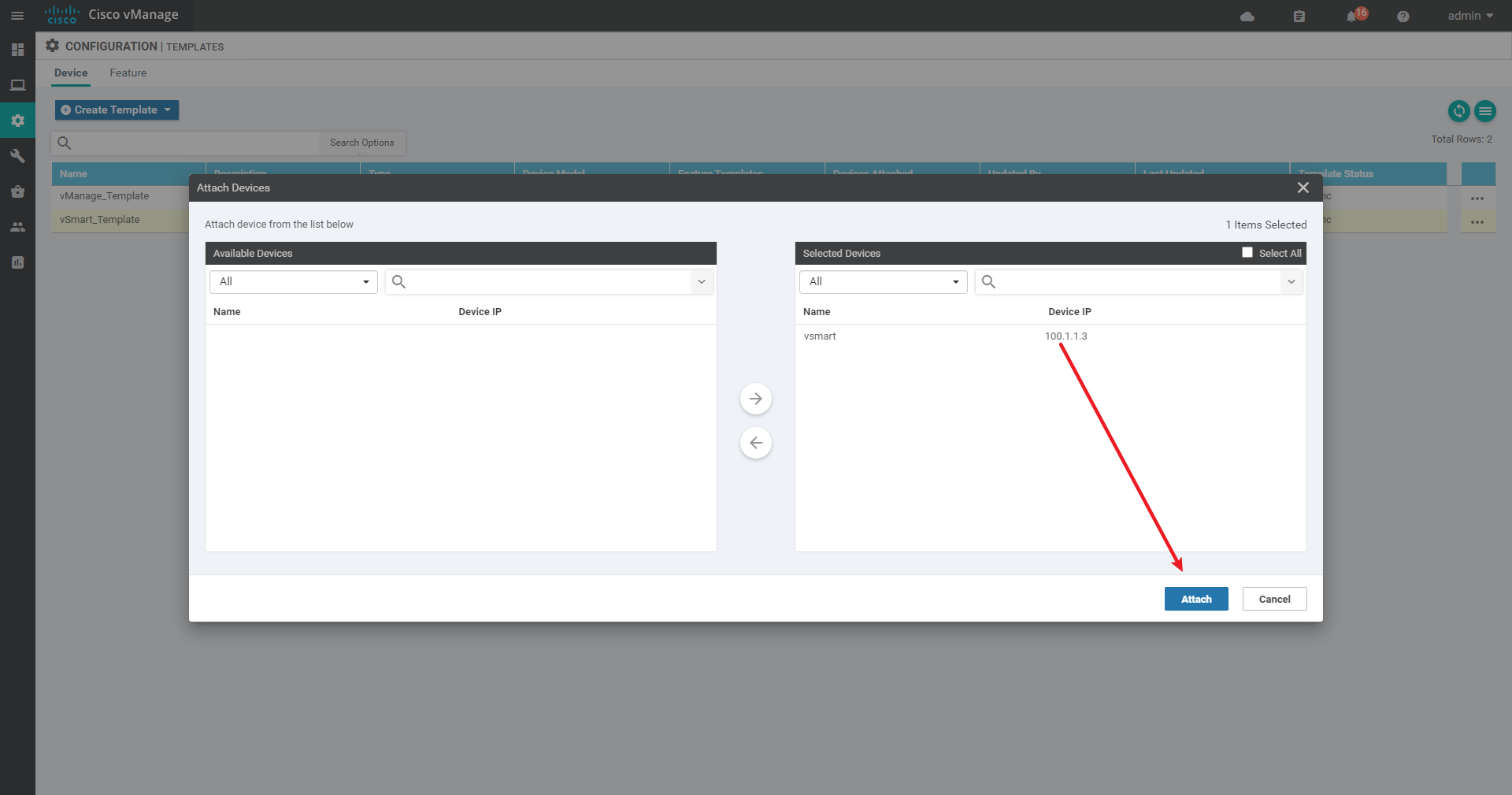
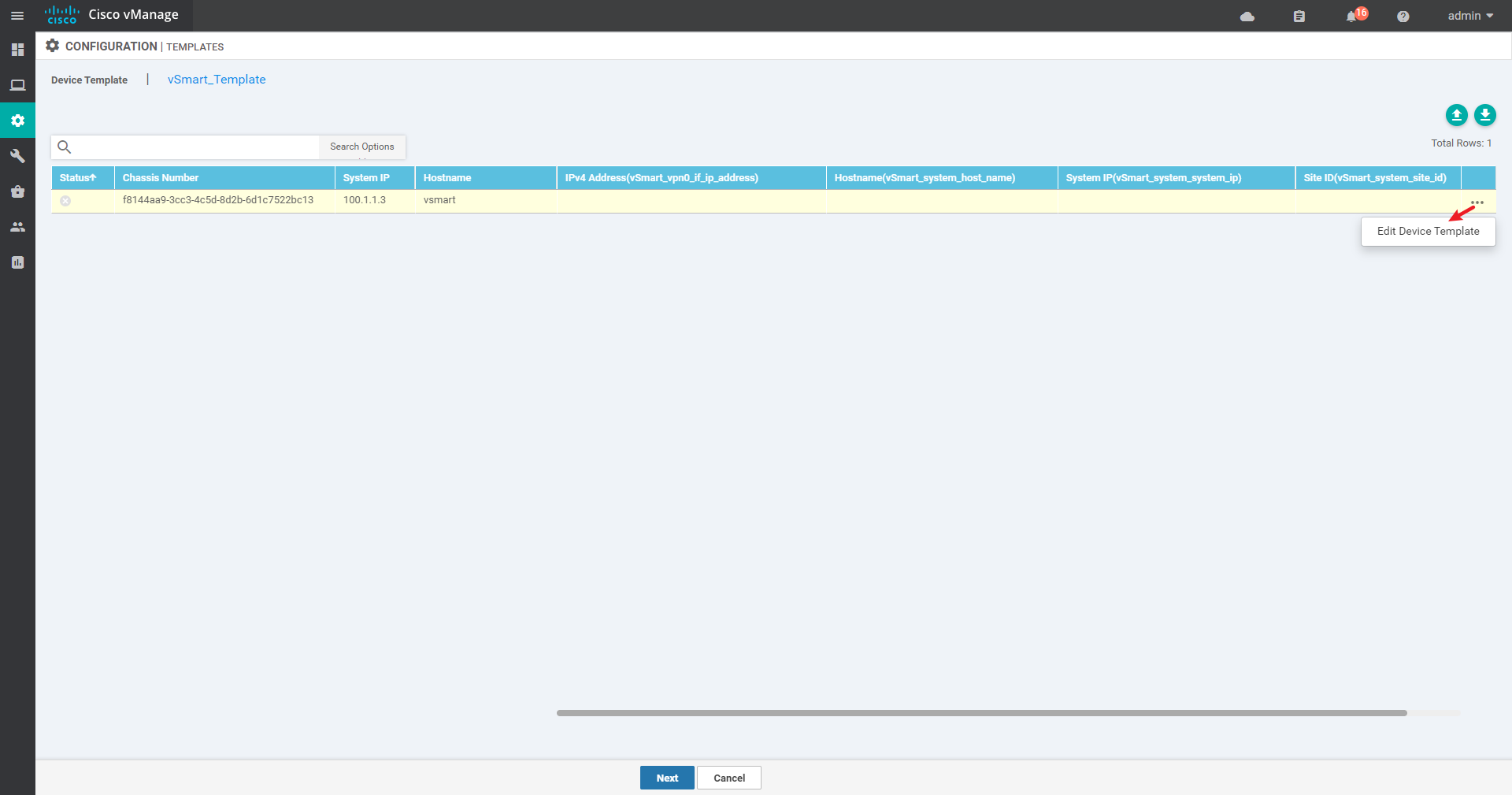
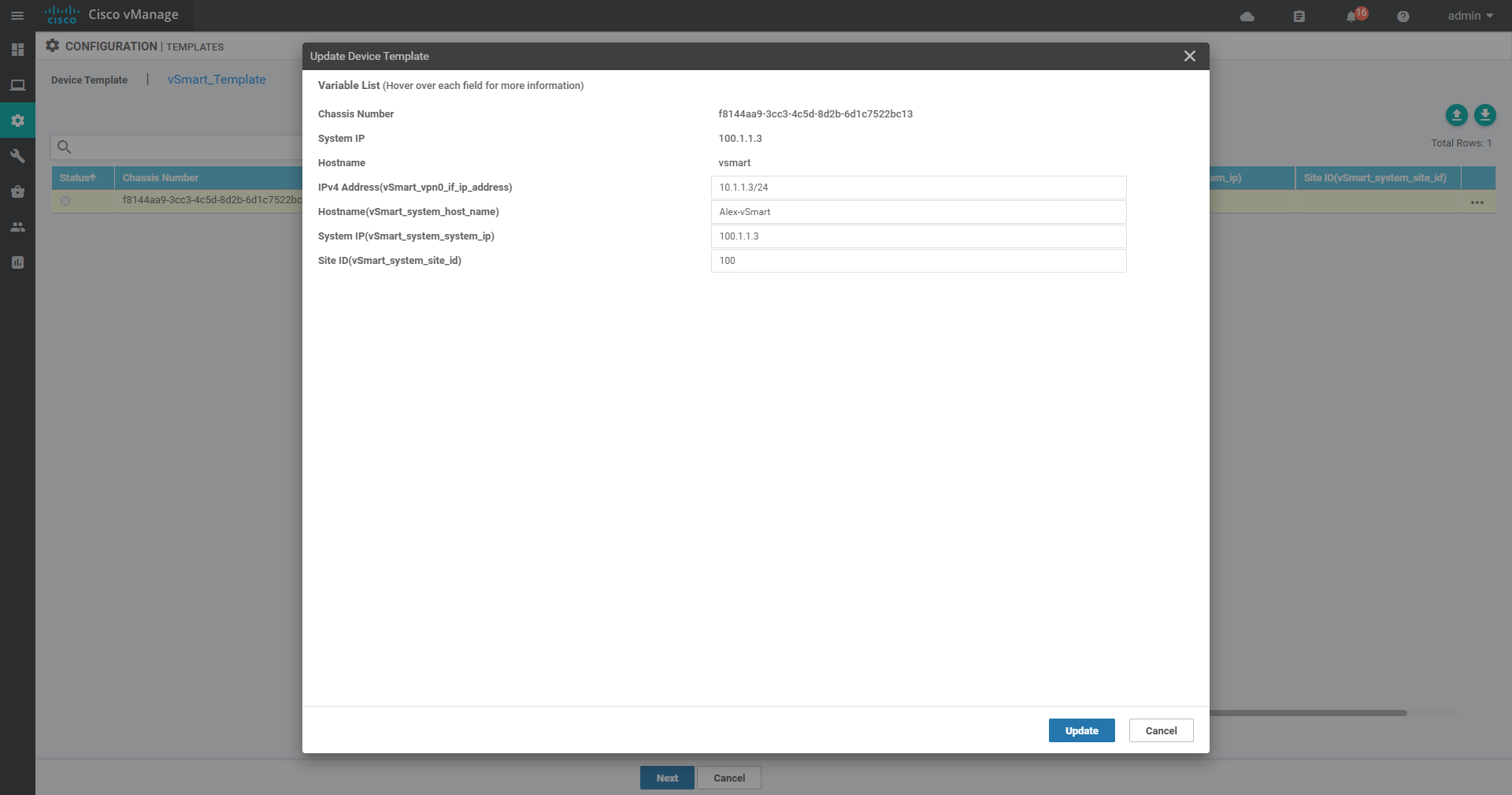
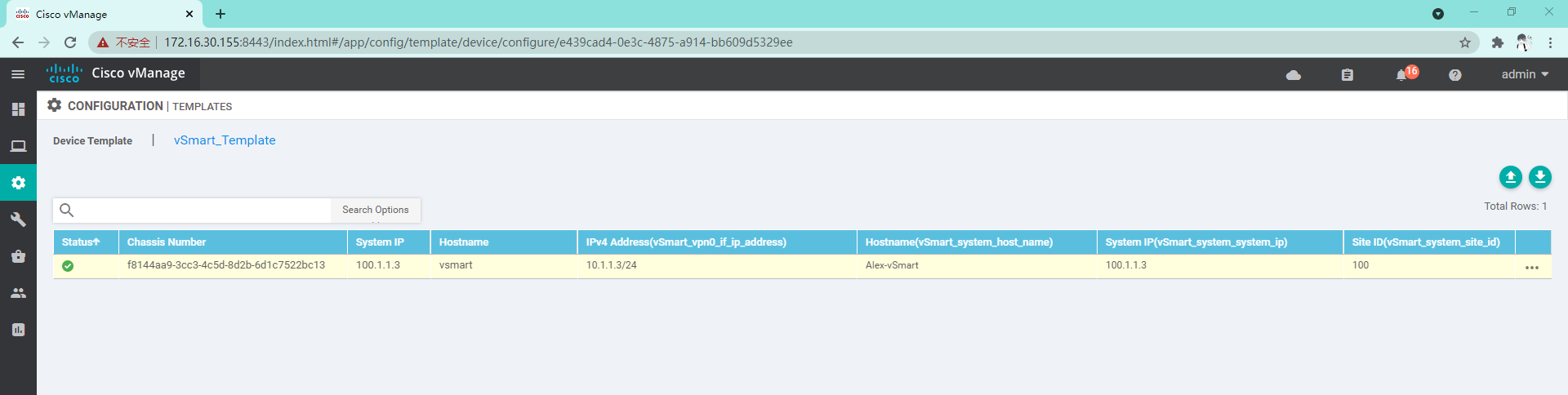
4.2.3 Success
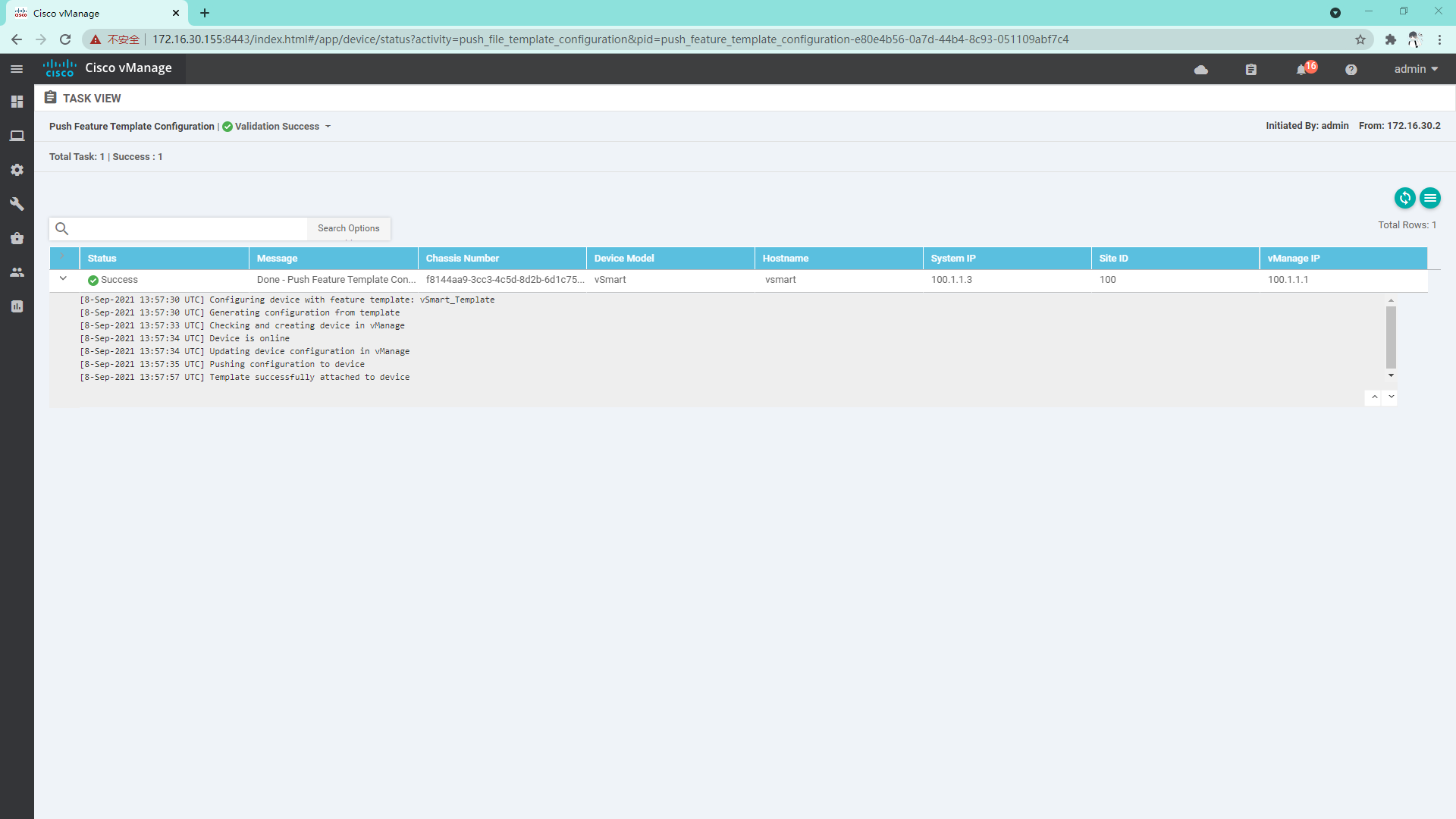
4.2.4 log in to vSmart to view system information
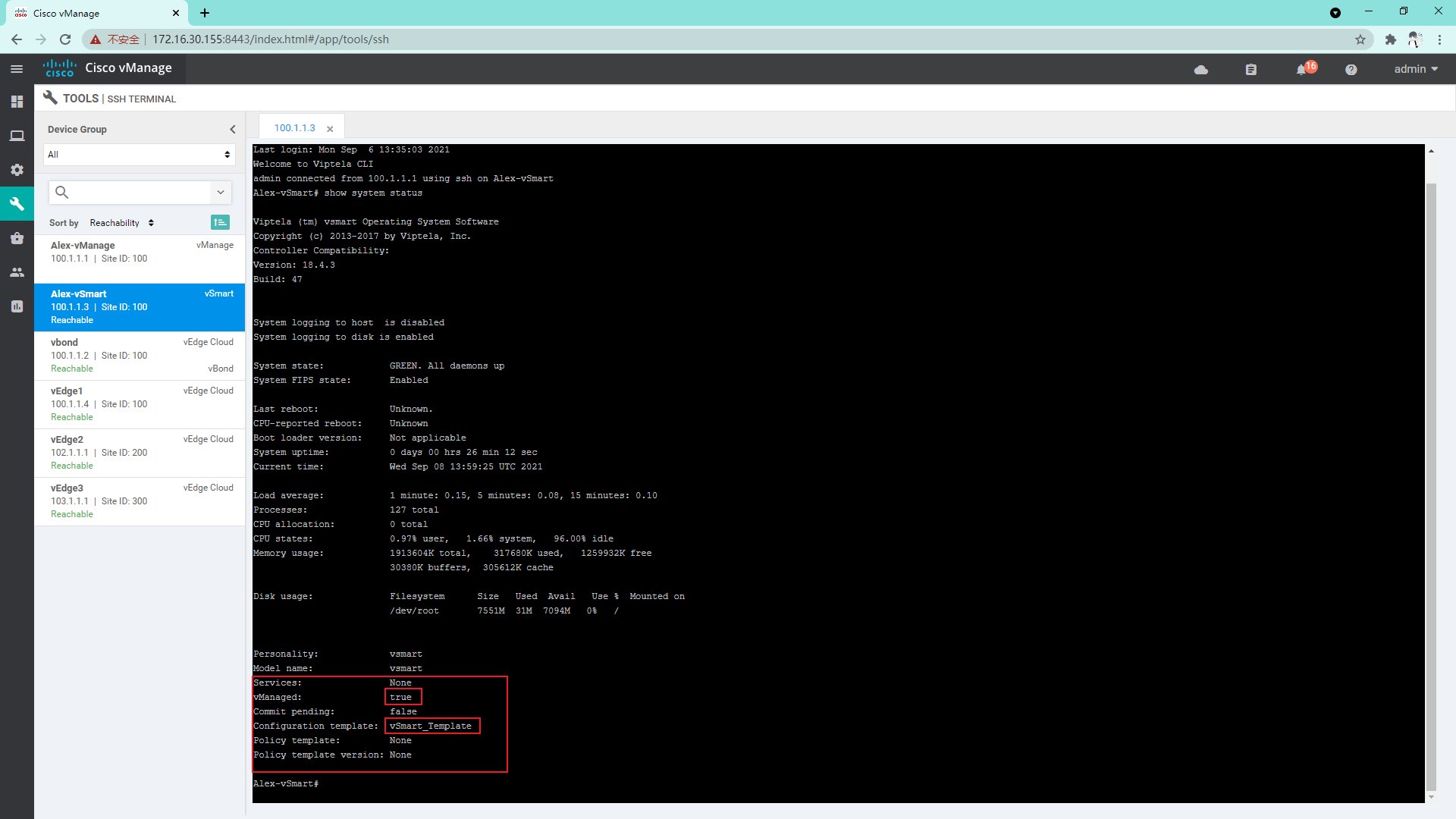
4.2.5 so far, vSmart has been managed by vManage
4.3 pipe laying
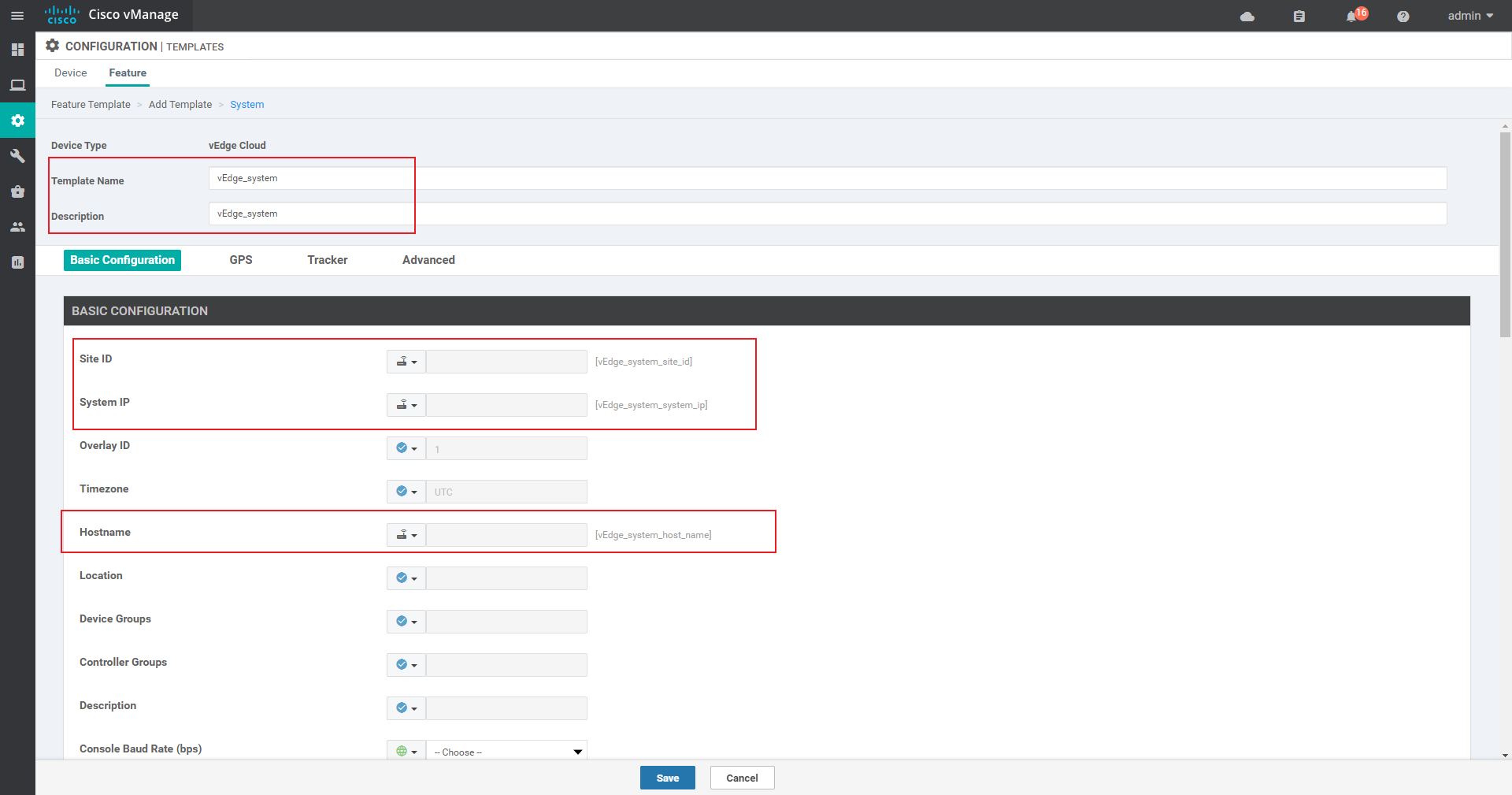
4.3.1 create a system template for vdge
4.3.2 create VPN 0 template for vdge
vEdge1:
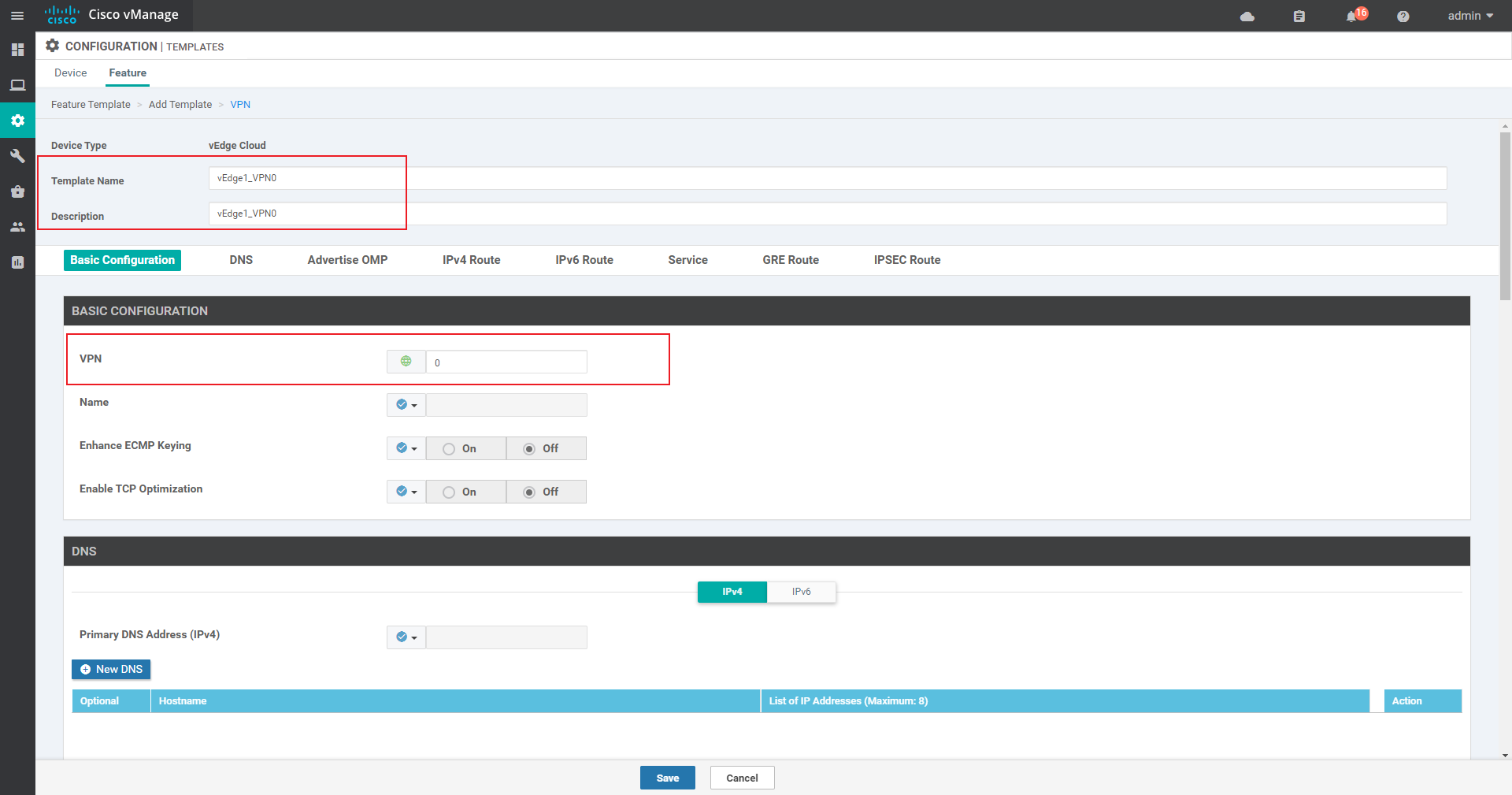
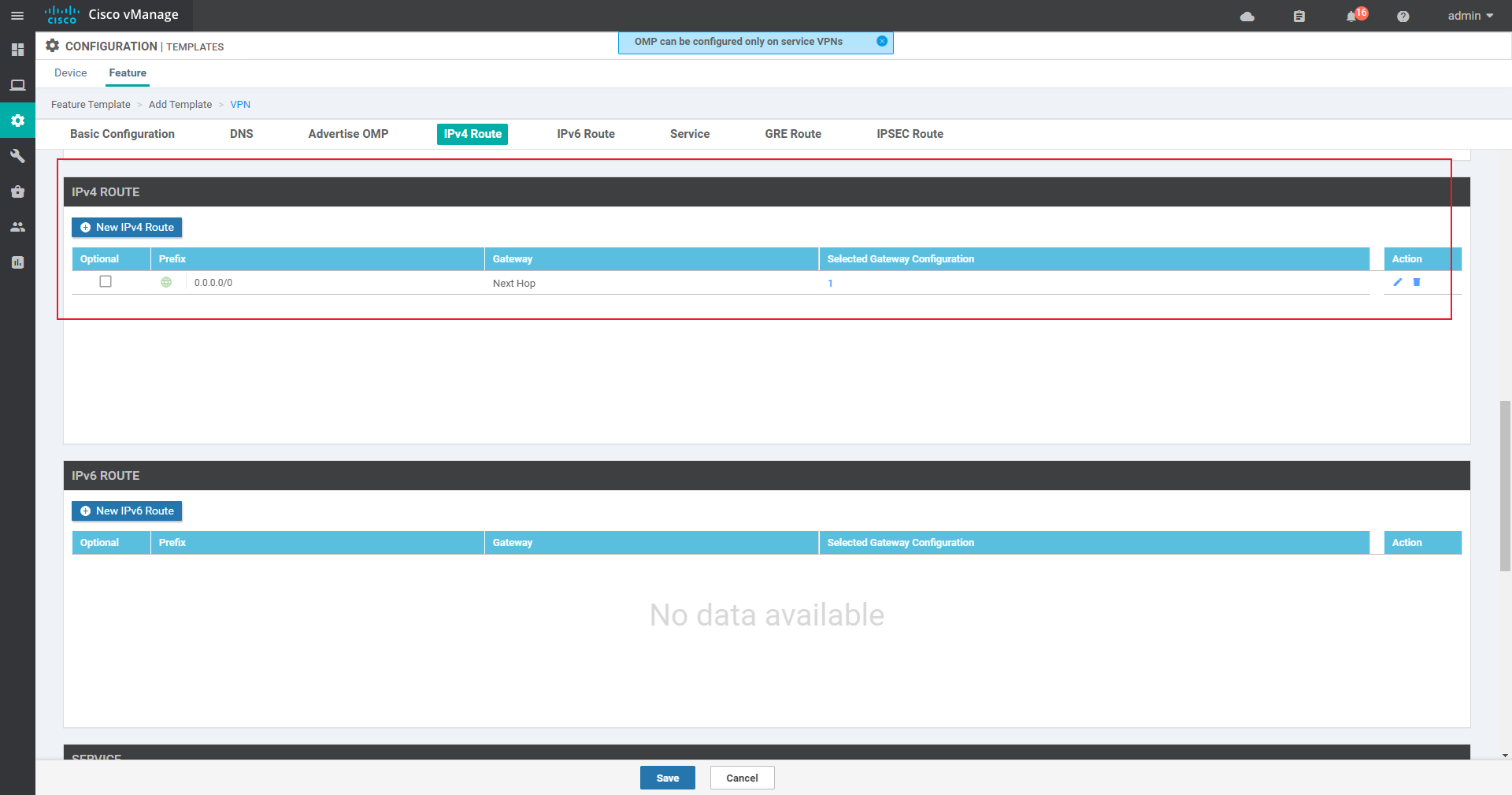
vEdge2 is similar to vEdge3, except that the next hop of IPv4 route is modified, which will not be repeated here;
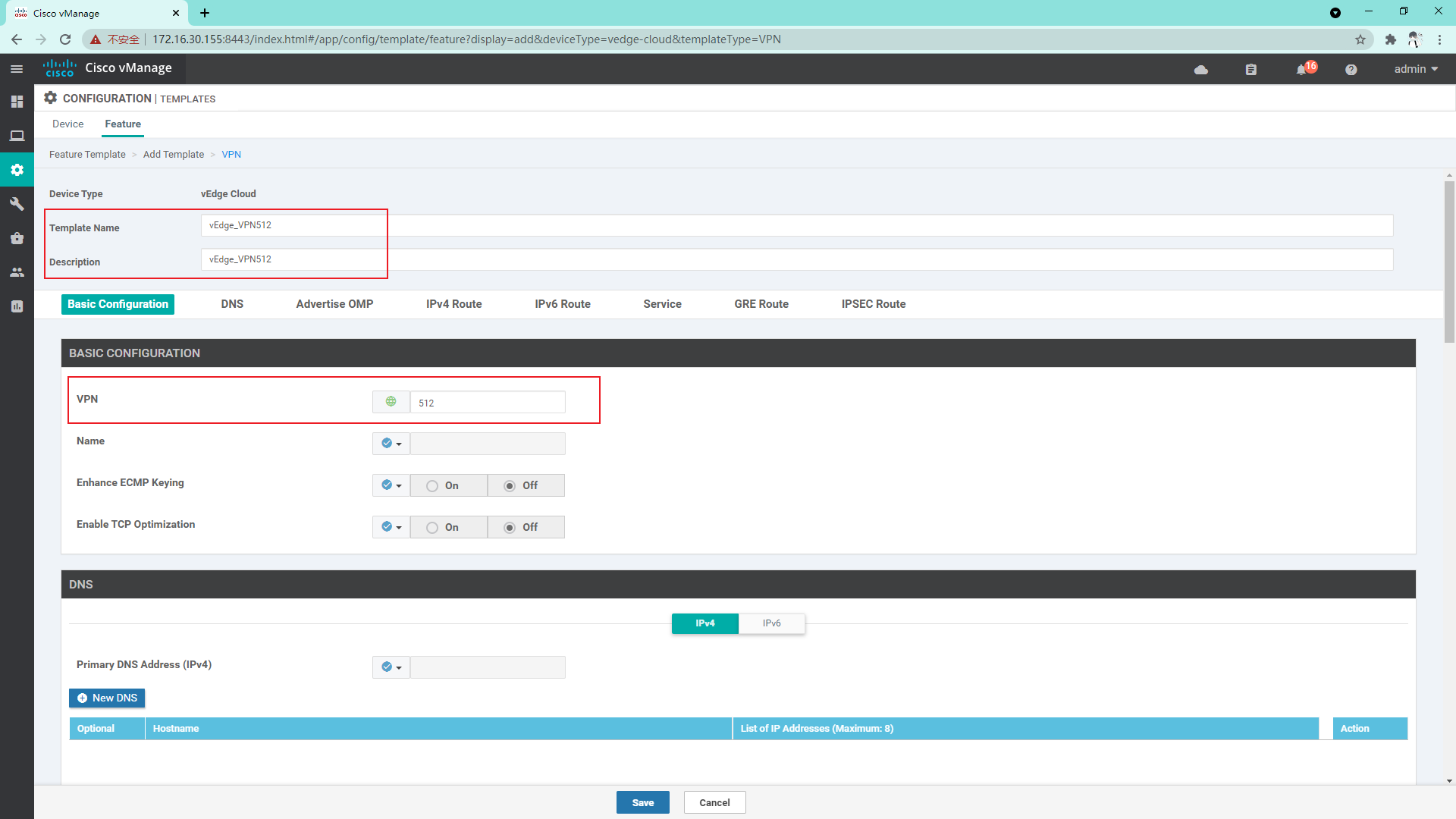
4.3.3 create VPN512 template for vdge
4.3.4 create VPN0 interface template
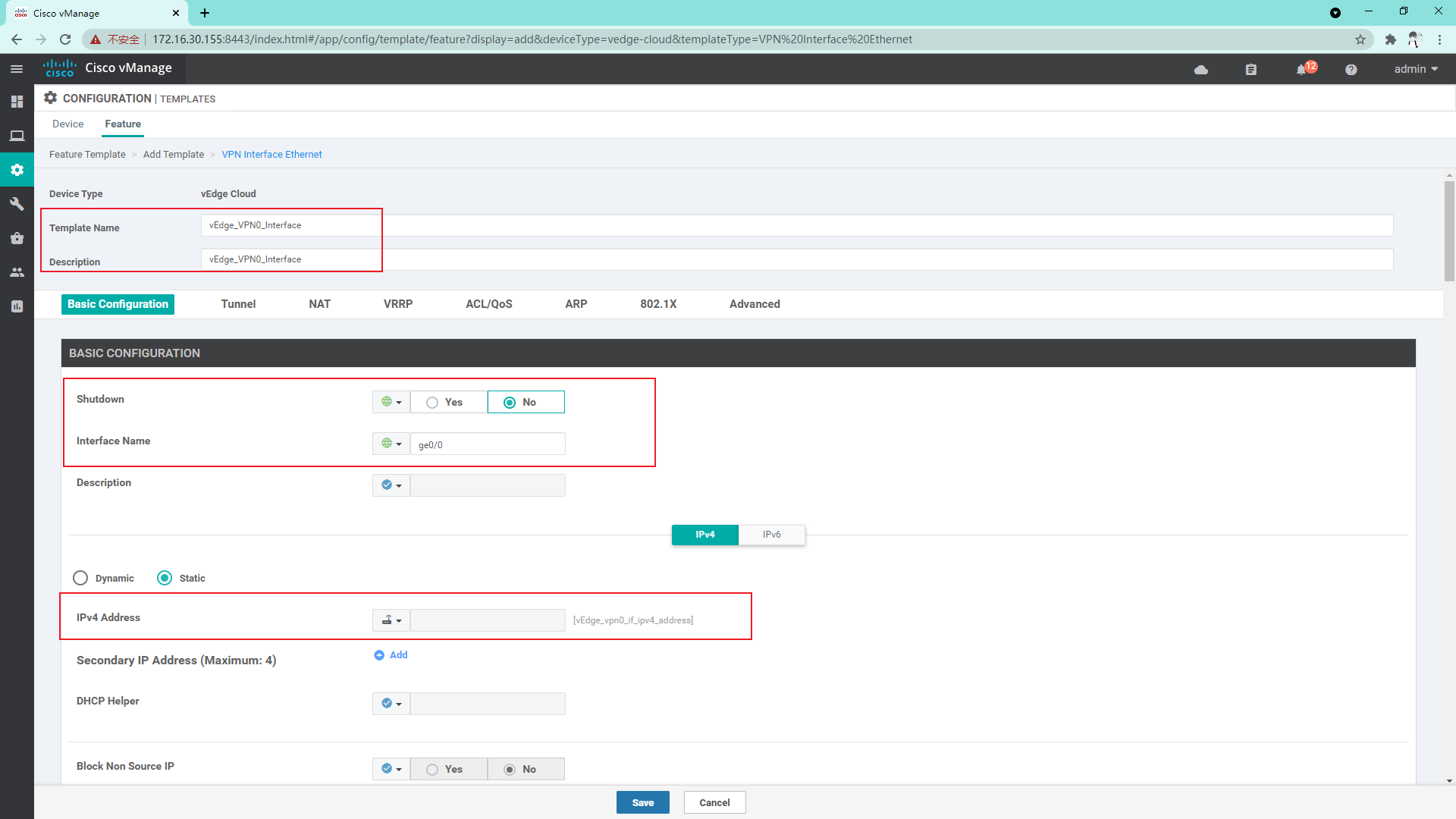
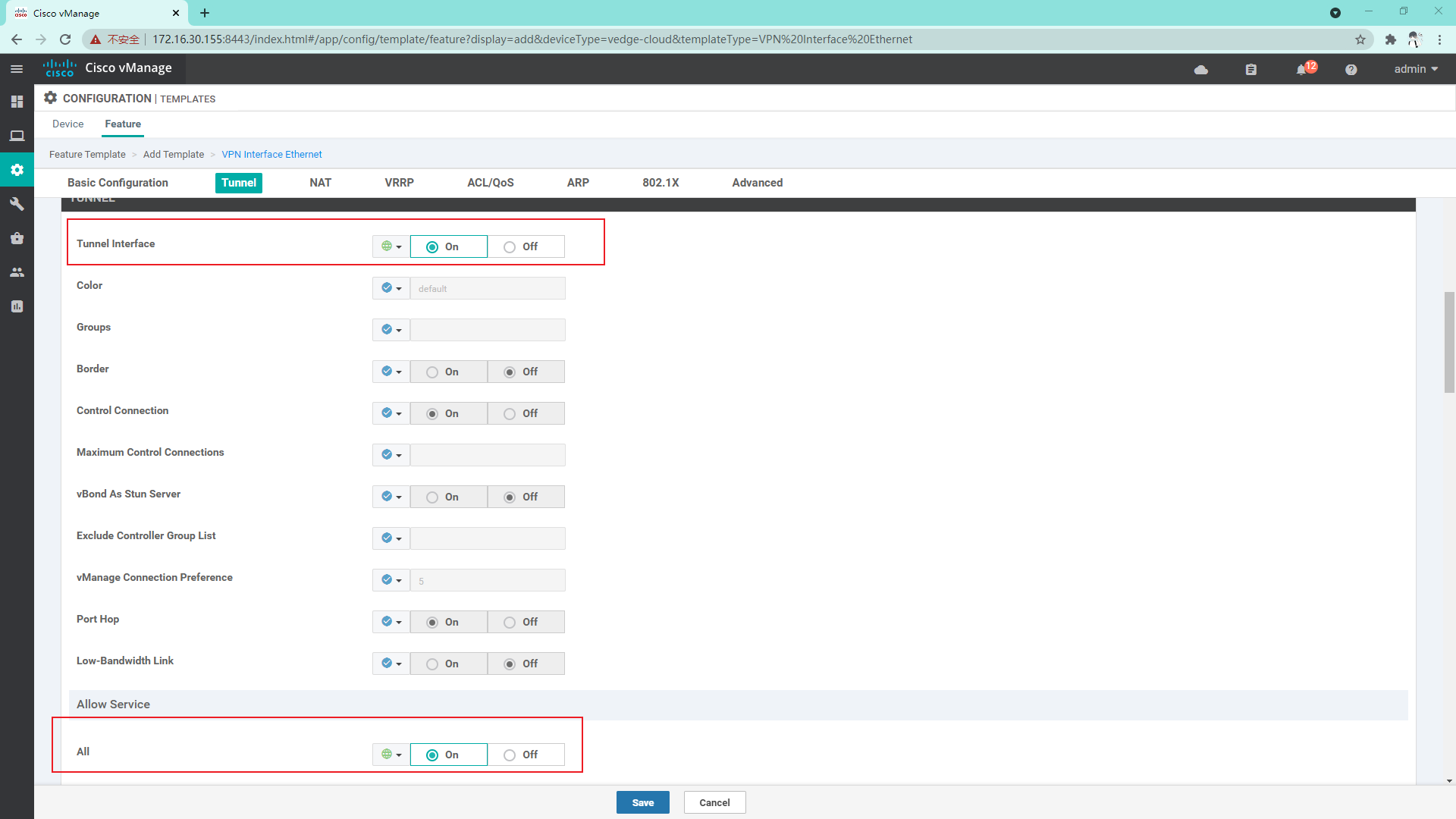
4.3.5 because the service side of the vdge connection uses sub interfaces, it is necessary to divide the physical interfaces into VPN0 templates. Here, it is necessary to create a service side physical interface template
4.3.6 create VPN512 interface template
4.3.7 create an OMP template (note that there is no IPv6 in the current network, so it needs to be turned off here, and IPv4 can be used by default)
4.3.8 create service side VPN template
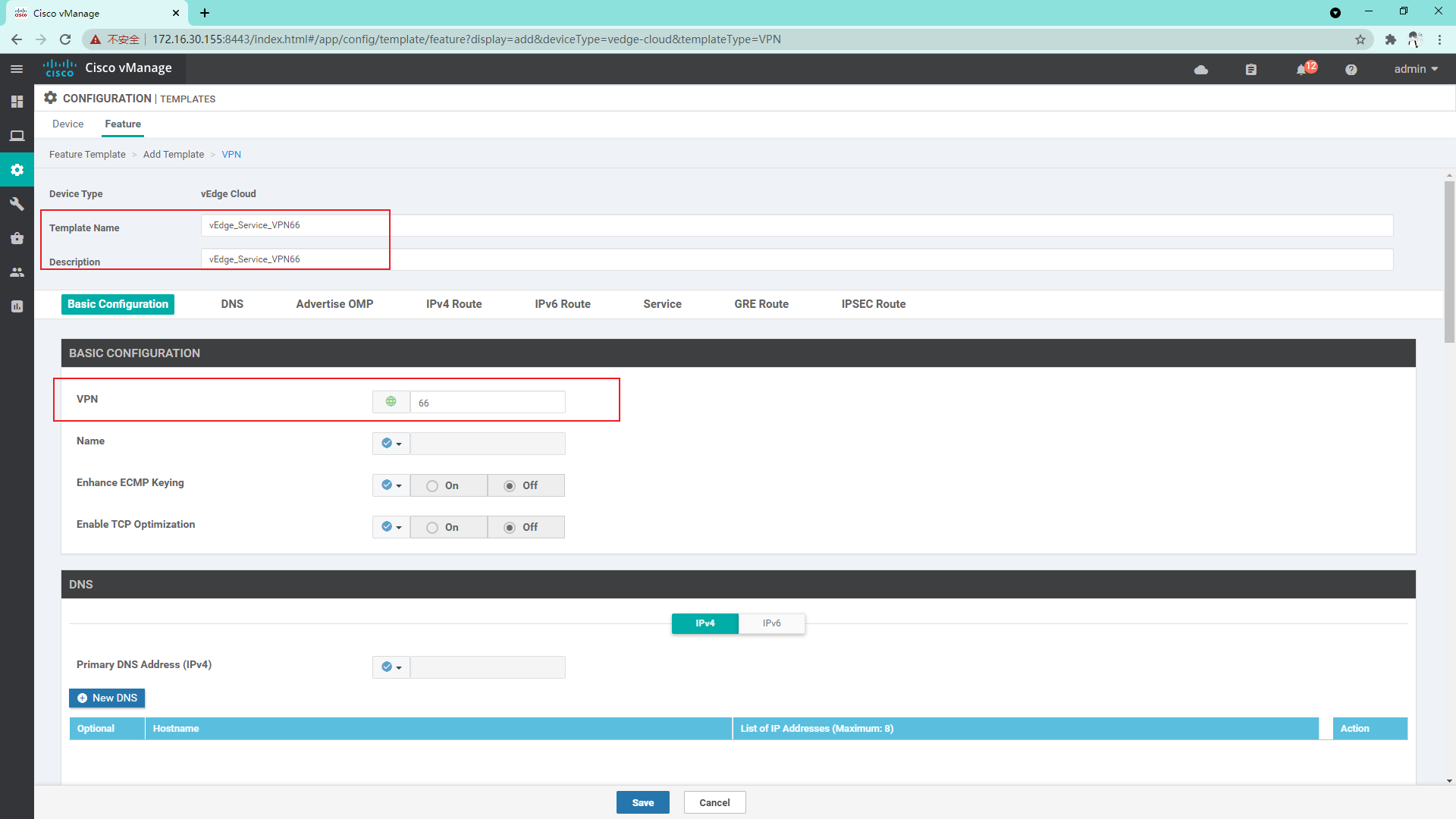
4.3.9 create Interface template for Service VPN66
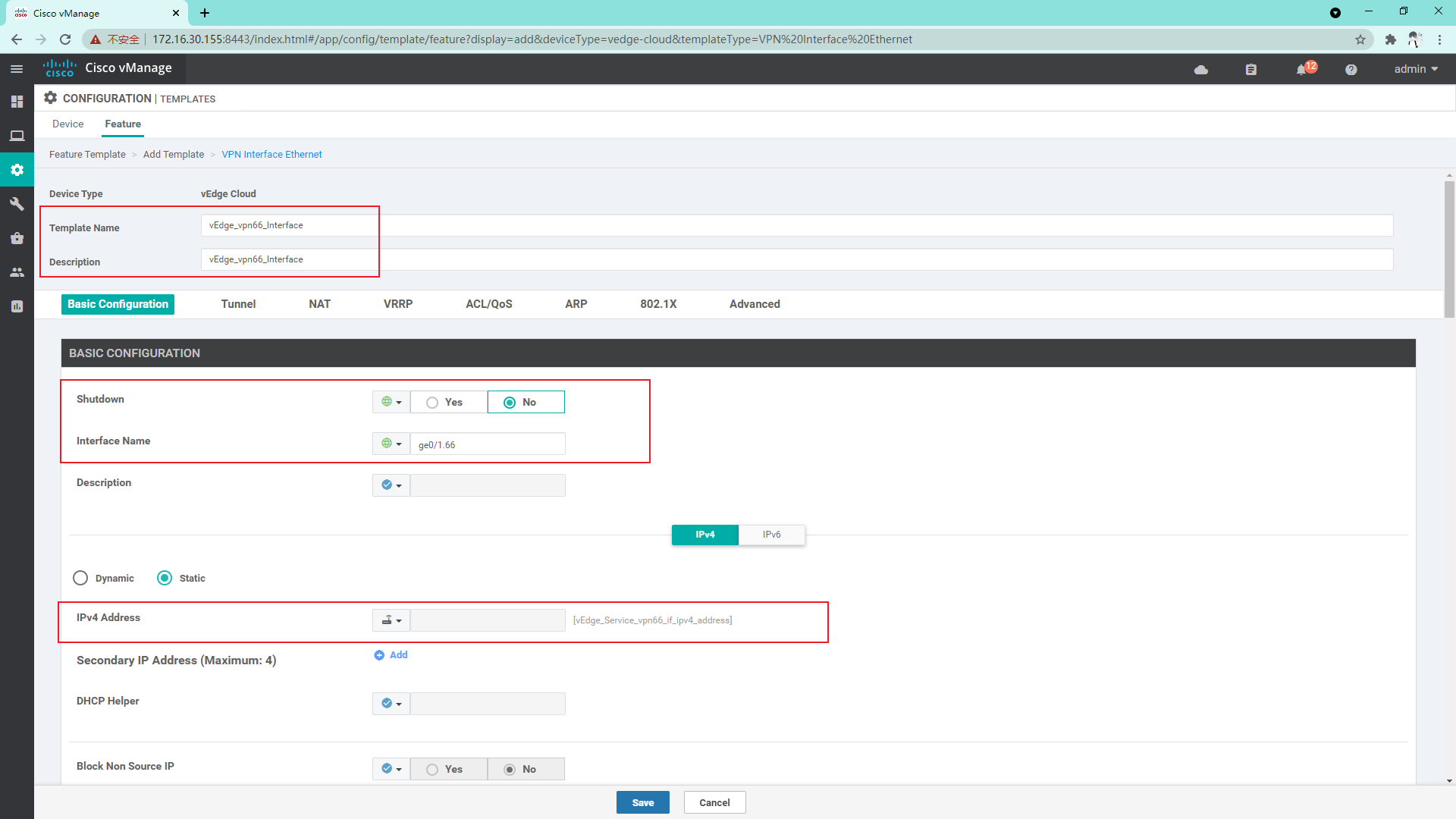
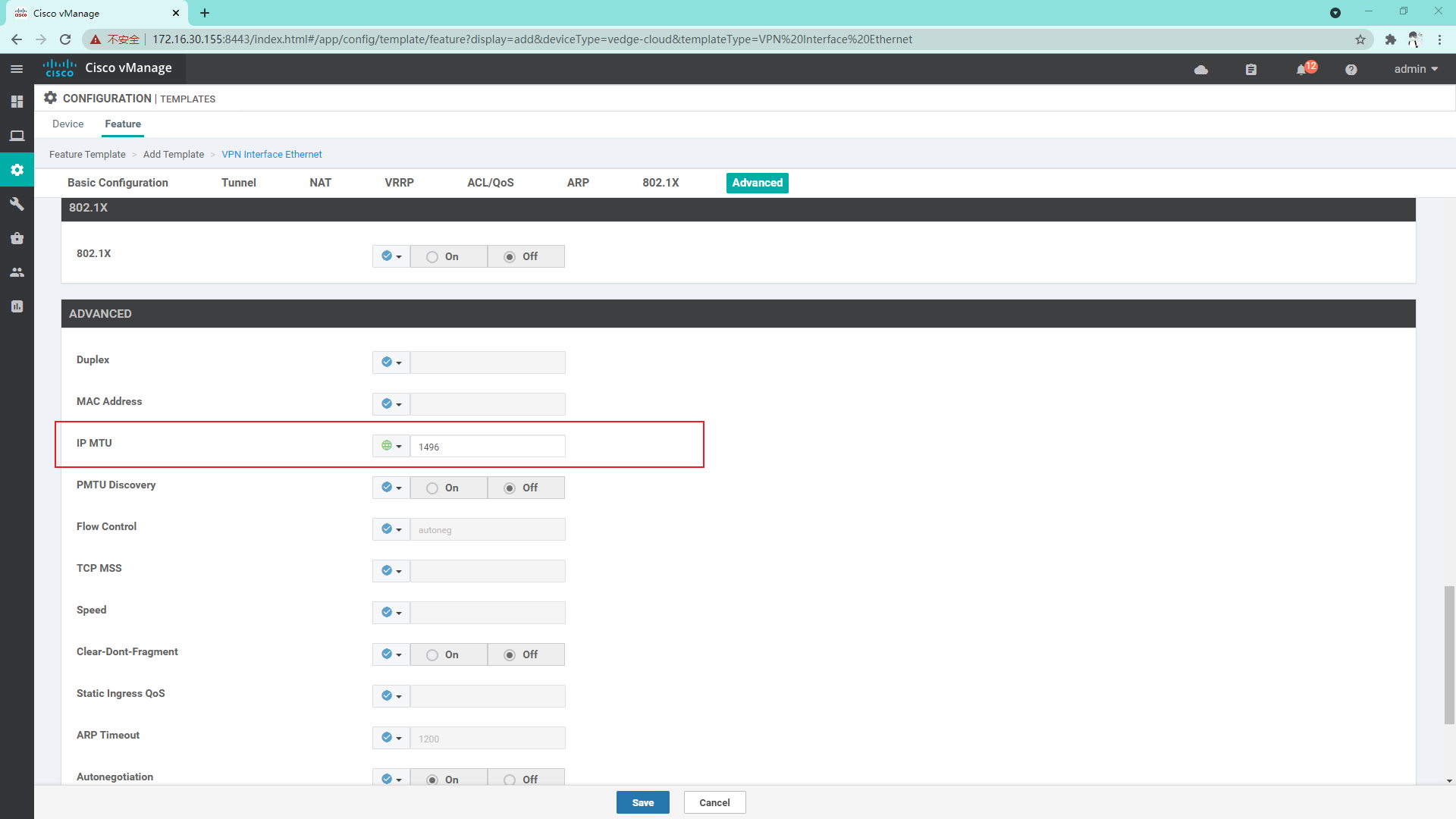
4.3.10 create OSPF template on Service side
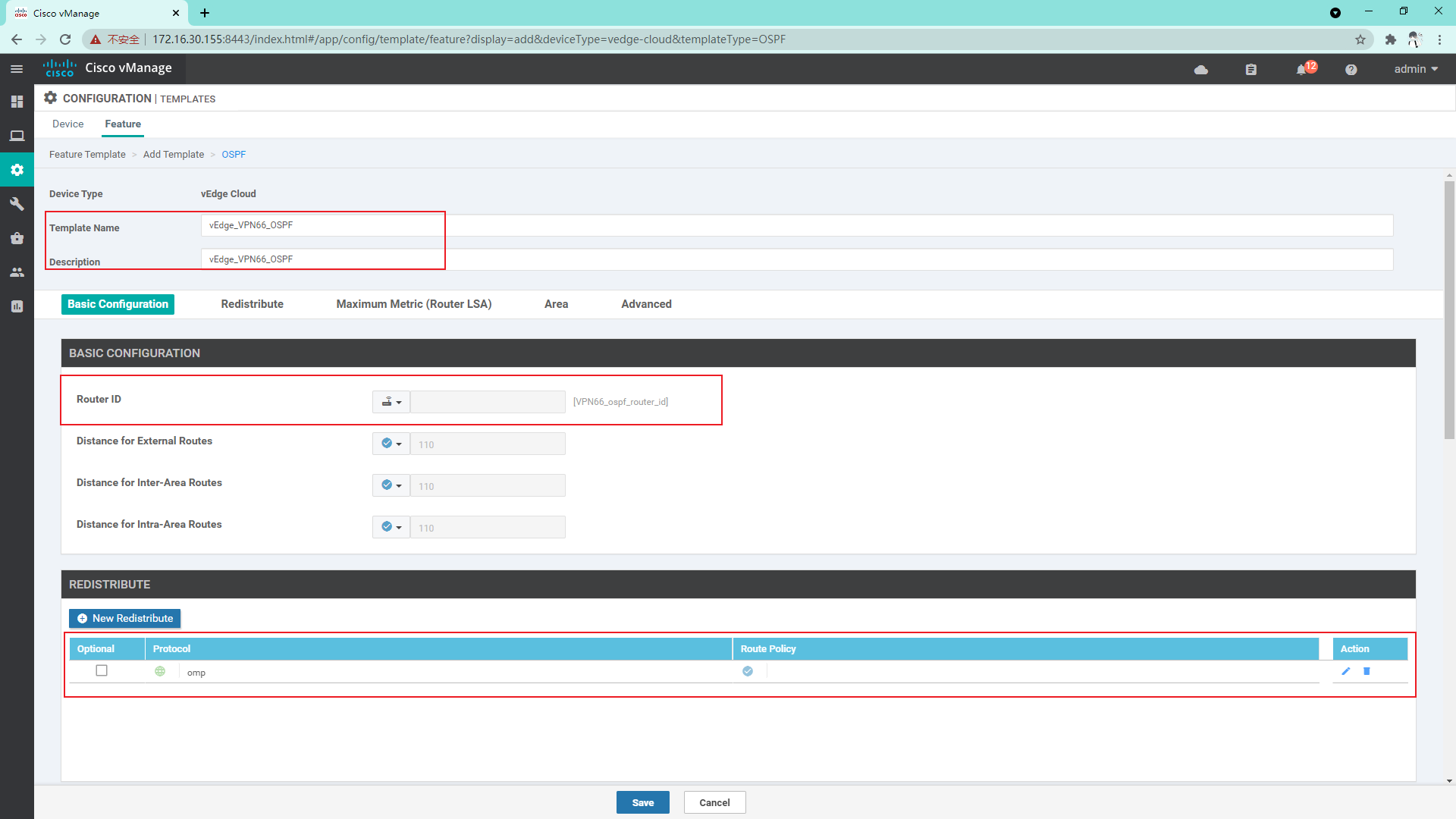
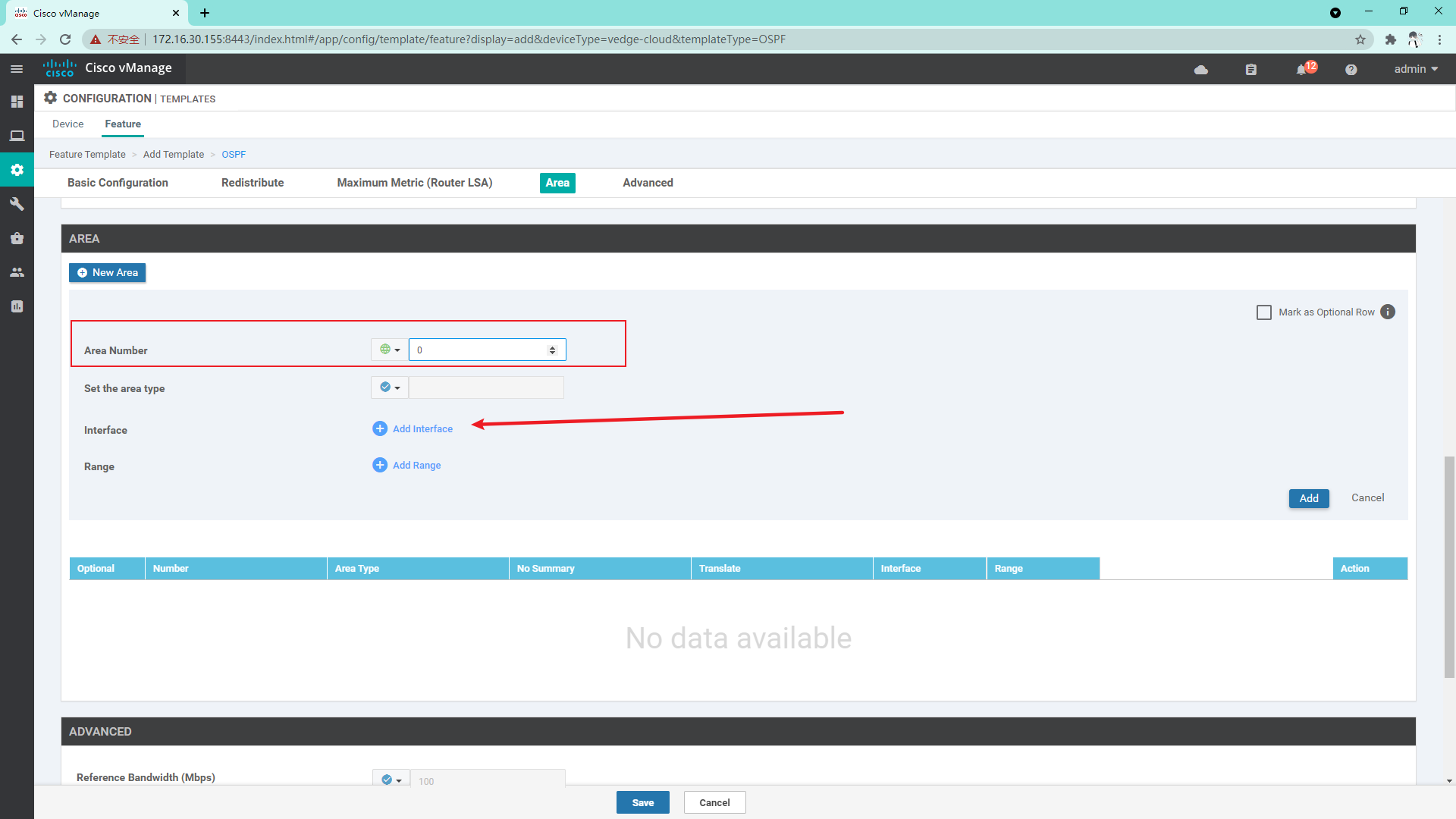
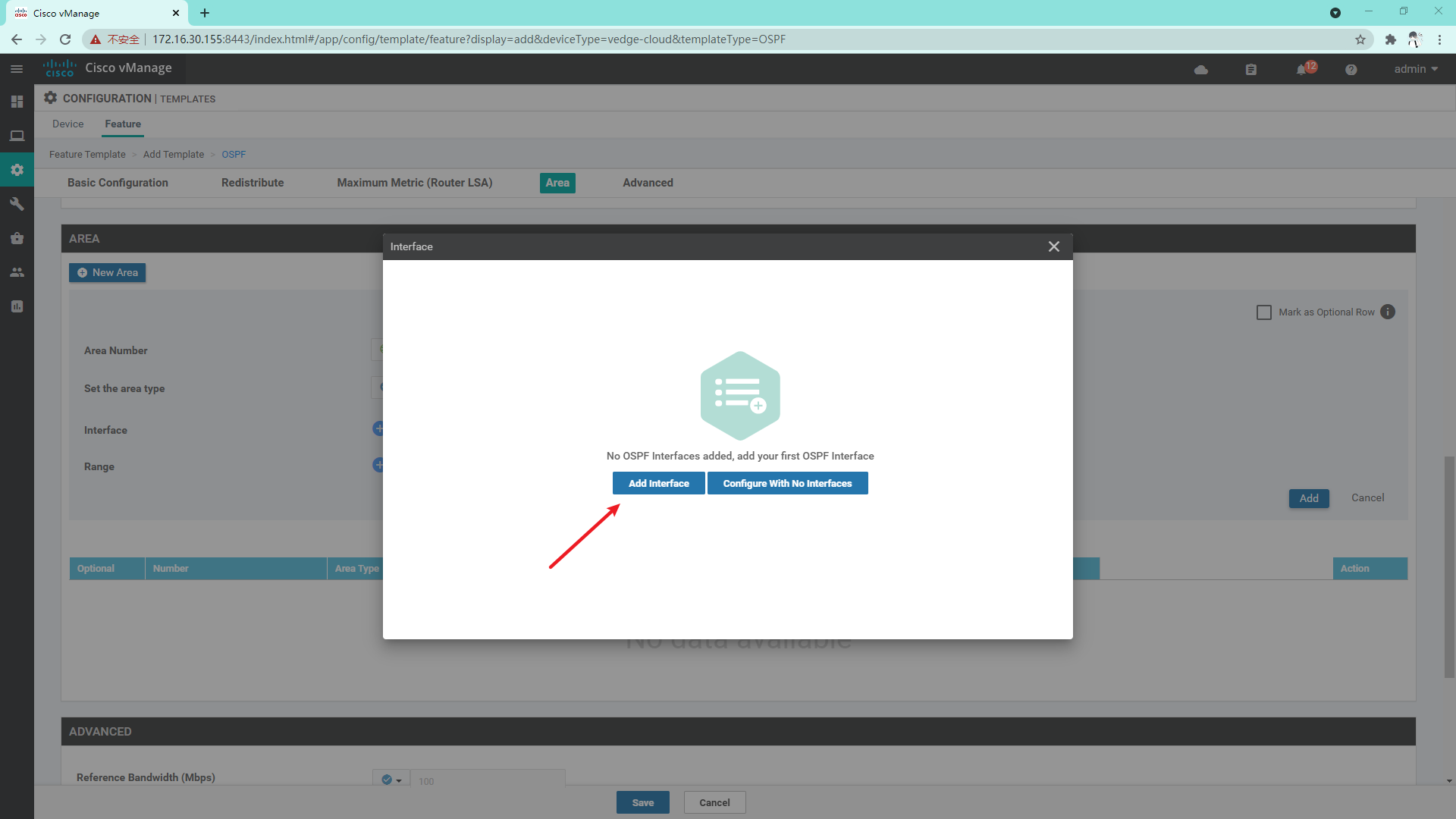
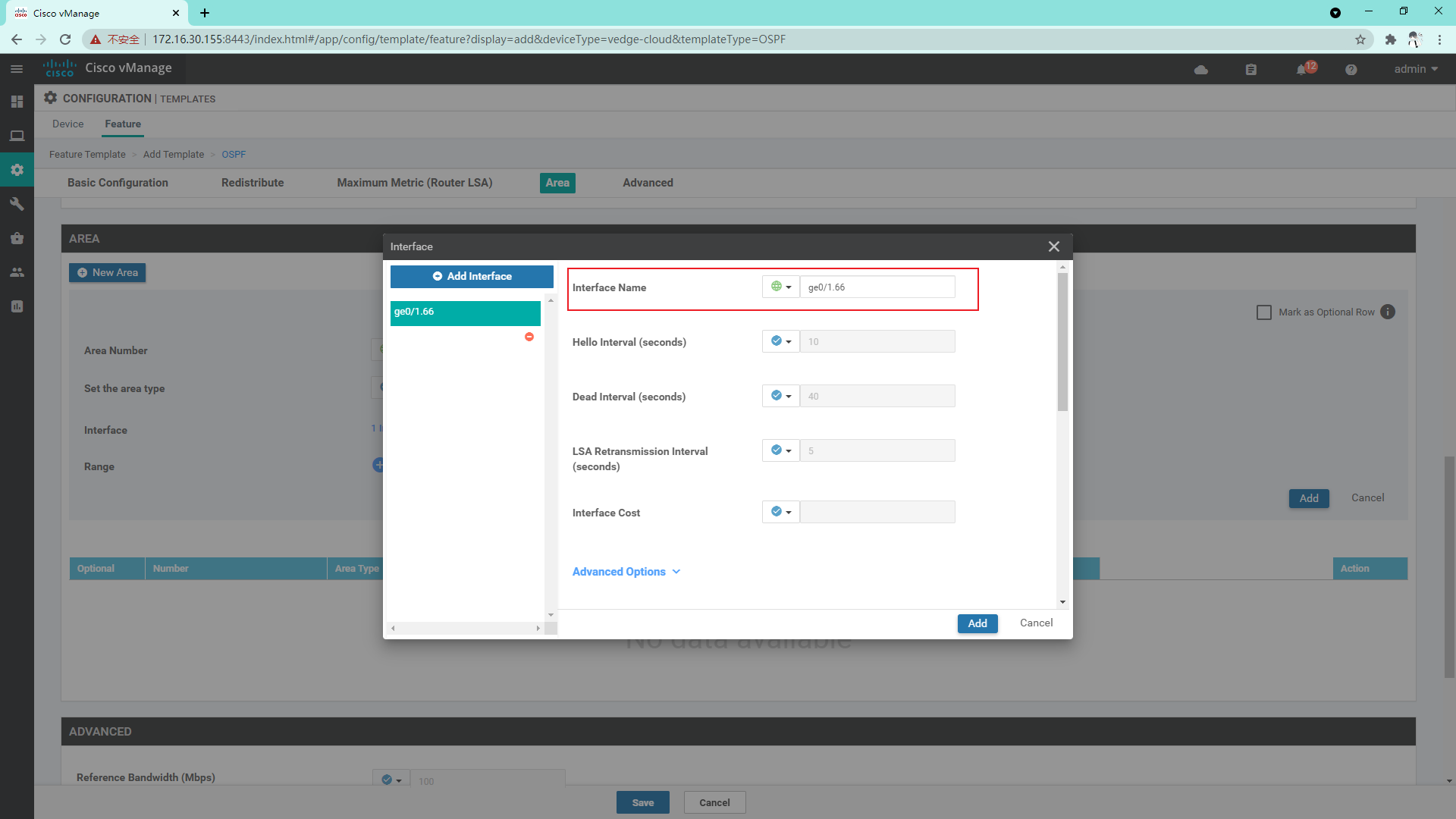
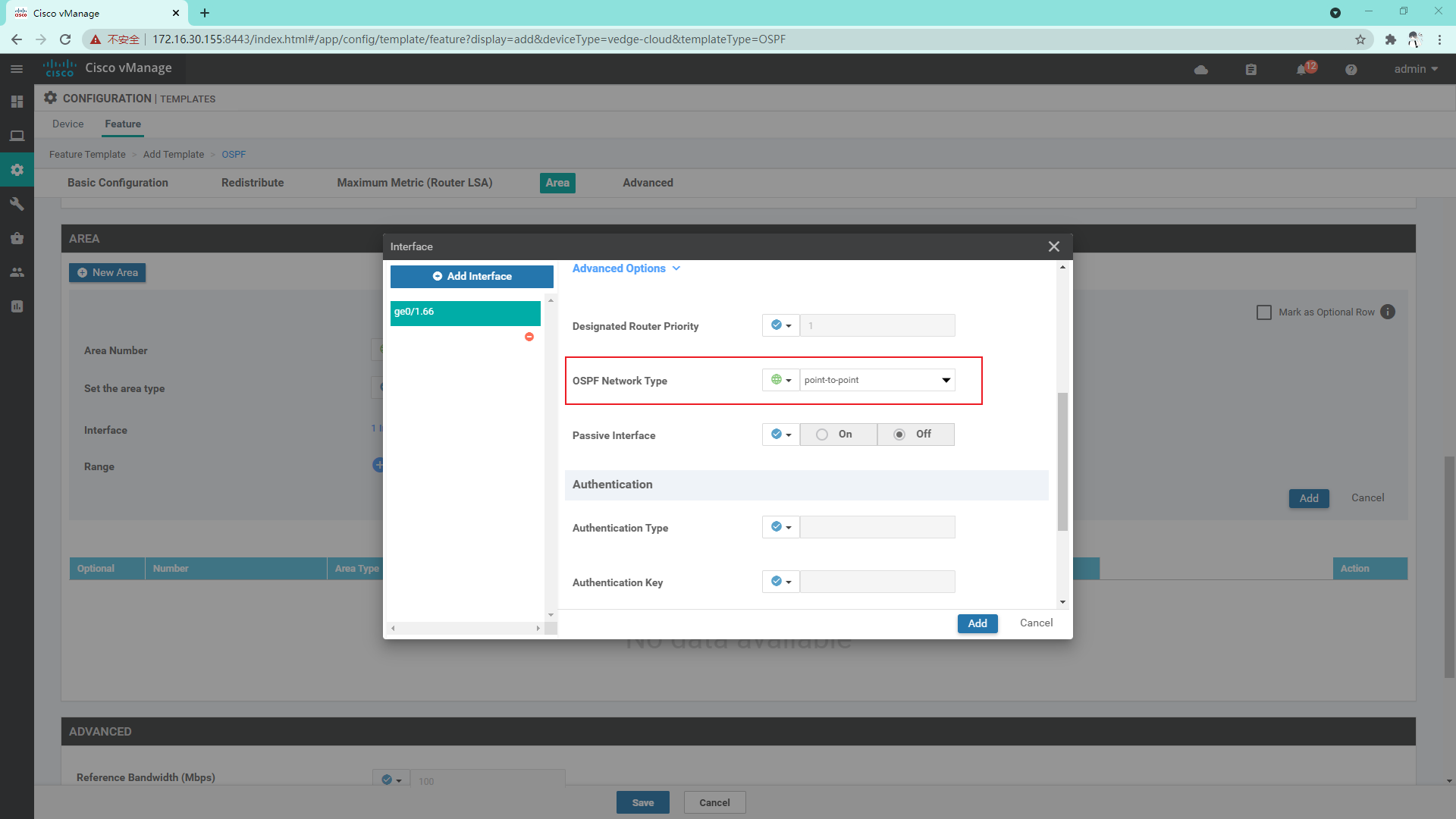
4.3.11 so far, the vdge template has been created and the Device template has been created
vEdge1:
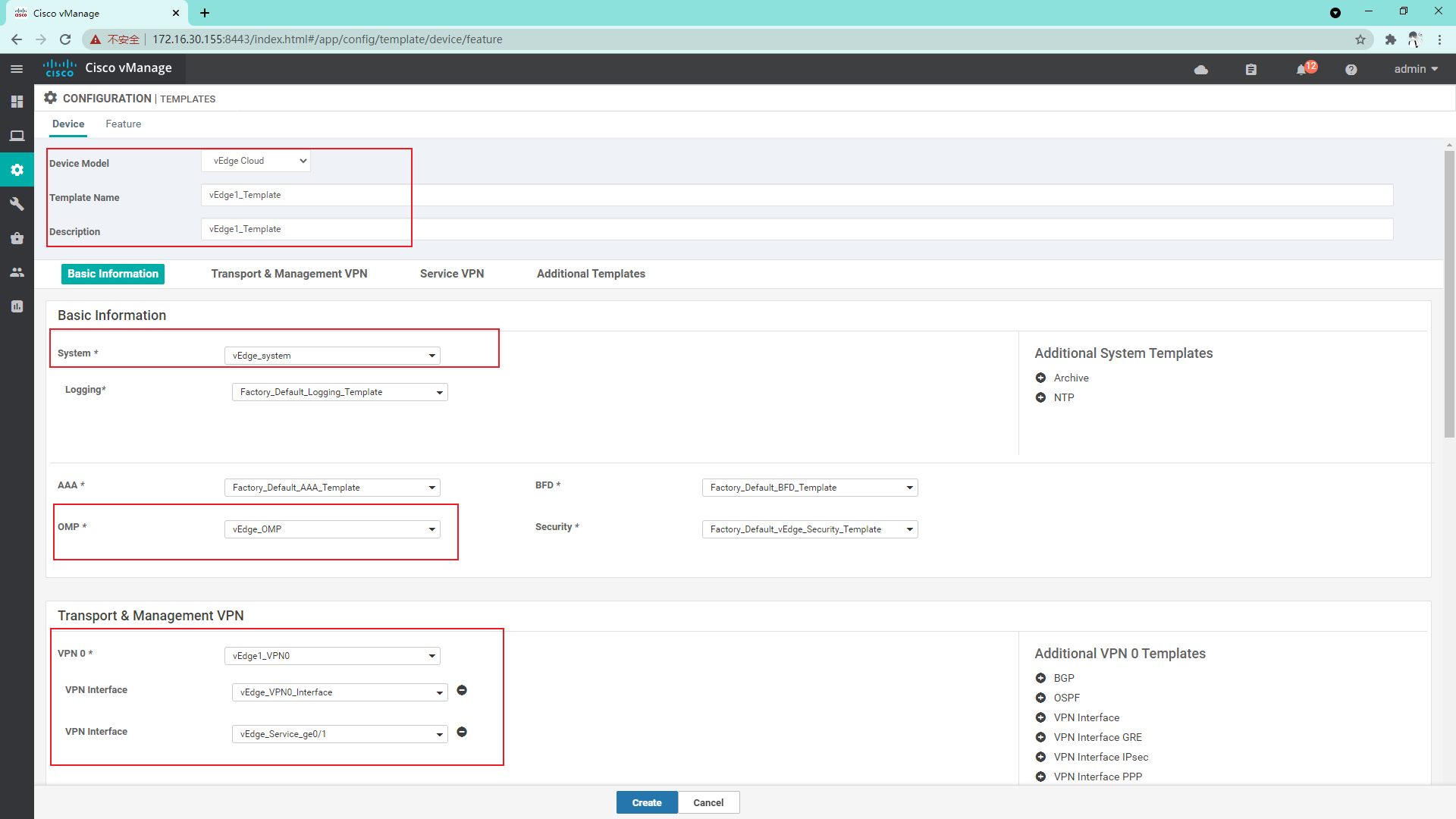
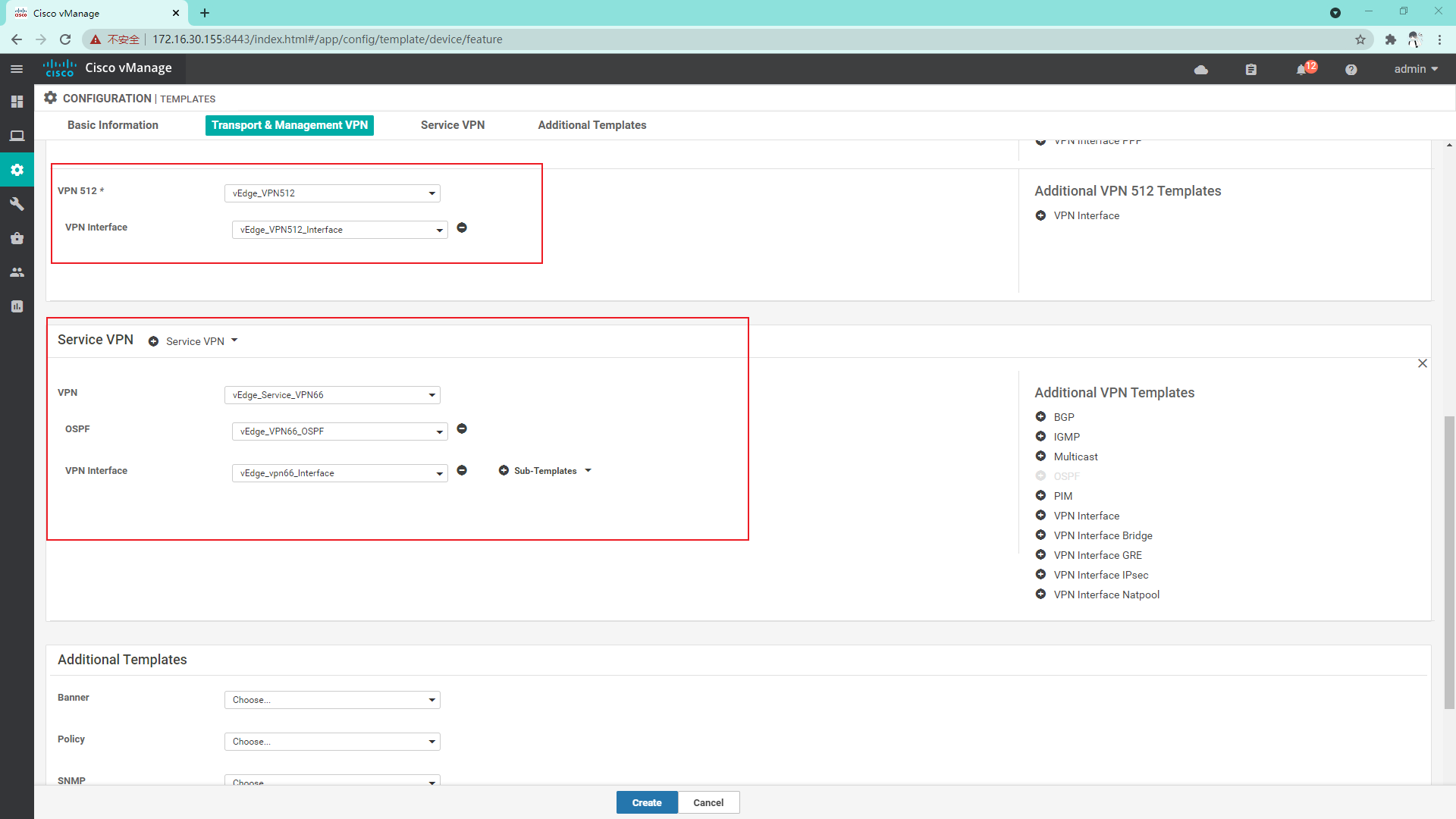
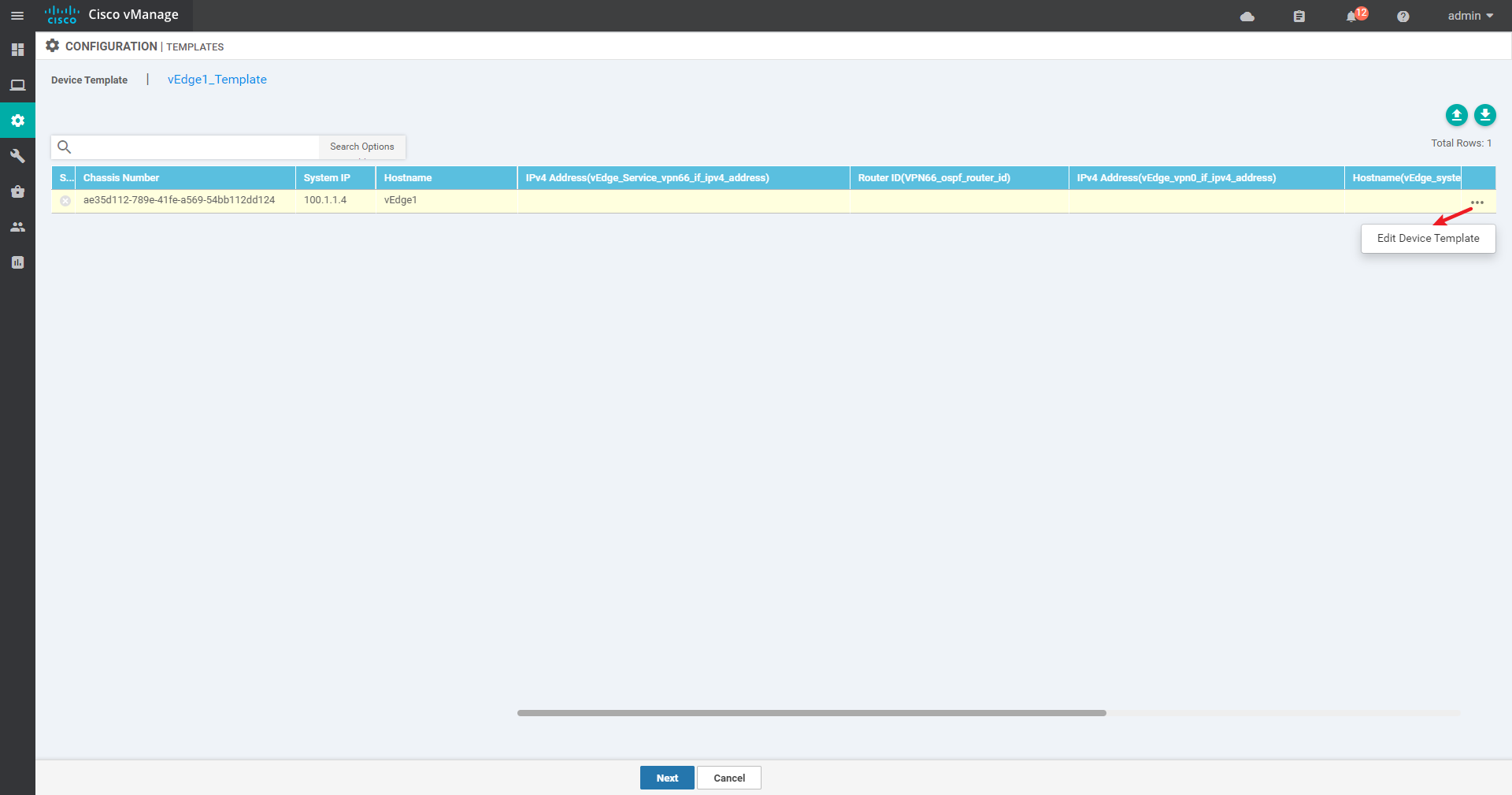
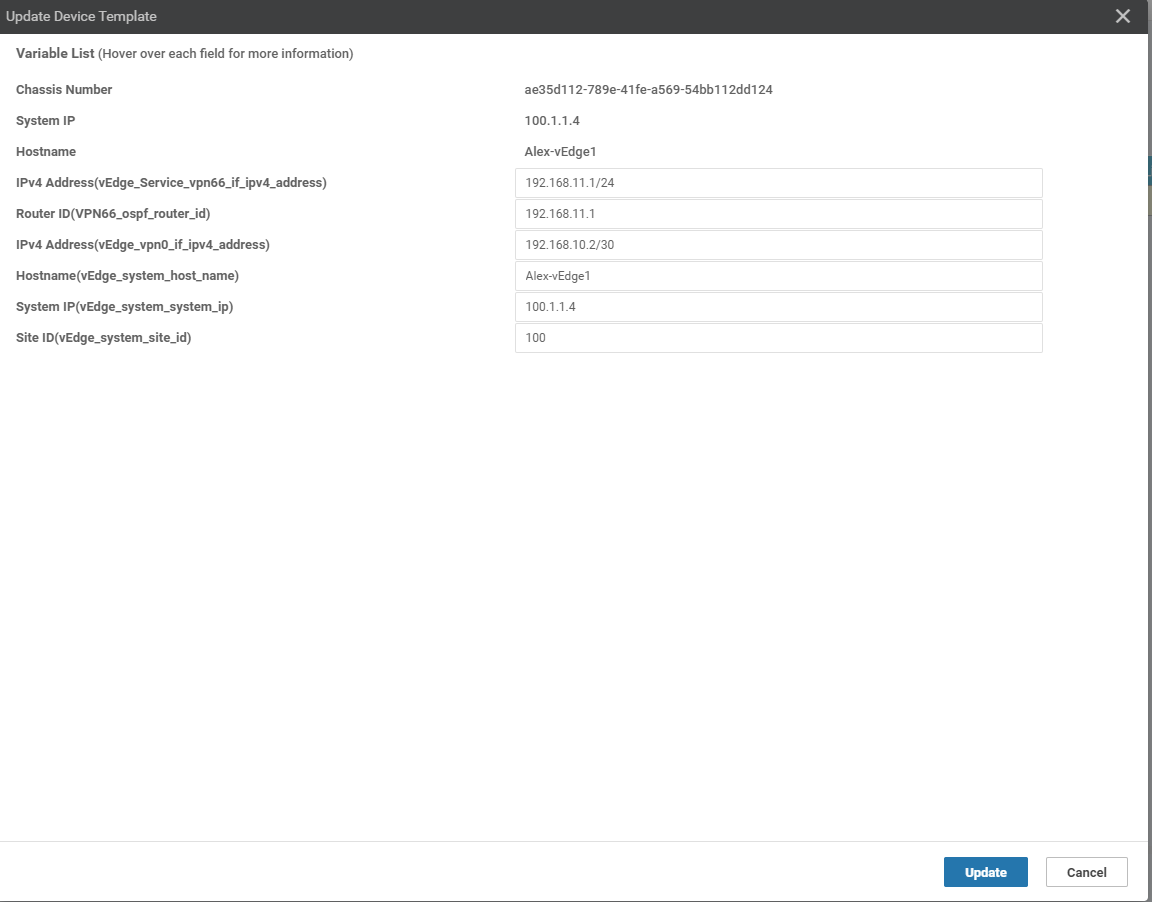
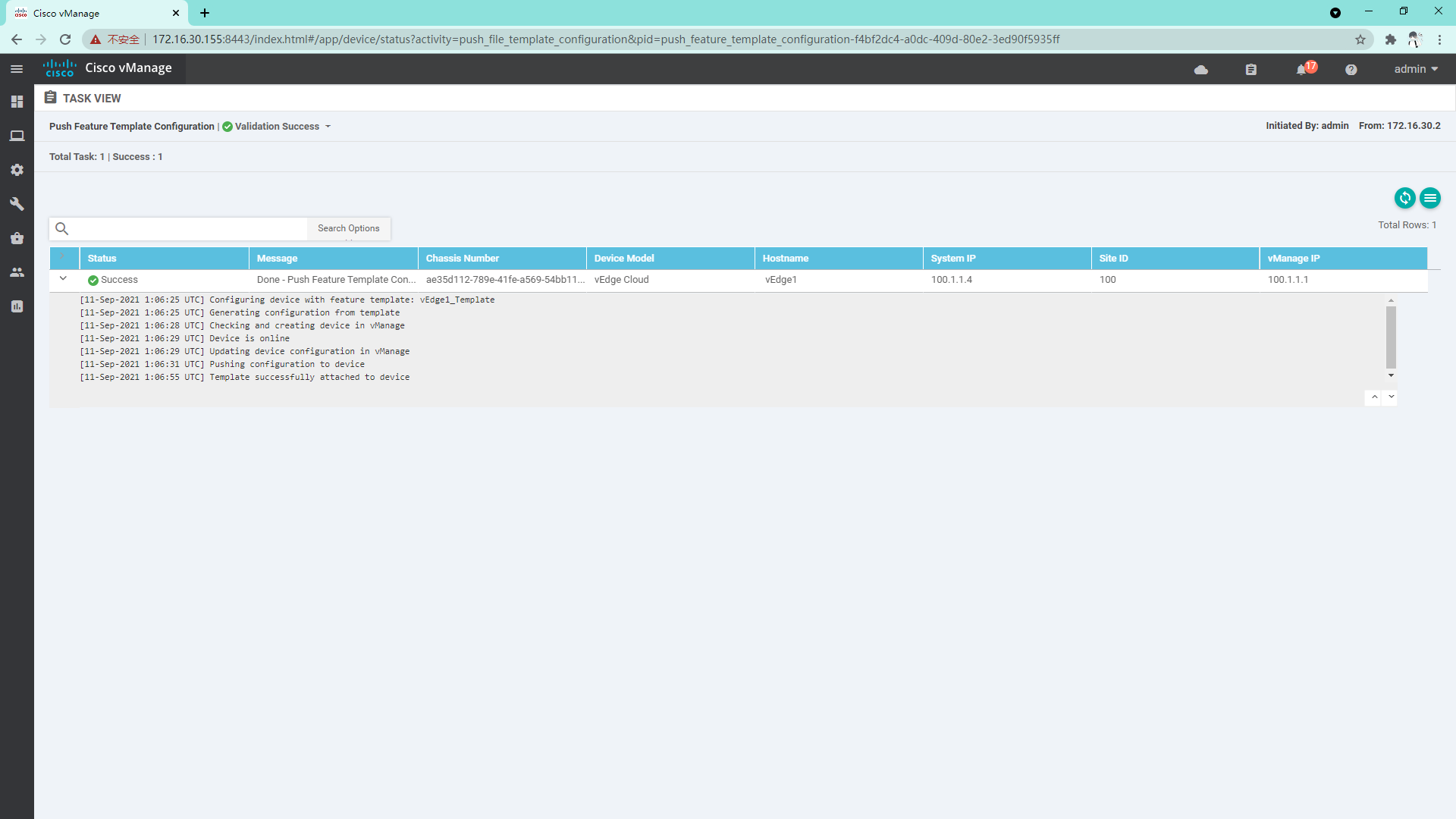
vEdge2 and vEdge3 are similar to vEdge1 and will not be repeated here;
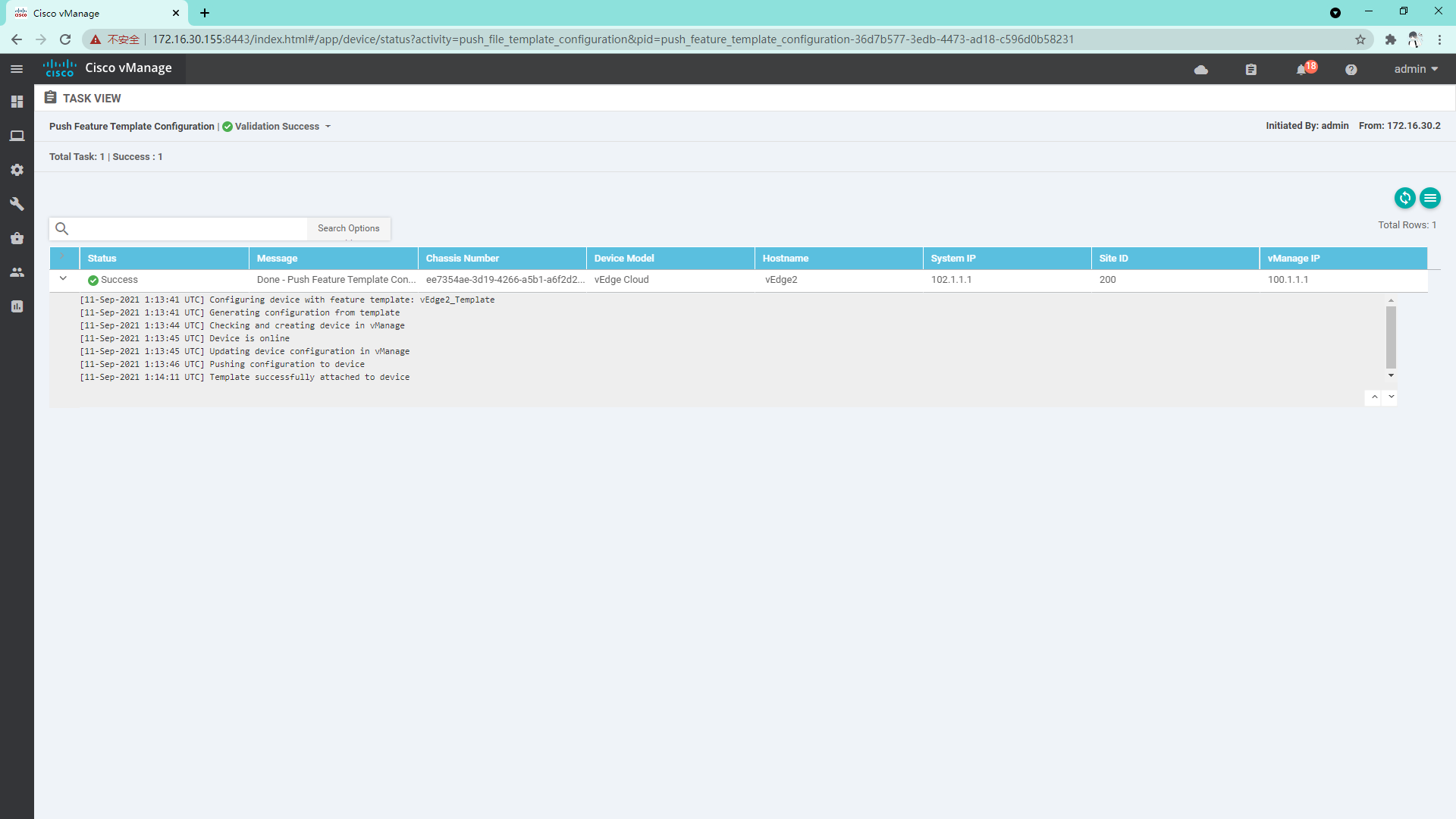
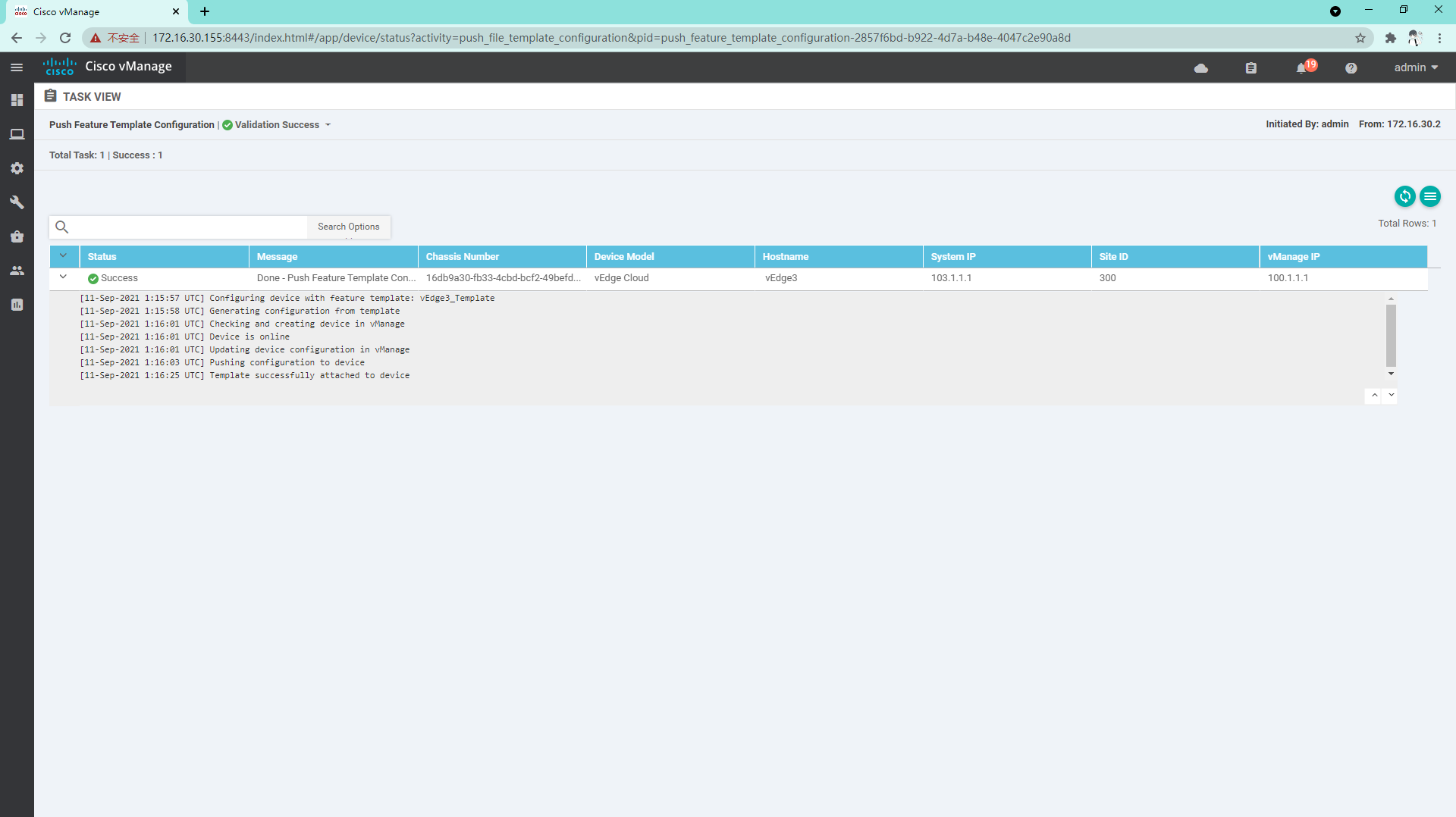
4.3.12 log in to vdge to view system information
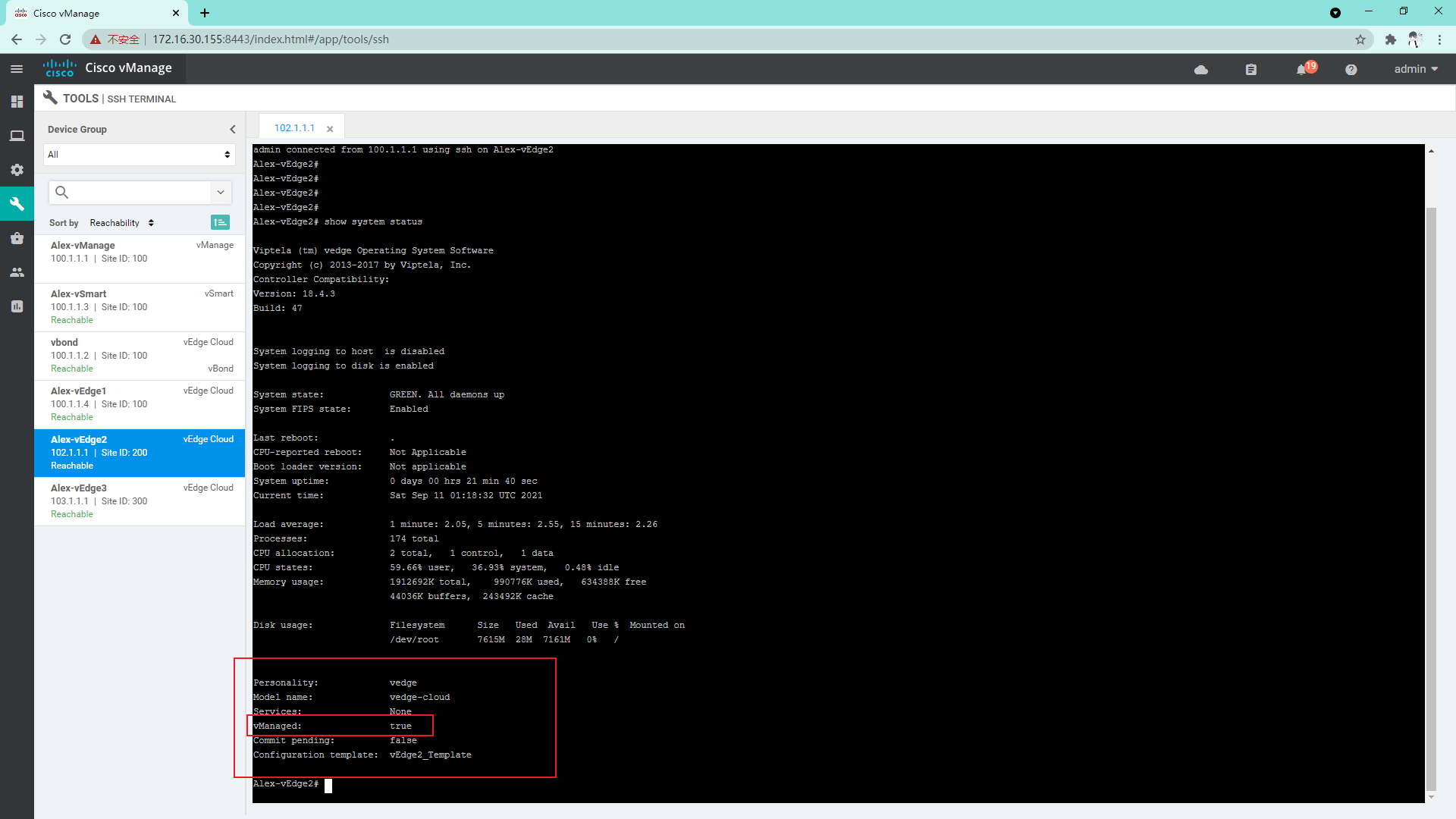
4.3.13 so far, all the vdges have been managed by vManage
4.3.14 the configuration of managed equipment can only be modified on vManage, not locally
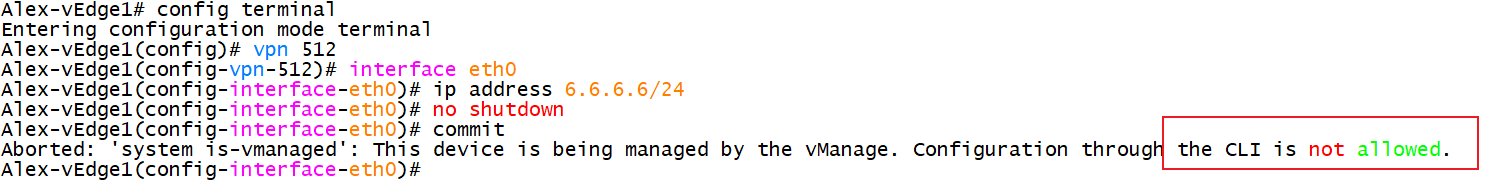
5. Site Switch
Switch_100:
interface Loopback0 ip address 123.1.1.1 255.255.255.255 ip ospf 1 area 0 ! interface Ethernet0/0 switchport trunk allowed vlan 66 switchport trunk encapsulation dot1q switchport mode trunk ! interface Vlan66 mtu 1496 ip address 192.168.11.2 255.255.255.0 ip ospf network point-to-point ip ospf 1 area 0 ! router ospf 1 router-id 123.1.1.1
Switch_200:
interface Loopback0 ip address 123.1.1.2 255.255.255.255 ip ospf 1 area 0 ! interface Ethernet0/0 switchport trunk allowed vlan 66 switchport trunk encapsulation dot1q switchport mode trunk ! interface Vlan66 mtu 1496 ip address 192.168.21.2 255.255.255.0 ip ospf network point-to-point ip ospf 1 area 0 ! router ospf 1 router-id 123.1.1.2
Switch_300:
interface Loopback0 ip address 123.1.1.3 255.255.255.255 ip ospf 1 area 0 ! interface Ethernet0/0 switchport trunk allowed vlan 66 switchport trunk encapsulation dot1q switchport mode trunk ! interface Vlan66 ip address 192.168.31.2 255.255.255.0 ! router ospf 1 router-id 123.1.1.3
six Routing information
6.1 viewing OMP neighbors on vSmart
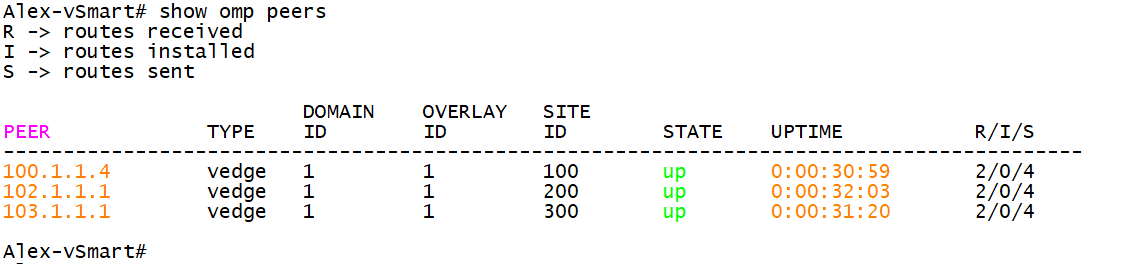
six point two Viewing OMP routes on vSmart
Alex-vSmart# show omp routes
---------------------------------------------------
omp route entries for vpn 66 route 123.1.1.1/32
---------------------------------------------------
RECEIVED FROM:
peer 100.1.1.4
path-id 65
label 1002
status C,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 100.1.1.4
type installed
tloc 100.1.1.4, default, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 100
preference not set
tag not set
origin-proto OSPF-intra-area
origin-metric 11
as-path not set
unknown-attr-len not set
ADVERTISED TO:
peer 102.1.1.1
ADVERTISED TO:
peer 103.1.1.1
---------------------------------------------------
omp route entries for vpn 66 route 123.1.1.2/32
---------------------------------------------------
RECEIVED FROM:
peer 102.1.1.1
path-id 65
label 1002
status C,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 102.1.1.1
type installed
tloc 102.1.1.1, default, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 200
preference not set
tag not set
origin-proto OSPF-intra-area
origin-metric 11
as-path not set
unknown-attr-len not set
ADVERTISED TO:
peer 100.1.1.4
ADVERTISED TO:
peer 103.1.1.1
---------------------------------------------------
omp route entries for vpn 66 route 123.1.1.3/32
---------------------------------------------------
RECEIVED FROM:
peer 103.1.1.1
path-id 65
label 1002
status C,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 103.1.1.1
type installed
tloc 103.1.1.1, default, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 300
preference not set
tag not set
origin-proto OSPF-intra-area
origin-metric 11
as-path not set
unknown-attr-len not set
ADVERTISED TO:
peer 100.1.1.4
ADVERTISED TO:
peer 102.1.1.1
---------------------------------------------------
omp route entries for vpn 66 route 192.168.11.0/24
---------------------------------------------------
RECEIVED FROM:
peer 100.1.1.4
path-id 65
label 1002
status C,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 100.1.1.4
type installed
tloc 100.1.1.4, default, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 100
preference not set
tag not set
origin-proto connected
origin-metric 0
as-path not set
unknown-attr-len not set
ADVERTISED TO:
peer 102.1.1.1
ADVERTISED TO:
peer 103.1.1.1
---------------------------------------------------
omp route entries for vpn 66 route 192.168.21.0/24
---------------------------------------------------
RECEIVED FROM:
peer 102.1.1.1
path-id 65
label 1002
status C,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 102.1.1.1
type installed
tloc 102.1.1.1, default, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 200
preference not set
tag not set
origin-proto connected
origin-metric 0
as-path not set
unknown-attr-len not set
ADVERTISED TO:
peer 100.1.1.4
ADVERTISED TO:
peer 103.1.1.1
---------------------------------------------------
omp route entries for vpn 66 route 192.168.31.0/24
---------------------------------------------------
RECEIVED FROM:
peer 103.1.1.1
path-id 65
label 1002
status C,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 103.1.1.1
type installed
tloc 103.1.1.1, default, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 300
preference not set
tag not set
origin-proto connected
origin-metric 0
as-path not set
unknown-attr-len not set
ADVERTISED TO:
peer 100.1.1.4
ADVERTISED TO:
peer 102.1.1.1
Alex-vSmart# 6.3 viewing OMP neighbor information on vdge
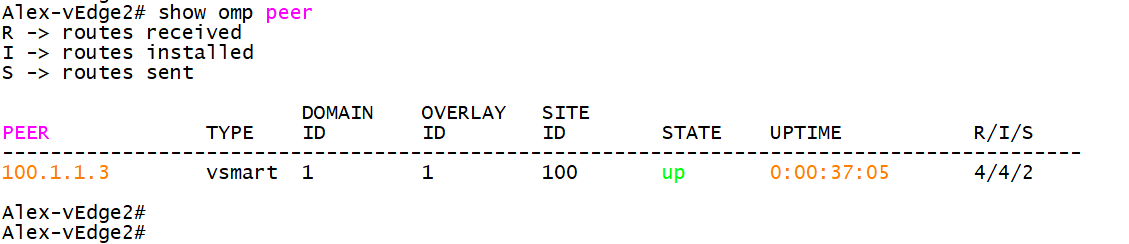
6.4 viewing OMP routing information on vdge
Alex-vEdge2# show omp routes
---------------------------------------------------
omp route entries for vpn 66 route 123.1.1.1/32
---------------------------------------------------
RECEIVED FROM:
peer 100.1.1.3
path-id 7
label 1002
status C,I,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 100.1.1.4
type installed
tloc 100.1.1.4, default, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 100
preference not set
tag not set
origin-proto OSPF-intra-area
origin-metric 11
as-path not set
unknown-attr-len not set
---------------------------------------------------
omp route entries for vpn 66 route 123.1.1.2/32
---------------------------------------------------
RECEIVED FROM:
peer 0.0.0.0
path-id 65
label 1002
status C,Red,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 102.1.1.1
type installed
tloc 102.1.1.1, default, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 200
preference not set
tag not set
origin-proto OSPF-intra-area
origin-metric 11
as-path not set
unknown-attr-len not set
ADVERTISED TO:
peer 100.1.1.3
---------------------------------------------------
omp route entries for vpn 66 route 123.1.1.3/32
---------------------------------------------------
RECEIVED FROM:
peer 100.1.1.3
path-id 5
label 1002
status C,I,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 103.1.1.1
type installed
tloc 103.1.1.1, default, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 300
preference not set
tag not set
origin-proto OSPF-intra-area
origin-metric 11
as-path not set
unknown-attr-len not set
---------------------------------------------------
omp route entries for vpn 66 route 192.168.11.0/24
---------------------------------------------------
RECEIVED FROM:
peer 100.1.1.3
path-id 6
label 1002
status C,I,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 100.1.1.4
type installed
tloc 100.1.1.4, default, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 100
preference not set
tag not set
origin-proto connected
origin-metric 0
as-path not set
unknown-attr-len not set
---------------------------------------------------
omp route entries for vpn 66 route 192.168.21.0/24
---------------------------------------------------
RECEIVED FROM:
peer 0.0.0.0
path-id 65
label 1002
status C,Red,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 102.1.1.1
type installed
tloc 102.1.1.1, default, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 200
preference not set
tag not set
origin-proto connected
origin-metric 0
as-path not set
unknown-attr-len not set
ADVERTISED TO:
peer 100.1.1.3
---------------------------------------------------
omp route entries for vpn 66 route 192.168.31.0/24
---------------------------------------------------
RECEIVED FROM:
peer 100.1.1.3
path-id 3
label 1002
status C,I,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 103.1.1.1
type installed
tloc 103.1.1.1, default, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 300
preference not set
tag not set
origin-proto connected
origin-metric 0
as-path not set
unknown-attr-len not set
Alex-vEdge2# 6.5 viewing global routes on vdge
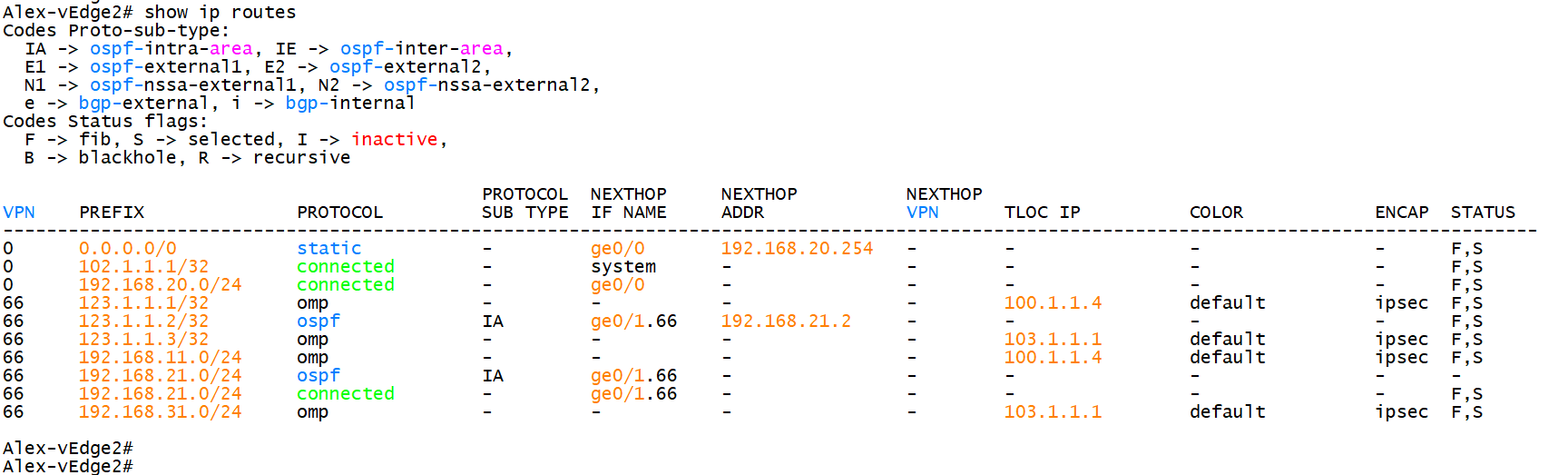
6.6 view route on site Switch
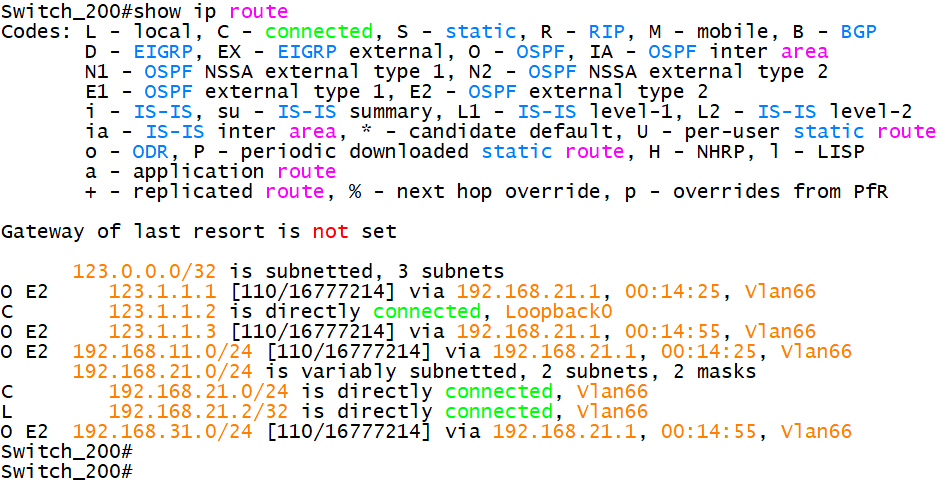
7. Connectivity test
7.1 test switch_ Loop return port and switch of 200_ Connectivity between loopback ports of 300
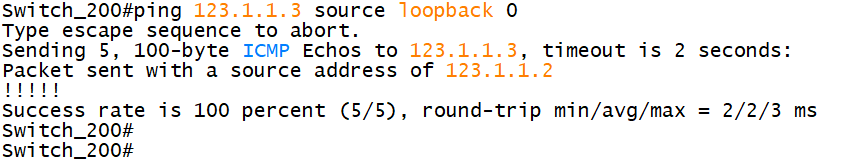
7.2 using traceroute to track the route
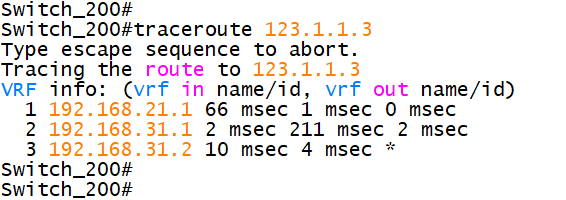
8. Precautions
- If there is no third-party certificate server, be sure to close the tunnel interface under VPN0, use the local certificate server, and open the tunnel interface after the certificates are loaded;
- The device must be configured with VPN 512 and bound, even if it is empty;
- If it is a sub interface used, the physical interface must be marked under VPN0;
- The sub interface must be modified to MTU 1496;