Catalog
Learning Notes: CentOS 7 Learning Seventeenth: Linux Scheduled Tasks and Log Management
This paper is used to record learning experience and experience, and make notes to facilitate future review and summary. The content is basically based on the teaching materials of theology education. Most of the pictures are based on the teaching materials of theology education. Thank you very much for the excellent teaching of MK and Theology education. I hope that when you want to reprint it because of your learning needs, you can affirm your origin as theological education. Thank you!
17.1 Planned Task-at-cron-Planned Task Usage Method
The role of planning tasks: do some periodic tasks, in production mainly used to backup data regularly
CROND: This daemon exists to perform tasks periodically or to handle waiting events
There are two kinds of task scheduling: system task scheduling and user task scheduling.
There are two ways to plan tasks:
- One is timing, which is routine. It's about doing this again every certain cycle, through at.
- One is unexpected, that is, once this is done, there will be no next time, temporary decision, only once to perform the task, through crontab to achieve.
at and crontab commands:
- at: It's a command that handles the end of execution only once
- crontab: It's going to keep the tasks or tasks you specify, such as scripts, going through the cycle you set.
17.1.1 Utilization of at Planned Tasks
Syntax format: at time; service: atd
As follows:
CentOS 7
[root@centos-7-24 ~]# systemctl start atd # Start the atd service
[root@centos-7-24 ~]# systemctl status atd # View atd service status
● atd.service - Job spooling tools
Loaded: loaded (/usr/lib/systemd/system/atd.service; enabled; vendor preset: enabled)
Active: active (running) since May 2019-06-21 00:11:10 CST; 3min 37s ago #The status of active indicates that it has been started
Main PID: 7149 (atd)
Tasks: 1
CGroup: /system.slice/atd.service
└─7149 /usr/sbin/atd -f
6 21:00:11:10 centos-7-24 systemd[1]: Started Job spooling tools.
[root@centos-7-24 ~]# systemctl enable atd #Add atd service to boot-up
[root@centos-7-24 ~]# systemctl list-unit-files --type service|grep atd #View the boot status of the atd service, display enable, successful
atd.service enabled
rpc-statd-notify.service static
rpc-statd.service static
CentOS 6
[root@centos6-22 ~]# service atd start #Start the atd service [root@centos6-22 ~]# service atd status #View atd service status atd (pid 11139) is running... [root@centos6-22 ~]# chkconfig --list | grep atd #View atd self-startup settings atd 0:off 1:off 2:off 3:off 4:off 5:off 6:off [root@centos6-22 ~]# chkconfig atd on #Open atd service boot-up and self-start [root@centos6-22 ~]# chkconfig --list | grep atd #Under runlevel 2, 3, 4 and 5, all on indicates that the boot-up self-startup has been set up. atd 0:off 1:off 2:on 3:on 4:on 5:on 6:off
Example: Creating a planned task using at
[root@centos6-22 ~]# date #View the current time Fri Jun 21 00:36:36 PDT 2019 [root@centos6-22 ~]# at 00:39 at> mkdir /test #Enter commands to be executed at> touch /test/attest1.txt at> <EOT> #crtl+D End job 1 at 2019-06-21 00:39 [root@centos6-22 ~]# at -l #View scheduled tasks 1 2019-06-21 00:39 a root [root@centos6-22 ~]# atq #View scheduled tasks 1 2019-06-21 00:39 a root [root@centos6-22 ~]# ll /test/ #View Find Execution Successful total 0 -rw-r--r--. 1 root root 0 Jun 21 00:39 attest1.txt [root@centos6-22 ~]# at -l #When the execution is completed, the planned tasks are cleared.
17.1.2 View and delete planned tasks to be performed by at
View, you can only see that it has not been executed. If the task has been started or completed, it is invisible.
As follows:
[root@centos6-22 ~]# at 03:20am #Create at tasks at> rm -rf /test/attest1.txt at> cp /etc/passwd /test/ at> echo "ok" at> <EOT> job 2 at 2019-06-21 03:20 [root@centos6-22 ~]# at -l #View at Task List 2 2019-06-21 03:20 a root
at task list description
| Task Number | Time of execution | queue | Executor |
|---|---|---|---|
| 2 | 2019-06-21 03:20 | a | root |
[root@centos6-22 ~]# at -c 2 #See at task details numbered 2
#!/bin/sh
# atrun uid=0 gid=0
# mail yangjie 0
umask 22
HOSTNAME=centos6-22; export HOSTNAME
SHELL=/bin/bash; export SHELL
HISTSIZE=1000; export HISTSIZE
USER=root; export USER
LS_COLORS=rs=0:di=01\;34:ln=01\;36:mh=00:pi=40\;33:so=01\;35:do=01\;35:bd=40\;33\;01:cd=40\;33\;01:or=40\;31\;01:mi=01\;05\;37\;41:su=37\;41:sg=30\;43:ca=30\;41:tw=30\;42:ow=34\;42:st=37\;44:ex=01\;32:\*.tar=01\;31:\*.tgz=01\;31:\*.arj=01\;31:\*.taz=01\;31:\*.lzh=01\;31:\*.lzma=01\;31:\*.tlz=01\;31:\*.txz=01\;31:\*.zip=01\;31:\*.z=01\;31:\*.Z=01\;31:\*.dz=01\;31:\*.gz=01\;31:\*.lz=01\;31:\*.xz=01\;31:\*.bz2=01\;31:\*.tbz=01\;31:\*.tbz2=01\;31:\*.bz=01\;31:\*.tz=01\;31:\*.deb=01\;31:\*.rpm=01\;31:\*.jar=01\;31:\*.rar=01\;31:\*.ace=01\;31:\*.zoo=01\;31:\*.cpio=01\;31:\*.7z=01\;31:\*.rz=01\;31:\*.jpg=01\;35:\*.jpeg=01\;35:\*.gif=01\;35:\*.bmp=01\;35:\*.pbm=01\;35:\*.pgm=01\;35:\*.ppm=01\;35:\*.tga=01\;35:\*.xbm=01\;35:\*.xpm=01\;35:\*.tif=01\;35:\*.tiff=01\;35:\*.png=01\;35:\*.svg=01\;35:\*.svgz=01\;35:\*.mng=01\;35:\*.pcx=01\;35:\*.mov=01\;35:\*.mpg=01\;35:\*.mpeg=01\;35:\*.m2v=01\;35:\*.mkv=01\;35:\*.ogm=01\;35:\*.mp4=01\;35:\*.m4v=01\;35:\*.mp4v=01\;35:\*.vob=01\;35:\*.qt=01\;35:\*.nuv=01\;35:\*.wmv=01\;35:\*.asf=01\;35:\*.rm=01\;35:\*.rmvb=01\;35:\*.flc=01\;35:\*.avi=01\;35:\*.fli=01\;35:\*.flv=01\;35:\*.gl=01\;35:\*.dl=01\;35:\*.xcf=01\;35:\*.xwd=01\;35:\*.yuv=01\;35:\*.cgm=01\;35:\*.emf=01\;35:\*.axv=01\;35:\*.anx=01\;35:\*.ogv=01\;35:\*.ogx=01\;35:\*.aac=01\;36:\*.au=01\;36:\*.flac=01\;36:\*.mid=01\;36:\*.midi=01\;36:\*.mka=01\;36:\*.mp3=01\;36:\*.mpc=01\;36:\*.ogg=01\;36:\*.ra=01\;36:\*.wav=01\;36:\*.axa=01\;36:\*.oga=01\;36:\*.spx=01\;36:\*.xspf=01\;36:; export LS_COLORS
MAIL=/var/spool/mail/root; export MAIL
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin:/root/bin; export PATH
PWD=/root; export PWD
LANG=en_US.UTF-8; export LANG
SSH_ASKPASS=/usr/libexec/openssh/gnome-ssh-askpass; export SSH_ASKPASS
HISTCONTROL=ignoredups; export HISTCONTROL
SHLVL=1; export SHLVL
HOME=/root; export HOME
LOGNAME=root; export LOGNAME
LESSOPEN=\|\|/usr/bin/lesspipe.sh\ %s; export LESSOPEN
G_BROKEN_FILENAMES=1; export G_BROKEN_FILENAMES
XAUTHORITY=/root/.xauth9hNSXA; export XAUTHORITY
cd /root || {
echo 'Execution directory inaccessible' >&2
exit 1
}
${SHELL:-/bin/sh} << 'marcinDELIMITER44b61201' #Here are the detailed classes of at tasks
rm -rf /test/attest1.txt
cp /etc/passwd /test/
echo "ok"
marcinDELIMITER44b61201
[root@centos6-22 ~]# ls /var/spool/at/ #at scheduled tasks under / var/spool folder
a00002018d02ec spool
[root@centos6-22 ~]# tail -5 /var/spool/at/a00002018d02ec #Look at the last five lines to see the details of the task
rm -rf /test/attest1.txt
cp /etc/passwd /test/
echo "ok"
marcinDELIMITER44b61201
Delete at Scheduled Tasks
Grammar: atrm task number
[root@centos6-22 ~]# at -l 3 2019-06-21 04:00 a root 2 2019-06-21 03:20 a root [root@centos6-22 ~]# atrm 3 #Delete at Timing Task 3 [root@centos6-22 ~]# at -l 2 2019-06-21 03:20 a root
17.1.3 Use of Crontab Timing Tasks
The crond command periodically checks for work to be performed and automatically executes if there is work to be performed.
cron is a timing execution tool under linux, which can run jobs without manual intervention.
linux task scheduling can be divided into the following two categories:
Work performed by the system: Work performed periodically by the system, such as updating whatis database updatedb database, periodically cutting logs, collecting system status information, / tmp periodically cleaning
Work performed by users: backing up database regularly, etc.
Start the crond service:
[root@CentOS 7-23 ~]# systemctl start crond #Start the crond service [root@CentOS 7-23 ~]# systemctl enable crond #Set up crond boot-up
Introduction of 17.1.4 cron command parameters
The parameters of crontab:
| crontab -u hr | # cron service for specified hr users |
|---|---|
| crontab -l | # List the details of the cron service under the current user |
| crontab -u yangjie -l | # List details of cron services under specified user Yangji |
| crontab -r | # Delete cron service |
| crontab -e | # Editing cron service |
For example:
crontab -u root -l # root Views Your cron Scheduled Tasks crontab -u san -r # root wants to delete san's cron scheduled task
The grammar for cron-e editing is shown in the following figure:
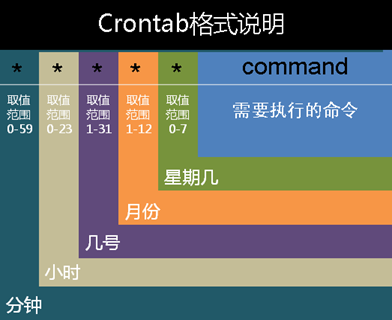
Sunday is expressed in 0 or 7.
A line corresponds to a task. The meaning of a special symbol is:
| * | Numbers representing the range of values | (arbitrary/per) |
|---|---|---|
| / | Interval frequency of specified time | */10 0-23/2 |
| - | Represents from a number to a number. | 8-17 |
| , | Separate several discrete numbers | 6,10-13,20 |
17.1.5 Create Planned Tasks
Example 1: Start backing up data at 2:1 a.m. every day
[root@CentOS 7-23 ~]# crontab -e #Timing tasks to create the current user root ... 1 2 * * * tar czvf /opt/grub2.tar.gz /boot/grub2 ... no crontab for root - using an empty one crontab: installing new crontab [root@CentOS 7-23 ~]# crontab -u yangjie -l #View user yangjie's timed tasks 30 0 * * 0 cp /etc/passwd /home/yangjie
Note: All users'scheduled tasks will generate corresponding files under / var/spool/cron /.
[root@CentOS 7-23 ~]# ll /var/spool/cron //Total dosage 8 -rw-------. 1 root root 49 6 February 2200:27 root -rw-------. 1 root root 40 6 February 2200:37 yangjie
17.1.6 System-level Planned Tasks
[root@CentOS 7-23 ~]# ll /etc/crontab #Viewing System-Level Timing Tasks -rw-r--r--. 1 root root 451 6 January 10, 2014 /etc/crontab [root@CentOS 7-23 ~]# vim /etc/crontab #View the timed task list for system boundaries SHELL=/bin/bash PATH=/sbin:/bin:/usr/sbin:/usr/bin MAILTO=root # For details see man 4 crontabs # Example of job definition: # .---------------- minute (0 - 59) # | .------------- hour (0 - 23) # | | .---------- day of month (1 - 31) # | | | .------- month (1 - 12) OR jan,feb,mar,apr ... # | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat # | | | | | # * * * * * user-name command to be executed
You can also add planned tasks directly to / etc/crontab
Notes for using the crontab command:
Problems of Environmental Variables
Clean up your email log, such as using redirection >/dev/null 2>&1
[root@CentOS 7-23 ~]# ll /etc/cron* -rw-------. 1 root root 0 11 February 20, 2018 /etc/cron.deny #Documents that control whether users can do planned tasks; -rw-r--r--. 1 root root 451 6 February 2200:40 /etc/crontab #The main configuration file can also add tasks. /etc/cron.d: #It is the task that the system needs to do automatically and regularly, but it is not carried out by hour, day, week and month. Then it is placed under this directory. //Total dosage 16 -rw-r--r--. 1 root root 128 11 January 20, 2018 hourly -rw-r--r--. 1 root root 108 10 Month 30 2018 raid-check -rw-r--r--. 1 root root 459 10 June 16, 2018 sa-update -rw-------. 1 root root 235 10 Month 31 2018 sysstat /etc/cron.daily: #Files executed daily are under this directory //Total dosage 12 -rwx------. 1 root root 219 10 Month 31 2018 logrotate -rwxr-xr-x. 1 root root 618 10 Month 30 2018 man-db.cron -rwx------. 1 root root 208 4 January 11, 2018 mlocate /etc/cron.hourly: #Documents executed hourly are in this directory //Total dosage 8
Also:
Monthly / monthly scripts executed monthly by cron.
The script that is executed weekly by cron.weekly/ #;
17.1.7 Common Task Writing and Cases
1. Restart apache every night at 21:00
0 21 * * * systemctl restart httpd # 0 21 * * * /etc/init.d/httpd restart
2. Restart apache at 4:45 on January 1, 10 and 22
45 4 1,10,22 * * /etc/init.d/httpd restart
3. Restart apache at 4:45 every month from 1 to 10
45 4 1-10 * * /etc/init.d/httpd restart
4. Restart apache every two days from 8 a.m. to 11 a.m. in the 3rd and 15th minutes
3,15 8-11 /2 * /etc/init.d/httpd restart
5. Restart apache every hour between 11 p.m. and 7 a.m.
0 23-7/1 * * * /etc/init.d/httpd restart
6. Send a letter to root@panda every night from Monday to Friday at 21:15 p.m.
15 21 * * 1-5 mail -s "hi" root@panda < /etc/fstab
7. Case requirements:
Backup / etc / directory to / tmp/backup at 2:00 a.m. per day
Write backup commands into a script
Daily Backup File Name Requirements Format: 2017-08-19_etc.tar.gz
Do not output task information when performing planned tasks
The directory where backup content is stored requires only three days
[root@CentOS 7-23 ~]# mkdir /tmp/backup #Create / tmp/backup folder
[root@CentOS 7-23 ~]# vim backup.sh #Edit backup script
#!/bin/bash
tar -czvf /tmp/backup/`date +'%Y-%m-%d'`_etc.tar.gz /etc/ #Create A / etc / archive named after date +_etc.tar.gz
find /tmp/backup/ -name *_etc.tar.gz -mtime +3 -exec rm -rf {}\; #Delete archives that have been modified for more than three days under / tmp/backup
[root@CentOS 7-23 ~]# chmod 755 backup.sh #Modify the execution permissions of backup.sh files
[root@CentOS 7-23 ~]# crontab -u root -e #Adding Timing Tasks to User root
1 2 * * * tar czxf /opt/grub2.tar.gz /boot/grub2
0 2 * * * /root/backup.sh & > /dev/null #backup.sh will be executed at 02:00 tomorrow without any information being displayed
crontab: installing new crontab
[root@CentOS 7-23 ~]# crontab -l #View the Timing Task List
1 2 * * * tar czxf /opt/grub2.tar.gz /boot/grub2
0 2 * * * /root/backup.sh & > /dev/null
17.2 Log Types and Recording Ways - Customize ssh Service Log Types and Storage Locations
In centos7, system log messages are handled by two services: system d-journald and rsyslog
17.2.1 The Role of Common Log Files
Overview of system log files: / var/log directory keeps some system and service specific log files maintained by rsyslog
| log file | purpose |
|---|---|
| /var/log/message | Most system log messages are logged here. There are also exceptions: regular job tasks related to authentication, e-mail processing, etc. |
| /var/log/secure | Security and authentication-related messages and log files for login failures. Log generated by ssh Remote Connection |
| /var/log/maillog | Message log files associated with mail servers |
| /var/log/cron | Log files associated with regular task execution |
| /var/log/boot.log | Message Logging Related to System Startup |
| /var/log/dmesg | Message Logging Related to System Startup |
Example 1: See which IP address often violently cracks system user passwords
[root@centos-7-24 ~]# ssh root@192.168.234.23 #Remote login 23 on 24, deliberately mistyped three passwords
The authenticity of host '192.168.234.23 (192.168.234.23)' can't be established.
ECDSA key fingerprint is SHA256:y4YpS7A4EB9G7GdT8weTstd5C4Y7iic8CoeTUy7Dc04.
ECDSA key fingerprint is MD5:32:66:6e:7a:76:ef:d7:c4:e9:0a:d3:f8:fe:33:7c:11.
Are you sure you want to continue connecting (yes/no)? y
Please type 'yes' or 'no': yes
Warning: Permanently added '192.168.234.23' (ECDSA) to the list of known hosts.
root@192.168.234.23's password:
Permission denied, please try again.
root@192.168.234.23's password:
Permission denied, please try again.
root@192.168.234.23's password:
Permission denied (publickey,gssapi-keyex,gssapi-with-mic,password).
[root@CentOS 7-23 ~]# grep Failed /var/log/secure #View login failure information on 23
Jun 24 21:44:03 CentOS 7-23 sshd[18379]: Failed password for root from 192.168.234.24 port 59360 ssh2
Jun 24 21:44:09 CentOS 7-23 sshd[18379]: Failed password for root from 192.168.234.24 port 59360 ssh2
Jun 24 21:44:13 CentOS 7-23 sshd[18379]: Failed password for root from 192.168.234.24 port 59360 ssh2
[root@CentOS 7-23 ~]# grep Failed /var/log/secure|awk '{print $12}'|uniq -c
#awk '{print $11}' #Print the data in column 11 using spaces as separators
#The uniq command is used to report or ignore duplicate lines in a file, - c or - count: show the number of duplicates next to each column;
3 192.168.234.24
Example 2: The Role of/var/log/wtmp Documents
/ var/log/wtmp is also a binary file that records the number of logins and duration of each user.
The last command can be used to output the contents of the wtmp: last displays the records of successful login to the system so far
[root@CentOS 7-23 ~]# last #Use last to view the latest login information of the system yangjie pts/0 :0 Mon Jun 24 21:40 still logged in yangjie :0 :0 Mon Jun 24 21:40 still logged in reboot system boot 3.10.0-693.el7.x Mon Jun 24 21:39 - 21:51 (00:12) yangjie pts/1 :0 Sat Jun 22 01:08 - 01:34 (00:26) yangjie pts/0 :0 Sat Jun 22 00:18 - 01:34 (01:15) yangjie :0 :0 Sat Jun 22 00:18 - down (01:16) [root@CentOS 7-23 ~]# last -f /var/log/wtmp yangjie pts/0 :0 Mon Jun 24 21:40 still logged in yangjie :0 :0 Mon Jun 24 21:40 still logged in reboot system boot 3.10.0-693.el7.x Mon Jun 24 21:39 - 21:54 (00:15) yangjie pts/1 :0 Sat Jun 22 01:08 - 01:34 (00:26) yangjie pts/0 :0 Sat Jun 22 00:18 - 01:34 (01:15) yangjie :0 :0 Sat Jun 22 00:18 - down (01:16)
Example 3: Use / var/log/btmp file to view users of Violent Cracking System
/ The var/log/btmp file is a log that records the incorrect login system. If it is found that the log file of / var / log / BTMP is larger than 1M, even if it is larger, it means that many people are violently cracking ssh service. This log needs to be checked by lastb program.
[root@CentOS 7-23 ~]# ll /var/log/btmp -rw-------. 1 root utmp 1536 6 24/21:44 /var/log/btmp [root@CentOS 7-23 ~]# lastb root ssh:notty 192.168.234.24 Mon Jun 24 21:44 - 21:44 (00:00) root ssh:notty 192.168.234.24 Mon Jun 24 21:44 - 21:44 (00:00) root ssh:notty 192.168.234.24 Mon Jun 24 21:44 - 21:44 (00:00) root pts/0 Mon Jun 24 21:42 - 21:42 (00:00) btmp begins Mon Jun 24 21:42:00 2019 #After discovery, use the firewall and reject it: the order is as follows: iptables -A INPUT -i eth0 -s. 192.168.234.24 -j DROP
Recording Method of 17.2.2 Logs
Naming rules for logs: classification - "level" in the form of: classification. level, respectively, as follows:
Classification of logs:
| classification | Explain |
|---|---|
| daemon | Background process correlation |
| kern | Information generated by the kernel |
| lpr | Printing system generated |
| authpriv | Security Authentication |
| cron | Timing correlation |
| Mail-related | |
| syslog | Logging service itself |
| news | News system |
| local0~7 | Custom Logging Device |
Note: local0-local7 8 system reserved classes for use by other programs or user-defined
Log Level: Light > Heavy
| Code | priority | Seriousness |
|---|---|---|
| 7 | debug | Information is useful for developers to debug applications, but not during operation. |
| 6 | info | Normal operation information, report collection, throughput measurement, etc. |
| 5 | notice | Note that normal but important events |
| 4 | warning | Warning, prompting if no action is taken. Errors will occur. For example, the file system uses 90% |
| 3 | err | Error to prevent a module or program from functioning properly |
| 2 | crit | Key errors have affected information that the entire system or software is not working properly. |
| 1 | alert | Alert, information that needs to be modified immediately |
| 0 | emerg | Serious information such as emergencies, kernel crashes, etc. |
17.2.3 rsyslog log service
RHEL5 - > service name syslog - > configuration file / etc/syslog.conf
Rhel6-7 - > service name rsyslog - > configuration file / etc/rsyslog.conf
View log configuration file information:
[root@CentOS 7-23 ~]# vim /etc/rsyslog.conf .... # Provides UDP syslog reception #$ModLoad imudp #$UDPServerRun 514 #Allow port 514 to receive logs forwarded using UDP protocol # Provides TCP syslog reception #$ModLoad imtcp #$InputTCPServerRun 514 #Allow port 514 to receive logs forwarded using TCP protocol .... .... # Don't log private authentication messages! *.info;mail.none;authpriv.none;cron.none /var/log/messages # All categories are above info except mail,authpriv,cron # The authpriv file has restricted access. authpriv.* /var/log/secure #All authentication information is stored in / var/log/secure # Log all the mail messages in one place. mail.* -/var/log/maillog #All mail-related information is stored in / var/log/maillog, "-" number: mail information is more, now the data is stored in memory, up to a certain size, all written to the hard disk. It is conducive to reducing the overhead of I/O process, data stored in memory, if inappropriate shutdown data disappears. # Log cron stuff cron.* /var/log/cron #Information related to planning tasks is stored in / var/log/cron # Everybody gets emergency messages *.emerg :omusrmsg:* # Save news errors of level crit and higher in a special file. uucp,news.crit /var/log/spooler # Save boot messages also to boot.log local7.* /var/log/boot.log #Information displayed on boot-up is stored in / var/log/boot.log
17.2.4 Log Entry Rules
All information greater than or equal to info level is recorded in a file.
= Level only records logs equal to a certain level
Example:. = info records only info-level logs
...! Level records all level information except one level.
Except err, all errs are recorded.
None refers to the exclusion of a category example: mail.none logs for all mail categories are not recorded
17.2.5 Log Type and Storage Location of Custom ssh Service
[root@CentOS 7-23 ~]# vim /etc/rsyslog.conf #Add to: local0.* /var/log/sshd.log #Add all logs at the local0 level to / var/log/sshd.log
Define the log category of ssh service as local0 and edit the main configuration file of sshd service
[root@CentOS 7-23 ~]# vim /etc/ssh/sshd_config [root@CentOS 7-23 ~]# ll /var/log/sshd.log -rw-------. 1 root root 151 6 24/23:12 /var/log/sshd.log #View the sshd.log file found under / var/log to show that the modification was successful [root@CentOS 7-23 ~]# cat /var/log/sshd.log Jun 24 23:12:24 CentOS 7-23 sshd[20137]: Server listening on 0.0.0.0 port 22. Jun 24 23:12:24 CentOS 7-23 sshd[20137]: Server listening on :: port 22.
17.3 Log Cutting-Setting up Remote Log Collection Server
17.3.1 Log Cutting
Logs under linux are periodically scrolled to increase, and we can cut the logs that are rolling back online in a specified size (dynamic), if the log is static. For example, there is no application to write content inside. Then we can also use split tools to cut; Logrotate supports automatic segmentation by time and size to prevent log files from being too large.
logrotate configuration files include:
/ etc/logrotate.conf and/etc/logrotate.d/detailed configuration files under this subdirectory.
The execution of logrotate is invoked by the crond service.
[root@CentOS 7-23 ~]# vim /etc/cron.daily/logrotate #View the logrotate script content
#!/bin/sh
/usr/sbin/logrotate -s /var/lib/logrotate/logrotate.status /etc/logrotate.conf #Call the / etc/logrotate.conf file
EXITVALUE=$?
if [ $EXITVALUE != 0 ]; then
/usr/bin/logger -t logrotate "ALERT exited abnormally with [$EXITVALUE]"
fi
exit 0
[root@CentOS 7-23 ~]# less /etc/logrotate.conf #View the / etc/logrotate.conf file
# uncomment this if you want your log files compressed
#compress
# RPM packages drop log rotation information into this directory
include /etc/logrotate.d
# no packages own wtmp and btmp -- we'll rotate them here #logrotate Log Cutting Configuration with wtmp and btmp Logs
/var/log/wtmp {
monthly
create 0664 root utmp
minsize 1M
rotate 1
}
/var/log/btmp {
missingok
monthly
create 0600 root utmp
rotate 1
}
# system-specific logs may be also be configured here.
[root@CentOS 7-23 ~]# ll /etc/logrotate.d #Look at the detailed configuration file under / etc/logrotate.d. There are logrotate profiles for different services
//Total dosage 64
-rw-r--r--. 1 root root 91 4 January 11, 2018 bootlog
-rw-r--r--. 1 root root 160 9 January 15, 2017 chrony
-rw-r--r--. 1 root root 71 4 January 11, 2018 cups
-rw-r--r--. 1 root root 172 9 Month 30 2016 iscsiuiolog
-rw-r--r--. 1 root root 165 5 29/08:16 libvirtd
-rw-r--r--. 1 root root 142 5 29/08:16 libvirtd.qemu
-rw-r-----. 1 root named 514 6 May 03:26 named
-rw-r--r--. 1 root root 106 4 January 11, 2018 numad
-rw-r--r--. 1 root root 136 6 January 10, 2014 ppp
-rw-r--r--. 1 root root 408 8 March 3, 2017 psacct
-rw-r--r--. 1 root root 115 10 Month 31 2018 samba
-rw-r--r--. 1 root root 68 10 June 16, 2018 sa-update
-rw-r--r--. 1 root root 224 10 Month 30 2018 syslog
-rw-r--r--. 1 root root 188 10 Month 31 2018 vsftpd
-rw-r--r--. 1 root root 100 10 Month 31 2018 wpa_supplicant
-rw-r--r--. 1 root root 103 11 May 5, 2018 yum
[root@CentOS 7-23 ~]# cat /etc/logrotate.d/yum #View the logrotate configuration file for the yum service
/var/log/yum.log {
missingok #During log rotation, any errors will be ignored, such as "file cannot be found" errors.
notifempty #If the log file is empty, rotation will not occur
maxsize 30k #Log Cutting for Files Over 30k
yearly #Perform log rollback once a year
create 0600 root root #Reconstruct the / var/log/yum.log file with user root, subgroup root and execution privilege 0600
}
The logrotate program is started daily by cron at a specified time (/etc/crontab)
Logs are very large. If it's a terrible thing to keep them unrestricted, hundreds of megabytes of disk space will be occupied over time.
Therefore, we need to do log cutting. When the log reaches a certain size, we classify the log. We keep a backup of the previous log and create a file with the same name to save the new log.
17.3.2 Practical Demonstration
Editing configuration files
[root@CentOS 7-23 ~]# vim /etc/logrotate.conf
# rotate log files weekly
weekly
# keep 4 weeks worth of backlogs
rotate 4
# create new (empty) log files after rotating old ones
create
# use date as a suffix of the rotated file
dateext
# uncomment this if you want your log files compressed
#compress
# Description: (Global parameters)
#Weekly: Perform weekly rollbacks, or log rollbacks once a week
#rotate: Represents how many [r t] rotations of the most recent historical files stored after log segmentation
#create: Specifies the permissions and ownership of newly created files and groups
#dateext : Rollback files with suffix dates #You can go to the / var/log directory.
# RPM packages drop log rotation information into this direct
ory
include /etc/logrotate.d
# no packages own wtmp and btmp -- we'll rotate them here
/var/log/wtmp {
monthly
create 0664 root utmp
minsize 1M
rotate 1
}
/var/log/btmp { # Name and path of the specified log file
missingok #If the file is lost, no error will be reported.
monthly #Rotate once a month
create 0600 root utmp Set up btmp Permissions for this log file, owner, group
minsize 1M #The file is rolled back over 1M, so you should know that it may not be partitioned every month, depending on the size of the file.
rotate 1 #Up to one historical file is saved after log segmentation, excluding the log currently in use.
}
# system-specific logs may be also be configured here.
Other parameters:
- Monthly: Log files will rotate monthly. Other available values are `daily', `weekly'or `yearly'.
- rotate 5: Five archive logs will be stored at a time. For the sixth archive, the longest archive will be deleted.
- compress: After the rotation task is completed, the rotation archives will be compressed using gzip.
- Delaycompress: Always used with the compress option. The delaycompress option instructs logrotate not to compress the latest archives. Compression will take place in the next cycle. This is useful when you or any software still needs to read the latest archives.
- missingok: During log rotation, any errors will be ignored, such as "file cannot be found".
- Notfempty: If the log file is empty, rotation will not take place.
- Create 644 root: Create a new log file with the specified permissions, and logrotate renames the original log file.
- Posrotate/endscript: After all other instructions have been completed, the commands specified in postrotate and endscript will be executed. In this case, the rsyslogd process immediately reads its configuration again and continues to run.
- / Default record time of logrotate last rotation log file in var/lib/logrotate/status
[root@CentOS 7-23 ~]# vim /var/lib/logrotate/logrotate.status logrotate state -- version 2 "/var/log/yum.log" 2019-6-20-21:0:0 "/var/log/cups/page_log" 2019-6-20-21:0:0 "/var/log/sa-update.log" 2019-6-20-21:0:0 "/var/log/cups/error_log" 2019-6-20-21:0:0 "/var/named/data/named.run" 2019-6-20-21:0:0 "/var/log/boot.log" 2019-6-20-21:0:0 "/var/log/cups/access_log" 2019-6-20-21:0:0 "/var/log/wtmp" 2019-6-20-21:0:0 "/var/log/chrony/*.log" 2019-6-20-21:0:0 "/var/log/spooler" 2019-6-20-21:0:0 "/var/log/btmp" 2019-6-20-21:0:0 "/var/log/xferlog" 2019-6-20-21:0:0 "/var/log/iscsiuio.log" 2019-6-20-21:0:0 "/var/log/maillog" 2019-6-20-21:0:0 "/var/log/libvirt/libvirtd.log" 2019-6-20-21:0:0 "/var/log/libvirt/qemu/*.log" 2019-6-20-21:0:0 "/var/log/wpa_supplicant.log" 2019-6-20-21:0:0 "/var/log/secure" 2019-6-20-21:0:0 <lib/logrotate/logrotate.status" 25L, 984C 1,1
17.3.3 logrotate for ssh log segmentation
ssh log storage is defined and executed on the basis of / var/log/sshd.
[root@CentOS 7-23 ~]# vim /etc/logrotate.d/sshd #Create a logrotate configuration file for sshd
/var/log/sshd.log{
missingok
weekly
create 0600 root root
minsize 1M
rotate 3
}
[root@CentOS 7-23 ~]# systemctl restart rsyslog #Restart Log Service [root@CentOS 7-23 ~]# logrotate -vf /etc/logrotate.d/sshd #Mandatory rotation, that is to say, even if the rotation conditions are not met, logrotate can be forced to rotate log files by adding-f reading config file /etc/logrotate.d/sshd Allocating hash table for state file, size 15360 B Handling 1 logs rotating pattern: /var/log/sshd.log forced from command line (3 rotations) empty log files are rotated, only log files >= 1048576 bytes are rotated, old logs are removed considering log /var/log/sshd.log log needs rotating rotating log /var/log/sshd.log, log->rotateCount is 3 dateext suffix '-20190625' glob pattern '-[0-9][0-9][0-9][0-9][0-9][0-9][0-9][0-9]' renaming /var/log/sshd.log.3 to /var/log/sshd.log.4 (rotatecount 3, logstart 1, i 3), renaming /var/log/sshd.log.2 to /var/log/sshd.log.3 (rotatecount 3, logstart 1, i 2), renaming /var/log/sshd.log.1 to /var/log/sshd.log.2 (rotatecount 3, logstart 1, i 1), renaming /var/log/sshd.log.0 to /var/log/sshd.log.1 (rotatecount 3, logstart 1, i 0), old log /var/log/sshd.log.0 does not exist fscreate context set to system_u:object_r:var_log_t:s0 renaming /var/log/sshd.log to /var/log/sshd.log.1 creating new /var/log/sshd.log mode = 0600 uid = 0 gid = 0 removing old log /var/log/sshd.log.4 set default create context [root@CentOS 7-23 ~]# ll /var/log/sshd* #After four lightweight rounds, we looked at the sshd log file and found that only the latest 4 log files were saved. -rw-------. 1 root root 0 6 February 2500:16 /var/log/sshd.log -rw-------. 1 root root 0 6 February 2500:16 /var/log/sshd.log.1 -rw-------. 1 root root 0 6 February 2500:16 /var/log/sshd.log.2 -rw-------. 1 root root 0 6 February 2500:16 /var/log/sshd.log.3
17.3.4 Log Configuration Step Summary:
Configure the appropriate level of storage location or file in the / etc/rsyslog.conf file, such as configuring the local0. * level log to / var/log/sshd.log
Configure the log level in the configuration file of / etc / corresponding services, such as configuring the log level to local0 in the / etc/ssh/sshd_config file
Configure the log partitioning configuration file for SSH D services in the / etc/logrotate.d directory, such as configuring the / etc/logrotate.d/ssh file
17.3.5 Configuring Remote Log Server-Implementing Log Centralization Management
Use 23 as server-side configuration
[root@CentOS 7-23 ~]# vim /etc/rsyslog.conf #Modify rsyslog.conf configuration file
# Amendment: 19 #$ModLoad imtcp
# 20 #$InputTCPServerRun 514
#For:
#19 $ModLoad imtcp
#20 $InputTCPServerRun 514
[root@CentOS 7-23 ~]# systemctl restart rsyslog #Restart rsyslog service
[root@CentOS 7-23 ~]# netstat -anutp|grep 514 #View Service Listening Status
tcp 0 0 0.0.0.0:514 0.0.0.0:* LISTEN 21476/rsyslogd
tcp6 0 0 :::514 :::* LISTEN 21476/rsyslogd
[root@CentOS 7-23 ~]# getenforce
Enforcing
[root@CentOS 7-23 ~]# setenforce 0 #Turn off selinux functionality
[root@CentOS 7-23 ~]# getenforce
Permissive
[root@CentOS 7-23 ~]# systemctl stop firewalld #Close the firewall
[root@CentOS 7-23 ~]# systemctl status firewalld #View firewall status
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled)
Active: inactive (dead) since II 2019-06-25 00:36:54 CST; 23s ago
Docs: man:firewalld(1)
Process: 6523 ExecStart=/usr/sbin/firewalld --nofork --nopid $FIREWALLD_ARGS (code=exited, status=0/SUCCESS)
Main PID: 6523 (code=exited, status=0/SUCCESS)
6 24/21:39:27 CentOS7-23 systemd[1]: Starting firewalld...
6 24/21:39:34 CentOS7-23 systemd[1]: Started firewalld ...
6 February 2500:36:54 CentOS 7-23 systemd[1]: Stopping firewall...
6 February 2500:36:54 CentOS 7-23 systemd[1]: Stopped firewalld...
Hint: Some lines were ellipsized, use -l to show in full.
[root@CentOS 7-23 ~]# iptables -F #Clear Firewall Rules
Use 24 as the cilent end configuration
[root@centos-7-24 ~]# vim /etc/rsyslog.conf #Edit/etc/rsyslog.conf file *.* @@192.168.234.23:514 #Add at the end [root@centos-7-24 ~]# systemctl restart rsyslog.service #Restart rsyslog service [root@centos-7-24 ~]# logger "aaaaa" #Testing on Client 24, using logger to simulate the sent log "aaaaa"
Viewing logs dynamically on 23 servers
[root@CentOS 7-23 ~]# tail -f /var/log/messages|grep centos --color #Viewing the message log file dynamically on 23, we found that 24 logs were sent successfully. Jun 25 00:50:20 centos-7-24 systemd: Stopping System Logging Service... Jun 25 00:50:20 centos-7-24 rsyslogd: [origin software="rsyslogd" swVersion="8.24.0-34.el7" x-pid="21170" x-info="http://www.rsyslog.com"] exiting on signal 15. Jun 25 00:50:20 centos-7-24 systemd: Stopped System Logging Service. Jun 25 00:50:20 centos-7-24 systemd: Starting System Logging Service... Jun 25 00:50:20 centos-7-24 rsyslogd: [origin software="rsyslogd" swVersion="8.24.0-34.el7" x-pid="21265" x-info="http://www.rsyslog.com"] start Jun 25 00:50:20 centos-7-24 systemd: Started System Logging Service. Jun 25 00:51:03 centos-7-24 yangjie: aaaaa
Note:
Summary: The server uses udp protocol, and the client can only use one line in the configuration file.@
. @192.168.234.24:514
The server uses the tcp protocol, and the client can only use two lines in the configuration file@@
. @@192.168.234.24:514