Article references:
Installing firewall in Centos7
https://www.cnblogs.com/anxminise/p/9650104.html
Firewalls (firewalld and iptables)
https://blog.csdn.net/weixin_40658000/article/details/78708375
Operation commands of CentOS7 firewall
https://www.cnblogs.com/leoxuan/p/8275343.html
https://blog.csdn.net/wangleiqqaaaaa/article/details/103408656
Thank you!
environment
System: CentOS 7.2
[root@VM-0-11-centos logs]# cat /etc/redhat-release CentOS Linux release 7.2.1511 (Core)
Firewall policy
3.1 firewall and iptables
The firewall policy used by systems before CentOS 7 is iptables. Systems after CentOS 7 use the firewall command to dynamically manage iptables, and iptables is also used at the bottom. The commands of firewall and iptables are also very different. Of course, CentOS 7 can also use iptables as a firewall.
3.2 firewall opening, closing and status viewing
First, enter the command to confirm your system version
$ cat /etc/redhat-release
You can see that the system version is Centos7.5. Generally, centos7 is installed with firewall firewall by default. If you need to write in the installation, please use the yum command to install and uninstall. This article will not explain it separately.
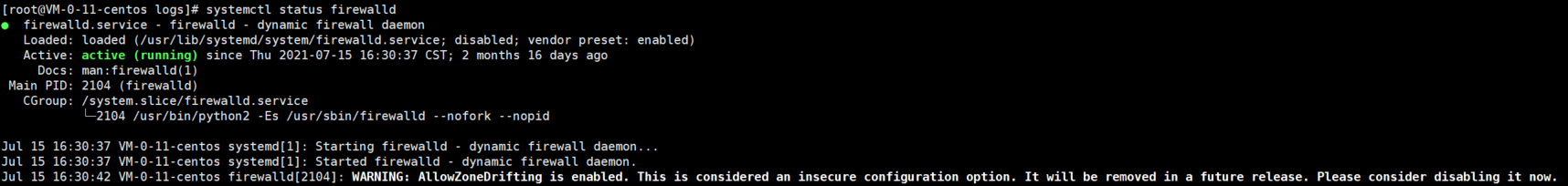
View the firewall status (this command and the command after the article are the firewall command of centos7 system, which is not applicable to systems below centos7)
$ systemctl status firewalld.service
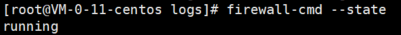
Or use the firewall command to view
$ firewall-cmd --state
Running indicates that the firewall is on and not running indicates that the firewall is off
Start firewall command
$ systemctl start firewalld.service
Turn off firewall command
$ systemctl stop firewalld.service
Restart firewall command
$ systemctl restart firewalld.service
Set boot command
$ systemctl enable firewalld.service
Disable boot command
$ systemctl disable firewalld.service
Check whether to start the command
$ systemctl is-enabled firewalld.service
3.3 firewall adding strategy
Before adding a firewall policy, first ensure that the firewall is turned on, and then execute the command. At present, only several common firewall policy commands are introduced. If you have special needs, please Baidu by yourself. This article will be continuously updated after meeting new needs in future work.
1. Allow the specified ip to access the specified port number
$ firewall-cmd --permanent --add-rich-rule="rule family="ipv4" source address="" port protocol="" port="" accept"
example:
$ firewall-cmd --permanent --add-rich-rule="rule family="ipv4" source address="10.92.183.44" port protocol="tcp" port="22" accept" #Allow 10.92.183.44 access to port 22
2. Allow the specified ip segment to access the specified port number
$ firewall-cmd --permanent --add-rich-rule="rule family="ipv4" source address="10.92.183.0/24" port protocol="tcp" port="22" accept" #Allow 10.92.183.0 network segment to access port 22
3. Allow the specified ip segment to access the specified port segment
$ firewall-cmd --permanent --add-rich-rule="rule family="ipv4" source address="10.92.183.0/24" port protocol="tcp" port="7000-9100" accept" #Allow the 10.92.183.0 network segment to access ports 7000-9100
Parameter interpretation – permanent
When executing the command, if the -- permanent parameter is not taken, the configuration will take effect immediately, but the configuration will not be stored, which is equivalent to restarting the server and will be lost. If you bring it, the configuration will be stored in the configuration file. However, this kind of configuration is only stored in the file, but it will not take effect in real time. You need to execute the firewall CMD -- reload command to reload the configuration before it takes effect.
After using the – permanent parameter, the firewall policy needs to be restarted to take effect
$ firewall-cmd --reload
View firewall policy
$ firewall-cmd --list-all