Brief description:
This experiment is based on blog https://www.cnblogs.com/zlslch/p/7306632.html. The IDS is an intrusion detection system based on LAMP architecture. The core components are Snort, Barnyard2 and Base. Intrusion Detection Using Snort and Output to alert File Use Barnyard2 to read alert file format and output to Library Using Base to Read Data from Library for Display Deployment test of clone experimental machine based on "CentOS 6 experimental machine template build deployment"
Install and configure LAMP:
# Install epel source
yum install -y epel-release
# Install and configure LAMP
yum -y install httpd mysql-server mysql-devel \
php php-mysql php-mbstring php-mcrypt php-gd
# Install php plug-ins
yum -y install mcrypt libmcrypt libmcrypt-devel
# Install the pear plug-in
yum -y install php-pear
pear upgrade pear
pear channel-update pear.php.net
pear install mail mail_mime Numbers_Roman\
Image_Graph-alpha Image_Canvas-alpha Image_Color
# Install adodb
# PHP access database middleware, download address:
# https://sourceforge.net/projects/adodb/files/latest/download
cd /var/www/html
unzip /tmp/adodb-5.20.12.zip
mv /var/www/html/adodb5 /var/www/html/adodb
# Install base, download address:
# https://sourceforge.net/projects/secureideas/files/latest/download
tar -xf /tmp/base-1.4.5.tar.gz -C /var/www/html
mv /var/www/html/base-1.4.5 /var/www/html/base
# Modify php.ini
sed -i 's/^\(error_reporting = E_ALL & \).*$/\1 ~E_NOTICE/g' /etc/php.ini
# Setting html directory permissions
chown -R apache:apache /var/www/html
# Setting adodb permissions
chmod 755 /var/www/html/adodb
# Configure mysql
service mysqld start
mysqladmin -uroot password vincent
mysql -uroot -pvincent
create database snort;
grant create,select,update,insert,delete
on snort.* to snort@localhost identified by 'snort';
flush privileges;
exit
# Download barnyard, download address:
# Download http://pan.baidu.com/s/1mgzYhO8 according to the corresponding disks mentioned in the reprinted blog
# Cannot use the latest version
cd /tmp
tar -xf barnyard2-1.9.tar.gz
mysql -usnort -psnort -Dsnort < barnyard2-1.9/schemas/create_mysql
# Configure base
service mysqld restart
sed -i 's/^#ServerName .*$/&\nServerName 127.0.0.1/g' /etc/httpd/conf/httpd.conf
service httpd start
# Web page configuration
http://192.168.77.200/base/setup/index.php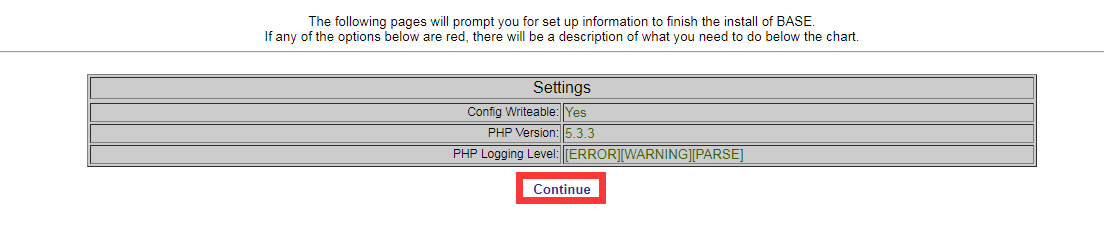
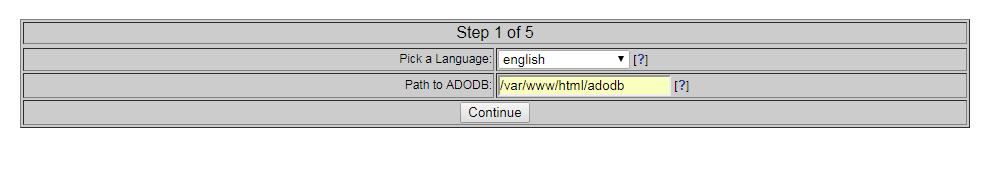
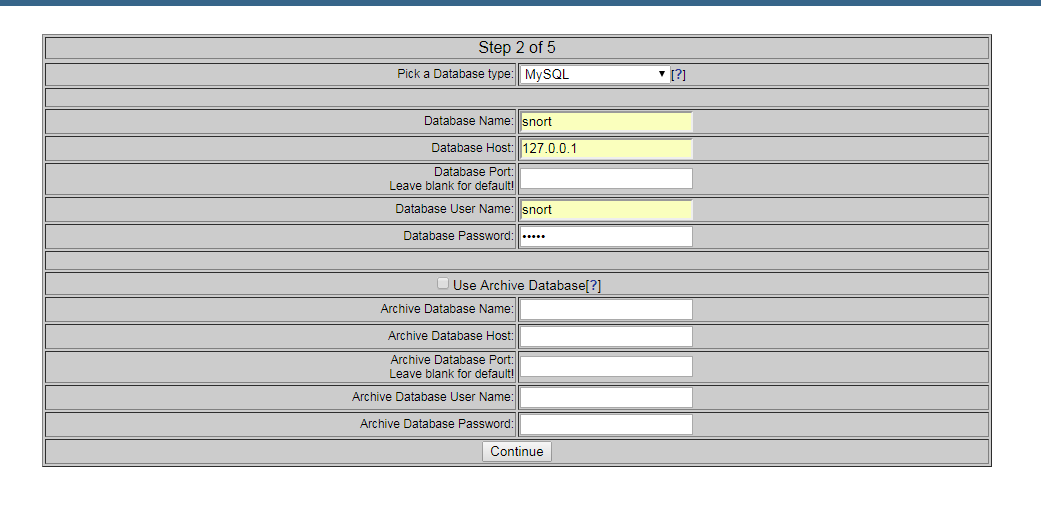
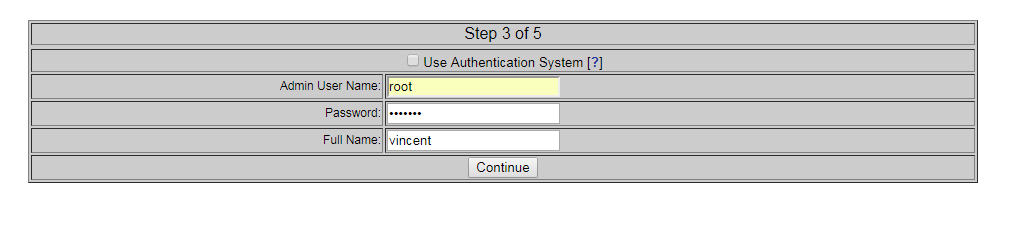
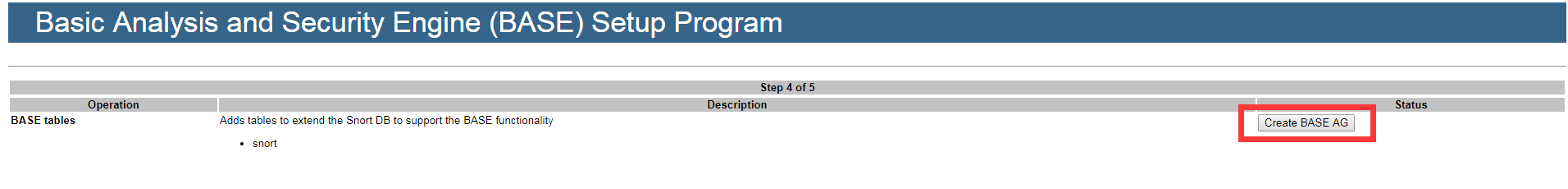
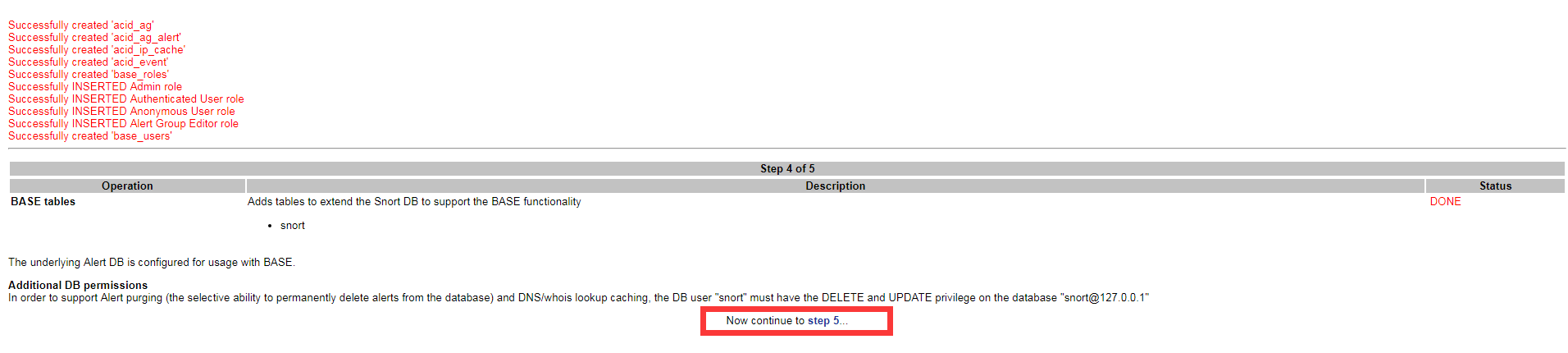
Install and configure Snort and Barnyard2:
# Install DAQ
yum -y install gcc flex bison tcpdump \
zlib zlib-devel libpcap libpcap-devel \
pcre pcre-devel libdnet libdnet-devel \
autoconf automake libtool
cd /tmp
tar -xf /tmp/daq-2.0.6.tar.gz
cd daq-2.0.6
./configure
make && make install
cd /usr/local/lib
ldconfig -v /usr/local/lib
# Install Snort
cd /tmp
tar -xf /tmp/snort-2.9.11.1.tar.gz
cd snort-2.9.11.1
./configure --enable-sourcefire
make && make install
cd /usr/local/lib
ldconfig -v /usr/local/lib
# Configure snort
mkdir /etc/snort
mkdir /var/log/snort
mkdir /usr/local/lib/snort_dynamicrules
mkdir /etc/snort/rules
touch /etc/snort/rules/white_list.rules
touch /etc/snort/rules/black_list.rules
cd /tmp/snort-2.9.11.1/etc
cp -av gen-msg.map threshold.conf \
classification.config reference.config \
unicode.map snort.conf /etc/snort/
# Configuration Change Path
sed -i 's|^\(var RULE_PATH\).*|\1 /etc/snort/rules|g' /etc/snort/snort.conf
sed -i 's|^\(var SO_RULE_PATH\).*|\1 /etc/snort/so_rules|g' /etc/snort/snort.conf
sed -i 's|^\(var PREPROC_RULE_PATH\).*|\1 /etc/snort/preproc_rules|g' /etc/snort/snort.conf
sed -i 's|^\(var WHITE_LIST_PATH\).*|\1 /etc/snort/rules|g' /etc/snort/snort.conf
sed -i 's|^\(var BLACK_LIST_PATH\).*|\1 /etc/snort/rules|g' /etc/snort/snort.conf
# Configure the log directory
sed -i 's|^# config logdir:|&\nconfig logdir: /var/log/snort|g' /etc/snort/snort.conf
# Configure the output plug-in
sed -i 's|^# output unified2:.*$|&\noutput unified2: filename snort.log,limit 128|g' /etc/snort/snort.conf
# Unzip Installation Configuration Rules
cd /tmp
tar -xf snortrules-snapshot-29111.tar.gz -C /etc/snort/
cp /etc/snort/etc/sid-msg.map /etc/snort/
# Test snort
snort -T -i eth0 -c /etc/snort/snort.conf
# - T Specifies Startup Mode: Testing
# - i Specify Network Interface
# - c Specifies the configuration file
# Snort successfully validated the configuration!
# Snort exiting
# Indicates that the test has passed
# Install barnyard2
cd /tmp/barnyard2-1.9
./autogen.sh
./configure --with-mysql \
--with-mysql-libraries=/usr/lib64/mysql/
make && make install
# Configure barnyard2
mkdir /var/log/barnyard2
touch /var/log/snort/barnyard2.waldo
cp -av /tmp/barnyard2-1.9/etc/barnyard2.conf /etc/snort
# Modify configuration files
cat >>/etc/snort/barnyard2.conf<<EOF
config logdir: /var/log/barnyard2
config hostname: localhost
config interface: eth0
config waldo_file:/var/log/snort/barnyard.waldo
output database: log, mysql, user=snort password=snort dbname=snort host=localhost
EOF
# Testing barnyard2
barnyard2 -c /etc/snort/barnyard2.conf \
-d /var/log/snort -f snort.log \
-w /var/log/snort/barnyard2.waldo
# - c Specifies the configuration file
# - d Specifies the log directory
# - f Specifies log file
# - w Specifies the waldo file
# If "Waiting for new spool file" appears, the configuration is successful
# ctrl+c termination testTest IDS:
# Testing whether IDS works properly
# Adding test rules
echo 'alert icmp any any -> any any (msg: "IcmP Packet detected";sid:1000001;)'>>/etc/snort/rules/local.rules
# Add a rule for checking ping packages
# Actions made after alert triggers rules
# icmp Protocol type
# The first any source IP (network segment), any represents arbitrary
# The second any source port, any represents arbitrary
# -> Direction
# The third any destination IP (network segment), any represents arbitrary
# The fourth any destination port, any represents arbitrary
# Msg character alarm name
# Sid ID number, rules written by individuals use more than 1,000,000
# Start LAMP
service mysqld restart
service httpd restart
# Manually start barnyard2 and snort
barnyard2 -c /etc/snort/barnyard2.conf \
-d /var/log/snort -f snort.log \
-w /var/log/snort/barnyard2.waldo -D
snort -c /etc/snort/snort.conf -i eth0 -D
# PING host test
ping 192.168.77.200
# See http://192.168.77.200/base/base_main.php
# Manual stop IDS
killall -9 snort barnyard2
service mysqld stop
service httpd stop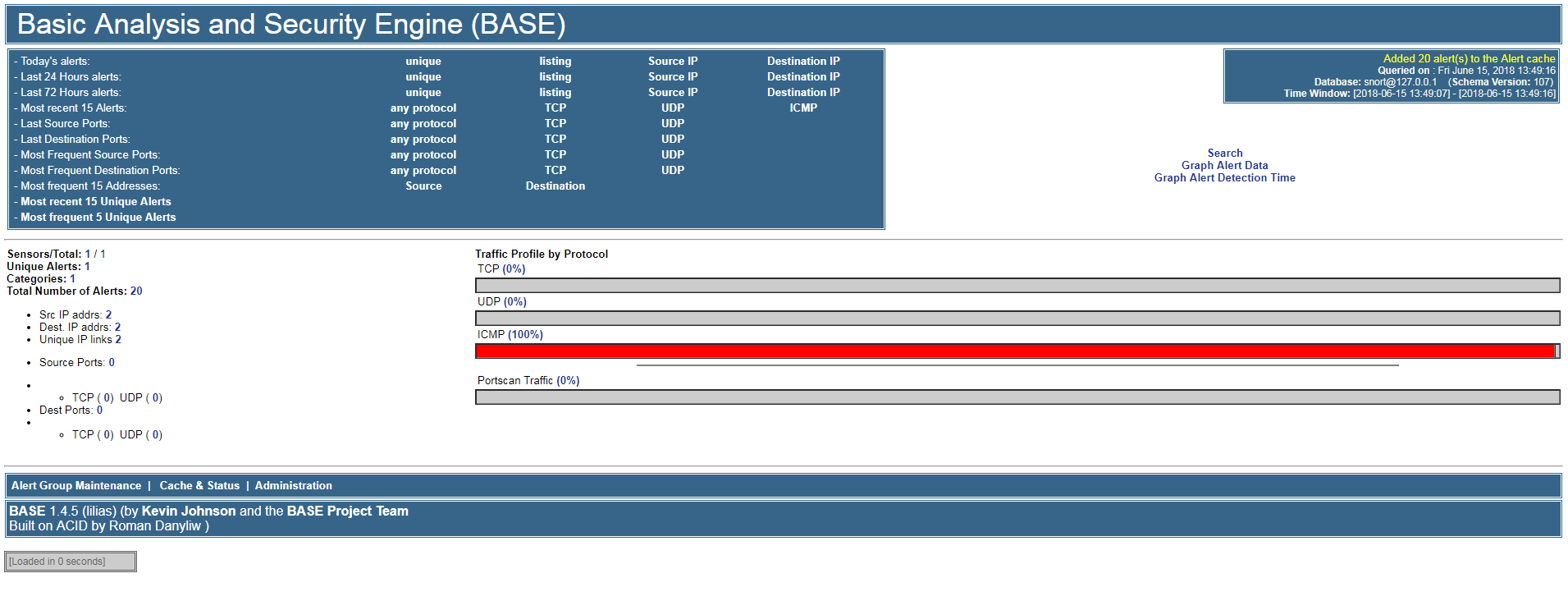
[TOC]