iptables filter small table case
- Introduce two possible future examples of iptables filter tables
Case 1. Requirements (Release of designated ports)
- Specify ports 80, 21, 22 to release, and 22 to specify an ip segment
- To fulfill this requirement, we need to write a script
vi /usr/local/sbin/iptables.sh //Add the following ######The editorial content is as follows######## #! /bin/bash ipt="/usr/sbin/iptables" //Define a variable to write an absolute path $ipt –F // Preemptive Rules $ipt -P INPUT DROP //Define some strategies $ipt -P OUTPUT ACCEPT $ipt -P FORWARD ACCEPT $ipt -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT //Adding rules to specify state release $ipt -A INPUT -s 192.168.133.0/24 -p tcp --dport 22 -j ACCEPT $ipt -A INPUT -p tcp --dport 80 -j ACCEPT $ipt -A INPUT -p tcp --dport 21 -j ACCEPT Designated port release
Case 2. Requirements (can connect to an external network, but can not ping locally)
- That's equivalent to banning ping locally
iptables -I INPUT -p icmp --icmp-type 8 -j DROP
iptables nat table application
Prepare for the goal of uuuuuuuuuuu
** A machine two network cards ens33(192.168.10.129), ens37(192.168.110.110), ens33 can access the external network, ens37 is only an internal network.
B machine only has en S37 (192.168.110.90), and A machine en S37 can communicate with each other. * * - Note: The two network cards ip is written in the same way as the new network cards in different segments of their own network cards.
- Get ready
- Open two clients and add two new network cards to them
- Command: ifconfig ens37 192.168.110.10/24 is used to add a new network card IP, of course, you can edit the configuration file directly.
- The ip gateway of the two new network cards should be the same
- Finally, remember to use cmd to check for compliance
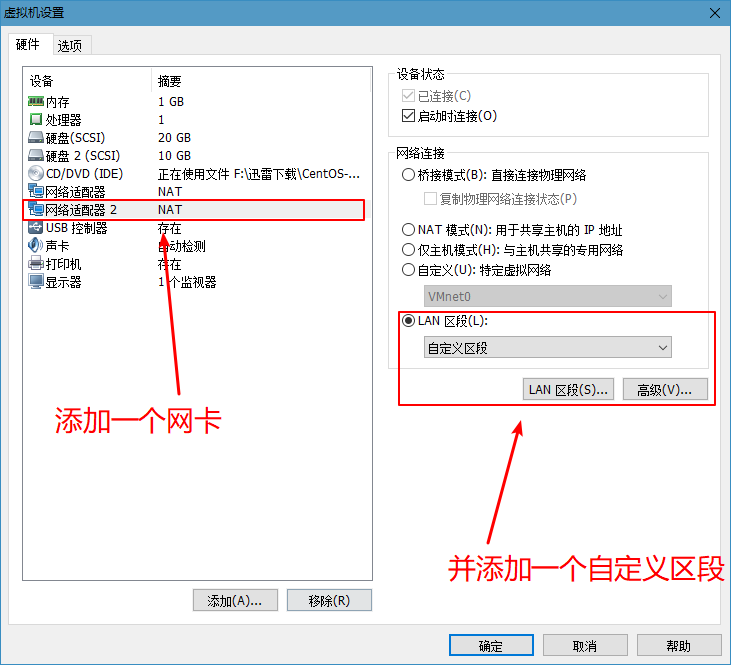
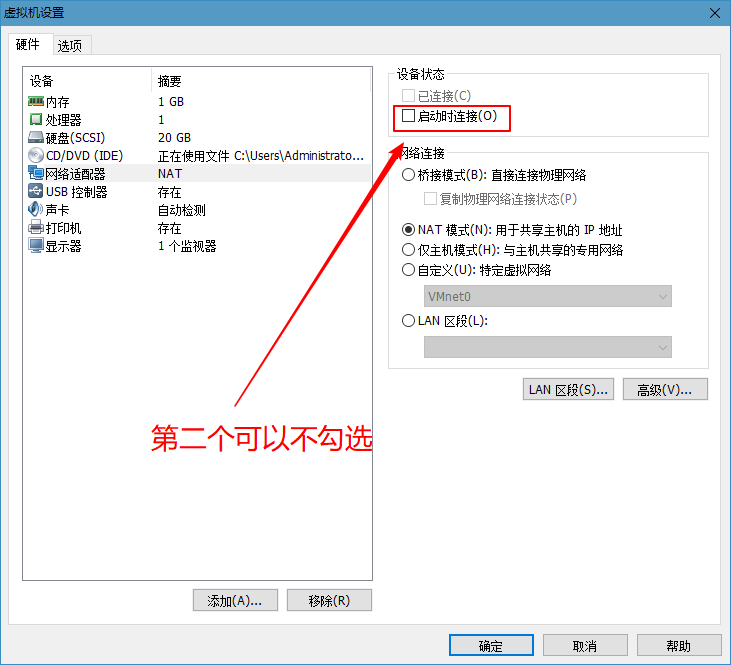
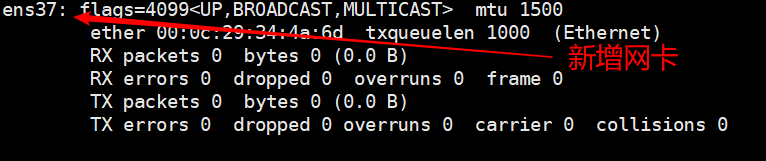
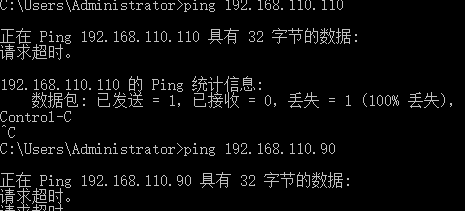
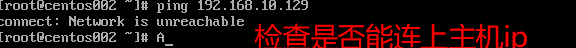
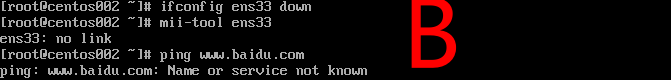
Requirement 1: B machines can be connected to the external network
- Step 1: Open Routing Forwarding on A Machine
- Check if the kernel forwarding is turned on: when the output of cat/proc/sys/net/ipv4/ip_forward is 0, it indicates that it is not turned on
- Open, change 0 to 1: echo "1" >! $
[root@centos001 ~]# cat /proc/sys/net/ipv4/ip [root@centos001 ~]# cat /proc/sys/net/ipv4/ip ip_default_ttl ipfrag_max_dist ip_dynaddr ipfrag_secret_interval ip_early_demux ipfrag_time ip_forward ip_local_port_range ip_forward_use_pmtu ip_local_reserved_ports ipfrag_high_thresh ip_nonlocal_bind ipfrag_low_thresh ip_no_pmtu_disc [root@centos001 ~]# cat /proc/sys/net/ipv4/ip_forward 0 [root@centos001 ~]# echo "1" > !$ echo "1" > /proc/sys/net/ipv4/ip_forward [root@centos001 ~]# !cat cat /proc/sys/net/ipv4/ip_forward 1
- The second step is to add a rule to the nat table of machine A in order to make the network segment accessible to the internet.
[root@centos001 ~]# iptables -t nat -A POSTROUTING -s 192.168.110.0/24 -o ens33 -j MASQUERADE [root@centos001 ~]# iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 MASQUERADE all -- * ens33 192.168.100.0/24 0.0.0.0/0 //At the bottom, we can see the rules we added.
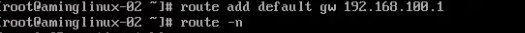
- Step 3: Adding Gateway
Demand 2:
- C machine can only communicate with A, so that C machine can directly connect to port 22 of B machine.
Open Route Forwarding echo "1" >/ proc/sys/net/ipv4/ip_forward on A
Execute iptables - t NAT - A PREROUTING - D 192.168.133.130 - P TCP -- dport 1122 - J DNA T -- to 192.168.100.100:22 on A Execute iptables -t nat -A POSTROUTING -s 192.168.100.100 -j SNAT --to 192.168.133.130
Setting up gateway on B is 192.168.100.1
extend
- iptables application in a network segment
http://www.aminglinux.com/bbs/thread-177-1-1.html - sant,dnat,masquerade
http://www.aminglinux.com/bbs/thread-7255-1-1.html - iptables limit syn rate
http://www.aminglinux.com/bbs/thread-985-1-1.html http://jamyy.us.to/blog/2006/03/206.html