FROM: http://blog.csdn.net/hovan/article/details/42674055
from My Opinion on trust zone You know, trustzone-enabled chips run in two worlds.
Ordinary world, security world, corresponding to Qualcomm here is HLOS,QSEE.
The following picture:

Here are the HLOS and QSEE software Framework chart
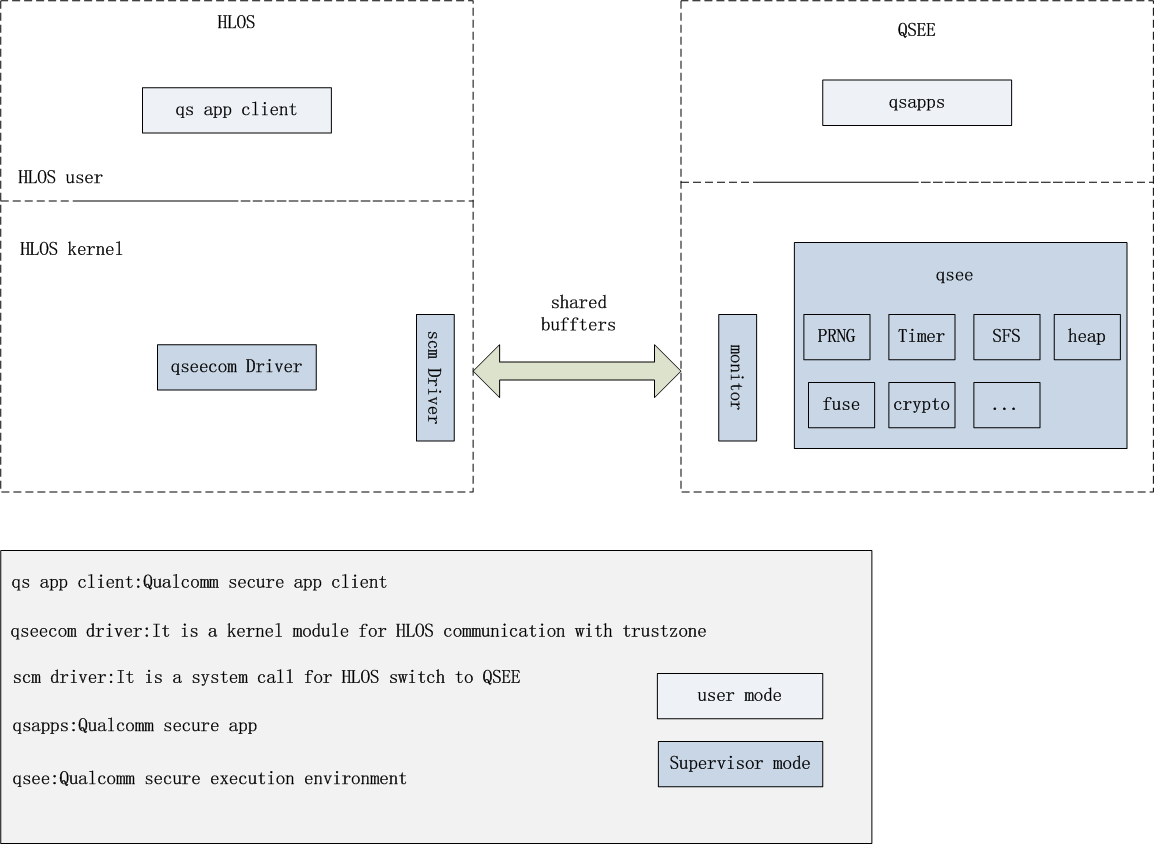
HLOS is divided into kernel layer and user layer. The user layer starts the app on trustzone through the API provided by qseecom.
In addition to providing API s, qseecom driver also calls scm functions for world switching.
When the scm driver receives a call from qseecom, it puts HLOS-related data (including instruction parameters) into its buffer, and then executes the scm call.
qsapp accepts requests from HLOS through the api provided by qsee and returns the execution results to HLOS.
In addition to providing API s, qsee also passes data from HLOS to qsapp from monitor, and then returns data from qsapp to HLOS.
The monitor doesn't need to say that it handles shared buffer s as well as switching the world.
It's a rough sketch. The details are rather complicated and there is no open source.
The whole invocation process is illustrated by a simple qseecom_security_test code.
The following picture:
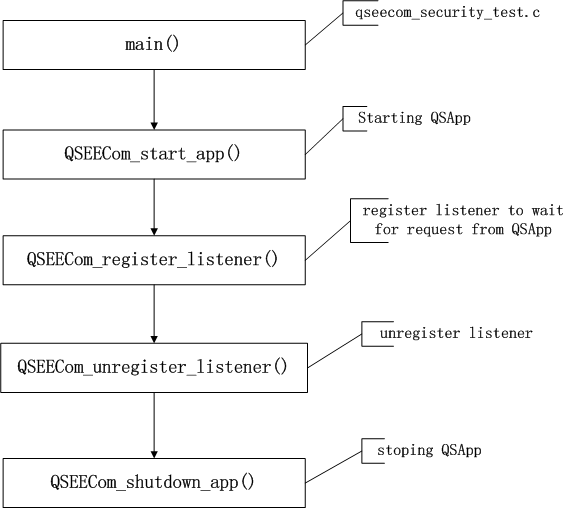
qseecom_security_test.c
-
int main( int argc, char *argv[] )
-
{
-
....
-
-
-
memset( g_qseeCommHandles, 0, sizeof(g_qseeCommHandles) );
-
memset( g_xors, 0, sizeof(g_xors) );
Initialize the global variable g_qseeCommHandles first
-
for( j = 0; j < NUM_CLIENTS; j++ ) {
-
-
-
-
ret = sem_init( &barrier[j], 0, 0 );
-
if( ret ) {
-
LOGD( "barrier init failed %i, %i", ret, errno );
-
g_err = -1;
-
break;
-
}
-
-
ret = pthread_create( &threads[j], NULL, &test_thread, (void*)j );
-
}
Initialize a barrier signal variable for synchronization at thread creation
Then call the pthread_create() function to create the test_thread thread thread, which will start QSApp.
-
void *test_thread( void* threadid )
-
{
-
...
-
do {
-
.....
-
LOGD( "T%#X: Starting QSApp...", (uint32_t)threadid );
-
ret = QSEECom_start_app( &g_qseeCommHandles[tid][0], "/firmware/image",
-
"securitytest", sizeof(qseecom_req_res_t)*2 );
-
LOGD( "T%#X: Started QSApp...", (uint32_t)threadid );
-
CHECK_RETURN( ret, __LINE__ );
Follow to the test_thread thread thread
Call the QSEECom_start_app() function to start QSApp.
This function is implemented in kernel as follows:
qseecom.c
-
static int qseecom_load_app(struct qseecom_dev_handle *data, void __user *argp)
-
{
-
...
-
-
ihandle = ion_import_dma_buf(qseecom.ion_clnt,
-
load_img_req.ifd_data_fd);
-
...
-
-
ret = scm_call(SCM_SVC_TZSCHEDULER, 1, &load_req,
-
sizeof(struct qseecom_load_app_ireq),
-
&resp, sizeof(resp));
Get shared buf fd, for communication with the security world
Call scm_call() to get into the safe world.
scm_call() is implemented as follows:
arch/arm/mach-msm/scm.c
-
int scm_call(u32 svc_id, u32 cmd_id, const void *cmd_buf, size_t cmd_len,
-
void *resp_buf, size_t resp_len)
-
{
-
...
-
-
ret = scm_call_common(svc_id, cmd_id, cmd_buf, cmd_len, resp_buf,
-
resp_len, cmd, len);
-
kfree(cmd);
-
return ret;
-
}
The implementation of scm_call_common is as follows:
-
static int scm_call_common(u32 svc_id, u32 cmd_id, const void *cmd_buf,
-
size_t cmd_len, void *resp_buf, size_t resp_len,
-
struct scm_command *scm_buf,
-
size_t scm_buf_length)
-
{
-
....
-
-
mutex_lock(&scm_lock);
-
ret = __scm_call(scm_buf);
-
mutex_unlock(&scm_lock);
-
if (ret)
-
return ret;
-
-
rsp = scm_command_to_response(scm_buf);
-
start = (unsigned long)rsp;
-
-
do {
-
scm_inv_range(start, start + sizeof(*rsp));
-
} while (!rsp->is_complete);
-
-
end = (unsigned long)scm_get_response_buffer(rsp) + resp_len;
-
scm_inv_range(start, end);
-
-
if (resp_buf)
-
memcpy(resp_buf, scm_get_response_buffer(rsp), resp_len);
-
-
return ret;
-
}
Call _scm_call() into the safe world and call scm_get_response_buffer() to get the information returned from the safe world for the above QSApp client to use
_ scm_call is implemented as follows:
-
static int __scm_call(const struct scm_command *cmd)
-
{
-
...
-
-
ret = smc(cmd_addr);
-
...
-
-
return ret;
-
}
smc is implemented as follows:
-
static u32 smc(u32 cmd_addr)
-
{
-
int context_id;
-
register u32 r0 asm("r0") = 1;
-
register u32 r1 asm("r1") = (u32)&context_id;
-
register u32 r2 asm("r2") = cmd_addr;
-
do {
-
asm volatile(
-
__asmeq("%0", "r0")
-
__asmeq("%1", "r0")
-
__asmeq("%2", "r1")
-
__asmeq("%3", "r2")
-
#ifdef REQUIRES_SEC
-
".arch_extension sec\n"
-
#endif
-
"smc #0 @ switch to secure world\n"
-
: "=r" (r0)
-
: "r" (r0), "r" (r1), "r" (r2)
-
: "r3");
-
} while (r0 == SCM_INTERRUPTED);
-
-
return r0;
-
}
QSApp is an assembler. Well, QSApp in the safe world is running. When QSApp completes the corresponding service, it will return the data. This function will return.
Starting QSApp has been completed. Now register listener, which is used to listen for requests from QSApp. Because sometimes QSApp also needs HLOS to do something.
The realization is as follows:
-
void *listener_thread( void* threadid )
-
{
-
....
-
-
do {
-
...
-
-
LOGD( "L%#X: Registering as listener with QSApp...", (uint32_t)threadid );
-
ret = QSEECom_register_listener( &g_qseeCommHandles[parent_tid][tid], GET_LSTNR_SVC_ID(parent_tid, tid),
-
sizeof(qseecom_req_res_t), 0 );
-
-
....
-
-
for( ;; ) {
-
-
ret = QSEECom_receive_req( g_qseeCommHandles[parent_tid][tid], req_res, sizeof(qseecom_req_res_t) );
-
if( ret ) break;
-
-
....
-
-
-
ret = QSEECom_send_resp( g_qseeCommHandles[parent_tid][tid], req_res, sizeof(qseecom_req_res_t) );
-
CHECK_RETURN( ret, __LINE__ );
-
}
-
} while( 0 );
-
...
-
}
This function is longer, simplify it, step by step.
First, call the QSEECom_register_listener() function to register the listener and tell QSApp that I can receive your application.
If you see the for loop again, it's waiting for the message from QSApp, but if there's a message from QSEECom_reveive_req, it's returned, and then it's processed here.
Then call qSEECom_send_resp() to send the response to QSApp.
Whether starting QSApp or registering listener is executed in threads, once all threads exit, the QSEECom_shutdown_app() function is called to stop QSApp.
The whole process is completed. As follows:
-
void *test_thread( void* threadid )
-
{
-
...
-
if ( g_qseeCommHandles[tid][0] != NULL ) {
-
QSEECom_shutdown_app( &g_qseeCommHandles[tid][0] );
-
}
-
} while( 0 );
-
-
pthread_exit( NULL );
-
return NULL;
-
}
Note: The functions at the beginning of QSEECom_XX are implemented in qseecom.c of kernel, and the system calls of SCM are implemented in scm.c.
HLOS user layer grasps QSEEComAPI.h file
HLOS kernel layer grasps qseecom.c and scm.c files
Thank you


