I. EC2
For the application above EC2, do not assign User Credentials, use IAM Role Attachment.
You can access the meatdata of EC2 to view the Role permission granted
curl http://169.254.169.254/latest/meta-data/iam/security-credentials/
2, Software on local laptop
For users who develop and test on their own computers, users need access rights of S3, and do not assign rights to users, so as to avoid losses caused by AK/SK loss. We can assign a cross account role to users, which allows users to obtain temporary AK/SK by using the interface assume role, and then access AWS resources.
2.1 create user alice
Do not assign any rights to the user.
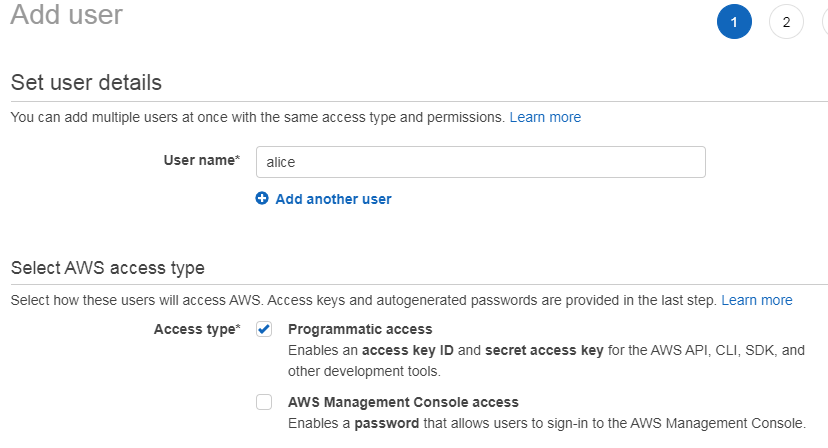
Finally, we get the user's AK/SK
Access key ID : AKIA5NAGHF6N2WFTQZP6 Secret access key: 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
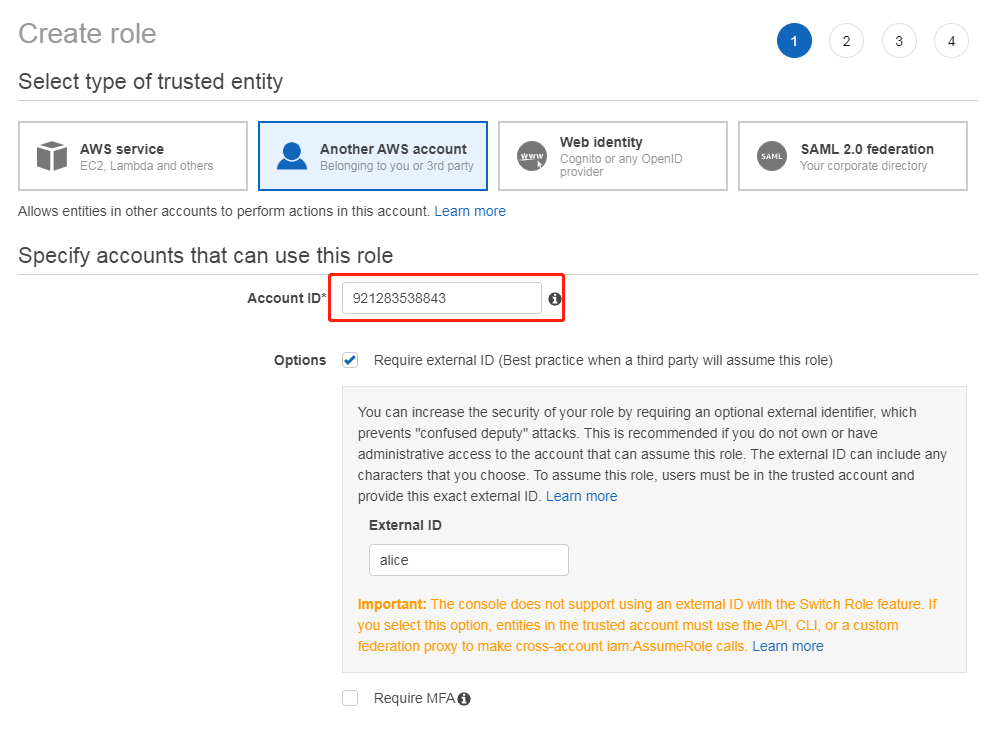
2.2. Create a cross account Role
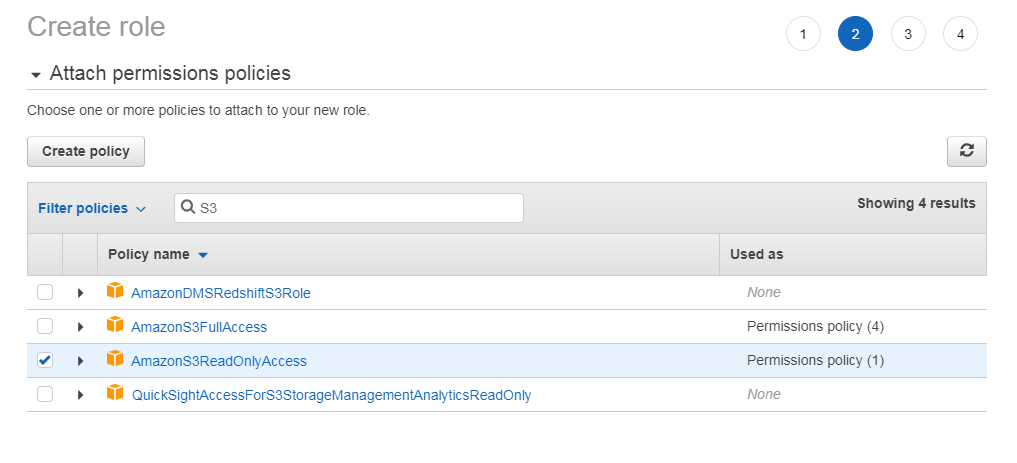
Add permissions to roles.
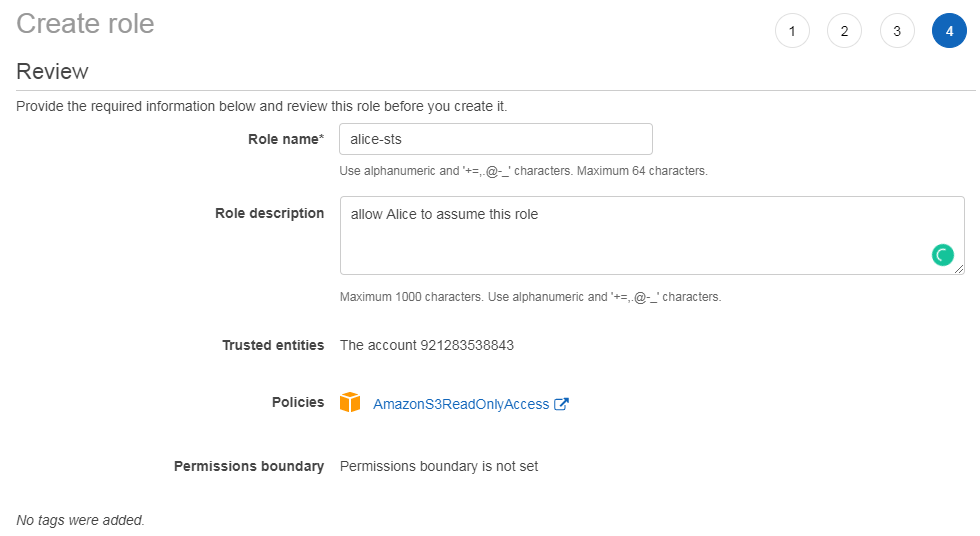
Generated Role ARN: ARN: AWS: iam:: 921283538843: role / Alice STS
Give alice the right to assume role.
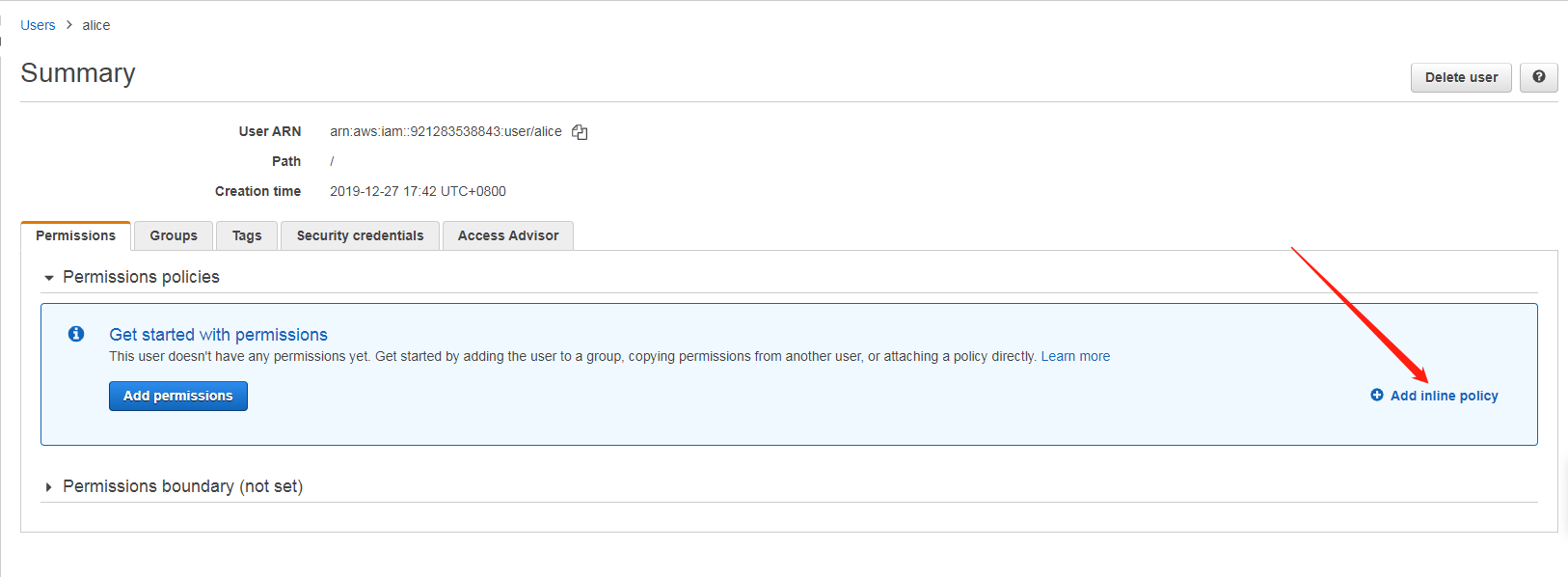
The Policy format is as follows:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::921283538843:role/alice-sts"
}
]
}2.3 test user authority
Use AK/SK directly to check whether the user has the corresponding permission.
Use aws configure configuration.
wangzan:~/.aws $ aws configure
AWS Access Key ID [****************H6YU]: AKIA5NAGHF6N2WFTQZP6
AWS Secret Access Key [****************bVA/]: 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
Default region name [us-east-1]:
Default output format [json]:
wangzan:~/.aws $ aws sts get-caller-identity
{
"Account": "921283538843",
"UserId": "AIDA5NAGHF6NZASTSA7Y6",
"Arn": "arn:aws:iam::921283538843:user/alice"
}
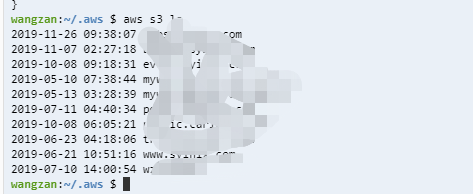
wangzan:~/.aws $ aws s3 ls
An error occurred (AccessDenied) when calling the ListBuckets operation: Access DeniedYou can't get permission if you use it directly. Let's use assume role.
wangzan:~/.aws $ aws sts assume-role --role-arn arn:aws:iam::921283538843:role/alice-sts --role-session-name s3-access --external-id alice
{
"AssumedRoleUser": {
"AssumedRoleId": "AROA5NAGHF6NSZZVCDMHE:s3-access",
"Arn": "arn:aws:sts::921283538843:assumed-role/alice-sts/s3-access"
},
"Credentials": {
"SecretAccessKey": "sJuL4gzx6ScdloJyyO6J4mCnFdtMcFm/uAPVjOz7",
"SessionToken": "IQoJb3JpZ2luX2VjECMaCXVzLWVhc3QtMSJHMEUCIGkmsQ250D6CqAQfsWxfMog5SYovpefP5jMS2+cOUexGAiEAnlNtMrdhtz60YEjEoCCHce3YVQOMTCXf2gAJf7RSv+Aq2QEIi///////////ARAAGgw5MjEyODM1Mzg4NDMiDE3ySalHbx1Bf97NjiqtAcmjLjLW8FsTQMkO1xBUFbREur7ZqtO/AGR2oG6AnZIUUXNr2RRcmE6+IQgArlMBzppC/Q2uAnPkbz1GIdMKohUbL+9d2eZIOBwr9Vs/43iFSuAsdiLa9C5HI3++keG+5IkjS/Yj9rP30p1Bj2JK6TlTUQnZtINf1im4PmoIrxotWXkJH6BU8kG7PJ3bOgFCRWeG8w3h/d3sCx4GqUmnKISKosHSBUidm6PJ41GNMMSul/AFOuMBB0LfECQaR+C8+uxpil5KRE0a5DDq+IPDWaPQIpQ+s5q4ewLpSfGKTwKTrDPk7Hi1R/vhuNKNNUcgSjzz5Wh4NwjkbGmddcFDvlZCv2rXIRMPbcM6i/bXTz3HbCX/f5K3bcubiIShpezfDm/00Iy+qGPzaqDLZ5XNkMZ9msXBVYYd0YS++wprPGpX5GQBKh/vqS4HPWCeqRRrHbKGQO3/ycMXjjeHKpY07WcXhM3lbDR583JDcLTsfItldFeC8y4aXMGugTLUwmQm9pihC/TxP13zjWl1rh/cgR4FGDFbosb1Bq0=",
"Expiration": "2019-12-27T11:04:52Z",
"AccessKeyId": "ASIA5NAGHF6NZJHS6VVN"
}
}Then edit ~ /. aws/credentials and put the generated Credentials in it, as follows:
[default] aws_access_key_id = ASIA5NAGHF6NZJHS6VVN aws_secret_access_key = sJuL4gzx6ScdloJyyO6J4mCnFdtMcFm/uAPVjOz7 aws_session_token = IQoJb3JpZ2luX2VjECMaCXVzLWVhc3QtMSJHMEUCIGkmsQ250D6CqAQfsWxfMog5SYovpefP5jMS2+cOUexGAiEAnlNtMrdhtz60YEjEoCCHce3YVQOMTCXf2gAJf7RSv+Aq2QEIi///////////ARAAGgw5MjEyODM1Mzg4NDMiDE3ySalHbx1Bf97NjiqtAcmjLjLW8FsTQMkO1xBUFbREur7ZqtO/AGR2oG6AnZIUUXNr2RRcmE6+IQgArlMBzppC/Q2uAnPkbz1GIdMKohUbL+9d2eZIOBwr9Vs/43iFSuAsdiLa9C5HI3++keG+5IkjS/Yj9rP30p1Bj2JK6TlTUQnZtINf1im4PmoIrxotWXkJH6BU8kG7PJ3bOgFCRWeG8w3h/d3sCx4GqUmnKISKosHSBUidm6PJ41GNMMSul/AFOuMBB0LfECQaR+C8+uxpil5KRE0a5DDq+IPDWaPQIpQ+s5q4ewLpSfGKTwKTrDPk7Hi1R/vhuNKNNUcgSjzz5Wh4NwjkbGmddcFDvlZCv2rXIRMPbcM6i/bXTz3HbCX/f5K3bcubiIShpezfDm/00Iy+qGPzaqDLZ5XNkMZ9msXBVYYd0YS++wprPGpX5GQBKh/vqS4HPWCeqRRrHbKGQO3/ycMXjjeHKpY07WcXhM3lbDR583JDcLTsfItldFeC8y4aXMGugTLUwmQm9pihC/TxP13zjWl1rh/cgR4FGDFbosb1Bq0=
Then go to request S3.
wangzan:~/.aws $ aws sts get-caller-identity
{
"Account": "921283538843",
"UserId": "AROA5NAGHF6NSZZVCDMHE:s3-access",
"Arn": "arn:aws:sts::921283538843:assumed-role/alice-sts/s3-access"
}
2.4. Automatic change of temporary authority
Modify ~ /. aws/credentials. There is a problem. I will remove the restriction in that Role, that is, the external ID.
[alice] aws_access_key_id = AKIA5NAGHF6N2WFTQZP6 aws_secret_access_key = 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 aws_session_token = [default] role_arn = arn:aws:iam::921283538843:role/alice-sts source_profile = alice
Take a look at the current Role.
wangzan:~/.aws $ aws sts get-caller-identity
{
"Account": "921283538843",
"UserId": "AROA5NAGHF6NSZZVCDMHE:botocore-session-1577441862",
"Arn": "arn:aws:sts::921283538843:assumed-role/alice-sts/botocore-session-1577441862"
}