Ansible's specified user and password login, secret-free login, specified ssh port, and host list Inventory configuration
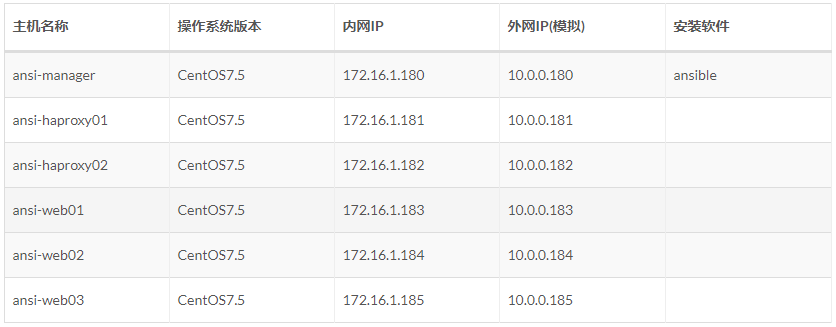
It is not necessary to modify the ansible configuration in practice, or it is only necessary to modify the ansible configuration.
Add user account
Explain:
1. Login accounts used by operations and maintenance personnel;
2. All businesses are placed under / app / in the "home directory of yun users" to avoid the disorder of business data;
3. This user is also used by ansible because almost all production environments prohibit root from logging on remotely (so this yun user also has sudo privileges).
1 # Use a dedicated user instead of using root directly 2 # Add users, specify home directories, and specify user passwords 3 # sudo claim 4 # Allow other users to access the directory to view information 5 useradd -u 1050 -d /app yun && echo '123456' | /usr/bin/passwd --stdin yun 6 echo "yun ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers 7 chmod 755 /app/
"Understand" based on password connection
In a real production environment, it is recommended that you use a key-based connection rather than a password connection.
The reasons are as follows:
1. Writing the password directly into the file is a potential security hazard;
2. The password of the production environment may be changed regularly. If password-based connection is used, we will also maintain it frequently, causing high maintenance costs.
3. Based on the key connection, we only need to do one key distribution, and no modification is needed for the later connection.
Inventory Configuration
1 [yun@ansi-manager ansible_info]$ pwd 2 /app/ansible_info 3 [yun@ansi-manager ansible_info]$ cat hosts_pwd 4 # Ungrouped machines, placed in front of all groups 5 # Default port 22, omitted 6 # Mode 1: Host + port + Password 7 172.16.1.180 ansible_ssh_port=22 ansible_ssh_user=yun ansible_ssh_pass='123456' 8 9 # Mode 2: Host + port + Password 10 [proxyservers] 11 172.16.1.18[1:2] ansible_ssh_port=22 ansible_ssh_user=yun ansible_ssh_pass='123456' 12 13 # Mode 3: Host + port + Password 14 [webservers] 15 172.16.1.18[3:5] ansible_ssh_port=22 ansible_ssh_user=yun 16 [webservers:vars] 17 ansible_ssh_pass='123456'
Test Connection
1 [yun@ansi-manager ansible_info]$ ansible 172.16.1.180 -m ping -i ./hosts_pwd # Ordinary User Execution 2 172.16.1.180 | FAILED! => { 3 "msg": "Using a SSH password instead of a key is not possible because Host Key checking is enabled and sshpass does not support this. Please add this host's fingerprint to your known_hosts file to manage this host." 4 } 5 [yun@ansi-manager ansible_info]$ sudo ansible 172.16.1.180 -m ping -i ./hosts_pwd # Authorization using root user execution 6 172.16.1.180 | FAILED! => { 7 "msg": "Using a SSH password instead of a key is not possible because Host Key checking is enabled and sshpass does not support this. Please add this host's fingerprint to your known_hosts file to manage this host." 8 }
A general tip: Because host key checking is enabled, sshpass does not support this.Please add the fingerprint of this host "172.16.1.180" to your local known_hosts file to manage this host.
There are two ways to skip host key checking:
Mode 1: Modify the Linux system configuration
1 [root@ansi-manager ssh]# vim /etc/ssh/ssh_config 2 # AddressFamily any 3 # ConnectTimeout 0 4 # StrictHostKeyChecking ask # Turn on the comment for this configuration and change it to StrictHostKeyChecking no so that Host Key Checking will not occur for all users 5 # IdentityFile ~/.ssh/identity
But this is the configuration that comes with Linux, and we can't change it at will.This is not recommended.
Mode 2: Modify the ansible configuration
1 [root@ansi-manager ansible]# pwd 2 /etc/ansible 3 [root@ansi-manager ansible]# vim ansible.cfg 4 # uncomment this to disable SSH key host checking 5 host_key_checking = False # Remove comments for this configuration
Configuration changes are only valid for root users, not for other normal users.This method is used here.
Connect test again
1 [yun@ansi-manager ansible_info]$ ansible 172.16.1.180 -m ping -i ./hosts_pwd # Ordinary users still can't 2 172.16.1.180 | FAILED! => { 3 "msg": "Using a SSH password instead of a key is not possible because Host Key checking is enabled and sshpass does not support this. Please add this host's fingerprint to your known_hosts file to manage this host." 4 } 5 [yun@ansi-manager ansible_info]$ sudo ansible 172.16.1.180 -m ping -i ./hosts_pwd # Authorization using root user execution 6 172.16.1.180 | SUCCESS => { 7 "ansible_facts": { 8 "discovered_interpreter_python": "/usr/bin/python" 9 }, 10 "changed": false, 11 "ping": "pong" 12 } 13 [yun@ansi-manager ansible_info]$ sudo ansible proxyservers -m ping -i ./hosts_pwd # normal 14 [yun@ansi-manager ansible_info]$ sudo ansible webservers -m ping -i ./hosts_pwd # normal
"Recommended" connection based on secret key
In a real production environment, it is recommended that you use a key-based connection rather than a password connection.
The reasons are as follows:
1. Writing the password directly into the file is a potential security hazard;
2. The password of the production environment may be changed regularly. If password-based connection is used, we will also maintain it frequently, causing high maintenance costs.
3. Based on the key connection, we only need to do one key distribution, and no modification is needed for the later connection.
Implement yun user secret-free key login
Requirements: Secret-free key login 172.16.1.180 to 172.16.1.180, 172.16.1.181, 172.16.1.182, 172.16.1.183, 172.16.1.184, 172.16.1.185 as planned
Therefore, a key needs to be created on 172.16.1.180 machines and distributed to the controlled machines.
Create Secret Key
1 [yun@ansi-manager ~]$ ssh-keygen -t rsa # You can notice that you are using the yun user all the way back 2 # After the build, a ".ssh"Folder 3 [yun@ansi-manager ~]$ ll -d .ssh/ 4 drwx------ 2 yun yun 38 Jul 25 10:51 .ssh/ 5 [yun@ansi-manager ~]$ ll .ssh/ 6 total 8 7 -rw------- 1 yun yun 1675 Jul 25 10:51 id_rsa 8 -rw-r--r-- 1 yun yun 398 Jul 25 10:51 id_rsa.pub
Distribution Key
1 [yun@ansi-manager ~]$ ssh-copy-id -i ~/.ssh/id_rsa.pub 172.16.1.180 2 [yun@ansi-manager ~]$ ssh-copy-id -i ~/.ssh/id_rsa.pub 172.16.1.181 3 [yun@ansi-manager ~]$ ssh-copy-id -i ~/.ssh/id_rsa.pub 172.16.1.182 4 [yun@ansi-manager ~]$ ssh-copy-id -i ~/.ssh/id_rsa.pub 172.16.1.183 5 [yun@ansi-manager ~]$ ssh-copy-id -i ~/.ssh/id_rsa.pub 172.16.1.184 6 [yun@ansi-manager ~]$ ssh-copy-id -i ~/.ssh/id_rsa.pub 172.16.1.185
Test for successful secret-free login
1 [yun@ansi-manager ~]$ ssh 172.16.1.180 # Equivalent to ssh yun@172.16.1.180 2 [yun@ansi-manager ~]$ ssh 172.16.1.181 3 [yun@ansi-manager ~]$ ssh 172.16.1.182 4 [yun@ansi-manager ~]$ ssh 172.16.1.183 5 [yun@ansi-manager ~]$ ssh 172.16.1.184 6 [yun@ansi-manager ~]$ ssh 172.16.1.185
Note: Secret login must be guaranteed for each machine, so authentication is required for each machine.
File description in.ssh directory
1 [yun@ansi-manager .ssh]$ pwd 2 /app/.ssh 3 [yun@ansi-manager .ssh]$ ll 4 total 16 5 -rw------- 1 yun yun 398 Jul 25 11:01 authorized_keys 6 -rw------- 1 yun yun 1675 Jul 25 10:51 id_rsa 7 -rw-r--r-- 1 yun yun 398 Jul 25 10:51 id_rsa.pub 8 -rw-r--r-- 1 yun yun 1120 Jul 25 11:04 known_hosts 9 ######################################################################################## 10 authorized_keys: Stores the public key of the machine to be logged on remotely and secret-free, mainly through this file to record the public keys of multiple machines to be logged on remotely 11 id_rsa: Generated private key file 12 id_rsa.pub: Generated public key file 13 know_hosts: List of known host public keys
Inventory Configuration
1 [yun@ansi-manager ansible_info]$ pwd 2 /app/ansible_info 3 [yun@ansi-manager ansible_info]$ cat hosts_key 4 # Ungrouped machines, placed in front of all groups 5 # Default port 22, omitted 6 # Mode 1, Host + port + secret key 7 172.16.1.180:22 8 9 # Mode 2: Host + port + secret key 10 [proxyservers] 11 172.16.1.18[1:2]:22 12 13 # Mode 3: Alias + Host + port + Password 14 [webservers] 15 web01 ansible_ssh_host=172.16.1.183 ansible_ssh_port=22 16 web02 ansible_ssh_host=172.16.1.184 ansible_ssh_port=22 17 web03 ansible_ssh_host=172.16.1.185 ansible_ssh_port=22
Test Connection
Test One
1 [yun@ansi-manager ansible_info]$ ansible 172.16.1.180 -m ping -i ./hosts_key 2 172.16.1.180 | SUCCESS => { 3 "ansible_facts": { 4 "discovered_interpreter_python": "/usr/bin/python" 5 }, 6 "changed": false, 7 "ping": "pong" 8 }
Test Two
1 [yun@ansi-manager ansible_info]$ ansible proxyservers -m ping -i ./hosts_key 2 172.16.1.181 | SUCCESS => { 3 "ansible_facts": { 4 "discovered_interpreter_python": "/usr/bin/python" 5 }, 6 "changed": false, 7 "ping": "pong" 8 } 9 172.16.1.182 | SUCCESS => { 10 "ansible_facts": { 11 "discovered_interpreter_python": "/usr/bin/python" 12 }, 13 "changed": false, 14 "ping": "pong" 15 }
Test Three
1 [yun@ansi-manager ansible_info]$ ansible webservers -m ping -i ./hosts_key 2 web03 | SUCCESS => { 3 "ansible_facts": { 4 "discovered_interpreter_python": "/usr/bin/python" 5 }, 6 "changed": false, 7 "ping": "pong" 8 } 9 web01 | SUCCESS => { 10 "ansible_facts": { 11 "discovered_interpreter_python": "/usr/bin/python" 12 }, 13 "changed": false, 14 "ping": "pong" 15 } 16 web02 | SUCCESS => { 17 "ansible_facts": { 18 "discovered_interpreter_python": "/usr/bin/python" 19 }, 20 "changed": false, 21 "ping": "pong" 22 }
Mixed and Host Group modes
Inventory Configuration
1 [yun@ansi-manager ansible_info]$ pwd 2 /app/ansible_info 3 [yun@ansi-manager ansible_info]$ cat hosts_group 4 # Ungrouped machines, placed in front of all groups 5 # Default port 22, omitted 6 # Mode 1, Host + port + secret key 7 172.16.1.180 8 9 # Mode 1. Host group variables + Host + Password 10 [proxyservers] 11 172.16.1.18[1:2] ansible_ssh_port=22 ansible_ssh_user=yun ansible_ssh_pass='123456' 12 13 # Mode 2 host group variables + Host + secret key 14 [webservers] 15 172.16.1.18[3:5]:22 16 17 # Define multiple groups, aggregate multiple groups 18 # The website group consists of two subgroups [proxyservers, webservers] 19 [website:children] 20 proxyservers 21 webservers
Note: Defining multiple groups is OK.However, you cannot configure both the password and the secret key as above, which increases maintenance costs.Password and secret key configurations are used here for demonstration purposes.
Test Connection
Test One
1 # If ~/.ssh/known_hosts Controlled fingerprint is not added to the file, so the operation must be authorized 2 [yun@ansi-manager ansible_info]$ sudo ansible proxyservers -m ping -i ./hosts_group --list-hosts 3 hosts (2): 4 172.16.1.181 5 172.16.1.182 6 [yun@ansi-manager ansible_info]$ sudo ansible proxyservers -m ping -i ./hosts_group 7 172.16.1.182 | SUCCESS => { 8 "ansible_facts": { 9 "discovered_interpreter_python": "/usr/bin/python" 10 }, 11 "changed": false, 12 "ping": "pong" 13 } 14 172.16.1.181 | SUCCESS => { 15 "ansible_facts": { 16 "discovered_interpreter_python": "/usr/bin/python" 17 }, 18 "changed": false, 19 "ping": "pong" 20 }
Test Two
1 [yun@ansi-manager ansible_info]$ ansible webservers -m ping -i ./hosts_group --list-hosts 2 hosts (3): 3 172.16.1.183 4 172.16.1.184 5 172.16.1.185 6 [yun@ansi-manager ansible_info]$ ansible webservers -m ping -i ./hosts_group 7 ..................
Test Three
1 [yun@ansi-manager ansible_info]$ ansible website -m ping -i ./hosts_group --list-hosts 2 hosts (5): 3 172.16.1.181 4 172.16.1.182 5 172.16.1.183 6 172.16.1.184 7 172.16.1.185 8 [yun@ansi-manager ansible_info]$ ansible website -m ping -i ./hosts_group
Test 4
Special group:all
1 [yun@ansi-manager ansible_info]$ ansible all -m ping -i ./hosts_group --list-hosts 2 hosts (6): 3 172.16.1.180 4 172.16.1.181 5 172.16.1.182 6 172.16.1.183 7 172.16.1.184 8 172.16.1.185 9 [yun@ansi-manager ansible_info]$ ansible all -m ping -i ./hosts_group
-—END-—
If you feel good, pay attention to the next chop (-^O^-)!
