Ansible playbook Vault encryption details and use cases
Host Planning
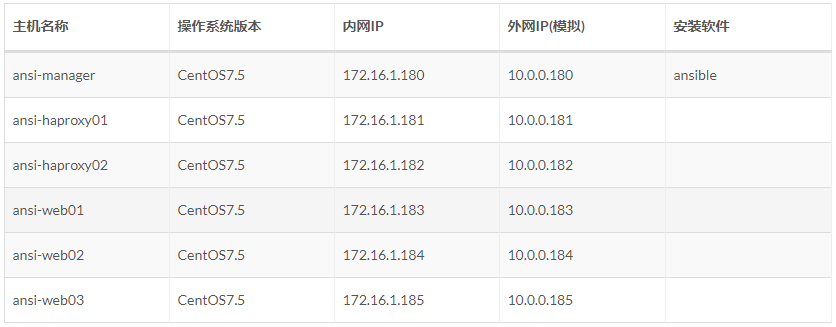
Add user account
Explain:
1. Login accounts used by operations and maintenance personnel;
2. All businesses are placed under / app / in the "home directory of yun users" to avoid the disorder of business data;
3. This user is also used by ansible because almost all production environments prohibit root from logging on remotely (so this yun user also has sudo privileges).
1 # Use a dedicated user instead of using root directly 2 # Add users, specify home directories, and specify user passwords 3 # sudo claim 4 # Allow other users to access the directory to view information 5 useradd -u 1050 -d /app yun && echo '123456' | /usr/bin/passwd --stdin yun 6 echo "yun ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers 7 chmod 755 /app/
Ansible Configuration Inventory
The following list of host configurations follows
1 [yun@ansi-manager ansible_info]$ pwd 2 /app/ansible_info 3 [yun@ansi-manager ansible_info]$ cat hosts_key 4 # Mode 1, Host + port + secret key 5 [manageservers] 6 172.16.1.180:22 7 8 [proxyservers] 9 172.16.1.18[1:2]:22 10 11 # Mode 2: Alias + Host + port + Password 12 [webservers] 13 web01 ansible_ssh_host=172.16.1.183 ansible_ssh_port=22 14 web02 ansible_ssh_host=172.16.1.184 ansible_ssh_port=22 15 web03 ansible_ssh_host=172.16.1.185 ansible_ssh_port=22
Overview of Ansible Vault
When we write playbook, sensitive information is involved, such as: database account password; MQ account password; host account password.In order to prevent these sensitive information from being leaked, vault can be used for encryption.
1 [yun@ansi-manager ~]$ ansible-vault -h 2 Usage: ansible-vault [create|decrypt|edit|encrypt|encrypt_string|rekey|view] [options] [vaultfile.yml] 3 4 Options: 5 --ask-vault-pass ask for vault password 6 -h, --help show this help message and exit 7 --new-vault-id=NEW_VAULT_ID 8 the new vault identity to use for rekey 9 --new-vault-password-file=NEW_VAULT_PASSWORD_FILE 10 new vault password file for rekey 11 --vault-id=VAULT_IDS the vault identity to use 12 --vault-password-file=VAULT_PASSWORD_FILES 13 vault password file 14 -v, --verbose verbose mode (-vvv for more, -vvvv to enable 15 connection debugging) 16 --version show program's version number, config file location, 17 configured module search path, module location, 18 executable location and exit 19 20 See 'ansible-vault <command> --help' for more information on a specific 21 command.
Parameter Description
create: create an encrypted file that requires a Vault password before it can be edited.
decrypt: decrypt vault encrypted files.
edit: edit the vault encrypted file.
encrypt: vault the file provided.
encrypt_string: vault encrypts the supplied string.
rekey: To make a secret-free change to a vault-encrypted file, you need to provide the previous password.
View: To view an encrypted file, you need to provide a password.
Ansible Vault Interactive
Create Encrypted File
1 [yun@ansi-manager object06]$ pwd 2 /app/ansible_info/object06 3 [yun@ansi-manager object06]$ ansible-vault create test_vault.yml 4 New Vault password: # Input password 5 Confirm New Vault password: # Confirm Password 6 --- 7 # vault test 8 - hosts: proxyservers 9 10 tasks: 11 - name: "touch file" 12 file: 13 path: /tmp/with_itemstestfile 14 state: touch 15 16 [yun@ansi-manager object06]$ cat test_vault.yml # View after encrypting 17 $ANSIBLE_VAULT;1.1;AES256 18 33663239636530353564393731363161623462386266613165326235353762343465653235396639 19 6138353833366637383066366662666236666338333237610a303263336234303866623834663361 20 39343633646434353334396162643063613964333337343336373232653266613264626564346566 21 6262633334353036620a633136313364383536323531373164346436663739663631353166663434 22 38663962363032643163333266633662376538383134333862373961313166656536353734363537 23 30626261366138383864653834336637393230363466336662306138323032373361656566663231 24 65363039393736326266316261383065363739633861646464373733643966333233343436303731 25 37366130363064366337393837396664356335363738663130333436656238666233396466393137 26 33306434343262313961393661313536386338383233303230613962663732323630663638313531 27 3236636438646166643937613761396564373033623637636166
Decrypt Encrypted Files
1 [yun@ansi-manager object06]$ ansible-vault decrypt test_vault.yml 2 Vault password: 3 Decryption successful 4 [yun@ansi-manager object06]$ 5 [yun@ansi-manager object06]$ cat test_vault.yml # View after decryption 6 --- 7 # vault test 8 - hosts: proxyservers 9 10 tasks: 11 - name: "touch file" 12 file: 13 path: /tmp/with_itemstestfile 14 state: touch
Encrypt existing files
1 [yun@ansi-manager object06]$ ansible-vault encrypt test_vault.yml 2 New Vault password: 3 Confirm New Vault password: 4 Encryption successful 5 [yun@ansi-manager object06]$ cat test_vault.yml 6 $ANSIBLE_VAULT;1.1;AES256 7 37313964663164613434656666323265376465303433633438613032303733363136316235623066 8 3930343836396537343333336432363732343936323937370a363239356233333634303464633539 9 61613264363037313833363738623866643762666662646165646561343631646434383864373338 10 6334333162616332320a353033323538643566666562646334623630343938646264663561316566 11 35633939653166326631303635363533613338326561666663623238396464383363613738323464 12 37306163663933323836316165666532336664353038303036383564346436633235373166663834 13 62383464373632373839323562306163666366313738663234656139346130373031626265613830 14 38373135616261616137326337633566306633343338306264646139396230613665356264353134 15 37376636646266626236323663376230313964323034623133333539393131333065323964303030 16 3139366661353732333961323764613332316535323334343939
Edit Encrypted Files
1 [yun@ansi-manager object06]$ ansible-vault edit test_vault.yml 2 Vault password: 3 --- 4 # vault test == 5 - hosts: proxyservers 6 7 tasks: 8 - name: "touch file" 9 file: 10 path: /tmp/with_itemstestfile 11 state: touch
Change password for encrypted files
1 [yun@ansi-manager object06]$ ansible-vault rekey test_vault.yml 2 Vault password: 3 New Vault password: 4 Confirm New Vault password: 5 Rekey successful
View Encrypted Files
1 [yun@ansi-manager object06]$ ansible-vault view test_vault.yml 2 Vault password: 3 --- 4 # vault test == 5 - hosts: proxyservers 6 7 tasks: 8 - name: "touch file" 9 file: 10 path: /tmp/with_itemstestfile 11 state: touch
Encrypt the provided string
1 [yun@ansi-manager object06]$ ansible-vault encrypt_string "111 222 333" 2 New Vault password: 3 Confirm New Vault password: 4 !vault | 5 $ANSIBLE_VAULT;1.1;AES256 6 61343332386237363437623939633334626231613539353566313336306562373538633937363566 7 6537336166356466666431663037623835643964366137340a336439313066356265666636383430 8 36613661393232613134333961643936646164396130613663656237393837366566356631353061 9 3034326337303932610a303232643464633239383563393836306565353835666431363132303835 10 3635 11 Encryption successful
Ansible Vault non-interactive
Create a password file
Safe use, remember to use 400 or 600 permissions.
1 [yun@ansi-manager object06]$ echo "111111" > vault_pwd 2 [yun@ansi-manager object06]$ echo "123456" > vault_pwd2 3 [yun@ansi-manager object06]$ ll vault_pwd* # Jurisdiction 400 4 -r-------- 1 yun yun 7 Aug 30 10:35 vault_pwd 5 -r-------- 1 yun yun 7 Aug 30 10:39 vault_pwd2
Create Encrypted File
1 [yun@ansi-manager object06]$ ansible-vault create test_vault02.yml --vault-password-file=vault_pwd 2 --- 3 # vault test 2 4 [yun@ansi-manager object06]$ cat test_vault02.yml 5 $ANSIBLE_VAULT;1.1;AES256 6 34356364613864656136616365383361386635316332363861656334643230366136313333376366 7 6638666536306162366263333037323231386365316238390a383139623435363738663832623533 8 34666539393036383365333062333039643832616233623764613132303966396534616633326366 9 6131313833383761620a383534363564393836306238666135656137623036386531653931623362 10 30613036333161613235393539633233663136653566366266353232386230383434
Decrypt Encrypted Files
1 [yun@ansi-manager object06]$ ansible-vault decrypt test_vault02.yml --vault-password-file=vault_pwd 2 Decryption successful 3 [yun@ansi-manager object06]$ cat test_vault02.yml 4 --- 5 # vault test 2
Encrypt existing files
1 [yun@ansi-manager object06]$ ansible-vault encrypt test_vault02.yml --vault-password-file=vault_pwd 2 Encryption successful 3 [yun@ansi-manager object06]$ 4 [yun@ansi-manager object06]$ cat test_vault02.yml 5 $ANSIBLE_VAULT;1.1;AES256 6 65653035393230366365363637343137636337663638346463303532623139353137366162396536 7 3533393766313339393665386463613831323366623962650a643365653833636663653938613966 8 39323037396635333236663239316431343461346562393731363537313865623534396533653931 9 3638363937626635390a303962653366353138373139623237356637656230386565663364626438 10 31613837383338323065346634323632396339323635323766386236623038616233
Edit Encrypted Files
1 [yun@ansi-manager object06]$ ansible-vault edit test_vault02.yml --vault-password-file=vault_pwd 2 --- 3 # vault test 2 ##
Change password for encrypted files
1 [yun@ansi-manager object06]$ ansible-vault rekey test_vault02.yml --vault-password-file=vault_pwd --new-vault-password-file=vault_pwd2 2 Rekey successful
View Encrypted Files
1 [yun@ansi-manager object06]$ ansible-vault view test_vault02.yml --vault-password-file=vault_pwd2 2 --- 3 # vault test 2 ##
Encrypt the provided string
1 [yun@ansi-manager object06]$ ansible-vault encrypt_string "test info" --vault-password-file=vault_pwd2 2 !vault | 3 $ANSIBLE_VAULT;1.1;AES256 4 30313766613263363963316663623664353862623032323331356563626636646239636666343766 5 6633363733303334373831303732326435396566313066630a373562633530333832613335393835 6 34396161313862656466353433313835643030633966383032656561343331616234373831623233 7 6636396135306436640a313531373835663633383665396139343464613861313034386365393137 8 6133 9 Encryption successful
Playbook uses vault files
1 # Where the vault password of test_vault.yml is the information in vault_pwd 2 [yun@ansi-manager object06]$ ansible-vault view test_vault.yml --vault-password-file=vault_pwd 3 --- 4 # vault test == 5 - hosts: proxyservers 6 7 tasks: 8 - name: "touch file" 9 file: 10 path: /tmp/with_itemstestfile 11 state: touch 12 13 [yun@ansi-manager object06]$ ansible-playbook -b -i ../hosts_key --syntax-check test_vault.yml --vault-password-file=vault_pwd # Grammar Detection 14 [yun@ansi-manager object06]$ ansible-playbook -b -i ../hosts_key -C test_vault.yml --vault-password-file=vault_pwd # Pre-Execution, Test Execution 15 [yun@ansi-manager object06]$ ansible-playbook -b -i ../hosts_key test_vault.yml --vault-password-file=vault_pwd # implement
Complete!
-—END-—
If you feel good, pay attention to the next chop (-^O^-)!
