essential information
Tycoon is a multi platform Java blackmail software for Windows ® and Linux ®, which has been in the field since at least December 2019. It is deployed in the form of Trojan Java runtime environment (JRE) and executed in the form of obscure java image format.
It has been observed that threat actors behind Tycoon use targeted delivery mechanisms to penetrate small and medium-sized companies and institutions in the education and software industries, where they will continue to encrypt file servers and demand ransom. However, since the public RSA private key is reused, it is possible to recover the data without having to pay in an earlier version.
Working with KPMG's UK Cyber Response Services, BlackBerry research and intelligence team recently discovered a new ransomware written in Java. Blackmail software is deployed against targeted attacks of the organization. After the domain controller and file server of the organization are attacked, the system administrator has been locked out of the system. After the forensic investigation of the infected system, it is obvious that the initial intrusion was carried out through the Internet Oriented RDP jump server.
The following figure illustrates how an attacker managed to gain initial access and start infecting the entire site's system:
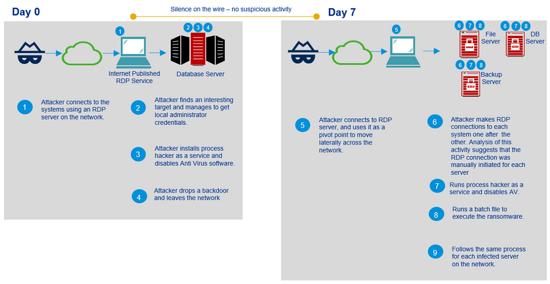
Figure 1: attack schedule
Post event analysis of an Internet facing RDP server cannot be performed because it has been restored. However, our analysis of the victim machine shows that some techniques used by the attacker are abnormal and noteworthy:
·In order to achieve persistence on the victim's machine, the attacker used a technique called "image file execution option" (IFEO) injection [2]. The IFEO settings are stored in the Windows registry. These settings give developers the option to debug the software by debugging the application's attachments during execution of the target application.
·Then, a backdoor operation is performed next to the Microsoft Windows onscreen keyboard (OSK) function of the operating system:
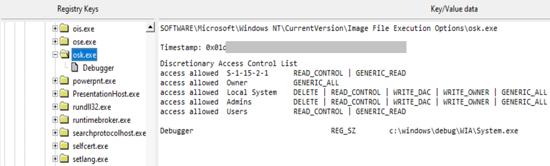
Figure 2: registry key for backdoor execution
·The attacker used the ProcessHacker utility to disable the organization's antimalware solution and change the password of the Active Directory server. This prevents victims from accessing their systems.
·Most attacker files are time stamped, including Java libraries and execution scripts, and the file date time stamp is 15:16:22, April 11, 2020:
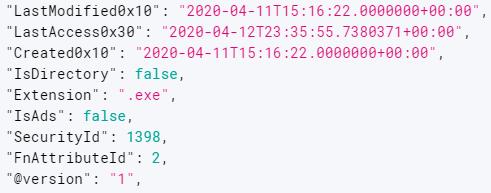
Figure 3: File timestamp
Finally, the attacker executed the Java ransomware module to encrypt all the file servers, including the backup system connected to the network.
Sample analysis
Tycoon ransomware comes in the form of a ZIP archive, which contains the Trojanized Java Runtime Environment (JRE) build. The malware is compiled as a java image file (JIMAGE), which is located in lib \ modules in the build directory.
JIMAGE is a special file format for storing a custom JRE image designed for use by the Java virtual machine (JVM) at run time. It contains the resources and class files for all Java modules that support a specific JRE build. This format was originally introduced in Java version 9 and has few records. Unlike the popular Java archive format (JAR), JIMAGE is mainly internal to the JDK and rarely used by developers:
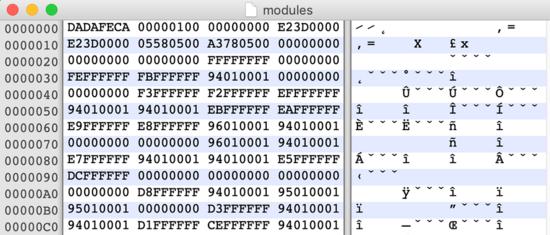
Figure 4: malicious "module" file; JIMAGE format with header beginning with 0xdafeca signature
The OpenJDK9 jimage utility can extract and decompile Java image files:
``` $ ./jimage --help Usage: jimage jimage... ```
After extraction, the ransomware image contains three modules related to a project named "tycoon":
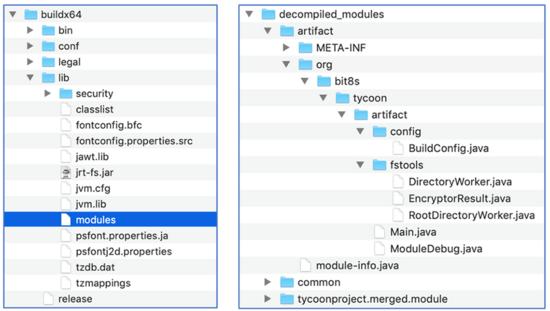
Figure 5: contents of ZIP archive (left) and structure of decompiled Java module JIMAGE (right)
Ransomware is triggered by executing a shell script that uses the java-m command to run the Main function of a malicious Java module.
A malicious JRE build contains both Windows ® and Linux ® versions of this script, which indicates that the threat factor is also for Linux ® servers:
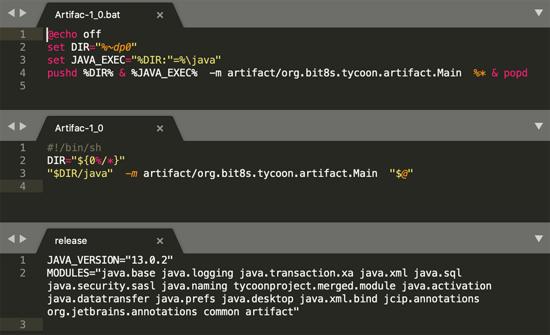
Figure 6: Shell scripts and Java "publish" files for ransomware execution
sample data
The malware configuration is stored in the BuildConfig file of the project and contains the following information:
·Attacker's email address
·RSA public key
·Contents of ransom statement
·Exclusion list
·List of Shell commands to execute
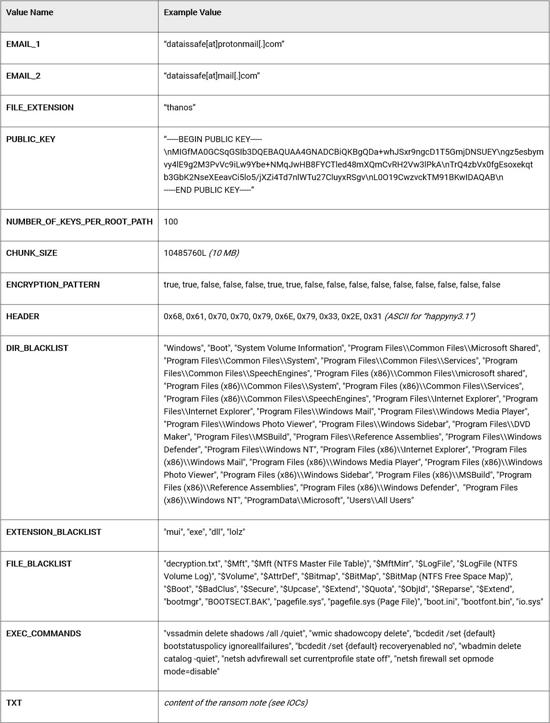
Figure 7: example configuration values
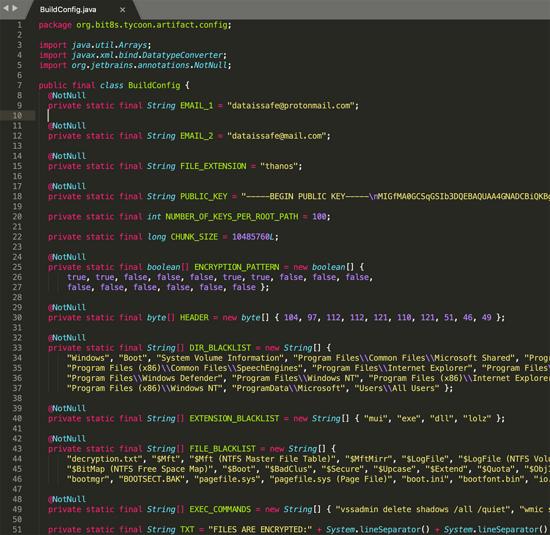
Figure 8: part of the BuildConfig file
aggressive behavior
After execution, the malware runs a set of Shell commands specified in the BuildConfig file:
vssadmin delete shadows /all /quiet
wmic shadowcopy delete
bcdedit /set {default} bootstatuspolicy ignoreallfailures
bcdedit /set {default} recoveryenabled no
wbadmin delete catalog -quiet
netsh advfirewall set currentprofile state off
netsh firewall set opmode mode=disable
The first four bytes of the SHA256 hash value of the system UUID value are used to generate an install for each victim_ ID value. To obtain the UUID, the malware executes the following wmic command:
wmic csproduct get UUID
The encrypted path list can be passed as a parameter; alternatively, the malware will generate a list of all root paths in the system. A separate encryption thread is created for each item in the path list.
After the encryption process is completed, the malware will ensure that the files are not recoverable by overwriting the deleted files in each encryption path. It uses embedded Windows utilities cipher.exe To complete this task:
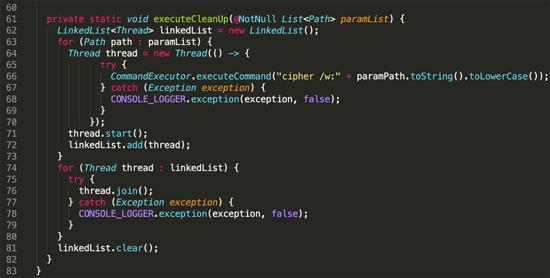
Figure 9: safely delete the original file
File encryption
AES-256 algorithm in [Galois / Counter (GCM) mode 3] is used to encrypt the file with 16 byte GCM authentication label to ensure data integrity. use java.security.SecureRandom Function to generate a 12 byte initialization vector (IV) for each block. The size of the encryption block is specified in BuildConfig and set to 10 MB, while the mode setting specifies the mode in which the file block is to be processed. By skipping a portion of a larger file, an attacker can speed up the encryption process while destroying the file and making it unusable.
For each encrypted path, use the java.security.Secure The. Random function generates an AES-256 key array. The maximum number of keys per path is set in BuildConfig and may vary between samples. Each file (or file block, if the file is larger than the block size) will be encrypted with a different AES key, then encrypted with the attacker's RSA-1024 public key and saved in the block metadata block:
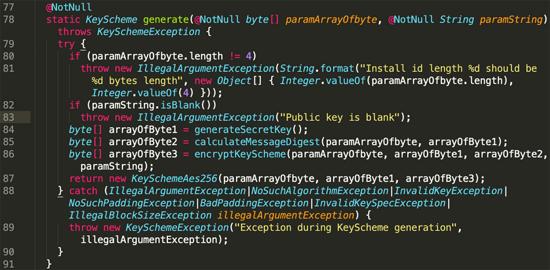
Figure 10: AES key generation
The metadata added to each encryption block contains the following:
·Header value specified in BuildConfig
·Block index (8 bytes)
·Block size (8 bytes)
·AES IV generated per block (12 bytes)
·AES GCM label (16 bytes)
·AES key scheme encrypted by RSA (128 bytes), including: o victim ID (4 bytes) o AES key (32 bytes) o SHA512 hash of victim ID and AES key (64 bytes)
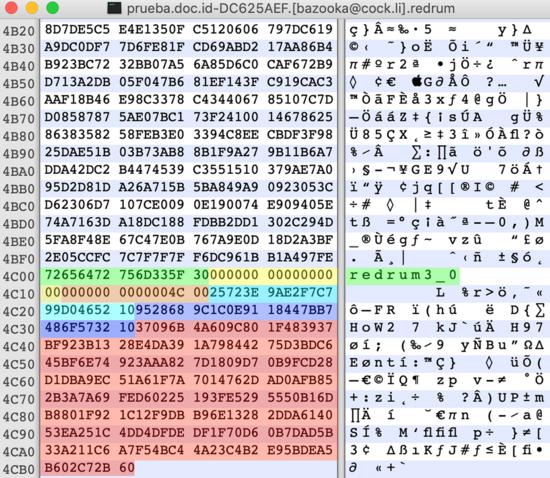
Figure 11: encrypted file with highlighted metadata
Because asymmetric RSA algorithm is used to encrypt the AES key, the private RSA key of the attacker is needed for file decryption. Although theoretically it can decompose the 1024 bit RSA key, it is not yet implemented and requires extraordinary computing power.
However, one of the victims who asked for help on the BleepingComputer forum [4] stored an RSA private key, presumably from the victim who bought it from the attacker. It turns out that this key can successfully decrypt some files affected by the earliest version of Tycoon ransomware, which added the. redrum extension to the encrypted file:
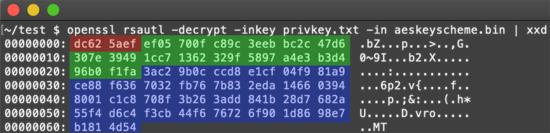
Figure 12: AES key metadata decrypted: install_id (red), AES key (green), sha512 hash (blue)
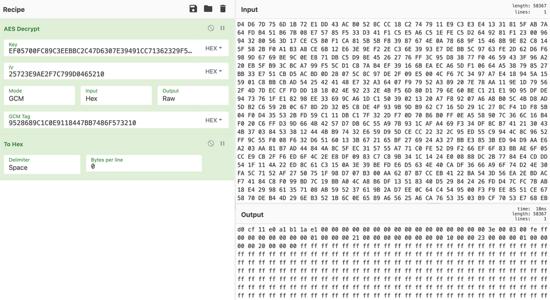
Figure 13: recovery of. redrum file using decrypted AES key
Unfortunately, it doesn't work with the latest "happyny3.1" version, which adds. grinch and. thanos extensions to encrypted files.
0x06 analysis summary
Malware writers have been looking for new ways to spread it. They are gradually getting rid of the traditional confusion technology and turning to the uncommon programming languages and obscure data formats. We've seen a significant increase in ransomware written in languages like Java and Go. This is the first example we encountered that specifically abused the Java JIMAGE format to create a custom malicious JRE build.
Tycoon has been out for at least six months, but the number of victims appears to be limited. This indicates that the malware may be highly targeted. It may also be part of a broader effort to use several different ransomware solutions, depending on the approach considered more successful in a particular environment.
Some overlaps in e-mail addresses, as well as ransomware text and naming conventions for encrypting files, indicate a link between Tycoon and Dharma / CrySIS ransomware.
0x07 IOCs
JIMAGE module (lib \ modules): eddc43ee369594ac8b0a8ab6960dba8d58c0b499a51a717667f05572617fb email address:
· pay4dec[at]cock[.]lu
· dataissafe[at]protonmail[.]com
· dataissafe[at]mail[.]com
· foxbit[at]tutanota[.]com
· moncler[at]tutamail[.]com
· moncler[at]cock[.]li
· relaxmate[at]protonmail[.]com
· crocodelux[at]mail[.]ru
· savecopy[at]cock[.]li
· bazooka[at]cock[.]li
· funtik[at]tutamail[.]com
· proff-mariarti[at]protonmail[.]com
Encryption file extension:
· thanos
· grinch
· redrum
Encrypted file signature:
· happyny3.1
· redrum3_0
RSA public key (happyny3.1 version):
-----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDa+whJSxr9ngcD1T5GmjDNSUEY gz5esbymvy4lE9g2M3PvVc9iLw9Ybe+NMqJwHB8FYCTled48mXQmCvRH2Vw3lPkA TrQ4zbVx0fgEsoxekqtb3GbK2NseXEeavCi5lo5/jXZi4Td7nlWTu27CluyxRSgv L0O19CwzvckTM91BKwIDAQAB -----END PUBLIC KEY-----
RSA private key (redrum3_0 version):
-----BEGIN RSA PRIVATE KEY----- MIICXQIBAAKBgQCyNELzNaPcGBlt2YEARamc+a+uyM8/mRadrMLLQ9tuzkppvdWI iM/LH+xATZUgByknwzaMtRQZi6R2pQ8nBG6DxNtdhla33L+njQLTW+7wo1tSaaJz 6Of0FvCUZNPZ0mF5OrJO+Z6ZfDxafcwv653Ii7aTwaKlhjFoZijBMrA43wIDAQAB AoGAPJ+I0yJBX0OXiwY+W3BXdj5+5LANyS30QqmeDvZDtRtat0RMW0lnn0t53JpI DABDoPJJIW8MqnAWAALA994LFhk9jUtJTUgwsViyKL/Q/dOCeBPJU3xyXNkqhmCN ImP4v7DxjvWp1pomrIIRCW68GkbB+cSGyLAzUo+1KHVh6LECQQDdL26UsVNsNYTX rfv6BZItGO1HJHYTiz0cI82n4woZY2fS2lpBDEvy3Rl8E4Y7F9tQby4odDLHi/9l RCeoif45AkEAzkDsPGauMmWsPXAbXrjzq3/0+MWgh7Vd8Gpgn83QUYjTO2RxtE1n zAYzTLrFFtM8zmCAubpKM1dyi4Xs7hlv1wJBAJD5ofV8NT3b5nKn61z5gdJlYEEd OPeecDOdlBLS0a/KZCbkT/wK300UdrvI4FajUHDsLsj9QLtim8f4YDYsHKECQQCX R40+XD3mnyZvRbv9hQDMyKSglyvAfimxvgSzEZ17QDVWubygd6nrPpz/6XnH3RYb dTLVhysHb1uHtKpslWGvAkAf0kivk9miSFnVeoO1XZumRAwrhTh6Rxhkg6MJCLBP ThoY7wYXmV9zNPo02xYTvZlyhwnWspz4Kx4LsUutWmBs -----END RSA PRIVATE KEY-----
Blackmail information:
Hello! All your documents, photos, databases and other important files have been ENCRYPTED! Do you really interested to restore your files? If so, you must buy decipher software and private key to unlock your data! Write to our email - %s and tell us your unique %s We will send you full instruction how to decrypt all your files. In case of no answer in 24 hours write us on additional e-mail address - %s ======================================================================================================================== FAQ FOR DECRYPTION YOUR FILES: ======================================================================================================================== * WHATS HAPPENED ??? Your files are NOT DAMAGED! Your files have been modified and encrypted with strong cipher algorithm. This modification is reversible. The only way to decrypt your files is to purchase the decipher software and private key. Any attempts to restore your files with the third-party software will be fatal for your files, because would damage data essential for decryption ! Note !!! You have only 24 hours to write us on e-mail or all your files will be lost or the decryption price will be "increased!" ==================================================================================== ==================================== * HOW TO RECOVERY MY FILES ??? You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decipher software and private key that will decrypt all your files. ======================================================================================================================== * FREE DECRYPTION !!! Free decryption as guarantee! If you don't believe in our service and you want to see a proof, you can ask us about test" for decryption. You send us up to 5 modified files. Use file-sharing service and Win-Rar to send files for test. Files have to be less than 1 MB (non archived). Files should not be important! Don't send us databases, backups, large excel files, etc. We will decrypt and send you your decrypted files back as a proof!" ======================================================================================================================== * WHY DO I NEED A TEST??? This is done so that you can make sure that only we can decrypt your files and that there will be no problems with the decryption! ======================================================================================================================== * HOW TO BUY BITCOINS ??? There are two simple ways to by bitcoins: https://exmo.me/en/support#/1_3 https://localbitcoins.net/guides/how-to-buy-bitcoins Read this information carefully because it's enough to purchase even in large amounts ======================================================================================================================== !!! ATTENTION !!! !!! After 60 hours the price for your encryption will increase 10 percent each day !!! Do not rename encrypted files. !!! Do not try to decrypt your data using third party software, it may cause permanent data loss. !!! Decryption of your files with the help of third parties