Users Accounts Authentication
kubeconfig configuration file
As mentioned earlier, communication between K8S is achieved through https, which requires authentication every time, such as when we enter a command from the command line
[root@k8s-master ~]# kubectl get pod
Requires https authentication, and https is stateless link means that certificates are required for every access. If all are specified manually, the actual operation will be very inconvenient. To simplify the connection and ease of use, K8s uses the kubeconfig configuration file to simplify the authentication information attached to the file when using it.
kubeconfig profile: three search paths
1. Specify the highest priority certificate location
2. through the environment variable $ KUBECONFIG Load config File
3. Read the user's home directory $ HOME/.kube/config
kubeconfig configuration file:
Organize user name, authentication information, etc. together to easily authenticate to the authentication information file on API Server. Supports n authentication information for m clusters in one file;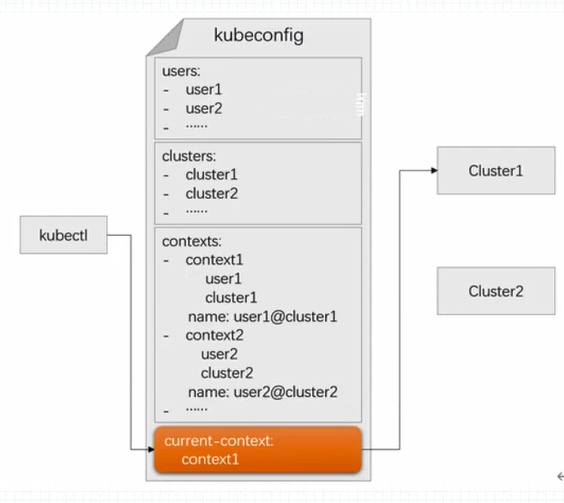
- You can see in the kubectl option that you can specify certificates and secret keys
[root@k8s-master kubernetes]# kubectl options
The following options can be passed to any command:
--add-dir-header=false: If true, adds the file directory to the header of the log messages
--alsologtostderr=false: log to standard error as well as files
--as='': Username to impersonate for the operation
--as-group=[]: Group to impersonate for the operation, this flag can be repeated to specify multiple groups.
--cache-dir='/root/.kube/cache': Default cache directory
--certificate-authority='': Path to a cert file for the certificate authority
--client-certificate='': Path to a client certificate file for TLS #Client Certificate
--client-key='': Path to a client key file for TLS #Refers to the client secret key
--cluster='': The name of the kubeconfig cluster to use
--context='': The name of the kubeconfig context to use
--insecure-skip-tls-verify=false: If true, the server's certificate will not be checked for validity. This will
make your HTTPS connections insecure
...kubeconfig configuration file
- There are roughly four kinds of information; Supports n authentication information for m clusters in one file;
- clusters: Configure the kubernetes cluster to access
- contexts: Configure the specific context for accessing the kubernetes cluster
- current-context: Configure the context currently in use
- users: Configure access to user information, user name, and certificate information
System default config profiles
[root@k8s-master core]# cd /etc/kubernetes/
[root@k8s-master kubernetes]# ll #kubernetes installation completes several config profiles
total 32
-rw------- 1 root root 5565 Jun 29 01:42 admin.conf #Administrator Profile
-rw------- 1 root root 5601 Jun 29 01:42 controller-manager.conf #Manage Controller Profile
-rw------- 1 root root 1933 Jun 29 01:43 kubelet.conf
drwx------ 2 root root 113 Jun 29 01:42 manifests
drwxr-xr-x 3 root root 4096 Jun 29 01:42 pki
-rw------- 1 root root 5541 Jun 29 01:42 scheduler.conf #Scheduler Profile
[root@k8s-master kubernetes]# cat admin.conf
apiVersion: v1
clusters: # Cluster-related information
- cluster: #API service ca certificate
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJeE1EWXlPREUzTkRJeE1Gb1hEVE14TURZeU5qRTNOREl4TUZvd0ZdFVBd2FneGRSd2ozS0V5N0hTQWNiTVhqS0ZTZEFsUTJRcTdDRzh2TFhpbHVySGhFRWJyenEKdW5idVZqSjgwZ0lXZWVvMjNIa0Fiak9pVGlTb2tOMkFvR3lHVzllUzNiTUxTSmdNSHpMdFg4MHVXd1M3NWpjMwoybU1yWWU1OW56R0lSMnlZMnp4a21tajZET0xvTVFLeUpscVBDMmZHS3lBdjBONzlRS0FHbDdKamJYell2YVYyCmVnV3RDazBGSG5mYWg5RnUrL1A4cE50WThhZ1NsdW5lZUhrTAotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://192.168.4.170:6443
name: kubernetes #Cluster name
contexts: #Clusters are associated with user names through the upper and lower files, so in a configuration file, there is no one-to-one correspondence, and a user can manage multiple clusters
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes #Setting up clusters and users
kind: Config
preferences: {}
users:
- name: kubernetes-admin #User-related information
user: #User token key
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURFekNDQWZ1Z0F3SUJBZ0lJTzB3MXV1SWhEbDR3RFFZSktvWklodmNOQVFFTEJRQXdGVEVUTUJFR0ExVUUKQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TVRBMk1qZ3hOelF5TVRCYUZ3MHlNakEyTWpneE56UXnp2V3RsRStRdUc2Ulk0bjB3UEc0OFR1N0JobGgxVTQKYTNVb3p4SHV4MmRBdi9JNHdBMmRrem8xc0FIL1pFUUFFTjNBN0JZL28rWWE1MXErNmNYMjYvN3hkVlhvMjVKTwpzRkdqUjVJbTIvcDYwR2R4N1MraGlDSE9MZzc1ZFBlZVQvOTZRMk15cVFiaHAyYmlERnNtMnRCSjBhWXdhQThyCm9rMHJYcTd4NmZ1M2l1R2NmaWt0azhRWjA5b29WM29Kd21ORVlSY3A5RTd4TjIxM042dFlOcHVtK0dxVWNiVTIKSHB5MmF4YjZhRWNOVk90YTVJdWluZUtmR1NaZ1hmND0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb2dJQkFBS0NBUUVBeVVSd3hnVmwvNmczRkpiYnh3Y2EwUi9kejdua0lpbGVFcWl1Tm1yTVE3UlhaSnR3Ckh1bEhnTlQvREtENUMxOTg0cGtQZXV5RzZJc3V6VHFtL0REVERMdndBNXArMWNFNksvWDI5LzV3U29TMUtJN2c3dXc2NEZnSHRBazB3aVloYkhQUGVOMVAKa0Y5RDVFUTdySkZ0S3ZDU2ZPKzdueDhYUEVFM01CTWdBNlR0cXdJREFRQUJBb0lCQUdldHVlcElIYUwxSkdxVwp5K0JhNkpXUnROR3RFTGdJVjAyRlZ6anhDd2hWZmk5MVl1eUpmeXYrak9RVWlEWXpta0dnVnprYlh1T3J6eEFwCmhwpdQpOMFFEaE9iZlE3c1BQV08wSWpzeVo0anVKbDlxYTVsS2N6TTNJTWU3aFdYcXpTUXMwblNKRW9QS04zQUh2UllhCkJNdFZBb0dBRnNkUyswcHBIVnllWlVoblRJZXhiOEhSa0ViT2I2Z3lXenM3bThzcllXK2dwU3RJTVBpR3NTNFoKL0xYZ0RvZ2xUQ01VTnJ1Zjd3RjVtRWcrVTFEZGEyTmtSeWZPRmlnZGQybDVyZkRTN1BxMDhIOGdrZmtNWXFYdQppYUg5cnR3QmRCOEF3bktzTjlKaWFTRkV4RXlxOCtRM3ZIaXpGenhkV1IxU0VQZzQ2V0E9Ci0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==Three different ways to specify kubeconfig files
- Mode 1 specifies the profile
[root@k8s-master ~]# kubectl --kubeconfig=/etc/kubernetes/admin.conf get pod #Specify config path This file is also the cluster initialization prompt that we copy to the home directory home file NAME READY STATUS RESTARTS AGE centos-deployment-66d8cd5f8b-9x47c 1/1 Running 1 44h demodb-0 1/1 Running 0 21h demodb-1 1/1 Running 0 19h
- Mode 2 is specified by an environment variable
[root@k8s-master ~]# export KUBECONFIG=/etc/kubernetes/admin.conf #Through environment variables [root@k8s-master ~]# echo $KUBECONFIG /etc/kubernetes/admin.conf
- Mode 3 Copy to Home Directory
- Cluster initialization prompts us to copy to the home directory home file
To start using your cluster, you need to run the following as a regular user:
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/config
You should now deploy a pod network to the cluster.
Run "kubectl apply -f [podnetwork].yaml" with one of the options listed at:
https://kubernetes.io/docs/concepts/cluster-administration/addons/
Then you can join any number of worker nodes by running the following on each as root:
kubeadm join 192.168.4.170:6443 --token abcdef.0123456789abcdef \
--discovery-token-ca-cert-hash sha256:d31662998938389c1f9e432a0c7bcef7d05678b42c2f5fd67213ed228f356db2Common commands for viewing kubeconfig files
[root@k8s-master ~]# kubectl config -h
Modify kubeconfig files using subcommands like "kubectl config set current-context my-context"
The loading order follows these rules:
1. If the --kubeconfig flag is set, then only that file is loaded. The flag may only be set once
and no merging takes place.
2. If $KUBECONFIG environment variable is set, then it is used as a list of paths (normal path
delimiting rules for your system). These paths are merged. When a value is modified, it is modified
in the file that defines the stanza. When a value is created, it is created in the first file that
exists. If no files in the chain exist, then it creates the last file in the list.
3. Otherwise, ${HOME}/.kube/config is used and no merging takes place.
Available Commands:
current-context Displays the current-context
delete-cluster Delete the specified cluster from the kubeconfig
delete-context Delete the specified context from the kubeconfig
get-clusters Display clusters defined in the kubeconfig
get-contexts Describe one or many contexts
rename-context Renames a context from the kubeconfig file.
set Sets an individual value in a kubeconfig file
set-cluster Sets a cluster entry in kubeconfig
set-context Sets a context entry in kubeconfig
set-credentials Sets a user entry in kubeconfig
unset Unsets an individual value in a kubeconfig file
use-context Sets the current-context in a kubeconfig file
view Display merged kubeconfig settings or a specified kubeconfig file- Display default config information
[root@k8s-master ~]# kubectl config view
apiVersion: v1
clusters:
- cluster:
server: ""
name: /etc/kubernetes/admin.conf
- cluster:
server: ""
name: etc/kubernetes/admin.conf
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.4.170:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED- View the context information for the specified config file
[root@k8s-master ~]# kubectl config get-contexts --kubeconfig=/etc/kubernetes/scheduler.conf CURRENT NAME CLUSTER AUTHINFO NAMESPACE * system:kube-scheduler@kubernetes kubernetes system:kube-scheduler
Example 1: Create a kubeconfig profile for the authentication account using openssl
- Create Private Key
X509 certification using openssl tool supports two-way certification and visa removal via k8s own CA - You can see that there is only one ca.crt in the K8S component directory, because all components are signed by api-server's ca. If you want our own key to be authenticated by api-server, you need to issue a certificate through this ca
[root@k8s-master pki]# ls apiserver.crt apiserver.key ca.crt front-proxy-ca.crt front-proxy-client.key apiserver-etcd-client.crt apiserver-kubelet-client.crt ca.key front-proxy-ca.key sa.key apiserver-etcd-client.key apiserver-kubelet-client.key etcd front-proxy-client.crt sa.pub
- Create Private Key
[root@k8s-master kubernetes]# mkdir usercerts [root@k8s-master kubernetes]# cd usercerts/ [root@k8s-master usercerts]# (umask 077; openssl genrsa -out tom.key 2048) Generating RSA private key, 2048 bit long modulus ...............................................................+++ .......................+++ e is 65537 (0x10001) [root@k8s-master usercerts]# ls tom.key
- Next, creating a certificate to create a self-visa based on this private key is not possible. You need to create a certificate signing request that is signed through k8s'ca
- openssl Common Options
-days time
-CA Specifies CA to use
-CAkey Specifies the private key
-CAcreateserial CA creates its own serial number
-in Files to Sign
-out output
[root@k8s-master usercerts]# openssl x509 -req -days 3655 -CA /etc/kubernetes/pki/ca.crt -CAkey /etc/kubernetes/pki/ca.key -CAcreateserial -in tom.csr -out tom.crt
Signature ok
subject=/CN=tom/O=kubeusers
Getting CA Private Key
[root@k8s-master usercerts]# openssl x509 -in tom.crt -text -noout #View Certificate Details
Certificate:
Data:
Version: 1 (0x0)
Serial Number:
bc:c3:53:df:96:10:ec:ed
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=kubernetes
Validity
Not Before: Aug 24 00:35:05 2021 GMT
Not After : Aug 27 00:35:05 2031 GMT
Subject: CN=tom, O=kubeusers
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:c5:c9:3d:ac:3a:b3:9d:38:58:f1:d9:c6:21:c5:
d5:57:d1:a5:5d:0a:92:a1:88:3e:3c:2d:8d:2d:20:
b1:a4:d1:07:03:7e:72:48:dd:d9:7e:4b:b6:fc:35:
46:b9:60:82:c2:36:30:7d:04:8c:83:b5:7c:8a:b1:
20:7d:f4:b3:5c:29:f4:e0:2b:67:96:5d:b8:a6:ba:
4a:0c:7e:4f:6b:34:82:5b:7d:1a:8c:26:ed:91:dd:
62:9f:37:68:70:14:a4:cf:ea:b0:51:b3:56:9e:d6:
1d:64:32:66:8c:c1:9e:40:4b:20:1c:0a:8b:2c:c8:
94:be:10:95:29:7f:8b:6e:a1:03:32:11:31:de:c6:
d1:8c:64:a8:43:4b:0b:ad:ff:64:e1:17:4d:55:fe:
04:9f:a5:59:2b:e5:13:5e:0d:2b:c1:c7:45:f8:b3:
a7:ad:da:dc:e8:aa:22:5a:37:e6:ce:75:8e:bc:e3:
1e:eb:95:db:be:14:dd:43:1b:51:e6:94:21:10:81:
1c:b5:e3:2d:3e:12:b6:78:14:d4:90:8a:06:32:7e:
ef:90:7b:e7:26:60:38:6c:52:04:bc:91:e1:3f:db:
8b:8a:05:39:ad:74:99:e1:80:ae:58:d6:4a:6d:7d:
64:a3:bc:16:b8:7c:d6:08:33:b8:23:56:35:75:18:
bb:57
Exponent: 65537 (0x10001)
Signature Algorithm: sha256WithRSAEncryption
40:fe:1b:d7:c1:67:bf:15:21:be:ac:0e:fb:32:a3:1e:58:e5:
c8:2a:3f:3a:21:87:23:9c:14:dc:05:39:fb:5f:f8:1e:f3:66:
98:54:48:1c:25:c1:b5:bc:1c:be:7d:d6:86:7d:09:ae:7c:40:
2d:cd:0b:5d:29:7f:67:ec:51:1b:c3:97:d3:a2:17:d4:96:04:
17:ba:aa:79:ff:0e:d0:53:2c:81:a3:8e:05:0b:a5:f5:12:0c:
f8:38:f1:fb:6e:bf:7b:1b:40:f0:dc:b1:5e:b1:a8:c8:fc:ec:
92:c5:fb:6b:76:ff:7c:ab:f5:ea:94:89:8a:fd:47:cf:c8:8a:
b6:f3:42:19:b9:b2:74:41:de:bf:66:7e:b3:e2:78:8e:e1:db:
ac:85:2b:ed:8d:c1:55:16:0f:15:8c:72:7b:0d:7e:31:ce:06:
ce:2e:d3:9f:77:60:22:4e:11:32:33:b6:28:d5:93:2f:c9:a5:
4c:f6:1f:4f:7d:e7:66:e0:74:14:c4:c8:de:c1:26:1e:56:db:
29:54:35:b9:3b:24:8b:5f:f5:81:af:30:27:f4:1f:99:a5:aa:
8d:f3:91:c4:4f:3e:3d:12:a9:a5:85:44:0b:17:19:2a:ac:ea:
50:3f:39:31:c5:ef:15:04:f7:bf:11:a3:57:af:8f:ce:8d:d1:
d7:5e:c4:31
- Generate kubeconfig configuration file Configuration cluster information stored in / tmp/mykubeconfig directory
[root@k8s-master core]# kubectl config set-cluster kubernetes --server=https://k8s-master:6443 --embed-certs --certificate-authority=/etc/kubernetes/pki/ca.crt --kubeconfig=/tmp/mykubeconfig
Cluster "kubernetes" set.
[root@k8s-master ~]# cat /tmp/mykubeconfig
apiVersion: v1
clusters:
- cluster: #Cluster authentication information
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJeE1EWXlPREUzTkRJeE1Gb1hEVE14TURZeU5qRTNOREl4TUZvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTXdRCm1DSkowR3VJRGR6WmE4WEFKSXk3QlJVR0JUMG9JMGxWdVdjM1BEMjV3aHIxTUJSeVVydTB1MG43bUtWUVR6YlkKMEc4VVNIendTblg1MU9vTXBVNVl3SEs2V0dMZ0o2Z2RDZmpBWTZ2MTJlN3krcnZqT0tZbnM2bGpVZjJNbmFJTApuckN5MS91NTZMbmgxd0NIMVhrTEVDUDUzOU1GYW1Za1JHeGVTOUZabEZjZ0x2SnA0M1ZYOVY0SVdRZXVtSGQ5CjFhYktWZWkvNDFxYmJ2eURVN2w0bDdrbFVtTFVUR0RsWXBmMUdQVS9KYW9tNFFMUmFFdDJjc1ljTlo4SjN5YVkKR3ZPbG9HTTE1MFJzeDR2TDhEV09xWmNVVWcvdVh1aktnMU1mV1JyRDlLdnFLMVFkUDkySUUrbDZuWFVLWTM0cgp2b0RDbU9jTDhKMG5QeWpieWYwQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZPd2kyd3JVYnV2Vm1iaVYycm5uTHR6MGhzZ2NNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFCQ0ZrRVU0Z3lvdURzNGhHMHBqZGxySlJrRHcxa0tnMUpWOG0zQ3FjS1VLbUpCVVQ5SAo5UjhMYVUycy82eVM1elgzVlNkVU5nRjFWL2hwalVKNmJTdWQ5WGZubWJ3OGxIS1V1Y1VTSVdVOWErVEdUdmtuCkRxSThGY0M4Z0tzdFVBd2FneGRSd2ozS0V5N0hTQWNiTVhqS0ZTZEFsUTJRcTdDRzh2TFhpbHVySGhFRWJyenEKdW5idVZqSjgwZ0lXZWVvMjNIa0Fiak9pVGlTb2tOMkFvR3lHVzllUzNiTUxTSmdNSHpMdFg4MHVXd1M3NWpjMwoybU1yWWU1OW56R0lSMnlZMnp4a21tajZET0xvTVFLeUpscVBDMmZHS3lBdjBONzlRS0FHbDdKamJYell2YVYyCmVnV3RDazBGSG5mYWg5RnUrL1A4cE50WThhZ1NsdW5lZUhrTAotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://k8s-master:6443
name: kubernetes
contexts: null
current-context: "" #Upper and lower file information is empty
kind: Config
preferences: {}
users: null #User is empty- Configure cluster user tom
[root@k8s-master ~]# kubectl config set-credentials --help #Users can authenticate in a variety of ways
...
Usage:
kubectl config set-credentials NAME [--client-certificate=path/to/certfile] [--client-key=path/to/keyfile]
[--token=bearer_token] [--username=basic_user] [--password=basic_password] [--auth-provider=provider_name]
[--auth-provider-arg=key=value] [--exec-command=exec_command] [--exec-api-version=exec_api_version] [--exec-arg=arg]
[--exec-env=key=value] [options]
[root@k8s-master usercerts]# kubectl config set-credentials tom --client-certificate=./tom.crt --client-key=./tom.key --embed-certs=true --kubeconfig=/tmp/mykubeconfig
User "tom" set.
[root@k8s-master usercerts]# kubectl config view --kubeconfig=/tmp/mykubeconfig
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://k8s-master:6443
name: kubernetes
contexts: null
current-context: ""
kind: Config
preferences: {}
users:
- name: tom #Add user tom
user:
client-certificate-data: REDACTED #Information Hiding--The Role of embed-certs=true
client-key-data: REDACTED #Hide Information- Add context to bind cluster to user
[root@k8s-master usercerts]# kubectl config set-context "tom@kubernetes" --user=tom --cluster=kubernetes --kubeconfig=/tmp/mykubeconfig
Context "tom@kubernetes" created.
[root@k8s-master usercerts]# kubectl config view --kubeconfig=/tmp/mykubeconfig
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://k8s-master:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: tom
name: tom@kubernetes #Users and clusters bind by
current-context: ""
kind: Config
preferences: {}
users:
- name: tom
user:
client-certificate-data: REDACTED
client-key-data: REDACTED- Toggle context toggle authenticated user is tom
[root@k8s-master usercerts]# kubectl config use-context tom@kubernetes --kubeconfig=/tmp/mykubeconfig
Switched to context "tom@kubernetes"
[root@k8s-master usercerts]# kubectl config view --kubeconfig=/tmp/mykubeconfig
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://k8s-master:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: tom
name: tom@kubernetes
current-context: tom@kubernetes #Current User
kind: Config
preferences: {}
users:
- name: tom
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
[root@k8s-master usercerts]# kubectl get nodes --kubeconfig=/tmp/mykubeconfig
Error from server (Forbidden): nodes is forbidden: User "tom" cannot list resource "nodes" in API group "" at the cluster scope
- The above error refers to a problem with authorization,Authentication has passed,Sample requirements have been completed,Authorization will be covered in the next sectionExample 2: kubeconfig Certificate Merge tom.crt Certificate Completed in Example 1
- Clusters don't need to already have a default profile created
[root@k8s-master usercerts]# kubectl config set-credentials tom --client-certificate=./tom.crt --client-key=./tom.key --embed-certs=true User "tom" set.
- Create contexts in default kubeconfig
[root@k8s-master usercerts]# kubectl config set-context "tom@kubernetes" --user=tom --cluster=kubernetes
Context "tom@kubernetes" created.
[root@k8s-master usercerts]# kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.4.170:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes #Default context
- context:
cluster: kubernetes
user: tom
name: tom@kubernetes #New context
current-context: kubernetes-admin@kubernetes #Current context
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: tom #New user
user:
client-certificate-data: REDACTED
client-key-data: REDACTED- Switch the current context to tom@kubernetes
[root@k8s-master usercerts]# kubectl config use-context tom@kubernetes Switched to context "tom@kubernetes". [root@k8s-master usercerts]# kubectl get pod #Prompt does not have permission Error from server (Forbidden): pods is forbidden: User "tom" cannot list resource "pods" in API group "" in the namespace "default"
- Specify Pre-use context
[root@k8s-master usercerts]# kubectl get nodes --context=kubernetes-admin@kubernetes NAME STATUS ROLES AGE VERSION k8s-master Ready master 56d v1.19.9 k8s-node1 Ready <none> 56d v1.19.9 k8s-node2 Ready <none> 56d v1.19.9 k8s-node3 Ready <none> 19d v1.19.9 [root@k8s-master usercerts]# kubectl config use-context kubernetes-admin@kubernetes #Modify Default context Switched to context "kubernetes-admin@kubernetes". [root@k8s-master usercerts]# kubectl get node NAME STATUS ROLES AGE VERSION k8s-master Ready master 56d v1.19.9 k8s-node1 Ready <none> 56d v1.19.9 k8s-node2 Ready <none> 56d v1.19.9 k8s-node3 Ready <none> 19d v1.19.9
- Delete context
[root@k8s-master usercerts]# kubectl config delete-context tom@kubernetes
[root@k8s-master usercerts]# kubectl config delete-user tom
[root@k8s-master usercerts]# kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.4.170:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- Merge profiles by merging environment variables Merge profiles
[root@k8s-master usercerts]# export KUBECONFIG=$HOME/.kube/config:/tmp/mykubeconfig
[root@k8s-master usercerts]# kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.4.170:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
- context:
cluster: kubernetes
user: tom
name: tom@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: tom
user:
client-certificate-data: REDACTED
client-key-data: REDACTED- Using the --merge--flatten option, you can flatten merged duplicates and generate new profiles based on merging profiles with environment variables
[root@k8s-master usercerts]# kubectl config view --merge --flatten > /tmp/newkubeconfig
[root@k8s-master usercerts]# kubectl config view --kubeconfig=/tmp/newkubeconfig
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.4.170:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
- context:
cluster: kubernetes
user: tom
name: tom@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: tom
user:
client-certificate-data: REDACTED
client-key-data: REDACTED