MISC
Really sign in


DASCTF{welc0m3_t0_9C51s_2021}
YUSA's little secret
Open the adjustment channel with Stegsolve to find the hidden flag; But it can't be seen when disturbed
Search engines look up data and find problems. This refers to a color coding model called YCrCb

Refer to [ByteCTF2020]Hardcore Watermark 01: https://bytectf.feishu.cn/docs/doccnqzpGCWH1hkDf5ljGdjOJYg
from cv2 import *
img = cv2.imread('yusa.png')
cv_color = cv2.cvtColor(img, cv2.COLOR_BGR2YCrCb)
cv2.imwrite('flag.png', cv_color)
The picture will be obtained. Use Stegsolve to open the adjustment channel again

DASCTF{2947b683036d49e5681f83f7bc3fbb34}
Yusa's Secret

volatility -f Yusa-PC.raw --profile=Win7SP1x64 psxview

Analyze suspicious processes
- wab.exe: it is a program of Windows operating system, which is used to store address book, contact and Email address. To support programs like Outlook.
- StikyNot.exe: Windows note program
First of all, let's take a look at five colored eggs (although it's useless)
egg1


egg2


egg3

cmdscan found egg4
>>> from base64 import *from base64 import *
>>> b64decode('eXVzYeWnkOWnkOacieWlveWkmuWlveWkmueahOWwj+Woh+Wmu++8jOa4o+eUtw==').decode('utf-8')
'yusa My sister has a lot of little wives, scum men'
egg5
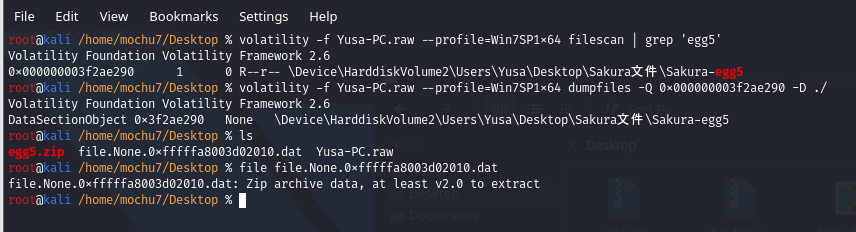
egg5.zip has a password. The password is in the screenshot


th1s_1s_3gg5_k3y

After reading the eggs, I began to work on the questions
volatility -f Yusa-PC.raw --profile=Win7SP1x64 filescan | grep -E '.zip$|.rar$|.7z$'

key.zip requires a password; Continue analysis
Called StikyNot.exe, trying to find snt file


Export the file and use win7's notes to load the file
PS: after testing, Win10 can also be loaded in this way
Location: C: \ users \ XXX \ appdata \ roaming \ Microsoft \ sticky notes \ sticky notes.snt
PS: this Sticky Notes folder may not be found. You can open a temporary note and find it

Then use the StickyNotes.snt we exported to replace the StickyNotes.snt temporarily generated here; Then open the note again to find the clue
key.zip password: the world has no heartbeat
Get exp.py
from PIL import Image
import struct
pic = Image.open('key.bmp')
fp = open('flag', 'rb')
fs = open('Who_am_I', 'wb')
a, b = pic.size
list1 = []
for y in range(b):
for x in range(a):
pixel = pic.getpixel((x, y))
list1.extend([pixel[1], pixel[0], pixel[2], pixel[2], pixel[1], pixel[0]])
data = fp.read()
for i in range(0, len(data)):
fs.write(struct.pack('B', data[i] ^ list1[i % a*b*6]))
fp.close()
fs.close()
What you need is the flag file, who_ am_ 1. Zip has a password; whoami here should refer to Yusa;

Try to crack the password of Yusa account and use Passware Kit 13



Get the password: YusaYusa520
Decompress to get Who_am_I
Who_ am_ If I have the key.bmp file, I can get the flag file




Get Sakura-didi.zip, but still have a password; Continue to analyze. Another clue that hasn't been used is wab.exe
The contact file suffix is. Contact


Yusa.contact, decode these base64 using the online station: https://the-x.cn/zh-cn/base64/

Get a BMP file, but this is not the key.bmp we want

MysteryMan.contact

base32->base64
This is what you will use key,You can use it to open the tools the organization gives you. Tool naming follows traditional rules. key: 820ac92b9f58142bbbc27ca295f1cf48
Use this key to unzip Sakura-didi.zip

In fact, the decryption script can refer to exp.py above, the key.bmp remains unchanged, and the flag is output, Who_am_I can be used as output. Change the position
from PIL import Image
import struct
pic = Image.open('key.bmp')
fp = open('Who_am_I', 'rb')
fs = open('flag', 'wb')
a, b = pic.size
list1 = []
for y in range(b):
for x in range(a):
pixel = pic.getpixel((x, y))
list1.extend([pixel[1], pixel[0], pixel[2], pixel[2], pixel[1], pixel[0]])
data = fp.read()
for i in range(0, len(data)):
fs.write(struct.pack('B', data[i] ^ list1[i % a*b*6]))
fp.close()
fs.close()
The resulting flag is a gif file. Use stegsolve to view each frame. You can barely see the flag in frame 10

DASCTF{c3837c61-77f1-413e-b2e6-3ccbc96df9f4}
WEB
Haomei's web
Directory scan
python3 dirsearch.py -u "http://b1c34857-a729-4b00-a22a-98323505597c.haomeidehelloworld-ctf.dasctf.com:2333/" -i 200 | grep -v "0B"
The path /. idea/dataSources.xml was found many times during the scanning process, and the scanned full path access is 404
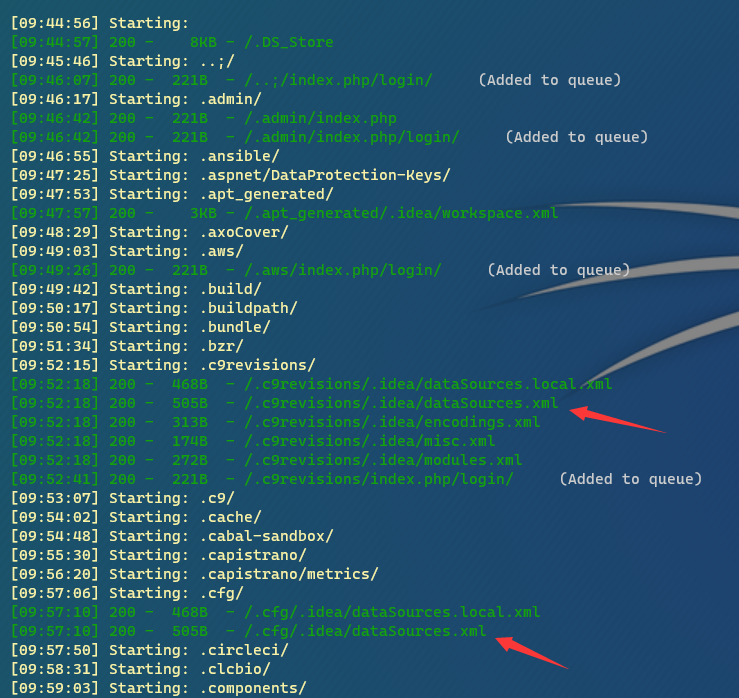

Try to access /. idea/dataSources.xml directly
