Why didn't my stack overflow???
I've been learning binary and garbage hydrology recently. Just smile
"Principles and practice of network security technology" Chapter 6 buffer overflow attack - textbook experiment
Case code
Let's read the code on the book first
#include<stdio.h>
#include<string.h>
#include<windows.h>
#define TEMP_BUFF_LEN 8
int bof(const char* buf) {
char temp[TEMP_BUFF_LEN];
strcpy(temp, buf);
return 0;
}
int main() {
char buff[] = "1234567";
MessageBox(NULL, "SampleBOF Test", "SampleBOF", MB_OK);
bof(buff);
printf("SampleBOF End\n");
return 0;
}
Take a look at the logic
MessageBox is a pop-up dialog box. SampleBOF Test is the content and SampleBOF is the title; Inside the bof function, assign buf to temp. Because the length is enough, the program runs normally
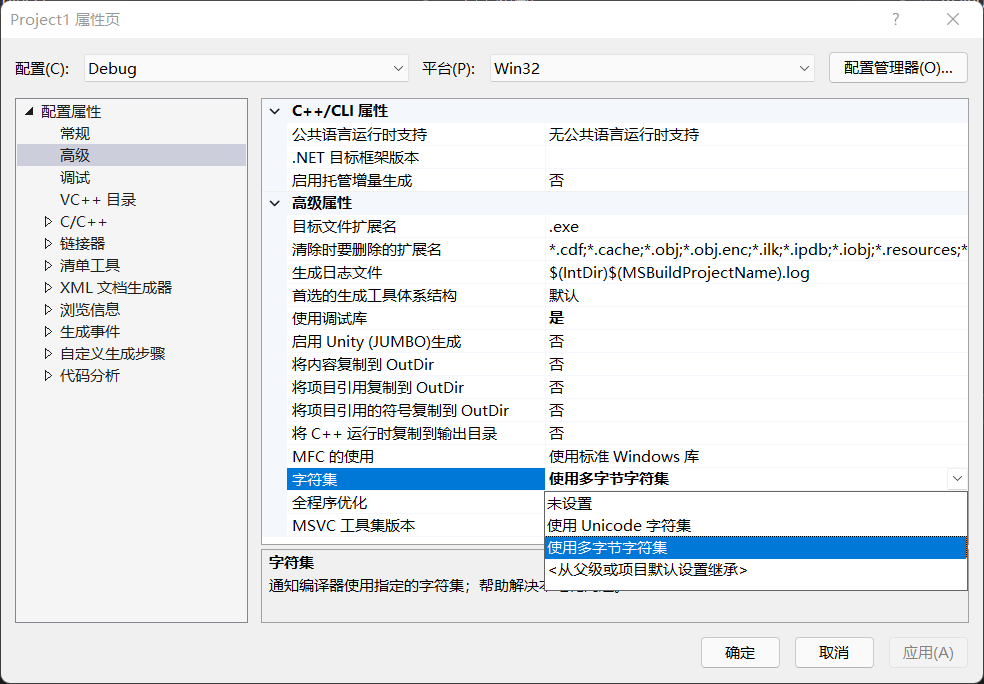
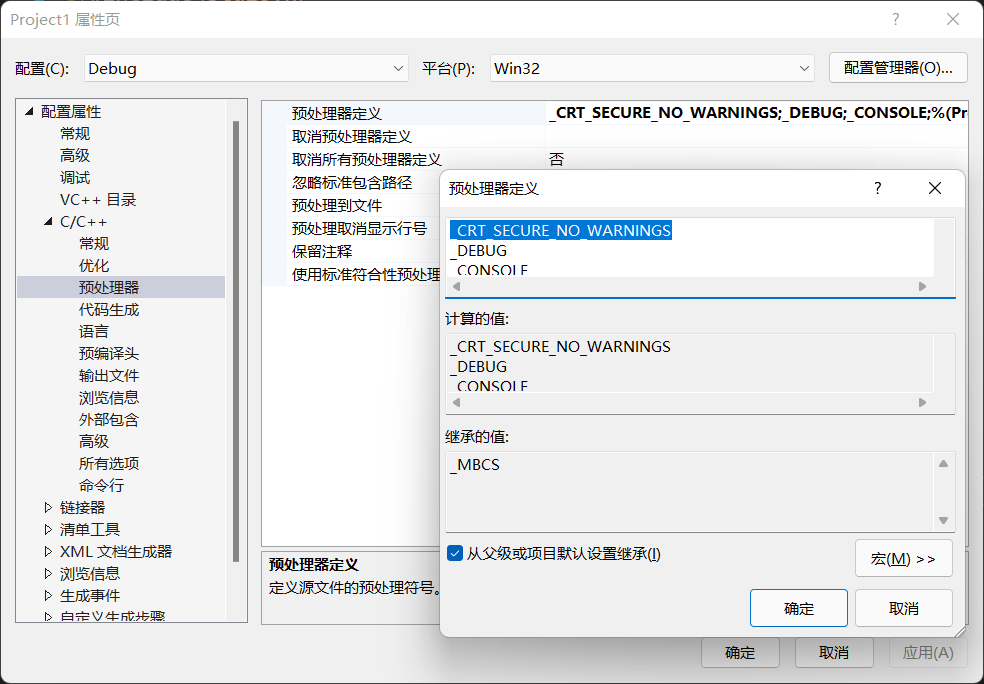
If you compile with VS2019, you should change two configurations, one is character set encoding, and the other is strcpy security option, as follows
_CRT_SECURE_NO_WARNINGS
OD debugging
Note: the addresses compiled by different machines may be different, and the information compiled by different compilers is also different. It does not need to be exactly the same as the test example
Open the compiled binary in OD
Because of the debugging information, we can see the function symbol, just like compiling with gcc and adding the - g parameter
$ gcc -g test.c -o test
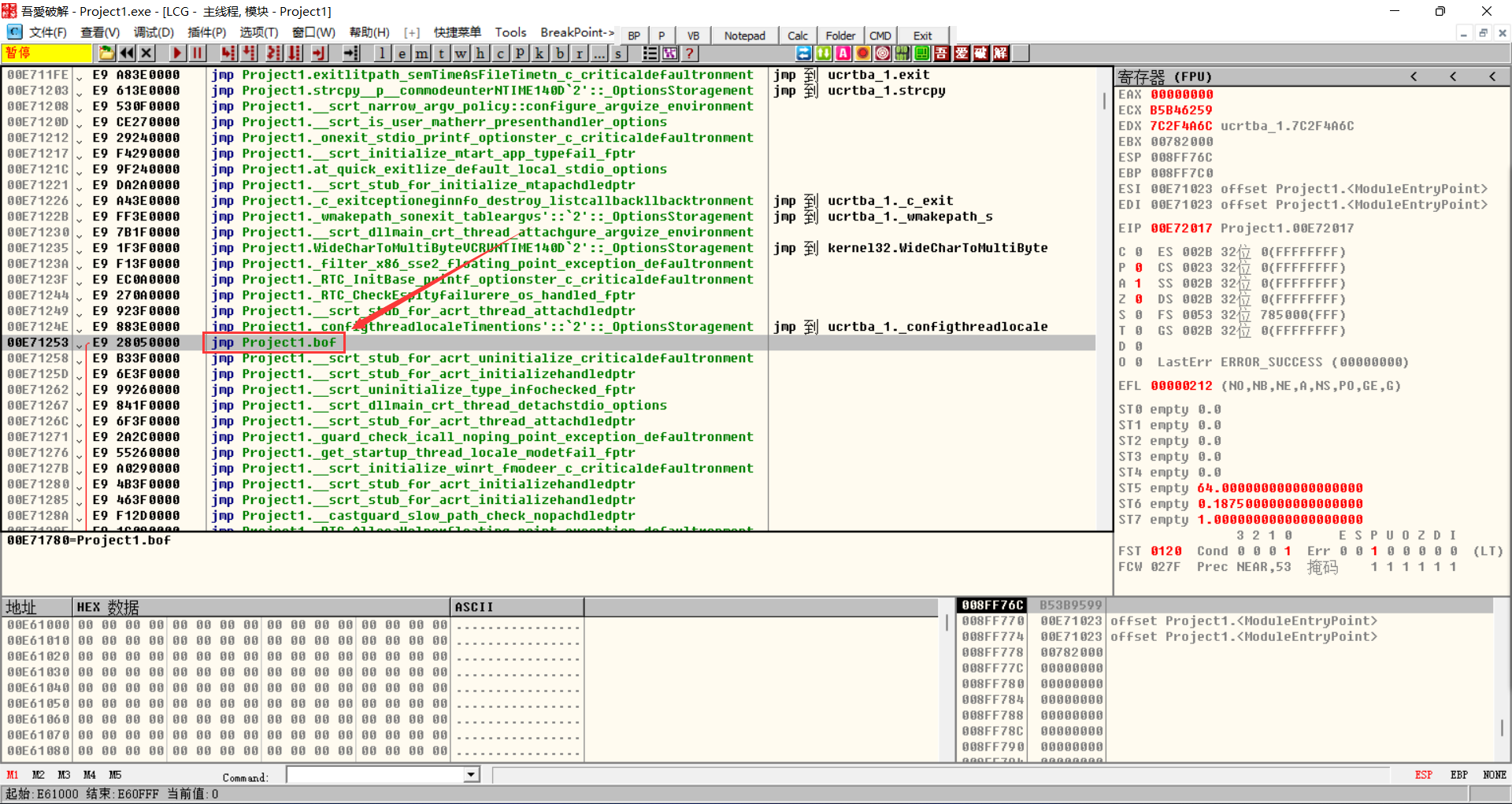
Take a simple look, find the address of each function and play with dynamic adjustment
You can quickly find the main function by searching the string
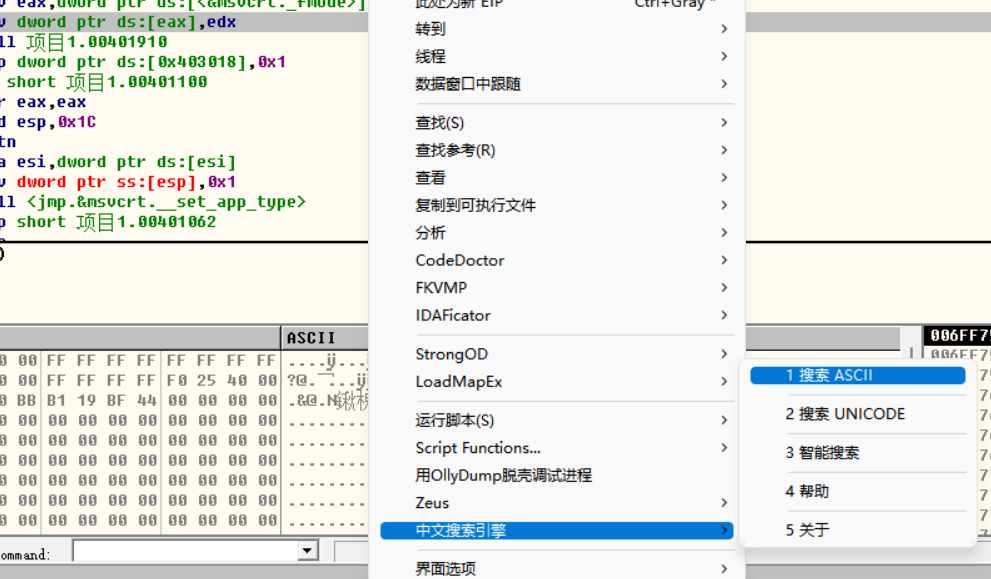
Directly click the string used to jump to the reference position and find the corresponding function
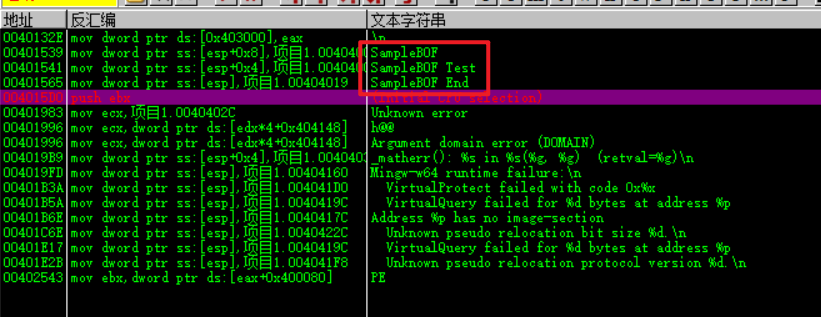
Buffer overflow utilization
Recompile file
#include<stdio.h>
#include<string.h>
#include<windows.h>
#define TEMP_BUFF_LEN 8
int bof(const char* buf) {
char temp[TEMP_BUFF_LEN];
strcpy(temp, buf);
return 0;
}
int sbofa() {
MessageBox(NULL,
"Congratulations!You have the basic principles of buffers overflow.",
"SampleBOF",
MB_OK);
return 0;
}
int main() {
MessageBox(NULL, "SampleBOF Test", "SampleBOF", MB_OK);
char buff[] = "1234567";
bof(buff);
printf("SampleBOF End\n");
return 0;
}
The meaning of stack overflow in the book should mean that the sbofa function is not used. If you want to overflow to the return address of the function through strcpy, and fill the return address with the address of sbofa, the final effect is that there will be two pop-up windows
Open it again in OD and find the address of sbofa, which is 0x00D710A0
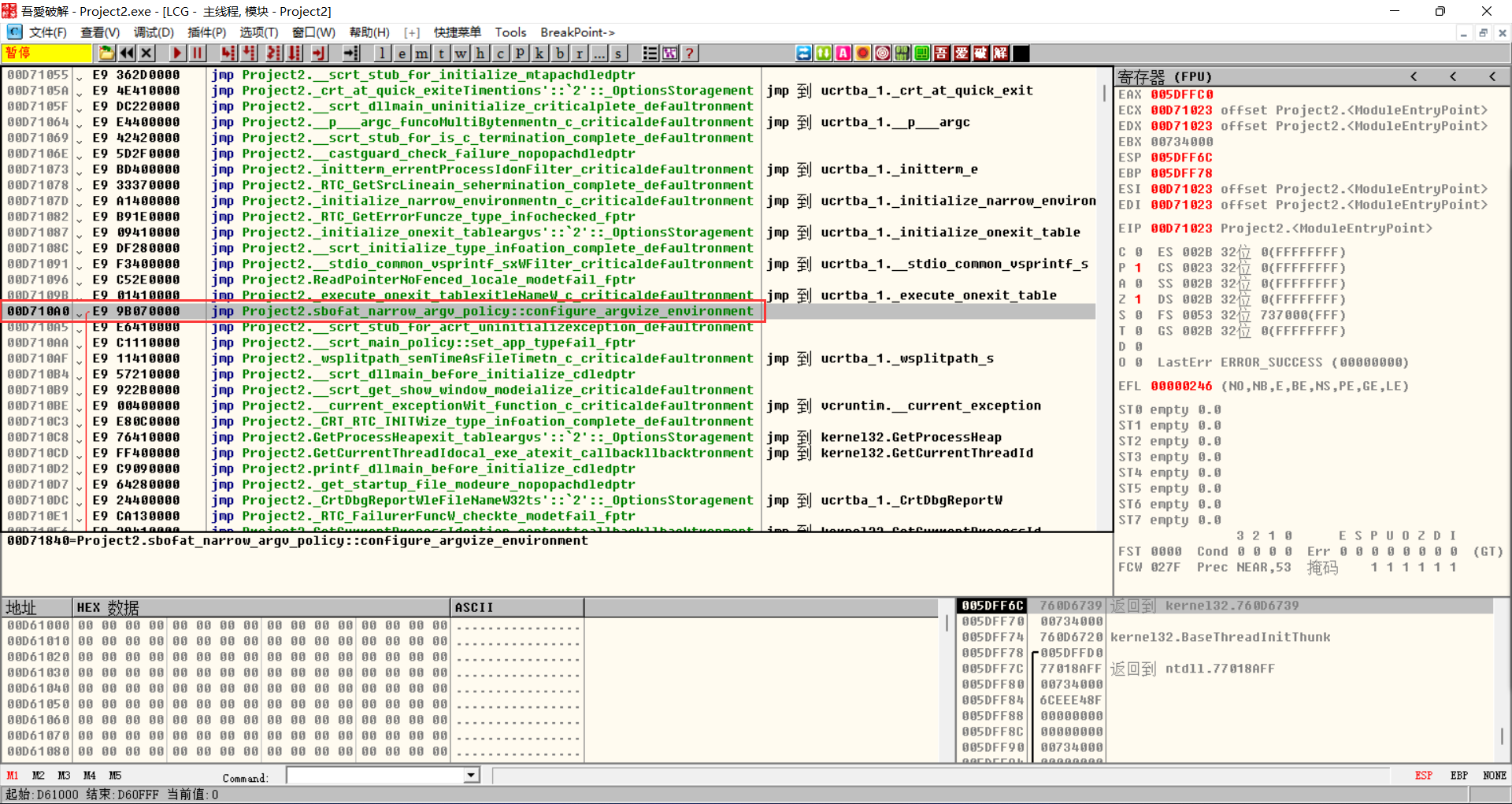
Then change the code above to
#include<stdio.h>
#include<string.h>
#include<windows.h>
#define TEMP_BUFF_LEN 8
int bof(const char* buf) {
char temp[TEMP_BUFF_LEN];
strcpy(temp, buf);
return 0;
}
int sbofa() {
MessageBox(NULL,
"Congratulations!You have the basic principles of buffers overflow.",
"SampleBOF",
MB_OK);
return 0;
}
int main() {
MessageBox(NULL, "SampleBOF Test", "SampleBOF", MB_OK);
char buff[] = "123456781234\xD7\x10\xA0"; // Small terminal sequence
bof(buff);
printf("SampleBOF End\n");
return 0;
}
However, there is obviously a problem with running directly like this. Even if ASLR is closed, the address of sbofa has changed and is no longer 0xD710A0 because the code has been changed and recompiled
In addition, by default, when stack overflow occurs, the system will detect it. At that time, it will be interrupted and pinched, and the effect can not be seen directly
So one idea is to turn off these protections and see this article on the snow
https://bbs.pediy.com/thread-259665.htm
Close these protections (mainly detect stack overflow and ASLR), and then repeat the above steps to get the results
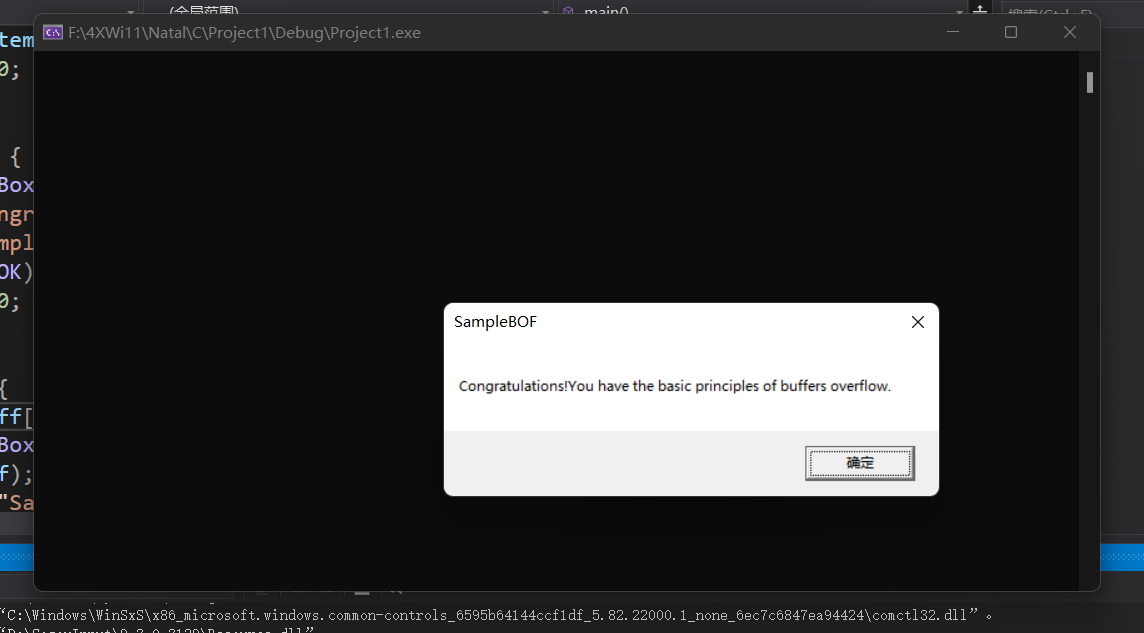
After class exercises
It is mainly about how to make the program exit normally. Obviously, we changed the retn address of bof, and the program was led to an unexpected place. In the retn of sbofa function, the return address in the main function is not recorded, and the program will not end normally
However, according to the stack overflow principle, we only need to overflow again. One idea is to overflow to the address of the exit function, and the program can exit "normally"
We continue debugging in OD and find the function that makes the whole program exit
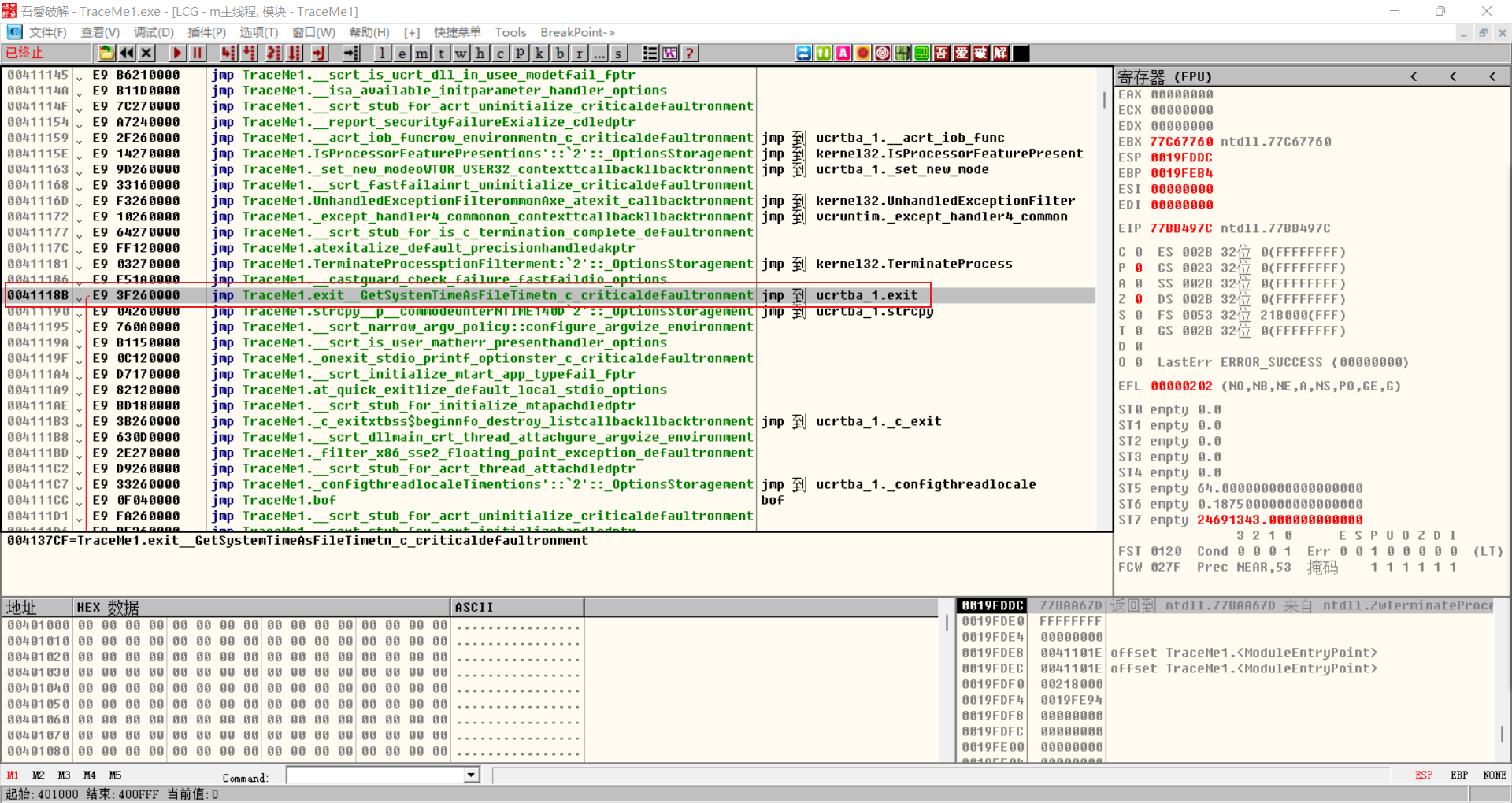
Modify the sbofa function as follows
int sbofa() {
char temp[TEMP_BUFF_LEN];
char buffer[] = "123456781234\x8B\x11\x41";
MessageBox(NULL,
"Congratulations!You have the basic principles of buffers overflow.",
"SampleBOF",
MB_OK);
strcpy(temp, buffer);
return 0;
}
Analysis and summary
Simple stack overflow, small experiment under windows
emmmmm so the calculation changes the source code. After recompiling, the address of the function remains unchanged?