Users, groups, and permissions
Content overview
- Security model of Linux
- User and group related files
- User and group management commands
- Understand and set file permissions
- Default permissions
- special competencies
- File access control permissions
1. Linux Security Model
Resource allocation:
- Authentication: authentication to verify the user's identity
- Authorization: authorization. Different users set different permissions
- Accounting|audit: audit
When the user logs in successfully, the system will automatically assign a token, including user ID, group member and other information
1.1 users
In Linux, each user is uniquely identified by User Id (UID)
- Administrator: root, 0
- Ordinary users: 1-60000 automatic allocation
- System users: 1-499 (before Centos 6), 1-999 (after Centos 7)
Allocate permissions to the resources obtained by the daemon - Login user: 500 + (before Centos 6), 1000 + (after Centos 7)
Interactive login for users
- System users: 1-499 (before Centos 6), 1-999 (after Centos 7)
1.2 user groups
In Linux, one or more users can be added to a user group, which is uniquely identified by Group ID (GID).
- Administrator group: root, 0
- General group:
- System group: 1-499 (before Centos 6) and 1-999 (after Centos 7) to allocate permissions for the resources obtained by the daemon
- Common group: 500 + (before Centos 6) and 1000 + (after Centos 7) for users
1.3 relationship between users and groups
- User and primary group: a user must belong to one and only one primary group. By default, a group with the same name as the user name will be automatically created when creating a user as the user's primary group. Because there is only one user in this group, it is also called a private group
- supplementary group: a user can belong to zero or more auxiliary groups and affiliated groups
example:
[root@CentOS-8 ~]# id postfix uid=89(postfix) gid=89(postfix) groups=89(postfix),12(mail)
1.4 security context
Linux security Context: a running program, that is, a process, runs as the initiator of the process. The permissions of the process to access resources depend on the identity of the operator of the process
For example, if you run / bin/cat /etc/shadow as root and du respectively, the results are different. Whether resources can be accessed is determined by the identity of the operator, not the program itself
example:
[du@CentOS-8 ~]$ cat /etc/shadow cat: /etc/shadow: Permission denied [root@CentOS-8 ~]# cat /etc/shadow root:$6$w094OhpSTIlvjEmg$IZd0Lf9REhlU5Ns.6dIRTrH32IuQsWQ8y9fVSaSeljDmae14bJe9Iv.Z0fxB/zxO77kVoER7LrsG.GhKbUrcO1::0:99999:7::: bin:*:18397:0:99999:7::: daemon:*:18397:0:99999:7::: adm:*:18397:0:99999:7::: lp:*:18397:0:99999:7:::
2. User and group profiles
2.1 main profiles of users and groups
- /etc/passwd: user and its attribute information (name, UID, primary group ID, etc.)
- /etc/shadow: user password and related attributes
- /etc/group: group and its attribute information
- /etc/gshadow: group password and its related attributes
2.2 passwd file format
[root@CentOS-8 ~]#cat /etc/passwd root:x:0:0:root:/root:/bin/bash bin:x:1:1:bin:/bin:/sbin/nologin du:x:1000:1000:dws,it,100001,111111:/home/du:/bin/bash
Login name: login name (du)
passwd: password (x)
UID: user ID number (1000)
GID: default login group number (1000)
GECOS: full user name or comment
Home directory: user home directory (/ home/du)
Shell: the user uses shell (/ bin/bash) by default
[root@CentOS-8 ~]#whatis passwd passwd (5) - password file openssl-passwd (1ssl) - compute password hashes passwd (1) - update user's authentication tokens #If not, sir [root@CentOS-8 ~]#mandb Purging old database entries in /usr/share/man/overrides... .... 72 man subdirectories contained newer manual pages. 621 manual pages were added. 0 stray cats were added. 19 old database entries were purged.
2.3 shadow file format
[09:22:53 root@CentOS-8 ~]#cat /etc/shadow root:$6$w094OhpSTIlvjEmg$IZd0Lf9REhlU5Ns.6dIRTrH32IuQsWQ8y9fVSaSeljDmae14bJe9Iv.Z0fxB/zxO77kVoER7LrsG.GhKbUrcO1::0:99999:7::: du:$6$5dz/5J8EJJW3KIqp$yh8YygMyLd0M7/SfAwUdUzsvzVH0Ukmg5G4pUde2vOVlesQs7MAL1/H8CadNqC68x5RTS9t8ICh0jgPD12AGC.:18760:0:99999:7:::
Login name
User password: generally encrypted with sha512
From January 1, 1970 to the time when the password was last modified
The password can be changed in a few days (0 means it can be changed at any time)
The password must be changed in a few days (99999 means it will never expire)
The system will remind the user a few days before the password expires (one week by default)
The account will be locked after a few days
From January 1, 1970, how many days after the account expires
Change password encryption algorithm:
authconfig --passalgo=sha256 --update
Password security policy
- Long enough
- Use at least 3 of numbers, uppercase letters, lowercase letters and special characters
- Use random password
- Change the password regularly and do not use the password that has been used recently
Example: generate random password
[root@CentOS-8 ~]# tr -dc '[:alnum:]' < /dev/urandom | head -c 12 AIhICqw8W9hf [root@CentOS-8 ~]# openssl rand -base64 9 Jw2KYsBBEnDy
Generate random password: https://suijimimashengcheng.bmcx.com/
2.4 group file format
[root@CentOS-8 ~]#cat /etc/group root:x:0: bin:x:1: daemon:x:2: sys:x:3:
Group name: the group name
Group password: it is usually unnecessary to set. The password is recorded in / etc/gshadow
GID: is the ID of the group
List of users with current group as additional group (comma separator)
2.5 gshadow file format
Group name: the name of the group
Group password:
Group administrator list: list of group administrators, changing group passwords and members
List of users with current group as additional group: multiple users are separated by commas
2.6 document operation
- vipw and vigr
- pwck and grpck
3 user and group management commands
User management commands
- useradd
- usermod
- userdel
Group account maintenance command
- groupadd
- groupmod
- groupdel
3.1 user creation
The useradd command creates a new Linux user
Format:
useradd [options] LOGIN
Common options:
-u UID -o coordination-u Option, do not check UID Uniqueness of -g GID Indicates the basic group to which the user belongs. It can be a group name or a group name GID -c "COMMENT" User's comment information -d HOME_DIR Take the specified path (which does not exist) as the home directory -s SHELL Indicates the user's default shell Program, available list in/etc/shells In the file -G GROUP1[,GROUP2,...] Indicates an additional group for the user, which must exist in advance -N Do not create a private group as the master group, use users Group as master group -r Create system user Centos 6 Before; ID<500,Centos 7 in the future: ID<1000 -m Create home directory for system users -M Do not create home directories for non system users -p Specifies the encrypted password
example:
#-The r option does not create a home directory, does not create a mailbox, and specifies an ID number with an ID of less than 1000 useradd -r -u 48 -g apache -s /sbin/nologin -d /var/www -c "Apache" apache [root@centos8 ~]#groupadd -r -g 80 nginx; useradd -r -g nginx -u 80 -d /var/www -s /sbin/nologin -c "nginx service" nginx [root@centos8 ~]#getent passwd nginx nginx:x:80:80:nginx service:/var/www:/sbin/nologin [root@centos8 ~]#ll /var/spool/mail/ total 0 -rw-rw----. 1 rpc mail 0 Oct 25 22:47 rpc -rw-rw----. 1 user mail 0 Oct 25 23:34 user
The default setting of the useradd command is defined by / etc/default/useradd
[root@CentOS-8 ~]# cat /etc/default/useradd # useradd defaults file GROUP=100 HOME=/home INACTIVE=-1 #Corresponding to column 7 of the / etc/shadow file, that is, the grace period for the expiration of the user password EXPIRE= #Corresponding to column 8 of the / etc/shadow file, that is, the validity period of the user account SHELL=/bin/bash SKEL=/etc/skel CREATE_MAIL_SPOOL=yes
Displays or changes the default settings
useradd -D useradd -D -s SHELL useradd -D -b BASE_DIR useradd -D -g GROUP
New user related files
- /etc/default/useradd
- /etc/skel/*
- /etc/login.defs
Batch create user
newusers passwd Format file
Batch modify user password
echo username:passwd | chpasswd
Example: CentOS 6 creates and specifies user passwords based on sha512
[root@centos6 ~]#grub-crypt --help Usage: grub-crypt [OPTION]... Encrypt a password. -h, --help Print this message and exit -v, --version Print the version information and exit --md5 Use MD5 to encrypt the password --sha-256 Use SHA-256 to encrypt the password --sha-512 Use SHA-512 to encrypt the password (default) Report bugs to <bug-grub@gnu.org>. EOF [root@centos6 ~]#grub-crypt --sha-512 Password: Retype password: $6$v9A2/xUNwAWwEmHN$q7Wz.uscsV/8J5Gss3KslX8hKXOoaP3hDpOBWeBfMQHVIRZiwHUUkii84cvQ WIMnvtnXYsdVHuLO4KhOiSOMh/ [root@centos6 ~]#useradd -p '$6$v9A2/xUNwAWwEmHN$q7Wz.uscsV/8J5Gss3KslX8hKXOoaP3hDpOBWeBfMQHVIRZiwHUUkii84cv QWIMnvtnXYsdVHuLO4KhOiSOMh/' test [root@centos6 ~]#getent shadow test test:$6$v9A2/xUNwAWwEmHN$q7Wz.uscsV/8J5Gss3KslX8hKXOoaP3hDpOBWeBfMQHVIRZiwHUUkii 84cvQWIMnvtnXYsdVHuLO4KhOiSOMh/:18459:0:99999:7:::
Example: CentOS7 uses Python program to generate sha512 encrypted password
[root@centos7 ~]#python -c 'import crypt,getpass;pw="magedu";print(crypt.crypt(pw))' $6$pt0SFMf6YqKea3mh$.7Hkslg17uI.Wu7BcMJStVVtkzrwktXrOC8DxcMFC4JO1igrqR7VAi87H5PH OuLTUEjl7eJqKUhMT1e9ixojn1
Example: CentOS8 generates sha512 encryption password
[root@centos8 ~]#openssl passwd -6 magedu $6$UOyYOao.iM2.rPnM$jCpTnBVIQBuGCLOm4N5hqh5YUc3wWXcDzkDMddthpKNL3scOZjTHh9fXds8E u6gNdEQqLMQgOboipZ08mnz2V.
Example: any system can run
[root@centos8 ~]#cat /dev/urandom |tr -dc '[:alnum:]'|head -c12 32lFOVFPf2E4[root@centos8 ~]#
3.2 user attribute modification
The usermod command can modify user properties
Format:
usermod [option] login
Common options:
-u UID: new UID -g GID: New master group -G GROUP1[,GROUP2,...[,GROUPN]]: New additional group, the original additional group will be overwritten; If the original is retained, it should be used at the same time-a option -s SHELL: New default SHELL -c 'COMMENT': New comment information -d HOME: The new home directory will not be created automatically: UN Build a new home directory and move the original home data while using-m option -l login_name: New name -L: lock Specify user, in/etc/shadow Increase of password bar! -u: unlock Specify the user, and/etc/shadow Password bar! Take it off -e YYYY-MM-DD: Indicates the expiration date of the user account -f INACTIVE: Set an inactive period, i.e. a grace period
3.3 delete user
userdel to delete a Linux user
Format:
userdel [option]...login
Common options:
-f, --force force -r, --remove Delete user home directory and mailbox
Example: force deletion of users and data
[root@centos8 ~]#useradd test [root@centos8 ~]#id test uid=1001(test) gid=1001(test) groups=1001(test) #Log in with test at another terminal [root@centos8 ~]#su - test [test@centos8 ~]$ #Failed to delete the logged in user [root@centos8 ~]#userdel -r test userdel: user test is currently used by process 29909 [root@centos8 ~]#id test uid=1001(test) gid=1001(test) groups=1001(test) #Force delete user [root@centos8 ~]#userdel -rf test userdel: user test is currently used by process 29909 [root@centos8 ~]#id test id: 'test': no such user
3.4 view user related ID information
The id command can view the user's UID, GID and other information
id [option]...[user]
Common options:
-u: display UID -g: display GID -G: Displays the name of the group to which the user belongs ID -n: Display name, to be matched ugG use
3.5 switching users or executing commands as other users
su: that is, switch user. The command can switch the user identity and execute the command as the specified user
Format:
su [options...] [-] [user [args...]]
Common options:
-l --login su -l username amount to su - username -c --command <command> pass a single command to the shell with -c
How to switch users:
- su UserName: non login switching, which neither reads the configuration file of the target user, nor changes the current working directory, nor completely switches
- su - UserName: login switching, which reads the configuration file of the target user and switches to its own home directory, that is, complete switching
Note: no password is required for root su to other users; A password is required for non root users to switch
Note: after su switches a new user, use exit to return to the old user instead of Su to switch to the old user. Otherwise, many bash sub processes will be generated and the environment may be chaotic.
Execute the command as a different identity:
su [-] username -c 'COMMAND'
example:
[root@CentOS-8 ~]# getent passwd du du:x:1000:1000:du:/home/du:/bin/bash [root@CentOS-8 ~]# usermod -s /bin/false du [root@CentOS-8 ~]# getent passwd du du:x:1000:1000:du:/home/du:/bin/false [root@CentOS-8 ~]# su - du [root@CentOS-8 ~]# whoami root
example:
[root@CentOS-8 ~]# su -s /sbin/nologin du This account is currently not available. [root@CentOS-8 ~]# whoami root [root@CentOS-8 ~]# su -s /sbin/false du su: failed to execute /sbin/false: No such file or directory [root@CentOS-8 ~]# whoami root
example:
[du@CentOS-8 ~]$ su - root -c "getent shadow" Password: root:$6$w094OhpSTIlvjEmg$IZd0Lf9REhlU5Ns.6dIRTrH32IuQsWQ8y9fVSaSeljDmae14bJe9Iv.Z0fxB/zxO77kVoER7LrsG.GhKbUrcO1::0:99999:7::: bin:*:18397:0:99999:7::: ...
example:
[root@CentOS-8 ~]# su - du -c 'touch du.txt' [root@CentOS-8 ~]# ll ~du total 0 -rw-rw-r--. 1 du du 0 May 17 16:00 du.txt
example:
[root@CentOS-8 ~]# su bin This account is currently not available. [root@CentOS-8 ~]# su -s /bin/bash bin bash-4.4$ whoami bin bash-4.4$ [root@CentOS-8 ~]# getent passwd tss tss:x:59:59:Account used by the trousers package to sandbox the tcsd daemon:/dev/null:/sbin/nologin [root@CentOS-8 ~]# su - -s /bin/bash tss su: warning: cannot change directory to /dev/null: Not a directory -bash: /dev/null/.bash_profile: Not a directory [tss@CentOS-8 root]$ pwd /root [tss@CentOS-8 root]$ whoami tss
3.6 setting password

passwd can change the user password
Format:
passwd [options] username echo "PASSWORD" | passwd --stdin USERNAME
Common options:
-d: Delete specified user password -l: Lock user -u: Unlock specified user -e: Force the user to change the password at the next login -f: Force operation -n mindays: Specify minimum service life -x maxdays: Maximum service life -w warndays: How many days in advance -i inactivedays: Inactive period --stdin: Receive user password from standard input, Ubuntu No such option
Example: non interactive user password modification
#This method is more general and applicable to various Linux versions, such as ubuntu [root@centos8 ~]#echo -e '123456\n123456' | passwd du Changing password for user du. New password: BAD PASSWORD: The password is shorter than 8 characters Retype new password: passwd: all authentication tokens updated successfully. #Linux version for red hat series [root@centos8 ~]#echo '123456' | passwd --stdin du Changing password for user du. passwd: all authentication tokens updated successfully.
Example: non interactive user password modification for Ubuntu
[root@ubuntu1804 ~]#echo dws:centos |chpasswd [root@ubuntu1804 ~]#passwd dws <<EOF > centos > centos > EOF Enter new UNIX password: Retype new UNIX password: passwd: password updated successfully [root@ubuntu1804 ~]#echo -e 'magedu\nmagedu' | passwd dws Enter new UNIX password: Retype new UNIX password: passwd: password updated successfully
Example: set the password that the user must change next time
[root@CentOS-8 ~]# useradd wang [root@CentOS-8 ~]# echo 123456 | passwd --stdin wang Changing password for user wang. passwd: all authentication tokens updated successfully. [root@CentOS-8 ~]# getent shadow wang wang:$6$pXOeyTc1AnSFPOnS$kC/oYg/gFViNH1xExLlkMp/GDMSzauImaRN9pbjcW6Dko5Q7jQKf3qepCuzuKu6w8Pi9JHlvl8lexNE.FZYWx/:18764:0:99999:7::: [root@CentOS-8 ~]# passwd -e wang Expiring password for user wang. passwd: Success [root@CentOS-8 ~]# getent shadow wang wang:$6$pXOeyTc1AnSFPOnS$kC/oYg/gFViNH1xExLlkMp/GDMSzauImaRN9pbjcW6Dko5Q7jQKf3qepCuzuKu6w8Pi9JHlvl8lexNE.FZYWx/:0:0:99999:7::: [root@CentOS-8 ~]# su - du [du@CentOS-8 ~]$ su - wang Password: You are required to change your password immediately (administrator enforced) Current password: New password: BAD PASSWORD: The password is the same as the old one su: Authentication token manipulation error [du@CentOS-8 ~]$ su - wang Password: You are required to change your password immediately (administrator enforced) Current password: New password: Retype new password: [wang@CentOS-8 ~]$ exit logout [du@CentOS-8 ~]$ exit logout [root@CentOS-8 ~]# getent shadow wang wang:$6$Z2HuqxwIgicE0a/V$sybtF8iiy.wTPkbUw/tL6T76AA5i5g1KL7WnYcBWDjze/WNX2oubdCaWtX1My2kZA2poFAM.j9TnhmzvPZnlZ1:18764:0:99999:7:::
3.7 modify user password policy
chage can modify the user password policy
Format:
chage [options]...login
Common options:
-d LAST_DAY #Time to change password -m --mindays MIN_DAYS -M --maxdays MAX_DAYS -w --warndays WARN_DAYS -I --inactive INACTIVE #Grace period after password expiration -E --expiredate EXPIRE_DATE #Validity period of the user -l Show password policy
example:
[root@centos8 ~]#chage du Changing the aging information for du Enter the new value, or press ENTER for the default Minimum Password Age [0]: 3 Maximum Password Age [99999]: 42 Last Password Change (YYYY-MM-DD) [2021-11-07]: 2022-01-01 Password Expiration Warning [7]: 10 Password Inactive [-1]: 20 Account Expiration Date (YYYY-MM-DD) [-1]: 2023-01-01 [root@centos8 ~]#getent shadow du du:$6$3dADcS3WSnr19Lgd$Rt7/7LZtfJJP1/nGtuC2Mk5ZaoRRWUYZypG5V8fn.CNo7x8VGB/Tk3sRbg758jQWY18Yh//zNkrsYDk.taQcy1:18993:3:42:10:20:19358: [root@CentOS-8 ~]# chage -m 3 -M 42 -W 14 -I 7 -E 2021-10-10 wang [root@CentOS-8 ~]# chage -l wang Last password change : May 17, 2021 Password expires : Jun 28, 2021 Password inactive : Jul 05, 2021 Account expires : Oct 10, 2021 Minimum number of days between password change : 3 Maximum number of days between password change : 42 Number of days of warning before password expires : 14 [root@CentOS-8 ~]# getent shadow wang wang:$6$Z2HuqxwIgicE0a/V$sybtF8iiy.wTPkbUw/tL6T76AA5i5g1KL7WnYcBWDjze/WNX2oubdCaWtX1My2kZA2poFAM.j9TnhmzvPZnlZ1:18764:3:42:14:7:18910: #Force password reset for next login [root@CentOS-8 ~]# chage -d 0 wang [root@CentOS-8 ~]# getent shadow wang wang:$6$Z2HuqxwIgicE0a/V$sybtF8iiy.wTPkbUw/tL6T76AA5i5g1KL7WnYcBWDjze/WNX2oubdCaWtX1My2kZA2poFAM.j9TnhmzvPZnlZ1:0:3:42:14:7:18910: [root@CentOS-8 ~]# chage -l wang Last password change : password must be changed Password expires : password must be changed Password inactive : password must be changed Account expires : Oct 10, 2021 Minimum number of days between password change : 3 Maximum number of days between password change : 42 Number of days of warning before password expires : 14 [root@CentOS-8 ~]# getent shadow wang wang:$6$Z2HuqxwIgicE0a/V$sybtF8iiy.wTPkbUw/tL6T76AA5i5g1KL7WnYcBWDjze/WNX2oubdCaWtX1My2kZA2poFAM.j9TnhmzvPZnlZ1:0:3:42:14:7:18910:
3.8 other user related commands
- chfn specify personal information
- chsh specifies the shell, which is equivalent to usermod -s
- finger can view the user's personal information
example:
[root@CentOS-7 ~]# chfn du Changing finger information for du. Name []: duwenshuo Office []: it Office Phone []: 100001 Home Phone []: 10001111 Finger information changed. [root@CentOS-7 ~]# finger du Login: du Name: duwenshuo Directory: /home/du Shell: /bin/bash Office: it, 100001 Home Phone: 10001111 Never logged in. No mail. No Plan. [root@CentOS-7 ~]# getent passwd du du:x:1000:1000:duwenshuo,it,100001,10001111:/home/du:/bin/bash [root@CentOS-7 ~]# chsh -s /bin/base64 du Changing shell for du. chsh: Warning: "/bin/base64" is not listed in /etc/shells. Shell changed. [root@CentOS-7 ~]# getent passwd du du:x:1000:1000:duwenshuo,it,100001,10001111:/home/du:/bin/base64 [root@centos7 ~]#chsh -s /bin/csh wang Changing shell for wang. Shell changed. [root@centos7 ~]#getent passwd wang wang:x:1000:1000:wangsicong,wanda,10000,11111:/home/wang:/bin/csh [root@centos7 ~]#usermod -s /bin/bash wang [root@centos7 ~]#getent passwd wang wang:x:1000:1000:wangsicong,wanda,10000,11111:/home/wang:/bin/bash
Example: modify the shell type that the user can not log in
[root@CentOS-7 ~]# getent passwd du du:x:1000:1000:duwenshuo,it,100001,10001111:/home/du:/bin/bash [root@CentOS-7 ~]# chsh -s /sbin/nologin du Changing shell for du. chsh: Warning: "/sbin/nologin" is not listed in /etc/shells. Shell changed. [root@CentOS-7 ~]# su - du This account is currently not available. [root@CentOS-7 ~]# chsh -s /bin/false du Changing shell for du. chsh: Warning: "/bin/false" is not listed in /etc/shells. Shell changed. [root@CentOS-7 ~]# su - du Last login: Mon May 17 17:09:12 CST 2021 on pts/0 [root@CentOS-7 ~]# id uid=0(root) gid=0(root) groups=0(root) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 [root@CentOS-7 ~]# chsh -s /bin/bash du Changing shell for du. Shell changed. [root@CentOS-7 ~]# su - du Last login: Mon May 17 17:09:36 CST 2021 on pts/0
3.9 creating groups
groupadd implements group creation
format
groupadd [option]...group_name
Common options:
-g GID to specify GID number;[GID_MIN,GID_MAX] -r Create system groups, Centos 6 Before: ID<500,Centos 7 in the future: ID<1000
example:
groupadd -g 48 -r apache
3.10 modification group
groupmod group attribute modification
Format:
groupmod [option]...group
Common options:
-n group_name: New name -g GID: new GID
3.11 group deletion
groupdel can delete groups
format
groupdel [options] group
Common options:
-f, --force Force deletion. Even the user's primary group should be forcibly deleted,However, users without a primary group will be unavailable and unable to log in
3.12 change group password
gpasswd command, you can change the group password or modify the membership of additional groups
format
gpasswd [option] group
Common options:
-a user take user Add to specified user group -d user Removes a user from the specified additional group user -A user1,user2,...Set the list of users with administrative rights
example:
#Add group members [root@CentOS-8 ~]# groupadd admins [root@CentOS-8 ~]# id du uid=1000(du) gid=1000(du) groups=1000(du) [root@CentOS-8 ~]# gpasswd -a du admins Adding user du to group admins [root@CentOS-8 ~]# id du uid=1000(du) gid=1000(du) groups=1000(du),1003(admins) [root@CentOS-8 ~]# groups du du : du admins [root@CentOS-8 ~]# getent group admins admins:x:1003:du #Delete group members [root@CentOS-8 ~]# gpasswd -d du admins Removing user du from group admins [root@CentOS-8 ~]# groups du du : du [root@CentOS-8 ~]# id du uid=1000(du) gid=1000(du) groups=1000(du) [root@CentOS-8 ~]# getent group admins admins:x:1003:
3.13 temporary switching of main group
The newgrp command can temporarily switch the primary group. If the user does not belong to this group, the group password is required
Format:
newgrp [-] [group]
If you use the - option, you can initialize the user environment
[root@CentOS-8 ~]# gpasswd root Changing the password for group root New Password: Re-enter new password: [root@centos8 ~]#getent gshadow root root:$6$G.jsR/jv.L/Eld$TInRxHmsafucROg9njCIy8gIdG/H50AF5Z0iqlAehOdQXVX2A9l6tVX9YF8pkwFo8./J.2oJhtC6JOHBnOiYX.:: [root@CentOS-8 ~]# su - wang [wang@CentOS-8 ~]$ newgrp root Password: [wang@CentOS-8 ~]$ id uid=1001(wang) gid=0(root) groups=0(root),1001(wang) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 [root@CentOS-8 ~]# su - du [du@CentOS-8 ~]$ newgrp root Password: [du@CentOS-8 ~]$ id uid=1000(du) gid=0(root) groups=0(root),1000(du) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 [du@CentOS-8 ~]$ getent passwd du du:x:1000:1000:duwenshuo,it,100001,111111:/home/du:/bin/bash [du@CentOS-8 ~]$ touch du1.txt [du@CentOS-8 ~]$ ll total 0 -rw-r--r--. 1 du root 0 May 18 14:55 du1.txt -rw-rw-r--. 1 du du 0 May 17 16:01 du.txt [du@CentOS-8 ~]$ exit exit [du@CentOS-8 ~]$ id uid=1000(du) gid=1000(du) groups=1000(du) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 [du@CentOS-8 ~]$ touch du2.txt [du@CentOS-8 ~]$ ll total 0 -rw-r--r--. 1 du root 0 May 18 14:55 du1.txt -rw-rw-r--. 1 du du 0 May 18 14:55 du2.txt -rw-rw-r--. 1 du du 0 May 17 16:01 du.txt
3.14 changing and viewing group members
Group MEMS can manage the membership of additional groups
Format:
groupmems [options] [action]
Common options:
-g, --group groupname #Change to the specified group (root only) -a, --add username #Specify the user to join the group -d, --delete username #Remove user from group -p, --purge #Clear all members from group -l, --list #Displays a list of group members
groups to view user group relationships
format
#View the list of groups to which the user belongs group [option].[username]...
example:
[root@CentOS-8 ~]# groupmems -l -g admins [root@CentOS-8 ~]# id mage uid=1002(mage) gid=1002(mage) groups=1002(mage) [root@CentOS-8 ~]# groupmems -a mage -g admins [root@CentOS-8 ~]# id mage uid=1002(mage) gid=1002(mage) groups=1002(mage),1003(admins) [root@CentOS-8 ~]# groupmems -l -g admins mage [root@CentOS-8 ~]# groupmems -a du -g admins [root@CentOS-8 ~]# groupmems -l -g admins mage du [root@CentOS-8 ~]# groupmems -d du -g admins [root@CentOS-8 ~]# groupmems -l -g admins mage [root@CentOS-8 ~]# groups du du : du [root@CentOS-8 ~]# groupmems -l -g admins mage [root@CentOS-8 ~]# groupmems -p -g admins [root@CentOS-8 ~]# groupmems -l -g admins
3.15 practice
- Create the user gentoo, the additional groups are bin and root, the default shell is / bin/csh, and the comment information is "Gentoo Distribution"“
[root@lianxi01 ~]# useradd gentoo -G bin,root -s /bin/csh -c "Gentoo istribution" [root@lianxi01 ~]# getent passwd gentoo gentoo:x:1005:1005:Gentoo istribution:/home/gentoo:/bin/csh
- Create the following user, group, and group memberships
Group named Web
User nginx, using web as an additional group
User varnish, using web as an additional group
The user mysql cannot log in to the system interactively, and is not a member of web. The passwords of nginx, varnish and mysql are magedu
[root@lianxi01 ~]# groupadd webs [root@lianxi01 ~]# useradd nginx -G webs [root@lianxi01 ~]# useradd varnish -G webs [root@lianxi01 ~]# useradd mysql -s /bin/nologin [root@lianxi01 ~]# echo -e "magedu\nmagedu"|passwd nginx Changing password for user nginx. New password: BAD PASSWORD: The password is shorter than 8 characters Retype new password: passwd: all authentication tokens updated successfully. [root@lianxi01 ~]# echo -e "magedu\nmagedu"|passwd varnish Changing password for user varnish. New password: BAD PASSWORD: The password is shorter than 8 characters Retype new password: passwd: all authentication tokens updated successfully. [root@lianxi01 ~]# echo -e "magedu\nmagedu"|passwd mysql Changing password for user mysql. New password: BAD PASSWORD: The password is shorter than 8 characters Retype new password: passwd: all authentication tokens updated successfully.
4 file authority management
The permission of a program to access a file depends on the initiator of the program
- The initiator of the process is the same as the owner of the file: the file owner permission is applied
- The initiator of the process belongs to the file group; the file group permission is applied
- Apply file "other" permissions
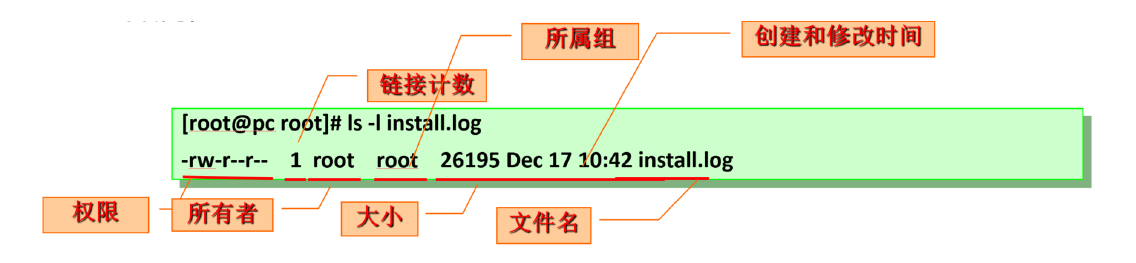
4.1 file owner and group attribute operation
4.1.1 owner of setting file chown
The chown command can modify the owner or group of a file
format
chown [option]...[owner][:[group]] file... chown [option]...--reference=rfile file...
Instructions:
owner #Modify owner only owner:group #Modify both owner and group :group #Only the group can be modified, and the colon can also be replaced --reference=rfile #Refer to the specified attribute to modify -R #Recursion, this option is used with caution and is very dangerous
example:
[root@CentOS-8 data]# cp /etc/fstab f1.txt [root@CentOS-8 data]# ll total 4 -rw-r--r--. 1 root root 709 May 18 15:30 f1.txt [root@CentOS-8 data]# pwd /data [root@CentOS-8 data]# ll total 4 -rw-r--r--. 1 root root 709 May 18 15:30 f1.txt [root@CentOS-8 data]# chown du f1.txt [root@CentOS-8 data]# ll total 4 -rw-r--r--. 1 du root 709 May 18 15:30 f1.txt [root@CentOS-8 data]# chown :admins f1.txt [root@CentOS-8 data]# ll f1.txt -rw-r--r--. 1 du admins 709 May 18 15:30 f1.txt [root@CentOS-8 data]# chown root.bin f1.txt [root@CentOS-8 data]# ll total 4 -rw-r--r--. 1 root bin 709 May 18 15:30 f1.txt [root@CentOS-8 data]# chown du:admins f1.txt [root@CentOS-8 data]# ll total 4 -rw-r--r--. 1 du admins 709 May 18 15:30 f1.txt [root@CentOS-8 data]# cp /etc/issue f2.txt [root@CentOS-8 data]# ll total 8 -rw-r--r--. 1 du admins 709 May 18 15:30 f1.txt -rw-r--r--. 1 root root 23 May 18 15:33 f2.txt [root@CentOS-8 data]# chown --reference=f1.txt f2.txt [root@CentOS-8 data]# ll total 8 -rw-r--r--. 1 du admins 709 May 18 15:30 f1.txt -rw-r--r--. 1 du admins 23 May 18 15:33 f2.txt
example:
[root@CentOS-8 ~]# chown -R du.admins /data/ [root@CentOS-8 ~]# ll / total 28 lrwxrwxrwx. 1 root root 7 Nov 3 2020 bin -> usr/bin dr-xr-xr-x. 5 root root 4096 Apr 30 10:36 boot drwxr-xr-x. 2 du admins 34 May 18 15:33 data ...
4.1.2 set the group information chgrp
The chgrp command can modify only the group to which the file belongs
format
chgrp [option]...group file... chgrp [option]...--reference=rfile file...
-R recursion
example:
[root@CentOS-8 data]# ll f1.txt -rw-r--r--. 1 du admins 709 May 18 15:30 f1.txt [root@CentOS-8 data]# chgrp admins f1.txt [root@CentOS-8 data]# ll f1.txt -rw-r--r--. 1 du admins 709 May 18 15:30 f1.txt
4.2 file permissions
4.2.1 document authority description
File permissions are mainly defined for three types of objects
owner Owner, u group Belonging group, g other other, o
be careful:
The final permissions of users are matched from left to right, that is, owners, groups and others. Once the permissions are matched, they will take effect immediately and will not view their permissions to the right r and w Permission pair root Invalid user As long as the owner,Group or other One of the three is x jurisdiction,root It can be executed
Each file defines three common permissions for each type of visitor
Each file defines three permissions for each type of visitor
r readable w writable x excutable
Permissions on files:
r You can use file viewing tools, such as: cat,You can get its content w Its contents can be modified x You can request the kernel to start this file as a program, that is, you can execute (run) this file (the content of this file must be executable)
Permissions on Directory:
r have access to ls View a list of files in this directory w You can create files in this directory or delete files in this directory, regardless of the permissions of the deleted files x sure cd Enter this directory to use ls -l View file metadata in this directory (must be matched) r Permission), which belongs to the minimum accessible permission of the directory X Directory only x Permission, do not give files without execution permission x jurisdiction
Interview questions:
Linux What is the difference between the permissions of directories and files in?(Explain the difference between read, write and execute permissions
Authority of mathematical method
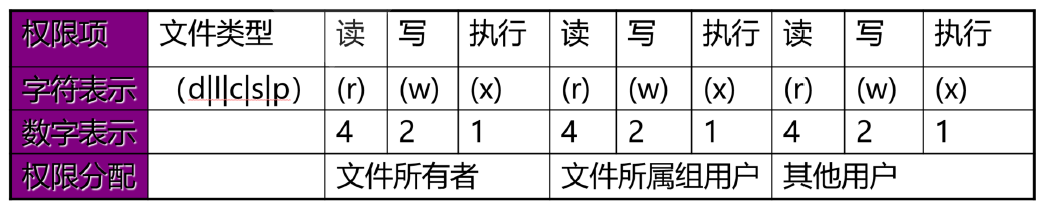
Octal digit
--- 000 0 --x 001 1 -w- 010 2 -wx 011 3 r-- 100 4 r-x 101 5 rw- 110 6 rwx 111 7
For example:
rw-r----- 640 rwxr-xr-x 755
4.2.2 modify file permissions chmod
Format:
chmod [option]...mode[,mode]...file... chmod [option]...octal-mode file... #Refer to the permissions of the rfile file and modify the file to be the same as the rfile file chmod [option]...--reference=rfile file...
Description: mode method format
mode: who opt permission who:u,g,o,a opt:+,-,= permission:r,w,x Modify all permissions of a specified type of user u= g= o= ug= a= u=,g= Modify one or more permissions of a specified type of user u+ u- g+ g- o+ o- a+ a- + - -R:Recursively modify permissions
Example: setting X permissions
[root@CentOS-8 data]# ll dir total 8 -rw-r--r--. 1 root root 709 May 18 16:19 f1.txt -rw-r--r--. 1 root root 23 May 18 16:19 f2.txt drw-r--r--. 2 root root 6 May 18 16:19 subdir [root@CentOS-8 data]# ll -d dir drw-r--r--. 3 root root 48 May 18 16:19 dir [root@CentOS-8 data]# chmod -R a+X dir [root@CentOS-8 data]# ll -d dir drwxr-xr-x. 3 root root 48 May 18 16:19 dir [root@CentOS-8 data]# ll dir total 8 -rw-r--r--. 1 root root 709 May 18 16:19 f1.txt -rw-r--r--. 1 root root 23 May 18 16:19 f2.txt drwxr-xr-x. 2 root root 6 May 18 16:19 subdir
example:
chmod u+wx,g-r,o=rx file chmod -R g+rwx /testdir chmod 600 file
Example: interview questions
implement cp /etc/issue /data/dir Minimum permissions required? /bin/cp need x jurisdiction /etc/ need x jurisdiction /etc/issue need r jurisdiction /data need x jurisdiction /data/dir need w,x jurisdiction
4.3 default permissions for new files and directories
The value of umask can be used to save permissions when creating files
Implementation method:
- The default permission for a new file is 666 umask. If a bit of the result has execution (odd) permission, its permission will be + 1, and the even number will not change
- Default permission for new directory: 777 umask
Unprivileged user umask is 002 by default
The umask of root is 022 by default
View umask
umask #Mode display umask -S #Output callable umask -p
Modify umask
umask #
example:
umask 002 umask u=rw,g=r,o=
Persistent umask
- Global settings: / etc/bashrc
- User settings: ~ /. bashrc
example:
[root@CentOS-8 ~]# umask 0022 [root@CentOS-8 ~]# umask -S u=rwx,g=rx,o=rx [root@CentOS-8 ~]# umask -p umask 0022
example:
[root@CentOS-8 ~]# umask 0022 [root@CentOS-8 ~]# ( umask 666; touch /data/f10.txt ) [root@CentOS-8 ~]# umask 0022 [root@CentOS-8 ~]# ll /data/f10.txt ----------. 1 root root 0 May 19 10:30 /data/f10.txt
practice
- When the user docker does not have permission to execute the / testdir directory, what operations do you mean you cannot do?
- When the user mongodb does not have read permission to the / testdir directory, what does it mean that it cannot do?
- When user redis does not have write permission to / testdir directory, can the read-only file file1 in this directory be modified and deleted?
- When user zabbix has write and execute permissions on / testdir directory, can the read-only file file1 in this directory be modified and deleted?
- Copy the / etc/fstab file to / var/tmp, set the owner of the file to tomcat and the group to which it belongs to apps. The group has read and write permissions, and others have no permissions
- User git's home directory is deleted by mistake. Please rebuild and restore the user's home directory and corresponding permission attributes
4.4 special permissions on Linux file system
Previously, we introduced three common permissions: r, w, x, and three special permissions: suid, sgid, and sticky
special competencies
- SUID acts on the binary executable, and the user will inherit the permissions of the program owner
- SGID
Acting on binary executables, users inherit the permissions of all groups of this program
As on a directory, the group of newly created files in this directory will automatically inherit from this directory - STICKY works on the directory. Files in this directory can only be deleted by the owner
4.4.1 special permission SUID
Premise: the process has a master and a group; The file has a master and a group
- Whether any executable program file can be started as a process depends on whether the initiator has execution permission on the program file
- After starting as a process, the owner of the process is the initiator, and the group of the process is the group to which the initiator belongs
- The permission of a process to access a file depends on the initiator of the process
- The initiator of the process is the same as the owner of the file: the file owner permission is applied
- The initiator of the process belongs to the file group; Apply file group permissions
- Apply file "other" permissions
SUID permission function on binary executable:
- Whether any executable program file can be started as a process depends on whether the initiator has execution permission on the program file
- After starting as a process, the owner of the process is the owner of the original program file
- SUID is only valid for binary executables
- SUID setting has no meaning on the directory
SUID permission setting:
chmod u+s FILE... chmod 4xxx FILE chmod u-s FILE...
example:
[root@centos8 ~]#ls -l /usr/bin/passwd -rwsr-xr-x. 1 root root 34928 May 11 2019 /usr/bin/passwd
4.4.2 special permission SGID
SGID permission function on binary executable:
- Whether any executable program file can be started as a process depends on whether the initiator has execution permission on the program file
- After starting as a process, the process belongs to the group of the original program file
SGID permission setting:
chmod g+s file... chmod 2xxx file... chmod g-s file...
SGID permission function on Directory:
By default, when a user creates a file, its group is the primary group to which the user belongs. Once a directory is set with SGID, the group to which the user with write permission creates a file in this directory is the group to which the directory belongs. It is usually used to create a collaboration directory
SGID permission setting:
chmod g+s dir... chmod 2xxx dir... chmod g-s dir...
4.4.3 Sticky bit of special permission
A directory with write permission. Usually, a user can delete any file in the directory, regardless of the permission or ownership of the file
Set the Sticky bit in the directory, and only the owner or root of the file can delete the file
sticky settings are meaningless on files
Sticky permission settings:
chmod o+t DIR... chmod 1xxx DIR chmod o-t DIR...
example:
[root@centos8 ~]#ll -d /tmp drwxrwxrwt. 15 root root 4096 Dec 12 20:16 /tmp
4.4.4 special authority digital method
SUID SGID STICKY
000 0 001 1 010 2 011 3 100 4 101 5 110 6 111 7
example:
chmod 4777 /tmp/a.txt
Permission bit mapping
SUID: user, occupying the execution permission bit of the owner
s: Owner has x permission
S: Owner does not have x permission
SGID: group, occupying the execution permission bit of the group
s: group has x permissions
S: group does not have x permission
Sticky: other, occupy the execution permission bit of other
t: other has x permissions
T: other does not have x permission
4.5 setting file special attributes
Set the special attributes of the file, and you can access the root user to delete or modify the file by mistake
Cannot delete, rename, change
chattr +i file
You can only add content, not delete, rename
chattr +a file
Show specific properties
lsattr
example:
[root@CentOS-8 data]# chattr +i dir [root@CentOS-8 data]# lsattr dir -------------------- dir/f1.txt -------------------- dir/f2.txt -------------------- dir/subdir [root@CentOS-8 data]# lsattr * -------------------- dir/f1.txt -------------------- dir/f2.txt -------------------- dir/subdir -------------------- f10.txt -------------------- f1.txt -------------------- f2.txt [root@CentOS-8 data]# ll total 8 drwxr-xr-x. 3 root root 48 May 18 16:19 dir ----------. 1 root root 0 May 19 10:30 f10.txt -rw-r--r--. 1 du admins 709 May 19 10:13 f1.txt -rw-r--r--. 1 du admins 23 May 18 15:33 f2.txt [root@CentOS-8 data]# rm -rf dir rm: cannot remove 'dir/f1.txt': Operation not permitted rm: cannot remove 'dir/f2.txt': Operation not permitted rm: cannot remove 'dir/subdir': Operation not permitted [root@CentOS-8 data]# lsattr -------------------- ./f1.txt -------------------- ./f2.txt ----i--------------- ./dir -------------------- ./f10.txt [root@CentOS-8 data]# chattr -i dir [root@CentOS-8 data]# lsattr -------------------- ./f1.txt -------------------- ./f2.txt -------------------- ./dir -------------------- ./f10.txt
4.6 Access Control List ACL
4.6.1 ACL permission function
ACL: Access Control List to realize flexible permission management
In addition to the owner of the file, the group and others, you can set permissions for more users
xfs and ext4 file systems created by CentOS7 by default have ACL functions
In versions before CentOS7, the ext4 file system created manually by default has no ACL function and needs to be added manually
tune2fs -o acl /dev/sdb1 mount -o acl /dev/sdb1 /mnt/test
ACL effective order:
Owner, custom user, group|Custom groups, others
4.6.2 ACL related commands
setfacl can set ACL permissions
getfacl to view the set ACL permissions
example:
[root@CentOS-8 data]# ll f1.txt -rw-r--r--. 1 root root 709 May 19 10:13 f1.txt [root@CentOS-8 data]# setfacl -m u:du:- f1.txt [root@CentOS-8 data]# ll f1.txt -rw-r--r--+ 1 root root 709 May 19 10:13 f1.txt [root@CentOS-8 data]# getfacl f1.txt # file: f1.txt # owner: root # group: root user::rw- user:du:--- group::r-- mask::r-- other::r-- [root@CentOS-8 data]# su du [du@CentOS-8 data]$ cat f1.txt cat: f1.txt: Permission denied [du@CentOS-8 data]$ echo xxx >> f1.txt bash: f1.txt: Permission denied
example:
[root@centos8 data]#getfacl f1.txt # file: f1.txt # owner: root # group: root user::rw- group::r-- other::r-- [root@centos8 data]#setfacl -m u:du:0 f1.txt [root@centos8 data]#setfacl -m g:admins:w f1.txt [root@centos8 data]#ll f1.txt -rw-rw-r--+ 1 root root 718 Dec 18 14:44 f1.txt [root@CentOS-8 data]# getfacl f1.txt # file: f1.txt # owner: root # group: root user::rw- user:du:--- group::r-- group:admins:-w- mask::rw- other::r-- [root@centos8 data]#id wang uid=1000(wang) gid=1000(wang) groups=1000(wang) [root@centos8 data]#id mage uid=1001(mage) gid=1001(mage) groups=1001(mage) [root@centos8 data]#su mage [mage@centos8 data]$cat f1.txt # # /etc/fstab # Created by anaconda on Wed Dec 11 11:11:16 2019 # # Accessible filesystems, by reference, are maintained under '/dev/disk/'. # See man pages fstab(5), findfs(8), mount(8) and/or blkid(8) for more info. # # After editing this file, run 'systemctl daemon-reload' to update systemd # units generated from this file. # UUID=1b950ef9-7142-46bd-975c-c4ac1e0d47e8 / xfs defaults 0 0 UUID=667a4c81-8b4b-4a39-a111-b11cb6d09309 /boot ext4 defaults 1 2 UUID=38d14714-c018-41d5-922c-49e415decbca /data xfs defaults 0 0 UUID=a0efb2bb-8227-4317-a79d-0a70d515046c swap swap defaults 0 0 magedata [mage@centos8 data]$echo magedata2 >> f1.txt bash: f1.txt: Permission denied [mage@centos8 data]$exit exit [root@centos8 data]#gpasswd -a mage admins Adding user mage to group admins [root@centos8 data]#id mage uid=1001(mage) gid=1001(mage) groups=1001(mage),1002(admins) [root@centos8 data]#su mage [mage@centos8 data]$echo magedata3 >> f1.txt [mage@centos8 data]$cat f1.txt cat: f1.txt: Permission denied [mage@centos8 data]$exit exit [root@centos8 data]#su wang [wang@centos8 data]$cat f1.txt cat: f1.txt: Permission denied [wang@centos8 data]$echo wangdata >> f1.txt bash: f1.txt: Permission denied [wang@centos8 data]$exit exit [root@centos8 data]#groupmems -a wang -g admins [root@centos8 data]#id wang uid=1000(wang) gid=1000(wang) groups=1000(wang),1002(admins) [root@centos8 data]#su wang [wang@centos8 data]$getfacl f1.txt # file: f1.txt # owner: root # group: root user::rwuser:wang:--- group::r-- group:admins:-w- mask::rw other::r-- [wang@centos8 data]$cat f1.txt cat: f1.txt: Permission denied [wang@centos8 data]$echo wangdata2 >> f1.txt bash: f1.txt: Permission denied
example:
mount -o acl /directory getfacl file |directory setfacl -m u:wang:rwx file|directory setfacl -m g:admins:rw file| directory setfacl -x u:wang file |directory #Clear all ACL permissions setfacl -b file1 #Copy the acl permission of file1 to file2 getfacl file1 | setfacl --set-file=- file2
mask permissions
- The mask only affects the maximum permissions of people and groups other than the owner and other
- The mask can become an effective permission only after logical and operation with the user's permission
- User or group settings must exist within the scope of mask permission settings to take effect
example:
setfacl -m mask::rx file
example:
[root@centos8 data]#ll f1.txt -rw-rw-r--+ 1 root root 728 Dec 18 14:51 f1.txt [root@centos8 data]#chmod g=r f1.txt [root@centos8 data]#ll f1.txt -rw-r--r--+ 1 root root 728 Dec 18 14:51 f1.txt [root@centos8 data]#getfacl f1.txt # file: f1.txt # owner: root # group: root user::rw- user:wang:--- group::r-- group:admins:-w- #effective:--- mask::r-- other::r-- [root@centos8 data]#setfacl -m mask::rw f1.txt [root@centos8 data]#getfacl f1.txt # file: f1.txt # owner: root # group: root user::rwuser:wang:--- group::r-- group:admins:-w- mask::rw- other::r-- [root@centos8 data]#setfacl -m u:wang:rwx f1.txt [root@centos8 data]#getfacl f1.txt # file: f1.txt # owner: root # group: root user::rwuser:wang:rwx group::r-- group:admins:-wmask::rwx other::r-- [root@centos8 data]#setfacl -m mask::rw f1.txt [root@centos8 data]#getfacl f1.txt # file: f1.txt # owner: root # group: root user::rw- user:wang:rwx #effective:rw- group::r-- group:admins:-w- mask::rw- other::r--
The – set option will delete the original ACL items and replace them with new ones. It should be noted that UGO settings must be included. You can't just add ACLS like - m
example:
setfacl --set u::rw,u:wang:rw,g::r,o::- file1
4.6.3 backup and restore ACL
The main file operation commands cp and mv support ACL, but the cp command needs to add the - p parameter. However, tar and other common backup tools do not retain ACL information of directories and files
example:
#Backup ACL getfacl -R /tmp/dir > acl.txt #Remove ACL permissions setfacl -R -b /tmp/dir #Restore ACL permissions setfacl -R --set-file=acl.txt /tmp/dir #Restore ACL permissions setfacl --restore acl.txt #View ACL permissions getfacl -R /tmp/dir
example:
[root@centos8 data]#getfacl * # file: f1.txt # owner: root # group: root user::rw- user:wang:rwx #effective:rw- group::r-- group:admins:-w- mask::rw- other::r-- # file: f2.txt # owner: root # group: root user::rw- group::r-- other::r-- # file: f3.txt # owner: root # group: root user::rw- user:wang:rwx #effective:rw- group::r-- group:admins:-w- mask::rw- other::r-- [root@centos8 data]#cd [root@centos8 ~]#tar cvf data.tar /data/ tar: Removing leading `/' from member names /data/ /data/f1.txt /data/f2.txt /data/f3.txt [root@centos8 ~]#tar xvf data.tar -C /opt data/ data/f1.txt data/f2.txt data/f3.txt [root@centos8 ~]#ls /opt data [root@centos8 ~]#cd /opt/data [root@centos8 data]#ll total 12 -rw-rw-r-- 1 root root 728 Dec 18 14:51 f1.txt -rw-r--r-- 1 root root 728 Dec 18 15:01 f2.txt -rw-rw-r-- 1 root root 728 Dec 18 14:51 f3.txt [root@centos8 data]#getfacl -R /data > /root/acl.txt getfacl: Removing leading '/' from absolute path names [root@centos8 data]#cat /root/acl.txt # file: data # owner: root # group: admins user::rwx group::rwx other::rwx # file: data/f1.txt # owner: root # group: root user::rw- user:wang:rwx #effective:rw- group::r-- group:admins:-w- mask::rw- other::r-- # file: data/f2.txt # owner: root # group: root user::rw- group::r-- other::r-- # file: data/f3.txt # owner: root # group: root user::rw- user:wang:rwx #effective:rw- group::r-- group:admins:-w- mask::rw- other::r-- [root@centos8 data]#ll /opt/data total 12 -rw-rw-r-- 1 root root 728 Dec 18 14:51 f1.txt -rw-r--r-- 1 root root 728 Dec 18 15:01 f2.txt -rw-rw-r-- 1 root root 728 Dec 18 14:51 f3.txt [root@centos8 data]#cd [root@centos8 ~]#setfacl -R --set-file=/root/acl.txt /opt [root@centos8 ~]#ll /opt/data/ total 12 -rw-rw-r--+ 1 root root 728 Dec 18 14:51 f1.txt -rw-rw-r--+ 1 root root 728 Dec 18 15:01 f2.txt -rw-rw-r--+ 1 root root 728 Dec 18 14:51 f3.txt [root@centos8 ~]#setfacl -b -R /opt/data [root@centos8 ~]#ll /opt/data total 12 -rw-r--r-- 1 root root 728 Dec 18 14:51 f1.txt -rw-r--r-- 1 root root 728 Dec 18 15:01 f2.txt -rw-r--r-- 1 root root 728 Dec 18 14:51 f3.txt
practice:
- New files created in / testdir/dir automatically belong to the web group. Members of group apps, such as tomcat, can read and write these new files. Members of group dbs, such as mysql, can only read new files. Other users (not belonging to web, apps, dbs) cannot access this folder
[root@centos8 ~]#mkdir -p /testdir/dir [root@centos8 ~]#groupadd webs groupadd: group 'webs' already exists [root@centos8 ~]#chgrp webs /testdir/dir [root@centos8 ~]#chmod g+s /testdir/dir [root@centos8 ~]#groupadd apps;groupadd dbs [root@centos8 ~]#useradd -G apps tomcat;useradd -G dbs mysql [root@centos8 ~]#setfacl -d -m g:apps:rw /testdir/dir [root@centos8 ~]#setfacl -d -m g:dbs:r /testdir/dir [root@centos8 ~]#chmod o= /testdir/dir [root@centos8 ~]#getfacl /testdir/dir/ getfacl: Removing leading '/' from absolute path names # file: testdir/dir/ # owner: root # group: webs # flags: -s- user::rwx group::r-x other::--- default:user::rwx default:group::r-x default:group:apps:rw- default:group:dbs:r-- default:mask::rwx default:other::r-x
- How to restore the / bin/chmod file after deleting its execution permission by mistake?
[root@centos8 ~]#ll /usr/bin/chmod -rwxr-xr-x. 1 root root 63880 Apr 27 2020 /usr/bin/chmod [root@centos8 ~]#chmod a-x /usr/bin/chmod [root@centos8 ~]#ll /usr/bin/chmod -rw-r--r--. 1 root root 63880 Apr 27 2020 /usr/bin/chmod [root@centos8 ~]#chmod a+x /usr/bin/chmod -bash: /usr/bin/chmod: Permission denied [root@centos8 ~]#setfacl -m u:root:x /usr/bin/chmod [root@centos8 ~]#chmod a+x /usr/bin/chmod [root@centos8 ~]#ll /usr/bin/chmod -rwxr-xr-x+ 1 root root 63880 Apr 27 2020 /usr/bin/chmod [root@centos8 ~]#setfacl -b /usr/bin/chmod [root@centos8 ~]#ll /usr/bin/chmod -rwxr--r-x. 1 root root 63880 Apr 27 2020 /usr/bin/chmod