✨ Learn, grow and love life with warmth ✨
preface
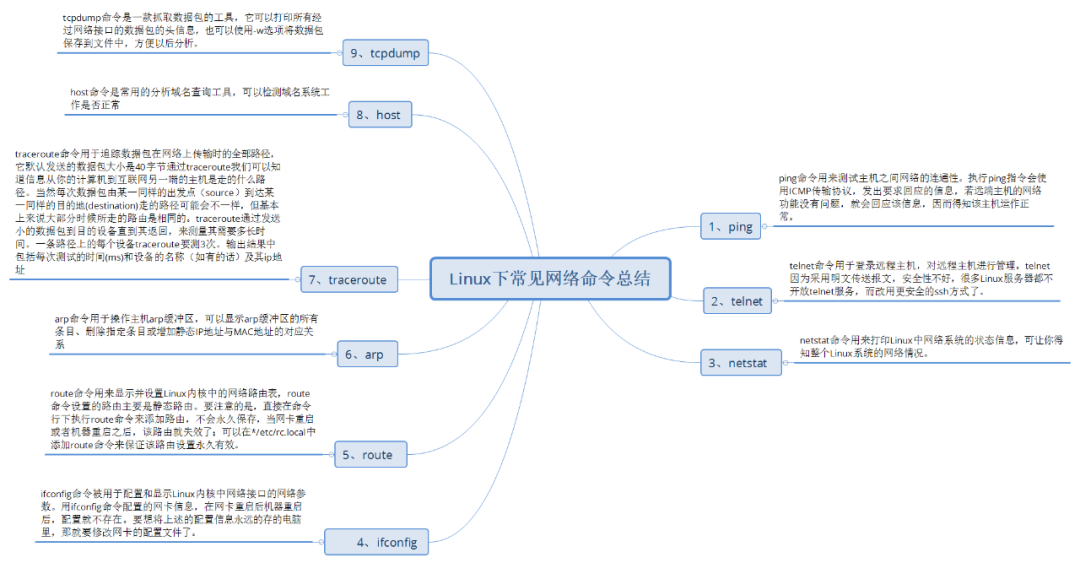
Today, let's talk about the content related to linux commands. In the ranking of the top 500 operating systems of supercomputers in the world, the proportion of Linux has been maintained at more than 85% for a long time in recent ten years, and has been showing a rapid upward trend. According to the 2016 ranking, The proportion of Linux has reached 98.80%. In fact, in the server application field of various large, medium and small enterprises, the market share of Linux system is getting closer and closer to this proportion, which is enough to show how excellent the performance of Linux is. Therefore, during the interview, we are often asked to make up for our shortcomings and find out the omissions and fill the vacancies according to our experience. Let's start today's dry goods. Let's go, Remember to like it and click to see it.

1.ping command
The ping command is used to test the network connectivity between hosts. When the ping command is executed, the ICMP transmission protocol will be used to send the message requesting response. If the network function of the remote host is OK, the message will be returned, so it is known that the host is operating normally.
usage
(1) Command format
ping (option) destination address
The destination address refers to the IP address, host name or domain name of the tested computer. The ping command contains 12 parameters, all of which can be viewed by executing Ping
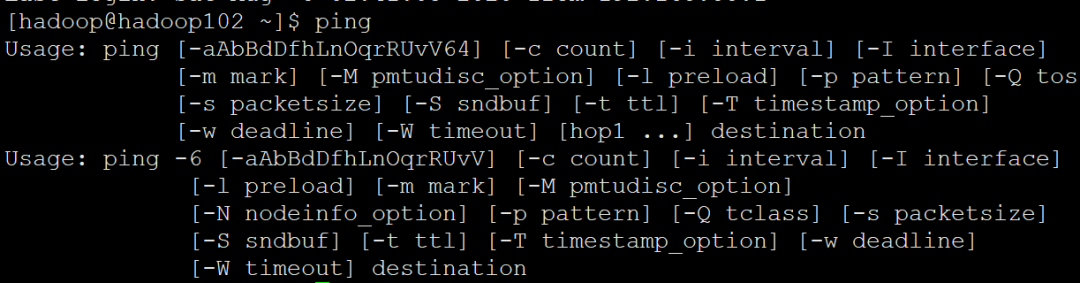
(2) Instance
ping www.baidu.com
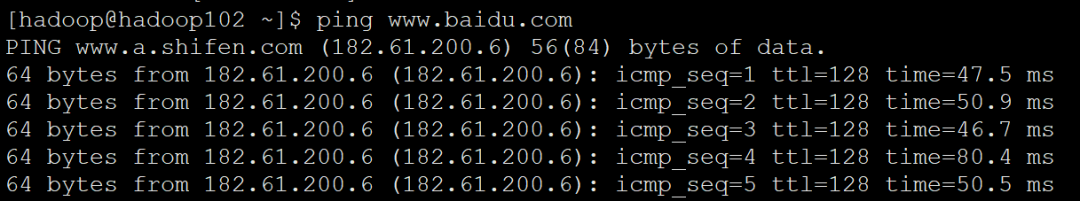
Note: The ping command under Linux is different from that under Windows , Ctrl+C is required to terminate
(3) Options
-d: use Socket of SO_DEBUG Function; -c<Completion times>: Set the number of times to complete the request response; -f: Limit detection; -i<Interval seconds>: Specify the interval between sending and receiving information; -L<network interface>: Send data packets using the specified network interface; -l<Preload>: Set the data packet sent before sending the request information; -n: Only output values; -p<Template style>: Set the template style of filling data packets; -q: The instruction execution process is not displayed, except for the relevant information at the beginning and end; -r: Ignore normal Routing Table,Directly send the data packet to the remote host; -R: Record the routing process; -s<Packet size>: Set the packet size; -v: Displays the execution process of the instruction in detail. -t<Survival value>: Set survival value TTL Size of
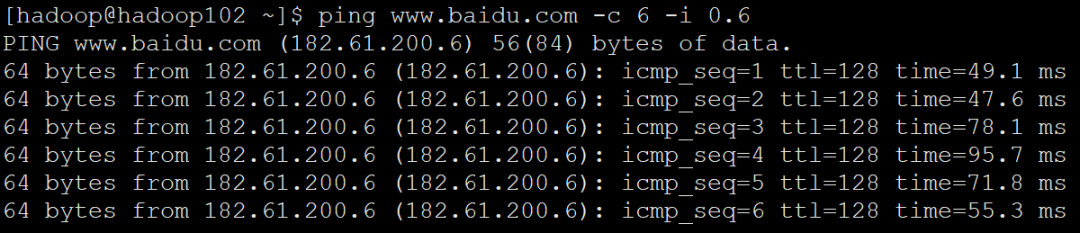
Tell me about one of them - c, -i parameter
Where – c count is the number of pings; - i interval is the time space between each ping
ping www.baidu.com -c 6 -i 0.6
2,telnet
Telnet command is used to log in to the remote host and manage the remote host. Because telnet uses plaintext to transmit messages, it has poor security and many problems Linux servers do not open telnet services, but use a more secure ssh mode .
3,netstat
The netstat command is used to print the status information of the network system in Linux, which can let you know the network situation of the whole Linux system.
Usage:
(1) Command format:
netstat (option)
(2) Options
-a or–all: Show all connections Socket; -A<Network type>or–<Network type>: List the relevant addresses in the network type connection; -c or–continuous: Continuously list network status; -C or–cache: Display the cache information configured by the router; -e or–extend: Display other network related information; -F or–fib: display FIB; -g or–groups: Display the member list of multi broadcast function group; -h or–help: Online help; -i or–interfaces: Display network interface information form; -l or–listening: Displays the name of the server under monitoring Socket; -M or–masquerade: Display the camouflaged network connection; -n or–numeric: Direct use ip Address, not through the domain name server; -N or–netlink or–symbolic: Display the symbolic connection name of the network hardware peripheral; -o or–timers: Display timer; -p or–programs: Show in use Socket Program identification code and program name; -r or–route: display Routing Table; -s or–statistice: Display the statistical table of network work information; -t or–tcp: display TCP Connection status of transmission protocol; -u or–udp: display UDP Connection status of transmission protocol; -v or–verbose: Display the instruction execution process; -V or–version: Display version information; -w or–raw: display RAW Connection status of transmission protocol; -x or–unix: Effect and assignment of this parameter-A unix"The parameters are the same; –ip or–inet: Effect and assignment of this parameter-A inet"Same parameters
(3) Instance
netstat -a // List all ports
netstat -at // List all tcp ports
netstat -au // List all udp ports
All TCP ports are displayed here
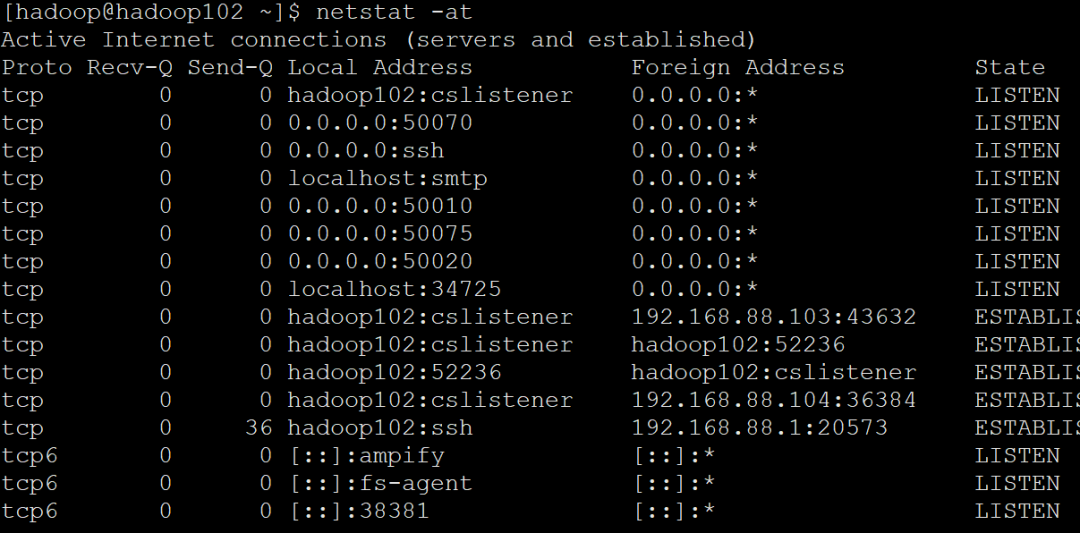
netstat - l // Show only listening ports
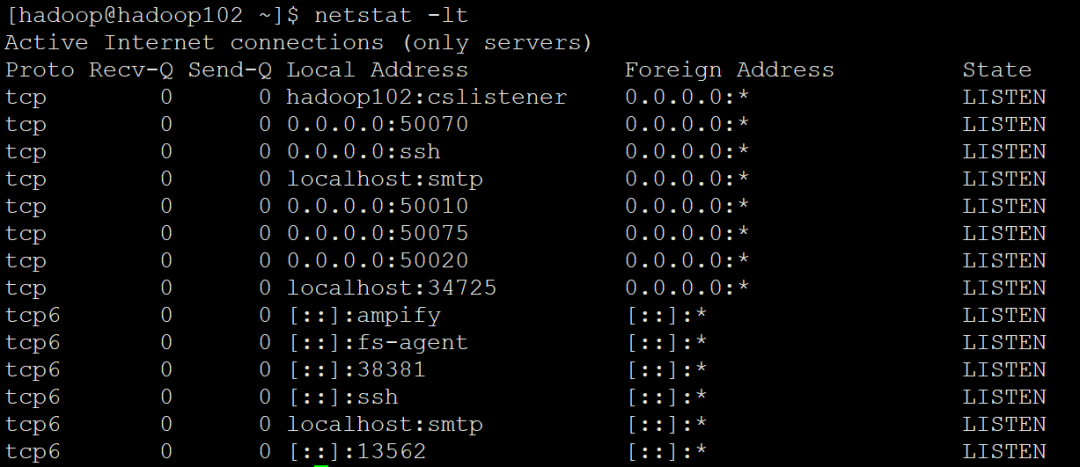
netstat -lt // Only all listening tcp ports are listed
netstat -lu // Only all listening udp ports are listed
Compared with the above figure, you can see that only the listening TCP ports are displayed
4,ifconfig
The ifconfig command is used to configure and display the network parameters of the network interface in the Linux kernel. The network card information configured with the ifconfig command does not exist after the network card is restarted and the machine is restarted. To store the above configuration information in the computer forever, it is necessary to modify the network card configuration file.
Usage:
(1) Command format
ifconfig (parameter)
(2) Instance
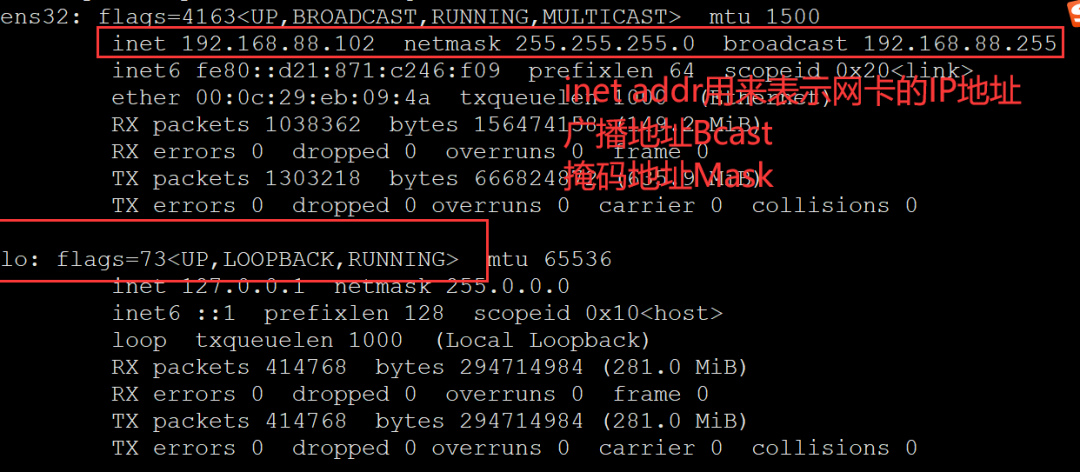
-
inet is used to represent the IP address of the network card. The IP address of the network card is 192.168.1.106
-
Broadcast address Bcast: 192.168.1.255
-
Mask address: 255.255.255.0
lo is the loopback address of the host , This is generally used to test a network program, but you don't want users of LAN or extranet to be able to view it. You can only run and view the network interface used on this host.
(3) Parameters
add<address>: Set up network devices IPv6 of ip address del<address>: Delete network device IPv6 of IP address down: Turn off the specified network device io_addr< I/O address>: Set network device I/O address irq< IRQ address>: Set network device IRQ; media<Network media type>: Set the media type of the network device; mem_start<Memory address>: Set the starting address occupied by the network device in the main memory; metric<number>: Specifies the number to be added when calculating the forwarding times of data packets; mtu<byte>: Set network device MTU; netmask<Subnet mask>: Set the subnet mask of the network device; tunnel<address>: establish IPv4 And IPv6 Tunnel communication address between; up: Start the specified network device; -broadcast<address>: Treat the data packet to be sent to the specified address as a broadcast data packet; -pointopoint<address>: Establish a direct connection with the network equipment at the specified address. This mode has the function of confidentiality; -promisc: Turns off or starts the of the specified network device promiscuous pattern; IP Address: Specifies the address of the network device IP Address; Network device: Specifies the name of the network device.
5,route
The route command is used to Display and set the network routing table in the Linux kernel , The route set by the route command is mainly a static route. It should be noted that the route is added directly by executing the route command on the command line and will not be permanently saved. After the network card is restarted or the machine is restarted, the route will fail. You can */ etc/rc.local Add the route command to ensure that the route setting is permanently valid.
Usage:
(1) Command format
route (option) (parameter)
(2) Options
-A: Set the address type; -C: Print will Linux Core routing cache; -v: Detailed information mode; -n: Do not execute DNS Reverse search, direct display in digital form IP Address; -e: netstat Display routing table in format; -net: Routing table to a network; -host: Routing table to a host.
(3) Parameters
Add: Add the specified route record Del: Deletes the specified routing record Target: Destination network or destination host gw: Set default gateway mss: set up TCP Maximum block length of(MSS),Unit is MB window: Specifies the path through the routing table TCP Connected TCP Window size dev: The network interface represented by the routing record
(4) Instance
The current route is displayed. You can see the change of adding option - n from the figure
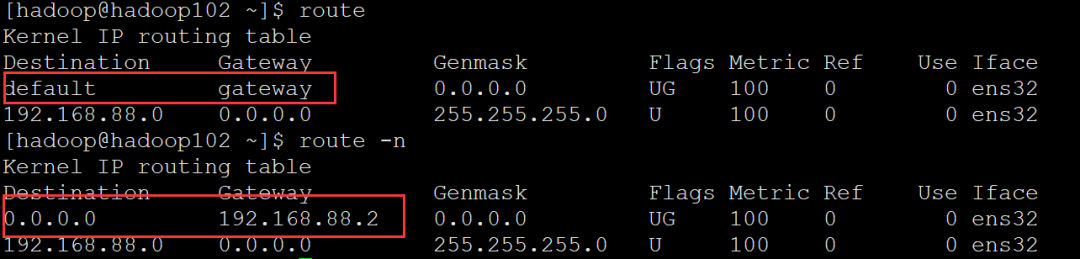
Delete and add default gateway settings (not shown here)
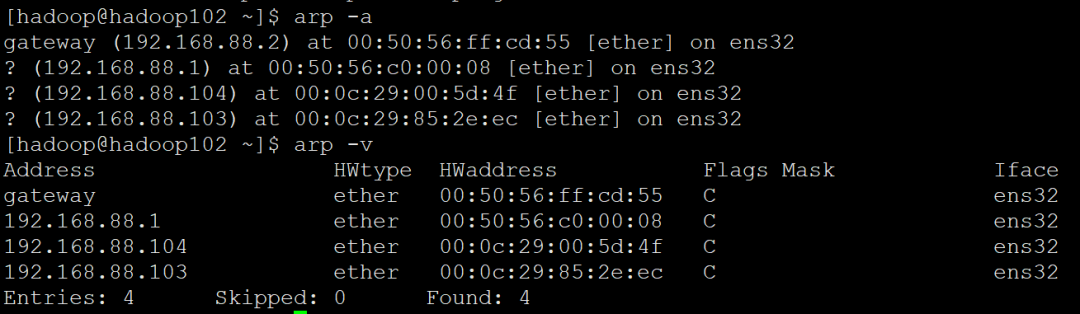
6,arp
The arp command is used to operate the host arp buffer. It can display all entries in the arp buffer, delete specified entries, or increase the correspondence between the static IP address and the MAC address
Usage:
(1) Command format
arp (option) (parameter)
(2) Options
-a<host>: display arp All entries in the buffer -H<Address type>: appoint arp Address type used by the instruction -d<host>: from arp Deletes the name of the specified host from the buffer arp entry -D: Use the hardware address of the specified interface -e: with Linux Display style display arp Entries in buffer -i<Interface>: Specify the action to perform arp Buffer network interface -s<host><hardware address>: Sets the of the specified host IP Address and MAC Static mapping of addresses -n: Display in digital form arp Entries in buffer -v: Show detailed arp Buffer entries, including statistics of buffer entries -f<file>: Set host IP Address and MAC Static mapping of addresses
(3) Parameters
Host: query the arp entry of the specified host in the arp buffer.
(4) Instance
arp -a
arp -v
7,traceroute
The traceroute command is used to track all paths of packets when they are transmitted over the network , The default packet size is 40 bytes. We can know from traceroute What is the path of information from your computer to the host at the other end of the Internet . Of course, every time a packet arrives at the same destination from the same source, the path may be different, but basically the route is the same most of the time. Traceroute measures how long it takes by sending a small packet to the destination device until it returns. The traceroute of each device on a path shall be tested 3 times. The output results include the time (ms) of each test, the name of the device (if any) and its ip address
Usage:
(1) Command format
traceroute (option) (parameter)
(2) Options
-d: use Socket Hierarchical troubleshooting function -f<survival time >: Set the survival value of the first detection packet TTL Size of -F: Set do not leave off position -g<gateway>: Set up 8 source routing gateways at most -i<network interface>: Send packets using the specified network interface -l: use ICMP Response substitution UDP Data information -m<Survival value>: Set the maximum survival value of the detection packet TTL Size of -n: Direct use IP Address, not hostname -p<Communication port>: set up UDP Communication port of transmission protocol -r: Ignore normal Routing Table,Send packets directly to the remote host -s<Source address>: Set the number of packets sent by the local host TOS numerical value -v: Displays the execution process of the instruction in detail -w<Timeout seconds>: Set the time to wait for the remote host to report -x: Turns on or off the correctness check of the packet
(3) Parameters
Host: specify the destination host IP address or host name
(4) Instance
traceroute www.baidu.com
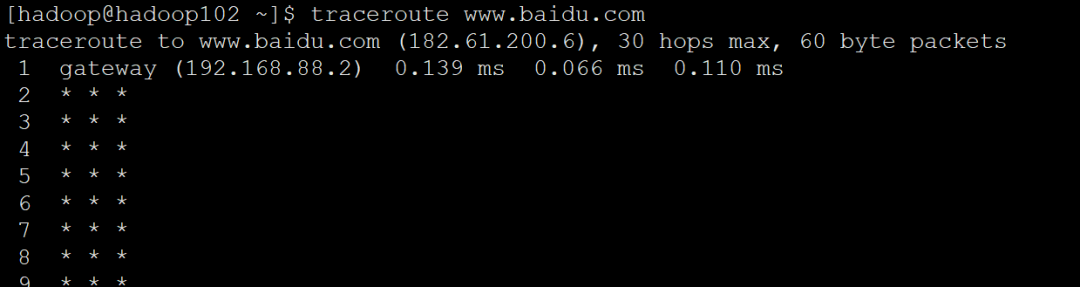
It can be seen from the figure that the record starts from 1 according to the serial number, Each record is a hop, and each hop represents a gateway, We can see that each line has three times in ms, which is actually the default parameter of - q. The return time after the detection packet sends three packets to each gateway and the gateway responds; In the later section, we will see that some lines are represented by asterisks. In this case, the firewall may block the ICMP return information, so we can't get any relevant packet return data.
8,host
The host command is a commonly used query tool for analyzing domain names. It can detect whether the domain name system works normally
Usage:
(1) Command format
host (option) (parameter)
(2) Options
-a: Show detailed DNS information -c<type>: Specify the query type. The default value is“ IN" -C: Query the full of the specified host SOA record -r: When querying the domain name, the recursive query method is not used -t<type>: Specifies the type of domain name information to query -v: Displays the details of instruction execution -a: Show detailed DNS Information; -w: If the domain name server does not give a response, wait until the domain name server gives a response -W<time>: Specify the maximum time for domain name query. If the domain name server does not give response information within the specified time, exit the instruction -4: use IPv4 -6: use IPv6
(3) Parameters
Host: the host information to query
9,tcpdump
tcpdump command is a tool for capturing data packets. It can print the header information of all data packets through the network interface, or use the - w option to save the data packets to a file for later analysis.
Usage:
(1) Command format
tcpdump (option)
(2) Options
-a: Attempt to convert network and broadcast addresses into names; -c<Number of packets>: Stop dumping after receiving the specified number of packets; -d: The compiled data packet is encoded into a readable format and dumped into standard output; -dd: Convert the compiled packet code into C Language format and dump to standard output; -ddd: Convert the compiled data packet code into decimal number format and dump it to standard output; -e: Display the header of the connection level on each column of dumping data; -f: Digital display of Internet address; -F<Expression file>: Specify the document containing the expression; -i<network interface>: Send data packets using the specified network section; -l: Buffer using standard output columns; -n: Do not convert the network address of the host into a name; -N: Do not list domain names; -O: Do not optimize packet coding; -p: Do not let the network interface enter the hybrid mode; -q : Fast output, only a few transmission protocol information are listed; -r<Packet file>: Read the packet data from the specified file; -s<Packet size>: Set the size of each packet; -S: List in absolute rather than relative values TCP Number of associations; -t: No time stamp is displayed on each column of dumping data; -tt: Display unformatted time stamps on each column of dumping data; -T<Packet type>: Force the packet specified by the expression to be translated into the set packet type; -v: Detailed display of instruction execution process; -vv: More detailed display of instruction execution process; -x: List packet data with hexadecimal word code; -w<Packet file>: Writes the packet data to the specified file.

end!