#Unified identity management platform IAM
Many enterprises have multiple office systems. Accounts, passwords, roles and permissions need to be set separately and cannot be managed uniformly.
I think the unified identity authentication management system IAM has the following three advantages:
- Establish a unified user management, identity rationing and identity authentication system to realize the dynamic synchronization of user identity and authority.
- Realize single sign on (B/S architecture) or password authentication login (C/S architecture) of all office systems (Applications).
- Strengthen information security early warning and audit, and improve system availability, security and user portability.
That is, one account opens up multiple office systems within the enterprise, covers multiple scenarios of control, and supports department, role, and personnel dimension authorization.
#Unified identity management platform IAM single sign on flow chart (B/S architecture)
Scope of use: a third-party system that needs to realize single sign on, use the login page of the unified identity management platform, and can send https requests. The following four steps are briefly summarized:
- authorize interface, request user authorization, and jump to the third-party system after completion.
- authorization_code interface to obtain authorization Token according to code.
- getUserInfo interface to obtain user information according to the Token.
- Logout interface, logout and login.
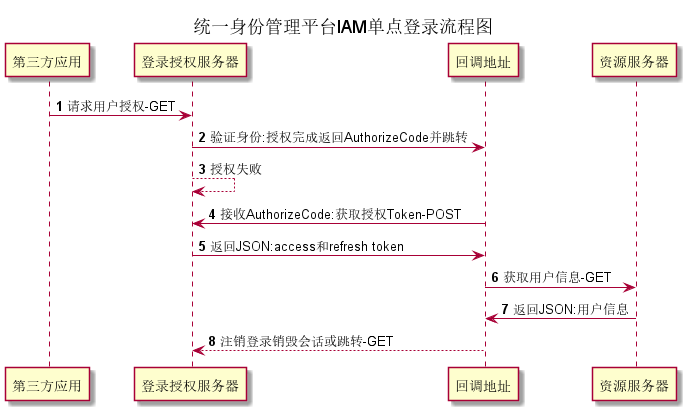
This paper will introduce the common single sign on third-party interface design of the unified identity authentication platform IAM.
#1. Request user authorization, and then jump to the third-party system for web design
Description of web interface:
| Request type | GET/WEB page access | |||||||||||||||
| Request example | https://iam.xxxxx.com:8080/idp/oauth2/authorize?redirect_uri=https://www.baidu.com&state=xxxx&client_id=xxxxx&response_type=code | |||||||||||||||
| Parameter description |
| |||||||||||||||
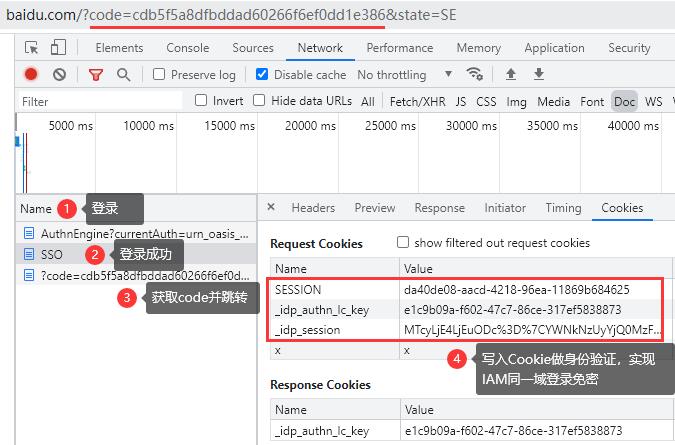
| processing logic | 1. Judgment parameters; 2. Validate client_ Whether the ID is valid; 3. Verify redirect_uri; 4. Display the authentication authorization page; 5. After authentication, the page jumps to redirect_uri with parameter authorization code (written into Cookie). | |||||||||||||||
| Return value | The callback address in the above text is Baidu as an example. After authorization, it will jump to https://www.baidu.com/?code=83953d36e2ae7c8903c6b589c8998670&state=xxxxx , carrying the parameters code and state. |
Actual operation:
WEB page login authorization interface (GET request)
Log in successfully and jump to the interface with the parameters code and state
#2. Obtain the Token authorization third-party interface design according to code
You can get access through the code above_ Token and refresh_token, when access_ When the token expires, you can use refresh_token to get new access again_ Token, keep the login status.
Interface Description:
| Request type | POST | |||||||||||||||
| Request example | https://iam.xxxxx.com:8080/idp/oauth2/getToken?client_id=xxxxxx&grant_type=authorization_code&code=xxxxxx&client_secret=xxxxxx | |||||||||||||||
| Parameter description |
| |||||||||||||||
| processing logic | 1. Verify the effectiveness of parameters; 2. Verify the validity and scope of authorization code; 3. Return JSON data according to the above judgment, verification and authentication results. | |||||||||||||||
| Return value | Type JSON, correct return value: { "access_token": "5e717f5eda086269706a407e3764092a", "refresh_token": "fb6e93b627a1a93679251f605097503c", "uid": "20210311135809626-B457-4E410EFEB", "expires_in": 1500 } |
Get token post request interface example code:
import org.apache.http.HttpEntity;
import org.apache.http.HttpResponse;
import org.apache.http.client.HttpClient;
import org.apache.http.client.methods.HttpPost;
import org.apache.http.impl.client.DefaultHttpClient;
import org.apache.http.params.BasicHttpParams;
import org.apache.http.params.HttpConnectionParams;
import org.apache.http.util.EntityUtils;
public class getToken {
public static String getToken(String url){
BasicHttpParams http = new BasicHttpParams();
//Set request timeout for 1 second
HttpConnectionParams.setConnectionTimeout(http,1000);
//Set the timeout for waiting for data for 1 second
HttpConnectionParams.setSoTimeout(http,1000);
HttpClient client = new DefaultHttpClient(http);
String jsonresult = "";
try {
//Http Post request
HttpPost post = new HttpPost(url);
HttpResponse response = client.execute(post);
//Get return parameters
HttpEntity entity =response.getEntity();
jsonresult = EntityUtils.toString(entity,"utf-8");
}catch (Exception ex){
ex.printStackTrace();
}finally {
client.getConnectionManager().shutdown();
}
return jsonresult;
}
public static void main(String[] args) {
String url = "https://iam.xxxxx.com:8080/idp/oauth2/getToken?client_id=SE&grant_type=authorization_code&code=dc605a7a6389b0898f653b4895359071&client_secret=6f369937851b4669ad66b41257b9a902";
//Output return JSON string
System.out.println(getToken(url));
}
}#3. Third party interface design for obtaining user information according to Token
Access obtained above_ Token can access the user interface, obtain user information, and realize the user's Secret free login on the third-party system (application).
Interface Description:
| Request type | GET | |||||||||
| Request example | https://iam.xxxxx.com:8080/idp/oauth2/getUserInfo?access_token=xxxxx&client_id=xxxxx | |||||||||
| Parameter description |
| |||||||||
| processing logic | 1. Verify the effectiveness of parameters; 2. Query the user information according to the attribute permission list configured by the application; 3. Return JSON data according to the above judgment, verification and authentication results. | |||||||||
| Return value | Type JSON string, correct return value: { "orgNamePath": "/ personnel department", "spRoleList": [], "uid": "20210311135809626-B457-4E410EFEB", "mail": "liming@qq.com", "orgCodePath": "W000001", "displayName": "Li Ming", "loginName": "E012345678", "mobile": "13999999999", "orgNumber": "P00000000", "employeeNumber": null } |
GET user information - GET request interface example code:
import org.apache.http.HttpEntity;
import org.apache.http.HttpResponse;
import org.apache.http.client.HttpClient;
import org.apache.http.client.methods.HttpGet;
import org.apache.http.impl.client.DefaultHttpClient;
import org.apache.http.params.BasicHttpParams;
import org.apache.http.params.HttpConnectionParams;
import org.apache.http.util.EntityUtils;
public class getUserInfo {
public static String getToken(String url){
BasicHttpParams http = new BasicHttpParams();
//Set request timeout for 1 second
HttpConnectionParams.setConnectionTimeout(http,1000);
//Set the timeout for waiting for data for 1 second
HttpConnectionParams.setSoTimeout(http,1000);
HttpClient client = new DefaultHttpClient(http);
String jsonresult = "";
try {
//Http Get request
HttpGet get = new HttpGet(url);
HttpResponse response = client.execute(get);
//Get return parameters
HttpEntity entity =response.getEntity();
jsonresult = EntityUtils.toString(entity,"utf-8");
}catch (Exception ex){
ex.printStackTrace();
}finally {
client.getConnectionManager().shutdown();
}
return jsonresult;
}
public static void main(String[] args) {
String url = "https://iam.xxxxx.com:8080/idp/oauth2/getUserInfo?access_token=xxxxx&client_id=xxxxx";
//Output return JSON string
System.out.println(getToken(url));
}
}#4. Logout log out, jump after completion, web design
The third-party application system requests the IAM authentication center to exit the URL globally. The authentication center destroys the user's global session and calls the application to destroy the session URL. The address needs to call the recycling authorization interface to clear the current oauth ticket and destroy the application local session.
The flow chart is as follows:
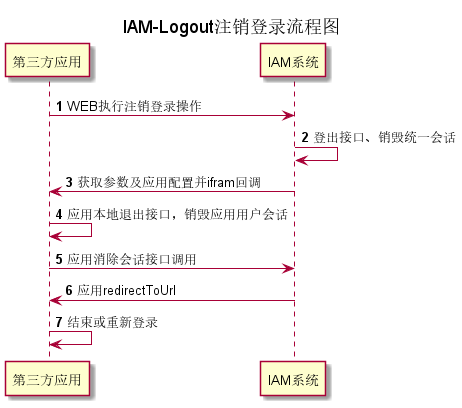
Description of web interface:
| Request type | GET/WEB page access | ||||||||||||
| Request example | https://iam.xxxxx.com:8080/idp/profile/OAUTH2/Redirect/GLO?redirctToUrl=https://www.baidu.com&redirectToLogin=true&entityId=xxxxx | ||||||||||||
| Parameter description |
| ||||||||||||
| processing logic | 1. Judgment parameters; 2. Return JSON data according to the above judgment, verification and authentication results. | ||||||||||||
| Return value | The callback address in the above text is Baidu as an example. After logging off, it will jump to https://www.baidu.com , if the jump is false, it will stay on the IAM logout page https://iam.xxxxx.com:8080/idp/http/logout.do |