2021 "Green League Cup" Chongqing University Student Information Security Competition - Light1ng team Writeup
For other directions, please refer to pdf:https://wws.lanzoui.com/iWk1ovo0eaj
Password: Le1a
Misc
Misc1: check in 1
The title gives a string of base64 codes
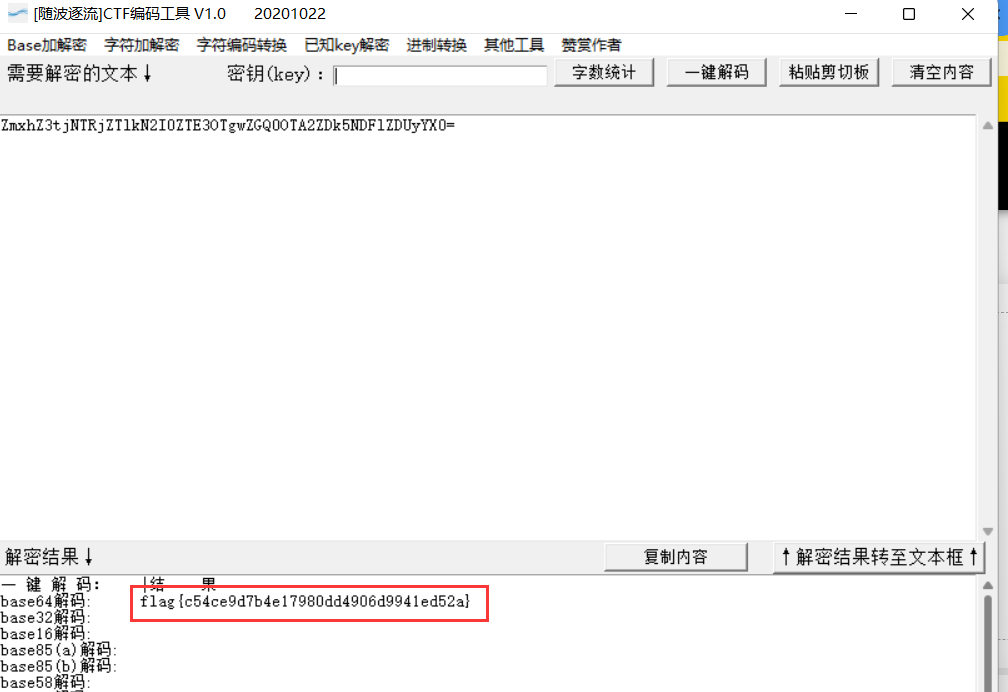
Decoded flag:
flag{c54ce9d7b4e17980dd4906d9941ed52a}
Misc2: DECODER
Download the attachment and open it to get 3 txt, which should correspond to the flag of the three parts
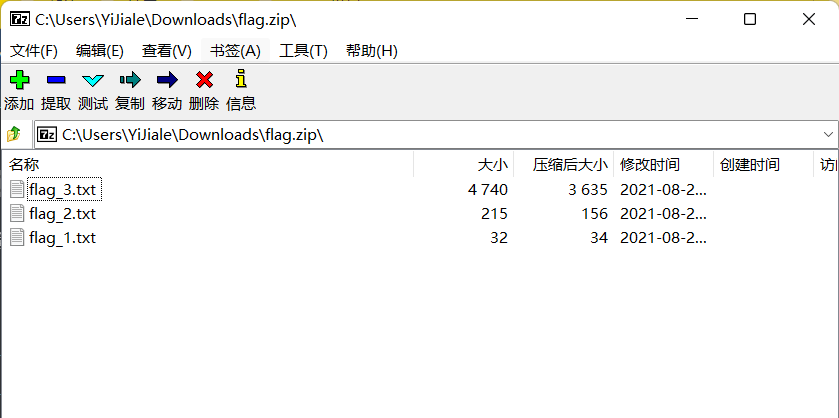
flag_1.txt: 042f38b694
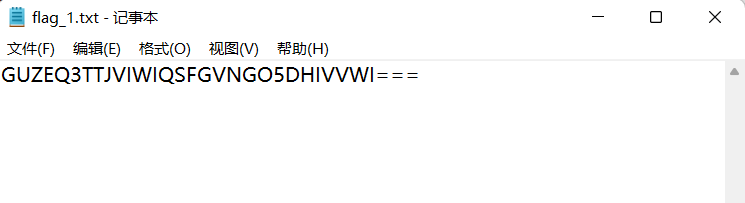
base32 decodes and obtains 52HnsMQdBE5ZgtgEkd
Decode base58 again to get 0JkOs1H8i%3A^
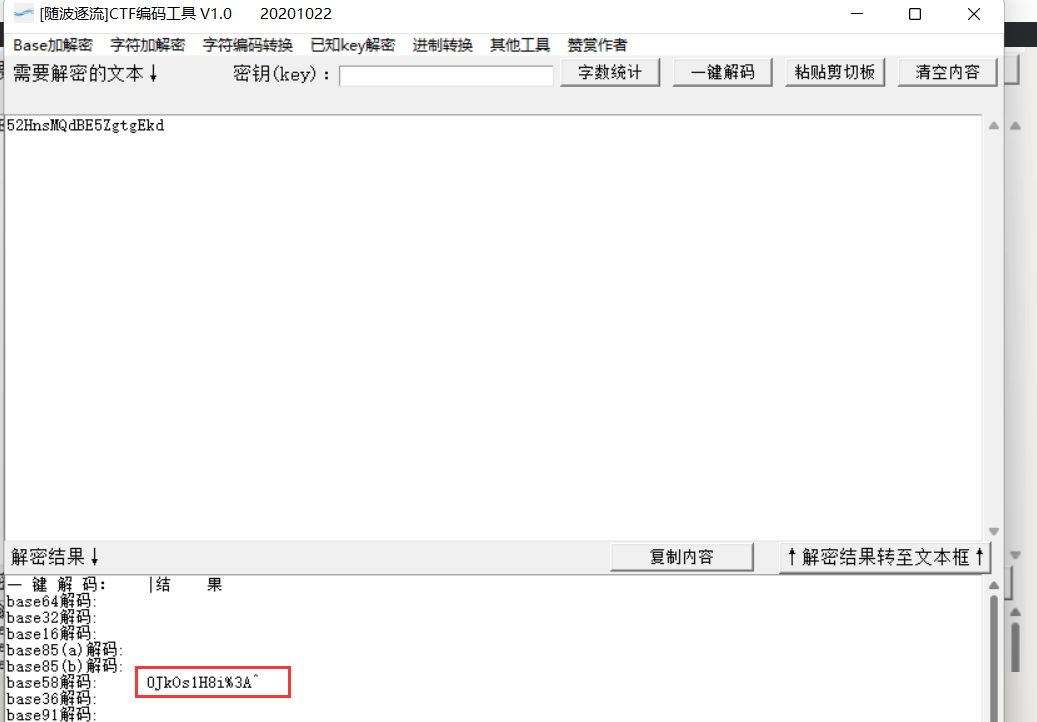
Decode base85(a) again to get 042f38b694
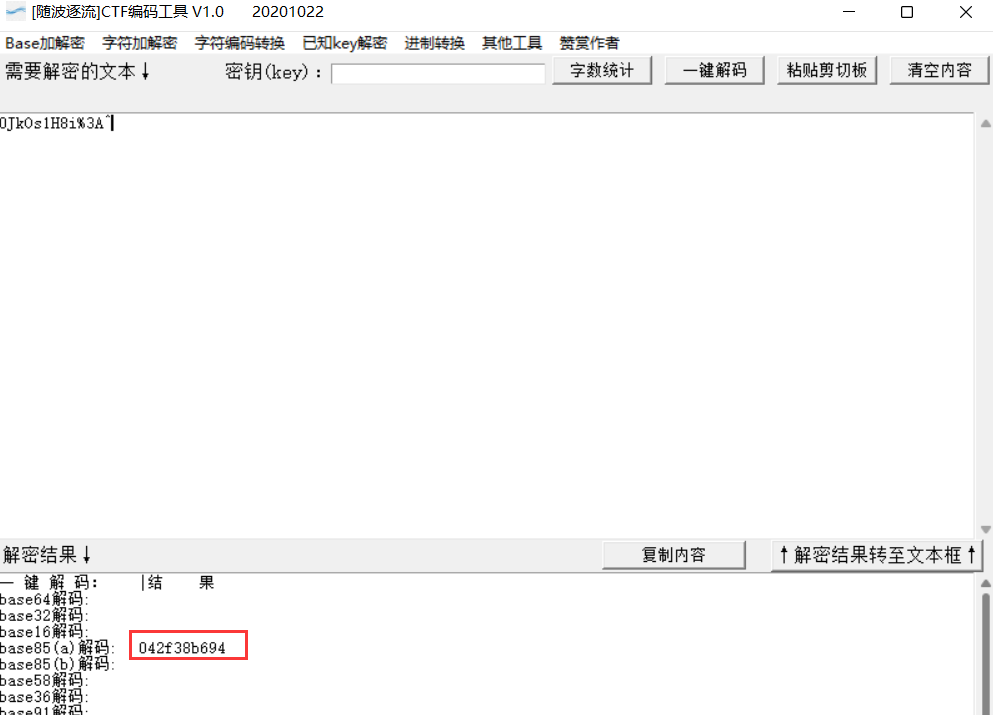
flag_2.txt:b52bff9568
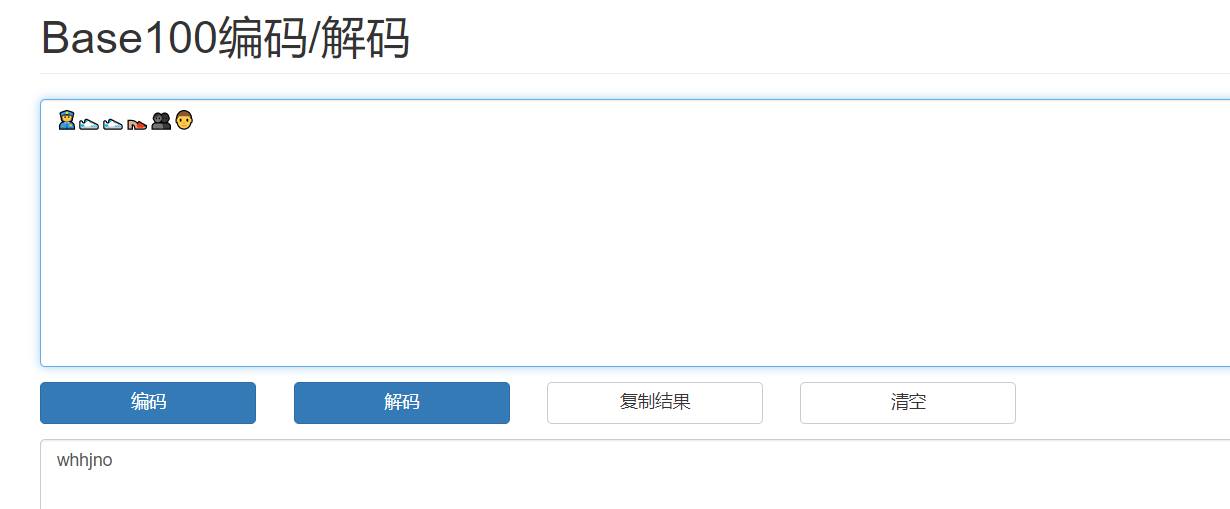
Key can be directly decoded by base100 whhjno
Then enter the Emoji AES decryption website https://aghorler.github.io/emoji-aes/
Direct decryption fails, so try advanced shift. When debugging to 36 bits, you can successfully decrypt and get b52bff9568
flag_3.txt
Open to get a string of characters, throw them into the drift and decode them with one key
Found to be base91, decoded to 37f267472516
U3RlZ2Fub2dyYXBoeSBpcyB0aGUgYXJ0IGFuZCBzY2llbmNlIG9m IHdyaXRpbmcgaGlkZGVuIG1lc3NhZ2VzIGluIHN1Y2ggYSB3YXkgdGhhdCBubyBvbmU= LCBhcGFydCBmcm9tIHRoZSBzZW5kZXIgYW5kIGludGVuZGVkIHJlY2lwaWVudCwgc3VzcGX= Y3RzIHRoZSBleGlzdGVuY2Ugb2YgdGhlIG1lc3M= YWdlLCBhIGZvcm0gb2Ygc2VjdXJpdHkgdGhyb3VnaCBvYnNjdXJpdHkuIFT= aGUgd29yZCBzdGVnYW5vZ3JhcGh5IGlzIG9mIEdyZWVrIG9yaWdpbiBhbmTgbWVhbnMgImNvbmNlYT== bGVkIHdyaXRpbmciIGZyb20gdGhlIEdyZWVrIHdvcmRzIHN0ZWdhbm9zIG1lYW5pbmcgImNv dmVyZWQgb3IgdHJvdGVjdGVkIiwgYW5kIGdyYXBoZWluIG1lYW5pbmdgInRvIHd= cml0ZSIuIFRoZSBmaXJzdCByZWNvcmRlZCB1c2Ugb2YgdGhlIHRlcm0gd2FzIGluIDE0OTkgYnkgSm9o YW5uZXMgVHJpdGhlbWl1cyBpbiBoaXMgU3RlZ2Fub2dyYXBoaWEsIGEgdHJlYd== dGlzZSBvbiBjcnl5dG9ncmF5aHkgYW5kIHN0ZWdhbm9ncmF5aHkgZGlzZ5== dWlzZWQgYXOgYSBib29rIG9uIG1hZ2ljLiBHZW5lcmFsbHksIG1lc3O= YWdlcyB3aWxsIGFwcGVhciB0byBiZSBzb21ldGhpbmcgZWxzZTogaW1hZ2VzLCBhcnRp Y2xlcywgc2hvcHBpbmcgbGlzdHMsIG9yIHNvbWUgb3Q= aGVyIGNvdmVydGV4dCBhbmQsIGNsYXNzaWNhbGx5LCB0aGUgaGlnZGVuIG1lc3NhZ2UgbWF5IGJlIGluIGludmn= c2libGUgaW5rIGJldHdlZW4gdGhlIHZpc2libGUgbGluZXMgb2YgYSBwcml2YXRlIGxldHRlci4= VGhlIGFkdmFudGFnZSBvZiBzdGVnYW5vZ3JhcGh5LCBvdmVyIGNy eXB0b2dyYXBoeSBhbG9uZSwgaXMgdGhhdCBtZXNzYWdlcyBkbyBub3QgYXR0cmFjdCBhdHRlbnRpb26= IHRvIHRoZW1zZWx2ZXMuIFBsYWlubHkgdmlzaWJsZSBlbmNyeXB0ZWQgbWVzc2FnZXPogbRubyBtYXR0ZXIg aG93IHVuYnJlYWthYmxl6IG0d2lsbCBhcm91c2Ugcz== dXNwaWNpb24sIGFuZCBtYXkgaW4gdGhlbXNlbHZlcyBiZSBpbmNyaW1pbmF0aW5nIG== aW4gY291bnRyaWVzIHdoZXJlIGVuY3J5cHRpb24gaXMgaWxsZWdhbC4gVGhlcmVmb3JlLD== IHdoZXJlYXMnY3J5cHRvZ3JhcGh5IHByb3RlY3RzIHRoZSBjb250ZW50cyBvZn== IGEgbWVzc2FnZSwgc3RlZ2Fub2dyYXBoeSBjYW4gYmUgc2FpZCB0byBwcm90ZWN0IGI= b3RoIG1lc3NhZ2VzIGFuZCBjb21tdW5pY2F0aW5nIHBhcnRpZXMu U3RlZ2Fub2dyYXBoeSBpbmNsdWRlcyD= dGhlIGNvbmNlYWxtZW51IG9mIGluZm9ybWF1aW9uIHdpdGhpbiBjb21= cHV0ZXIgZmlsZXMuIEluIGRpZ2l0YWwgc3RlZ2Fub2dyYXBoeSwgZWxlY3Ryb25pYyBjb21tdW5pY2F0aW9u cyBtYXkgaW5jbHVkZSBzdGVnYW5vZ3JhcGhpYyBjb2RpbmcgaW5zaQ== ZGUgb2YgYSB0cmFuc3BvcnQgbGF5ZXIsIHN1Y2ggYXMgYSBkb2N1bWVudCBmaWxlLCBpbWFnZSBmaWz= ZSwgcHJvZ3JhbSBvciBwcm90b2NvbC4gTWVkaWEg ZmlsZXMgYXJlIGlkZWFsIGZvciBzdGVnYW5vZ3JhcGhpYyB0cmFuc21pc3Npb3== biBiZWNhdXNlIG9mIHRoZWlyIGxhcmdlIHNpemUuIEFzID== YSBzaW1wbGUgZXhhbXBsZSwgYSBzZW5kZXIgbWlnaHQgc3RhcnQgd2l0aCBh biBpbm5vY3VvdXMgaW1hZ2UgZmlsZSBhbmQgYWRqdXN0IHRoZSBjb2xvciBvZiBldmVyeSAxMDB0aCBwaXhlbCA= dG8gY29ycmVzcG9uZCB0byBhIGxldHRlciBpbiB0aGUgYWxwaGFiZXQsIGG= IGNoYW5nZSBzbyBzdWJ0bGUgdGhhdCBzb21lb25lIG5vdCBzcGVjaWZpY2FsbHkgbG9va2luZyBm b3IjaXQjaXMjdW5saWtlbHkjdG8jbm90aWNlIGl0Lj== VGhlJGZpcnN0JHJlY29yZGVkJHVzZXMgb2Ygc3RlZ2Fub2dyYXBoeSBjYW4gYmUgdHJ= YWNlZCBiYWNrIHRvIDQ0MCBCQyB3aGVuIEhlcm9kb3R1cyBtZW50aW9ucyB0d28gZXhhbXBsZXMgb0== ZiBzdGVnYW5vZ3JhcGh5IGluIFRoZSBIaXN0b3JpZXMgb2Yg SGVyb2RvdHVzLiBEZW1hcmF0dXMgc2VudCBhIHdhcm5pbmcgYWJvdXQgYSD= Zm9ydGhjb21pbmcgYXR0YWNrIHRvIEdyZWVjZSBieSB3 cml0aW5nIGl0IGRpcmVjdGx5IG9uIHRoZSB3b29kZW4gYmFja2luZyBvZiBhIHdheCB0YWJsZXQgYmVm b3JlIGFwcGx5aW5nIGl0cyBiZWVzd2F4IHN1cmZhY2UuIFdheCB0YWJsZXRzIHdlcmUgaW4gY29tbW9uIHVzZR== IHRoZW4gYXMgcmV1c2FibGUgd3JpdGluZyBzdXJmYWNlcywgc29tZXRpbWU= c3VzZWQgZm9yIHNob3J0aGFuZC4gQW5vdGhlciBhbmNpZW50IGV4YW1wbGUgaXMgdGhhdCBv Zkhpc3RpYWV1cywgd2hvIHNoYXZlZCB0aGUgaGVhZCBvZiBoaXPgbW9zdCB0cnVzdGVkIHP= bGF2ZSBhbmQgdGF0dG9vZWQgYSBtZXNzYWdlIG9uIGl0LiBBZnRlciBoaXMgaGFpciBoYWQgZ2== cm93biB0aGUgbWVzc2FnZSB3YXMgaGlkZGVuLiBUaGUgcHVycG9zZSB3YXMgdG8= aW5zdGlnYXRlIGEgcmV2b2x0IGFnYWluc3QgdGhlIFBlcnNpYW5zLg== U3RlZ2Fub2dyYXBoeSBoYXMgYmVlbiB3aWRlbHkgdXNlZCwg aW5jbHVkaW5nIGluIHJlY2VudCBoaXN0b3JpY2FsIHRpbWVzIGFuZCB0 aGUgcHJlc2VudCBkYXkuIFBvc3NpYmxlIHBlcm11dGF0aW9ucyBhcmUgZW5kbGVzcyBhbmQ= a25vd24gZXhhbXBsZXMgaW5jbHVkZTo= SGlkZGVuIG1lc3NhZ2VzIHdpdGhpbiB3YXggdGE= YmxldHM6IGluIGFuY2llbnQgR3JlZWNlLCBwZW9wbGUgd3JvdGUgbWU= c3NhZ2VzIG9uIHRoZSB3b29kLCB0aGVuIGNvdmVyZWQgaXQgd2l0aCB3YXggdXBvbiB3aGljaCBhbiBpbm5vY2Vu dCBjb3ZlcmluZyBtZXNzYWdlIHdhcyB3cml0dGVu SGlkZGVuIG1lc3NhZ2VzIG9uIG1lc3NlbmdlcidzIGJvZHk6IGFsc28gdXNlZCBpbiBhbmNpZW4=
Decode base64 again
Steganography is the art and science of writing hidden messages in such a way that no one
Such a long base64 cannot only get such a string of English, so I guess base64 is steganographic, and 37f267472516 is obtained through python script
The script is as follows:
import re
import base64
b64chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
# ccc.txt is the file where the base64 steganographic string to be decrypted is located
f = open('ccc.txt','r')
base64str = f.readline()
# pattern2 is the character before the equal sign when matching two equal signs
# pattern2 is used to match the character before the equal sign when an equal sign is used
pattern2 = r'(\S)==$'
pattern1 = r'(\S)=$'
# The extracted steganographic binary characters are added to binstring
binstring = ''
# Read the base64 steganographic string to be decrypted line by line and process it line by line
while(base64str):
# Match two equal signs first. If not, configure another equal sign
# If there is no equal sign, it is not hidden and does not need to be processed
if re.compile(pattern2).findall(base64str):
# mstr is a character before the equal sign, which is the character where the steganographic binary information is located
mstr = re.compile(pattern2).findall(base64str)[0]
# Confirm the base64 binary number corresponding to mstr character and assign it to mbin
mbin = bin(b64chars.find(mstr))
# Mbin format, such as 0b100, mbin[0:2] is 0b
# mbin[2:].zfill(6) is to supplement the binary number after 0b with 0 so that the length after 0b is 6
mbin2 = mbin[0:2] + mbin[2:].zfill(6)
# The 4-bit binary number is hidden in the two equal signs, so the last 4 bits of mbin2 are extracted
# Assigned to stegobin, this is the hidden binary information
stegobin = mbin2[-4:]
binstring += stegobin
elif re.compile(pattern1).findall(base64str):
mstr = re.compile(pattern1).findall(base64str)[0]
mbin = bin(b64chars.find(mstr))
mbin2 = mbin[0:2] + mbin[2:].zfill(6)
# In an equal sign case, 2-bit binary numbers are steganographed, so the last 2 bits of mbin2 are extracted
stegobin = mbin2[-2:]
binstring += stegobin
base64str = f.readline()
# stegobin stitches together the hidden binary characters in each row
# Starting from bit 0, 8bit and 8bit processes, so the step of range is 8
for i in range(0,len(binstring),8):
# int(xxx,2), convert binary string to decimal integer, and then chr() to character
print(chr(int(binstring[i:i+8],2)),end='')
So the flag is:
flag{042f38b694b52bff956837f267472516}
Misc3: huahua
Download the attachment to get huahua.zip, but it can't be opened, so it is thrown into 010 to analyze the structure. It is found that the file header is abnormal. The normal zip file header is 50 4B 03 04
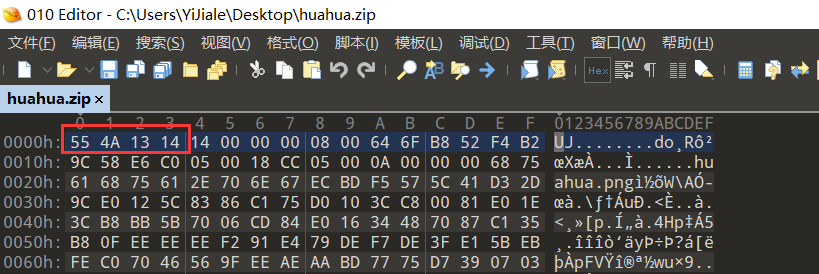
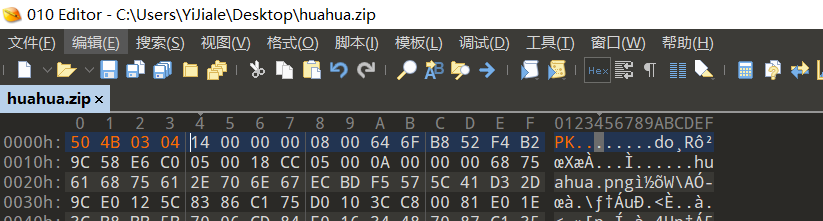
After saving, open it again to get a huahua.png. The same picture cannot be opened and is thrown into 010
[the external chain picture transfer fails. The source station may have an anti-theft chain mechanism. It is recommended to save the picture and upload it directly (IMG ggrchgtl-1634977125660)( http://img.le1a.com/2021/10/23/9f9a9abc4f1a9.png )]
The front of normal 49 should be 89 50 4E 47 0d 0A 1A 0A 00 00 0d. huahua.png lacks 89 50 4E 47
Fill in the file header and open it to get a normal picture

Modify the height to get the flag

So the flag is:
flag{b3afc91a8fbb6cc798bdebb253b02550}
Misc4:NOISE
Download the attachment. There are three files in it. The out file is dropped into 010. It is found that it is a wav audio file
Add the. wav suffix to the out file, then open it with Audacity, analyze the spectrum diagram and get the flag
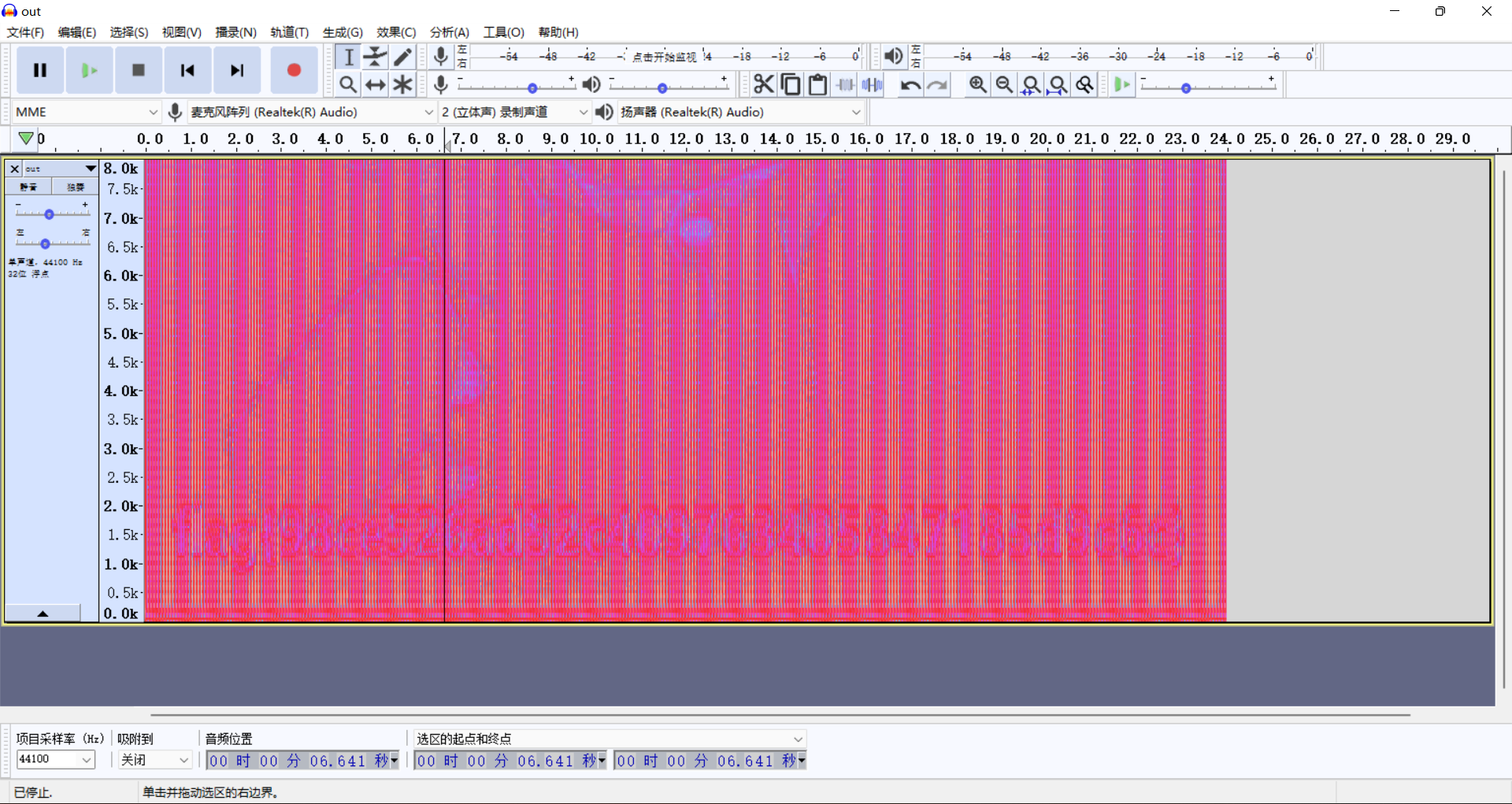
So the flag is:
flag{98ce526ad52c409763405847185d9c6c}
Misc5:DdDdDd
Open the traffic package and export the http traffic. It is found that Smashing%20Wolt.gcode is the G language
use https://ncviewer.com/ Website online compilation
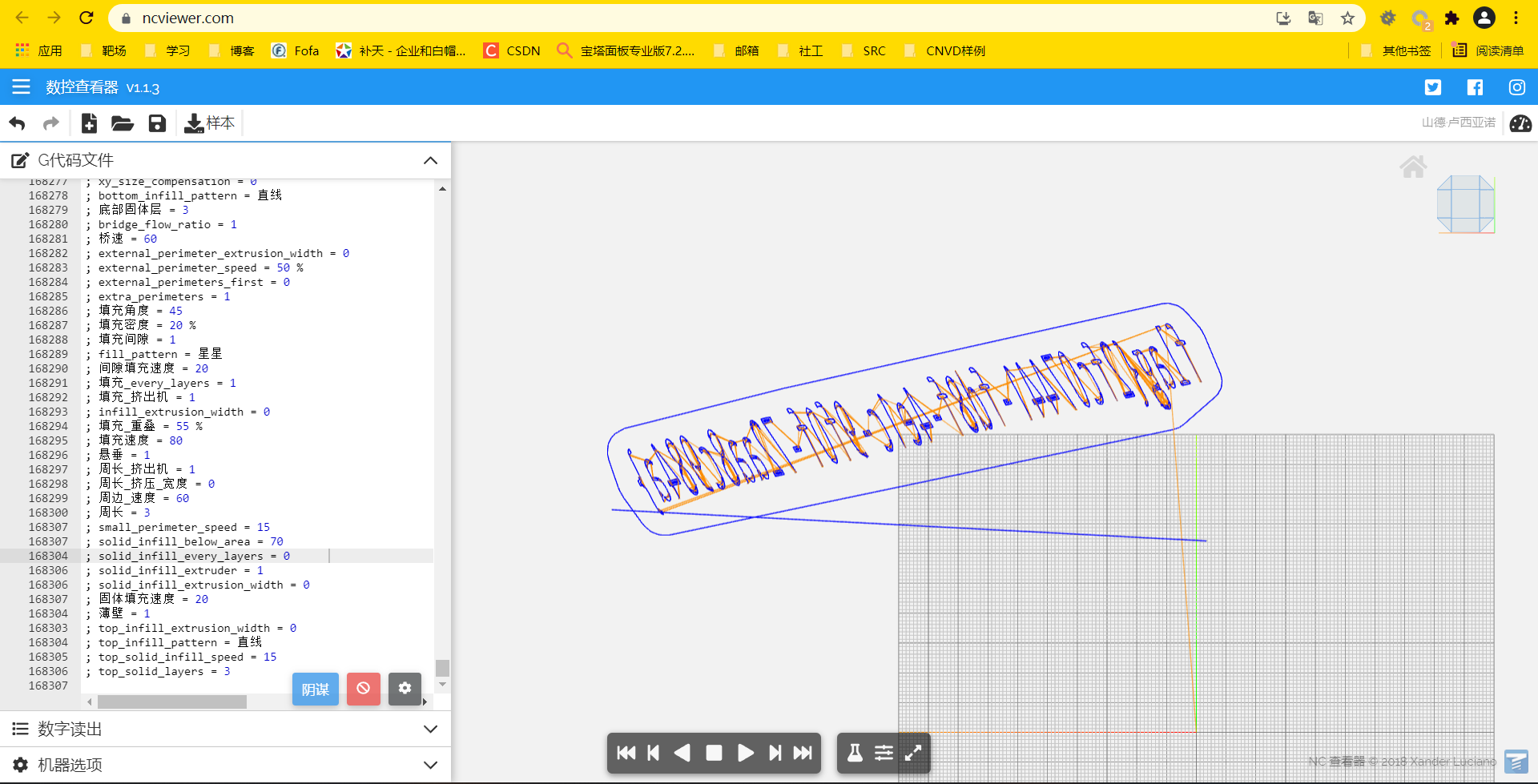
You can adjust the angle in the upper right corner to get the flipped flag. Take a screenshot and use the online tool https://www.91gif.com/giffanzuan/ You can flip the mirror over
The obtained flag is:
flag{2fc07441-fd8f-4e1c-9f0f-72aa8c984a}
Misc6:Forensic
Download the attachment, analyze the memory with vol.exe, and directly find the file with flag
Command:
vol.exe -f data.raw --profile=Win7SP1x64 filescan |findstr /r "flag"
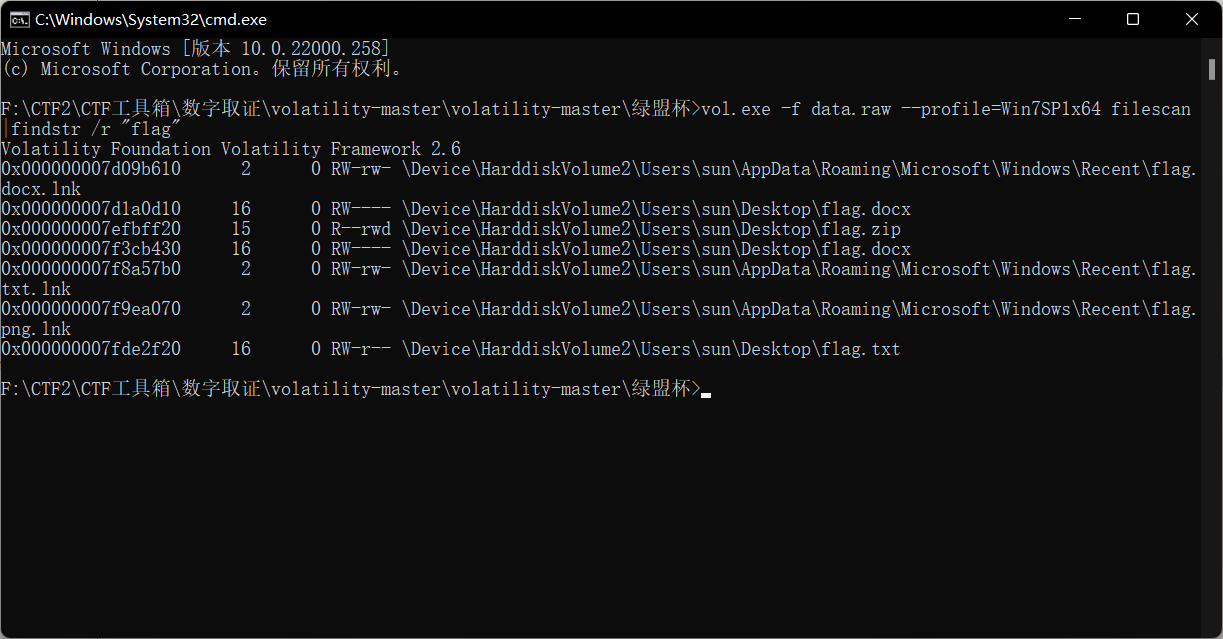
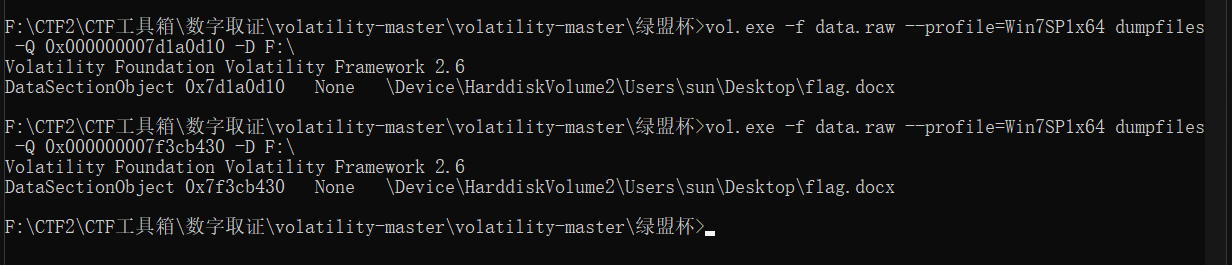
There are two flag.docx, one flag.zip, one flag.zip cannot be exported, and one flag.docx contains base64, but it is hidden
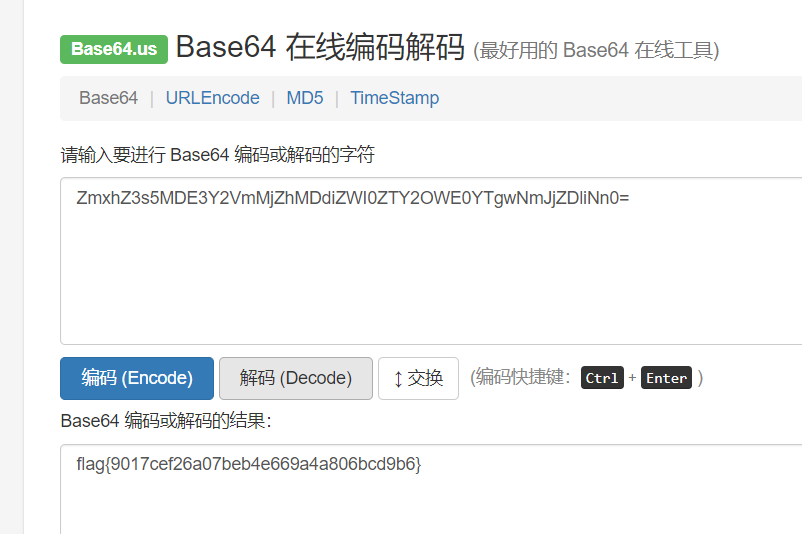
Unhide and decrypt the flag:
flag{9017cef26a07beb4e669a4a806bcd9b6}
Misc7: hidden data
Download the attachment to get a flag.zip and a word document
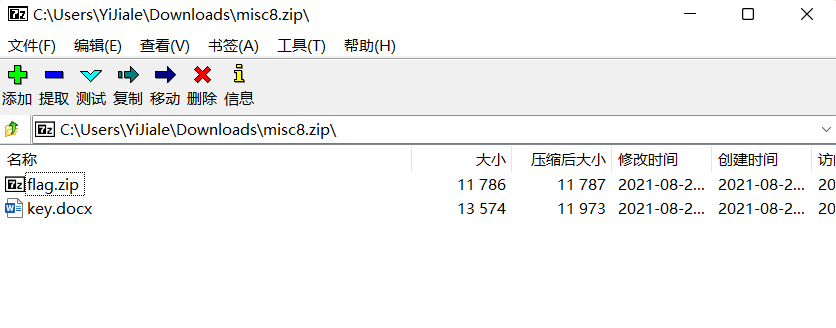
Open flag.zip and find that there is a flag file in it. After 010 analysis, it is found that it is a pseudo encrypted compressed package, but 7z you can ignore the pseudo encryption, so open it directly and there is another flag file in it
Open it again and find that you need a password. Blow it up and get the password 0546
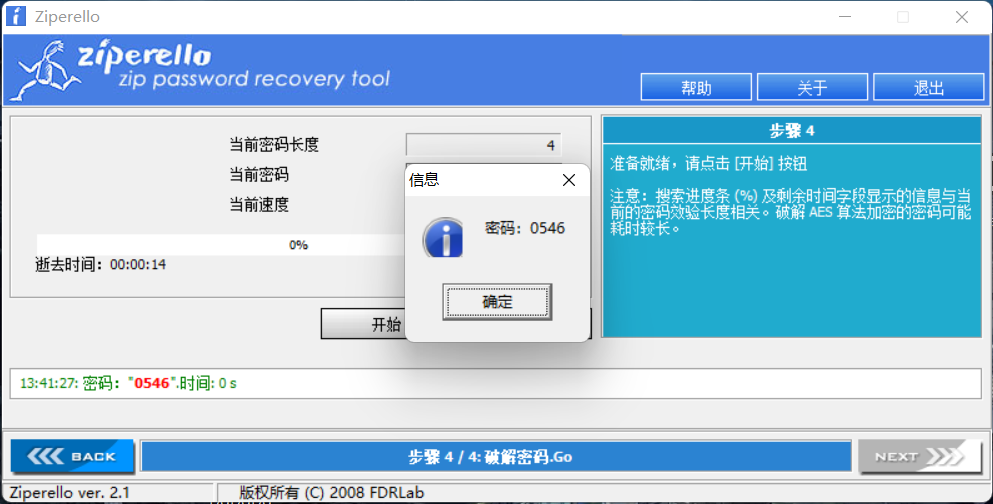
Open the compressed package to get the flag_not_here.docx, I tried to open it. I found that I needed a password and couldn't burst it. So I thought that the word document had not been opened at the beginning
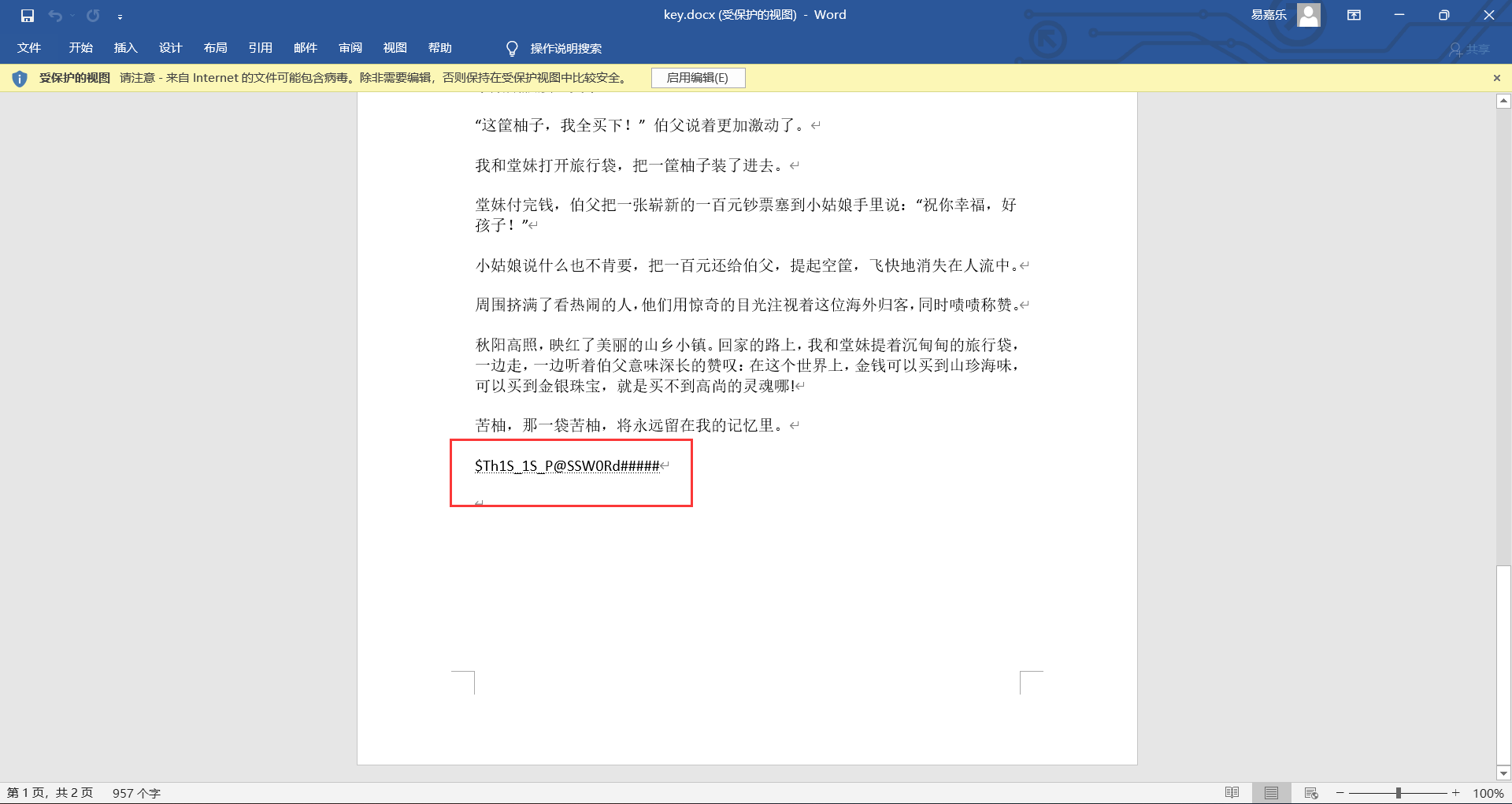
There is a password $th1s in it_ 1S_ P@SSW0Rd #####
With this password, you can open the flag just now_ not_ here.docx
Nothing was found in it, so I changed. docx to. zip, and then opened the compressed package to view the structure of the word document
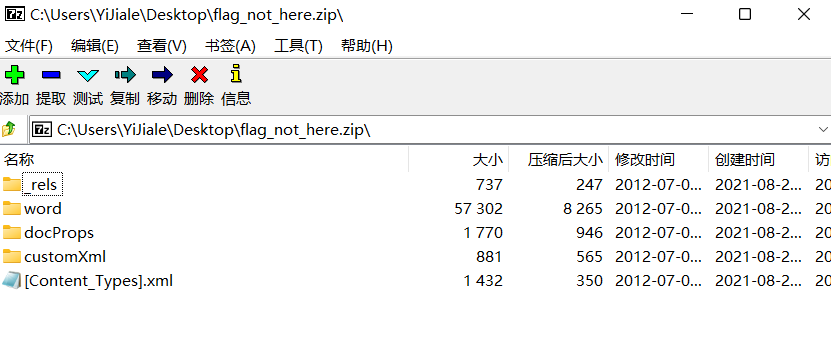
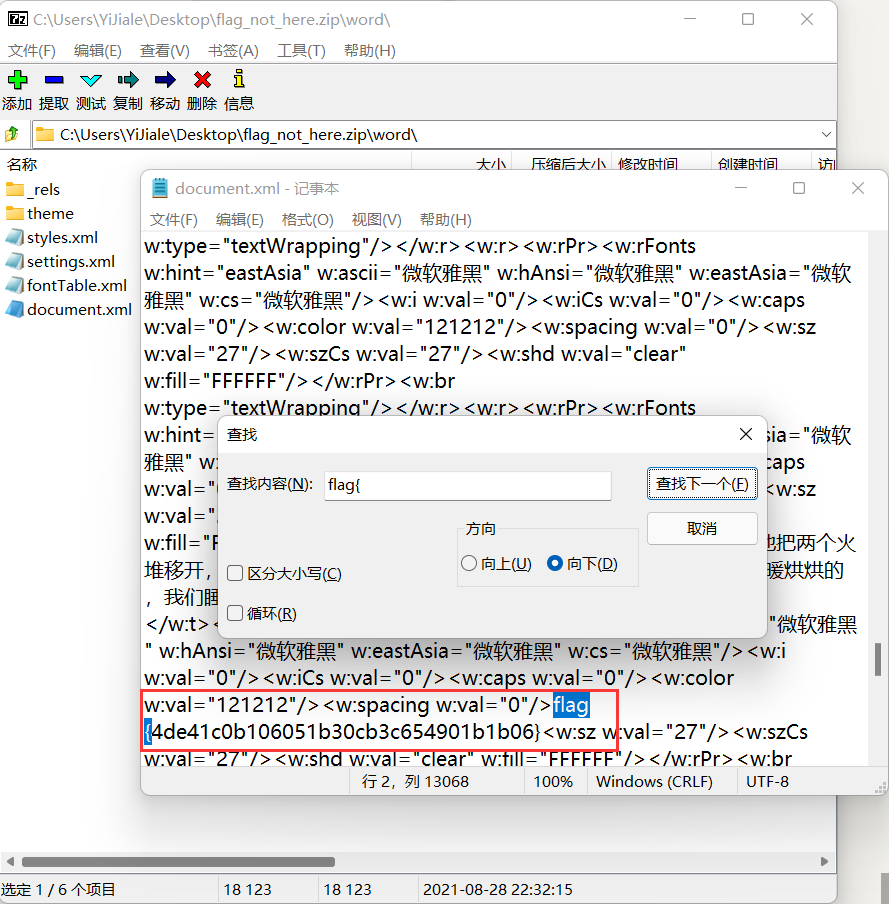
flag found in document.xml:
flag{4de41c0b106051b30cb3c654901b1b06}
Misc8:something in picture
This is the original title of the fifth strong net cup Threebody. Post a wp link to the original title https://www.sohu.com/a/472787619_ one hundred and twenty-one million one hundred and eighteen thousand nine hundred and ninety-six
flag:
flag{D1mEn5i0nAl_Pr061em}